1.Linux Security Model
Resource allocation:
- Authentication: authentication to verify the user's identity
- Authorization: authorization. Different users set different permissions
- Accounting audit
When the user logs in successfully, the system will automatically assign a token, including user ID, group member and other information
1.1 users
In Linux, each user is uniquely identified by User Id (UID)
- Administrator: root, 0
- Ordinary users: 1-60000 automatic allocation
- System users: 1-499 (before CentOS 6), 1-999 (after CentOS 7)
- Allocate permissions to the resources obtained by the daemon
- Login user: 500 + (before CentOS6), 1000 + (after CentOS7)
- Interactive login for users
- System users: 1-499 (before CentOS 6), 1-999 (after CentOS 7)
1.2 user groups
In Linux, one or more users can be added to a user group, which is uniquely identified by Group ID (GID).
- Administrator group: root, 0
- General group:
- System group: 1-499 (before CentOS 6) and 1-999 (after CentOS 7) to allocate permissions to the resources obtained by the daemon
- Common group: 500 + (before CentOS 6) and 1000 + (after CentOS 7) for users
example:
[root@rocky8 ~]# id raymond id: 'raymond': no such user [root@rocky8 ~]# useradd raymond;echo 123456 | passwd --stdin raymond Changing password for user raymond. passwd: all authentication tokens updated successfully. [root@rocky8 ~]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond) [root@rocky8 ~]# id root uid=0(root) gid=0(root) groups=0(root)
1.3 relationship between users and groups
- User's primary group: a user must belong to one and only one primary group. By default, a group with the same name as the user name will be automatically created when creating a user as the user's primary group. Because there is only one user in this group, it is also called a private group
- Supplementary group: a user can belong to zero or more auxiliary groups and affiliated groups
example:
[root@rocky8 ~]# id postfix uid=89(postfix) gid=89(postfix) groups=89(postfix),12(mail)
1.4 security context
Linux security Context: a running program, that is, a process, runs as the initiator of the process. The permissions of the process to access resources depend on the identity of the operator of the process
For example, if you run / bin/cat /etc/shadow as root and wang respectively, the results are different. Whether resources can be accessed is determined by the identity of the operator, not the program itself
example:
[root@rocky8 ~]# cat /etc/shadow root:$6$U/LuWNVHLX6clXpP$BxhDbz7cPwm7gEkDmpwihdC/FpCPkeJ6iiM/Dvp96b.d0O0pN6oawZFpIE62JT3KNwz68sy2Lgjhhj7GYsFtG1::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18898:::::: systemd-coredump:!!:18898:::::: systemd-resolve:!!:18898:::::: tss:!!:18898:::::: polkitd:!!:18898:::::: sssd:!!:18898:::::: sshd:!!:18898:::::: postfix:!!:18900:::::: raymond:$6$vrjGOXHemHh7iLRM$MWPT.XZC7yEfkrhBXovPVPxowO4T6h7yO7Ve/iBljliSAnVbrMvIRZQoCUYvodt3nJWrifd2n1PHZQMHSZay5.:18905:0:99999:7:::
2. User and group profiles
2.1 main profiles of users and groups
- /etc/passwd: user and its attribute information (name, UID, primary group ID, etc.)
