1. Introduction to JumpServer
Jumpserver is the world's first open source fortress machine, developed and open source by flying to cloud Internet company. "Fortress machine" is also called operation and maintenance security audit system. The core function of jumpserver is 4a. It uses GNU GPL v2 0 open source protocol, which is a professional operation and maintenance security audit system in accordance with 4A specification.
jumpserver is mainly developed using Python/Django, follows the Web 2.0 specification, and is equipped with the industry-leading Web Terminal scheme, with beautiful interactive interface and good user experience.
Compared with traditional fortress machines, jumpserver adopts distributed architecture design, supports multi machine room cross regional deployment, supports multi cloud environment and can be flexibly expanded. In terms of asset management, jumpserver has no concurrency and asset quantity restrictions, and supports horizontal expansion. Jumpserver can use the industry-leading container deployment method and experience excellent Web Terminal. Jumpserver can also realize Web-based file transfer and support users to save O & M Design Videos in the cloud (such as AWS S3, Alibaba cloud OSS, Elastsearch, etc.). It provides Internet enterprises with certification, authorization, audit, automatic operation and maintenance, etc.
jumpserver now supports SSH, Telnet, RDP and VNC protocol assets.
Latest version: v2 ten point two
Other fortress machines include: Xingyun housekeeper, newdun fortress machine, etc.
Official website: https://www.jumpserver.org
Official documents: https://docs.jumpserver.org/zh/master/index.html
2. What is 4A
4A refers to Authentication, Authorization, Account and Audit. The Chinese name is "unified installation management platform solution". Identity Authentication, Authorization, Audit and Account number (i.e. non repudiation and data integrity) are defined as the four components of network security, so as to establish the status and role of identity Authentication in the whole network security system.
In 1995, the international network security community proposed 4A (authentication, authorization, account number and audit) unified security management platform, which officially took identity authentication as the basis and indispensable part of the whole network security, that is, identity authentication, authorization, bookkeeping and audit were defined as the four components of network security
Establish the status and role of identity authentication in the whole network security system.
The so-called 4A unified security management platform solution, which integrates the four elements of unified user account management, unified authentication management, unified authorization management and unified security audit, will cover security functions such as single sign on (SSO), which can provide customers with fully functional and high-level 4A management, It can also provide users with internal control reports that meet the requirements of Sarbanes Oxley Act (SOX).
3. JumpServer special advantages
⚫ Open source: zero threshold, fast online acquisition and installation.
⚫ Distributed: easily support large-scale access.
⚫ No plug-ins: just a browser, the ultimate Web Terminal experience.
⚫ Multi cloud support: a system that manages assets on different clouds at the same time.
⚫ Cloud storage: audit videos are stored in the cloud and will never be lost.
⚫ Multi tenancy: a system used by multiple subsidiaries and departments at the same time.
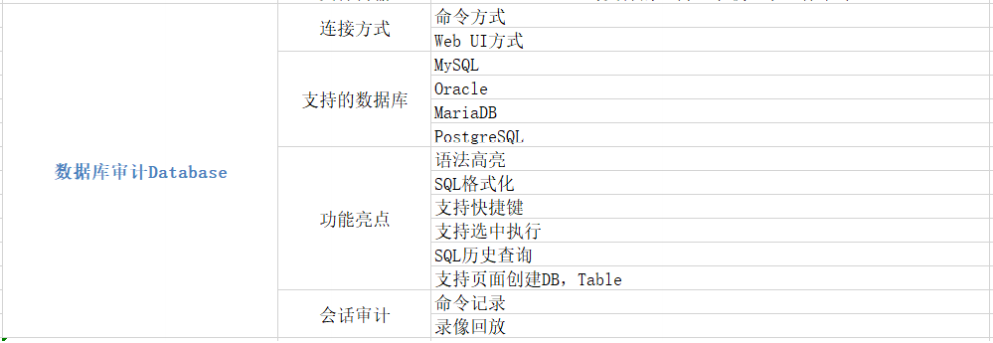
⚫ Application support: database, windows remote application, kubernetes.
4. Functions provided by JumpServer
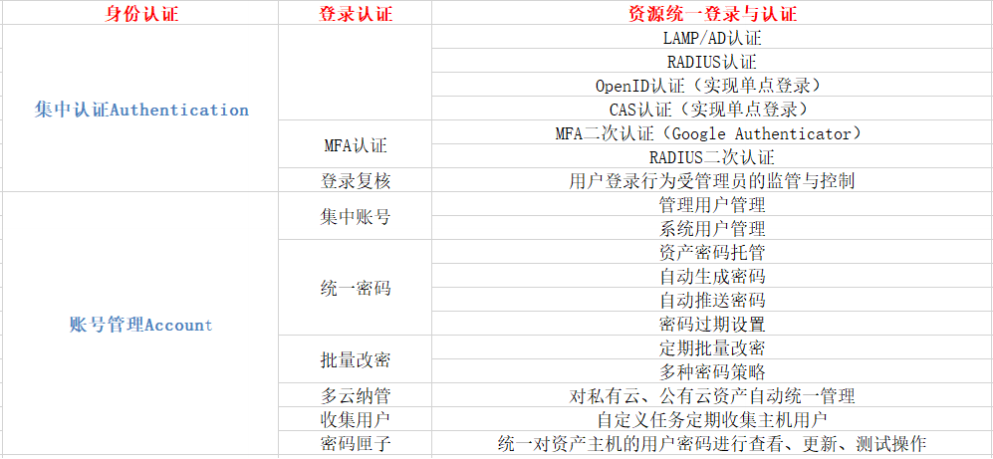
 Centralized account management
Centralized account management
It provides users with unified account management. The resources supporting management include mainstream operating systems, network devices and application systems. It can not only realize the basic functions contained in the account life cycle such as the creation, deletion and synchronization of managed resource accounts, but also set the account password policy, password strength and generation cycle through the platform.
Centralized authentication management
According to the actual needs of user applications, it can provide users with different strength authentication methods, which can not only maintain the original static password, but also provide high-strength authentication with two factor authentication methods (one-time password, digital integer, dynamic password), but also integrate other existing new authentication methods such as biological characteristics. It can not only realize the unified management of user authentication, but also provide users with a unified authentication portal and realize the single sign on of enterprise information resource access.
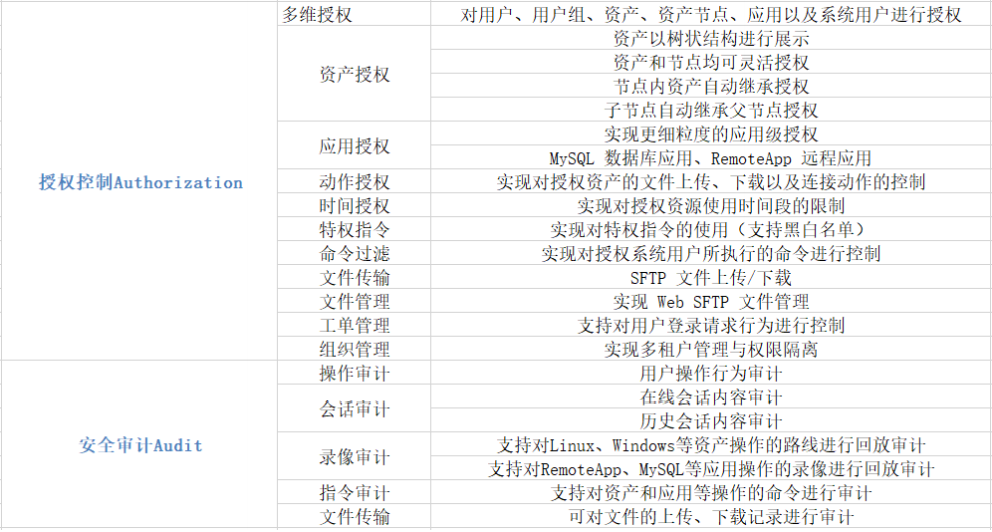
Centralized Authorization management
Users' resource access rights can be controlled centrally. It can not only control the access rights of B/S and C/S application system resources, but also control the operation rights of database, host and network equipment. The resource control type includes B/S URL, C/S function module, database data, records and operation commands, IP address and port of host and network equipment.
Centralized Audit management
Centralized record management and analysis of all user operation logs can not only monitor user behavior, but also conduct data mining through centralized audit data, so as to facilitate the identification of safety accident responsibility afterwards.
6. Environmental planning
| OS | IP address | host name | Installation services |
|---|---|---|---|
| CentOS7.5 | 192.168.8.2 | jump-server | docker-ce |
| CentOS7.5 | 192.168.8.3 | node-01 | |
| CentOS7.5 | 192.168.8.4 | node-02 |
7. Container deployment jumpserver (version 2.8.4)
7.1 basic environment configuration
hostname jumpserver systemctl stop firewalld systemctl disable firewalld setenforce 0
7.2 installing docker environment
[root@jumpserver ~]# cd /etc/yum.repos.d/
[root@jumpserver yum.repos.d]# wget https://mirrors.aliyun.com/dockerce/linux/centos/docker-ce.repo
[root@jumpserver yum.repos.d]# yum clean all && yum makecache fast
[root@jumpserver ~]# yum -y install docker-ce
[root@jumpserver ~]# systemctl enable --now docker
Configure mirror accelerator
https://dockerhub.azk8s.cn //Azuer China image
https://hub-mirror.c.163.com / / Netease cloud accelerator
[root@jumpserver ~]# cat << EOF >> /etc/docker/daemon.json
{ "registry-mirrors": [
"https://e815eh6a.mirror.aliyuncs.com",
"https://hub-mirror.c.163.com"
]
}
EOF
[root@jumpserver ~]# systemctl daemon-reload
[root@jumpserver ~]# systemctl restart docker
7.3 installing jumpserver
7.3.1 randomly generate encryption key
[root@jump-server ~]# if [ "$SECRET_KEY" = "" ]; then SECRET_KEY=`cat /dev/urandom | tr -dc A-Za-z0-9 | head -c 50`; echo "SECRET_KEY=$SECRET_KEY" >> ~/.bashrc; echo $SECRET_KEY; else echo $SECRET_KEY; fi CWL1znY9BnphHHMAW3YjLuSz765J8EaRnYFRl25CYGBqDimwBu [root@jump-server ~]# if [ "$BOOTSTRAP_TOKEN" = "" ]; then BOOTSTRAP_TOKEN=`cat /dev/urandom | tr -dc A-Za-z0-9 | head -c 16`; echo "BOOTSTRAP_TOKEN=$BOOTSTRAP_TOKEN" >> /.baserc; echo $BOOTSTRAP_TOKEN; else echo $BOOTSTRAP_TOKEN; fi h4o6qWnQgLyYCDmZ
7.3.2 deploying jumpserver
[root@jump-server ~]# docker run -itd \ --name jumpserver \ --restart=always \ -p 80:80 -p 2222:2222 \ -e SECRET_KEY=CWL1znY9BnphHHMAW3YjLuSz765J8EaRnYFRl25CYGBqDimwBu \ -e BOOTSTRAP_TOKEN=h4o6qWnQgLyYCDmZ \ -v /opt/jumpserver/data/:/opt/jumpserver/data/ \ -v /opt/jumpserver/mysql/:/var/lib/mysql \ jumpserver/jms_all:v2.8.4 d5337a815cb8c28a4dd5c516ec1b8a9c1b31f8d58bd530925b85f3da9dd581d2 [root@jump-server ~]# docker ps -a CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES d5337a815cb8 jumpserver/jms_all:v2.8.4 "./entrypoint.sh" About a minute ago Up About a minute 0.0.0.0:80->80/tcp, :::80->80/tcp, 0.0.0.0:2222->2222/tcp, :::2222->2222/tcp jumpserver
7.3.3 accessing jumpserver Web interface
http://192.168.8.2 or http://192.168.8.2/ui
User: admin
Password: admin (the password needs to be changed for the first time)
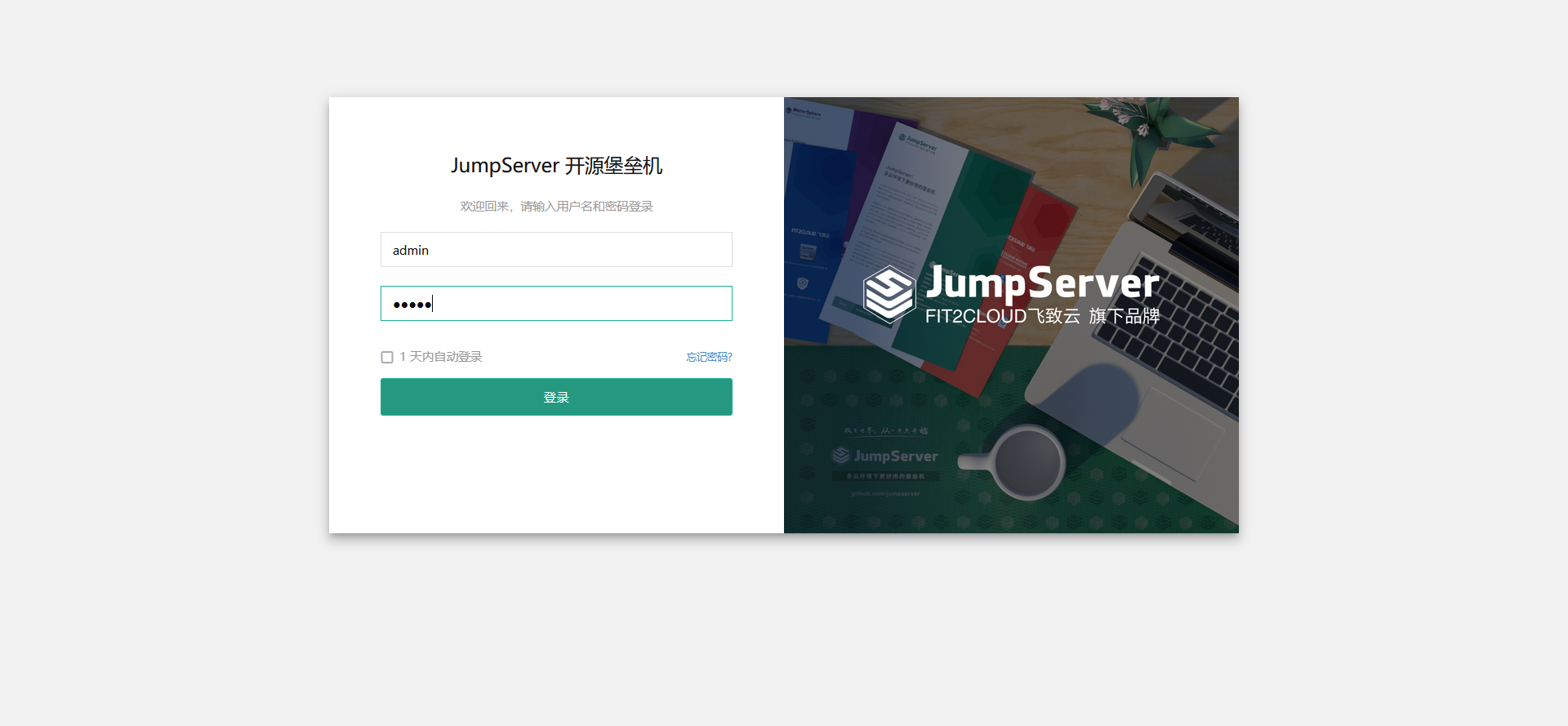
Reset the password and log in again
7.4 create JumpServer user groups and users
For security, we will reasonably plan jumpserver to manage users and groups.
