Electronic signature technology sharing
1. What is electronic signature - in a word, it is to use the Internet to realize contract signing
Electronic contract is one of the written forms of contract stipulated in the contract law of the people's Republic of China. It refers to the agreement reached between two or more parties in electronic form through electronic information network to establish, change and terminate the relationship of property civil rights and obligations. Traditional contract signing requires both parties to be present at the same time, sign after confirming the content of the contract and affix the fingerprint (official seal), so as to have the effectiveness of legal recognition and restrict the parties to the contract. This way of signing contracts is naturally not suitable for Internet-based products. With the progress of Internet technology, relevant laws also comply with the development of the times, stipulating that qualified electronic contracts have the same validity recognized by law and can be protected by law. The introduction of electronic contracts has greatly promoted the rapid development of Internet products that rely on contracts signed by both parties.
Simply put, an electronic signature is electronic signature Image processing technology is used to transform the electronic signature operation into the same visual effect as the seal operation of paper documents. At the same time, electronic signature technology is used to ensure the authenticity and integrity of electronic information and the non repudiation of the signer. Electronic signature, to a certain extent, is a sign of enterprise digitization. The realization of electronic signature can better realize the digital needs of enterprises. In today's society, digitization is a sign to test whether an enterprise has tenacious vitality.
2. Why do we need electronic contracts
Of course, it is to reduce costs and increase efficiency, so as to save costs for enterprises. In supply chain finance, it can improve the trust between enterprises, prevent various default behaviors, effectively improve the cooperation efficiency between enterprises, and better integrate the information flow in the whole supply chain system. It effectively improves the operation efficiency of the enterprise. It has brought more survival opportunities to financing enterprises and revitalized the capital flow of the whole supply chain ecology, which will not make the financing enterprises unable to make ends meet or revitalize the capital flow in time due to long-term accounts receivable.
3. What kind of electronic contract is true and effective:
1. Be able to ensure that the sender of the contract is himself, not a forged ----------- true identity
The determination of the true identity of the contracting party is guaranteed by various real name authentication methods, so real name authentication is an essential part in the design of electronic contract products. The real name authentication function can be provided by the electronic contract service provider or other third-party service providers that meet the requirements. In the signing docking, we use the original real name authentication system,
2. Be able to ensure that the contract is signed by the signatory who is really willing to sign, rather than uncertain - true will
Willingness authentication refers to the confirmation of the user's identity before each signature, which is the authentication method of the user's own operation. Our common user password login is actually a kind of willingness authentication. However, due to the high risk of loss, theft and cracking of login password, for electronic contracts involving large amount and more important, other willingness authentication methods should be considered in product design to strengthen the reliability.
Common willingness authentication methods include fingerprint login, SMS verification code login, voice verification code login, face recognition login, UKEY login, etc. All kinds of willingness authentication methods have the same reliability and user experience, which can be selected according to different product requirements.
3. Be able to ensure that the original contract and the contract signature are not modified by the intermediary ----------- the signature is not modified and the original text is not modified
The unchanged signature and the original text are guaranteed and realized through digital signature technology + timestamp + digital certificate issued by CA. digital signature technology is the core part of it. Digital signature is used in the implementation of timestamp and digital certificate.
Digital signature is the combined application of asymmetric algorithm and hash algorithm, which is briefly explained as follows:
**Asymmetric algorithm: * * asymmetric algorithm is a magical encryption algorithm, which can generate a pair of keys, one of which is called public key and the other is called private key.
- The public key is public, and anyone on the Internet can obtain the public key of all others;
- The private key is private and can only be used by the holder himself.
Asymmetric algorithm can achieve the purpose of anti repudiation. The principle is that A uses its own private key to encrypt files; After receiving the file, B decrypts it with A's public key; If it can be decrypted, the supporting documents must come from A.
**Hash algorithm: * * the hash value of any different data after the hash algorithm is different, while the hash value of any same data after the hash algorithm is the same. Therefore, the hash value is also called the digital fingerprint of the data.