- /etc/shadow: user password and related attributes
- /etc/group: group and its attribute information
- /etc/gshadow: group password and its related attributes
2.2 passwd file format
Login name: login name (raymond)
passwd: password (x)
UID: user ID number (1000)
GID: default login group number (1000)
GECOS: full user name or comment
Home directory: user home directory (/ home/raymond)
Shell: the user uses shell (/bin/bash) by default
example:
[root@rocky8 ~]# cat /etc/passwd root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin systemd-coredump:x:999:997:systemd Core Dumper:/:/sbin/nologin systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin tss:x:59:59:Account used for TPM access:/dev/null:/sbin/nologin polkitd:x:998:996:User for polkitd:/:/sbin/nologin sssd:x:997:994:User for sssd:/:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin raymond:x:1000:1000::/home/raymond:/bin/bash [root@rocky8 ~]# yum -y install man-pages [root@rocky8 ~]# whatis passwd openssl-passwd (1ssl) - compute password hashes passwd (1) - update user's authentication tokens passwd (5) - password file [root@rocky8 ~]# man 5 passwd
2.3 shadow file format
Login name
User password: generally encrypted with sha512
From January 1, 1970 to the time when the password was last changed
The password can be changed in a few days (0 means it can be changed at any time)
The password must be changed in a few days (99999 means it will never expire)
The system will remind the user a few days before the password expires (one week by default)
The account will be locked a few days after the password expires
From January 1, 1970, how many days after the account expires
Password security policy
- Long enough
- Use at least 3 of numbers, uppercase letters, lowercase letters and special characters
- Use random password
- Change the password regularly and do not use the password that has been used recently
example:
[root@rocky8 ~]# ll /etc/shadow ---------- 1 root root 768 Oct 5 20:09 /etc/shadow [root@rocky8 ~]# cat /etc/shadow root:$6$U/LuWNVHLX6clXpP$BxhDbz7cPwm7gEkDmpwihdC/FpCPkeJ6iiM/Dvp96b.d0O0pN6oawZFpIE62JT3KNwz68sy2Lgjhhj7GYsFtG1::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18898:::::: systemd-coredump:!!:18898:::::: systemd-resolve:!!:18898:::::: tss:!!:18898:::::: polkitd:!!:18898:::::: sssd:!!:18898:::::: sshd:!!:18898:::::: postfix:!!:18900:::::: raymond:$6$vrjGOXHemHh7iLRM$MWPT.XZC7yEfkrhBXovPVPxowO4T6h7yO7Ve/iBljliSAnVbrMvIRZQoCUYvodt3nJWrifd2n1PHZQMHSZay5.:18905:0:99999:7::: #$6 indicates that the encryption algorithm is sha512 [root@rocky8 ~]# echo `date +%s` 1633436307 [root@rocky8 ~]# echo `date +%s`/18584|bc 87894 [root@rocky8 ~]# passwd raymond Changing password for user raymond. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. [root@rocky8 ~]# passwd raymond <<EOF > 123456 > 123456 > EOF Changing password for user raymond. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. #You can change the password with multiline redirection [root@rocky8 ~]# echo 123456 | passwd --stdin raymond Changing password for user raymond. passwd: all authentication tokens updated successfully. #passwd --stdin raymond non interactive password modification. This method is only available for centos. ubuntu cannot use this method [root@rocky8 ~]# echo 123456 | passwd --stdin neteagle &> /dev/null raymond@ubuntu1804:~$ sudo -i [sudo] password for raymond: root@ubuntu1804:~# echo -e '123456\n123456' |passwd raymond Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully root@ubuntu1804:~# echo -e '123456\n123456' |passwd raymond &> /dev/null root@ubuntu1804:~# exit logout #ubuntu uses this method to change passwords non interactively [root@rocky8 ~]# whatis shadow shadow (3) - encrypted password file routines shadow (5) - shadowed password file [root@rocky8 ~]# man 5 shadow
Example: generate random password
[root@rocky8 ~]# tr -dc '[:alnum:]' < /dev/urandom | head -c 12 4XQZg4DXlKxQ[root@rocky8 ~]# openssl rand -base64 9 rL/ARTdsvLDX
Reference link: generate random password https://suijimimashengcheng.51240.com/
2.4 group file format
Group name: the group name
Group password: it is usually unnecessary to set. The password is recorded in / etc/gshadow
GID: is the ID of the group
List of users with current group as additional group (comma separator)
2.5 gshdow file format
Group name: the name of the group
Group password:
Group administrator list: list of group administrators, changing group passwords and members
List of users with current group as additional group: multiple users are separated by commas
example:
[root@rocky8 ~]# ll /etc/group /etc/gshadow -rw-r--r-- 1 root root 524 Oct 5 20:09 /etc/group ---------- 1 root root 414 Oct 5 20:09 /etc/gshadow [root@rocky8 ~]# cat /etc/group root:x:0: bin:x:1: daemon:x:2: sys:x:3: adm:x:4: tty:x:5: disk:x:6: lp:x:7: mem:x:8: kmem:x:9: wheel:x:10: cdrom:x:11: mail:x:12:postfix man:x:15: dialout:x:18: floppy:x:19: games:x:20: tape:x:33: video:x:39: ftp:x:50: lock:x:54: audio:x:63: users:x:100: nobody:x:65534: dbus:x:81: utmp:x:22: utempter:x:35: input:x:999: kvm:x:36: render:x:998: systemd-journal:x:190: systemd-coredump:x:997: systemd-resolve:x:193: tss:x:59: polkitd:x:996: ssh_keys:x:995: sssd:x:994: sshd:x:74: postdrop:x:90: postfix:x:89: raymond:x:1000:
3. User and group management commands
User management commands
- useradd
- usermod
- userdel
Group account maintenance command
- groupadd
- groupmod
- groupdel
example:
[root@rocky8 ~]# ll `which adduser` lrwxrwxrwx. 1 root root 7 May 19 11:02 /usr/sbin/adduser -> useradd
3.1 user creation
The useradd command creates a new Linux user
Format:
useradd [options] LOGIN
Common options:
-u UID -o coordination-u Option, do not check UID Uniqueness of -g GID Indicates the basic group to which the user belongs. It can be a group name or a group name GID -c "COMMENT" User's comment information -d HOME_DIR To the specified path(non-existent)Home directory -s SHELL Indicates the user's default shell Program, available list in/etc/shells In the file -G GROUP1[,GROUP2,...] Indicates an additional group for the user, which must exist in advance -N Do not create a private group as the master group, use users Group as master group -r Create system user CentOS 6 before: ID<500,CentOS 7 in the future: ID<1000 -m Create home directory for system users -M Do not create home directory for non system users
example:
useradd -r -u 48 -g apache -s /sbin/nologin -d /var/www -c "Apache" apache
example:
root@ubuntu1804:~# ll /bin/false -rwxr-xr-x 1 root root 30904 Jan 18 2018 /bin/false* [root@rocky8 ~]# useradd boss [root@rocky8 ~]# grep "boss" /etc/passwd boss:x:1001:1001::/home/boss:/bin/bash #User created [root@rocky8 ~]# grep "boss" /etc/shadow boss:!!:18905:0:99999:7::: #!! Indicates that the password is not set and the login is not run [root@rocky8 ~]# usermod -s /sbin/nologin boss #usermod -s sets the user shell type [root@rocky8 ~]# grep "boss" /etc/passwd boss:x:1001:1001::/home/boss:/sbin/nologin #The shell type has been modified here [root@rocky8 ~]# userdel boss #delete user [root@rocky8 ~]# grep "boss" /etc/passwd #User deleted [root@rocky8 ~]# ls /home boss raymond ##The home directory is still there [root@rocky8 ~]# ls /var/spool/mail/ boss raymond #The mailbox is also there [root@rocky8 ~]# useradd boss2 [root@rocky8 ~]# userdel -r boss2 #userdel -r delete user, delete home directory and mailbox [root@rocky8 ~]# ls /home boss raymond [root@rocky8 ~]# ls /var/spool/mail/ boss raymond [root@rocky8 ~]# groupadd g1 [root@rocky8 ~]# grep "g1" /etc/group g1:x:1001: [root@rocky8 ~]# useradd -G g1 boss3 #useradd -G set additional group [root@rocky8 ~]# id boss3 uid=1001(boss3) gid=1002(boss3) groups=1002(boss3),1001(g1) [root@rocky8 ~]# usermod -aG g1 raymond #usermod -aG append additional group [root@rocky8 ~]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond),1001(g1) [root@rocky8 ~]# usermod -G "" raymond ##Delete additional group [root@rocky8 ~]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond) [root@rocky8 ~]# groupdel g1 [root@rocky8 ~]# groupdel raymond groupdel: cannot remove the primary group of user 'raymond' #To delete a group, no one in this group can take this group as the primary group [root@rocky8 ~]# su - raymond [root@rocky8 ~]# userdel raymond userdel: user raymond is currently used by process 14264 #This user cannot be deleted [root@rocky8 ~]# ps aux |grep raymond root 14263 0.0 0.8 336996 6776 pts/1 S 20:43 0:00 su - raymond raymond 14264 0.0 0.4 233912 3848 pts/1 S+ 20:43 0:00 -bash root 14295 0.0 0.1 221928 1148 pts/0 R+ 20:44 0:00 grep --color=auto raymond #Because the user is logging in, the logged in user cannot be deleted
The default setting of the useradd command is defined by / etc/default/useradd
[root@rocky8 ~]# cat /etc/default/useradd # useradd defaults file GROUP=100 HOME=/home INACTIVE=-1 EXPIRE= SHELL=/bin/bash SKEL=/etc/skel CREATE_MAIL_SPOOL=yes #Controls the behavior of users created by default
New user related files
- /etc/default/useradd
- /etc/skel/*
- /etc/login.defs
example:
[root@rocky8 ~]# ls -a /etc/skel/ . .. .bash_logout .bash_profile .bashrc #New user's template folder [root@rocky8 ~]# useradd -N boss4 [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users) #Instead of creating the default primary group, use - N to make it a group with gid of 100, users [root@rocky8 ~]# cat /etc/login.defs # # Please note that the parameters in this configuration file control the # behavior of the tools from the shadow-utils component. None of these # tools uses the PAM mechanism, and the utilities that use PAM (such as the # passwd command) should therefore be configured elsewhere. Refer to # /etc/pam.d/system-auth for more information. # # *REQUIRED* # Directory where mailboxes reside, _or_ name of file, relative to the # home directory. If you _do_ define both, MAIL_DIR takes precedence. # QMAIL_DIR is for Qmail # #QMAIL_DIR Maildir MAIL_DIR /var/spool/mail #MAIL_FILE .mail # Default initial "umask" value used by login(1) on non-PAM enabled systems. # Default "umask" value for pam_umask(8) on PAM enabled systems. # UMASK is also used by useradd(8) and newusers(8) to set the mode for new # home directories if HOME_MODE is not set. # 022 is the default value, but 027, or even 077, could be considered # for increased privacy. There is no One True Answer here: each sysadmin # must make up their mind. UMASK 022 # HOME_MODE is used by useradd(8) and newusers(8) to set the mode for new # home directories. # If HOME_MODE is not set, the value of UMASK is used to create the mode. HOME_MODE 0700 # Password aging controls: # # PASS_MAX_DAYS Maximum number of days a password may be used. # PASS_MIN_DAYS Minimum number of days allowed between password changes. # PASS_MIN_LEN Minimum acceptable password length. # PASS_WARN_AGE Number of days warning given before a password expires. # PASS_MAX_DAYS 99999 PASS_MIN_DAYS 0 PASS_MIN_LEN 5 PASS_WARN_AGE 7 # # Min/max values for automatic uid selection in useradd # UID_MIN 1000 UID_MAX 60000 # System accounts SYS_UID_MIN 201 SYS_UID_MAX 999 # # Min/max values for automatic gid selection in groupadd # GID_MIN 1000 GID_MAX 60000 # System accounts SYS_GID_MIN 201 SYS_GID_MAX 999 # # If defined, this command is run when removing a user. # It should remove any at/cron/print jobs etc. owned by # the user to be removed (passed as the first argument). # #USERDEL_CMD /usr/sbin/userdel_local # # If useradd should create home directories for users by default # On RH systems, we do. This option is overridden with the -m flag on # useradd command line. # CREATE_HOME yes # This enables userdel to remove user groups if no members exist. # USERGROUPS_ENAB yes # Use SHA512 to encrypt password. ENCRYPT_METHOD SHA512
Batch modify user password
echo username:passwd | chpasswd
3.2 user attribute modification
The usermod command can modify user properties
Format:
usermod [OPTION] login
Common options:
-u UID: new UID -g GID: New master group -G GROUP1[,GROUP2,...[,GROUPN]]]: For a new additional group, the original additional group will be overwritten; if the original group is retained, it will be used at the same time-a option -s SHELL: New default SHELL -c 'COMMENT': New comment information -d HOME: A new home directory is not created automatically; to create a new home directory and move the original home data, use-m option -l login_name: New name -L: lock Designated user,stay/etc/shadow Addition of password bar ! -U: unlock Designated user,take /etc/shadow Password bar ! Take it off -e YYYY-MM-DD: Indicates the expiration date of the user account -f INACTIVE: Set an inactive period, i.e. a grace period
3.3 delete user
userdel to delete a Linux user
Format:
userdel [OPTION]... Login
Common options:
-f, --force force -r, --remove Delete user home directory and mailbox
3.4 view user related ID information
The id command can view the user's UID, GID and other information
id [OPTION]... [USER]
Common options:
-u: display UID -g: display GID -G: Displays the name of the group to which the user belongs ID -n: Display name, to be matched ugG use
3.5 switching users or executing commands as other users
su: that is, switch user. The command can switch the user identity and execute the command as the specified user
Format:
su [options...] [-] [user [args...]]
Common options:
-l --login su -l UserName amount to su - UserName -c, --command <command> pass a single command to the shell with -c
How to switch users:
- su UserName: non login switching, that is, the configuration file of the target user will not be read, and the current working directory will not be changed, that is, the switching is not complete
- su - UserName: login switching, which reads the configuration file of the target user and switches to its own home directory, that is, complete switching
Note: no password is required for root su to other users; A password is required for non root users to switch
Note: after su switches a new user, use exit to return to the old user instead of Su to switch to the old user. Otherwise, many bash sub processes will be generated and the environment may be chaotic.