7.4.1 create jumpserver user group
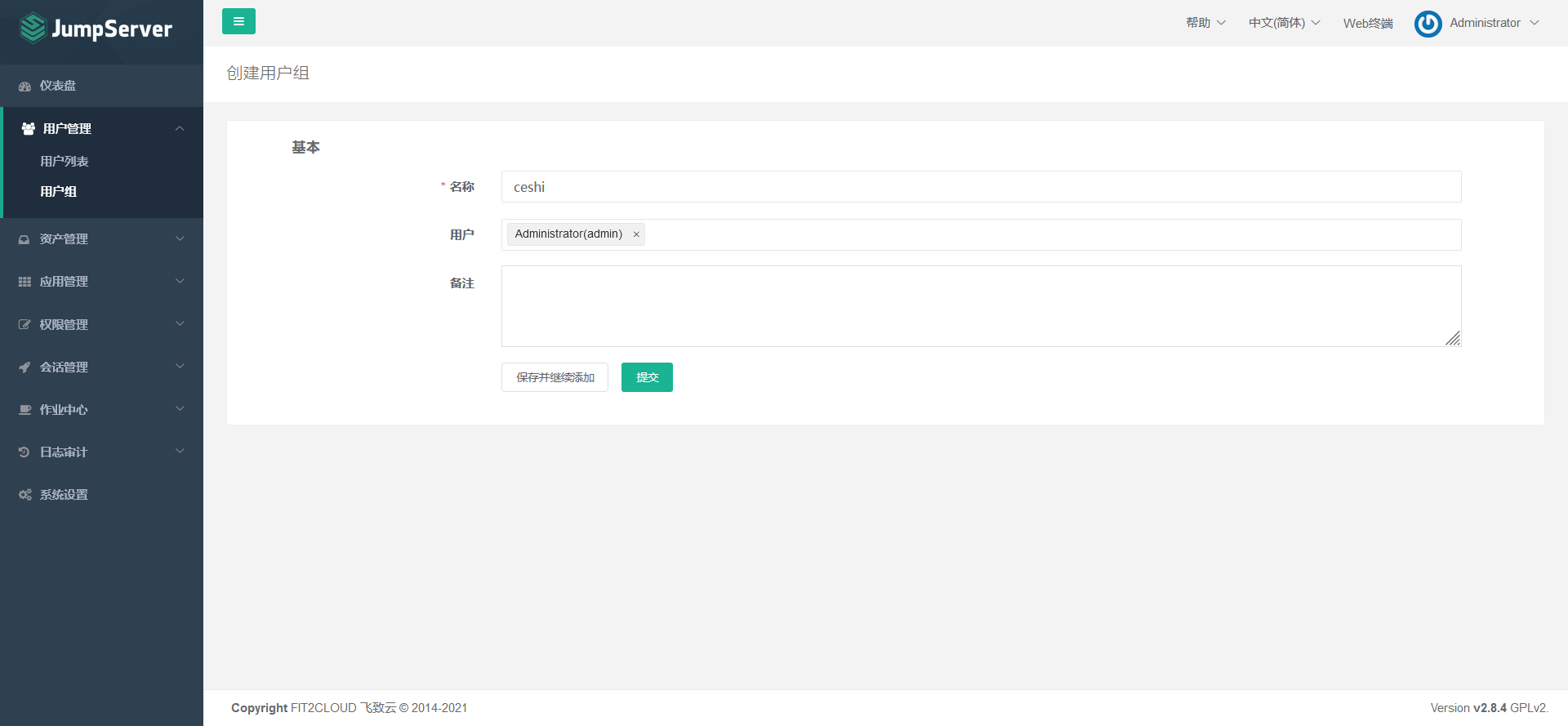
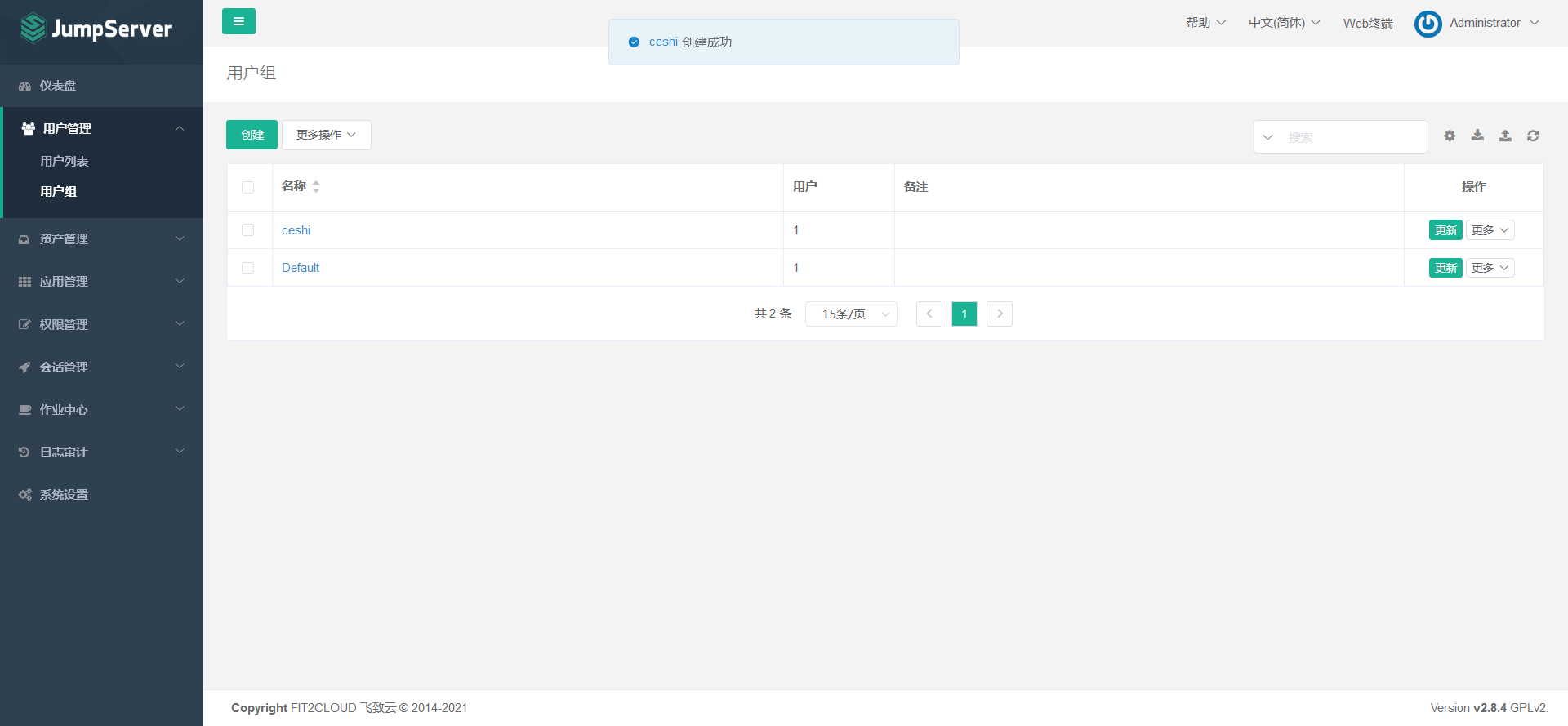
7.4.2 create jumpserver user
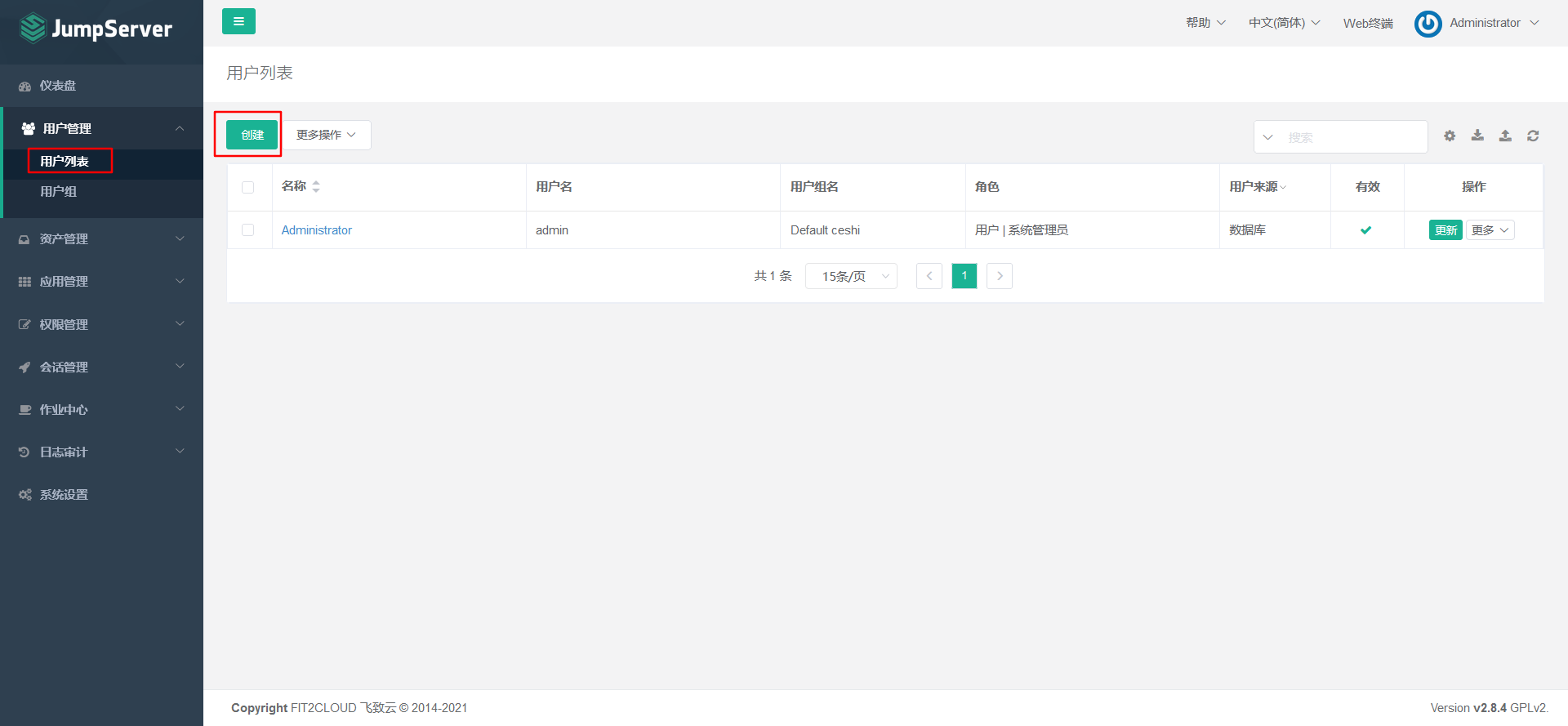
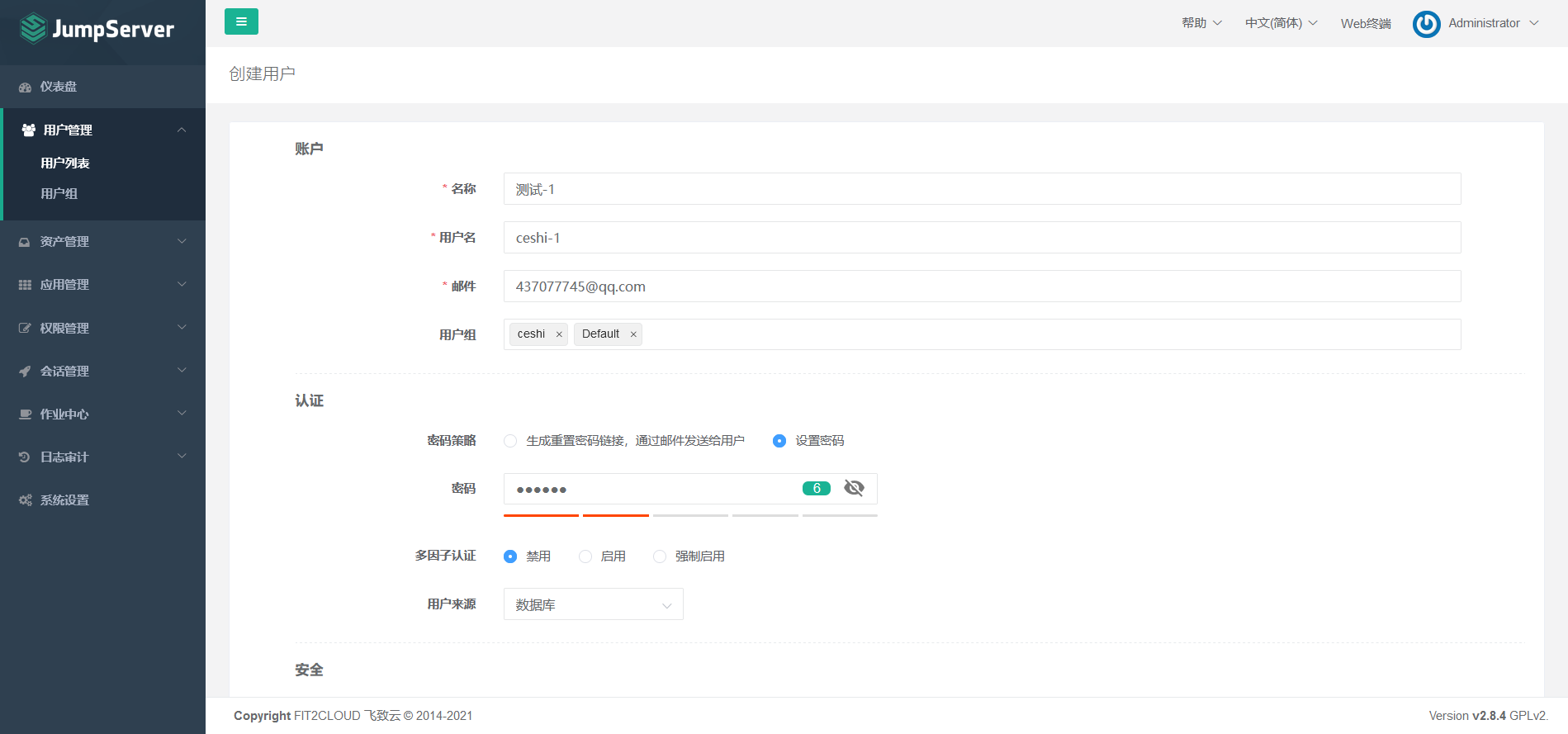
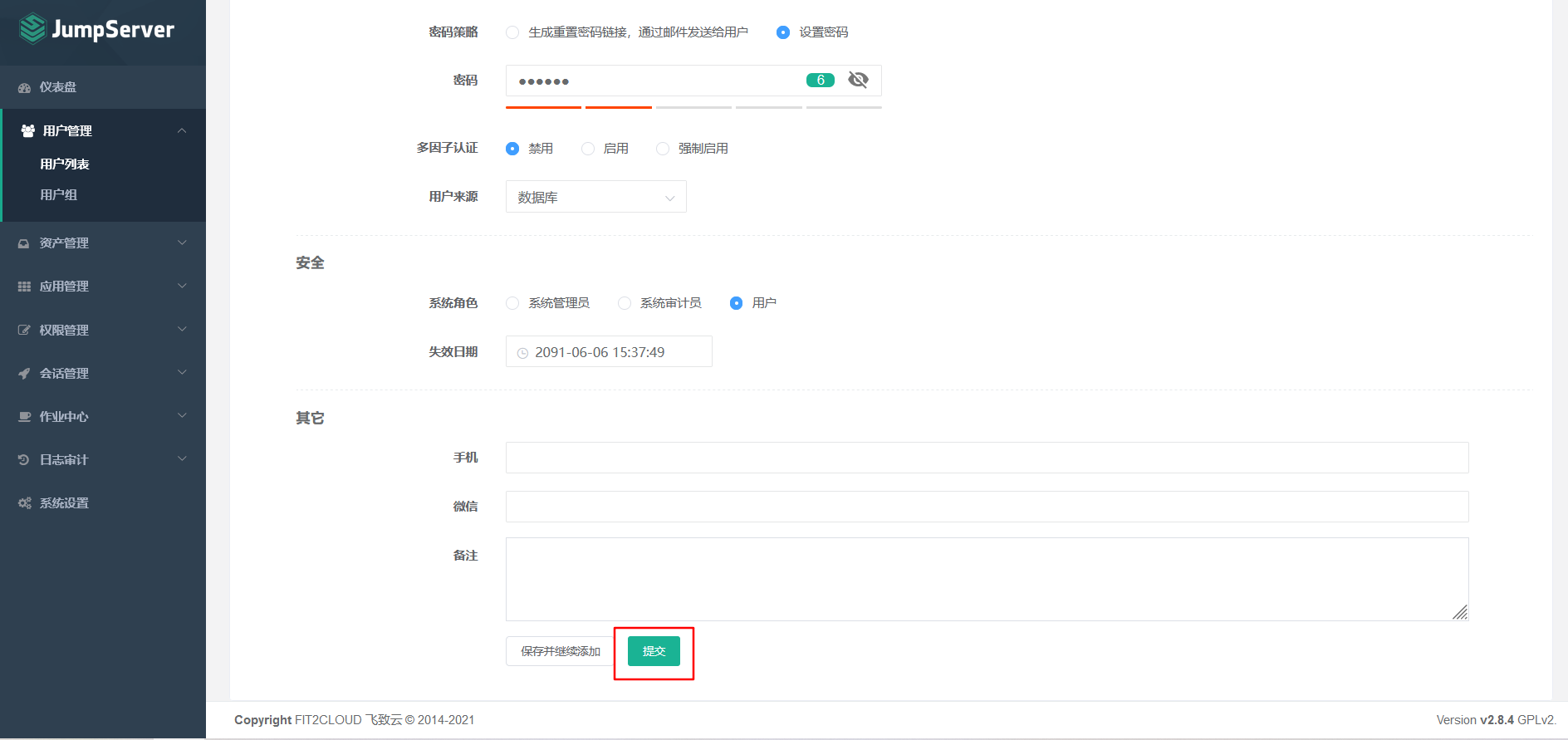
