Experiment introduction and preparation
There are 15 experiments in this part, which need to be completed by Cisco packet tracker software.
Please first understand the concepts of VLSM, CIDR, RIP, OSPF, VLAN, STP, NAT and DHCP to enable network planning and configuration.
preface
This is my third experiment, the Cisco packet tracker experiment of computer network.
The following is the main body of this article.
1, Connect two PC s directly to build LAN
Purpose:
(1)Put two PC Direct connections form a network. Note: cross wires are required for direct connection. (2)Carry out two PC Basic network configuration, only configuration is required IP Address, and then mutual ping Communication is successful.
record:

2, Building LAN with switches
Purpose:

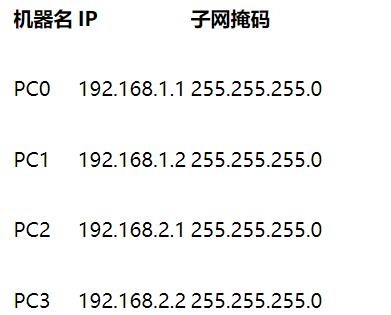
Question:
(1) Can PC0 ping PC1, PC2 and PC3?
(2) Can PC3 ping PC0, PC1 and PC2? Why?
(3) Change the masks of the four PC s to 255.255.0.0. Can they ping each other? Why?
(4) Does the network connected by layer-2 switch need to be configured with a gateway? Why?
Answer: (1) yes.
(2) Hosts 0 and 1 are under one subnet, and hosts 2 and 3 are under another subnet. Therefore, host 3 can ping host 2, but not host 1 and 2. Hosts under the same subnet can ping each other, while hosts under different subnets cannot Ping each other.
(3) Yes, because they have the same subnet mask, they are on the same subnet.
(4) If necessary, configure gateway network interconnection in layer 2 switch. Without a gateway, the local host cannot communicate with other networks.
Additional questions:
Hub is a multi interface device working in the physical layer. What is the difference between hub and switch? Please build the network with hub in CPT software for actual verification.
A: the Switch, a data link layer device, is used to forward data packets. Like the bridge, it also identifies the MAC address in the frame and forwards it to a specific port. HUB is a device that works in the physical layer. Because it only works in the physical layer, it does not care about and cannot care about the issues involved in the upper layers of OSI. Its working mechanism process is: when a packet is received from one port, it will forward the packet at other ports, Because it does not know and cannot know who the packet is sent to (the physical layer device only cares about the physical concepts of voltage), it can only broadcast to everyone.
3, Switch interface address list
Purpose:
(1)Layer 2 switch is a plug and play multi interface device. It has three processing methods for received frames: broadcasting, forwarding and discarding (please find out when and what operations). Then, in order to forward successfully, there must be an interface address list in the switch, i.e MAC Table, which is automatically obtained by the switch through learning! (2)Still build the topology shown in the figure above and configure the configuration of each computer IP In the same subnet, use the magnifying glass in the toolbar to click a switch, such as the one on the left Switch3,choice MAC Table,You can see the of the original switch MAC The table is empty, that is, it does not know how to forward frames (so what will it do?), use PC0 Visit( ping)PC1 After that, check the status of the switch MAC Table, there are corresponding records now. Please think about how to get it. With the increase of network communication, each switch will generate its own complete MAC Table. At this time, the switching speed of the switch is the fastest!
record:

4, Spanning Tree Protocol
explain:
The switch will broadcast when the destination address is unknown or the broadcast frame is received. If there is a loop / loop between switches, a broadcast cycle storm will occur, which will seriously affect the network performance.
The STP protocol running in the switch can avoid the broadcast cycle storm between switches.
Using only switches, build the following topology:

This is the initial state. We can see that there is a loop between switches, which will cause the cyclic transmission of broadcast frames, that is, a broadcast storm, which will seriously affect the network performance.
Then, the switch will automatically block the redundant lines through the spanning tree protocol (STP) to form a spanning tree with a unique path tree with Switch4 as the root (which root switch has relevant policies)!
After a period of time, with the STP protocol successfully building the spanning tree, the two interfaces of Switch5 are physically connected, but logically impassable. They are in Blocking state (Orange), as shown in the following figure:

During network operation, if there is a problem with the physical connection between Switch4 and Switch5 at some time (cut off the connection between Switch4 and Switch5), the spanning tree will change automatically. The previous Blocking interface above Switch5 is now active (green), but the interface below Switch5 is still Blocking (Orange). As shown in the figure below:
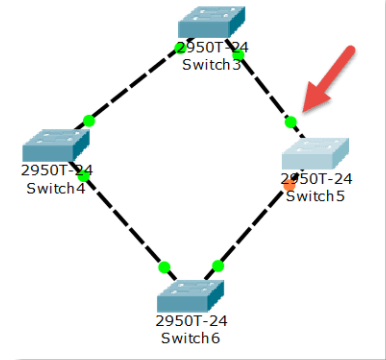
Note: the STP protocol of the switch, i.e. spanning tree protocol, always automatically ensures that there will be no loop between switches, thus forming a broadcast storm.
5, Preliminary router configuration
explain:
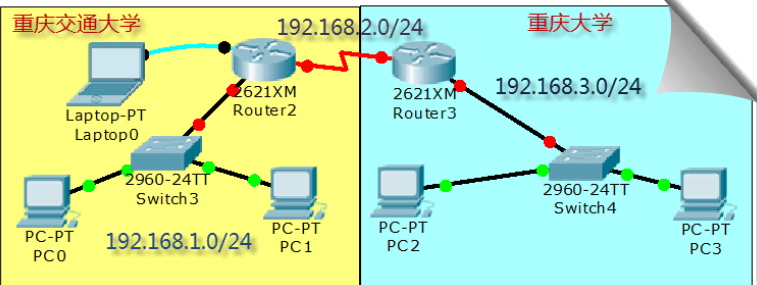
We simulate the connection between Chongqing Jiaotong University and Chongqing University, and construct the following topology:
Note 1:
Jiaotong University and Chongqing University are obviously two different subnets. The communication between different subnets needs to pass through the router.
There is at least one subnet under each interface of the router. In the figure, we simply plan three subnets:
(1)The router on the left belongs to Jiaotong University. The switch is used to connect the network of Jiaotong University and assign the network number 192.168.1.0/24, The router interface is also the gateway of Jiaotong University network IP 192.168.1.1 (2)The router on the right belongs to Chongqing University. The switch is used to connect the network of Chongqing University and assign the network number 192.168.3.0/24, The router interface is also the gateway of Chongqing University network IP 192.168.3.1 (3)The two routers are connected by WAN interface, which is also a subnet, and the network number 192 is assigned.168.2.0/24
Note 2:
In reality, the connection between Jiaotong University and Chongqing University is remote. The connection is either through the optical fiber interface of the router or through the WAN interface, the so-called serial port (as shown in the topology diagram). Generally, it is not connected through twisted pair (why?).
