4. Document authority management
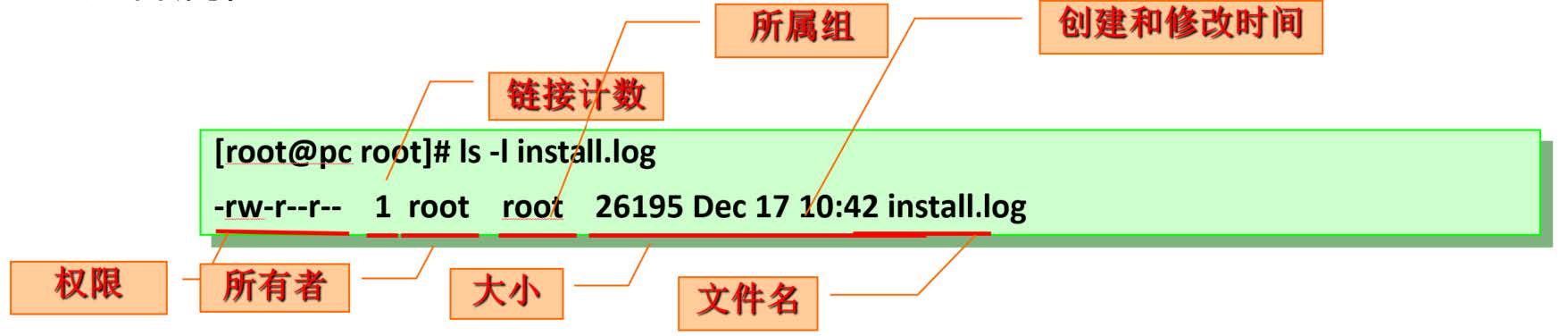
4.1 file owner and group attribute operation
4.1.1 owner of setting file chown
The chown command can modify the owner or group of a file
format
chown [OPTION]... [OWNER][:[GROUP]] FILE... chown [OPTION]... --reference=RFILE FILE...
Instructions:
OWNER #Modify owner only OWNER:GROUP #Modify both owner and group :GROUP #Only the group can be modified, and the colon can also be replaced --reference=RFILE #Refer to the specified properties to modify -R #Recursion, use this option with caution, very dangerous!
example:
[root@rocky8 ~]# ll /etc/passwd -rw-r--r-- 1 root root 1091 Oct 6 17:18 /etc/passwd [root@rocky8 ~]# su - raymond [raymond@rocky8 ~]$ cat /etc/passwd root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin systemd-coredump:x:999:997:systemd Core Dumper:/:/sbin/nologin systemd-resolve:x:193:193:systemd Resolver:/:/sbin/nologin tss:x:59:59:Account used for TPM access:/dev/null:/sbin/nologin polkitd:x:998:996:User for polkitd:/:/sbin/nologin unbound:x:997:994:Unbound DNS resolver:/etc/unbound:/sbin/nologin sssd:x:996:993:User for sssd:/:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin raymond:x:1000:1000::/home/raymond:/bin/bash [raymond@rocky8 ~]$ cat /etc/shadow cat: /etc/shadow: Permission denied [raymond@rocky8 ~]$ ll /etc/shadow ---------- 1 root root 791 Oct 6 17:18 /etc/shadow [raymond@rocky8 ~]$ exit logout [root@rocky8 ~]# ll /etc/shadow ---------- 1 root root 791 Oct 6 17:18 /etc/shadow [root@rocky8 ~]# cat /etc/shadow root:$6$as0jTt3r/Z5Ilkm4$wgwx4FOC16qQq0v4O.Uq9B6LE/JaL/GpO19NbwYNTk0xDd.tXn06HCAfU4qHXRn1R4A/iVjPlXgs1Lxx74f000::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18906:::::: systemd-coredump:!!:18906:::::: systemd-resolve:!!:18906:::::: tss:!!:18906:::::: polkitd:!!:18906:::::: unbound:!!:18906:::::: sssd:!!:18906:::::: sshd:!!:18906:::::: postfix:!!:18906:::::: raymond:$6$2HjxBEEo.SCJS8JE$HHXAOspKQ4/3lUUh5FCkSACYhv70uhgI90QfKduqXD0ZC2/cLenJJq8eXHa21h68itQEQVuljiXtV4q8dy/aO1:18906:0:99999:7::: [root@rocky8 ~]# ll /etc/shadow ---------- 1 root root 791 Oct 6 17:18 /etc/shadow [root@rocky8 ~]# echo xx >> /etc/shadow [root@rocky8 ~]# cat /etc/shadow root:$6$as0jTt3r/Z5Ilkm4$wgwx4FOC16qQq0v4O.Uq9B6LE/JaL/GpO19NbwYNTk0xDd.tXn06HCAfU4qHXRn1R4A/iVjPlXgs1Lxx74f000::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18906:::::: systemd-coredump:!!:18906:::::: systemd-resolve:!!:18906:::::: tss:!!:18906:::::: polkitd:!!:18906:::::: unbound:!!:18906:::::: sssd:!!:18906:::::: sshd:!!:18906:::::: postfix:!!:18906:::::: raymond:$6$2HjxBEEo.SCJS8JE$HHXAOspKQ4/3lUUh5FCkSACYhv70uhgI90QfKduqXD0ZC2/cLenJJq8eXHa21h68itQEQVuljiXtV4q8dy/aO1:18906:0:99999:7::: xx #Can append [root@rocky8 ~]# ll /etc/shadow ---------- 1 root root 794 Oct 6 19:06 /etc/shadow #Can read, can write, no execution permission [root@rocky8 ~]# /etc/shadow -bash: /etc/shadow: Permission denied #No one has execution permission, including root [root@rocky8 ~]# cd /data [root@rocky8 data]# cp /etc/fstab a.txt [root@rocky8 data]# ll a.txt -rw-r--r-- 1 root root 709 Oct 6 19:28 a.txt [root@rocky8 data]# chown raymond a.txt #chown change owner [root@rocky8 data]# ll a.txt -rw-r--r-- 1 raymond root 709 Oct 6 19:28 a.txt [root@rocky8 data]# chgrp bin a.txt #chgrp change group [root@rocky8 data]# ll a.txt -rw-r--r-- 1 raymond bin 709 Oct 6 19:28 a.txt [root@rocky8 data]# useradd boss [root@rocky8 data]# chown boss.nobody a.txt #chown owner. Or: Group modify owner and group [root@rocky8 data]# ll a.txt -rw-r--r-- 1 boss nobody 709 Oct 6 19:28 a.txt [root@rocky8 data]# chown boss:raymond a.txt [root@rocky8 data]# ll a.txt -rw-r--r-- 1 boss raymond 709 Oct 6 19:28 a.txt [root@rocky8 data]# ll -d /data/ drwxr-xr-x. 2 root root 19 Oct 6 19:28 /data/ [root@rocky8 data]# chown -R raymond.raymond /data #chown -R modifies the folder owner and group, including the files and subdirectories under the folder. Without - R, only the folder itself is modified, and the files and subdirectories under the folder are not affected [root@rocky8 data]# ll -d /data/ drwxr-xr-x. 2 raymond raymond 19 Oct 6 19:28 /data/ [root@rocky8 data]# ll total 4 -rw-r--r-- 1 raymond raymond 709 Oct 6 19:28 a.txt [root@rocky8 data]# chown -R raymond.raymond / data #This command is extremely dangerous. If there is an extra space in front of data, the permissions of all files under the root will be changed. Use it carefully. Its function is equivalent to deleting the root rm -rf/* [root@rocky8 data]# chown -R root.root /data [root@rocky8 data]# ll total 4 -rw-r--r-- 1 root root 709 Oct 6 19:28 a.txt [root@rocky8 data]# su raymond [raymond@rocky8 data]$ id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond) [raymond@rocky8 data]$ cat a.txt # # /etc/fstab # Created by anaconda on Wed Oct 6 11:16:34 2021 # # Accessible filesystems, by reference, are maintained under '/dev/disk/'. # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info. # # After editing this file, run 'systemctl daemon-reload' to update systemd # units generated from this file. # UUID=57f3a077-bb67-42c3-9e6c-bc8a0fed3776 / xfs defaults 0 0 UUID=c72110fc-5dae-470c-9940-97ba978c7dc7 /boot xfs defaults 0 0 UUID=02ae6744-8c28-4c86-b85b-e113c06a834f /data xfs defaults 0 0 UUID=4f387202-0a81-4202-9e12-90d04af4d308 none swap defaults 0 0 [raymond@rocky8 data]$ echo raymond data >> a.txt bash: a.txt: Permission denied [raymond@rocky8 data]$ exit exit #You can only read, not write [root@rocky8 data]# chown raymond a.txt #Change the owner of a.txt file to raymond [root@rocky8 data]# ll total 4 -rw-r--r-- 1 raymond root 709 Oct 6 19:28 a.txt [root@rocky8 data]# su raymond [raymond@rocky8 data]$ cat a.txt # # /etc/fstab # Created by anaconda on Wed Oct 6 11:16:34 2021 # # Accessible filesystems, by reference, are maintained under '/dev/disk/'. # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info. # # After editing this file, run 'systemctl daemon-reload' to update systemd # units generated from this file. # UUID=57f3a077-bb67-42c3-9e6c-bc8a0fed3776 / xfs defaults 0 0 UUID=c72110fc-5dae-470c-9940-97ba978c7dc7 /boot xfs defaults 0 0 UUID=02ae6744-8c28-4c86-b85b-e113c06a834f /data xfs defaults 0 0 UUID=4f387202-0a81-4202-9e12-90d04af4d308 none swap defaults 0 0 [raymond@rocky8 data]$ echo raymond data >> a.txt [raymond@rocky8 data]$ cat a.txt # # /etc/fstab # Created by anaconda on Wed Oct 6 11:16:34 2021 # # Accessible filesystems, by reference, are maintained under '/dev/disk/'. # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info. # # After editing this file, run 'systemctl daemon-reload' to update systemd # units generated from this file. # UUID=57f3a077-bb67-42c3-9e6c-bc8a0fed3776 / xfs defaults 0 0 UUID=c72110fc-5dae-470c-9940-97ba978c7dc7 /boot xfs defaults 0 0 UUID=02ae6744-8c28-4c86-b85b-e113c06a834f /data xfs defaults 0 0 UUID=4f387202-0a81-4202-9e12-90d04af4d308 none swap defaults 0 0 raymond data [raymond@rocky8 data]$ exit exit #Now you can read or write [root@rocky8 data]# chown root a.txt [root@rocky8 data]# ll total 4 -rw-r--r-- 1 root root 722 Oct 6 19:38 a.txt [root@rocky8 data]# groupadd admins #Add admins group [root@rocky8 data]# groupmems -l -g admins #View group members [root@rocky8 data]# groupmems -a raymond -g admins #Add group members [root@rocky8 data]# groupmems -a boss -g admins [root@rocky8 data]# groupmems -l -g admins raymond boss #Now there are members in the admins group [root@rocky8 data]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond),1002(admins) [root@rocky8 data]# id boss uid=1001(boss) gid=1001(boss) groups=1001(boss),1002(admins) [root@rocky8 data]# chown :admins a.txt #Change the group to admins [root@rocky8 data]# ll total 4 -rw-r--r-- 1 root admins 722 Oct 6 19:38 a.txt chmod who opt per file who: u,g,o,a opt: +,-,= per: r,w,x [root@rocky8 data]# chmod g+w a.txt #Group grant write permission [root@rocky8 data]# ll total 4 -rw-rw-r-- 1 root admins 722 Oct 6 19:38 a.txt [root@rocky8 data]# su boss [boss@rocky8 data]$ echo boss data >> a.txt [boss@rocky8 data]$ cat a.txt # # /etc/fstab # Created by anaconda on Wed Oct 6 11:16:34 2021 # # Accessible filesystems, by reference, are maintained under '/dev/disk/'. # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info. # # After editing this file, run 'systemctl daemon-reload' to update systemd # units generated from this file. # UUID=57f3a077-bb67-42c3-9e6c-bc8a0fed3776 / xfs defaults 0 0 UUID=c72110fc-5dae-470c-9940-97ba978c7dc7 /boot xfs defaults 0 0 UUID=02ae6744-8c28-4c86-b85b-e113c06a834f /data xfs defaults 0 0 UUID=4f387202-0a81-4202-9e12-90d04af4d308 none swap defaults 0 0 raymond data boss data [boss@rocky8 data]$ exit exit #Now both users can write [root@rocky8 data]# chmod g=w a.txt #=Override permissions [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 732 Oct 6 19:45 a.txt [root@rocky8 data]# su boss [boss@rocky8 data]$ cat a.txt cat: a.txt: Permission denied [boss@rocky8 data]$ echo boss data >> a.txt [boss@rocky8 data]$ exit exit #Only write permission, can not see the file, can only write the file [root@rocky8 data]# ll /bin/ls -rwxr-xr-x. 1 root root 143408 Mar 15 2021 /bin/ls [root@rocky8 data]# ls a.txt [root@rocky8 data]# su raymond [raymond@rocky8 data]$ ls a.txt [raymond@rocky8 data]$ exit exit #It can now be executed [root@rocky8 data]# chmod o-x /bin/ls #other went to the x permission [root@rocky8 data]# ll /bin/ls -rwxr-xr--. 1 root root 143408 Mar 15 2021 /bin/ls [root@rocky8 data]# su raymond [raymond@rocky8 data]$ ls bash: /usr/bin/ls: Permission denied #ls cannot execute now [raymond@rocky8 data]$ exit exit [root@rocky8 data]# ll /bin/ls -rwxr-xr--. 1 root root 143408 Mar 15 2021 /bin/ls [root@rocky8 data]# chmod u-x /bin/ls #Remove the owner's x permissions [root@rocky8 data]# ls a.txt #ls can also execute [root@rocky8 data]# ll /bin/ls -rw-r-xr--. 1 root root 143408 Mar 15 2021 /bin/ls #Because the group has x permissions [root@rocky8 data]# chmod a-x /bin/ls #Remove all x permissions [root@rocky8 data]# ll /bin/ls -bash: /usr/bin/ls: Permission denied #Now root cannot execute [root@rocky8 data]# chmod o+x /bin/ls #Add x permission to other [root@rocky8 data]# ll /bin/ls -rw-r--r-x. 1 root root 143408 Mar 15 2021 /bin/ls [root@rocky8 data]# ls a.txt #Now root can execute [root@rocky8 data]# ll /bin/ls -rw-r--r-x. 1 root root 143408 Mar 15 2021 /bin/ls #As long as the owner, group, or other has an execution permission, root can execute [root@rocky8 data]# chmod +x /bin/ls #+x is the same as a+x [root@rocky8 data]# ll /bin/ls -rwxr-xr-x. 1 root root 143408 Mar 15 2021 /bin/ls
example:
[root@rocky8 data]# pwd /data [root@rocky8 data]# mkdir dir [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt drwxr-xr-x 2 root root 6 Oct 6 19:59 dir [root@rocky8 data]# su raymond [raymond@rocky8 data]$ cd dir [raymond@rocky8 dir]$ ls [raymond@rocky8 dir]$ touch raymond.txt touch: cannot touch 'raymond.txt': Permission denied #Cannot access [raymond@rocky8 dir]$ cd .. [raymond@rocky8 data]$ ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt drwxr-xr-x 2 root root 6 Oct 6 19:59 dir [raymond@rocky8 data]$ exit exit [root@rocky8 data]# touch dir/root.txt [root@rocky8 data]# su raymond [raymond@rocky8 data]$ ls dir root.txt [raymond@rocky8 data]$ ll dir total 0 -rw-r--r-- 1 root root 0 Oct 6 20:01 root.txt [raymond@rocky8 data]$ touch dir/raymond.txt touch: cannot touch 'dir/raymond.txt': Permission denied #Cannot access [raymond@rocky8 data]$ rm -f dir/root.txt rm: cannot remove 'dir/root.txt': Permission denied #Cannot delete [raymond@rocky8 data]$ exit exit [root@rocky8 data]# chmod a+w dir #Give all directories permission to execute [root@rocky8 data]# ll -d dir drwxrwxrwx 2 root root 22 Oct 6 20:01 dir [root@rocky8 data]# su raymond [raymond@rocky8 data]$ ls dir root.txt [raymond@rocky8 data]$ touch dir/raymond.txt #You can now create a new file [raymond@rocky8 data]$ ll dir/root.txt -rw-r--r-- 1 root root 0 Oct 6 20:01 dir/root.txt [raymond@rocky8 data]$ echo raymond data >> dir/root.txt bash: dir/root.txt: Permission denied #Can't write [raymond@rocky8 data]$ rm -f dir/root.txt #Can delete [raymond@rocky8 data]$ ll -d dir drwxrwxrwx 2 root root 25 Oct 6 20:06 dir #For the folder, it only stores the file directory. other has rwx permission. All raymond files in the folder can be deleted or read [raymond@rocky8 data]$ touch dir/raymond2.txt [raymond@rocky8 data]$ ll dir total 0 -rw-rw-r-- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt -rw-rw-r-- 1 raymond raymond 0 Oct 6 20:05 raymond.txt #Can create files #Whether a file can be deleted is related to the folder, not to the file [raymond@rocky8 data]$ chmod a= dir/raymond* [raymond@rocky8 data]$ ll dir total 0 ---------- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt ---------- 1 raymond raymond 0 Oct 6 20:05 raymond.txt [raymond@rocky8 data]$ ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt drwxrwxrwx 2 root root 45 Oct 6 20:07 dir [root@rocky8 data]# su boss [boss@rocky8 data]$ ll dir total 0 ---------- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt ---------- 1 raymond raymond 0 Oct 6 20:05 raymond.txt [boss@rocky8 data]$ rm dir/raymond.txt rm: remove write-protected regular empty file 'dir/raymond.txt'? y [boss@rocky8 data]$ ll dir total 0 ---------- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt [boss@rocky8 data]$ exit exit #The file does not have permission, but the file can be deleted. Whether the file can be deleted depends on whether the folder has write permission [root@rocky8 data]# chmod a-r dir [root@rocky8 data]# ll dir total 0 ---------- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 26 Oct 6 20:09 dir [root@rocky8 data]# su boss [boss@rocky8 data]$ ll dir ls: cannot open directory 'dir': Permission denied #If the folder does not have read permission, you will not see the file list [boss@rocky8 data]$ cd dir [boss@rocky8 dir]$ ls ls: cannot open directory '.': Permission denied #You can enter the folder, but you can't see what's inside [boss@rocky8 dir]$ ll raymond2.txt ---------- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt #If you know any documents, you can see them [boss@rocky8 dir]$ cp raymond2.txt ~/ cp: cannot open 'raymond2.txt' for reading: Permission denied #Cannot copy because the file does not have read permission [boss@rocky8 dir]$ exit exit [root@rocky8 data]# chmod a+r dir/raymond2.txt #Give file read permission [root@rocky8 data]# ll dir/raymond2.txt -r--r--r-- 1 raymond raymond 0 Oct 6 20:07 dir/raymond2.txt [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 26 Oct 6 20:09 dir [root@rocky8 data]# su boss [boss@rocky8 data]$ ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 26 Oct 6 20:09 dir [boss@rocky8 data]$ ll dir ls: cannot open directory 'dir': Permission denied #I can't read the file [boss@rocky8 data]$ cp dir/raymond2.txt ~ [boss@rocky8 data]$ ll ~ total 0 -r--r--r-- 1 boss boss 0 Oct 6 20:15 raymond2.txt #You can copy files [boss@rocky8 data]$ exit exit [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 26 Oct 6 20:09 dir [root@rocky8 data]# chmod o=rw dir [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wxrw- 2 root root 26 Oct 6 20:09 dir #The directory does not have execution permission now [root@rocky8 data]# su boss [boss@rocky8 data]$ ll dir ls: cannot access 'dir/raymond2.txt': Permission denied total 0 -????????? ? ? ? ? ? raymond2.txt #You can see the file name, but you cannot access the file [boss@rocky8 data]$ cd dir #Cannot enter directory bash: cd: dir: Permission denied [boss@rocky8 data]$ cat dir/raymond2.txt #Can't see the file cat: dir/raymond2.txt: Permission denied [boss@rocky8 data]$ cp dir/raymond2.txt ~/boss.txt cp: cannot stat 'dir/raymond2.txt': Permission denied #Nor can it be copied [boss@rocky8 data]$ exit exit [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wxrw- 2 root root 26 Oct 6 20:09 dir #For folders, rx permissions are basic [root@rocky8 data]# ll -d dir d-wx-wxrw- 2 root root 26 Oct 6 20:09 dir [root@rocky8 data]# su raymond [raymond@rocky8 data]$ touch dir/raymond2.txt touch: cannot touch 'dir/raymond2.txt': Permission denied #The folder has only rx permissions and cannot create new files [raymond@rocky8 data]$ ll dir ls: cannot access 'dir/raymond2.txt': Permission denied total 0 -????????? ? ? ? ? ? raymond2.txt #Without x permission, you can't enter or write. X permission