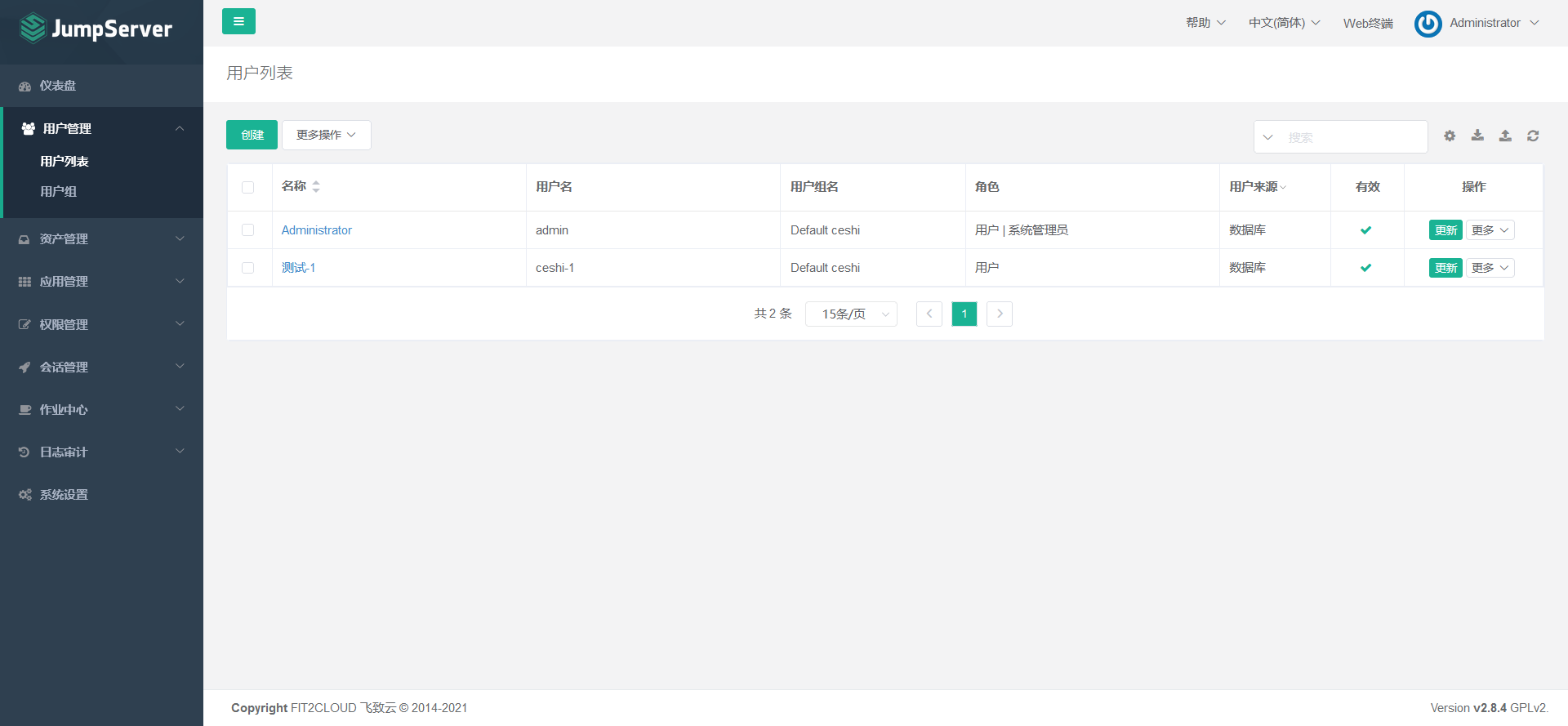
7.5 create and manage assets and asset authorization
General steps: create system user - > create management user - > Add asset - > asset authorization
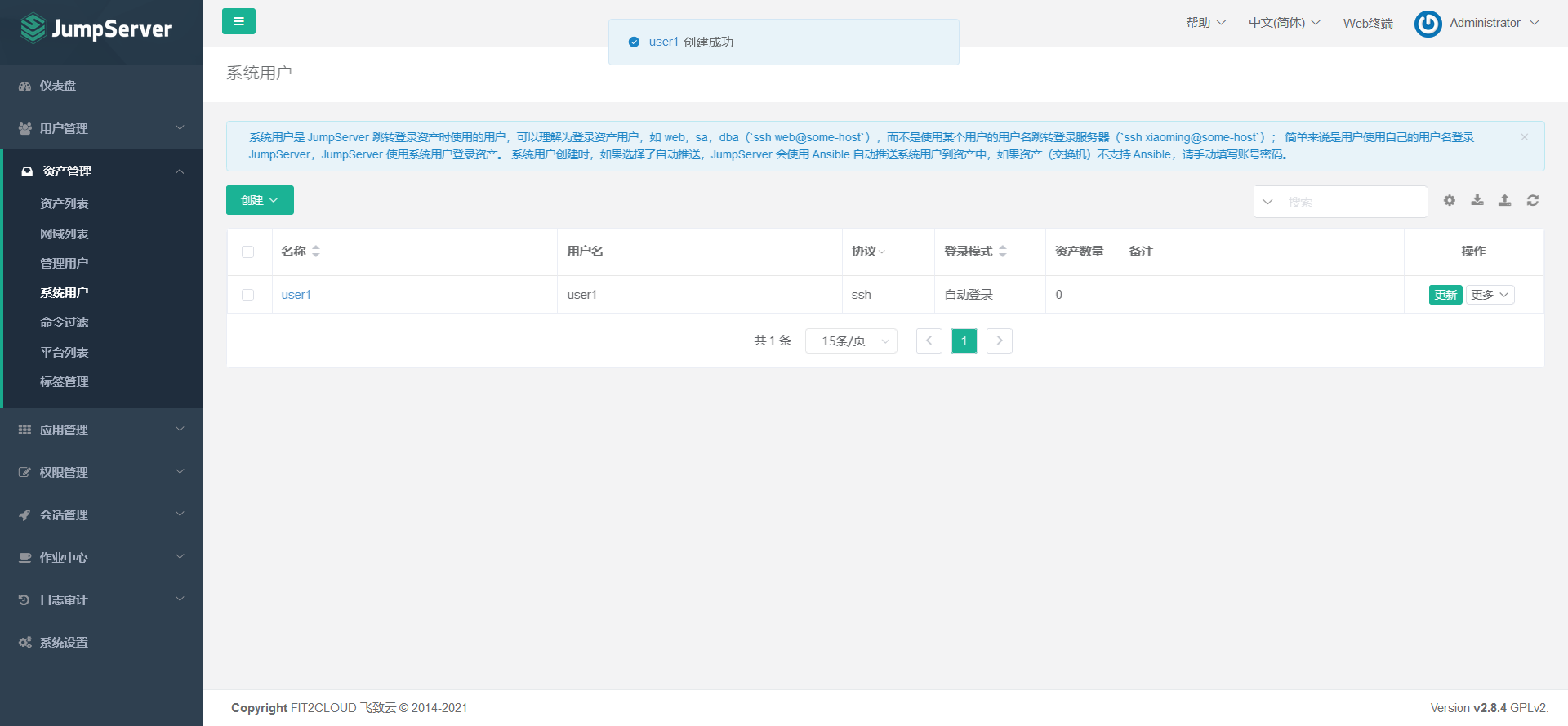
7.5.1 create system user (login asset user)
