I've been looking at Cisco's SD-WAN introduction for a while, which is based on film. To find an environment for specific experiments, it seems to be very difficult to view many materials based on official website documents. We can only explore this to do a "simple" experiment, and follow-up experiments are slowly studied. This paper makes a record.
Experimental purpose
The loopback 1.1.1.1 and 2.2.2.2 of two routes of Site1 and Site2 can communicate normally.
In fact, such a "simple" little thing takes some trouble...
This experiment will be divided into four parts
1. Initialization of vManage, vBond, vSmart, vEdge and other devices
2. Certificate processing of vManage, vBond, vSmart and vEdge
3. vManage adds vBond, vSmart, and vEdge devices
4. Routing between two sites
Note: the environment and documents required for the experiment and how to build them are not explained here
Experimental topology
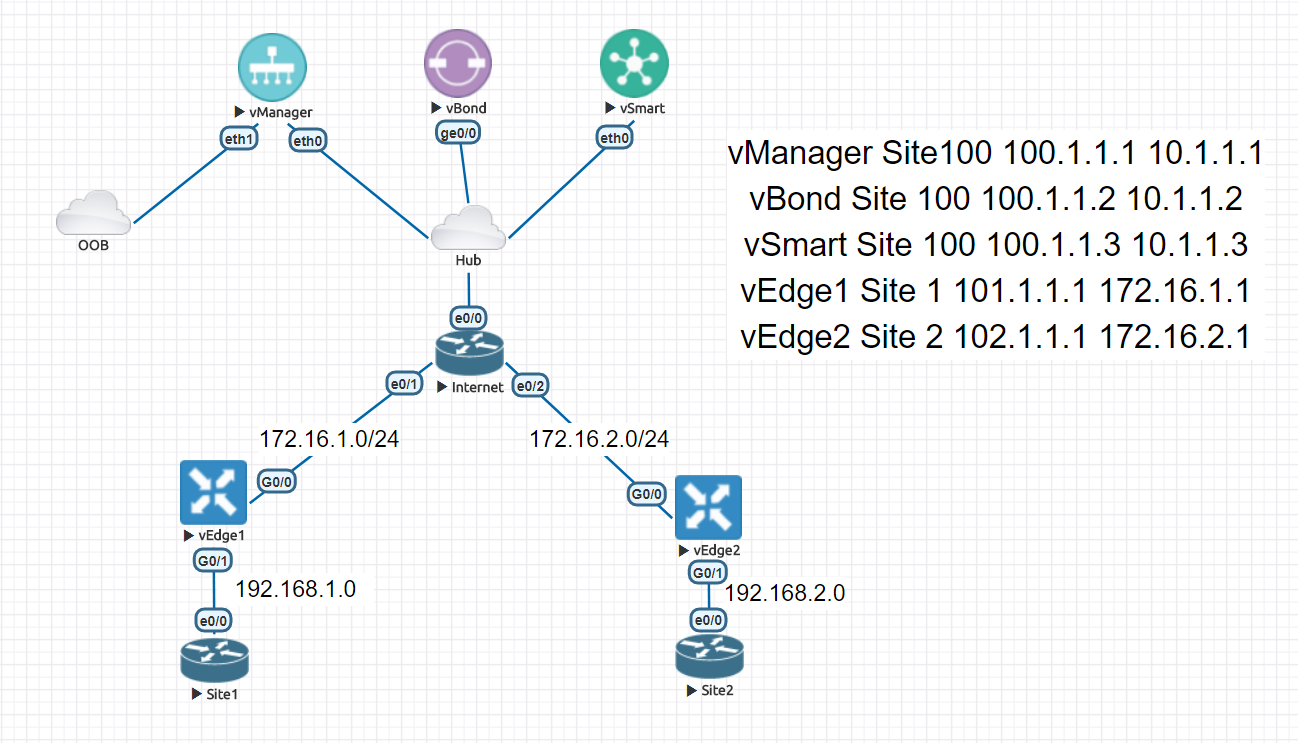
The interconnection of devices is shown in the figure above. vManage is connected with an out of band for remote use of Web management.
Equipment address and relevant information
| equipment | Site ID | System-IP | Interface IP | Edition |
|---|---|---|---|---|
| vManage | 100 | 100.1.1.1 | 10.1.1.1 | 16.3.2->17.2.0 |
| vBond | 100 | 100.1.1.2 | 10.1.1.2 | 16.3.2->17.2.0 |
| vSmart | 100 | 100.1.1.3 | 10.1.1.3 | 16.3.2->17.2.0 |
| vEdge1 | 1 | 101.1.1.1 | 172.16.1.1 | 17.2.0 |
| Site1 | - | 1.1.1.1 | 192.168.1.1 | - |
| vEdge2 | 2 | 102.1.1.1 | 172.16.2.1 | 17.2.0 |
| Site2 | - | 2.2.2 | 192.168.2.1 | - |
Important: it needs to be explained that vManage, vBond and vSmart are first used in 16.3.2 and then upgraded to 17.2.0. Because vManage to 17.X.X and later versions need SmartAccount account account to generate the authentication file of vManage on Cisco official website to import vManage to add vManage, while the version before 17.X.X can manually create and edit the CSV file to enter vManage. The reason that vdge uses 17.X.X is that previous versions cannot use their own generated certificates for validation.
So here is the certificate of all devices installed first and then the authentication file of the vEdge is added. After the vManage is upgraded to 17.2.0, add the vEdge device. However, once the device is upgraded to 17.2.0, it will not be able to manually edit and add the vEdge authentication file.
Initialization of vManage, vBond, vSmart, vEdge and other devices
vManage initial configuration
system host-name vmanage system-ip 100.1.1.1 site-id 100 organization-name iteachs.com vbond 10.1.1.2 vpn 0 interface eth0 ip address 10.1.1.1/24 no tunnel-interface no shutdown ! ip route 0.0.0.0/0 10.1.1.254 ! vpn 512 interface eth1 ip address 192.168.188.61/24 no shutdown ! ip route 0.0.0.0/0 192.168.188.254 ! commit and-quit
Initial configuration of vBond
system host-name vbond system-ip 100.1.1.2 organization-name iteachs.com vbond 10.1.1.2 local vbond-only vpn 0 interface ge0/0 ip address 10.1.1.2/24 no tunnel-interface no shutdown ! ip route 0.0.0.0/0 10.1.1.254 ! commit and-quit
vSmart initial configuration
system host-name vsmart system-ip 100.1.1.3 site-id 100 organization-name iteachs.com vbond 10.1.1.2 ! vpn 0 interface eth0 ip address 10.1.1.3/24 no tunnel-interface no shutdown ! ip route 0.0.0.0/0 10.1.1.254 ! commit and-quit
Initial configuration of vEdge1
system host-name vedge1 system-ip 101.1.1.1 site-id 1 organization-name iteachs.com vbond 10.1.1.2 ! vpn 0 interface ge0/0 ip address 172.16.1.1/24 no tunnel-interface no shutdown ! ip route 0.0.0.0/0 172.16.1.254 ! vpn 10 interface ge0/1 ip address 192.168.1.254/24 no shutdown ! ip route 0.0.0.0/0 vpn 0 ! ! commit and-quit
Site1 initial configuration
version 15.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Site1 ! enable secret 4 X4ZqtPJ///KxuEWxHSsJrv3beQVnz2ise/xj8fF6eFU ! aaa new-model ! no ip domain lookup ip cef ! username admin privilege 15 secret 4 X4ZqtPJ///KxuEWxHSsJrv3beQVnz2ise/xj8fF6eFU ! interface Loopback0 ip address 1.1.1.1 255.255.255.255 ip ospf network point-to-point ip ospf 1 area 0 ! interface Ethernet0/0 ip address 192.168.1.1 255.255.255.0 ip ospf network point-to-point ip ospf 1 area 0 ! router ospf 1 router-id 1.1.1.1 passive-interface default no passive-interface Ethernet0/0 ! end
Initial configuration of vEdge2
system host-name vedge2 system-ip 102.1.1.1 site-id 2 organization-name iteachs.com vbond 10.1.1.2 ! vpn 0 interface ge0/0 ip address 172.16.2.1/24 no tunnel-interface no shutdown ! ip route 0.0.0.0/0 172.16.2.254 ! vpn 10 interface ge0/1 ip address 192.168.2.254/24 no shutdown ! ip route 0.0.0.0/0 vpn 0 ! ! commit and-quit
Site2 initial configuration
version 15.2 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Site2 ! enable secret 4 X4ZqtPJ///KxuEWxHSsJrv3beQVnz2ise/xj8fF6eFU ! aaa new-model ! no ip domain lookup ip cef ! username admin privilege 15 secret 4 X4ZqtPJ///KxuEWxHSsJrv3beQVnz2ise/xj8fF6eFU ! interface Loopback0 ip address 2.2.2.2 255.255.255.255 ip ospf network point-to-point ip ospf 1 area 0 ! interface Ethernet0/0 ip address 192.168.2.1 255.255.255.0 ip ospf network point-to-point ip ospf 1 area 0 ! router ospf 1 router-id 2.2.2.2 passive-interface default no passive-interface Ethernet0/0 ! end
Internet Configuration
version 15.2 service config service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname Internet ! enable secret 4 X4ZqtPJ///KxuEWxHSsJrv3beQVnz2ise/xj8fF6eFU ! aaa new-model ! no ip domain lookup ip cef ! username admin privilege 15 secret 4 X4ZqtPJ///KxuEWxHSsJrv3beQVnz2ise/xj8fF6eFU ! interface Loopback100 ip address 100.100.100.100 255.255.255.255 !#Simulated public network access test interface Ethernet0/0 ip address 10.1.1.254 255.255.255.0 !#Connected to management terminal equipment interface Ethernet0/1 ip address 172.16.1.254 255.255.255.0 !#Connected to Site1 terminal equipment interface Ethernet0/2 ip address 172.16.2.254 255.255.255.0 !#Connect to Site2 terminal equipment no ip http server no ip http secure-server ! no cdp run ! end
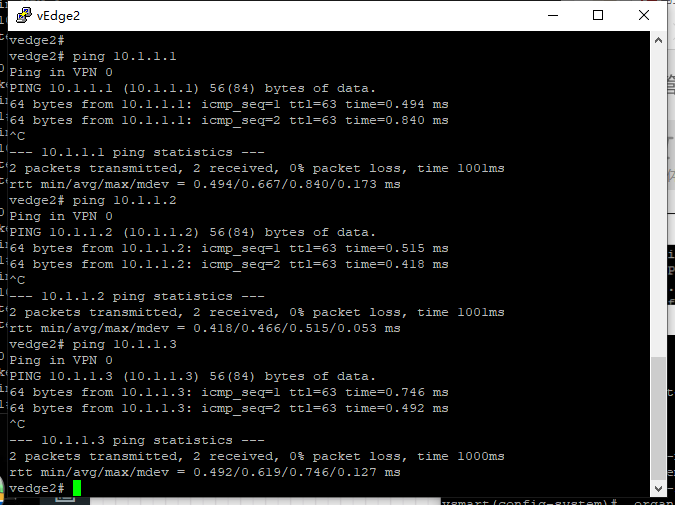
After the above configuration is completed, the direct connections between devices can be interconnected, and the vdge, vManage, vBond, and vSmart can be interconnected. However, OSPF has no neighbors, and the Site cannot be interconnected internally.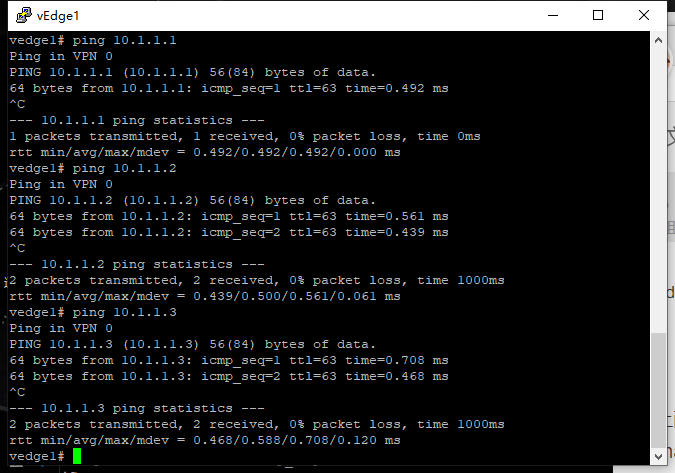
Certificate processing of vManage, vBond, vSmart and vEdge
Certificate servers are required to process certificates for these devices. You can use Cisco IOS, windows server, or other certificate servers. For the sake of simple experiment, I directly use OpenManage's openssl to sign and issue certificates. The production environment cannot be used.
