Kali Linux only does penetration testing in the LAN, which is a little overqualified. Perhaps the long-distance penetration of aircraft with the wind can better reflect its original intention (strong concealment, maybe no trace!). To realize this idea, we need to solve a core problem: how to capture the network traffic of remote LAN? This problem can be further divided into two sub problems: A. collect remote network traffic; b. Return the collected traffic. In order to solve these two sub problems, two network cards are required (the problem of aircraft should be solved better): for sub problem a, use the network card with Monitor function; For sub problem B, use any other type of wireless network card. The following are classified:
Solve a. collect remote network traffic
It can be asserted that wireless routing has been popularized to all households. With the help of the monitor function of the wireless network card, you can quietly collect the wireless signals of each household without physical contact (the only limitation is the strength of the signal). I use Kali Linux + ALFA AC1200 to collect wireless data (AC1200 can switch to monitor mode and support 80211a/b/g/n/ac protocol, which can cover all frequency bands of wireless routing in the market)
kali:~$ sudo lsb_release -a No LSB modules are available. Distributor ID: Kali Description: Kali GNU/Linux Rolling Release: 2021.4 Codename: kali-rolling kali:~$ uname -a Linux kali 5.15.0-kali2-amd64 #1 SMP Debian 5.15.5-2kali2 (2021-12-22) x86_64 GNU/Linux
kali:~$ sudo iw list #Parameters of ALFA AC1200 Wiphy phy0 wiphy index: 0 max # scan SSIDs: 20 Supported Ciphers: * WEP40 (00-0f-ac:1) * WEP104 (00-0f-ac:5) * TKIP (00-0f-ac:2) * CCMP-128 (00-0f-ac:4) * GCMP-128 (00-0f-ac:8) * GCMP-256 (00-0f-ac:9) * CMAC (00-0f-ac:6) * GMAC-128 (00-0f-ac:11) * GMAC-256 (00-0f-ac:12) Available Antennas: TX 0x3 RX 0x3 Configured Antennas: TX 0x3 RX 0x3 Supported interface modes: * IBSS * managed * AP * AP/VLAN * monitor #Support monitor mode
Kali Linux does not support ALFA AC1200. You need to download and compile the source code of rtl88xx (ALFA AC1200 uses rtl8812 chip internally):
kali:~$ git clone https://github.com/aircrack-ng/rtl8812au.git # download 8812 driver source code kali:~$ sudo apt-get install build-essential libelf-dev linux-headers-`uname -r` #Install compile driver time dependent tools kali:~$ cd rtl8812au && make && make install kali:~$ sudo insmod 8812au.ko
In order to automatically load the rtl88xx driver every time you power on, you need to add the module to the / etc/modules file:
kali:~$ sudo cat 8812au >> /etc/modules
So far, ALFA AC1200 can work normally and switch to monitor mode:
kali:~$ iwconfig wlan1
wlan1 unassociated ESSID:"" Nickname:"<WIFI@REALTEK>"
Mode:Managed Frequency=2.412 GHz Access Point: Not-Associated
#Currently wlan1 works in Managed mode (default working mode)
kali:~$ sudo ifconfig wlan1 down #Turn off wlan1
kali:~$ sudo iwconfig wlan1 mode monitor #After switching to monitor mode, wireless packets can be captured
kali:~$ sudo ifconfig wlan1 up #Enable wlan1
kali:~$ iwconfig wlan1
wlan1 IEEE 802.11b ESSID:"" Nickname:"<WIFI@REALTEK>"
Mode:Monitor Frequency:2.412 GHz Access Point: Not-Associated
#The current wlan1 operation has successfully switched to monitor modeAt this time, open wireshark and set the capture interface to wlan1. You can see the wireless packets flowing through ALFA:

Solve b. return the collected traffic
With the solution of problem a, a new problem b is born: how can I retrieve the data captured by the remote wireshark? Although wireshark can save data to a file, due to storage space constraints, I prefer to use wireshark's remote interface function to capture data. To enable this function, you need to deploy the rpcapd daemon program on Kali Linux (Note: rpcapd can only be installed through source compilation, not apt install). Due to compatibility issues with rpcapd, please download from https://github.com/xiaoxiaobian/rpcapd-linux.git https://github.com/xiaoxiaobian/rpcapd-linux.git I have successfully deployed the source code
https://github.com/xiaoxiaobian/rpcapd-linux.git I have successfully deployed the source code
After successful compilation, execute the following command on Kali Linux to start the rpc service It will forward the data captured by wireshark on Kali Linux:
kali$ sudo ./rpcapd -4 -n [sudo] password for eugene: Press CTRL + C to stop the server...