Explanation: the system user is the user used by jumpserver when jumping / logging in to the asset server. It is generally an ordinary user on the server. Of course, all asset services should also be used at the same time
There is this user in the. It can be understood that it is limited to users who log in to assets and have low permissions.
Select the protocol to use to create the system user, which must exist in the server.
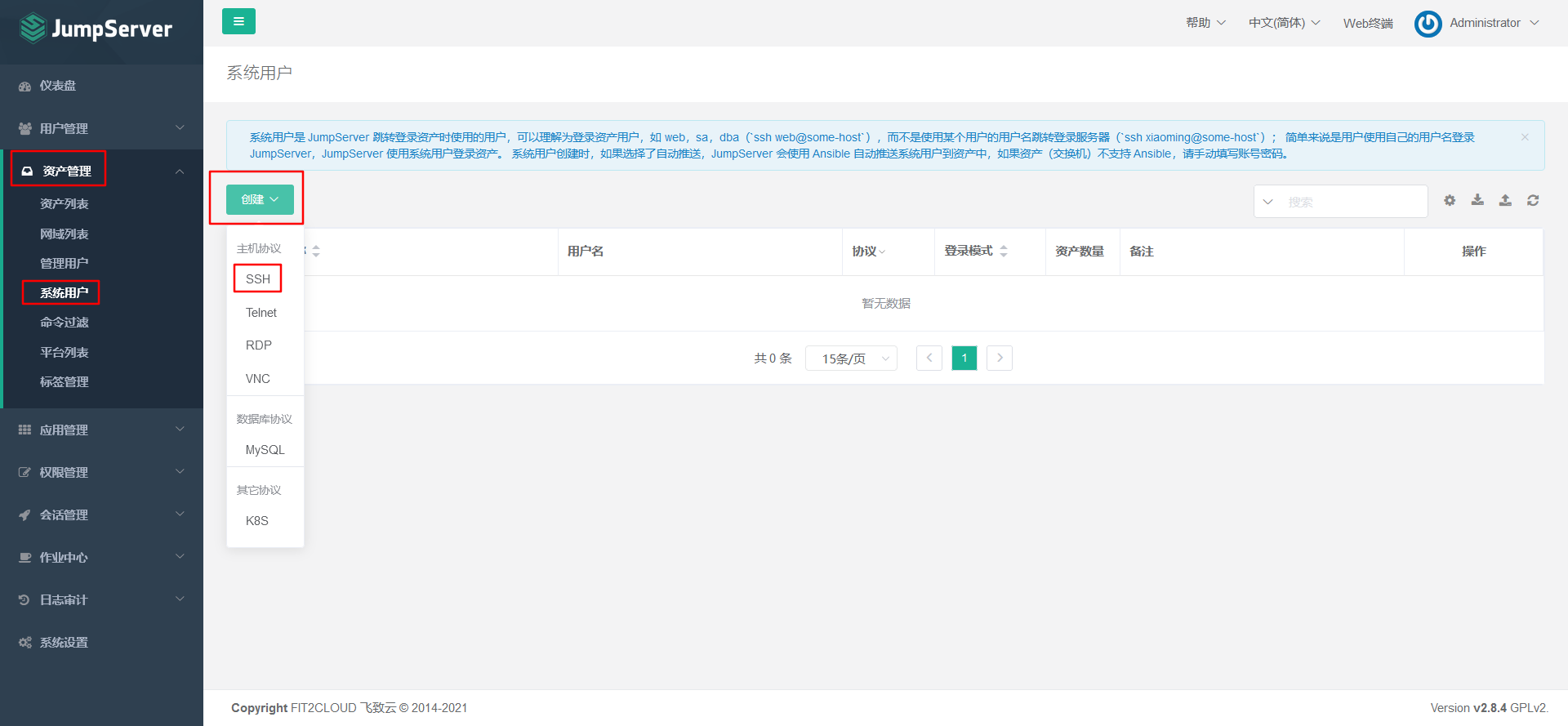
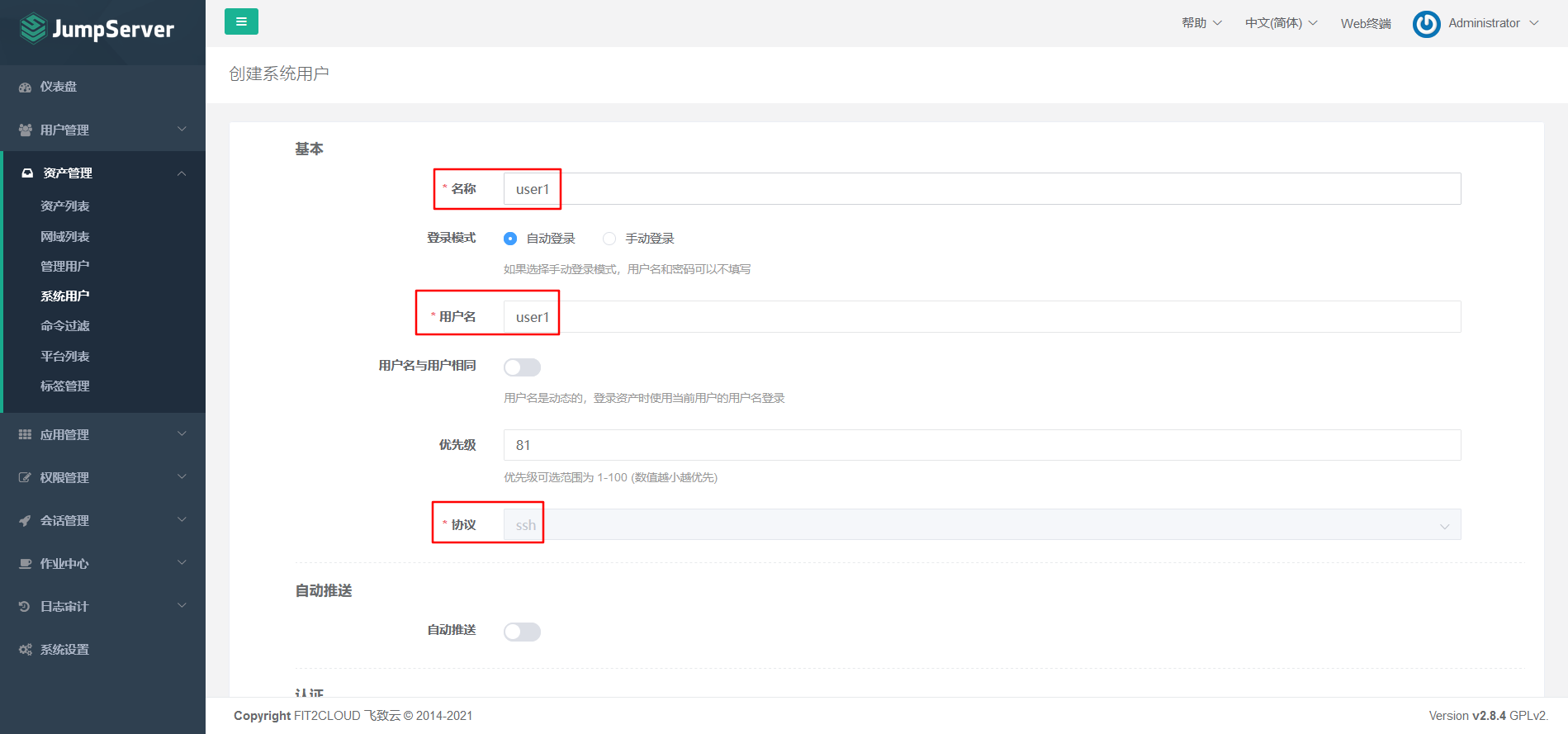
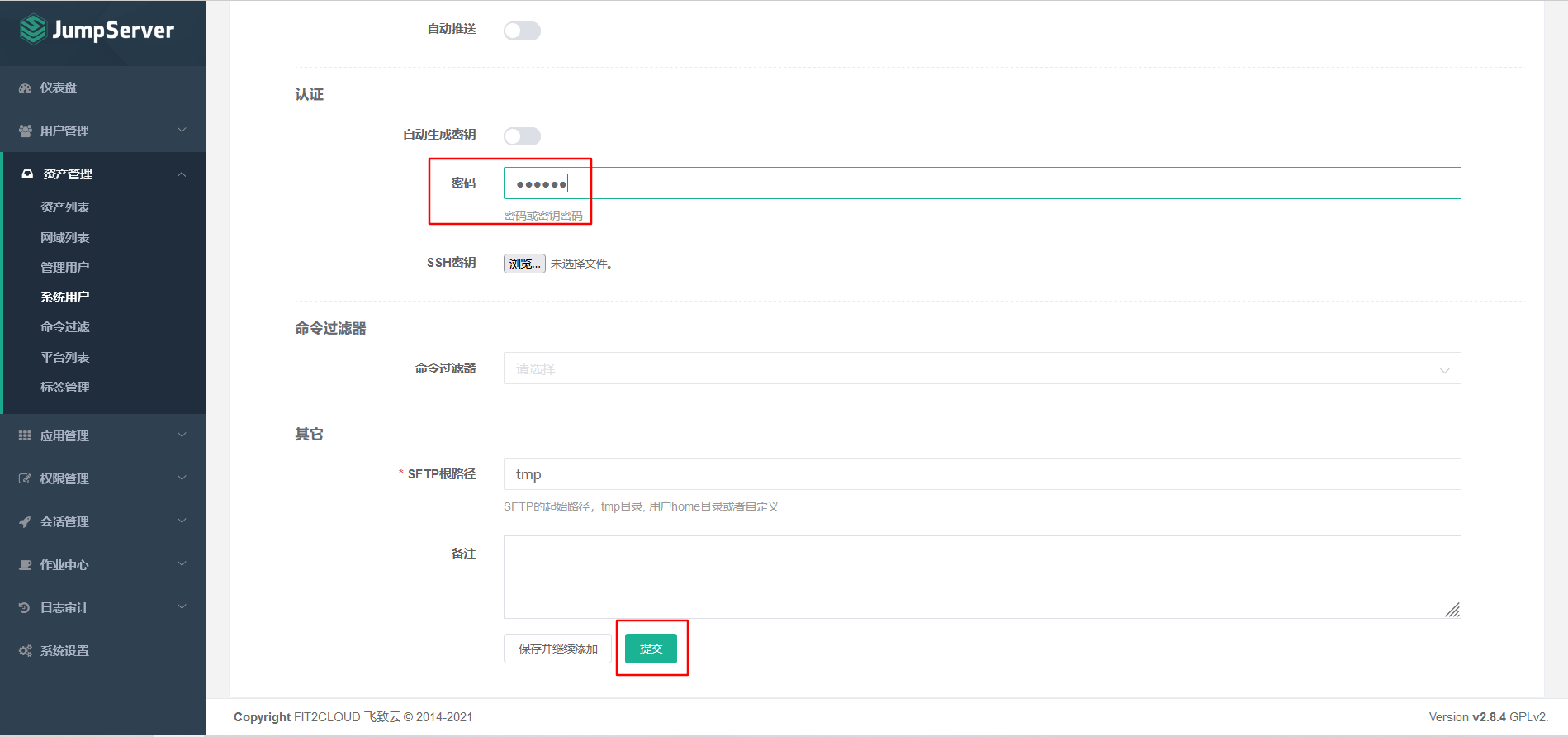