Generate root certificate
Generate a key first, length 2048
vshell openssl genrsa -out ROOTCA.key 2048
Generate root certificate
openssl req -x509 -new -nodes -key ROOTCA.key -sha256 -days 1024 \
-subj "/C=CN/ST=Nanjing/L=Jiangsu/O=iteachs.com/CN=ca.local" \
-out ROOTCA.pem
The following is the output
vmanage# vshell vmanage:~$ vmanage:~$ openssl genrsa -out ROOTCA.key 2048 Generating RSA private key, 2048 bit long modulus .............+++ ..................................+++ e is 65537 (0x10001) vmanage:~$ openssl req -x509 -new -nodes -key ROOTCA.key -sha256 -days 1024 \ > -subj "/C=CN/ST=Nanjing/L=Jiangsu/O=iteachs.com/CN=ca.local" \ > -out ROOTCA.pem vmanage:~$ vmanage:~$ dir ROOTCA.key ROOTCA.pem archive_id_rsa.pub vmanage:~$
View vManage default root and personal certificates
vmanage# show certificate root-ca-cert
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
6e:cc:7a:a5:a7:03:20:09:b8:ce:bc:f4:e9:52:d4:91
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=(c) 2006 VeriSign, Inc. - For authorized use only, CN=VeriSign Class 3 Public Primary Certification Authority - G5
Validity
Not Before: Feb 8 00:00:00 2010 GMT
Not After : Feb 7 23:59:59 2020 GMT
Subject: C=US, O=VeriSign, Inc., OU=VeriSign Trust Network, OU=Terms of use at https://www.verisign.com/rpa (c)10, CN=VeriSign Class 3 Secure Server CA - G3
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b1:87:84:1f:c2:0c:45:f5:bc:ab:25:97:a7:ad:
a2:3e:9c:ba:f6:c1:39:b8:8b:ca:c2:ac:56:c6:e5:
bb:65:8e:44:4f:4d:ce:6f:ed:09:4a:d4:af:4e:10:
9c:68:8b:2e:95:7b:89:9b:13:ca:e2:34:34:c1:f3:
5b:f3:49:7b:62:83:48:81:74:d1:88:78:6c:02:53:
f9:bc:7f:43:26:57:58:33:83:3b:33:0a:17:b0:d0:
4e:91:24:ad:86:7d:64:12:dc:74:4a:34:a1:1d:0a:
ea:96:1d:0b:15:fc:a3:4b:3b:ce:63:88:d0:f8:2d:
0c:94:86:10:ca:b6:9a:3d:ca:eb:37:9c:00:48:35:
86:29:50:78:e8:45:63:cd:19:41:4f:f5:95:ec:7b:
98:d4:c4:71:b3:50:be:28:b3:8f:a0:b9:53:9c:f5:
ca:2c:23:a9:fd:14:06:e8:18:b4:9a:e8:3c:6e:81:
fd:e4:cd:35:36:b3:51:d3:69:ec:12:ba:56:6e:6f:
9b:57:c5:8b:14:e7:0e:c7:9c:ed:4a:54:6a:c9:4d:
c5:bf:11:b1:ae:1c:67:81:cb:44:55:33:99:7f:24:
9b:3f:53:45:7f:86:1a:f3:3c:fa:6d:7f:81:f5:b8:
4a:d3:f5:85:37:1c:b5:a6:d0:09:e4:18:7b:38:4e:
fa:0f
Exponent: 65537 (0x10001)
X509v3 extensions:
Authority Information Access:
OCSP - URI:http://ocsp.verisign.com
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Certificate Policies:
Policy: 2.16.840.1.113733.1.7.23.3
CPS: https://www.verisign.com/cps
User Notice:
Explicit Text: https://www.verisign.com/rpa
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.verisign.com/pca3-g5.crl
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
1.3.6.1.5.5.7.1.12:
0_.].[0Y0W0U..image/gif0!0.0...+..............k...j.H.,{..0%.#http://logo.verisign.com/vslogo.gif
X509v3 Subject Alternative Name:
DirName:/CN=VeriSignMPKI-2-6
X509v3 Subject Key Identifier:
0D:44:5C:16:53:44:C1:82:7E:1D:20:AB:25:F4:01:63:D8:BE:79:A5
X509v3 Authority Key Identifier:
keyid:7F:D3:65:A7:C2:DD:EC:BB:F0:30:09:F3:43:39:FA:02:AF:33:31:33
Signature Algorithm: sha1WithRSAEncryption
0c:83:24:ef:dd:c3:0c:d9:58:9c:fe:36:b6:eb:8a:80:4b:d1:
a3:f7:9d:f3:cc:53:ef:82:9e:a3:a1:e6:97:c1:58:9d:75:6c:
e0:1d:1b:4c:fa:d1:c1:2d:05:c0:ea:6e:b2:22:70:55:d9:20:
33:40:33:07:c2:65:83:fa:8f:43:37:9b:ea:0e:9a:6c:70:ee:
f6:9c:80:3b:d9:37:f4:7a:6d:ec:d0:18:7d:49:4a:ca:99:c7:
19:28:a2:be:d8:77:24:f7:85:26:86:6d:87:05:40:41:67:d1:
27:3a:ed:dc:48:1d:22:cd:0b:0b:8b:bc:f4:b1:7b:fd:b4:99:
a8:e9:76:2a:e1:1a:2d:87:6e:74:d3:88:dd:1e:22:c6:df:16:
b6:2b:82:14:0a:94:5c:f2:50:ec:af:ce:ff:62:37:0d:ad:65:
d3:06:41:53:ed:02:14:c8:b5:58:28:a1:ac:e0:5b:ec:b3:7f:
95:4a:fb:03:c8:ad:26:db:e6:66:78:12:4a:d9:9f:42:fb:e1:
98:e6:42:83:9b:8f:8f:67:24:e8:61:19:b5:dd:cd:b5:0b:26:
05:8e:c3:6e:c4:c8:75:b8:46:cf:e2:18:06:5e:a9:ae:a8:81:
9a:47:16:de:0c:28:6c:25:27:b9:de:b7:84:58:c6:1f:38:1e:
a4:c4:cb:66
vmanage#
vmanage# show certificate installed
vmanage#
You can see that there is a root certificate but no personal certificate by default. We will delete the default root certificate of all devices and use our own generated root certificate before applying for personal certificate.