(Note: for other parameters of rpcapd, please refer to: rpcapd(8) man page | TCPDUMP & LIBPCAP)
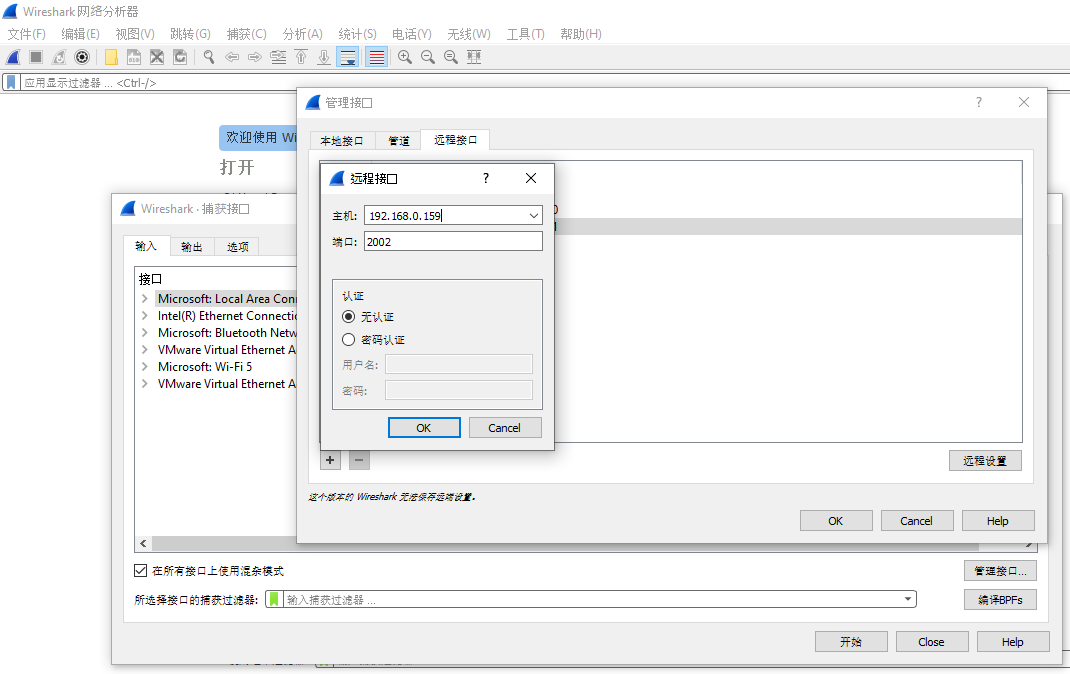
Now, from Kali Linux(ip:192.168.0.159) to Windows(ip:192.168.0.104), simulate obtaining the data captured by the remote ALFA on the local windows side: connect with the evil