Copyright notice: it can be reproduced at will. When reprinting, please be sure to indicate the original source and author information of the article and this copyright notice in the form of hyperlink (author: Zhang Hua, published on: June 29, 2021)
problem
The test environment is openstack over openstack. There is only one named zhhuabj under my tenant in the underlying openstack_ admin_ Net, and then upper openstack uses this vxlan network to provide ext_net, and upper openstack provides a vxlan network called private.
Now I want to test the vlan network in upper openstack. In addition, I don't have the permission to change the physical switch to trunk. How can I change it?
Review Neutron trunking
This requires the neutron trunking feature. This [article] is very good. ( https://blog.csdn.net/bc_vnetwork/article/details/53927687)[1]
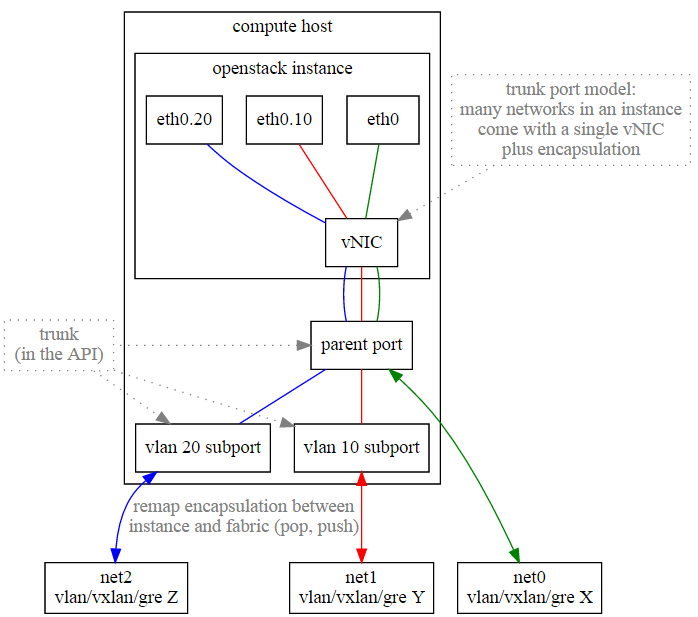
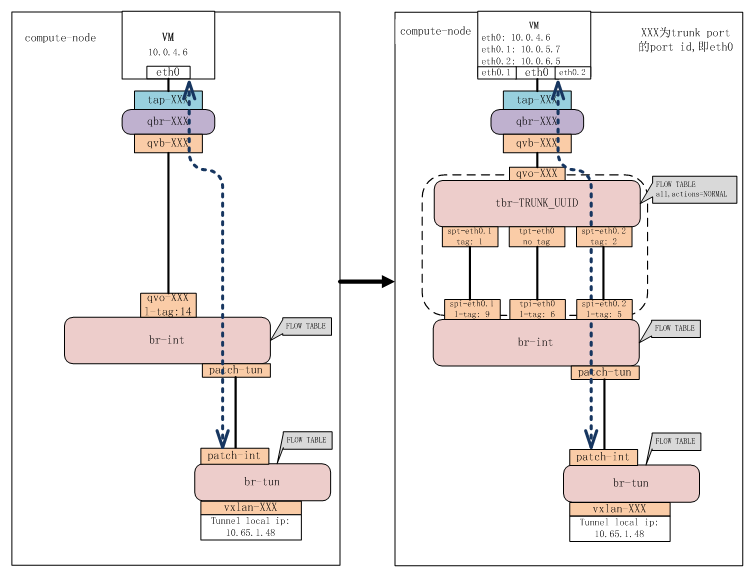
After using the neutron trunking port, you can play vlan in the virtual machine, so that you can support many networks through a network card in the virtual machine at the same time. The specific steps are:
openstack network create net0 openstack network create net1 openstack network create net2 openstack subnet create --network net0 --subnet-range 10.0.4.0/24 subnet0 openstack subnet create --network net1 --subnet-range 10.0.5.0/24 subnet1 openstack subnet create --network net2 --subnet-range 10.0.6.0/24 subnet2 openstack network trunk create --parent-port trunkparent \ --subport port=subport1,segmentation-type=vlan,segmentation-id=1 \ --subport port=subport2,segmentation-type=vlan,segmentation-id=2 mytrunk # inside vm sudo ip link add link eth0 eth0.1 address fa:16:3e:cc:b9:27 broadcast ff:ff:ff:ff:ff:ff type vlan id 1 sudo ip link add link eth0 eth0.2 address fa:16:3e:25:d2:c9 broadcast ff:ff:ff:ff:ff:ff type vlan id 2 sudo ip link set eth0.1 up sudo ip link set eth0.2 up sudo dhclient eth0.1 sudo dhclient eth0.2 ping -I eth0.1 10.0.5.2 tcpdump -en -i qvob7d4c968-af
Transformation principle
In upper openstack, define the neutron vlan 1000 network