Remove the old root certificate and install a new root certificate
vManage device operations
vmanage# request root-cert-chain uninstall Successfully uninstalled the root certificate chain vmanage# vmanage# request root-cert-chain install home/admin/ROOTCA.pem Uploading root-ca-cert-chain via VPN 0 Copying ... /home/admin/ROOTCA.pem via VPN 0 Successfully installed the root certificate chain vmanage#
vBond, vSmart, vEdge1, vEdge2 device operation
vedge2# request root-cert-chain uninstall CMD_MAAPI is true [mtid = 0] CMD_MAAPI is true [mtid = 407] CMD_MAAPI is true [mtid = 407] CMD_MAAPI is true [mtid = 0] Successfully uninstalled the root certificate chain vedge2# vedge2# vedge2# request root-cert-chain install scp://admin@10.1.1.1:/home/admin/ROOTCA.pem Uploading root-ca-cert-chain via VPN 0 Copying ... admin@10.1.1.1:/home/admin/ROOTCA.pem via VPN 0 Warning: Permanently added '10.1.1.1' (ECDSA) to the list of known hosts. viptela 16.3.2 admin@10.1.1.1's password: ROOTCA.pem 100% 1285 1.7MB/s 00:00 CMD_MAAPI is true [mtid = 0] CMD_MAAPI is true [mtid = 411] CMD_MAAPI is true [mtid = 411] CMD_MAAPI is true [mtid = 0] CMD_MAAPI is true [mtid = 0] CMD_MAAPI is true [mtid = 415] CMD_MAAPI is true [mtid = 415] CMD_MAAPI is true [mtid = 0] Successfully installed the root certificate chain vedge2#
View root certificate after operation
vmanage# show certificate root-ca-cert
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
88:db:55:e2:55:58:83:e9
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=Nanjing, L=Jiangsu, O=iteachs.com, CN=ca.local
Validity
Not Before: Mar 5 08:38:12 2020 GMT
Not After : Dec 24 08:38:12 2022 GMT
Subject: C=CN, ST=Nanjing, L=Jiangsu, O=iteachs.com, CN=ca.local
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d6:ae:7f:bd:a3:6b:86:a0:bb:15:a0:8d:da:37:
59:8a:d3:d3:43:f5:50:52:82:fd:63:36:ba:e9:32:
69:51:e5:5e:58:87:ae:0f:11:1b:65:56:8a:85:a1:
e9:02:39:4d:e7:bd:8d:e9:45:e3:20:98:66:57:ab:
da:7d:81:23:a4:07:f3:b5:6a:a4:69:0a:57:d3:8b:
50:fb:d7:9c:2b:2c:ba:be:18:62:59:6f:f6:57:55:
84:1a:69:2d:39:4f:7e:55:9b:5c:9a:68:67:61:03:
89:ca:26:76:14:8f:5d:72:af:3f:2b:9b:03:c1:b0:
59:72:cb:8d:2f:76:b7:d8:9f:fa:bd:38:ed:5b:db:
63:f5:b3:0a:49:db:6a:e9:eb:57:ba:7c:99:60:09:
e5:d9:78:e5:a2:0a:9d:9a:c3:32:14:c5:da:65:73:
11:4a:81:89:b6:3f:02:32:72:db:7d:a7:1b:b1:f1:
ad:27:94:5b:ea:fe:f4:74:60:04:e4:13:2b:54:9e:
c9:29:67:b4:c5:e1:cd:7d:69:70:79:27:6d:e9:8d:
34:16:f1:39:0b:2c:51:14:04:2b:a7:97:9f:ed:04:
2a:05:47:d1:80:7a:91:5f:48:f7:91:fa:12:b0:e9:
9f:37:d2:0a:a3:96:fb:33:54:bb:03:44:62:94:34:
f9:37
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
A7:B6:B0:03:68:EA:9C:94:6D:7C:98:D7:23:7D:60:98:51:F2:35:E9
X509v3 Authority Key Identifier:
keyid:A7:B6:B0:03:68:EA:9C:94:6D:7C:98:D7:23:7D:60:98:51:F2:35:E9
X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
b9:fa:f3:b8:54:5a:5d:c0:70:b7:40:64:a3:76:a8:bb:32:9f:
fe:a1:e4:4d:ba:cc:5d:dc:32:24:38:ff:01:3b:52:a2:aa:07:
87:84:d8:83:14:1f:22:72:aa:49:1c:10:93:74:a7:24:45:60:
9b:0a:a7:af:a7:68:a2:70:28:f5:d2:ec:8b:67:83:68:de:67:
a0:da:0a:1d:b4:33:b2:cd:39:36:31:f8:20:04:ac:1a:1f:be:
20:50:f4:3d:bf:23:2c:83:9d:8d:49:a2:88:59:e7:e1:5a:f3:
d9:9a:20:13:f2:46:cc:2b:a0:6d:ac:2e:b0:a4:a5:0c:41:e3:
06:51:d7:ad:26:6c:68:c0:8c:e1:f3:ab:8b:5a:5b:ff:b4:45:
29:d4:b6:dc:dc:b4:f5:62:51:bb:77:19:fe:4e:12:f5:d3:10:
c9:2c:9b:d2:91:a7:61:bf:e3:3d:2d:f6:73:b5:fc:a4:b6:92:
9a:07:1f:19:98:67:34:df:2f:1b:83:27:91:a9:f6:e5:20:a4:
c9:6b:a9:a5:fe:b3:84:77:2d:ea:f8:f6:99:32:03:40:ac:b9:
76:0c:08:86:f9:38:b1:8b:70:bb:66:75:88:72:c9:4e:44:34:
05:17:ea:69:c5:c8:d3:9b:33:5f:77:27:3e:7b:d7:5a:83:66:
3d:43:c3:4f
vmanage#
Generate certificate request for vManage, vBond, vSmart, and vEdge
vManage generates certificate request
vmanage# request csr upload /home/admin/vmanage.csr Uploading CSR via VPN 0 Enter organization name : iteachs.com Re-enter organization name : iteachs.com Generating private/public pair and CSR for this vmanage device Generating CSR for this vmanage device ........[DONE] Copying ... /home/admin/vmanage.csr via VPN 0 CSR upload successful vmanage#
Note that the organization of this input is very important. It must be the same as in the configuration.
Other equipment generate certificate request
Don't demonstrate one by one, post the command.
vBond: request csr upload scp://admin@10.1.1.1:/home/admin/vbond.csr vSmart: request csr upload scp://admin@10.1.1.1:/home/admin/vsmart.csr vEdge1: request csr upload scp://admin@10.1.1.1:/home/admin/vedge1.csr vEdge2: request csr upload scp://admin@10.1.1.1:/home/admin/vedge2.csr
Issue certificates for vManage, vBond, vSmart, vEdge
vmanage# vmanage# vmanage# vshell vmanage:~$ vmanage:~$ openssl x509 -req -in vmanage.csr \ > -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \ > -out vmanage.crt -days 500 -sha256 Signature ok subject=/C=US/ST=California/L=San Jose/OU=iteachs.com/O=vIPtela Inc/CN=vmanage_1d83a485-e824-4836-ab82-00db7bea4c1c_0.viptela.com/emailAddress=support@viptela.com Getting CA Private Key vmanage:~$ vmanage:~$ openssl x509 -req -in vbond.csr \ > -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \ > -out vbond.crt -days 500 -sha256 Signature ok subject=/C=US/ST=California/L=San Jose/OU=iteachs.com/O=vIPtela Inc/CN=vbond_d797a9bd-eef2-40a2-9bf5-953b6525947c_0.viptela.com/emailAddress=support@viptela.com Getting CA Private Key vmanage:~$ vmanage:~$ openssl x509 -req -in vsmart.csr \ > -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \ > -out vsmart.crt -days 500 -sha256 Signature ok subject=/C=US/ST=California/L=San Jose/OU=iteachs.com/O=vIPtela Inc/CN=vsmart_1cda07a5-81a4-486b-8cef-426dbd285d20_0.viptela.com/emailAddress=support@viptela.com Getting CA Private Key vmanage:~$ vmanage:~$ vmanage:~$ openssl x509 -req -in vedge1.csr \ > -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \ > -out vedge1.crt -days 500 -sha256 Signature ok subject=/C=US/ST=California/L=San Jose/OU=iteachs.com/O=vIPtela Inc/CN=vedge-49918191-566f-4ef1-875c-c8557c317275-0.viptela.com/emailAddress=support@viptela.com Getting CA Private Key vmanage:~$ vmanage:~$ vmanage:~$ openssl x509 -req -in vedge2.csr \ > -CA ROOTCA.pem -CAkey ROOTCA.key -CAcreateserial \ > -out vedge2.crt -days 500 -sha256 Signature ok subject=/C=US/ST=California/L=San Jose/OU=iteachs.com/O=vIPtela Inc/CN=vedge-4ea4eb5d-dfba-4e33-8ea8-da22db5446a2-0.viptela.com/emailAddress=support@viptela.com Getting CA Private Key vmanage:~$ vmanage:~$ dir ROOTCA.key ROOTCA.srl vbond.crt vedge1.crt vedge2.crt vmanage.crt vsmart.crt ROOTCA.pem archive_id_rsa.pub vbond.csr vedge1.csr vedge2.csr vmanage.csr vsmart.csr vmanage:~$ vmanage:~$
Install certificates for vManage, vBond, vSmart, and vEdge
vManage installation certificate
vmanage# request certificate install home/admin/vmanage.crt Installing certificate via VPN 0 Copying ... /home/admin/vmanage.crt via VPN 0 Successfully installed the certificate
vBond, vSmart, vEdge installation certificate
vBond: request certificate install scp://admin@10.1.1.1:/home/admin/vbond.crt vSmart: request certificate install scp://admin@10.1.1.1:/home/admin/vsmart.crt vEdge1: request certificate install scp://admin@10.1.1.1:/home/admin/vedge1.crt vEdge2: request certificate install scp://admin@10.1.1.1:/home/admin/vedge2.crt
Process is not posted one by one
View personal certificates installed under
vmanage# show certificate installed
Server certificate
------------------
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
f2:f9:b9:94:7b:e8:20:84
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=CN, ST=Nanjing, L=Jiangsu, O=iteachs.com, CN=ca.local
Validity
Not Before: Mar 5 08:59:05 2020 GMT
Not After : Jul 18 08:59:05 2021 GMT
Subject: C=US, ST=California, L=San Jose, OU=iteachs.com, O=vIPtela Inc, CN=vmanage_1d83a485-e824-4836-ab82-00db7bea4c1c_0.viptela.com/emailAddress=support@viptela.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d1:30:e0:3a:02:a9:a3:26:72:0f:1c:04:3c:63:
9d:b5:d5:7f:13:49:22:9e:82:2f:3d:60:81:c2:0c:
ae:88:7a:8f:c0:15:0b:0f:fd:2b:b0:90:e1:a3:b8:
92:b6:12:dc:1f:88:78:ca:0f:6f:a9:95:26:6d:dd:
08:6f:10:f9:48:10:8a:53:12:c8:39:d2:59:7a:05:
ff:68:20:bf:8f:68:96:8d:6e:99:11:6f:11:64:8c:
1b:53:e6:a6:5c:e0:aa:fc:00:1f:0d:78:06:7d:84:
29:b2:1a:f6:d7:33:46:f2:32:21:ea:38:8a:08:05:
c4:f3:5e:58:9d:f7:db:03:05:7e:c7:44:6b:cc:38:
74:25:c7:f0:03:d6:b1:51:20:4e:0f:66:cb:81:6f:
5d:31:50:02:87:26:b5:c7:13:fe:44:52:6e:2e:44:
54:f6:32:4d:00:4d:6a:c3:c4:7e:e0:93:80:48:ab:
23:e4:2c:be:3f:73:b6:c0:a8:92:d6:44:8c:91:57:
35:c1:6f:ba:f4:8e:6d:d4:34:11:a4:c5:f7:f3:bf:
c1:c6:ee:83:95:41:f5:94:66:a5:99:6d:71:76:00:
44:8e:41:63:c3:9e:27:ae:cd:5e:44:07:66:b1:c5:
3b:6b:17:22:10:70:a6:f3:f1:10:f8:09:5f:cd:92:
eb:e3
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
6d:9d:a3:e7:1c:bd:45:a8:fc:0b:e1:10:27:23:b7:06:7f:75:
90:4f:aa:ce:9d:22:e1:43:98:c3:3c:66:a2:fc:94:2f:4c:b2:
9f:7a:f0:5d:6d:ee:5e:4c:11:df:39:e4:b7:1e:75:21:44:6d:
43:f5:aa:7d:51:bc:9d:87:5c:2d:79:4b:96:b3:f3:a1:f1:27:
16:64:1b:dd:87:cd:b7:b9:f9:9a:78:e8:9e:4f:6a:8e:b7:fe:
73:e3:10:6d:e6:f4:b8:a6:77:c8:59:30:cf:65:74:62:96:18:
8b:9e:01:20:64:74:79:25:b6:33:47:46:43:b1:c6:55:5c:f7:
ba:80:52:3c:9e:df:82:e8:3a:c9:50:f9:ad:2e:1f:48:8b:ef:
e8:88:4a:1c:ff:97:e0:00:a1:9b:2e:5c:96:3b:f9:e9:e3:da:
7e:d3:5f:4f:8b:d5:c8:10:c3:d0:d5:06:f7:51:19:70:e8:25:
3b:31:b5:88:4d:1b:ac:b6:94:16:a7:05:22:16:b8:cf:1f:36:
8d:d7:2d:0d:35:9e:2f:1b:7b:d4:8b:a1:f0:61:7d:30:03:2f:
a4:00:d6:68:9d:53:d2:82:01:39:27:b9:10:5a:28:27:ea:8f:
e6:ae:51:14:6e:ed:66:8d:28:de:2e:f7:e3:e4:ab:70:41:fc:
43:4b:9e:bc
vmanage#
It needs to be noted that in fact, CSR and installation certificate can also be generated under the page, but there is a bug in 16.3.2. The device entry is not displayed under the page, and you cannot click generate and install. And I think it's just below the command line.