belongs to the basic permission of the folder [raymond@rocky8 data]$ exit exit [root@rocky8 data]# ll dir total 0 -r--r--r-- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt [root@rocky8 data]# ll -d dir d-wx-wxrw- 2 root root 26 Oct 6 20:09 dir [root@rocky8 data]# su boss [boss@rocky8 data]$ rm dir/raymond2.txt rm: cannot remove 'dir/raymond2.txt': Permission denied #It can't be deleted #Deleting or creating a new directory does not have X permission. Without x permission, it is impossible to delete and create a new file [boss@rocky8 data]$ exit exit [root@rocky8 data]# chmod a=wx dir [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 26 Oct 6 20:09 dir [root@rocky8 data]# ll dir total 0 -r--r--r-- 1 raymond raymond 0 Oct 6 20:07 raymond2.txt [root@rocky8 data]# su boss [boss@rocky8 data]$ touch dir/boss.txt #Folders have w and x permissions and can create new files [boss@rocky8 data]$ rm -f dir/raymond2.txt #You can also delete files [boss@rocky8 data]$ ll dir ls: cannot open directory 'dir': Permission denied #But I don't have read permission and can't see the files inside [boss@rocky8 data]$ exit exit [root@rocky8 data]# ll dir total 0 -rw-rw-r-- 1 boss boss 0 Oct 6 20:23 boss.txt
example:
Digital method r 4 w 2 x 1 rwx rw- r-- 111 110 100 7 6 4 chmod 764 file #These are the most used rwx 7 rw- 6 r-x 5 r-- 4 --- 0 #These use less -wx 3 -w- 2 --x 1 [root@rocky8 data]# ll total 4 -rw--w-r-- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 22 Oct 6 20:23 dir [root@rocky8 data]# chmod 640 a.txt [root@rocky8 data]# ll total 4 -rw-r----- 1 root admins 742 Oct 6 19:47 a.txt d-wx-wx-wx 2 root root 22 Oct 6 20:23 dir [root@rocky8 data]# chmod 750 dir [root@rocky8 data]# ll total 4 -rw-r----- 1 root admins 742 Oct 6 19:47 a.txt drwxr-x--- 2 root root 22 Oct 6 20:23 dir
example:
[root@rocky8 data]# cp /etc/fstab f1.txt [root@rocky8 data]# pwd /data [root@rocky8 data]# ll total 4 -rw-r--r-- 1 root root 709 Oct 6 20:28 f1.txt [root@rocky8 data]# chown raymond f1.txt [root@rocky8 data]# ll total 4 -rw-r--r-- 1 raymond root 709 Oct 6 20:28 f1.txt [root@rocky8 data]# chown :admins f1.txt [root@rocky8 data]# ll total 4 -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt [root@rocky8 data]# chown root.bin f1.txt [root@rocky8 data]# ll total 4 -rw-r--r-- 1 root bin 709 Oct 6 20:28 f1.txt [root@rocky8 data]# chown raymond:admins f1.txt [root@rocky8 data]# ll total 4 -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt [root@rocky8 data]# cp /etc/issue f2.txt [root@rocky8 data]# ll total 8 -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt -rw-r--r-- 1 root root 23 Oct 6 20:30 f2.txt [root@rocky8 data]# chown --reference=f1.txt f2.txt [root@rocky8 data]# ll total 8 -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt -rw-r--r-- 1 raymond admins 23 Oct 6 20:30 f2.txt
example:
[root@rocky8 data]# chown -R raymond.admins /data/ [root@rocky8 data]# ll -d /data drwxr-xr-x. 2 raymond admins 34 Oct 6 20:30 /data
4.1.2 set the group information chgrp
The chgrp command can modify only the group to which the file belongs
format
chgrp [OPTION]... GROUP FILE... chgrp [OPTION]... --reference=RFILE FILE...
-R recursion
example:
[root@rocky8 data]# ll f1.txt -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt [root@rocky8 data]# chown raymond.root f1.txt [root@rocky8 data]# ll f1.txt -rw-r--r-- 1 raymond root 709 Oct 6 20:28 f1.txt [root@rocky8 data]# chgrp admins f1.txt [root@rocky8 data]# ll f1.txt -rw-r--r-- 1 raymond admins 709 Oct 6 20:28 f1.txt
4.2 file permissions
4.2.1 document authority description
File permissions are mainly defined for three types of objects
owner Owner, u group Genus group, g other other, o
Note: the final permission of the user is matched from left to right, that is, the owner, the group and others. Once the permission is matched, it will be immediately
Effective, no longer view its permissions to the right
Each file defines three common permissions for each type of visitor
Each file defines three permissions for each type of visitor
r Readable w Writable x eXcutable
Permissions on files:
r You can use file viewing tools, such as: cat,You can get its content w Its contents can be modified x You can request the kernel to start this file as a process, that is, you can execute (run) this file (the contents of this file must be executable)
Permissions on Directory:
r have access to ls View a list of files in this directory w You can create files in this directory or delete files in this directory, regardless of the permissions of the deleted files x sure cd Enter this directory to use ls -l View file metadata in this directory (must be matched) r Permission), which belongs to the minimum accessible permission of the directory X Directory only x Permission, do not give files without execution permission x jurisdiction
Interview question: what is the difference between the permissions of directories and files in Linux? (explain the difference between read, write and execute permissions respectively)
Authority of mathematical method
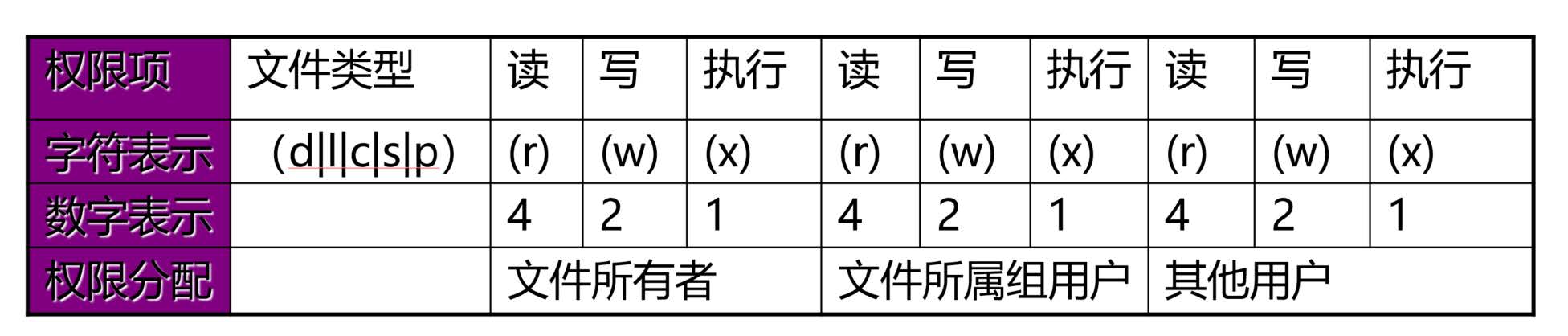
Octal digit
--- 000 0 --x 001 1 -w- 010 2 -wx 011 3 r-- 100 4 r-x 101 5 rw- 110 6 rwx 111 7
For example:
rw-r----- 640 rwxr-xr-x 755
4.2.2 modify file permissions chmod
format
chmod [OPTION]... MODE[,MODE]... FILE... chmod [OPTION]... OCTAL-MODE FILE... #Refer to the permission of RFILE FILE and modify the FILE to be the same as RFILE chmod [OPTION]... --reference=RFILE FILE...