Assuming that A user A has signed an electronic contract, the server first hashes the original text of the electronic contract to obtain the hash value of the original text of the electronic contract. Then use the private key of user A to encrypt the hash value, and send the encrypted digital signature together with the electronic contract.
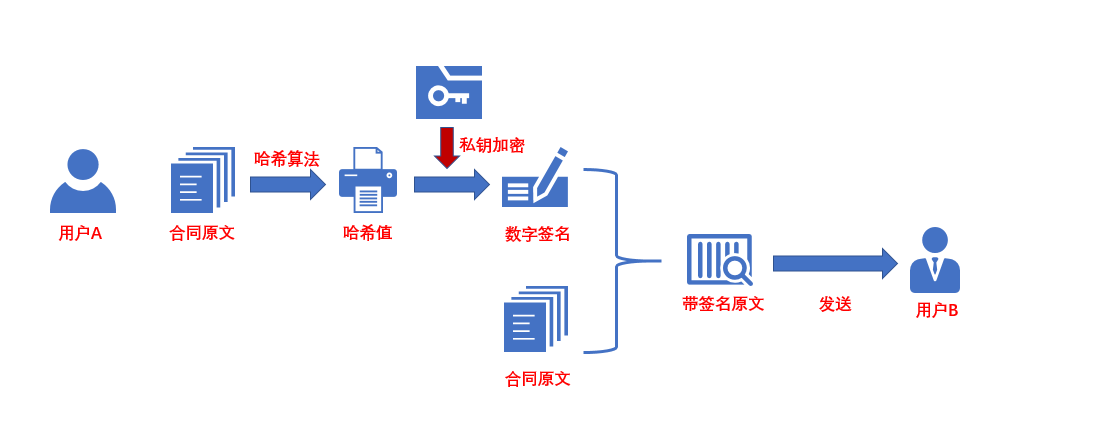
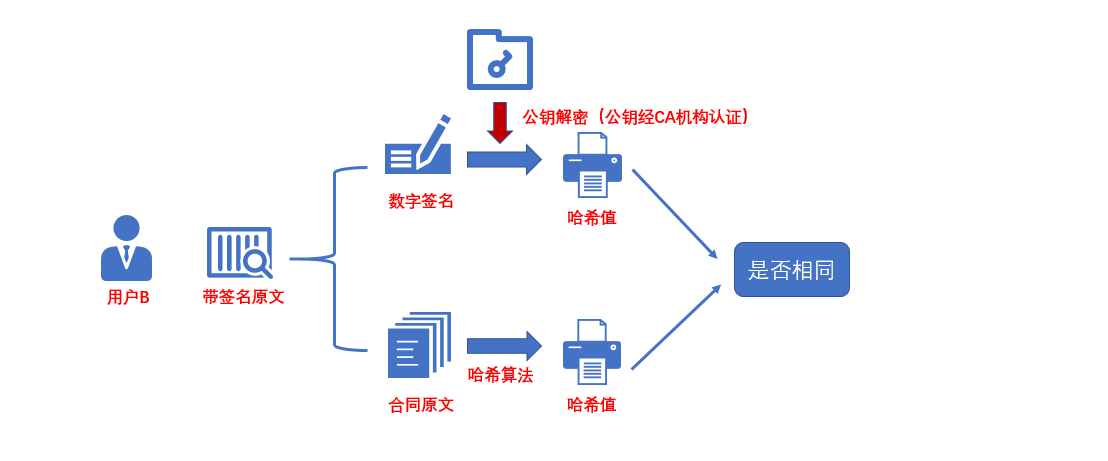
After receiving the electronic contract with digital signature, user B first obtains the hash value of the original text with the hash algorithm, and then decrypts the digital signature with user A's public key (the credibility of user A's public key is guaranteed by the digital certificate of Ca organization. As long as the digital certificate issued by the national certified CA organization is considered to be credible, it will not be explained here), The hash value obtained by decryption is compared with the hash value obtained by the hash algorithm of the original text. If the hash value is consistent, it proves that the electronic contract is indeed signed by A and has not been edited and modified, so as to achieve the purpose of verifying that "the signature has not been modified and the original text has not been modified".