- ./bin/neutron-ext-net-ksv3 --project admin --network-type flat -g $GATEWAY -c $CIDR_EXT -f $FIP_RANGE ext_net + ./bin/neutron-ext-net-ksv3 --project admin --network-type vlan --vlan-id 1000 -g $GATEWAY -c $CIDR_EXT -f $FIP_RANGE ext_net
The EXT of upper openstack_ Net as a provider network uses zhuabj of underlying openstack_ admin_ Net vxlan network.
At this time, unlike normal neutron trunking, vlan is played in the virtual machine. At this time, because the vlan network is defined in the upper openstack, vlan is not played in the virtual machine in the upper openstack (vlan is also played in the br int of the virtual machine)
In this way, define another one named zhuabj in the underlying openstack_ admin_ Net2's vxlan network is dedicated to trunk
source ~/novarc openstack router create zhhuabj_router2 openstack network create --disable-port-security zhhuabj_admin_net2 openstack subnet create --subnet-range 10.10.0.0/24 --network zhhuabj_admin_net2 --allocation-pool start=10.10.0.50,end=10.10.0.100 --gateway 10.10.0.1 zhhuabj_admin_net2_subnet openstack router add subnet zhhuabj_router2 zhhuabj_admin_net2 openstack router set --external-gateway zhhuabj_admin_net2 zhhuabj_router2
In this way, you can use the following command to make a trunk for the port of a node of upper openstack (the ports used by all upper computing nodes and neutron gateway nodes should be converted into trunk)
+ parent_port_id=$(openstack port create $current_model-data-port-$i --network lathiat_vlan_net --no-fixed-ip -f value -c id) + child_port_id=$(openstack port create $current_model-child-port-$i --network $network --no-fixed-ip -f value -c id) + openstack network trunk create $current_model-trunk0-$i --parent-port $parent_port_id --subport port=$child_port_id,segmentation-type=vlan,segmentation-id=1000
In this way, the traffic from the vlan network of upper openstack will be marked with vlan at br int, and the port to its computing node and neutral gateway will be converted into trunk in the underlying openstack. In this way, the underlying openstack will still send the vlan traffic from the upper layer as vxlan. In this way, the real physical environment does not need to modify the physical exchange into trunk.