explain:
MODE: who opt permission who:u,g,o,a opt:+,-,= permission:r,w,x Modify all permissions of a specified type of user u= g= o= ug= a= u=,g= Modify one or more permissions of a specified type of user u+ u- g+ g- o+ o- a+ a- + - -R: Recursively modify permissions
Example: setting X permissions
[root@rocky8 data]# chown -R root.root /data/
[root@rocky8 data]# touch dir/f{1..2}.txt
[root@rocky8 data]# ll dir
total 0
-rw-r--r-- 1 root root 0 Oct 6 20:36 f1.txt
-rw-r--r-- 1 root root 0 Oct 6 20:36 f2.txt
[root@rocky8 data]# ll -d dir
drwxr-xr-x 2 root root 34 Oct 6 20:36 dir
[root@rocky8 data]# chmod -R a+X dir
[root@rocky8 data]# ll -d dir
drwxr-xr-x 2 root root 34 Oct 6 20:36 dir
[root@rocky8 data]# ll dir
total 0
-rw-r--r-- 1 root root 0 Oct 6 20:36 f1.txt
-rw-r--r-- 1 root root 0 Oct 6 20:36 f2.txt
example:
chmod u+wx,g-r,o=rx file chmod -R g+rwX /testdir chmod 600 file
Example: interview questions
implement cp /etc/issue /data/dir/ Minimum permissions required? /bin/cp need x jurisdiction /etc/ need x jurisdiction /etc/issue need r jurisdiction /data need x jurisdiction /data/dir need w,x jurisdiction
4.3 default permissions for new files and directories
The value of umask can be used to retain permissions when creating files
Implementation method:
- The default permission for a new file is 666 umask. If a bit of the result has execution (odd) permission, its permission will be + 1, and the even number will not change
- Default permission for new directory: 777 umask
Unprivileged user umask is 002 by default
The umask of root is 022 by default
View umask
umask #Mode display umask –S #Output can be called umask –p
Modify umask
umask #
example:
umask 002 umask u=rw,g=r,o=
Persistent umask
- Global settings: / etc/bashrc
- User settings: ~ /. bashrc
example:
[root@rocky8 data]# type umask umask is a shell builtin [root@rocky8 data]# touch root.txt [root@rocky8 data]# ll root.txt -rw-r--r-- 1 root root 0 Oct 6 20:42 root.txt [root@rocky8 data]# mkdir dir2 [root@rocky8 data]# ll -d dir2 drwxr-xr-x 2 root root 6 Oct 6 20:42 dir2 [root@rocky8 data]# touch root2.txt [root@rocky8 data]# mkdir dir3 [root@rocky8 data]# ll total 0 drwxr-xr-x 2 root root 34 Oct 6 20:36 dir drwxr-xr-x 2 root root 6 Oct 6 20:42 dir2 drwxr-xr-x 2 root root 6 Oct 6 20:42 dir3 -rw-r--r-- 1 root root 0 Oct 6 20:42 root2.txt -rw-r--r-- 1 root root 0 Oct 6 20:42 root.txt #The default folder permissions are 755 and file permissions are 644 [root@rocky8 data]# touch pass.txt [root@rocky8 data]# ll pass.txt -rw-r--r-- 1 root root 0 Oct 6 20:43 pass.txt [root@rocky8 data]# chmod 0 pass.txt [root@rocky8 data]# ll pass.txt ---------- 1 root root 0 Oct 6 20:43 pass.txt [root@rocky8 data]# umask 0022 umask+default= Folder 777 file 666 777-022=755 666-022-644 file 666-111=555 ,If you add 1666 to the odd number [root@rocky8 data]# umask 111 [root@rocky8 data]# touch b.txt [root@rocky8 data]# ll b.txt -rw-rw-rw- 1 root root 0 Oct 6 20:45 b.txt [root@rocky8 data]# umask 123 [root@rocky8 data]# touch c.txt;mkdir dir4;ll c.txt -d dir4 -rw-r--r-- 1 root root 0 Oct 6 20:45 c.txt drw-r-xr-- 2 root root 6 Oct 6 20:45 dir4 [root@rocky8 data]# umask 0123 [root@rocky8 data]# exit logout [root@rocky8 ~]# umask 0022 #Log out and log in again, and the umask value is restored [root@rocky8 ~]# vim .bashrc #To take effect permanently, change this document
example:
[root@rocky8 ~]# umask 0022 [root@rocky8 ~]# umask -S u=rwx,g=rx,o=rx [root@rocky8 ~]# umask -p umask 0022
example:
[root@rocky8 ~]# cd /data [root@rocky8 data]# rm -f pass.txt [root@rocky8 data]# touch pass.txt [root@rocky8 data]# ll pass.txt -rw-r--r-- 1 root root 0 Oct 6 20:48 pass.txt [root@rocky8 data]# rm -f pass.txt [root@rocky8 data]# umask 777;touch pass.txt #It is generally used like this [root@rocky8 data]# ll pass.txt ---------- 1 root root 0 Oct 6 20:48 pass.txt [root@rocky8 data]# touch a.txt [root@rocky8 data]# ll a.txt ---------- 1 root root 0 Oct 6 20:49 a.txt #However, the subsequent files created in this way have this permission [root@rocky8 data]# rm -f *.txt [root@rocky8 data]# exit logout [root@rocky8 ~]# umask 0022 [root@rocky8 ~]# ( umask 777;touch pass.txt ) #Parentheses are added to make it temporarily effective without affecting the subsequent creation of files [root@rocky8 ~]# ll pass.txt ---------- 1 root root 0 Oct 6 20:50 pass.txt [root@rocky8 ~]# umask 0022
4.4 practice
- When the user docker does not have permission to execute the / testdir directory, what operations do you mean you cannot do?
- When the user mongodb does not have read permission to the / testdir directory, what does it mean that it cannot do?
- When user redis does not have write permission to / testdir directory, can the read-only file file1 in this directory be modified and deleted?
- When user zabbix has write and execute permissions on / testdir directory, can the read-only file file1 in this directory be modified and deleted?
- Copy the / etc/fstab file to / var/tmp, set the owner of the file to tomcat and the group to which it belongs to apps. The group has read and write permissions, and others have no permissions
- User git's home directory is deleted by mistake. Please rebuild and restore the user's home directory and corresponding permission attributes
4.5 special permissions on Linux file system
Previously, we introduced three common permissions: r, w, x, and three special permissions: suid, sgid, and sticky
4.5.1 special permission SUID
Premise: the process has a master and a group; The file has a master and a group
- Whether any executable program file can be started as a process depends on whether the initiator has execution permission on the program file
- After starting as a process, the owner of the process is the initiator, and the group of the process is the group to which the initiator belongs
- The permission of a process to access a file depends on the initiator of the process
(a) The initiator of the process is the same as the owner of the file: the file owner permission is applied
(b) The initiator of the process belongs to the file group; Apply file group permissions
© Apply file "other" permissions
SUID permission function on binary executable:
- Whether any executable program file can be started as a process depends on whether the initiator has execution permission on the program file
- After starting as a process, the owner of the process is the owner of the original program file
- SUID is only valid for binary executables
- SUID setting has no meaning on the directory
SUID permission setting:
chmod u+s FILE... chmod 6xxx FILE chmod u-s FILE...