All devices need to be restarted after the certificate is installed. One third of the simple experiments have been completed.
After the restart, log in to vManage using the browser.
vManage add vBond, vSmart, and vEdge devices
Use the browser to log in to vManage, and the default username and password are all admin.
The following picture: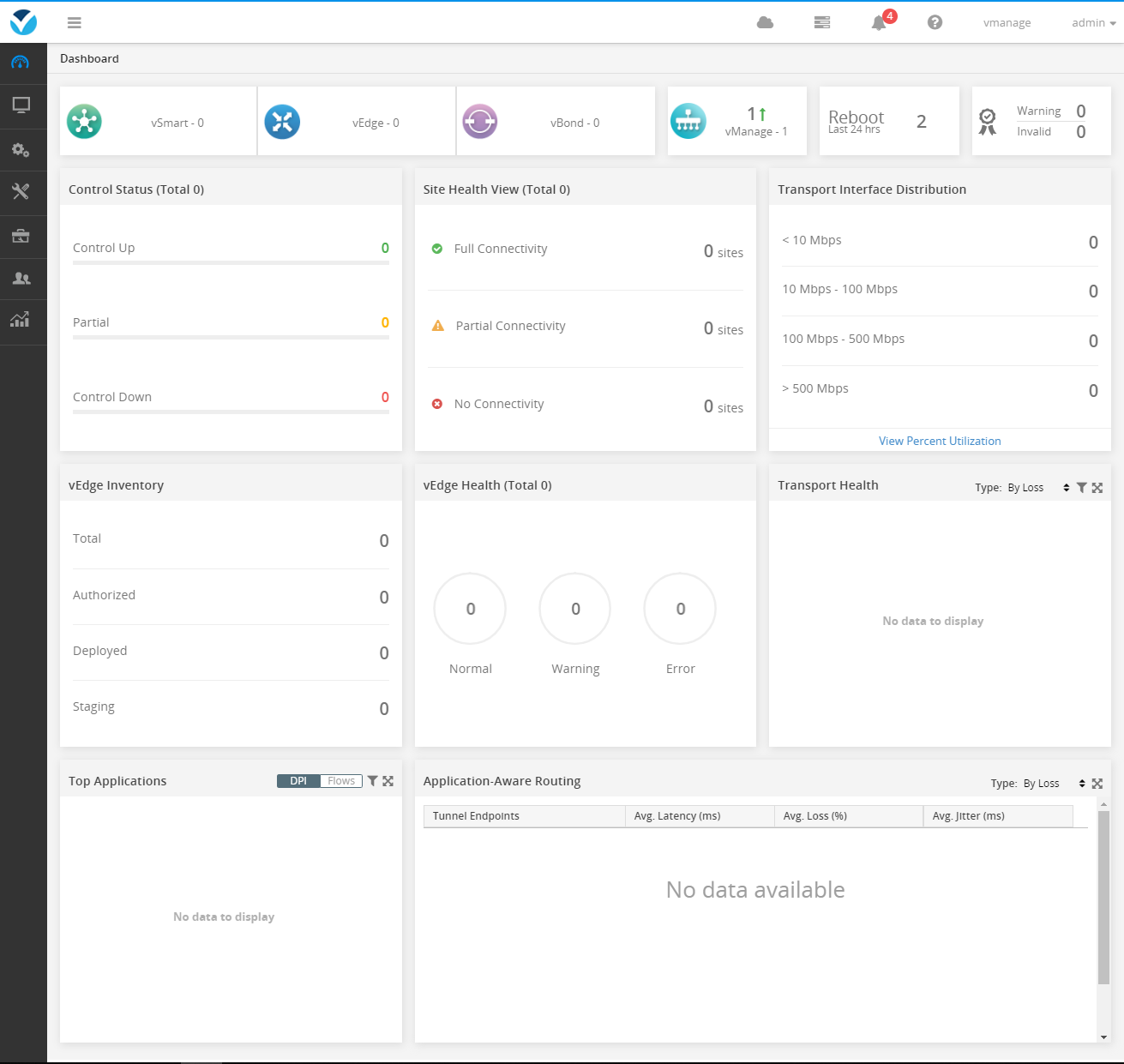
Because vManage has installed the certificate before, it can be seen that the device is directly online and shows that the synchronization and certificate have been installed.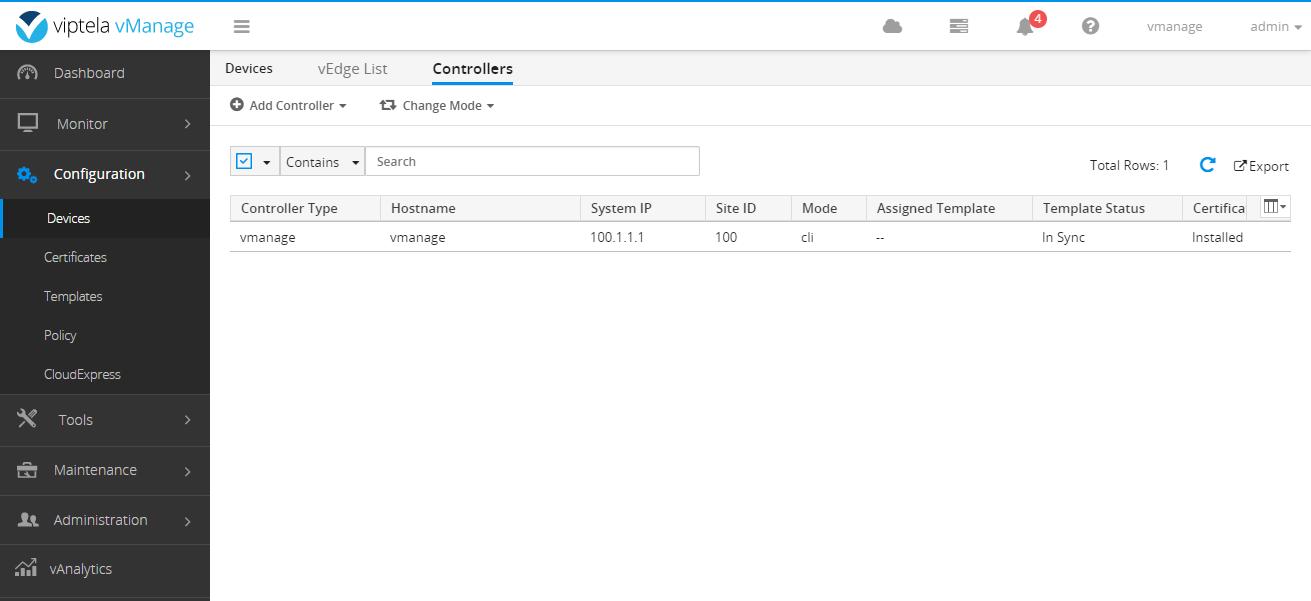
Configure the organization and vBond on vManage and make sure the warranty is manual.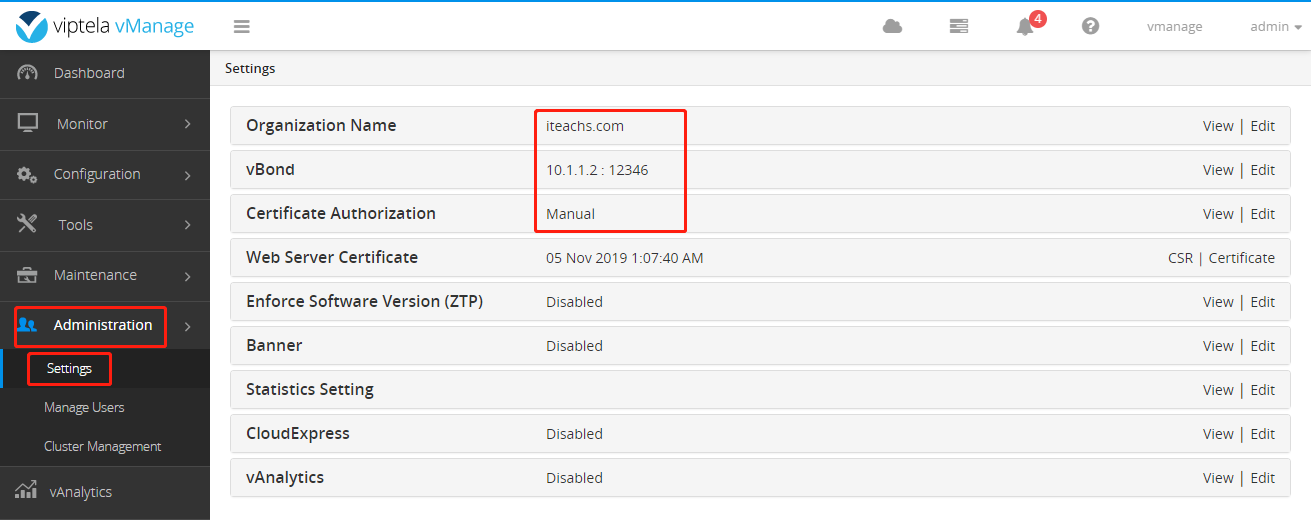