Let's take the WAN port connection through the router as an example to make relevant configuration. Please note: the router we selected does not have a WAN module (WIC-1T, etc.) by default. You need to turn off the router, add it, and then turn it on.
Note 3:
In the simulated WAN connection, pay attention to the DCE and DTE terminals (there is a prompt on the line when connecting, and the DCE terminal with a clock flag. Please refer to relevant materials for the concepts of DCE and DTE), The clock frequency of 64000 shall be configured at the DCE end.
Note 4:
The router has a variety of command line configuration modes, and each mode corresponds to different prompts and corresponding permissions.
Please pay attention to entering configuration related commands in the correct mode.
User mode: User mode Privileged mode: Privileged mode Global configuration mode: Global configuration mode Interface mode: Interface configuration mode Subinterface mode: Sub interface configuration mode
Note V:
In reality, it is obvious that the new router cannot be configured remotely. We must connect with the console interface of the router through the serial port of the notebook and make the initial configuration (note that the bit rate is set to 9600) before we can configure remotely through the network. This is also the intention of the notebook connection drawn on the upper left of the figure above.
Note 6:
In the CLI interface of the router, you can see that after the router is started successfully, because there is NO configuration, you will be prompted whether to enter the initial configuration dialog, Select NO because there are many steps
For example, the preliminary configuration of Jiaotong University router can be as follows:
In our experiment, the following configurations are not necessary, but in reality, for security, the following login and privileged password configurations are necessary, otherwise everyone can operate your router or switch!
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#interface FastEthernet0/0 Router(config-if)#ip address 192.168.1.1 255.255.255.0 Router(config-if)#no shutdown Router(config-if)#exit Router(config)#line vty 0 4 / / five terminals from 0 to 4 can log in at the same time Router(config-line)#password dswybs / / remote login password Router(config-line)#login Router(config-line)#exit Router(config)#enable password dswybs / / privilege mode password Router(config)#^Z / / exit
The basic configuration of Jiaotong University router is as follows:
Ethernet port:
Router>enable // Enter privileged mode from normal mode Router#configure terminal / / enter global configuration mode Router(config)#interface f0/0 / / enter the configuration Ethernet port mode Router(config-if)#ip address 192.168.1.1 255.255.255.0 / / configure the IP address of the interface Router(config-if)#no shutdown / / activate the interface Router(config-if)#^z / / directly retreat to privileged mode Router#
WAN port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int s0/0 / / enter the WAN port configuration mode Router(config-if)#ip address 192.168.2.1 255.255.255.0 / / configure the IP address of the interface Router(config-if)#clock rate 64000 / / it is the DCE terminal. Configure the clock frequency Router(config-if)#no shutdown / / activate the interface Router(config-if)#^z / / directly retreat to privileged mode Router#
The basic configuration of Chongqing University router is as follows:
Ethernet port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int f0/0 / / enter the configuration Ethernet port mode Router(config-if)#ip address 192.168.3.1 255.255.255.0 / / configure the IP address of the interface Router(config-if)#no shutdown / / activate the interface Router(config-if)#^z / / directly retreat to privileged mode Router#
WAN port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int s0/0 / / enter the WAN port configuration mode Router(config-if)#ip address 192.168.2.2 255.255.255.0 / / configure the IP address of the interface Router(config-if)#no shutdown / / activate the interface Router(config-if)#^z / / directly retreat to privileged mode Router#
Basic network configuration of PC:
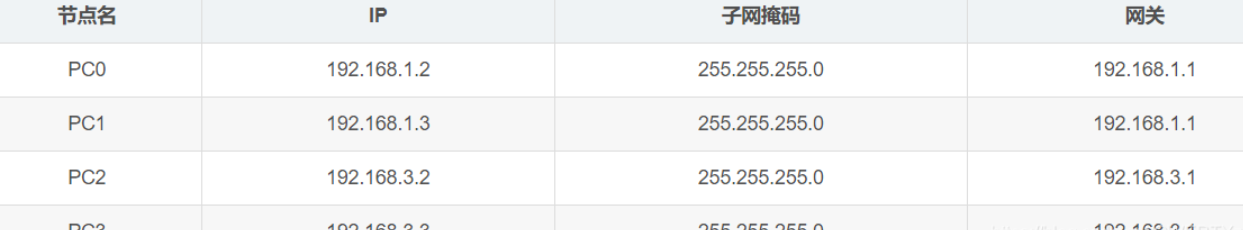
After configuration, the topology diagram:

Question:
At present, PCs and gateways in Jiaotong University can ping each other, and Chongqing University is similar. However, you cannot Ping major PCs from Jiaotong University's PCs, and vice versa, that is, you cannot cross subnets. Why?
A: when testing the network, the usual method is to ping an IP address. If you can ping, it means that the link is unblocked. If there is no Ping, it means that the link is blocked. The conclusion drawn by this test method is not rigorous and may not be correct. Unlike complete TCP/IP packets, the ping function sends only ICMP control message protocol packets. When you use the ping function, the local PC will first query the local ARP address mapping table. If the destination IP is not in the ARP cache, the restricted PC will query the ARP mapping table. If your circuit is connected to a general router, that is, there is no layer 3 switching routing function. When the local circuit queries the ARP mapping table, it will send an ICMP packet with the MAC layer destination address as the router's MAC address. After receiving the ICMP packet, the router will discard the ICMP packet if it finds that the destination IP address is not the subnet of its router through address filtering, ARP query package will not be sent for ARP address query. If the local computer is connected to a switch or router with three-layer interactive routing function, it will send ARP query packet for network query.
6, Static routing
explain:
Static routing is a non adaptive routing protocol, which is manually configured by network managers and cannot be based on The network topology changes. Therefore, static routing is simple and efficient, and is suitable for networks with very simple structure Collaterals. In the current simple topology, we can use static routing, that is, directly tell the router to a network Just tell me how to get there.
When the basic configuration of the above router is successful, use the following command to configure the static routing protocol:
Static routing configuration of Jiaotong University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#ip route 192.168.3.0 255.255.255.0 192.168.2.2 / / tell the router of Jiaotong University that the next hop of the network to 192.168.3.0 is 192.168.2.2 Router(config)#Exit / / exit to privileged mode Router#show ip route / / view the route table
Chongqing University router static routing configuration:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#ip route 192.168.1.0 255.255.255.0 192.168.2.1 / / tell the Chongqing University router that the next hop to 192.168.1.0 is 192.168.2.1 Router(config)#Exit / / exit to privileged mode Router#show ip route / / view the route table
Check the routing table and you can see a route marked S, which means Static.