example:
[root@rocky8 ~]# ll /bin/passwd -rwsr-xr-x. 1 root root 33544 Mar 15 2021 /bin/passwd #It has s permissions [root@rocky8 ~]# cat /etc/shadow root:$6$G1LP.xcEYUJFDzkv$VMsBxrdURN9r6YyZr/8O16SHioMr87fye1o6lsnfdQnm9T9qWbQWa4aG5gVxuCJIQUGrby7vIyPqk90hjtcT21::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18906:::::: systemd-coredump:!!:18906:::::: systemd-resolve:!!:18906:::::: tss:!!:18906:::::: polkitd:!!:18906:::::: unbound:!!:18906:::::: sssd:!!:18906:::::: sshd:!!:18906:::::: postfix:!!:18906:::::: raymond:$6$ATgT1/69V4P9rymT$iVlReKGeE6/Q0BdAHbFfvnWHpmpcv0H4Evrp9oYTo7p2GamkPbv.vQiy/4z8xwtEKJD3rwK/iegq8Vt8K2pCG0:18906:0:99999:7::: boss:!!:18906:0:99999:7::: #Whether you can access the file has nothing to do with what software to open, but with the user [root@rocky8 ~]# su raymond [raymond@rocky8 root]$ cat /etc/shadow cat: /etc/shadow: Permission denied #This file cannot be accessed [raymond@rocky8 root]$ passwd Changing password for user raymond. Current password: New password: Retype new password: passwd: all authentication tokens updated successfully. #Users can change their passwords [raymond@rocky8 root]$ ll /etc/shadow ---------- 1 root root 818 Oct 6 20:58 /etc/shadow #The access time of this file is modified [raymond@rocky8 root]$ cat /etc/shadow cat: /etc/shadow: Permission denied #But you can't access this file [raymond@rocky8 root]$ ll /bin/passwd -rwsr-xr-x. 1 root root 33544 Mar 15 2021 /bin/passwd #Because this tool has suid attribute [raymond@rocky8 root]$ exit exit #Suid permission function: when a user runs this program, it will automatically inherit the permission of the program owner, and then modify the file and set suid permission. The file must be an executable file and the file must be a binary executable program #Sgid permission function. When a user runs this program, it is equivalent to the permission of this group [root@rocky8 ~]# ll /bin/cat -rwxr-xr-x. 1 root root 38568 Mar 15 2021 /bin/cat [root@rocky8 ~]# chmod u+s /bin/cat #Model method [root@rocky8 ~]# ll /bin/cat -rwsr-xr-x. 1 root root 38568 Mar 15 2021 /bin/cat [root@rocky8 ~]# chmod 4755 /bin/cat #Digital method [root@rocky8 ~]# ll /bin/cat -rwsr-xr-x. 1 root root 38568 Mar 15 2021 /bin/cat [root@rocky8 ~]# su raymond [raymond@rocky8 root]$ cat /etc/shadow root:$6$G1LP.xcEYUJFDzkv$VMsBxrdURN9r6YyZr/8O16SHioMr87fye1o6lsnfdQnm9T9qWbQWa4aG5gVxuCJIQUGrby7vIyPqk90hjtcT21::0:99999:7::: bin:*:18700:0:99999:7::: daemon:*:18700:0:99999:7::: adm:*:18700:0:99999:7::: lp:*:18700:0:99999:7::: sync:*:18700:0:99999:7::: shutdown:*:18700:0:99999:7::: halt:*:18700:0:99999:7::: mail:*:18700:0:99999:7::: operator:*:18700:0:99999:7::: games:*:18700:0:99999:7::: ftp:*:18700:0:99999:7::: nobody:*:18700:0:99999:7::: dbus:!!:18906:::::: systemd-coredump:!!:18906:::::: systemd-resolve:!!:18906:::::: tss:!!:18906:::::: polkitd:!!:18906:::::: unbound:!!:18906:::::: sssd:!!:18906:::::: sshd:!!:18906:::::: postfix:!!:18906:::::: raymond:$6$RZ9Ch9wo01t7qk2M$4cGm1sBSEwVakl5q80Mhme1h6iicq.wVXI5unLDPLo7OCarO29S6MQWoC6w.tdVQS1H.Wm1JnOYYvtZb4qQgO/:18906:0:99999:7::: boss:!!:18906:0:99999:7::: #Now ordinary users can also access the / etc/shadow file [raymond@rocky8 root]$ ll /etc/shadow ---------- 1 root root 818 Oct 6 20:58 /etc/shadow #Although / etc/shadow does not have permission [raymond@rocky8 root]$ ll /bin/cat -rwsr-xr-x. 1 root root 38568 Mar 15 2021 /bin/cat #However, if / bin//cat gives suid permission, it is equivalent to having root user permission. It can do anything [raymond@rocky8 root]$ exit exit [root@rocky8 ~]# ll /bin/cat -rwsr-xr-x. 1 root root 38568 Mar 15 2021 /bin/cat [root@rocky8 ~]# chmod u-s /bin/cat [root@rocky8 ~]# ll /bin/cat -rwxr-xr-x. 1 root root 38568 Mar 15 2021 /bin/cat stick bit Viscous potential [root@rocky8 ~]# ll /tmp total 8 -rwx------. 1 root root 291 Oct 6 19:20 ks-script-hu2_65lt -rwx------. 1 root root 701 Oct 6 19:20 ks-script-ltsb0ybt drwx------ 2 root root 6 Oct 6 19:27 vmware-root_720-2957714511 drwx------. 2 root root 6 Oct 6 19:21 vmware-root_727-4290690966 drwx------ 2 root root 6 Oct 6 19:25 vmware-root_733-4248680474 drwx------. 2 root root 6 Oct 6 19:21 vmware-root_773-4256676260 [root@rocky8 ~]# su raymond [raymond@rocky8 root]$ touch /tmp/raymond.txt [raymond@rocky8 root]$ exit exit [root@rocky8 ~]# su boss [boss@rocky8 root]$ touch /tmp/boss.txt [boss@rocky8 root]$ rm -f /tmp/raymond.txt rm: cannot remove '/tmp/raymond.txt': Operation not permitted #You can't delete other people's files [boss@rocky8 root]$ rm -f /tmp/boss.txt #You can only delete your own files [boss@rocky8 root]$ ll -d /tmp drwxrwxrwt. 11 root root 4096 Oct 6 21:06 /tmp #Why can't I delete it? Because / tmp has the permission of stick bit #stick bit permission. If you want to delete a file, you can only delete your own, not others [boss@rocky8 root]$ exit exit [root@rocky8 ~]# chmod o-t /tmp [root@rocky8 ~]# ll -d /tmp drwxrwxrwx. 11 root root 4096 Oct 6 21:06 /tmp suid 4 sgid 2 stick 1 [root@rocky8 ~]# chmod 7777 /tmp [root@rocky8 ~]# ll -d /tmp drwsrwsrwt. 11 root root 4096 Oct 6 21:06 /tmp [root@rocky8 ~]# chmod 777 /tmp [root@rocky8 ~]# ll -d /tmp drwsrwsrwx. 11 root root 4096 Oct 6 21:06 /tmp #In this way, suid and sgid permissions cannot be removed [root@rocky8 ~]# chmod 0777 /tmp [root@rocky8 ~]# ll -d /tmp drwsrwsrwx. 11 root root 4096 Oct 6 21:06 /tmp #It won't go away [root@rocky8 ~]# chmod u-s,g-s /tmp [root@rocky8 ~]# ll -d /tmp drwxrwxrwx. 11 root root 4096 Oct 6 21:06 /tmp #The pattern method can be removed [root@rocky8 ~]# chmod o+t /tmp [root@rocky8 ~]# ll -d /tmp drwxrwxrwt. 11 root root 4096 Oct 6 21:06 /tmp sgid On the directory, new files created in this directory will automatically continue the group permissions of this directory [root@rocky8 ~]# mkdir /data/dir [root@rocky8 ~]# ll -d /data/dir drwxr-xr-x 2 root root 6 Oct 6 21:11 /data/dir [root@rocky8 ~]# chmod 750 /data/dir [root@rocky8 ~]# ll -d /data/dir drwxr-x--- 2 root root 6 Oct 6 21:11 /data/dir [root@rocky8 ~]# chgrp raymond /data/dir [root@rocky8 ~]# ll -d /data/dir drwxr-x--- 2 root raymond 6 Oct 6 21:11 /data/dir [root@rocky8 ~]# touch /data/dir/root.txt [root@rocky8 ~]# ll /data/dir/root.txt -rw-r--r-- 1 root root 0 Oct 6 21:13 /data/dir/root.txt #Now it has nothing to do with the group to which the folder belongs [root@rocky8 ~]# chmod g+s /data/dir [root@rocky8 ~]# ll -d /data/dir drwxr-s--- 2 root raymond 22 Oct 6 21:13 /data/dir #Add sgid permission to the directory [root@rocky8 ~]# touch /data/dir/root2.txt [root@rocky8 ~]# ll -d /data/dir/root2.txt -rw-r--r-- 1 root raymond 0 Oct 6 21:15 /data/dir/root2.txt #The group it now belongs to is raymond, which inherits the group permissions from the folder suid sgid It acts on binary programs and has executable permissions sticky Act on Directory sgid Act on Directory
4.5.2 special permission SGID
SGID permission function on binary executable:
- Whether any executable program file can be started as a process depends on whether the initiator has execution permission on the program file
- After starting as a process, the process belongs to the group of the original program file
SGID permission setting:
chmod g+s FILE... chmod 2xxx FILE chmod g-s FILE...