Execute the command as a different identity:
su [-] UserName -c 'COMMAND'
example:
[root@rocky8 ~]# pwd /root [root@rocky8 ~]# echo $PATH /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin [root@rocky8 ~]# su raymond [raymond@rocky8 root]$ echo $PATH /home/raymond/.local/bin:/home/raymond/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin [raymond@rocky8 root]$ id uid=1000(raymond) gid=1000(raymond) groups=1000(raymond) [raymond@rocky8 root]$ whoami raymond [raymond@rocky8 root]$ who am i root pts/0 2021-10-05 16:55 (172.31.0.1) [raymond@rocky8 root]$ ls ls: cannot open directory '.': Permission denied [raymond@rocky8 root]$ su boss4 Password: #Ordinary users need to enter a password to switch to other users, and root users do not need a password to switch to other users su: Authentication failure [raymond@rocky8 root]$ exit exit [root@rocky8 ~]# echo 123456 |passwd --stdin boss4 Changing password for user boss4. passwd: all authentication tokens updated successfully. [root@rocky8 ~]# su raymond [raymond@rocky8 root]$ su boss4 Password: [boss4@rocky8 root]$ echo $PATH /home/boss4/.local/bin:/home/boss4/bin:/home/raymond/.local/bin:/home/raymond/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/root/bin [boss4@rocky8 root]$ exit exit [raymond@rocky8 root]$ exit exit [root@rocky8 ~]# su - raymond Last login: Tue Oct 5 20:54:36 CST 2021 on pts/0 [raymond@rocky8 ~]$ pwd /home/raymond [raymond@rocky8 ~]$ echo $PATH /home/raymond/.local/bin:/home/raymond/bin:/usr/local/bin:/usr/bin:/usr/local/sbin:/usr/sbin [raymond@rocky8 ~]$ whoami raymond [raymond@rocky8 ~]$ who am i root pts/0 2021-10-05 16:55 (172.31.0.1) [raymond@rocky8 ~]$ su root -c "cat /etc/shadow" #-c execute the command under another identity Password: root:$6$U/LuWNVHLX6clXpP$BxhDbz7cPwm7gEkDmpwihdC/FpCPkeJ6iiM/Dvp96b.d0O0pN6oawZFpIE62JT3KNwz68sy2Lgjhhj7GYsFtG1::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18898:::::: systemd-coredump:!!:18898:::::: systemd-resolve:!!:18898:::::: tss:!!:18898:::::: polkitd:!!:18898:::::: sssd:!!:18898:::::: sshd:!!:18898:::::: postfix:!!:18900:::::: raymond:$6$3Xnp/ePoeBr9LGsS$t5.nRfAlu48h5jUT8K3HVyx5EPInGdvZ.0HWBclN2NUo1LoJ/aM5o9ZlGrZ2GRurj6R4wKxgzWqjslVTlTW31.:18905:0:99999:7::: boss3:!!:18905:0:99999:7::: boss4:$6$RSftvDLVPblj5qnr$hKUfGm3fVVwC1pyRK5KwwdiAFMBJequr0.aLjnkvNYsFsIZuUdUDb3Hs.AYmOvDfBEFKTOP0kGQkGO3RJo/QZ.:18905:0:99999:7::: [raymond@rocky8 ~]$ exit logout
example:
[root@centos8 ~]#getent passwd mage mage:x:1001:1001::/home/mage:/bin/bash [root@centos8 ~]#usermod -s /bin/false mage [root@centos8 ~]#getent passwd mage mage:x:1001:1001::/home/mage:/bin/false [root@centos8 ~]#su - mage Last login: Fri Mar 27 09:18:57 CST 2020 on pts/0 [root@centos8 ~]#whomai -bash: whomai: command not found [root@centos8 ~]#whoami root