So far, these PC s can ping each other!
record:

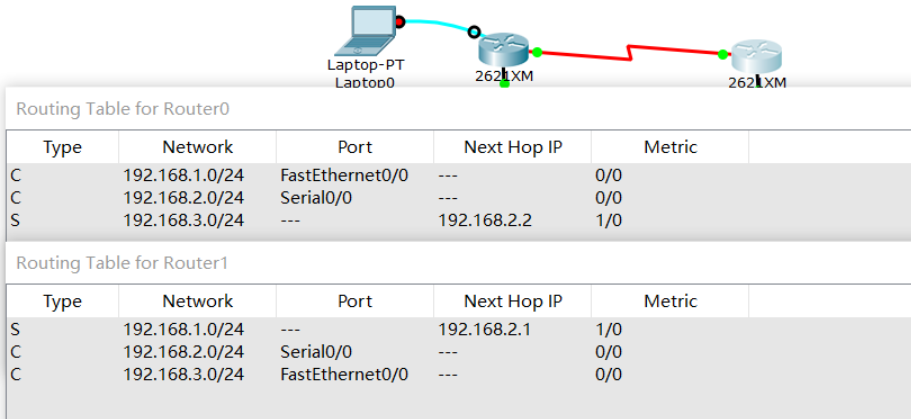
Note: our topology only simulates 3 networks. In reality, the number of networks connected by the router is very large. We also need to configure a default route, otherwise other networks cannot reach! Of course, our topology can be ignored.
Router(config)#ip route 0.0.0.0 0.0.0.0 ... // By default, forward all to This IP
7, Dynamic routing RIP
explain:
Dynamic routing protocol adopts adaptive routing algorithm, which can reset the computer according to the change of network topology Good routing. RIP My full name is Routing Information Protocol,Is the representative of distance vector routing Although the former is eliminated, it can be used as the object of our study). use RIP The protocol only needs to tell the router Which networks are directly connected, and then RIP The routing table is automatically constructed according to the algorithm. Because the network we simulate is very simple, we can't use static and dynamic routing at the same time. Otherwise, look No effect, so we need to clear the static route just configured.
Clear static routing configuration:
(1)Turn off the router directly. It is equivalent to that no configuration is saved, and then each interface is reconfigured according to the previous basic configuration Set IP And other parameters (this method is recommended. You can get familiar with the interface configuration command again); (2)use no Command to clear static routes. In the global configuration mode, the router of Jiaotong University uses: no ip route 192.168.3.0 255.255.255.0 192.168.2.2,Chongqing University router uses: no ip route 192.168.1.0 255.255.255.0 192.168.2.1 . Equivalent to using no The command cancels the static routing command just configured.
RIP routing configuration of Jiaotong University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#router rip / / enable the RIP routing protocol. Note the router command Router(config-router)#Network 192.168.1.0 / / network 192.168.1.0 is directly connected to me Router(config-router)#Network 192.168.2.0 / / network 192.168.2.0 is directly connected to me Router(config-router)#^z / / directly retreat to privileged mode Router#show ip route / / view the route table
RIP routing configuration of Chongqing University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#router rip / / enable the RIP routing protocol. Note the router command Router(config-router)#Network 192.168.3.0 / / network 192.168.3.0 is directly connected to me Router(config-router)#Network 192.168.2.0 / / network 192.168.2.0 is directly connected to me Router(config-router)#^z / / directly retreat to privileged mode Router#show ip route / / view the route table
Looking at the routing table, you can see a route marked R, which means RIP.
So far, these PC s can ping each other!
record:
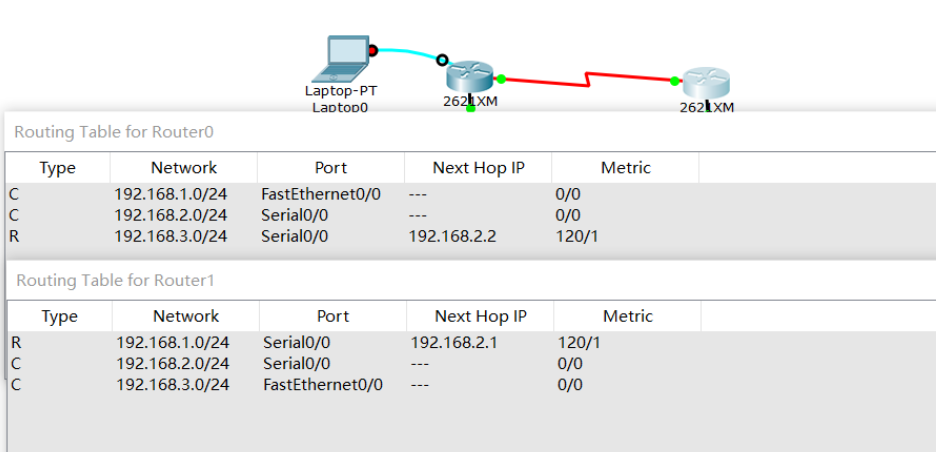
8, Dynamic routing OSPF
explain:
OSPF(Open Shortest Path First Open shortest path first) is an internal gateway Agreement( Interior Gateway Protocol,abbreviation IGP), Used in a single autonomous system( Autonomous System,AS) Intra decision routing. OSPF Better performance RIP,It is a widely used routing protocol for intra domain routing. Similarly, we need to put the configuration just now RIP The route is cleared first.
Clear RIP routing configuration:
(1)Turn off the router directly. It is equivalent to that no configuration is saved, and then each interface is reconfigured according to the previous basic configuration IP Equal parameters (2)use no Command clear RIP route. In the global configuration mode, each router uses: no router rip Command to clear
OSPF routing configuration of Jiaotong University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#router ospf 1 / / enable OSPF routing protocol. The process number is 1 (you can ignore the concept of process number temporarily) Router(config-router)#Network 192.168.1.0 0.0.255 area 0 / / all hosts belonging to the 192.168.1.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF Router(config-router)#Network 192.168.2.0 0.0.255 area 0 / / all hosts belonging to the 192.168.2.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF Router(config-router)#^z / / directly retreat to privileged mode Router#show ip route / / view the route table
OSPF routing configuration of Chongqing University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#router ospf 1 / / enable OSPF routing protocol. The process number is 1 Router(config-router)#Network 192.168.3.0 0.0.255 area 0 / / all hosts belonging to the 192.168.3.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF Router(config-router)#Network 192.168.2.0 0.0.255 area 0 / / all hosts belonging to the 192.168.2.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF Router(config-router)#^z / / directly retreat to privileged mode Router#show ip route / / view the route table
Looking at the routing table, you can see a route marked O, which means OSPF.
