Total Catalog Index: K8s Network Calico From Getting Started to Abandoning Series
1. Create Front End, Back End, Client and Manage User Interface Applications
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/manifests/00-namespace.yaml
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/manifests/01-management-ui.yaml
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/manifests/02-backend.yaml
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/manifests/03-frontend.yaml
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/manifests/04-client.yaml
Wait for all pod s to be running
kubectl get pod --all-namespaces
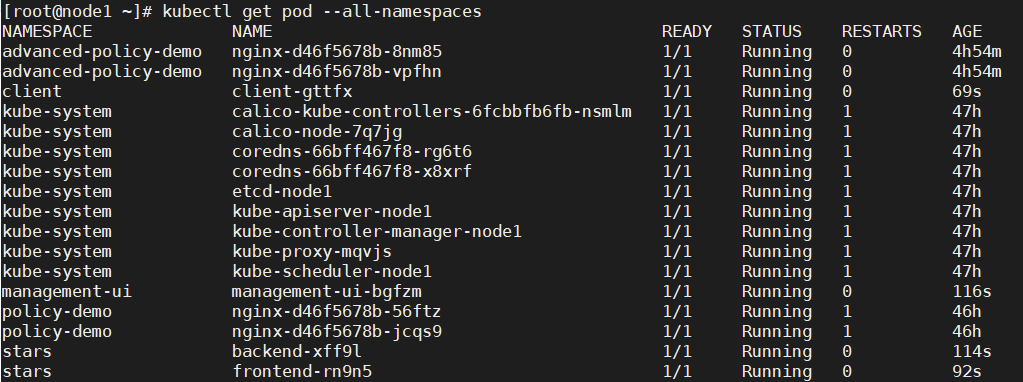
You can view the UI by accessing it in a browser at http://worker IP:30002.
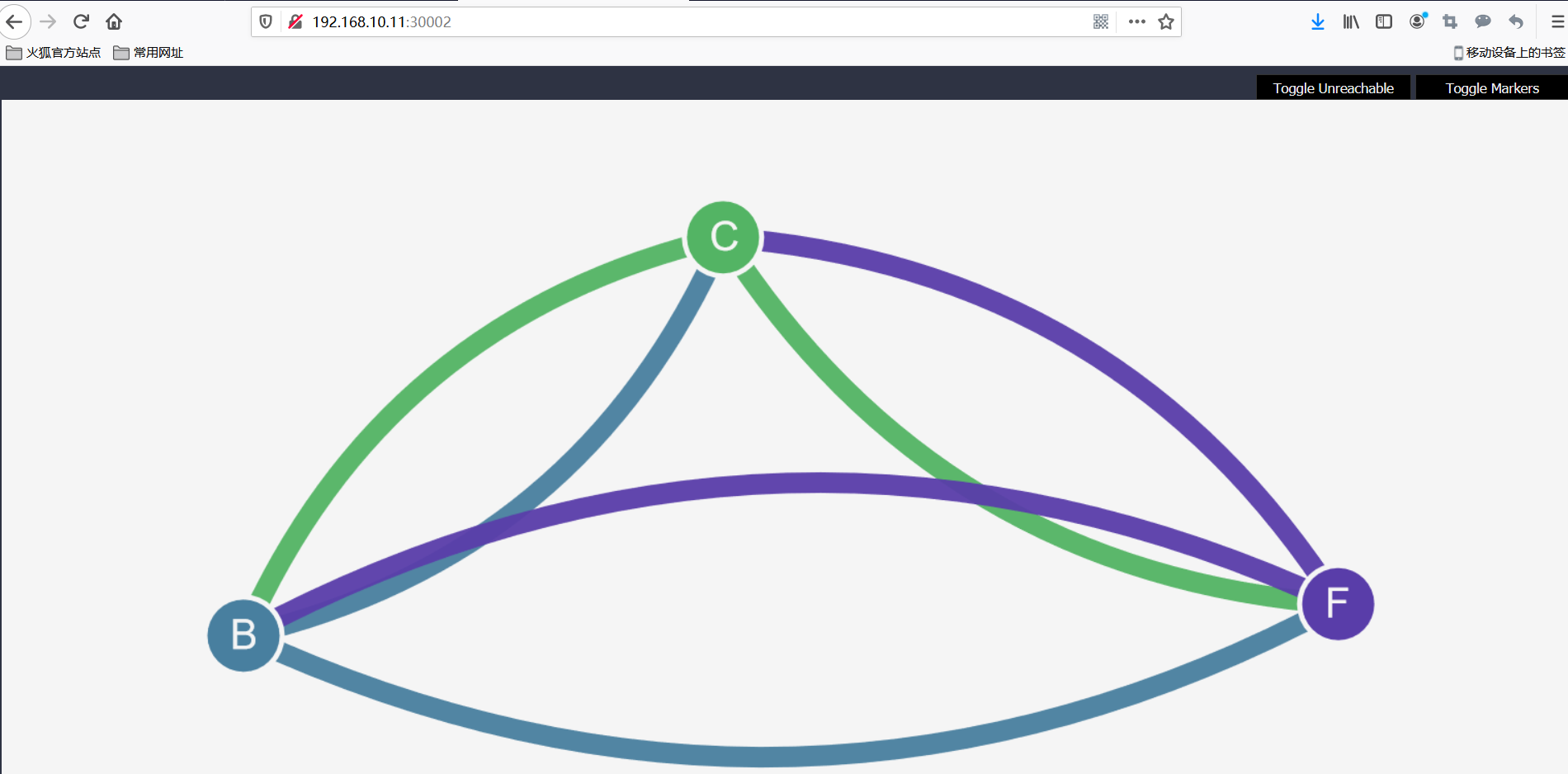
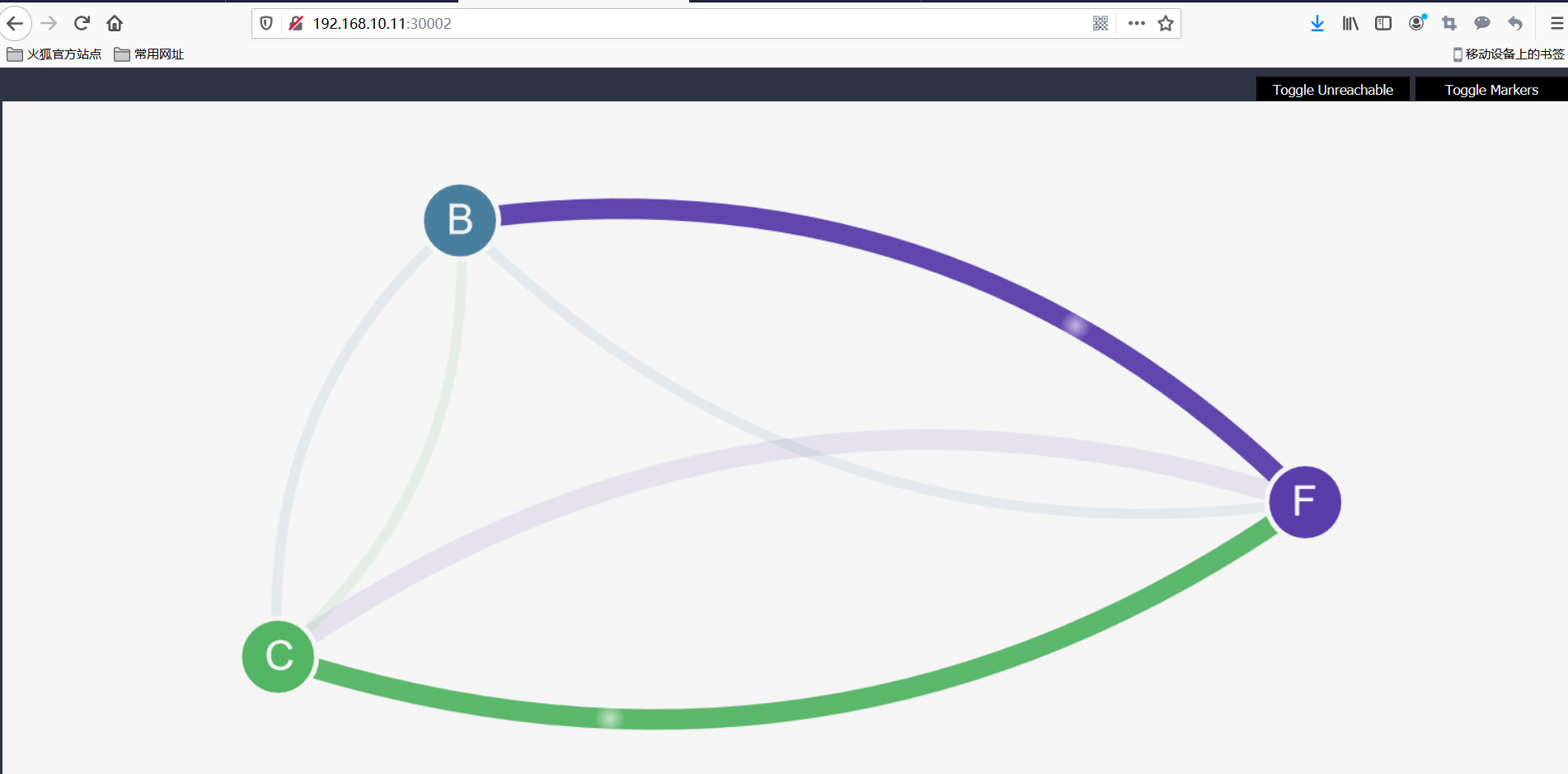
Once all Pod s are started, they should be fully connected.You can view it by accessing the UI.Each service is represented by a single node in the diagram.