7.5.2 create management user
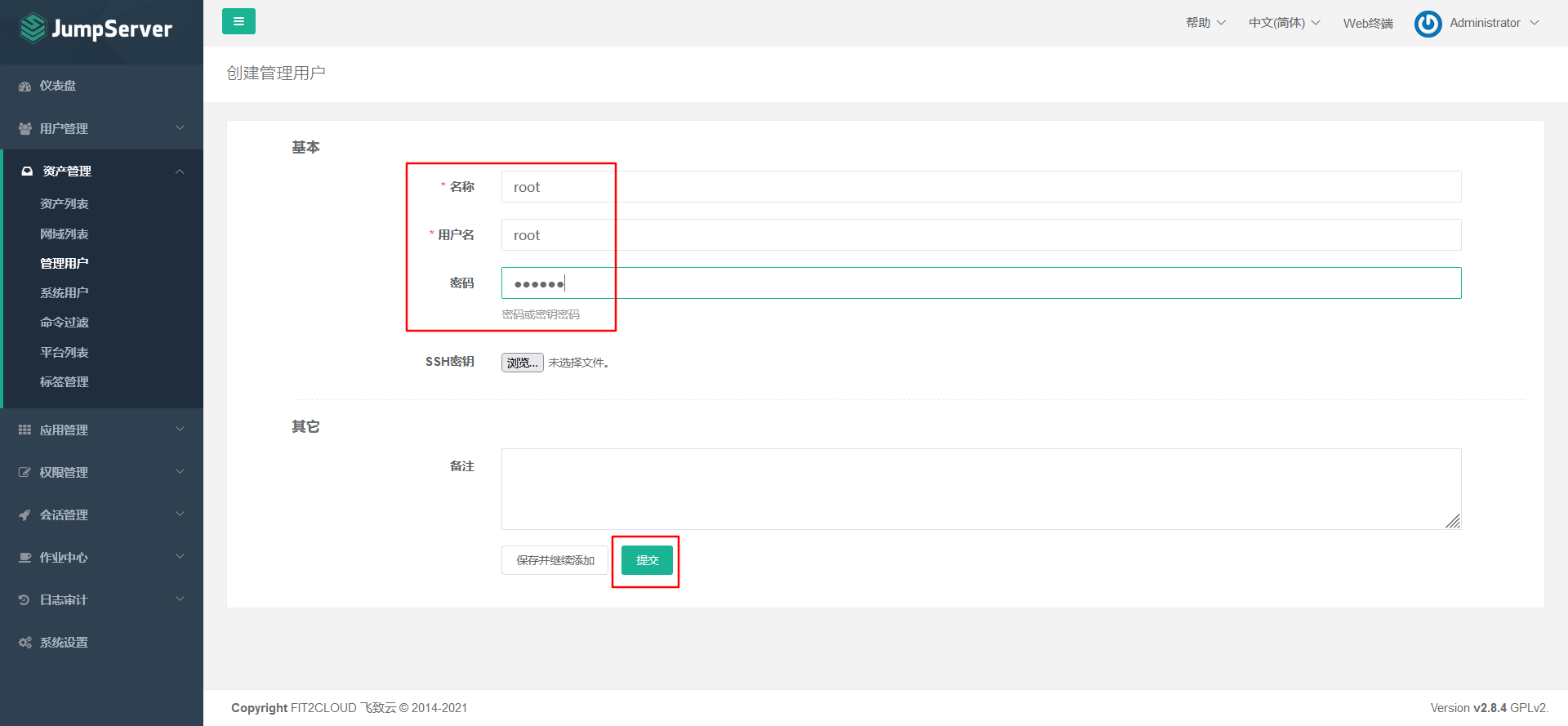
Explanation: the management user is the root on the asset (charged server), or has NOPASSWD: ALL
User with sudo privileges.
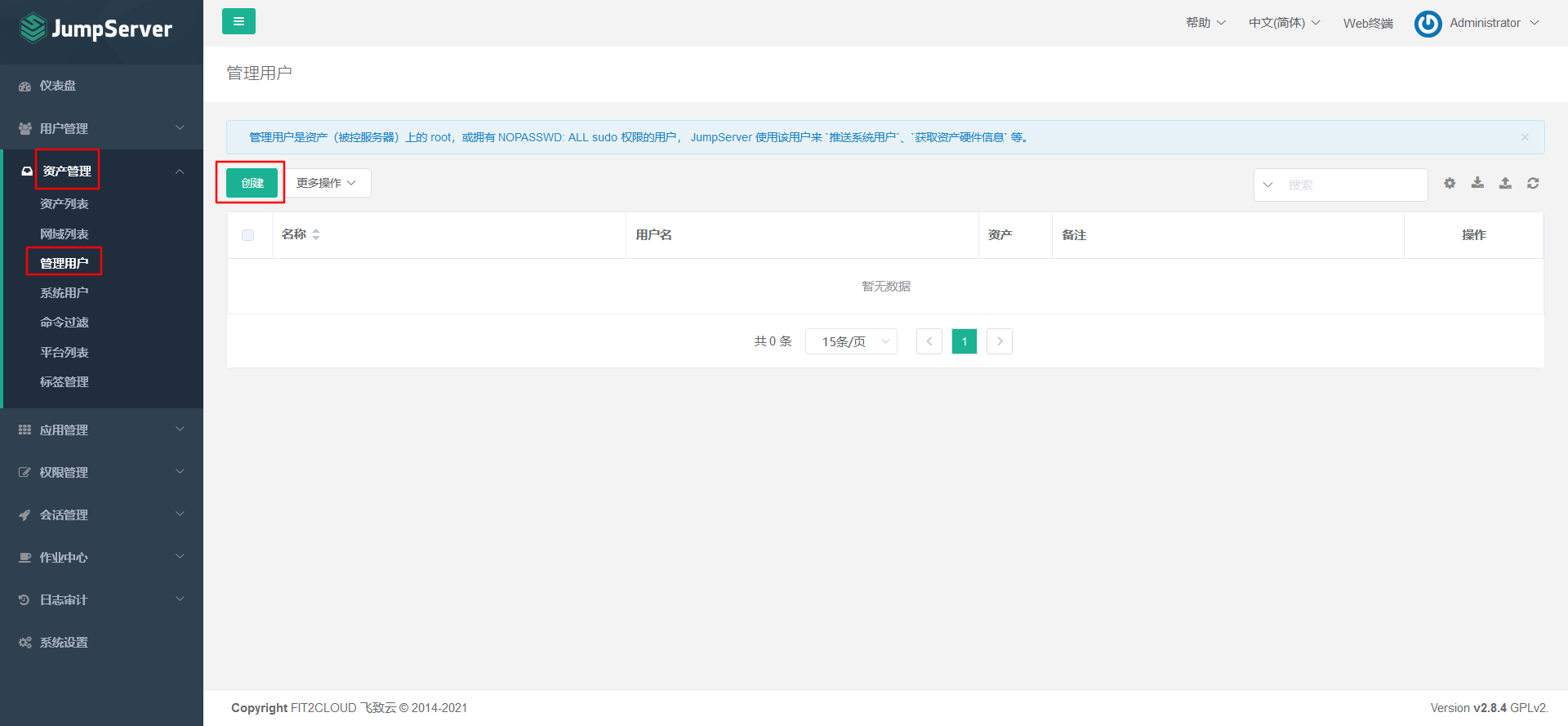