Wireshark -- capture -- Wireshark capture interface -- input -- management interface -- click "remote interface":
1). To add a remote Kali Linux interface:
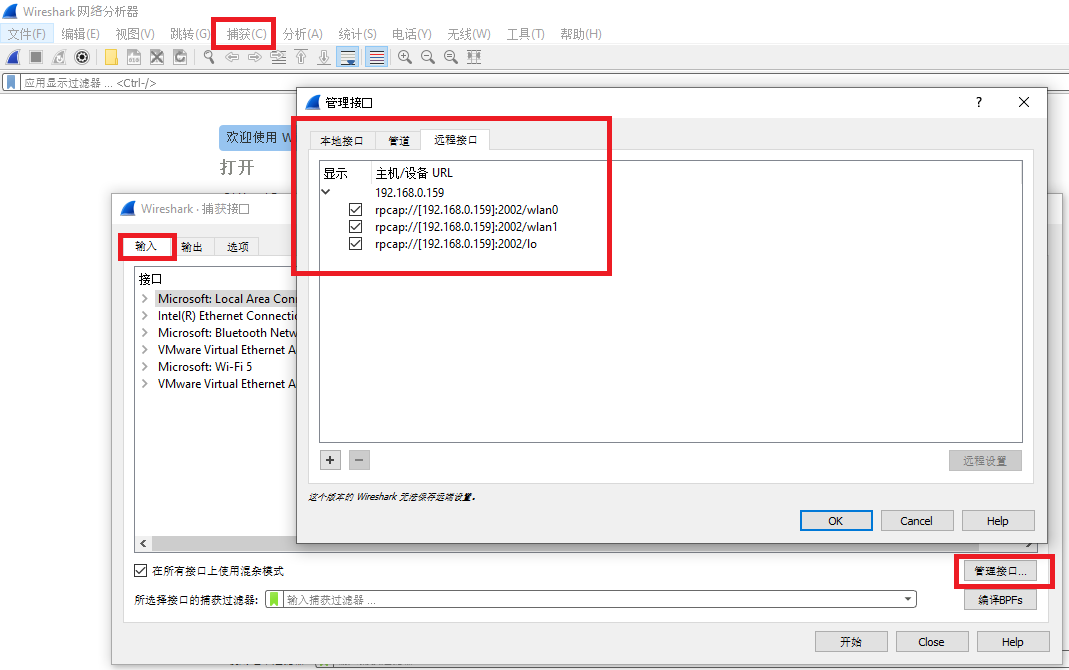
2). Select remote interface wlan1:
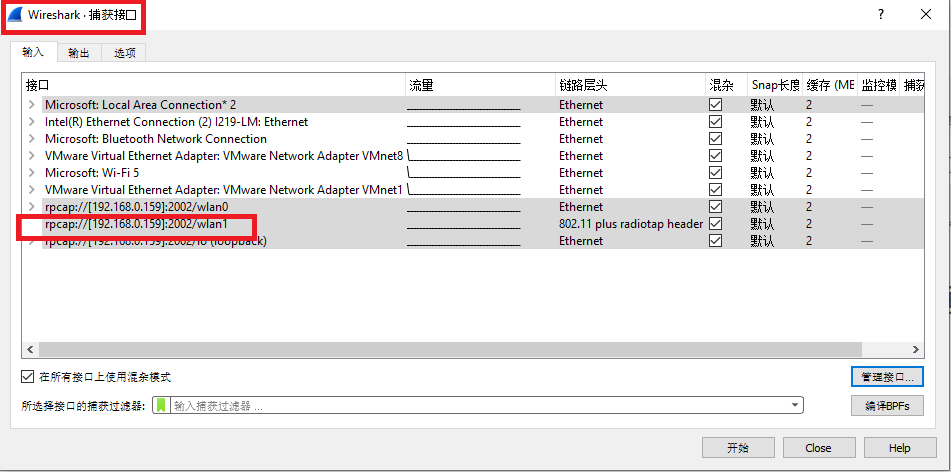