So far, these PC s can ping each other!
record:
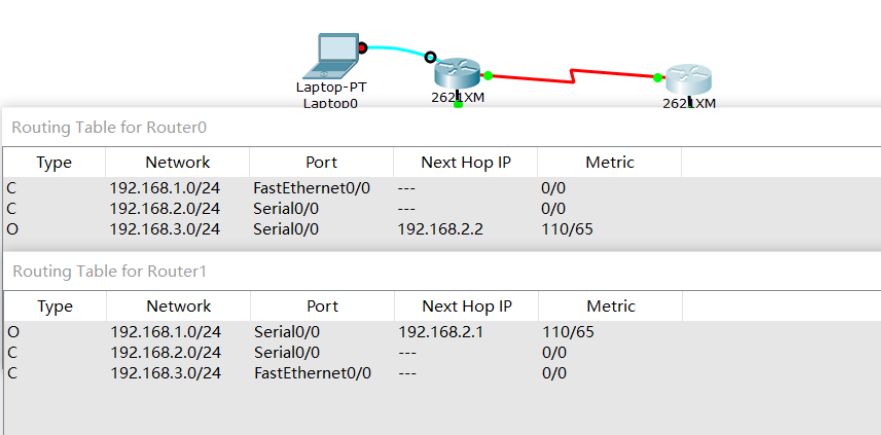
Reverse mask: our common subnet mask is the so-called forward mask, which is represented by continuous 1 and 0, where 1 indicates that accurate matching is required and 0 does not need to be, so as to obtain the network number. Similarly, the reverse mask is also represented by continuous 1 and 0, but on the contrary, where 0 means that exact matching is required, and 1 does not need to, so as to obtain the relevant IP, which is mainly used in OSPF. There is also a wildcard mask, which also adopts rules similar to the reverse mask. It is mainly used in the Access Control List ACL.
9, Port based network address translation PAT
sketch:
Network address translation( NAT,Network Address Translation)By each Internet Service provider ISP Widely used in their networks, including WiFi Network. The reason is simple, NAT Not only did it solve perfectly lP It can also effectively avoid attacks from outside the network, hide and protect computers inside the network. NAT There are generally three implementation methods: 1.Static conversion: Static NAT 2.Dynamic conversion: Dynamic NAT 3.Port multiplexing: OverLoad
explain:
Port multiplexing is the most used and flexible. OverLoad refers to not only changing the source IP address of data packets sent to the Internet, but also changing its source port, that is, Port Address Translation (PAT).
Using port multiplexing, all hosts in the internal network can share a legal external IP address to access the Internet, so as to save IP address resources to the greatest extent. At the same time, it can hide all hosts inside the network to effectively avoid attacks from the Internet. Therefore, port multiplexing is the most widely used method in the network.
We still use the topology of Chongqing Jiaotong University and Chongqing University for PAT experiment. We need to ensure that the routing of the two schools has been configured successfully. Whether static routing or dynamic routing is used, we give a complete configuration process as follows: set the routers of the two schools to use OSPF protocol, simulate Jiaotong University to use internal IP address (192.168.1.0 / 24), and simulate Chongqing University to use external IP address (8.8.8.0 / 24), The external IP address (202.202.240.0 / 24) is used between the two routers to implement PAT at the exit of Jiaotong University, that is, the WAN port.
The PC configuration data in the topology diagram is as follows:
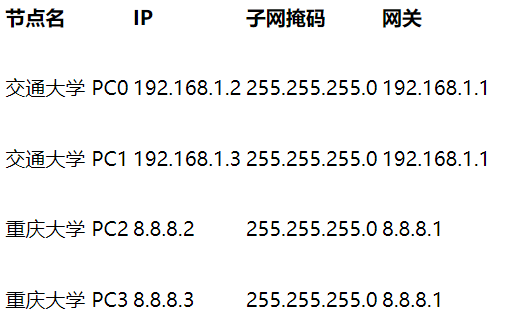
🗣 Please note that the network configuration of the two pcs of Chongqing University has changed. We simulate it as an external / public IP address!
The router interface configuration data in the topology diagram is as follows:

🗣 Please note that the network configuration of the two interfaces of Chongqing University router and the WAN port of Jiaotong University has changed, then configure OSPF routing, and finally implement PAT at the WAN port of Jiaotong University router!
The router interface configuration of Jiaotong University is as follows:
Ethernet port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int f0/0 / / enter the configuration Ethernet port mode Router(config-if)#ip address 192.168.1.1 255.255.255.0 / / configure IP address Router(config-if)#no shutdown / / activate the interface
WAN port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int s0/0 / / enter the WAN port configuration mode Router(config-if)#ip address 202.202.240.1 255.255.255.0 / / configure IP address Router(config-if)#clock rate 64000 / / it is the DCE terminal. Configure the clock frequency Router(config-if)#no shutdown / / activate the interface
The router interface configuration of Chongqing University is as follows:
Ethernet port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int f0/0 / / enter the configuration Ethernet port mode Router(config-if)#ip address 8.8.8.1 255.255.255.0 / / configure IP address Router(config-if)#no shutdown / / activate the interface
WAN port:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#int s0/0 / / enter the WAN port configuration mode Router(config-if)#ip address 202.202.240.2 255.255.255.0 / / configure IP address Router(config-if)#no shutdown / / activate the interface