Practical steps
1. Create zhuabj of special trunk in underlying openstack_ admin_ net2 (vxlan)
source ~/novarc openstack router create zhhuabj_router2 openstack network create --disable-port-security zhhuabj_admin_net2 openstack subnet create --subnet-range 10.10.0.0/24 --network zhhuabj_admin_net2 --allocation-pool start=10.10.0.50,end=10.10.0.100 --gateway 10.10.0.1 zhhuabj_admin_net2_subnet openstack router add subnet zhhuabj_router2 zhhuabj_admin_net2 openstack router set --external-gateway zhhuabj_admin_net2 zhhuabj_router2
2. patch
3. Create upper openstack
./generate-bundle.sh --defaults --name dt --create-model -r stein -s bionic --revision-info ./xxx.bundle --num-compute 2 --run
4. Transfer the port used by the computing node from the underlying openstack to the trunk port
./configure
5. Transfer the port used by the neutron gateway node from the underlying openstack to the trunk port
# Since the neutron gateway has created a data port before, you must delete it from the underlying openstack, and then run the following command ./bin/add-data-ports.sh neutron-gateway
6. Create test virtual machine
openstack keypair create --public-key ~/.ssh/id_rsa.pub mykey openstack server create --wait --image bionic --flavor m1.small --key-name mykey --nic net-id=$(openstack network show ext_net -c id -f value) i1 openstack server create --wait --image bionic --flavor m1.small --key-name mykey --nic net-id=$(openstack network show ext_net -c id -f value) i2
7. Do not work in the previous step. Open dhcp and work
openstack subnet set --dhcp ext_net_subnet nova reboot --hard i1 nova reboot --hard i2
8. Other information
From zhuabj_ admin_ Net to TRUNK and then from zhhuabj_admin_net2 is sent to other physical machines through vxlan.
$ source ~/novarc $ openstack network trunk list +--------------------------------------+-------------+--------------------------------------+-------------+ | ID | Name | Parent Port | Description | +--------------------------------------+-------------+--------------------------------------+-------------+ | 05814a30-1f72-4ca2-a2b8-c31de133fac5 | dt-trunk0-0 | c1aaa0ad-bd27-40c2-9c7f-76f415900b00 | | | e466bf99-1989-4f03-b179-e58e555591c0 | dt-trunk0-1 | e299e0d6-5037-40dc-b9d7-a539994de2af | | | ec6f6d96-960f-445e-80f3-a1695b07d954 | dt-trunk0-0 | 2abf732c-e3d3-4039-b43a-852bd703847c | | +--------------------------------------+-------------+--------------------------------------+-------------+ $ openstack network list |grep admin | 6999cbde-1293-45a1-9c83-c10277885993 | zhhuabj_admin_net2 | ed151d07-574e-4d9f-8351-254f68af45a5 | | b0268083-fcab-417b-b291-f1465880ee82 | zhhuabj_admin_net | 3b593653-04fb-407a-9853-e7886a608cd7 | $ openstack port show c1aaa0ad-bd27-40c2-9c7f-76f415900b00 |grep network_id | network_id | 6999cbde-1293-45a1-9c83-c10277885993 $ openstack network trunk show 05814a30-1f72-4ca2-a2b8-c31de133fac5 +-----------------+--------------------------------------------------------------------------------------------------+ | Field | Value | +-----------------+--------------------------------------------------------------------------------------------------+ | admin_state_up | UP | | created_at | 2021-06-29T09:00:58Z | | description | | | id | 05814a30-1f72-4ca2-a2b8-c31de133fac5 | | name | dt-trunk0-0 | | port_id | c1aaa0ad-bd27-40c2-9c7f-76f415900b00 | | project_id | 01c14ded0bf84e139c4f82316a377ca5 | | revision_number | 2 | | status | ACTIVE | | sub_ports | port_id='f281c260-d3ba-4481-b67b-83e73f095393', segmentation_id='1000', segmentation_type='vlan' | | tags | [] | | tenant_id | 01c14ded0bf84e139c4f82316a377ca5 | | updated_at | 2021-06-29T09:01:24Z | +-----------------+--------------------------------------------------------------------------------------------------+ $ openstack port show f281c260-d3ba-4481-b67b-83e73f095393 |grep network_id | network_id | b0268083-fcab-417b-b291-f1465880ee82
$ source ~/stsstack-bundles/openstack/novarc $ neutron net-list |grep ext_net | 0bdab84d-0320-4796-be08-64c5d3ddbc11 | ext_net | 8201ba31-3dbb-41be-a118-944ccce62b6d 10.5.0.0/16 |
Reference
[1] Introduction to the new features of openstack neutron VLAN aware VMS- https://blog.csdn.net/bc_vnetwork/article/details/53927687