backend ->node "B"
Frontend ->node "F"
client ->Node "C"
2. Enable isolation
Running the following command will prevent all access to front-end, back-end, and client services
kubectl create -n stars -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/policies/default-deny.yaml
kubectl create -n client -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/policies/default-deny.yaml
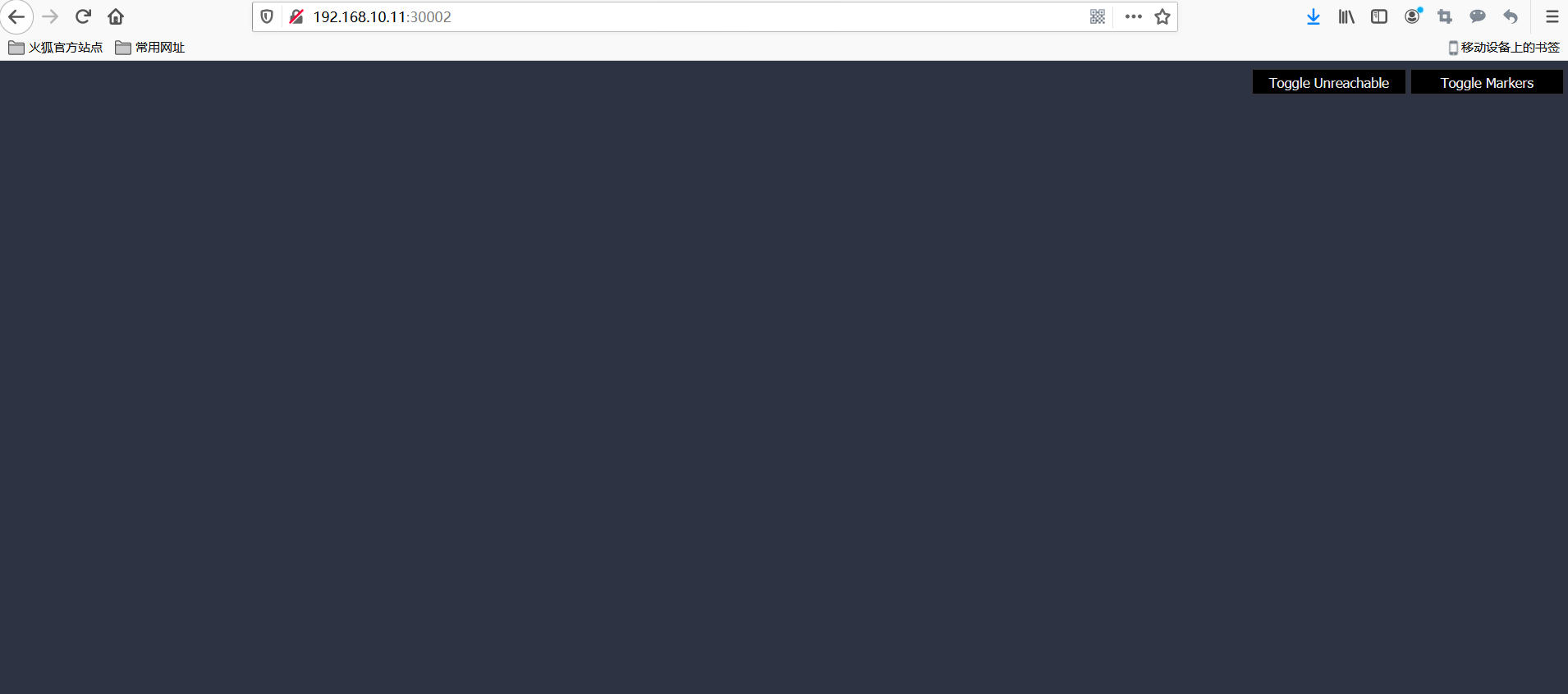
Confirm isolation
Refresh the management user interface (changes may take up to 10 seconds to be reflected in the user interface).Now that isolation is enabled, the UI will no longer be able to access panes, so they will no longer appear in the UI.