Add vBond and vSmart below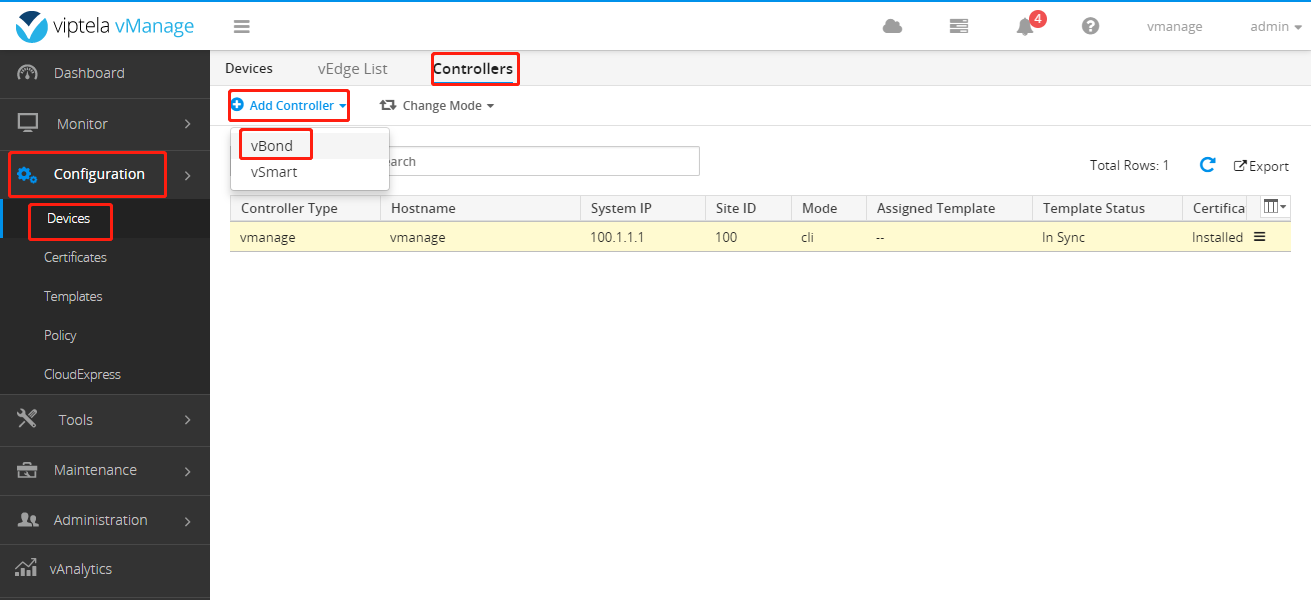
Do not check generate CSR because certificate has been installed before.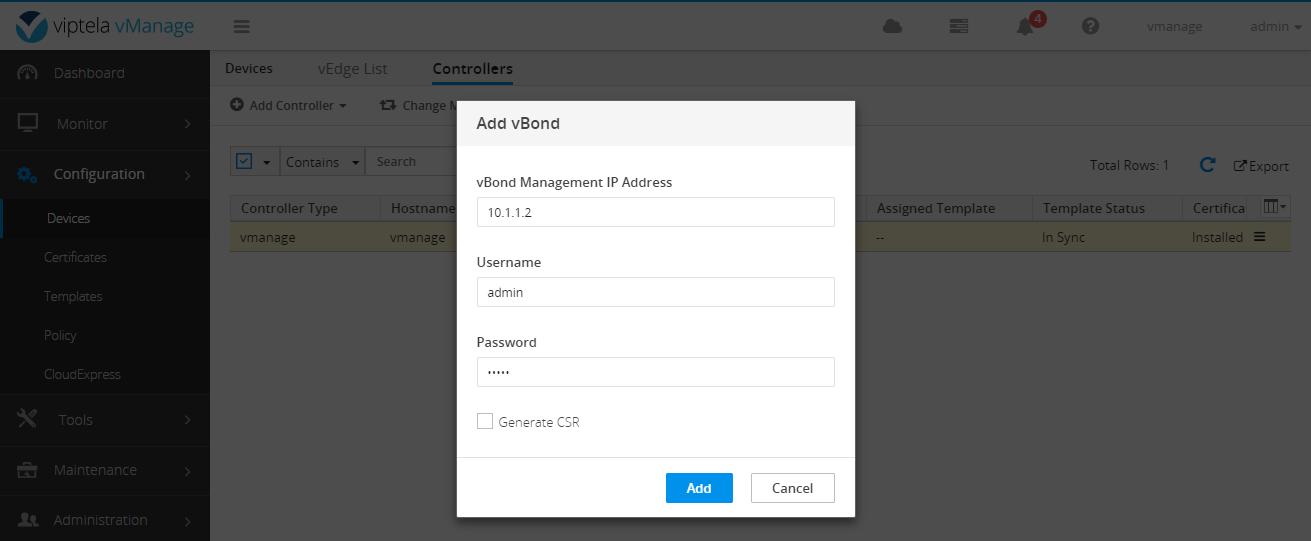
See the figure below after completion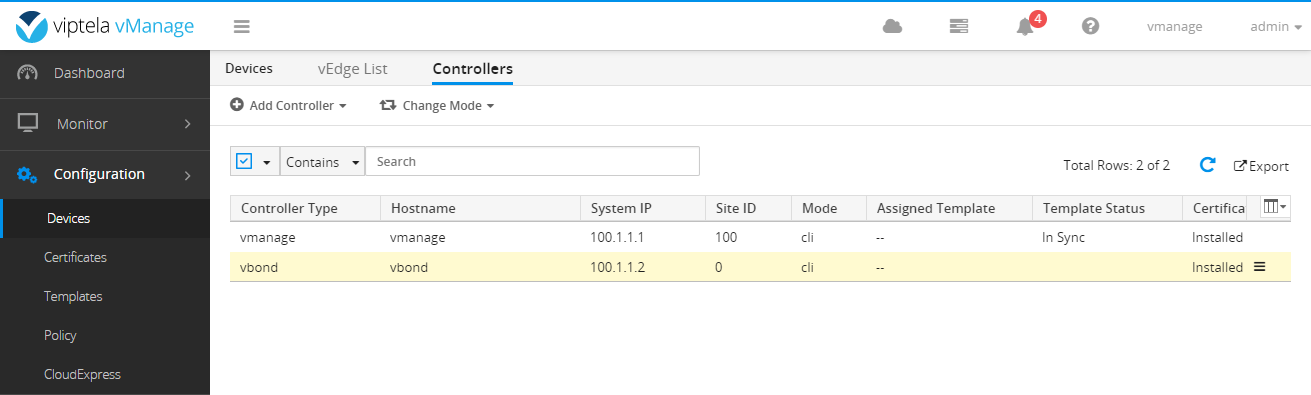
Add vSmart the same way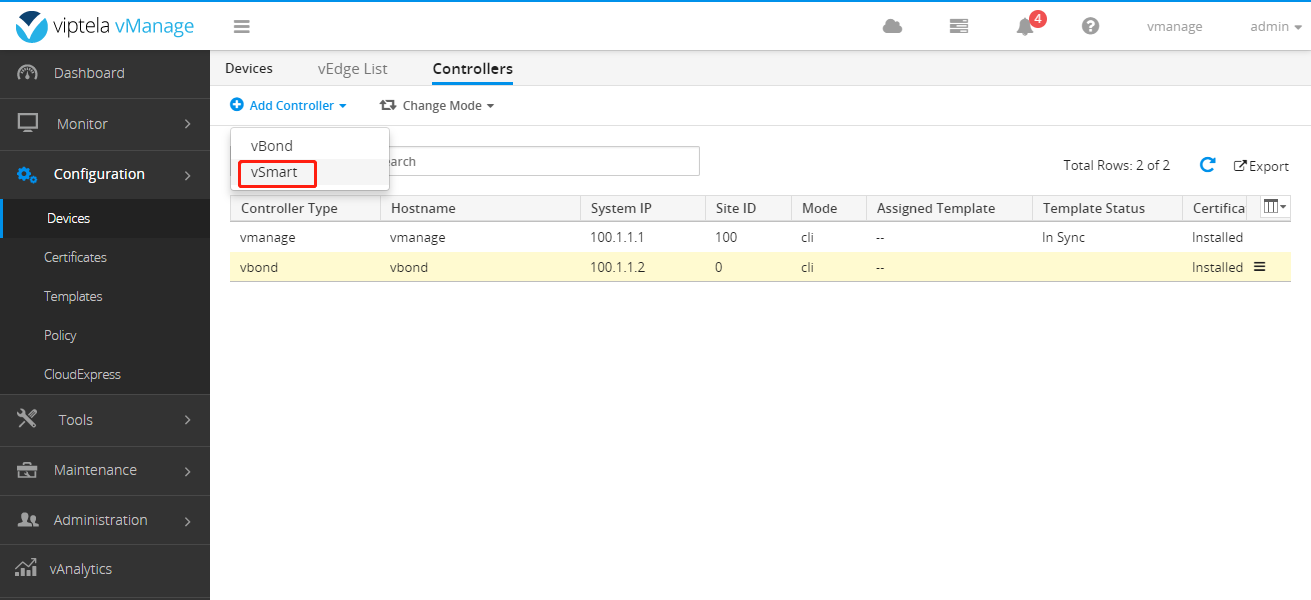
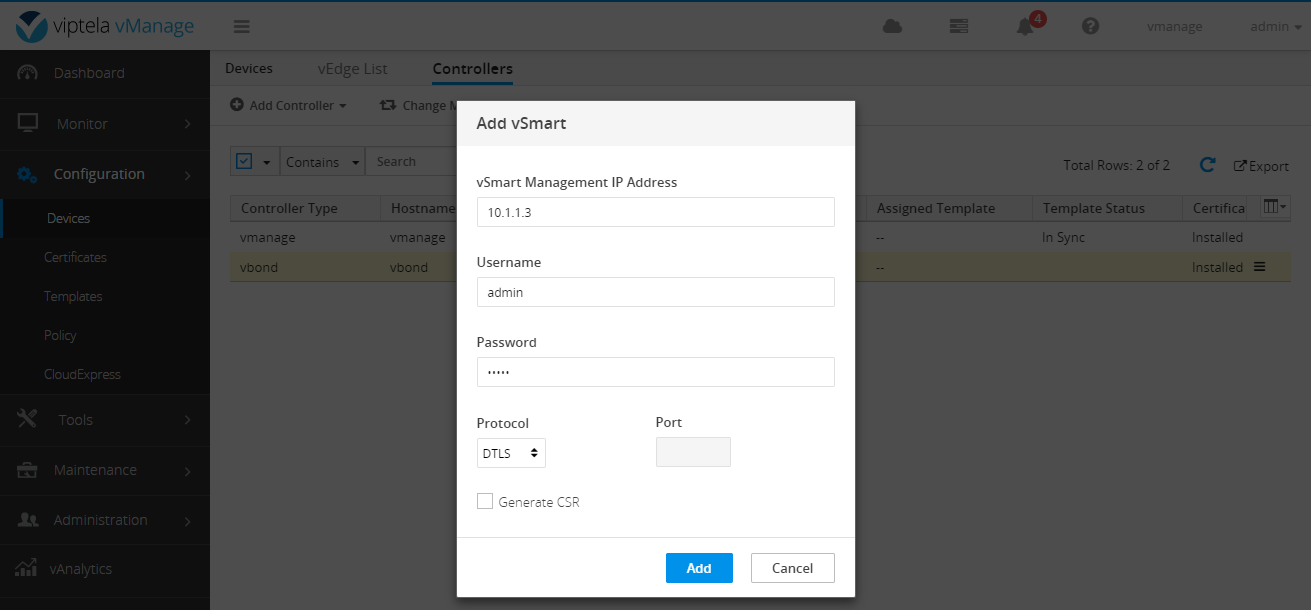
Similarly, the certificate installed before does not need to generate CSR. Add as follows: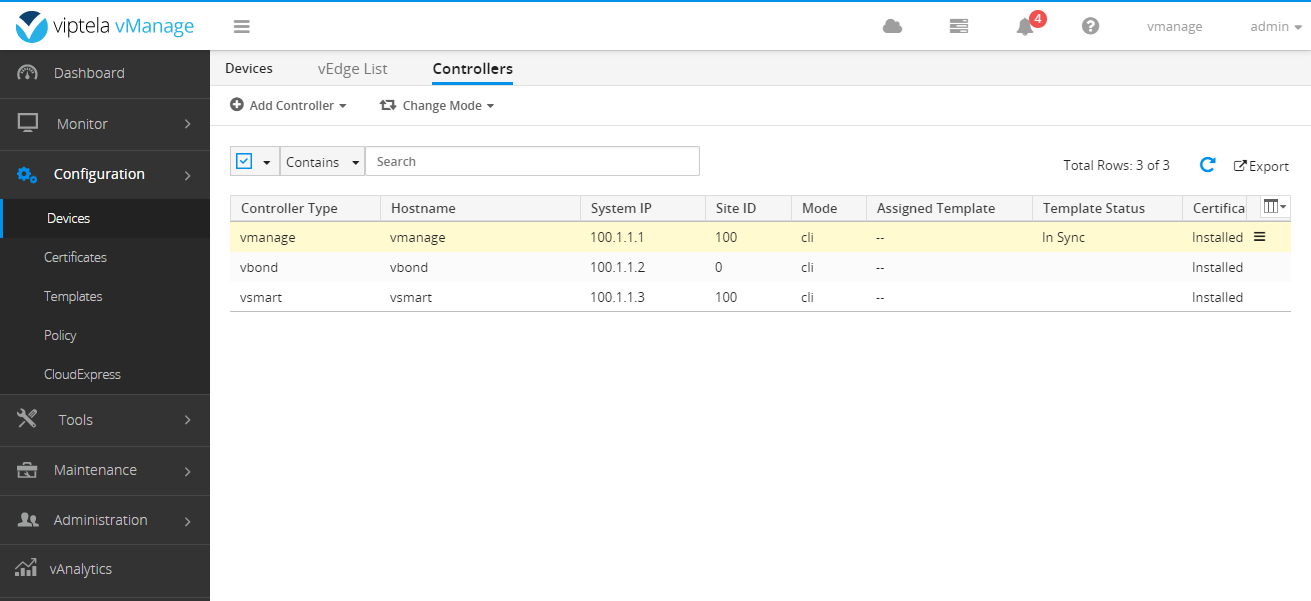
Then Send to vBond.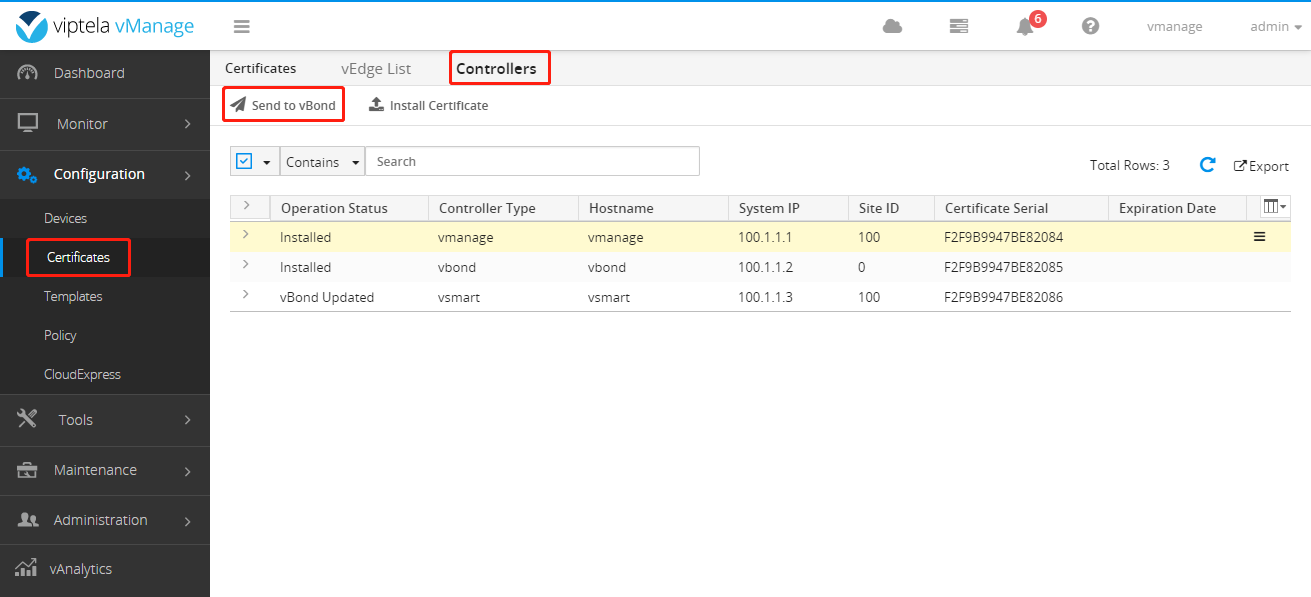
After completion, it is as follows: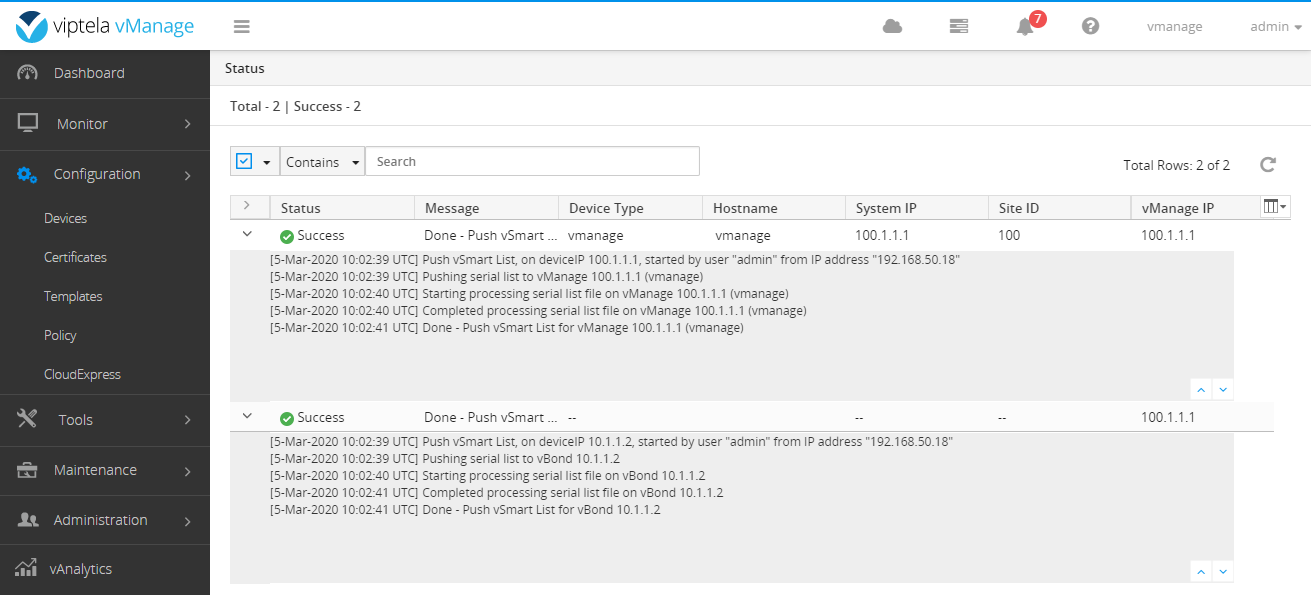
Next install the vEdge List
View the certificate sequence of the vEdge
vedge1# show certificate serial Chassis number: 49918191-566f-4ef1-875c-c8557c317275 serial number: F2F9B9947BE82087 vedge1# vedge2# show certificate serial Chassis number: 4ea4eb5d-dfba-4e33-8ea8-da22db5446a2 serial number: F2F9B9947BE82088 vedge2#
Then you will edit and create a new edge-list.csv file. The content is:
49918191-566f-4ef1-875c-c8557c317275,F2F9B9947BE82087 4ea4eb5d-dfba-4e33-8ea8-da22db5446a2,F2F9B9947BE82088
There are several devices added. Previously, it was said that the version before 17.0 can be added in this way. Later versions need to apply for a Cisco smart account and then download the file to add.