example:
[root@rocky8 ~]# su -s /sbin/nologin raymond This account is currently not available. [root@rocky8 ~]# whoami root [root@rocky8 ~]# su -s /bin/false raymond [root@rocky8 ~]# whoami root
example:
[root@rocky8 ~]# su - raymond Last login: Tue Oct 5 20:59:43 CST 2021 on pts/0 [raymond@rocky8 ~]$ su - root -c "getent shadow" Password: root:$6$U/LuWNVHLX6clXpP$BxhDbz7cPwm7gEkDmpwihdC/FpCPkeJ6iiM/Dvp96b.d0O0pN6oawZFpIE62JT3KNwz68sy2Lgjhhj7GYsFtG1::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18898:::::: systemd-coredump:!!:18898:::::: systemd-resolve:!!:18898:::::: tss:!!:18898:::::: polkitd:!!:18898:::::: sssd:!!:18898:::::: sshd:!!:18898:::::: postfix:!!:18900:::::: raymond:$6$3Xnp/ePoeBr9LGsS$t5.nRfAlu48h5jUT8K3HVyx5EPInGdvZ.0HWBclN2NUo1LoJ/aM5o9ZlGrZ2GRurj6R4wKxgzWqjslVTlTW31.:18905:0:99999:7::: boss3:!!:18905:0:99999:7::: boss4:$6$RSftvDLVPblj5qnr$hKUfGm3fVVwC1pyRK5KwwdiAFMBJequr0.aLjnkvNYsFsIZuUdUDb3Hs.AYmOvDfBEFKTOP0kGQkGO3RJo/QZ.:18905:0:99999:7::: [raymond@rocky8 ~]$ exit logout
example:
[root@rocky8 ~]# su - raymond -c 'touch raymond.txt' [root@rocky8 ~]# ll ~raymond total 0 -rw-rw-r-- 1 raymond raymond 0 Oct 5 21:01 raymond.txt
example:
[root@rocky8 ~]# su -s /bin/bash bin bash-4.4$ whoami bin bash-4.4$ exit exit [root@rocky8 ~]# getent passwd tss tss:x:59:59:Account used for TPM access:/dev/null:/sbin/nologin [root@rocky8 ~]# su - -s /bin/bash tss su: warning: cannot change directory to /dev/null: Not a directory -bash: /dev/null/.bash_profile: Not a directory [tss@rocky8 root]$ pwd /root [tss@rocky8 root]$ whoami tss [tss@rocky8 root]$ exit logout -bash: /dev/null/.bash_logout: Not a directory
3.6 setting password
passwd can change the user password
Format:
passwd [OPTIONS] UserName
Common options:
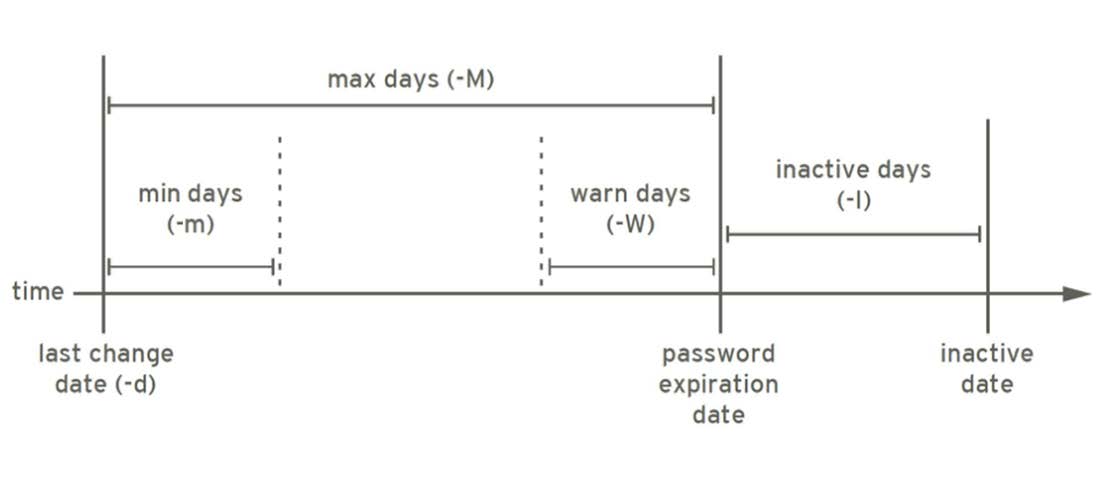
-d: Delete specified user password -l: Lock the specified user -u: Unlock specified user -e: Force the user to change the password at the next login -f: Force operation -n mindays: Specify minimum service life -x maxdays: Maximum service life -w warndays: How many days in advance -i inactivedays: Inactive period --stdin: Receive user password from standard input,Ubuntu No such option
Example: non interactive user password modification
#This method is more general and applicable to various Linux versions, such as ubuntu and centos [root@rocky8 ~]# echo -e '123456\n123456' | passwd raymond Changing password for user raymond. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. #Linux version for red hat series [root@rocky8 ~]# echo '123456' | passwd --stdin raymond Changing password for user raymond. passwd: all authentication tokens updated successfully.