OSPF routing configuration of Jiaotong University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#router ospf 1 / / enable OSPF routing protocol. The process number is 1 (you can ignore the concept of process number temporarily) Router(config-router)#Network 192.168.1.0 0.0.255 area 0 / / all hosts belonging to the 192.168.1.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF Router(config-router)#Network 202.202.240.0 0.0.255 area 0 / / all hosts belonging to the 202.202.240.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF
OSPF routing configuration of Chongqing University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#router ospf 1 / / enable OSPF routing protocol. The process number is 1 Router(config-router)#Network 202.202.240.0 0.0.255 area 0 / / all hosts belonging to the 202.202.240.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF Router(config-router)#Network 8.8.8.0 0.0.255 area 0 / / all hosts belonging to the 8.8.8.0/24 network in autonomous domain 0 (reverse mask) participate in OSPF
Packet loss configuration of Chongqing University Router:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#Access list 1 deny 192.168.1.0 0.0.255 / / create ACL 1, discard / do not forward all packets from the 192.168.1.0/24 network Router(config)#Access list 1 allow any / / add ACL 1 rules and forward packets from all other networks Router(config)#int s0/0 / / configure WAN port Router(config-if)#IP access group 1 in / / implement the rules in ACL 1 on the WAN port for incoming packets. In fact, if the WAN port receives packets from 192.168.1.0/24 IP, it will be discarded
Router PAT configuration of Jiaotong University:
Router>en // Enter privileged mode from normal mode Router#conf t / / enter global configuration mode Router(config)#Access list 1 permit 192.168.1.0 0.0.255 / / create ACL 1 to allow all packets from the 192.168.1.0/24 network Router(config)#ip nat inside source list 1 interface s0/0 overload / / the IP from the ACL will implement PAT on the WAN interface Router(config)#int f0/0 / / configure Ethernet port Router(config-if)#ip nat inside / / configure the Ethernet port as the internal port of PAT Router(config)#int s0/0 / / configure WAN port Router(config-if)#ip nat outside / / configure the WAN port as the external port of PAT
📬 Secret script
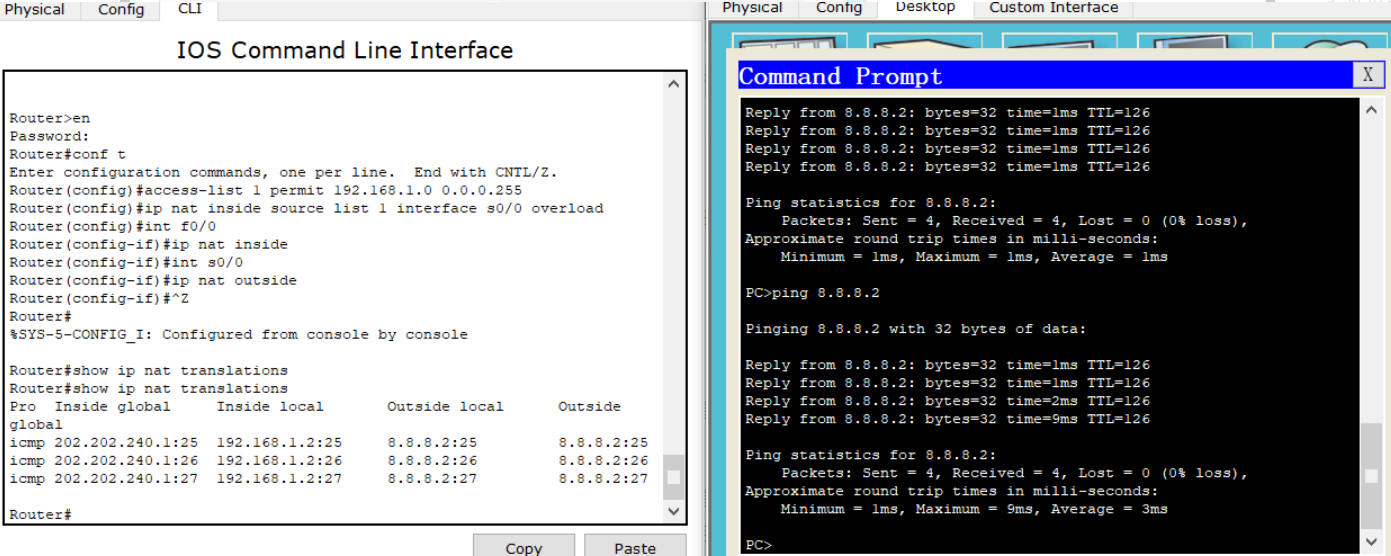
After the ping is successful, use show ip nat translations in the privileged configuration mode of Jiaotong University router to view the translation process!
record:
(1) ping Tong
(2) View translation
10, Virtual LAN VLAN
In the actual network (such as the network of our university), you can see that routers are generally located at the boundary of the network, and almost all of them are connected by switches.
As we analyzed earlier, the switch is connected to the same subnet! Obviously, broadcasting and even broadcasting storm in such a large-scale subnet will seriously affect the network performance and even paralysis.
In addition, we already know that in fact, the school is divided into N subnets, so these switches are not connected to a subnet! How to explain such contradictory things? We actually use VLAN enabled switches! The aforementioned switch is only an ordinary layer 2 switch (or we use it as a layer 2 switch).
VLAN(Virtual Local Area Network)Virtual local area network. By Division VLAN,We can divide a physical network into multiple logical network segments, that is, multiple subnets. divide VLAN It can eliminate the storm of network broadcasting, enhance the security of the network, and facilitate unified management.
Build a topology in CPT as shown in the following figure:
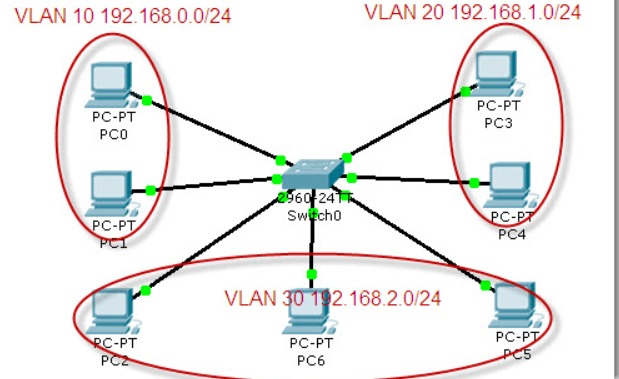
Cisco 2960 switch is a VLAN supporting switch with 24 100M and 2 1000M Ethernet ports. By default, all interfaces are in VLAN 1, so the connected computers are in the same VLAN and can communicate.
Next, the 24 100M interfaces of the switch are divided into three parts and divided into three different VLAN s. The id numbers are set to 10, 20 and 30 respectively, and aliases (computer, communication and electronic) are set to facilitate differentiation and management.