Upload the file to vManage after editing.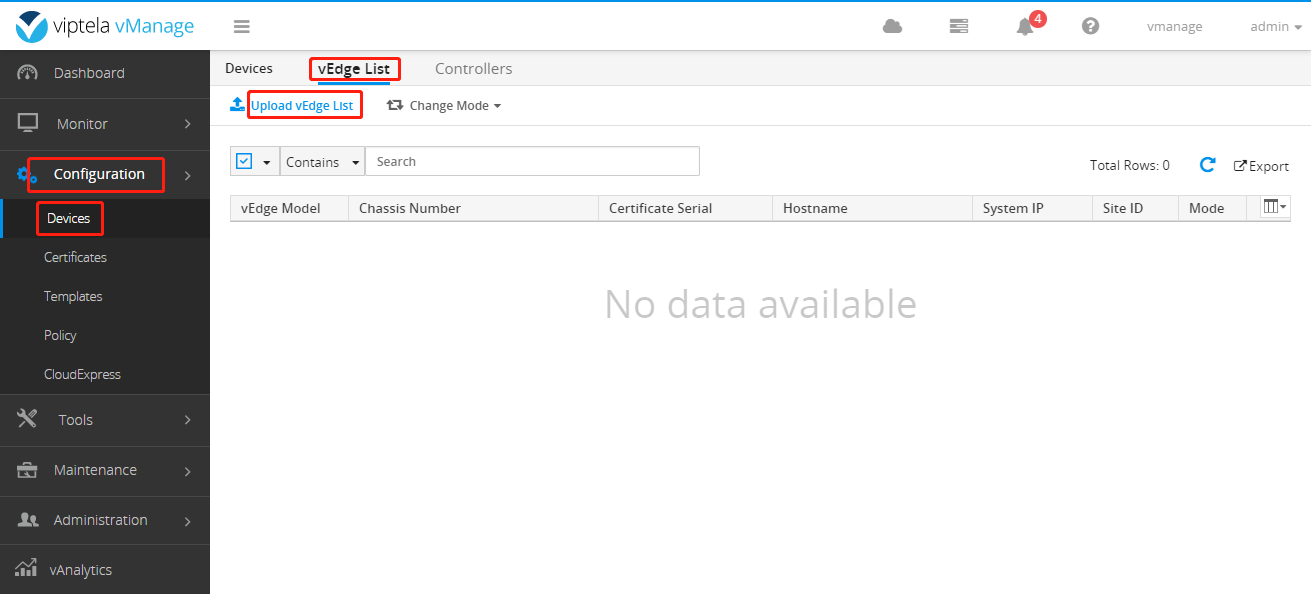
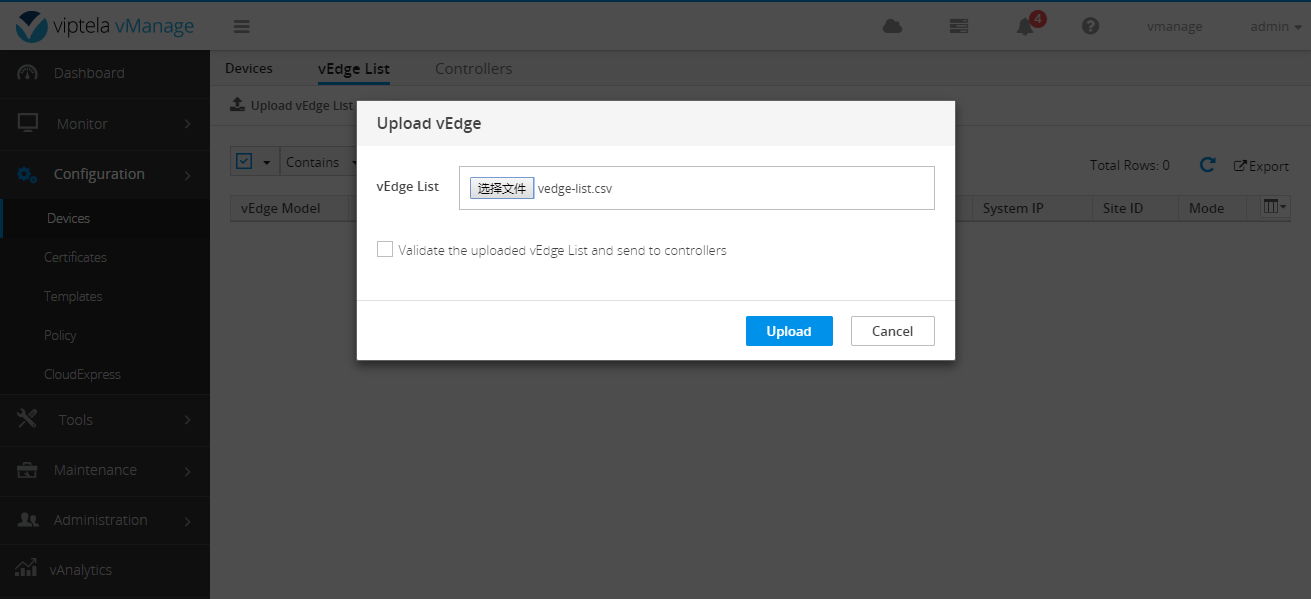
After completion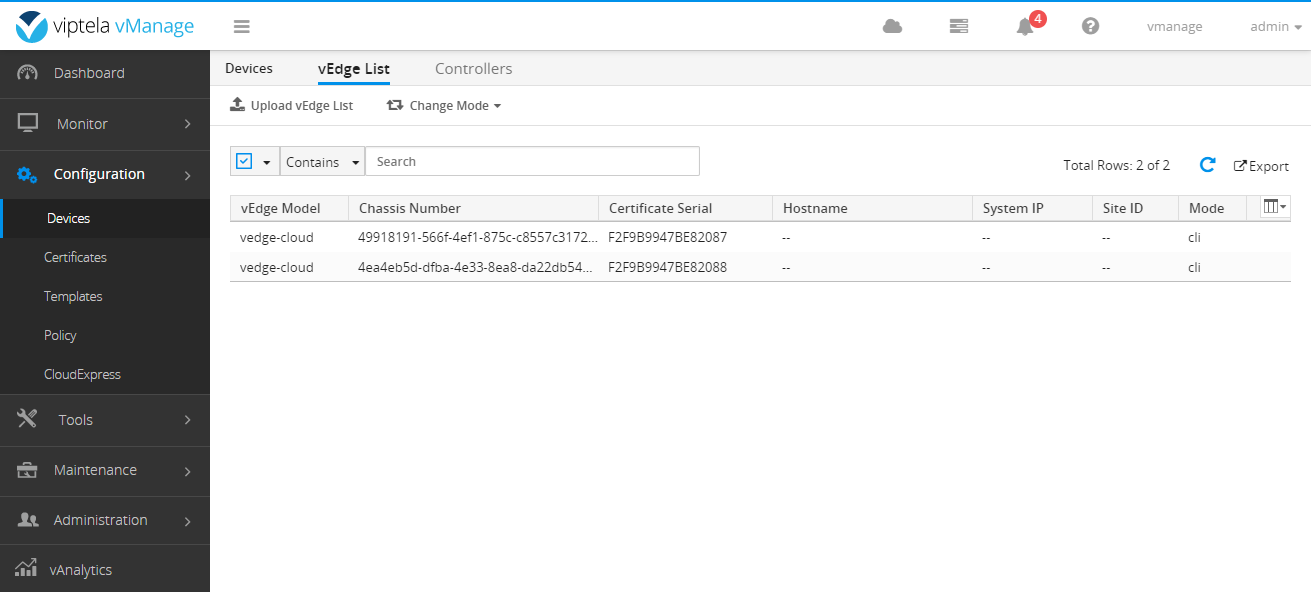
Then Send to Controllers is required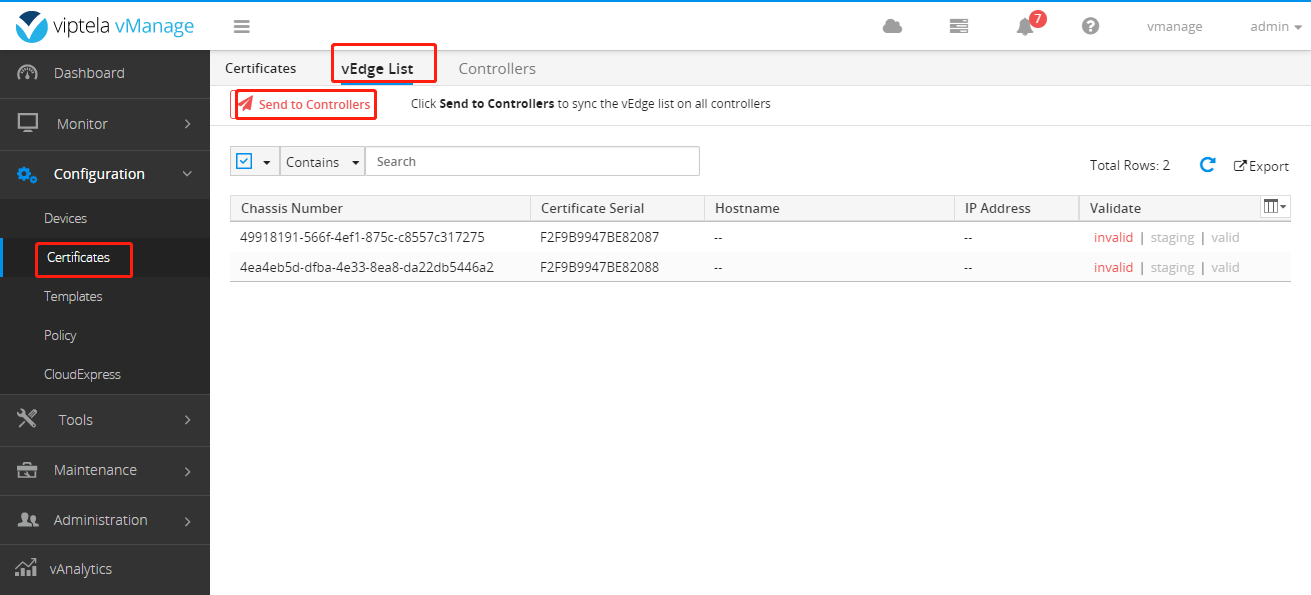
After completion, it is as follows: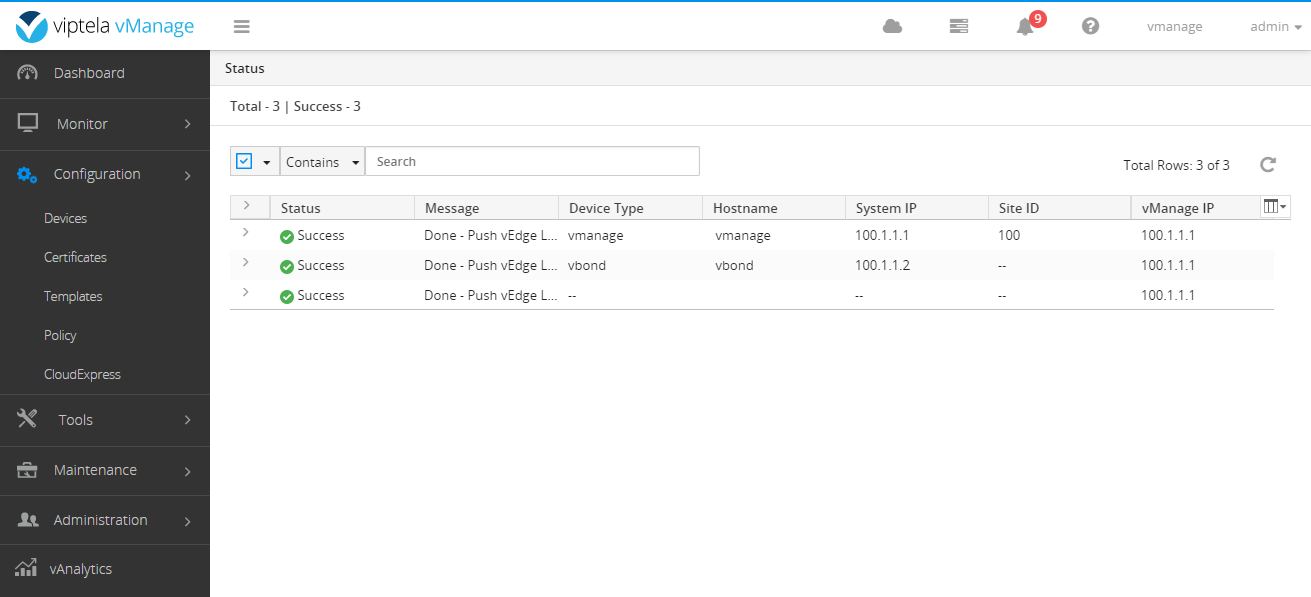
Open the tunnel interface of vManage, vBond, vSmart, and vEdge.