SGID permission function on Directory:
By default, when a user creates a file, its group is the primary group to which the user belongs. Once a directory is set with SGID, the group to which the user with write permission creates a file in this directory is the group to which the directory belongs. It is usually used to create a collaboration directory
SGID permission setting:
chmod g+s DIR... chmod 2xxx DIR chmod g-s DIR...
4.5.3 Sticky bit of special permission
A directory with write permission. Usually, a user can delete any file in the directory, regardless of the permission or ownership of the file
Set the Sticky bit in the directory, and only the owner or root of the file can delete the file
sticky settings are meaningless on files
Sticky permission settings:
chmod o+t DIR... chmod 1xxx DIR chmod o-t DIR...
example:
[root@rocky8 ~]# ll -d /tmp drwxrwxrwt. 11 root root 4096 Oct 6 21:06 /tmp
4.5.4 special authority digital method
SUID SGID STICKY
000 0 001 1 010 2 011 3 100 4 101 5 110 6 111 7
example:
chmod 4777 /tmp/a.txt
Permission bit mapping
- SUID: user, occupying the execution permission bit of the owner
- s: Owner has x permission
- S: Owner does not have x permission
- SGID: group, occupying the execution permission bit of the group
- s: group has x permissions
- S: group does not have x permission
- Sticky: other, occupy the execution permission bit of other
- t: other has x permissions
- T: other does not have x permission
4.6 setting file special attributes
Set the special attributes of the file, and you can access the root user to delete or modify the file by mistake
Cannot delete, rename, change
chattr +i file
You can only add content, not delete, rename
chattr +a file
Show specific properties
lsattr
example:
[root@rocky8 ~]# ll /etc/passwd -rw-r--r-- 1 root root 1130 Oct 6 19:31 /etc/passwd [root@rocky8 ~]# chattr +i /etc/passwd [root@rocky8 ~]# mv /etc/passwd /opt mv: cannot move '/etc/passwd' to '/opt/passwd': Operation not permitted [root@rocky8 ~]# rm -f /etc/passwd rm: cannot remove '/etc/passwd': Operation not permitted [root@rocky8 ~]# echo aaa >> /etc/passwd -bash: /etc/passwd: Operation not permitted #If i attribute is added, the file cannot be moved, deleted or written [root@rocky8 ~]# ll /etc/passwd -rw-r--r-- 1 root root 1130 Oct 6 19:31 /etc/passwd [root@rocky8 ~]# lsattr /etc/passwd ----i--------------- /etc/passwd #You can see that this file has the i attribute #The i attribute prohibits file modification and becomes a read-only file [root@rocky8 ~]# useradd boss2 useradd: cannot open /etc/passwd #Users can't create it now [root@rocky8 ~]# chattr -i /etc/passwd #Remove the i attribute [root@rocky8 ~]# lsattr /etc/passwd -------------------- /etc/passwd [root@rocky8 ~]# ls anaconda-ks.cfg anaconda-screenshots pass.txt [root@rocky8 ~]# chattr +a pass.txt [root@rocky8 ~]# ll pass.txt ---------- 1 root root 0 Oct 6 20:50 pass.txt [root@rocky8 ~]# rm -f pass.txt rm: cannot remove 'pass.txt': Operation not permitted [root@rocky8 ~]# mv pass.txt /opt mv: cannot move 'pass.txt' to '/opt/pass.txt': Operation not permitted #With the a attribute added, the file cannot be deleted or moved [root@rocky8 ~]# echo new data >> pass.txt [root@rocky8 ~]# cat pass.txt new data #a attribute, the file can only be appended [root@rocky8 ~]# echo new data2 > pass.txt -bash: pass.txt: Operation not permitted #No coverage [root@rocky8 ~]# lsattr pass.txt -----a-------------- pass.txt #You can see that this file has a attribute [root@rocky8 ~]# chattr -a pass.txt #Remove the a attribute [root@rocky8 ~]# lsattr pass.txt -------------------- pass.txt [root@rocky8 ~]# rm -f pass.txt #You can delete it now
4.7 access control list
4.7.1 ACL permission function
ACL: Access Control List to realize flexible permission management
In addition to the owner of the file, the group and others, you can set permissions for more users
xfs and ext4 file systems created by CentOS7 by default have ACL functions
In versions before CentOS7, the ext4 file system created manually by default has no ACL function and needs to be added manually
tune2fs –o acl /dev/sdb1 mount –o acl /dev/sdb1 /mnt/test
ACL effective order:
Owner, custom user, group|Custom groups, others
4.7.2 ACL related commands
setfacl can set ACL permissions
getfacl to view the set ACL permissions
example:
[root@rocky8 ~]# cd /data [root@rocky8 data]# ls dir dir2 dir3 dir4 [root@rocky8 data]# rm -rf * [root@rocky8 data]# su raymond [raymond@rocky8 data]$ cat a.txt #Can read [raymond@rocky8 data]$ echo raymond >> a.txt bash: a.txt: Permission denied #Can't write [raymond@rocky8 data]$ exit exit [root@rocky8 data]# setfacl -m u:boss:rw a.txt #Allow boss users to rw, raymond can't read or write [root@rocky8 data]# ll a.txt -rw-rw-r--+ 1 root root 0 Oct 6 21:28 a.txt #There is an extra +, + plus sign indicates ACL permission [root@rocky8 data]# getfacl a.txt #getfacl view acl permissions # file: a.txt # owner: root # group: root user::rw- user:boss:rw- group::r-- mask::rw- other::r-- [root@rocky8 data]# setfacl -m u:raymond:0 a.txt #Write 0 or - here [root@rocky8 data]# getfacl a.txt # file: a.txt # owner: root # group: root user::rw- user:raymond:--- user:boss:rw- group::r-- mask::rw- other::r-- [root@rocky8 data]# ll a.txt -rw-rw-r--+ 1 root root 0 Oct 6 21:28 a.txt [root@rocky8 data]# su raymond [raymond@rocky8 data]$ cat a.txt cat: a.txt: Permission denied [raymond@rocky8 data]$ echo xx >> a.txt bash: a.txt: Permission denied #raymond users cannot read or write [raymond@rocky8 data]$ exit exit [root@rocky8 data]# su boss [boss@rocky8 data]$ cat a.txt [boss@rocky8 data]$ echo boss >> a.txt [boss@rocky8 data]$ cat a.txt boss #boss users