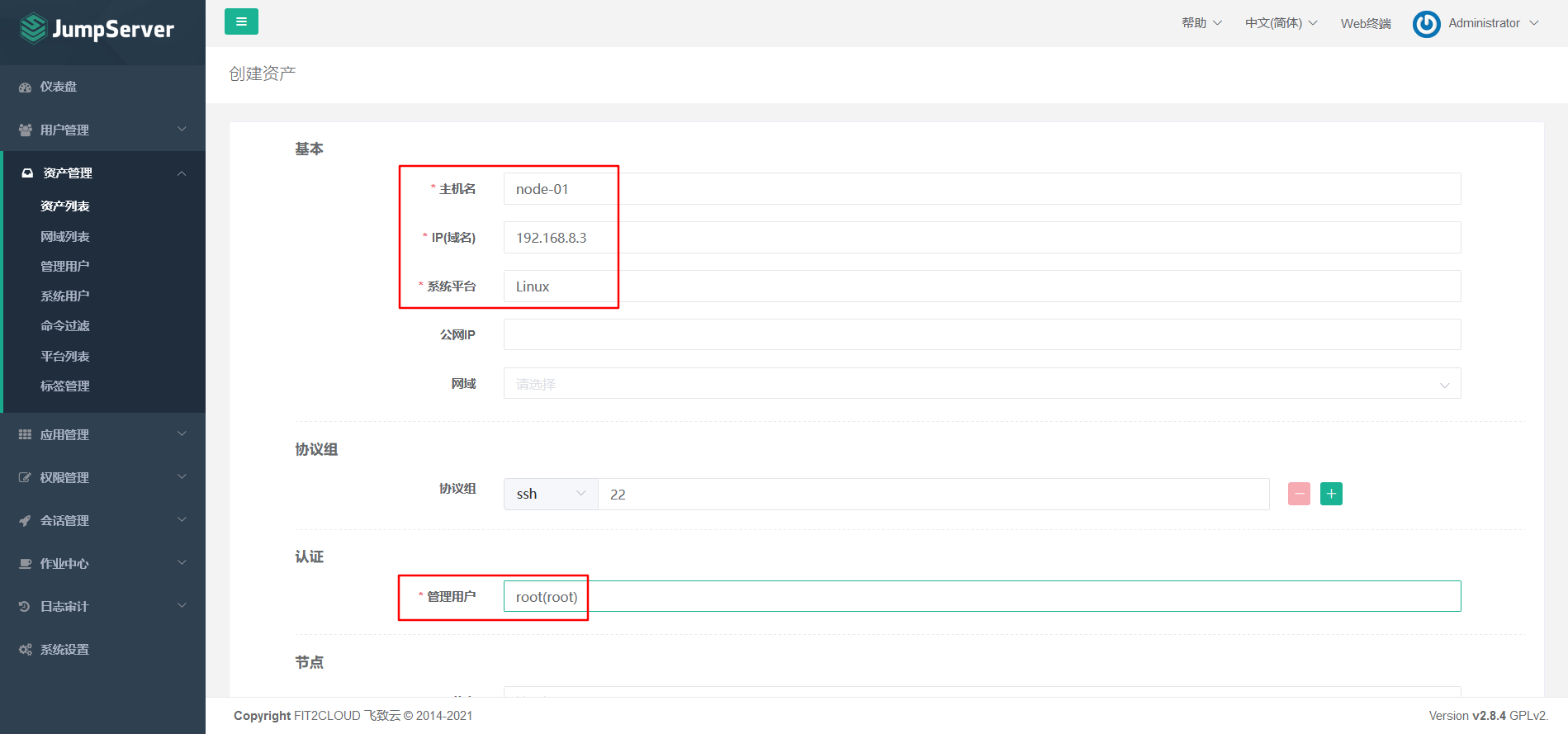
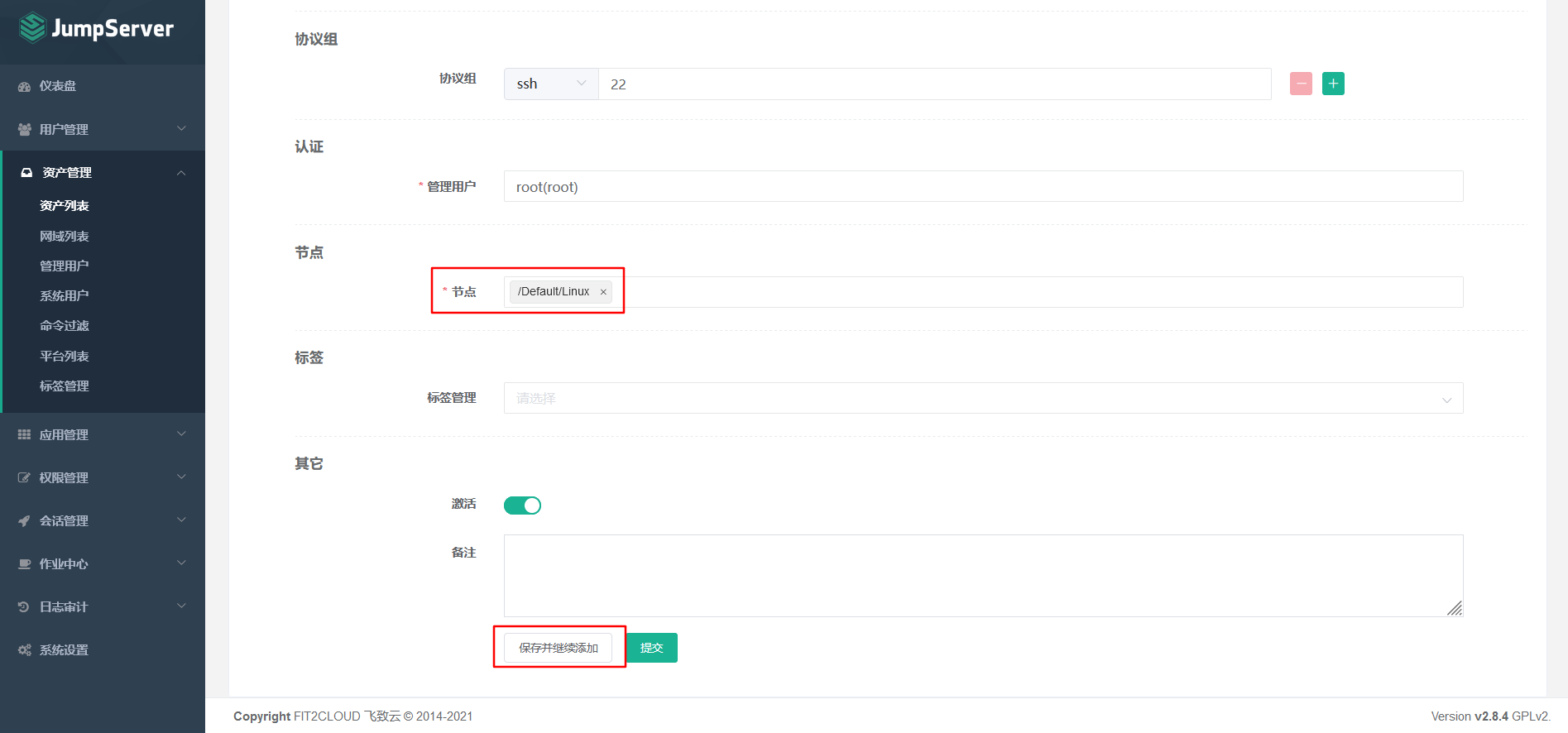
7.5.3 Adding Assets
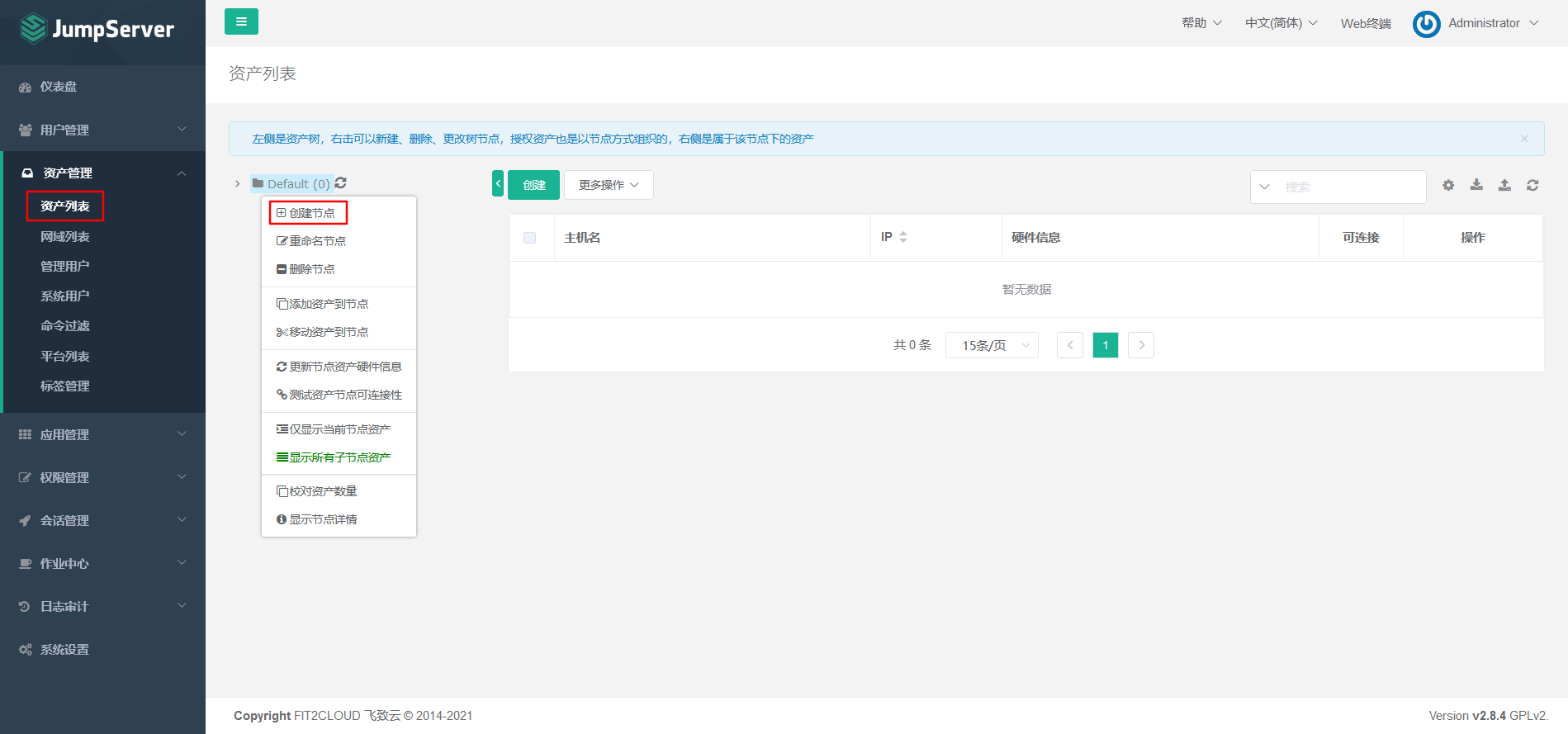
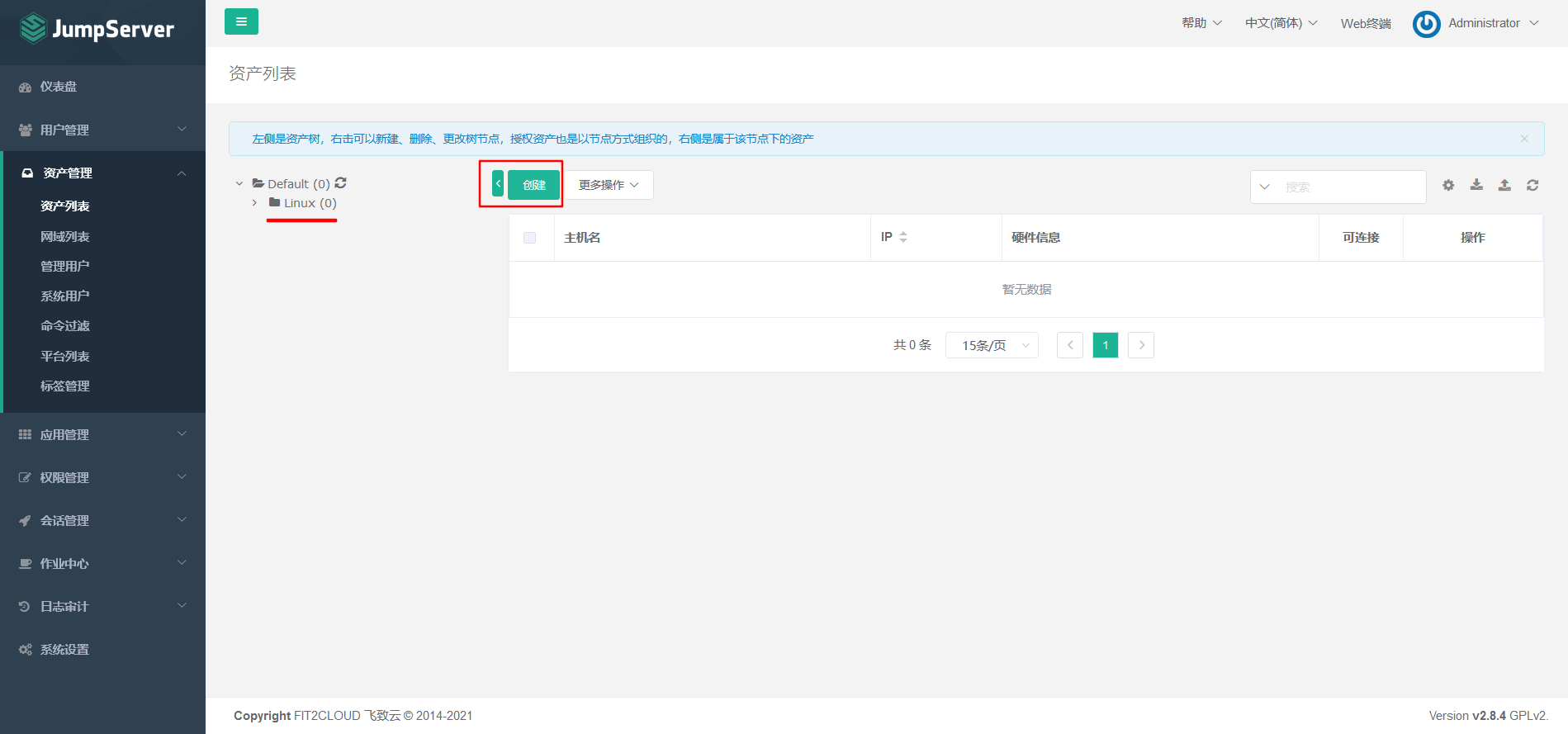 Asset 1: 192.168.8.3 node-01
Asset 1: 192.168.8.3 node-01
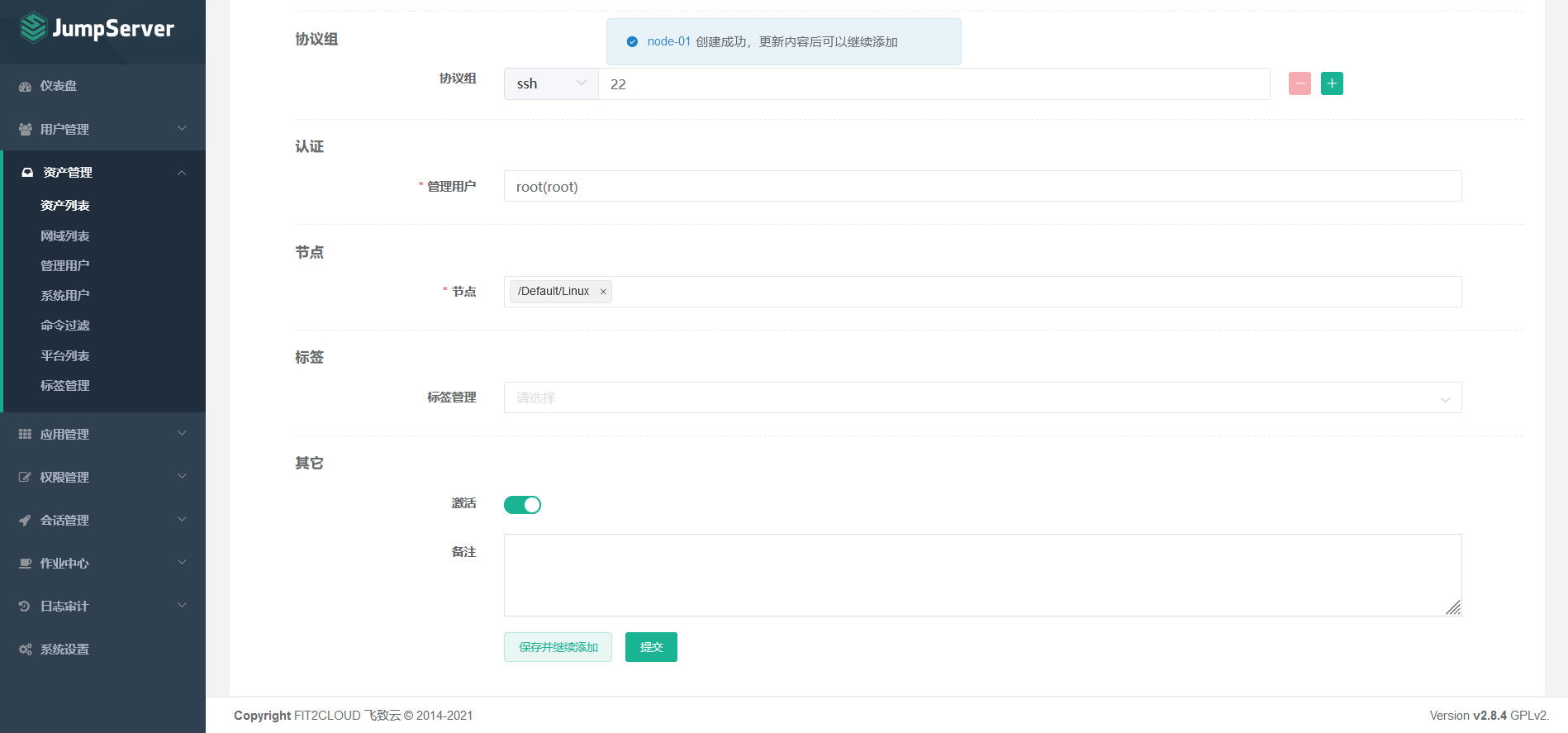 Asset 2: 192.168.8.4