vManage,vSmart: vpn 0 interface eth0 tunnel-interface commit and-quit vBond,vEdge: vpn 0 interface ge0/0 tunnel-interface encapsulation ipsec commit and-quit
After tapping, return to the main interface.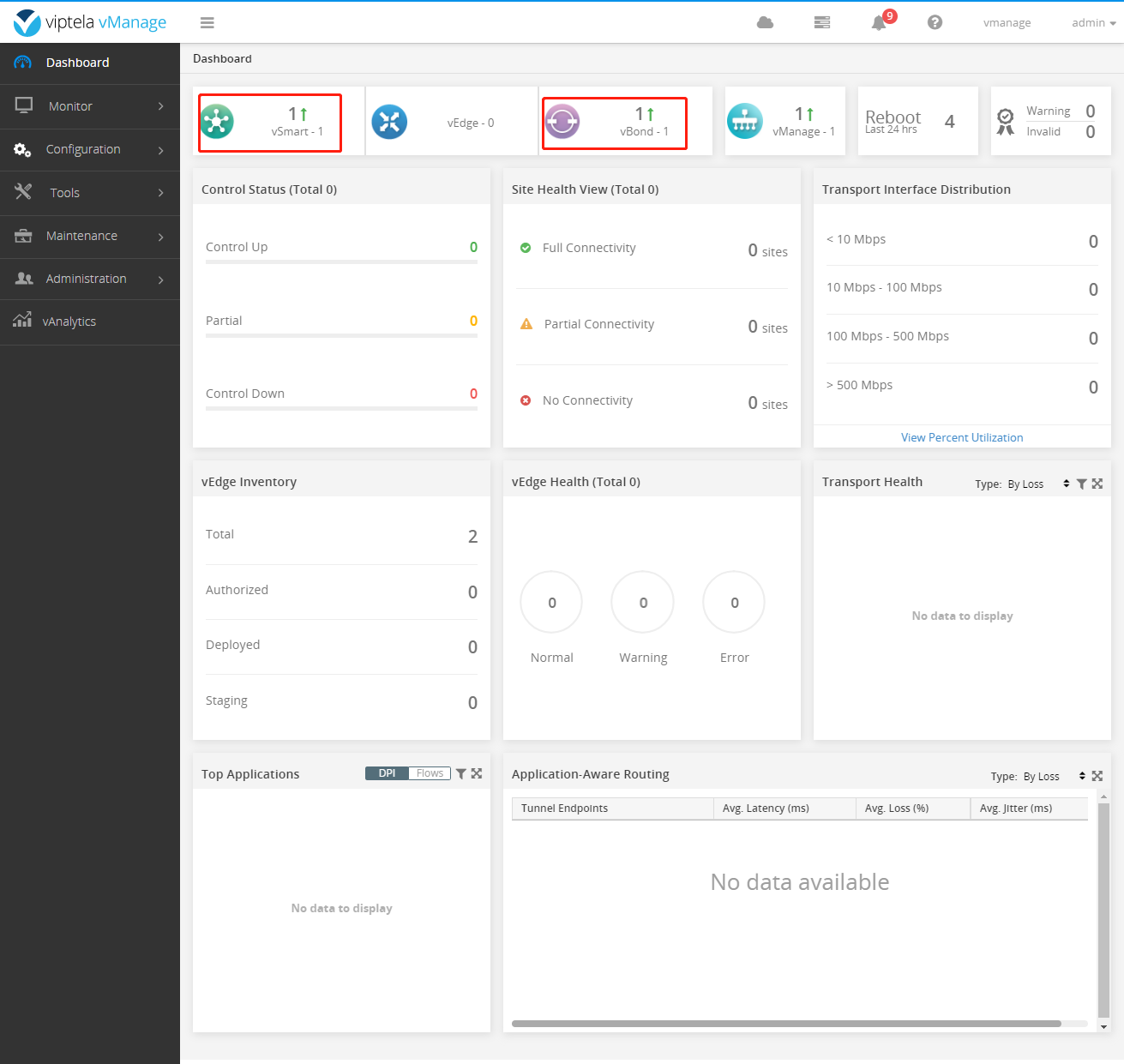
You can see that vSmart and vBond are online, but vEdge is not online. Don't hurry to continue.
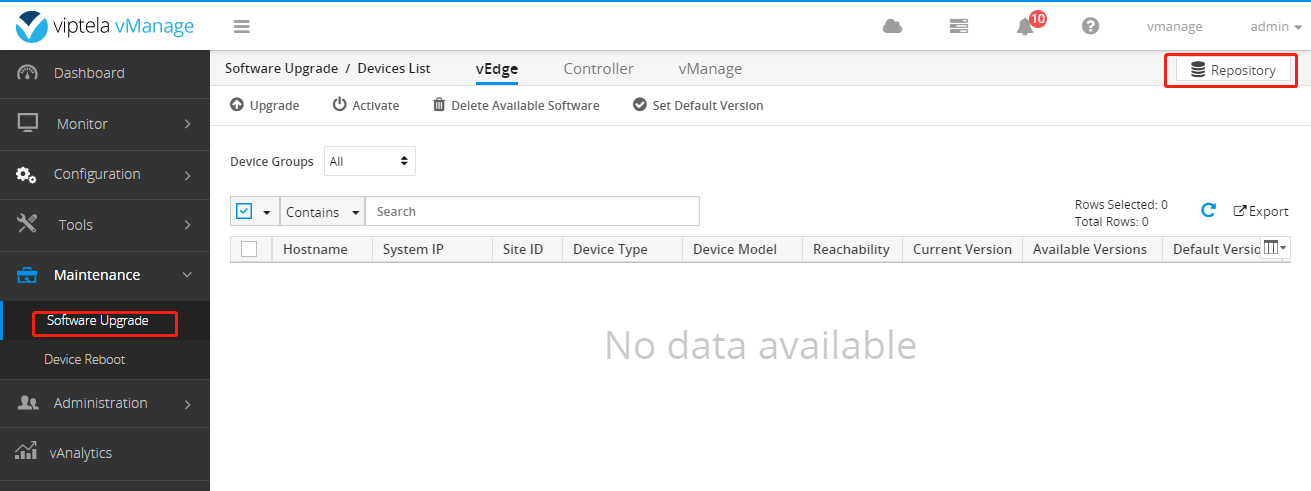
Upgrade vManage, vSmart, and vBond
Upgrade vManage
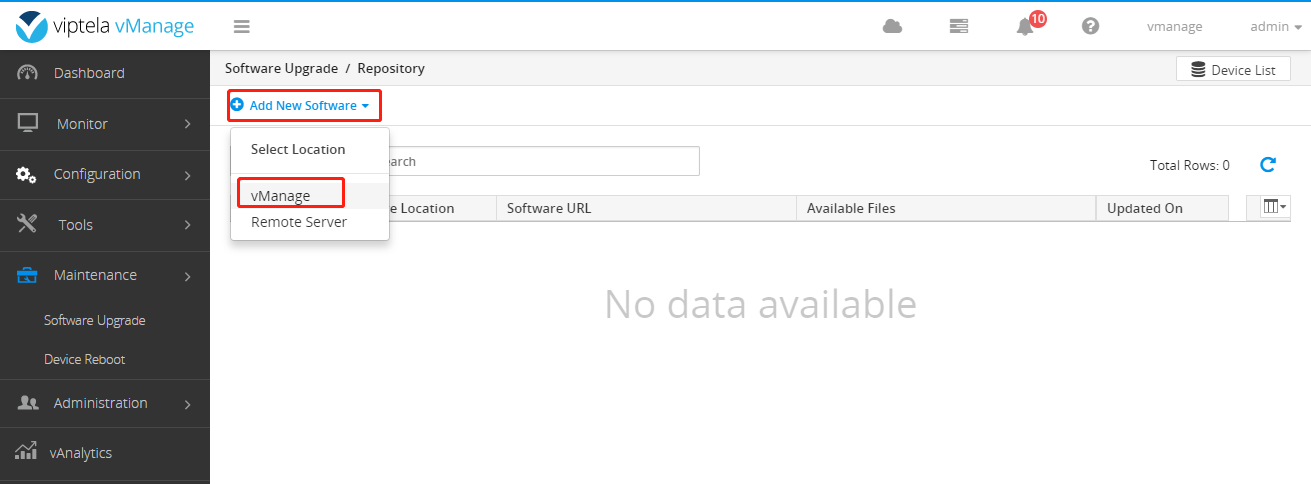
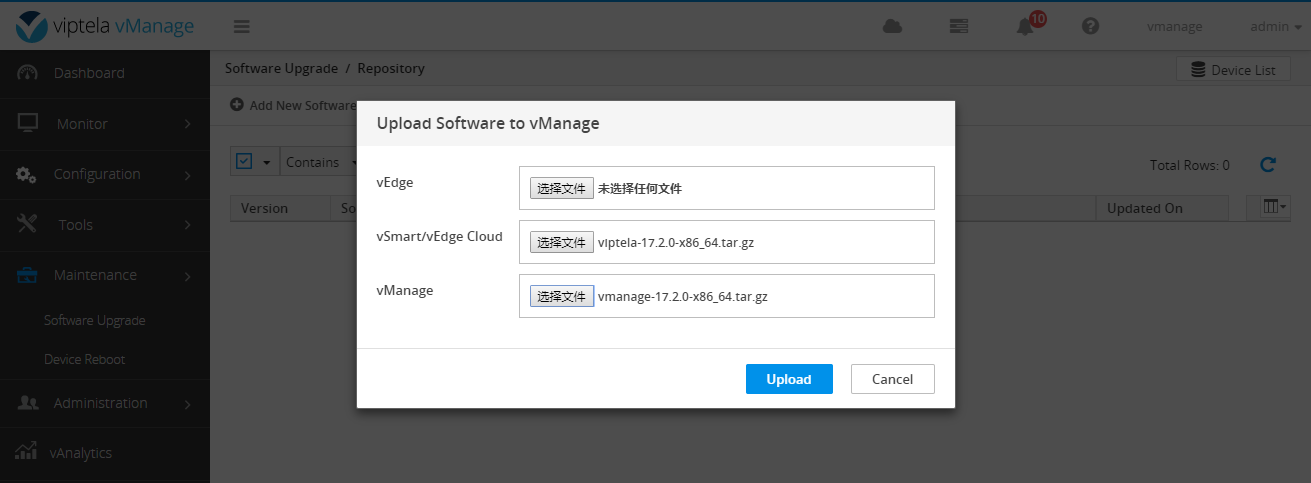
Upload the required files to vManage.