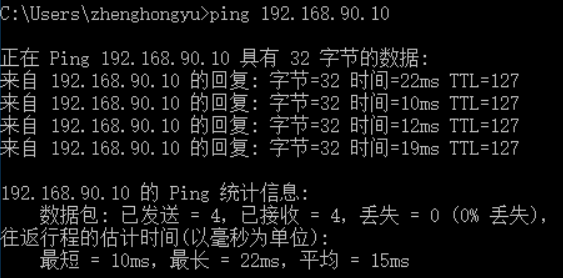
I. experimental configuration and requirements
The configuration requirements for establishing ACL extension on the route are as follows:
1. Allow PC1 to access Linux web Services
2. Allow PC2 to access the ftp service of Linux
3. Prohibit PC1 and PC2 from accessing other Linux services
4. Allow PC1 to access PC2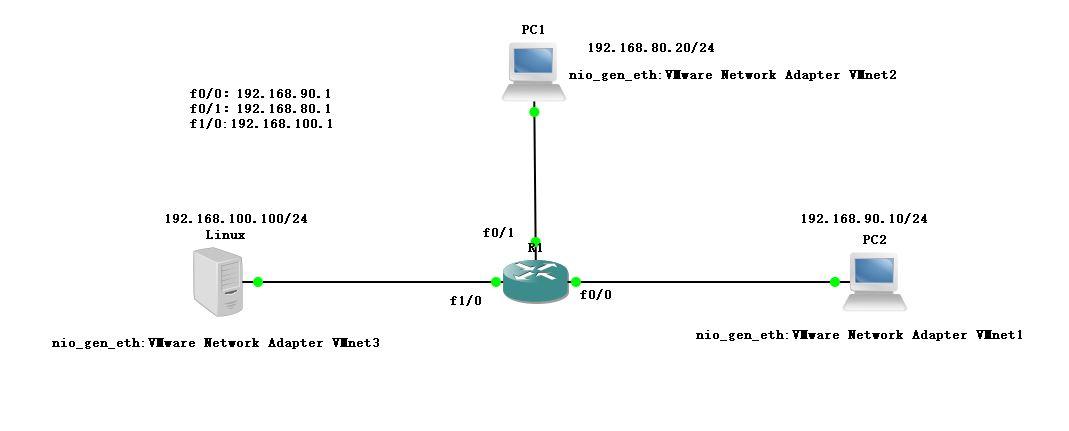
II. Deployment of experimental environment
1. pc1, pc2 and Linux systems are set with static IP, sub mask and gateway, and are bound with corresponding network card.
2. Complete the installation and startup of Linux server related services
[root@localhost ~]# yum install vsftpd -y / / install ftp service. [root@localhost ~]# yum install httpd -y / / install http service. [root@localhost ~]# systemctl stop firewalld.service / / turn off the firewall [root@localhost ~]# setenforce 0 / / turn off enhanced security [root@localhost ~]# systemctl start httpd / / start the service [root@localhost ~]# systemctl start vsftpd [root@localhost ~]# netstat -ntap | egrep '(21|80)' / / check the service startup status (port 80 is http, port 21 is ftp) tcp6 0 0 :::80 :::* LISTEN 6399/httpd tcp6 0 0 :::21 :::*
3. Routing configuration: three ports set IP
R1#conf t
R1(config)#int f 0/0
R1(config-if)#ip add 192.168.90.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f 0/1
R1(config-if)#ip add 192.168.80.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#int f 1/0
R1(config-if)#ip add 192.168.100.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#ex
R1(config)#do show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
C 192.168.90.0/24 is directly connected, FastEthernet0/0
C 192.168.80.0/24 is directly connected, FastEthernet0/1
C 192.168.100.0/24 is directly connected, FastEthernet1/04. Configure the extended ACL
R1(config)#access-list 100 permit tcp 192.168.80.20 0.0.0.255 192.168.100.100 0.0.0.255 eq 80
R1(config)#access-list 100 permit tcp host 192.168.90.10 host 192.168.100.100 eq 21
R1(config)#access-list 100 permit ip host 192.168.80.20 192.168.90.0 0.0.0.255
R1(config)#do show access-list
Extended IP access list 100
10 permit tcp 192.168.80.0 0.0.0.255 192.168.100.0 0.0.0.255 eq www
20 permit tcp host 192.168.90.10 host 192.168.100.100 eq ftp
30 permit ip host 192.168.80.20 192.168.90.0 0.0.0.255
R1(config)#int f0/1
R1(config-if)#ip access-group 100 in
R1(config-if)#int f0/0
R1(config-if)#ip access-group 100 in
R1(config-if)#ex 5. Result test
pc1 can access web site services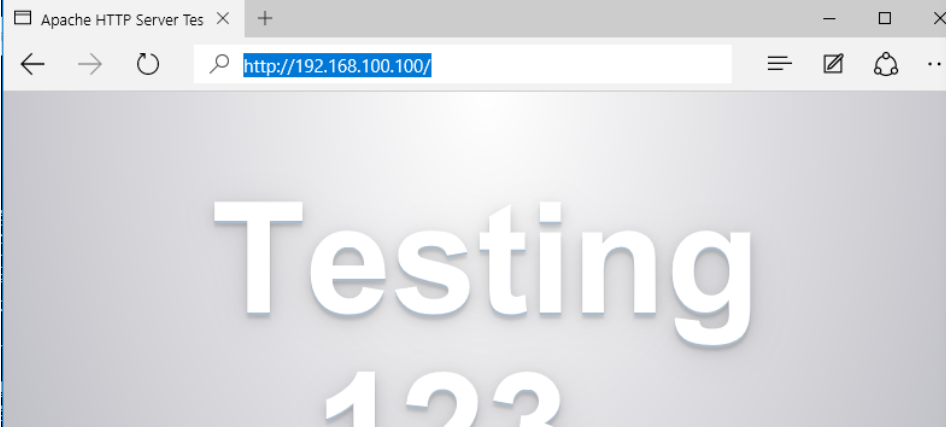
PC 2 can access ftp service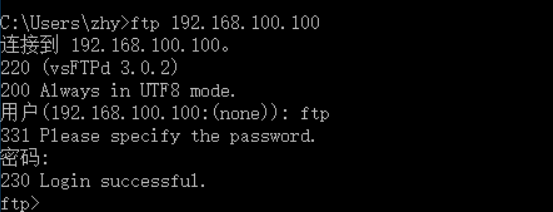
Allow pc1 to access pc2