3. Allow UI to access services using Network Policy Objects
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/policies/allow-ui.yaml
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/policies/allow-ui-client.yaml
After a few seconds, refresh the UI - services should now be displayed, but they no longer have access to each other
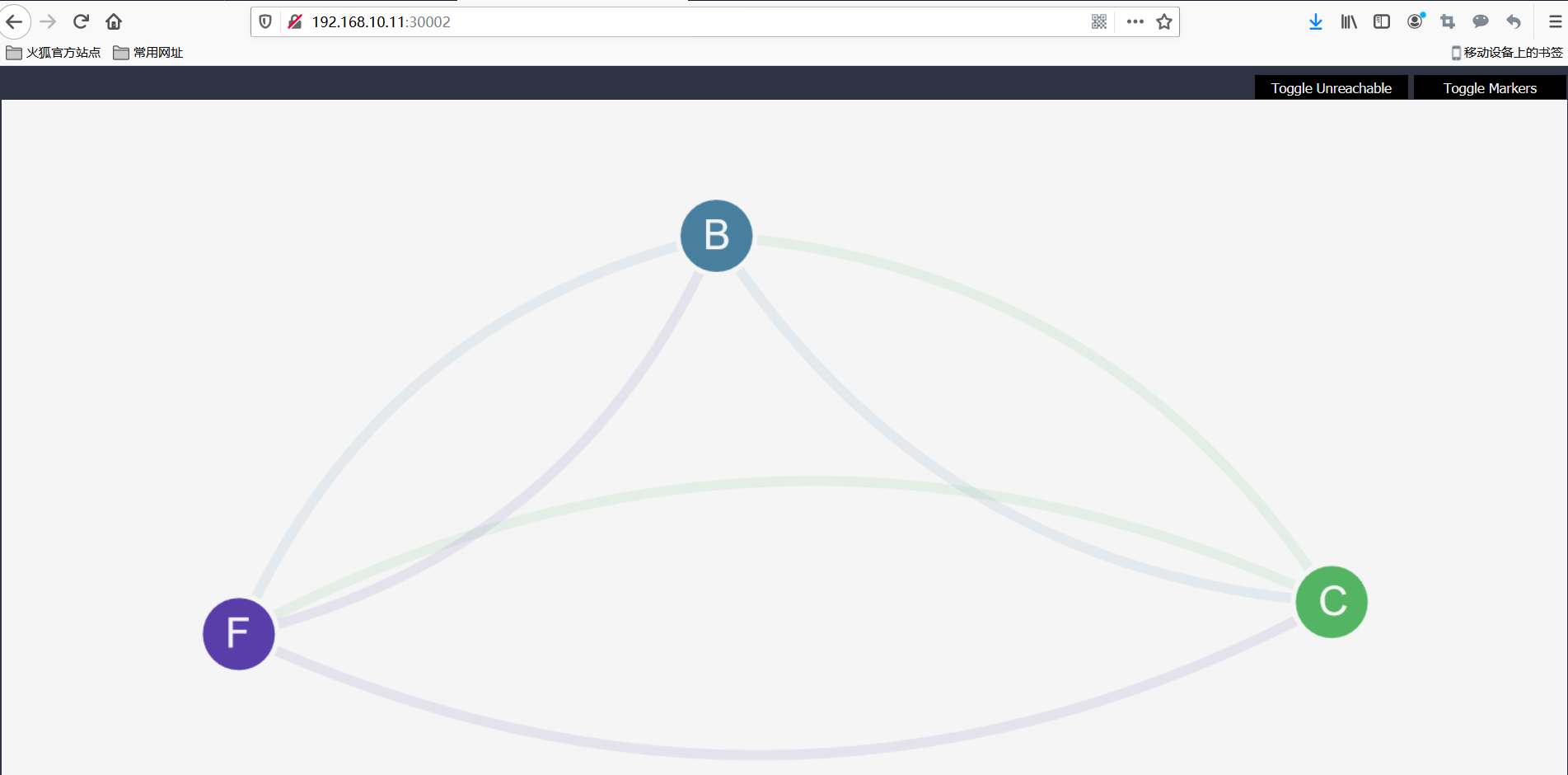
4. Create a backend-policy.yaml file to allow traffic from the front end to the back end
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/policies/backend-policy.yaml
Refresh UI.You should see the following:
The front end can now access the back end (only on TCP port 6379).