Example: set the password that the user must change next time
[root@rocky8 ~]# useradd tom [root@rocky8 ~]# echo 123456 | passwd --stdin tom Changing password for user tom. passwd: all authentication tokens updated successfully. [root@rocky8 ~]# getent shadow tom tom:$6$T1oH2FdR91eSb8F1$ibihs464PYrNxbfwDZ19cGfHMQM6l6Eql9kJGLFBehmq3Wk0sBThxVT.smSyXxqlLX4GaEx0VRokE6WJRZFwi0:18905:0:99999:7::: [root@rocky8 ~]# passwd -e tom Expiring password for user tom. passwd: Success [root@rocky8 ~]# getent shadow tom tom:$6$T1oH2FdR91eSb8F1$ibihs464PYrNxbfwDZ19cGfHMQM6l6Eql9kJGLFBehmq3Wk0sBThxVT.smSyXxqlLX4GaEx0VRokE6WJRZFwi0:0:0:99999:7::: [root@rocky8 ~]# su - raymond Last login: Tue Oct 5 21:01:13 CST 2021 on pts/0 [raymond@rocky8 ~]$ su - tom Password: You are required to change your password immediately (administrator enforced) Current password: New password: Retype new password: Last failed login: Tue Oct 5 21:13:02 CST 2021 on pts/0 There were 2 failed login attempts since the last successful login. [tom@rocky8 ~]$ exit logout [raymond@rocky8 ~]$ exit logout [root@rocky8 ~]# getent shadow tom tom:$6$RL3M.RG6.yoL7a3/$0x7mVapHsu7P3bFEh4uT1gNm01vRfmpM7Qk7TpG1PIILp463u1GoMF2S.sX1WajK0Z0AywUFLR/2qC9Ve7tnz/:18905:0:99999:7:::
3.7 modify user password policy
chage can modify the user password policy
Format:
chage [OPTION]... LOGIN
Common options:
-d LAST_DAY #Time to change password -m --mindays MIN_DAYS -M --maxdays MAX_DAYS -W --warndays WARN_DAYS -I --inactive INACTIVE #Grace period after password expiration -E --expiredate EXPIRE_DATE #Validity period of the user -l #Show password policy
example:
[root@rocky8 ~]# getent shadow boss4 boss4:$6$RSftvDLVPblj5qnr$hKUfGm3fVVwC1pyRK5KwwdiAFMBJequr0.aLjnkvNYsFsIZuUdUDb3Hs.AYmOvDfBEFKTOP0kGQkGO3RJo/QZ.:18905:0:99999:7::: @rocky8 ~]# chage -d 0 boss4 #The user must change the password next time he logs in [root@rocky8 ~]# getent shadow boss4 boss4:$6$RSftvDLVPblj5qnr$hKUfGm3fVVwC1pyRK5KwwdiAFMBJequr0.aLjnkvNYsFsIZuUdUDb3Hs.AYmOvDfBEFKTOP0kGQkGO3RJo/QZ.:0:0:99999:7:::
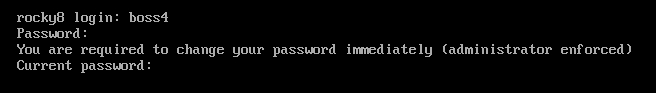
When logging in, you will be prompted that the password has expired and you will be prompted to change the password
[root@rocky8 ~]# useradd boss5 ;echo 123456 |passwd --stdin boss5;chage -d 0 boss5 Changing password for user boss5. passwd: all authentication tokens updated successfully. [root@rocky8 ~]# getent shadow boss4 boss4:$6$RSftvDLVPblj5qnr$hKUfGm3fVVwC1pyRK5KwwdiAFMBJequr0.aLjnkvNYsFsIZuUdUDb3Hs.AYmOvDfBEFKTOP0kGQkGO3RJo/QZ.:0:0:99999:7::: [root@rocky8 ~]# passwd boss4 Changing password for user boss4. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. [root@rocky8 ~]# getent shadow boss4 boss4:$6$XBIumyDG.k/SUIfc$5CUSqPI2j6OHZM0.k8Ip2NKxP4eWRxh4/d1vbkYnDRbas4Bdlni.tZh7jN0LOF0FuwYZvlvfkOk5ArdeP1bke0:18905:0:99999:7::: [root@rocky8 ~]# passwd -e boss4 #The passwd -e key will expire immediately. Change the password next time you log in Expiring password for user boss4. passwd: Success [root@rocky8 ~]# getent shadow boss4 boss4:$6$XBIumyDG.k/SUIfc$5CUSqPI2j6OHZM0.k8Ip2NKxP4eWRxh4/d1vbkYnDRbas4Bdlni.tZh7jN0LOF0FuwYZvlvfkOk5ArdeP1bke0:0:0:99999:7:::
example:
[root@rocky8 ~]# chage -m 3 -M 42 -W 14 -I 7 -E 2022-10-10 boss4 [root@rocky8 ~]# chage -l boss4 Last password change : password must be changed Password expires : password must be changed Password inactive : password must be changed Account expires : Oct 10, 2022 Minimum number of days between password change : 3 Maximum number of days between password change : 42 Number of days of warning before password expires : 14 [root@rocky8 ~]# getent shadow boss4 boss4:$6$XBIumyDG.k/SUIfc$5CUSqPI2j6OHZM0.k8Ip2NKxP4eWRxh4/d1vbkYnDRbas4Bdlni.tZh7jN0LOF0FuwYZvlvfkOk5ArdeP1bke0:0:3:42:14:7:19275: #Force password reset for next login [root@rocky8 ~]# chage -d 0 boss4 [root@rocky8 ~]# getent shadow boss4 boss4:$6$XBIumyDG.k/SUIfc$5CUSqPI2j6OHZM0.k8Ip2NKxP4eWRxh4/d1vbkYnDRbas4Bdlni.tZh7jN0LOF0FuwYZvlvfkOk5ArdeP1bke0:0:3:42:14:7:19275: [root@rocky8 ~]# chage -l boss4 Last password change : password must be changed Password expires : password must be changed Password inactive : password must be changed Account expires : Oct 10, 2022 Minimum number of days between password change : 3 Maximum number of days between password change : 42 Number of days of warning before password expires : 14
3.9 creating groups
groupadd implements group creation
format
groupadd [OPTION]... group_name
Common options:
-g GID to specify GID number;[GID_MIN, GID_MAX] -r Create system groups, CentOS 6 before: ID<500,CentOS 7 in the future: ID<1000
example:
groupadd -g 48 -r apache
3.10 modification group
groupmod group attribute modification
Format:
groupmod [OPTION]... group
Common options:
-n group_name: New name -g GID: new GID
3.11 group deletion
groupdel can delete groups
format
groupdel [options] GROUP
Common options:
-f, --force Force deletion, even if it is the user's primary group
3.12 changing and viewing group members
Group MEMS can manage the membership of additional groups
format
groupmems [options] [action]
Common options:
-g, --group groupname #Change to the specified group (root only) -a, --add username #Specify the user to join the group -d, --delete username #Remove user from group -p, --purge #Clear all members from group -l, --list #Displays a list of group members
groups to view user group relationships
format
#View the list of groups to which the user belongs groups [OPTION].[USERNAME]...
example:
[root@rocky8 ~]# groupmems -l -g raymond #See which users are in the group [root@rocky8 ~]# groupmems -a boss4 -g raymond #Add additional group [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users),1000(raymond) [root@rocky8 ~]# groupmems -d boss4 -g raymond #Delete additional group [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users) [root@rocky8 ~]# usermod -aG bin boss4 #-a add group [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users),1(bin) [root@rocky8 ~]# usermod -G boss5 boss4 #No - a coverage group [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users),1004(boss5) [root@rocky8 ~]# usermod -aG root boss4 #To keep the original group plus - a [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users),1004(boss5),0(root) [root@rocky8 ~]# usermod -G "" boss4 #Delete additional group [root@rocky8 ~]# id boss4 uid=1002(boss4) gid=100(users) groups=100(users)
example:
[root@rocky8 ~]# useradd admins [root@rocky8 ~]# groupmems -l -g admins [root@rocky8 ~]# groupmems -a raymond -g admins [root@rocky8 ~]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond),1005(admins) [root@rocky8 ~]# groupmems -l -g admins raymond [root@rocky8 ~]# groupmems -a tom -g admins [root@rocky8 ~]# groupmems -l -g admins raymond tom [root@rocky8 ~]# groupmems -d tom -g admins [root@rocky8 ~]# groups tom tom : tom [root@rocky8 ~]# groupmems -l -g admins raymond [root@rocky8 ~]# groupmems -p -g admins [root@rocky8 ~]# groupmems -l -g admins
3.13 practice
- Create the user gentoo, the additional groups are bin and root, the default shell is / bin/csh, and the comment information is "Gentoo Distribution"
- Create the following users, groups, and group memberships
Group named Web
User nginx, using web as an additional group
User varnish, using web as an additional group
The user mysql cannot log in to the system interactively, and is not a member of web. The passwords of nginx, varnish and mysql are raymond