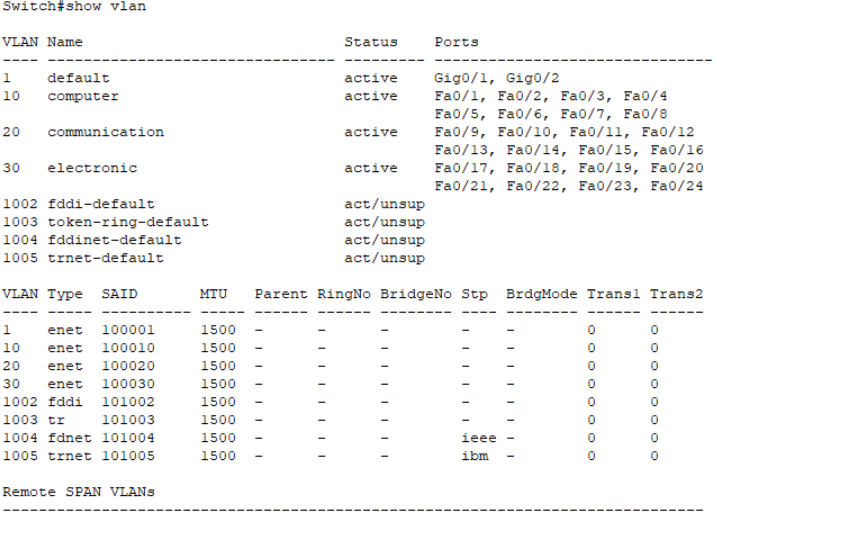
Switch VLAN configuration:
Switch>en Switch#conf t Switch(config)#vlan 10 / / create a VLAN with id 10 (by default, all interfaces of the switch belong to VLAN 1 and cannot be used) Switch(config-vlan)#name computer / / set the alias of VLAN Switch(config-vlan)#exit Switch(config)#int vlan 10 / / the VLAN is a subnet. Set its IP as the subnet gateway Switch(config-if)#ip address 192.168.0.1 255.255.255.0 Switch(config-if)#exit Switch(config)#vlan 20 / / create a VLAN with id 20 Switch(config-vlan)#name communication / / set alias Switch(config-vlan)#exit Switch(config)#int vlan 20 Switch(config-if)#ip addr 192.168.1.1 255.255.255.0 Switch(config-if)#exit Switch(config)#vlan 30 / / create a VLAN with id 20 Switch(config-vlan)#name electronic / / set alias Switch(config-vlan)#exit Switch(config)#int vlan 30 Switch(config-if)#ip add 192.168.2.1 255.255.255.0 Switch(config-if)#exit Switch(config)#int range f0/1-8 / / group configuration interface (1-8) Switch(config-if-range)#switchport mode access / / set to access mode Switch(config-if-range)#switchport access vlan 10 / / classified into VLAN 10 Switch(config-if-range)#exit Switch(config)#int range f0/9-16 Switch(config-if-range)#switchport mode access Switch(config-if-range)#switchport access vlan 20 Switch(config-if-range)#exit Switch(config)#int range f0/17-24 Switch(config-if-range)#switchport mode access Switch(config-if-range)#switchport access vlan 30 Switch(config-if-range)#^Z Switch#show vlan / / view the VLAN partition
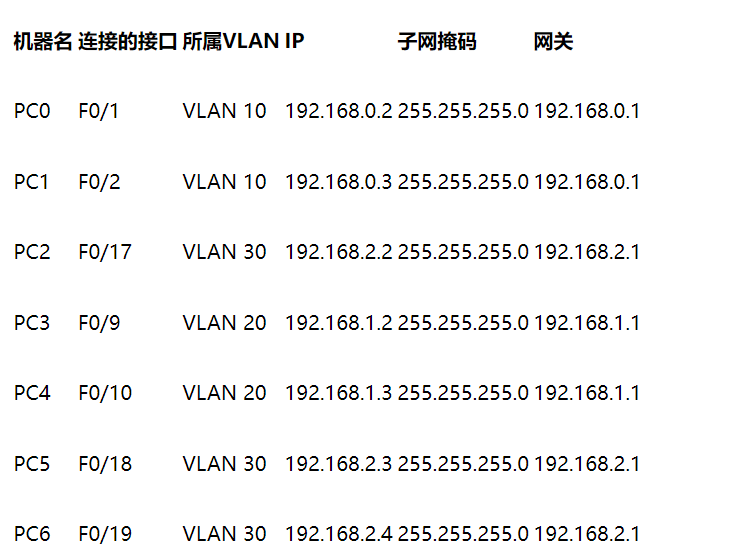
The network configuration of PC under each VLAN and the connected switch interface are as follows:
record:
(1)
(2)
Question:
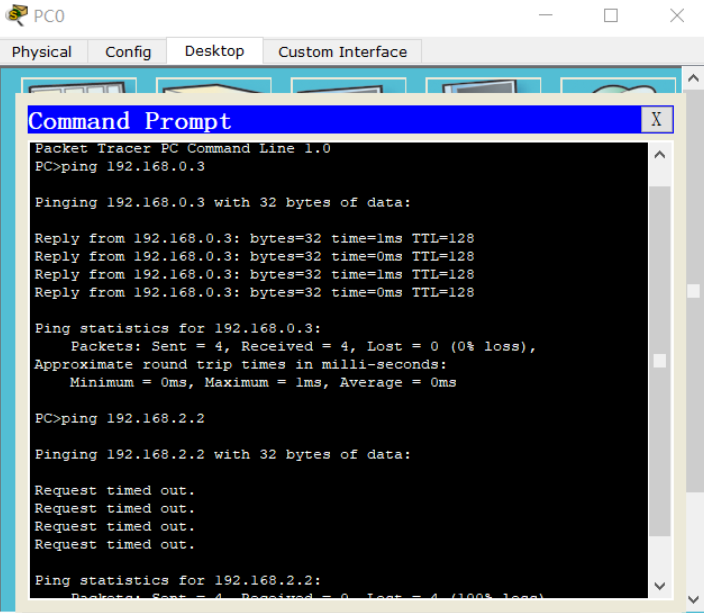
Why can't PC s in different VLAN s communicate? What does the gateway do here? Where is our gateway? How do I initiate a broadcast test?
Answer: VLAN has the function of dividing the network, so PC s in different VLANs cannot communicate with each other; VLAN is the protocol of data link layer, which is responsible for dividing the broadcast domain without considering IP; Gateway is used for protocol conversion. Gateway must be used for communication between different network segments. If a broadcast test needs to be initiated, a layer 3 switch is required
11, Virtual LAN management VTP
In the previous experiment, we planned and divided VLANs on the switch. However, in practical application, we will never allow arbitrary VLAN division on these switches that support VLAN, which will cause management confusion! VLAN division must be uniformly planned and managed, which requires VTP protocol.
VTP (VLAN Trunk Protocol) is the VLAN relay protocol. VTP maintains the uniformity of VLAN configuration through ISL frame or Cisco private DTP frame (refer to relevant materials). It is also known as virtual LAN trunk protocol. It is Cisco private protocol. VTP uniformly manages, adds, deletes and adjusts VLANs, and automatically broadcasts information to other switches in the network.
In addition, VTP reduces the configurations that may cause security problems. As long as the corresponding settings are made in the VTP Server, the VTP Client will automatically learn the VLAN information on the VTP Server.