The back end has no access to the front end at all.
Clients cannot access either the front end or the back end.
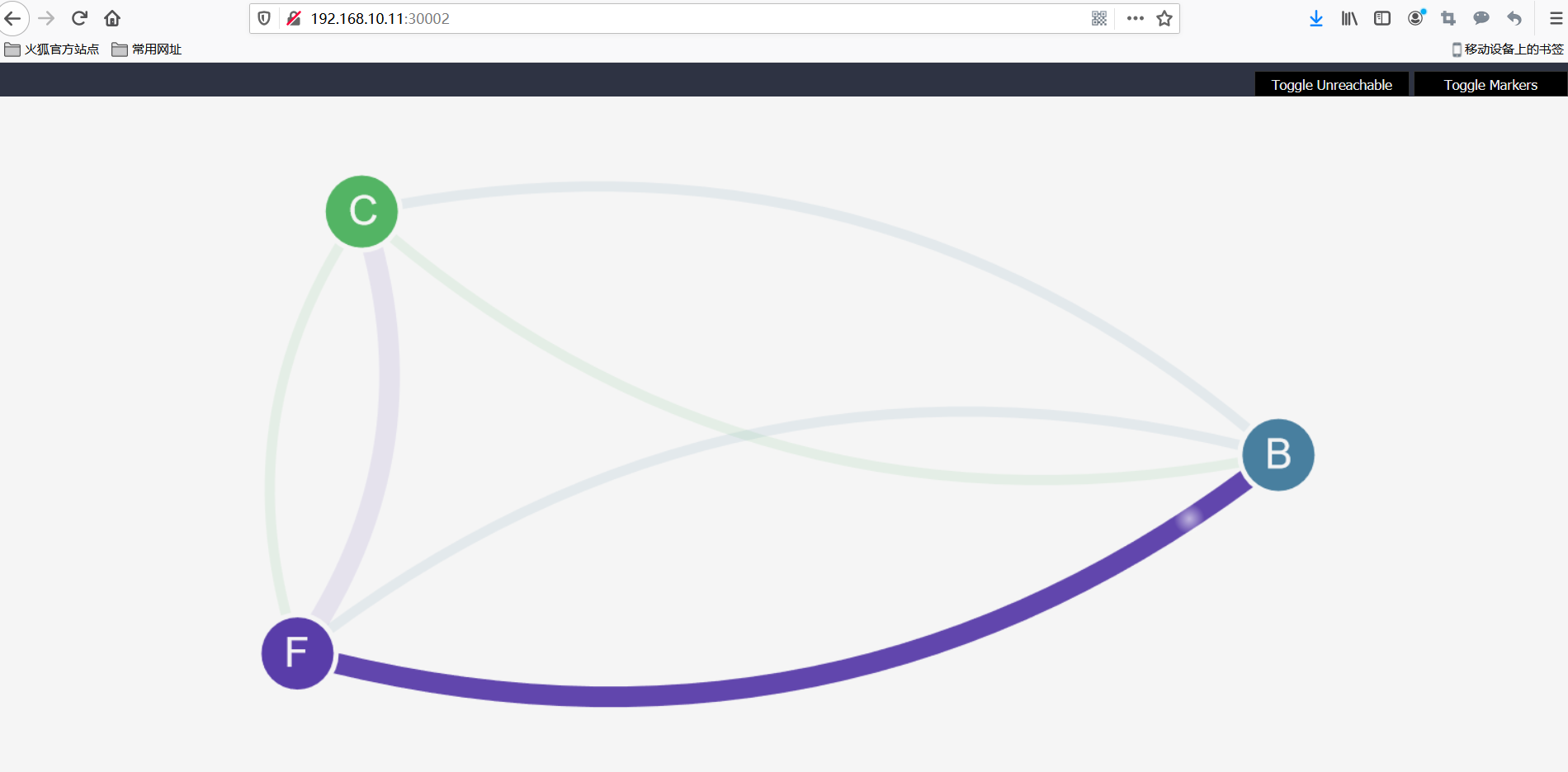
5. Exposing front-end services to client namespaces
kubectl create -f https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/policies/frontend-policy.yaml
Clients can now access the front end, but not the back end.Neither the front-end nor the back-end can start a connection to the client.Front end still has access to back end
6. Clean up the namespace
kubectl delete ns client stars management-ui
Reference article: https://docs.projectcalico.org/security/tutorials/kubernetes-policy-demo/kubernetes-demo