**Time stamp: * * signing time is also the key link of the establishment and validity of electronic signature. Electronic signature generally uses time stamp technology to effectively confirm the signing time of electronic contract. The principle is to perform a hash operation on the electronic contract and send the hash value to the timestamp issuing center. The timestamp issuing center uses digital signature technology to digitally sign the hash value and the current time.
Because the hash value of the electronic contract is unique, the digital signature of the timestamp can confirm the time point of signing the electronic contract, which ensures the realization of "unchanged signature".
4. Common docking skills of third-party interface
1. According to the api docking documents provided by the third-party enterprises, extract the public request part of the api. In supply chain finance 2.0, we use to save the public parameters of various api requests into the database, encrypt them, and query and obtain them in the public part of the api. This can effectively prevent the code modification caused by the change of third-party services, and replace the old parameters with new parameters in time without restarting the application, which effectively improves the operation efficiency. It enhances the flexibility of the whole system.
2. In terms of interface docking, the general three-party Service Association will ask us to sign the request information. In the interface involving finance, we usually add timestamp and asynchronous callback. Therefore, when dealing with api docking, we need to extract and refine these common functions and write the same functions together to avoid repeated code, Improve the readability of the code and reduce the coupling degree of the code
3. The most important part of interfacing with the third-party api interface is to understand the business requirements. We need to discuss an effective solution with the third-party service provider to avoid prolonging working hours and reducing work efficiency due to various uncertainties. This is the most important point and what we need to do most. If we can't do this well, everything else is useless.
5. Business process of signing
Explain with the financing end:
The financier registers at the financing end. After the registration is completed, (bind the account number and the customer id with the signing system to identify the financier), we will require it to carry out real name authentication (now we use the signing authentication system). The financing end can enter the financing enterprise end after the real name authentication. When entering the system at the financing end, you can select the corresponding financing product. The financing product is bound with the relevant contract template. When sending the contract (if the account number has not been bound, it needs to be bound again). In all contract operations, it is necessary to ensure that the customer id has been bound with the signing system. Send the contract and fill in the dynamic fields of the template, that is, assign values to the fields of the template. After sending the contract (asynchronous notification - record the corresponding contract in the system), the platform can approve the contract. After approval, the fund party can sign or cancel it (asynchronous notification dynamically changes the contract status)
6. Skills used in signing and docking
1. Configure the signing public parameters in the third-party api management module, use the public function to calculate the request header information required by the signing request, and then you can call it directly
2. Use the signed asynchronous notification to update the data (corresponding asynchronous notification will be generated when sending, revoking, signing the contract, creating and modifying the template)
3. First, implement the request and blur the parameters. A String parameter is used to represent the whole parameter type, and it is expanded when implementing the business requirements.
7. Explanation of core logic code extraction:
/**
* Get the signed public part
*
* @return
*/
@Cacheable
@Override