3). After adding, in Wireshark In the capture interface dialog box, you can see the ALFA interface on Kali Linux:
4). Click Start capture to see the wireless packet flowing through Kali Linux ALFA network card:
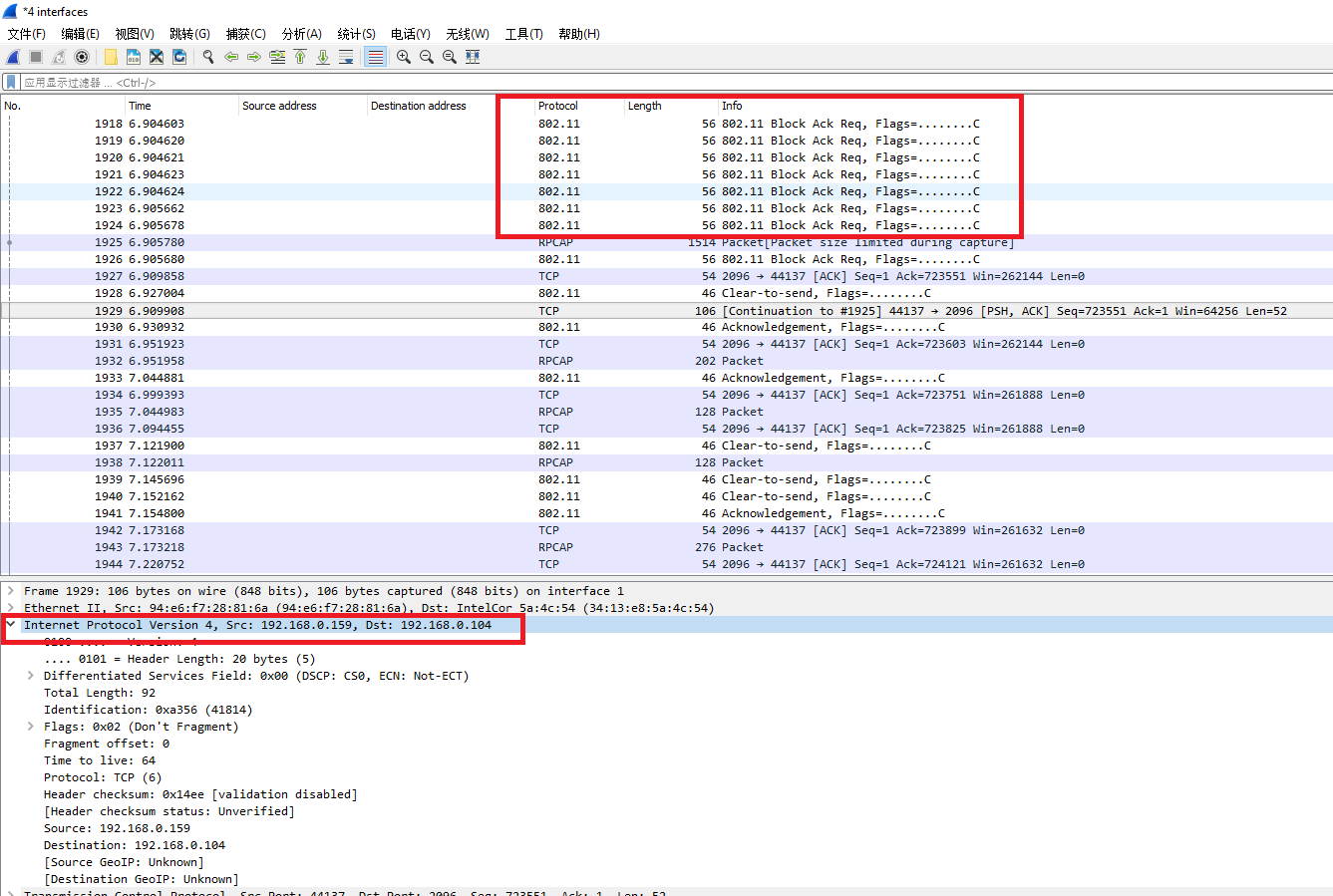
Now that the information collection process has been completed, we are short of a four-axis aircraft