I've given you a simple Got to know docker , and how Create an image through dockerfile , and Push image to private warehouse . This article briefly talks about using docker compose to make a simple container arrangement
What is container orchestration
Our application system may create multiple images according to different dependent tools, micro services, front and rear ends, different businesses, etc. for example, do we need to start the configuration center, registration center and various tools before starting the familiar micro services? Does the front end need to access the back end before it takes effect after the gateway is started. When we create containers with images, it is choreography to coordinate management in a certain order.
Our different containers are originally isolated, but we need to make certain mutual access rules between some of them. For example, each micro service needs to access the registry, the port number of these containers in the database, and the front-end container needs to request the port number of the gateway, but does not need to access the registry and database. We let the network, files and other resources between containers be adjusted in certain rules to meet our functional needs, which is also choreography.
Before the advent of double 11, we should flexibly expand or shrink some containers, maintain health, high availability, regularly schedule resources, monitor status, etc kubernetes(k8s), for example, is a container choreography tool, and the docker compose I introduced here is also a choreography tool. Its function is simple. It is suitable for container arrangement of single machine and small cluster. It is also very suitable for us to start and help novices understand.
First install docker compose
#/bin/cp -f ./docker-compose /usr/local/bin/docker-compose
-- 1.download docker-compose sudo curl -L "https://github.com/docker/compose/releases/download/v2.2.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose -- 2.Give permission chmod +x /usr/local/bin/docker-compose -- 3.Create soft chain ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
Code: docker compose yml
Then we need to write a file named docker - compose YML file, write our layout rules, such as which image the container is created from, which directories to mount, which ports to open, how to associate the container with the container, and the sequence of startup. Specific tutorials, but more description, online random query Docker compose tutorial
I'll give some examples of my project here for reference
version: '3' --First line,Description execution docker-composer The version number of the rule. Now I use version 3
services: --Example all the services I want to choreograph, that is, treat each container as a service and take an alias
nginx: --I named the front-end service nginx
restart: always --This means that if the container exits unexpectedly, it will be restarted automatically
image: 192.168.1.14/material-management/nginx:latest --From our basic image
container_name: mynginx --Take a container name
network_mode: "service:nacos" --join nacos The network of this service, they use the same IP,This is my opportunistic realization. See the description below
privileged: true --Let the container use privileges to create the mounted directory or file without reporting permission related errors
cap_drop: --The following is also permission related. It is used to close all permissions and grant specific permissions
- ALL
cap_add:
- CHOWN
- DAC_OVERRIDE
- SETGID
- SETUID
volumes: --Mount a specific directory or file
- /data/nginx/etc/nginx.conf:/etc/nginx/nginx.conf --If it is a file, the record shall be written in the directory in advance, otherwise it will be generated as a directory with the same name
- /data/nginx/log/:/var/log/nginx
- /data/nginx/www/:/var/www
nacos:
image: 192.168.1.14/common/nacos:fengshun
container_name: mynacos
restart: always
networks:
- mynetwork
ports: --Open these ports because I let the following containers join the network and share the same IP,It belongs to my personal speculation
- 80:8080
- 8080:8080
- 8081:8081
- 8088:8088
- 8848:8848
- 6379:6379
- 9876:9876
- 10909:10909
- 10911:10911
rocketmq-server: --rocketmq Naming service for
image: 192.168.1.14/common/rocketmq:namesvr
container_name: rocketmq-server
restart: always
volumes:
- /data/rocketmq-server/:/etc/rocketmq/
network_mode: "service:nacos"
rocketmq-broker:
image: foxiswho/rocketmq:broker
container_name: rocketmq-broker
restart: always
environment:
NAMESRV_ADDR: "localhost:9876"
JAVA_OPTS: " -Duser.home=/opt"
JAVA_OPT_EXT: "-server -Xms128m -Xmx128m -Xmn128m"
command: mqbroker -c /etc/rocketmq/broker.conf
volumes:
- /data/rocketmq-broker/broker.conf:/etc/rocketmq/broker.conf
network_mode: "service:nacos"
depends_on:
- rocketmq-server --etc. rocketmq Create after the naming service is started
minio:
image: 192.168.1.14/common/minio:fengshun
container_name: myminio
restart: always
cap_add:
- ALL
volumes:
- /data/miniodata:/data
network_mode: "service:nacos"
redis:
image: 192.168.1.14/common/redis:latest
container_name: myredis
restart: always
network_mode: "service:nacos"
volumes:
- /data/redisdata:/data
file-server:
image: 192.168.1.14/material-management/file-server:pre-1.2.6-SNAPSHOT
container_name: file-server
restart: always
volumes:
- /data/logs/filelog/:/tmp/mclog/
network_mode: "service:nacos"
privileged: true
cap_add:
- ALL
depends_on:
- minio --etc. minio Create after service startup
- nacos --etc. nacos Create after the registry is started
msg-server:
image: 192.168.1.14/material-management/message-server:pre-1.2.9-SNAPSHOT
container_name: msg-server
restart: always
volumes:
- /data/logs/msglog:/tmp/mclog/
network_mode: "service:nacos"
privileged: true
cap_add:
- ALL
depends_on:
- redis
- nacos
log-server:
image: 192.168.1.14/material-management/log-server:pre-1.2.9-SNAPSHOT
container_name: log-server
restart: always
privileged: true
cap_add:
- ALL
volumes:
- /data/logs/loglog/:/tmp/mclog/
network_mode: "service:nacos"
depends_on:
- nacos
gateway-server:
image: 192.168.1.14/material-management/gateway-server:pre-1.2.9-SNAPSHOT
container_name: gateway-server
restart: always
privileged: true
volumes:
- /data/logs/gatewaylog/:/tmp/mclog/
network_mode: "service:nacos"
cap_add:
- ALL
depends_on:
- nacos
networks: --Create a docker network
mynetwork:
name: 'mynetwork' --Named network
external: false
driver: bridge --Bridging, and HOST,Is to follow the host IP
I use a opportunistic method here, because to let the registry nacos run first, I let it open the ports I need to expose, and then let the containers related to nacos join the nacos network, so that they all use the same IP. Otherwise, their IP is isolated and dynamically produced. In order to let the containers access the IP of other containers, You can use the container name as IP to access
Start orchestration and create containers
cd to docker compose In the same level directory of YML, 5 Run docker compose up - D to pull the image and create the container
docker-compose up -d #-d is to make it run in the background
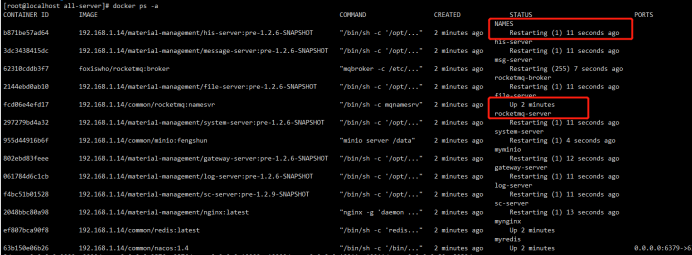
After completion, docker ps -a checks the running status to see if any services fail. You can see that some of them are UP, indicating the startup status. Other startup fails and try to start again. Restarting
How to update containers
Sometimes after we run a bunch of images and create containers with docker compose up, we update some functions. For example, I repaired the front end and recreated a new image We need to modify docker - compose The image in YML is your latest image name and label name
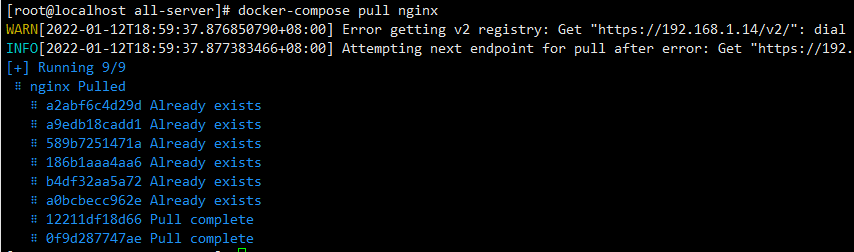
Then execute docker compose pull [service name] to pull the image again
docker-compose pull nginx #Here is the service name in the yaml file,
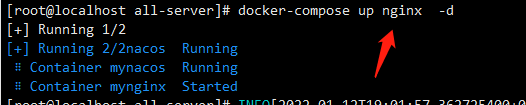
Then recreate the container
docker-compose up nginx -d Indicates re creation nginx The container of this service can also be added --force-recreate option
Common exceptions:
Permission denied class error
Generally, the authority is insufficient, which can be solved from multiple perspectives, such as
When creating an image, whether the user permission or read-write permission of the mount directory is given
The former adds the USER parameter to the dockerfile, while the latter specifies the directory and grants permissions with the chmod command
FROM minio/minio
MAINTAINER kuizii.com
USER root
EXPOSE 9000 8088
VOLUME /data
ENV MINIO_ACCESS_KEY=admin MINIO_SECRET_KEY=123
RUN chmod a+rwx /data
ENTRYPOINT ["minio", "server", "/data" ]
Add the – privileged=true parameter when running docker,
docker run --rm-v /data:/data --privileged=true minio:kuizii
If it is a container created with docker compose
Add privileged: true
The second scheme is to consider whether docker or docker compose permission is not given
For example, Chmod + X / usr / local / bin / docker compose
The third scheme is to consider the security policy of linux system, such as kernel security setting
You can try shutting down selinux temporarily
Execute setenforce0
If it is valid, edit the system configuration so that the restart is also closed
vi /etc/selinux/config modify SELINUX=disabled and restart will take effect
The first solution is recommended. The second solution is rare. The third solution reduces the overall security of the system due to the shutdown of selinux
That's all for the basic application of microservices in docker. The contents of docker, dockerfile and docker compose are not very detailed. You can find specific tutorials on the Internet. Later, I will share K8S as a special topic