To demonstrate VTP, rebuild the following topology:
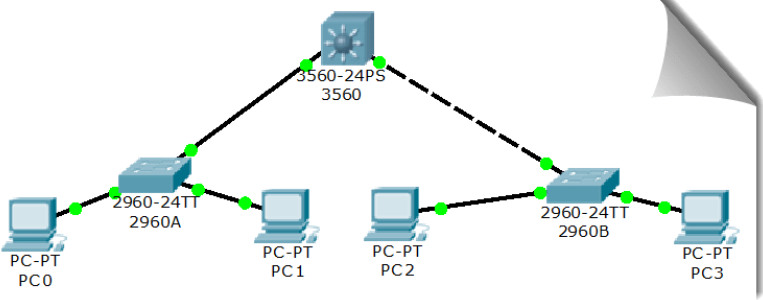
We will do the following work on the core switch 3560:
(1)Set to server pattern, VTP Domain is cqjtu (2)newly build VLAN 2,Network number 192.168.1.0/24,Gateway 192.168.1.1 (3)newly build VLAN 3,Network number 192.168.2.0/24,Gateway 192.168.2.1
3560 VTP Server configuration:
Switch>en Switch#conf t Switch(config)#hostname 3560 / / change the switch name (optional) 3560(config)#vtp domain cqjtu / / set the VTP domain name to cqjtu 3560(config)#vtp mode server / / set it to VTP server mode 3560(config)#VLAN 2 / / create a new VLAN 2 3560(config-vlan)#name computer / / set the alias of VLAN 2 (optional) 3560(config-vlan)#exit 3560(config)#VLAN 3 / / rebuild VLAN 3 3560(config-vlan)#name communication / / set the alias of VLAN 2 (optional) 3560(config-vlan)#exit 3560(config)#int vlan 2 / / configure interface VLAN 2, which will be the gateway of the subnet (on the left) 3560(config-if)#ip address 192.168.1.1 255.255.255.0 3560(config-if)#exit 3560(config)#int vlan 3 / / configure interface VLAN 3, which will be the gateway of the subnet (on the right) 3560(config-if)#ip address 192.168.2.1 255.255.255.0
We will do the following work on the left switch 2960A:
Join named cqjtu of VTP field Configure the Gigabit interface connected to the core switch 3560 g0/1 by trunk pattern Interface f0/1 Divided into VLAN 2 in Interface f0/2 Divided into VLAN 3 in
2960A (left) VTP Client configuration:
Switch>en Switch#conf t Switch(config)#hostname 2960A / / change the switch name (optional) 2960A(config)#vtp domain cqjtu / / join a VTP domain named cqjtu 2960A(config)#vtp mode client / / set the mode to VTP client 2960A(config)#int g0/1 / / configure the g0/1 Gigabit interface connected to the core switch 3560 2960A(config-if)#switchport mode trunk / / set the interface to trunk mode 2960A(config-if)#switchport trunk allowed vlan all / / allow trunking for all VLANs 2960A(config-if)#exit 2960A(config)#int f0/1 / / configure interface 1 2960A(config-if)#switchport mode access / / set the interface to normal access mode 2960A(config-if)#switchport access vlan 2 / / divide the interface into VLAN 2 2960A(config-if)#exit 2960A(config)#int f0/2 / / configure interface 2 2960A(config-if)#switchport mode access / / set the interface to normal access mode 2960A(config-if)#switchport access vlan 3 / / divide the interface into VLAN 3
We will do the same on the right switch 2960B:
1.Join named cqjtu VTP field 2.Configure the Gigabit interface connected to the core switch 3560 g0/1 by trunk pattern 3.Interface f0/1 Divided into VLAN 2 in 4.Interface f0/2 Divided into VLAN 3 in
2960B (right) VTP Client configuration:
Switch>en Switch#conf t Switch(config)#hostname 2960B / / change the switch name (optional) 2960B(config)#vtp domain cqjtu / / join a VTP domain named cqjtu 2960B(config)#vtp mode client / / set the mode to VTP client 2960B(config)#int g0/1 / / configure the g0/1 Gigabit interface connected to the core switch 3560 2960B(config-if)#switchport mode trunk / / set the interface to trunk mode 2960B(config-if)#switchport trunk allowed vlan all / / allow trunking for all VLANs 2960B(config-if)#exit 2960B(config)#int f0/1 / / configure interface 1 2960B(config-if)#switchport mode access / / set the interface to normal access mode 2960B(config-if)#switchport access vlan 2 / / divide the interface into VLAN 2 2960B(config-if)#exit 2960B(config)#int f0/2 / / configure interface 2 2960B(config-if)#switchport mode access / / set the interface to normal access mode 2960B(config-if)#switchport access vlan 3 / / divide the interface into VLAN 3
📬 Secret script
At this time, in the privileged mode of the three switches, you can use the show vtp status command to view the VTP status and the show vlan command to view the VLAN status
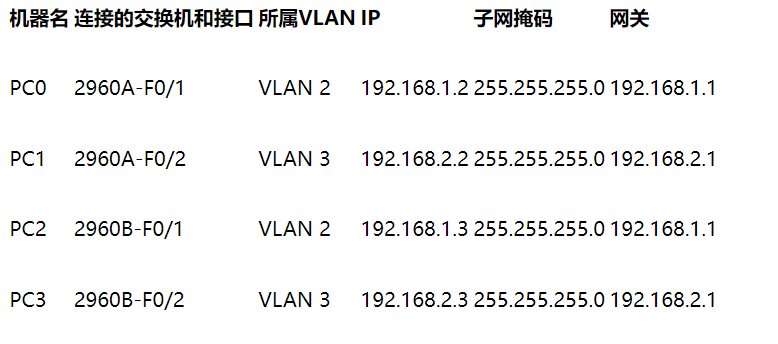
The switches, interfaces and network configurations connected to each PC are as follows:
record:
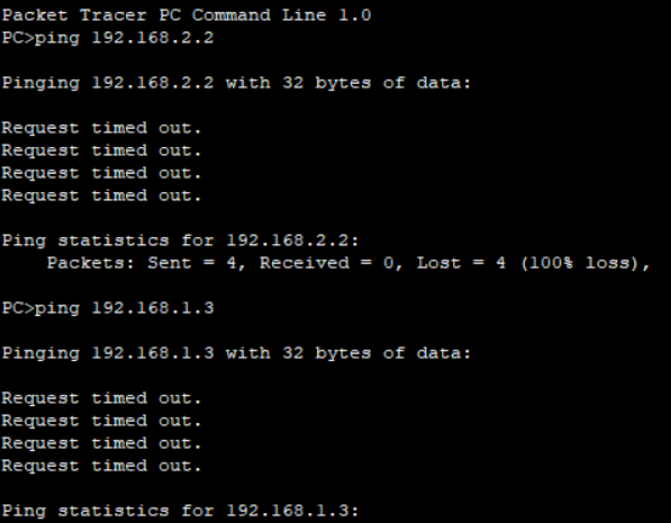
Question:
What is the result of pinging PC1 (192.168.2.2) with PC0 (192.168.1.2)? What is the result of using PC0 to Ping PC2? Think about why?
A: PC0 cannot Ping PC1, but PC0 can ping PC2, because PC0 and PC2 belong to the same vlan, while PC0 and PC1 do not belong to the same valn.
12, Communication between VLAN s
VTP only provides convenience for us to divide and manage VLANs. According to the above tests, we still can't communicate between VLANs.
Because by default, communication between VLANs is not allowed. At this time, we need the so-called single arm router to forward it between VLANs!
