Recently, all kinds of servers have been intruded, so in terms of security, we should pay great attention to it. We hereby record that we can use google's authentication plug-in to obtain dynamic authentication code to complete ssh login.
OS:
centos7
Installation configuration:
1. Install epel source
yum -y install epel-release
2. Install Qrencode, and Google authenticator generates QR code through the program
yum install -y qrencode
3. Install Google authenticator, compile and install
git clone https://github.com/google/google-authenticator-libpam.git cd google-authenticator-libpam/
./bootstrap.sh
./configure –prefix=/usr/local/google-authenticator
make && make install
4. Copy the authentication pam module of google to the system
cp /usr/local/google-authenticator/lib/security/pam_google_authenticator.so /lib64/security/
5. Configure the pam authentication of sshd, write it in the upper line of auth include password auth password based authentication, and first authenticate based on google verification code
auth required pam_google_authenticator.so
6. Modify ssh service configuration
ChallengeResponseAuthentication yes
7. Restart ssh service
systemctl restart sshd
8. Enter the Google authenticator libpam directory just cloned and execute
./google-authenticator #Verify based on the current user. If you want to switch other system users, please log in to other users and execute this command
Do you want authentication tokens to be time-based (y/n) y #Enter y to prompt for time-based authentication
Next, a QR code image will be generated: download the authentication app software on the mobile phone and scan the QR code

Your new secret key is: JS57SLVUDEEA7SQ7LD6BEBWGAA #This security key needs to be backed up for subsequent replacement of mobile phones or loss of QR code. After the authentication of browser is lost, can you obtain new authentication through this security key Your verification code is 005421 #After scanning the above QR code, check the verification and input Your emergency scratch codes are: # Are the following verifications for future use? They can only be verified once 45412365 21522365 85124632 85124631 14785216 Do you want me to update your "/root/.google_authenticator" file (y/n) y Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) y By default, tokens are good for 30 seconds. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. If you experience problems with poor time synchronization, you can increase the window from its default size of +-1min (window size of 3) to about +-4min (window size of 17 acceptable tokens). Do you want to do so? (y/n) y # Security related, continue by default If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting (y/n) y # Security related, continue by default
9. xshell terminal configuration log in linux host based on google authentication
The connection mode of xshell terminal is changed to: keyboard Interactive
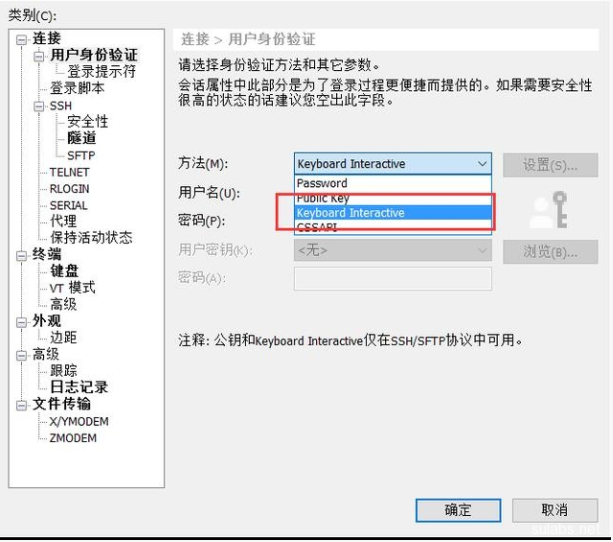
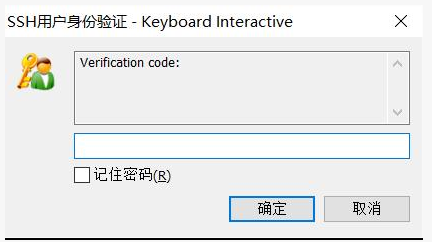
Secondary verification code input:
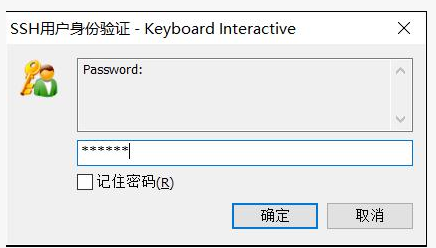
Enter system password:
The above is ssh login based on google authentication.