can read or write [boss@rocky8 data]$ ll a.txt -rw-rw-r--+ 1 root root 5 Oct 6 21:34 a.txt [boss@rocky8 data]$ exit exit In this way, more people can have different permissions [root@rocky8 data]# setfacl -m g:admins:rwx a.txt #Set acl permissions on groups [root@rocky8 data]# getfacl a.txt # file: a.txt # owner: root # group: root user::rw- user:raymond:--- user:boss:rw- group::r-- group:admins:rwx mask::rwx other::r-- [root@rocky8 data]# ll a.txt -rw-rwxr--+ 1 root root 5 Oct 6 21:34 a.txt #First, check whether the file owner has permission, then acl permission, then the group, and finally other [root@rocky8 data]# setfacl -x u:raymond a.txt # Remove the acl permission of raymond user [root@rocky8 data]# getfacl a.txt # file: a.txt # owner: root # group: root user::rw- user:boss:rw- group::r-- group:admins:rwx mask::rwx other::r-- [root@rocky8 data]# setfacl -b a.txt #setfacl -b remove all permissions [root@rocky8 data]# ll a.txt -rw-r--r-- 1 root root 5 Oct 6 21:34 a.txt #After removing the + plus sign, there is no more
example:
[root@rocky8 data]# touch f1.txt [root@rocky8 data]# ll f1.txt -rw-r--r-- 1 root root 0 Oct 6 22:01 f1.txt [root@rocky8 data]# setfacl -m u:raymond:- f1.txt [root@rocky8 data]# ll f1.txt -rw-r--r--+ 1 root root 0 Oct 6 22:01 f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:--- group::r-- mask::r-- other::r-- [root@rocky8 data]# su raymond [raymond@rocky8 data]$ cat f1.txt cat: f1.txt: Permission denied [raymond@rocky8 data]$ echo xx >> f1.txt bash: f1.txt: Permission denied [raymond@rocky8 data]$ exit exit
example:
[root@rocky8 data]# rm -f f1.txt [root@rocky8 data]# touch f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- group::r-- other::r-- [root@rocky8 data]# setfacl -m u:raymond:0 f1.txt [root@rocky8 data]# setfacl -m g:admins:w f1.txt [root@rocky8 data]# ll f1.txt -rw-rw-r--+ 1 root root 0 Oct 6 22:03 f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:--- group::r-- group:admins:-w- mask::rw- other::r-- [root@rocky8 data]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond),1002(admins) [root@rocky8 data]# id boss uid=1001(boss) gid=1001(boss) groups=1001(boss),1002(admins) [root@rocky8 data]# usermod -G "" raymond [root@rocky8 data]# usermod -G "" boss [root@rocky8 data]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond) [root@rocky8 data]# id boss uid=1001(boss) gid=1001(boss) groups=1001(boss) [root@rocky8 data]# su boss [boss@rocky8 data]$ cat f1.txt [boss@rocky8 data]$ echo bossdata >> f1.txt bash: f1.txt: Permission denied [boss@rocky8 data]$ exit exit [root@centos8 data]#gpasswd -a mage admins Adding user mage to group admins [root@centos8 data]#id mage uid=1001(mage) gid=1001(mage) groups=1001(mage),1002(admins) [root@centos8 data]#su mage [mage@centos8 data]$echo magedata3 >> f1.txt [mage@centos8 data]$cat f1.txt cat: f1.txt: Permission denied [mage@centos8 data]$exit exit [root@centos8 data]#su wang [wang@centos8 data]$cat f1.txt cat: f1.txt: Permission denied [wang@centos8 data]$echo wangdata >> f1.txt bash: f1.txt: Permission denied [wang@centos8 data]$exit exit [root@rocky8 data]# groupmems -a raymond -g admins [root@rocky8 data]# id raymond uid=1000(raymond) gid=1000(raymond) groups=1000(raymond),1002(admins) [root@rocky8 data]# su raymond [raymond@rocky8 data]$ getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:--- group::r-- group:admins:-w- mask::rw- other::r-- [raymond@rocky8 data]$ cat f1.txt cat: f1.txt: Permission denied [raymond@rocky8 data]$ echo raymonddata2 >> f1.txt bash: f1.txt: Permission denied [raymond@rocky8 data]$ exit exit
example:
mount -o acl /directory getfacl file |directory setfacl -m u:raymond:rwx file|directory setfacl -m g:admins:rw file| directory setfacl -x u:raymond file |directory #Clear all ACL permissions setfacl -b file1 #Copy the acl permission of file1 to file2 getfacl file1 | setfacl --set-file=- file2
mask permissions
- The mask only affects the maximum permissions of people and groups other than the owner and other
- The mask can become an effective permission only after logical and operation with the user's permission
- User or group settings must exist within the scope of mask permission settings to take effect
example:
setfacl -m mask::rx file
example:
[root@rocky8 data]# ll f1.txt -rw-rw-r--+ 1 root root 0 Oct 6 22:03 f1.txt [root@rocky8 data]# chmod g=r f1.txt [root@rocky8 data]# ll f1.txt -rw-r--r--+ 1 root root 0 Oct 6 22:03 f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:--- group::r-- group:admins:-w- #effective:--- mask::r-- other::r-- [root@rocky8 data]# setfacl -m mask::rw f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:--- group::r-- group:admins:-w- mask::rw- other::r-- [root@rocky8 data]# setfacl -m u:raymond:rwx f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:rwx group::r-- group:admins:-w- mask::rwx other::r-- [root@rocky8 data]# setfacl -m mask::rw f1.txt [root@rocky8 data]# getfacl f1.txt # file: f1.txt # owner: root # group: root user::rw- user:raymond:rwx #effective:rw- group::r-- group:admins:-w- mask::rw- other::r--
The – set option will delete the original ACL items and replace them with new ones. It should be noted that UGO settings must be included. You can't just add ACLS like - m
example:
setfacl --set u::rw,u:raymond:rw,g::r,o::- file1
4.8 practice
- New files created in / testdir/dir automatically belong to the web group. Members of group apps, such as tomcat, can read and write these new files. Members of group dbs, such as mysql, can only read new files. Other users (not belonging to web, apps, dbs) cannot access this folder
- How to restore the / bin/chmod file after deleting its execution permission by mistake?