public BestSignConfig getBestSignCommon() {
/**
*Query the parameters related to signing in the three-party system
*/
OthersApi otherApi = iOthersApiService.lambdaQuery().eq(OthersApi::getApiNo, OtherApiType.BEST_SIGN.getCode()).eq(OthersApi::getStatus, EnableOrDisableEnum.DISABLE.getCode()).one();
Long id = otherApi.getId();
List<OthersApiParams> othersApiParamsList = iOthersApiParamsService.lambdaQuery().eq(Func.isNotEmpty(otherApi), OthersApiParams::getApiId, id).list();
othersApiParamsList = othersApiParamsList.stream().map(e -> {
if (IsEncryptEnum.ENCRYPT_ENUM.getCode().equals(e.getIsEncrypt())) {
String encryptValue = e.getApiKeyValue();
e.setApiKeyValue(DesUtil.encryptToHex(encryptValue, encryptDesKey));
}
return e;
}).collect(Collectors.toList());
/**
*Sign on to allocate the clientId accessed by the system
*/
String clientId = othersApiParamsList.stream().filter(e -> BestSignCommonEnum.CLIENT_ID.getBizField().equals(e.getApiKeyName())).findAny().get().getApiKeyValue();
/**
*devAccount-----id of the system bound to the signature
*/
String devAccountId = othersApiParamsList.stream().filter(e -> BestSignCommonEnum.DEV_ACCOUNT_ID.getBizField().equals(e.getApiKeyName())).findAny().get().getApiKeyValue();
/**
*Sign client secret key
*/
String clientSecrect = othersApiParamsList.stream().filter(e -> BestSignCommonEnum.CLIENT_SECRECT.getBizField().equals(e.getApiKeyName())).findAny().get().getApiKeyValue();
/***
***Encapsulate the signed public request parameters
*/
BestSignConfig bestSignConfig = new BestSignConfig();
bestSignConfig.setHost(otherApi.getApiLink())
.setSecrectContent(DesUtil.decryptFormHex(otherApi.getApiSecrectContent(), encryptDesKey))
.setClientId(clientId)
.setDevAccountId(devAccountId)
.setClientSecret(clientSecrect);
this.setBestSignConfig(bestSignConfig);
return bestSignConfig;
}
/**
**Get the public header request parameters for signing up
*/
public Map<String, String> getHeader(String url, String requestData, Long timeStamp) {
Map<String, String> headers = new HashMap<>(16);
headers.put(BestSignHeaderEnum.CONTENT_TYPE.getFiled(), BestSignConstant.APPLICATION_TYPE);
headers.put(BestSignHeaderEnum.BESTSIGN_SIGN_TIMESTAMP.getFiled(), timeStamp.toString());
headers.put(BestSignHeaderEnum.BESTSIGN_CLIENT_ID.getFiled(), bestSignConfig.getClientId());
headers.put(BestSignHeaderEnum.BESTSIGN_SIGNATURE.getFiled(), getSign(url, null, requestData, timeStamp));
headers.put(BestSignHeaderEnum.BESTSIGN_SIGNATURE_TYPE.getFiled(), BestSignConstant.SIGNATURE_TYPE);
headers.put(BestSignHeaderEnum.authorization.getFiled(), "Bearer " + getAccessToken());
return headers;
}
Asynchronous notification:
@Transactional(rollbackFor = Exception.class)
public Boolean updateContractStatusByNotify(NotifyDecryptDTO notifyDecryptDTO) {
/**
* Contract status set
*SENT,The contract has been refused to sign COMPLETE,
* Revoke completed_ Cancel, the contract has been cancelled, OVERDUE,
* Overdue unsigned in_ SEND_ Approved, SEND_APPROVAL_NOT_PASSED, approval rejected
*
*/
JSONObject decrypt = notifyDecryptDTO.getDecryptMsg();
String contractId = decrypt.getString("contractId");
Contract contract = this.lambdaQuery().eq(Contract::getContractId, contractId).one();
CONTRACT_STATUS contract_status = getContractStatusByCode(notifyDecryptDTO.getType());
switch (contract_status) {
case CONTRACT_LIST_REVOKE_CANCEL:
return this.setToTargetStatus(contract,CONTRACT_LIST_REVOKE_CANCEL.getStatus());
case CONTRACT_REVOKE:
return this.setToTargetStatus(contract, CONTRACT_REVOKE.getStatus());
case CONTRACT_SEND_RESULT:
return this.saveContract(String.valueOf(contractId));
case CONTRACT_OVERDUE:
return this.setToTargetStatus(contract, CONTRACT_OVERDUE.getStatus());
case CONTRACT_COMPLETE:
return this.setToTargetStatus(contract, CONTRACT_COMPLETE.getStatus());
case CONTRACT_IN_SEND_APPROVAL:
return this.setToTargetStatus(contract, CONTRACT_IN_SEND_APPROVAL.getStatus());
case CONTRACT_SEND_APPROVAL_NOT_PASSED:
return this.setToTargetStatus(contract, CONTRACT_SEND_APPROVAL_NOT_PASSED.getStatus());
case CONTRACT_SEND_APPROVAL_PASSED:
return this.setToTargetStatus(contract, CONTRACT_SEND_APPROVAL_PASSED.getStatus());
default:
return Boolean.FALSE;
}
}