The core switch 3560 we use is a layer 3 switch, which can work in the network layer, also known as the routing switch, that is, it has the routing function and can carry out this forwarding operation.
3560 switch configuration:
3560>en 3560#conf t 3560(config)#int g0/1 / / configure the interface connecting the 2960A switch on the left 3560(config-if)#switchport trunk encapsulation dot1q / / encapsulating VLAN protocol 3560(config-if)#switchport mode trunk / / set to relay mode 3560(config-if)#switchport trunk allowed vlan all / / forward between all VLANs 3560(config-if)#exit 3560(config)#int g0/2 / / configure the interface connecting the 2960B switch on the right 3560(config-if)#switchport trunk encapsulation dot1q / / encapsulating VLAN protocol 3560(config-if)#switchport mode trunk / / set to relay mode 3560(config-if)#switchport trunk allowed vlan all / / forward between all VLANs 3560(config-if)#exit 3560(config)#ip routing / / enable routing forwarding
🗣 Defects of one arm routing
When the above test is performed using CPT simulation (PC0 ping PC1), you will clearly see that all ICMP packets are forwarded by 3560 switches, which is very easy to form a bottleneck.
12, Simple configuration of DHCP, DNS and Web server
Dynamic host configuration DHCP, domain name resolution DNS and Web services play a great role in daily applications. Let's build the following simple topology for practice.

In this topology, both servers and clients are connected to the same switch. For simplicity, the Server-PT serves as DHCP, DNS and Web servers at the same time. Each client does not need to be configured and will automatically obtain the network configuration.
Click the Server icon in the CPT topology diagram, set its static IP address to 19.89.6.4/24, and then select Service for the following related configurations:
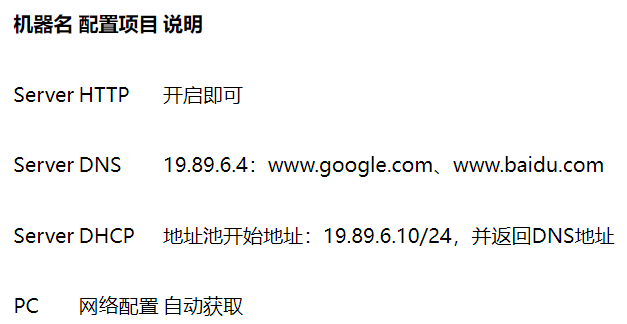
record:
(1)
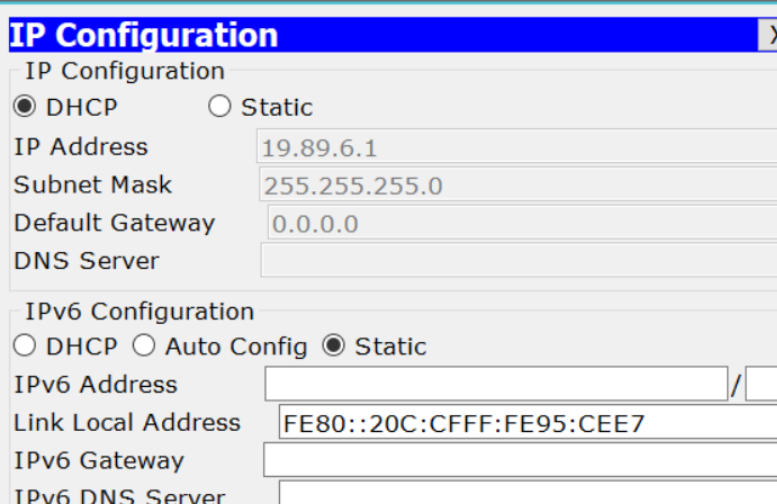
(2)
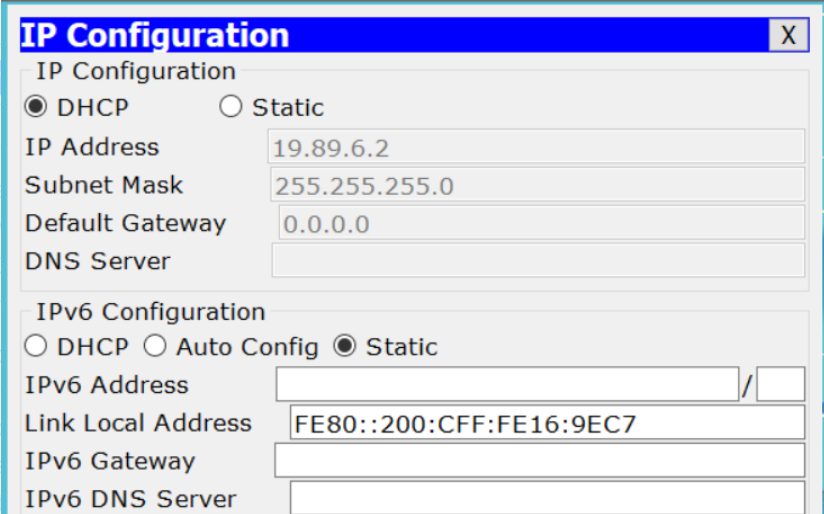
Question:
✎ give it a try
1. Check each PC first to see if the network configuration is available
2. Because we set the IP addresses of Google and Baidu to 19.89.6.4, i.e. server Pt, in the DNS server, if you open the browser of PC0, enter www.google Com or www.baidu.com COM, we should all see the default server Pt, the home page of the Web server (you can also edit it)
13, WLAN Preliminary Configuration
WLAN, namely WiFi, is also widely used in various scenarios.
Let's practice the related configuration by building a home WLAN with the following topology:
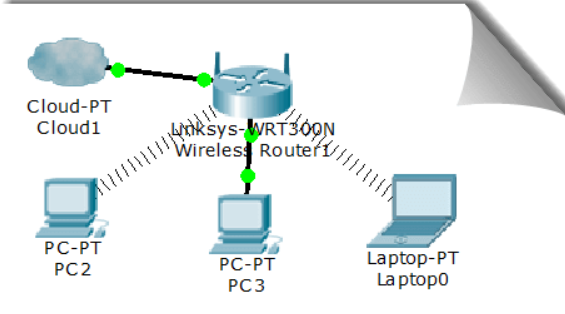
📬 Secret script
Notebook and desktop computers only have wired network cards by default. Please shut down first, delete the wired network card in the shutdown state, add a wireless network card, and then turn on.
Generally, we need to configure the basic network configuration of the wireless router (IP, mask, gateway, DNS, etc., which are mostly obtained automatically in reality), then configure the wireless access part of the wireless router, such as connection password and encryption type, and turn on the DHCP function. Please refer to relevant materials for configuration.
14, Summary of this experiment
Learning is a very difficult thing. Stick to it.