Asset 2: 192.168.8.4
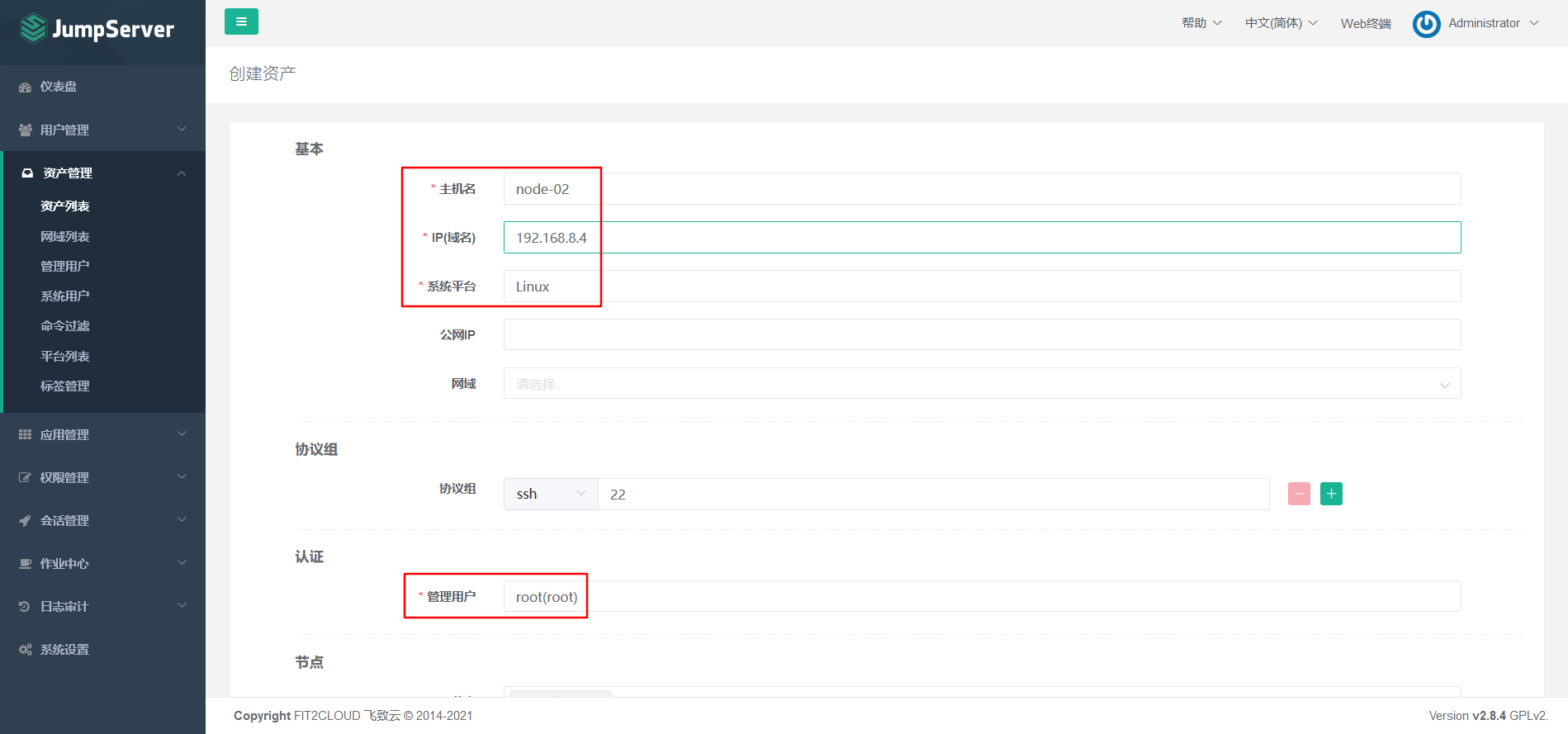
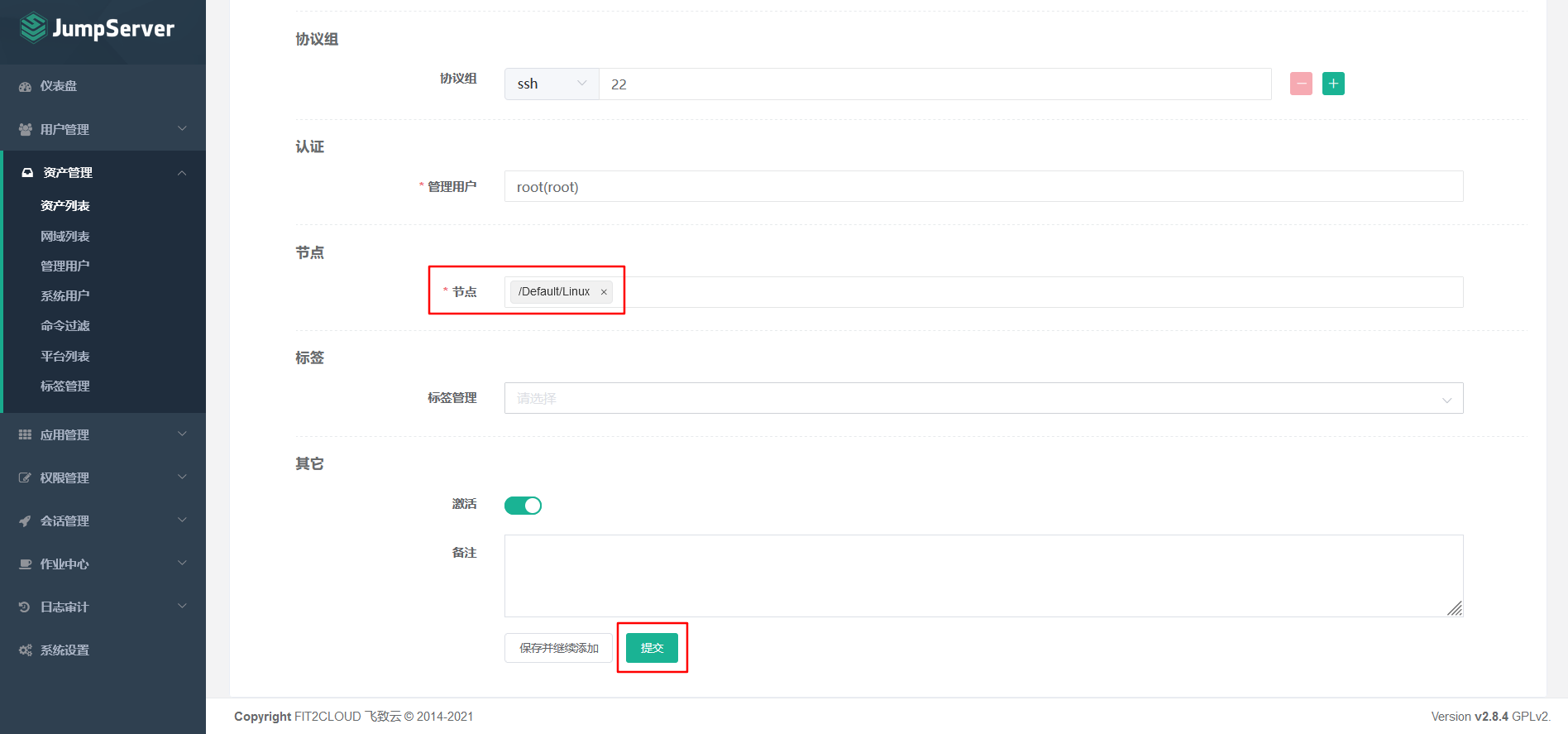
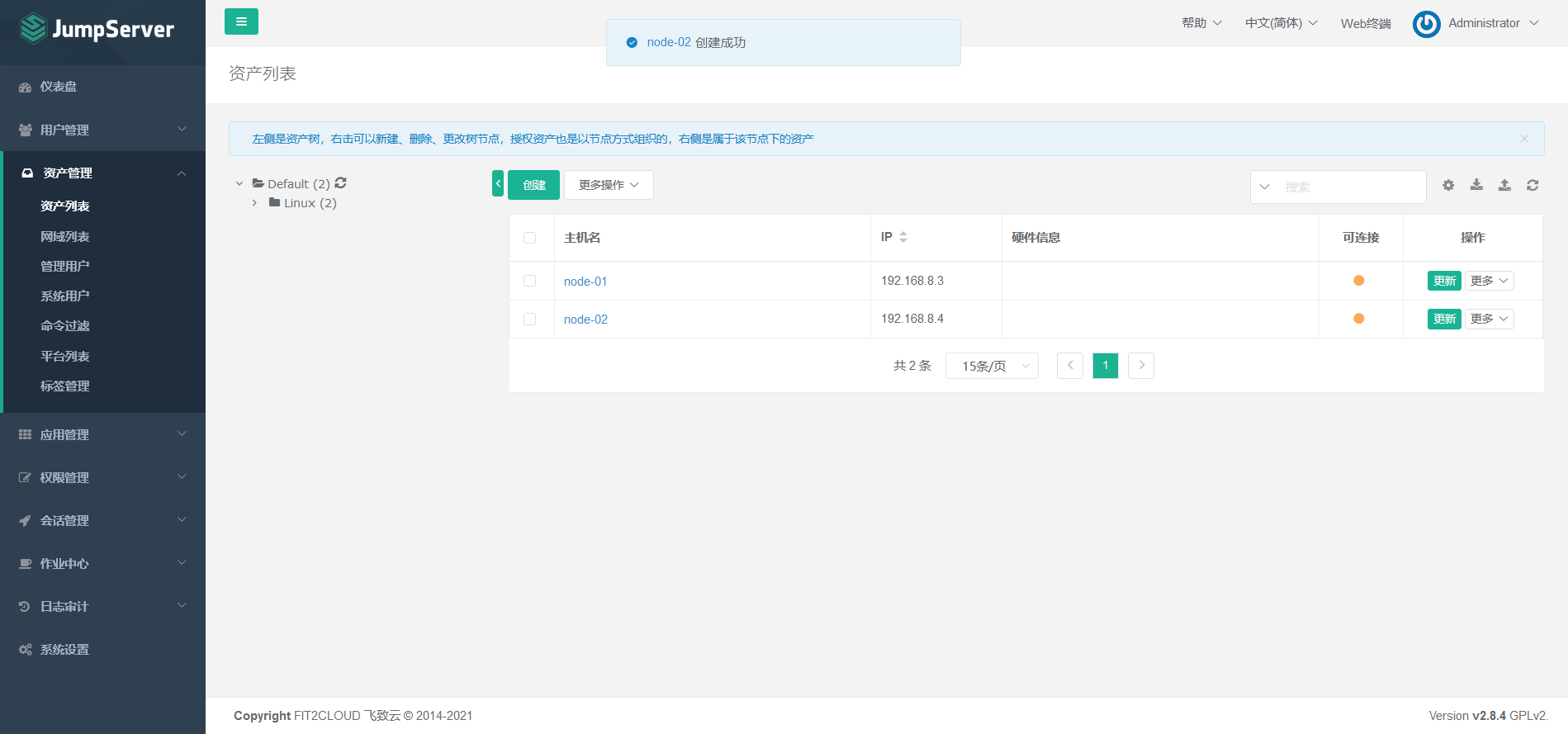
7.5.4 asset authorization
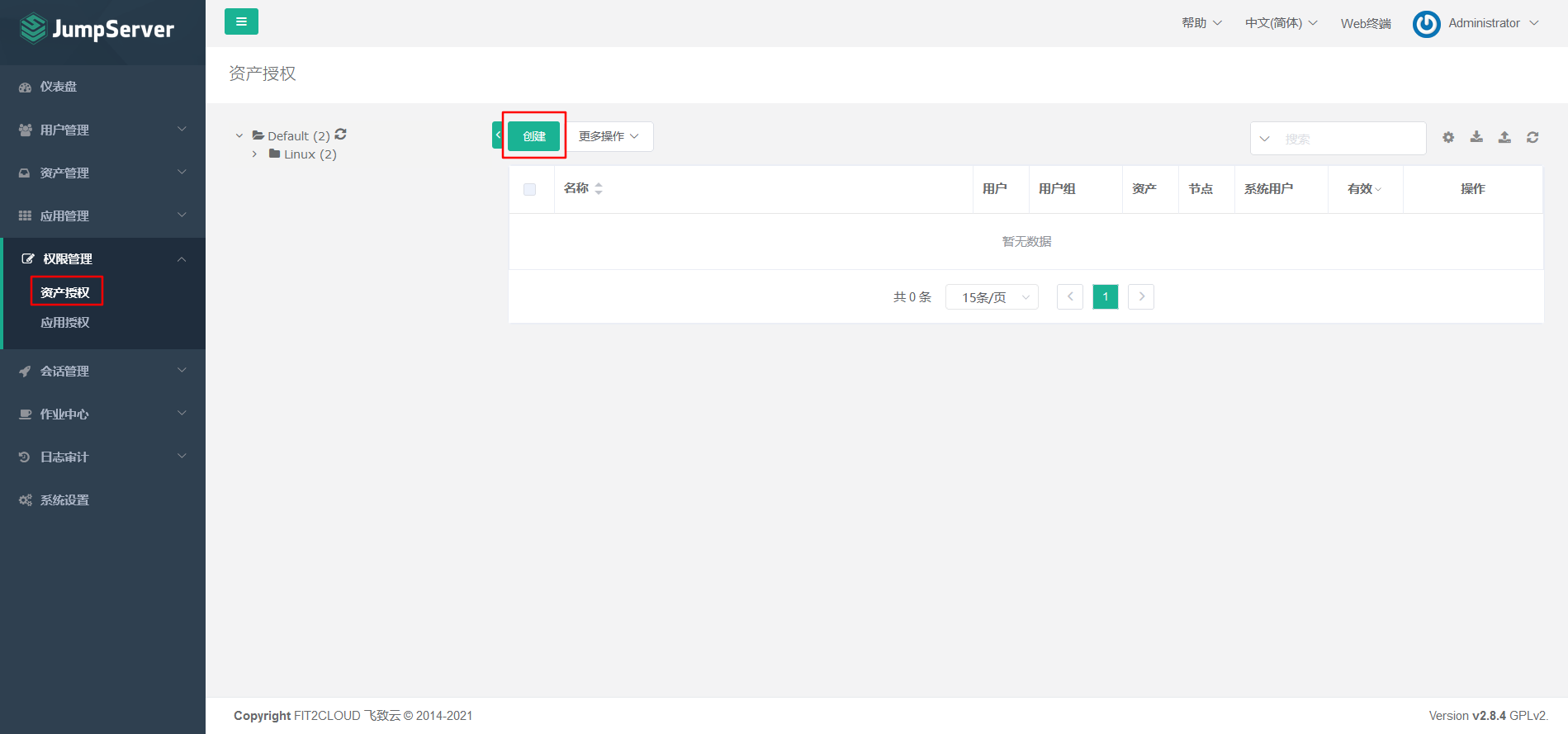
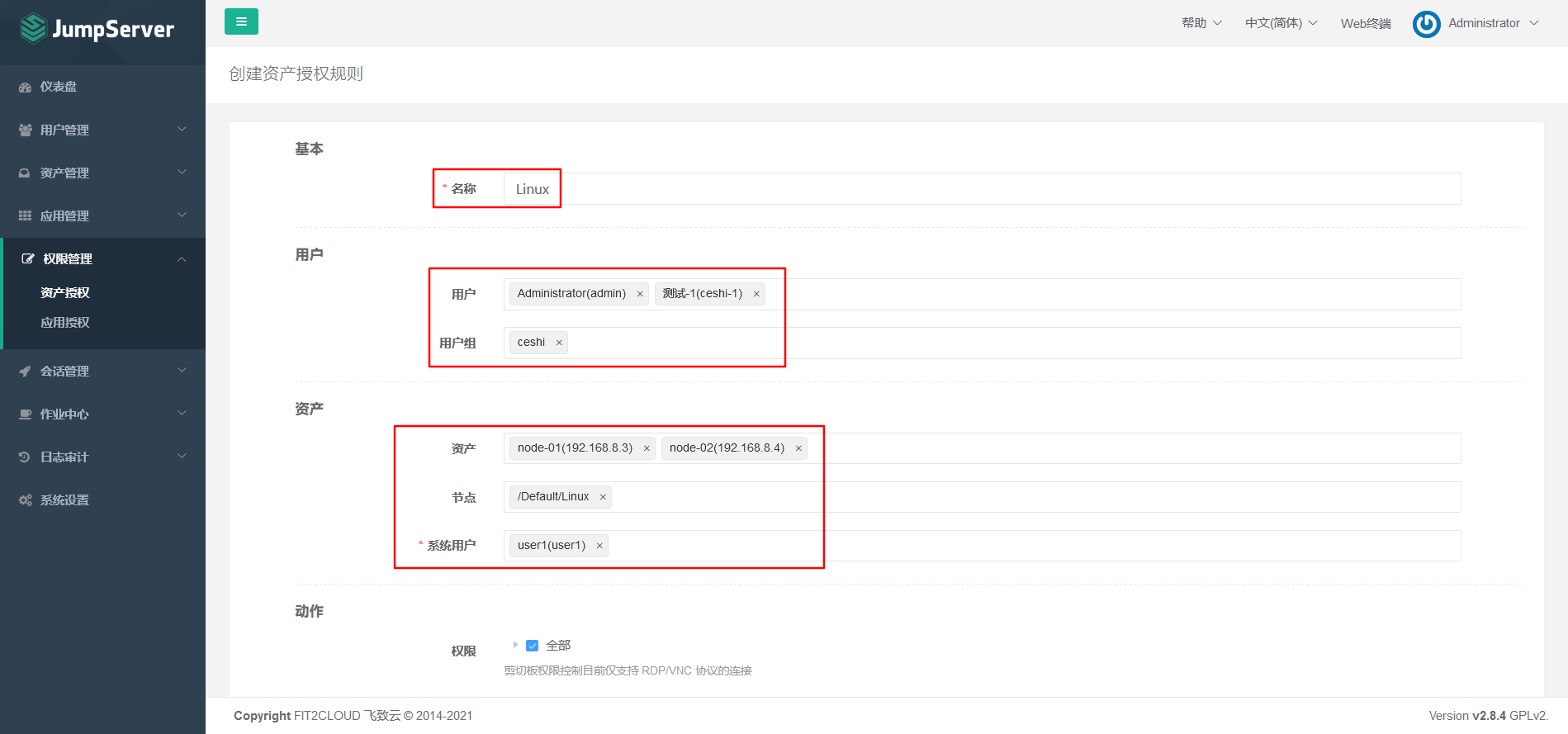
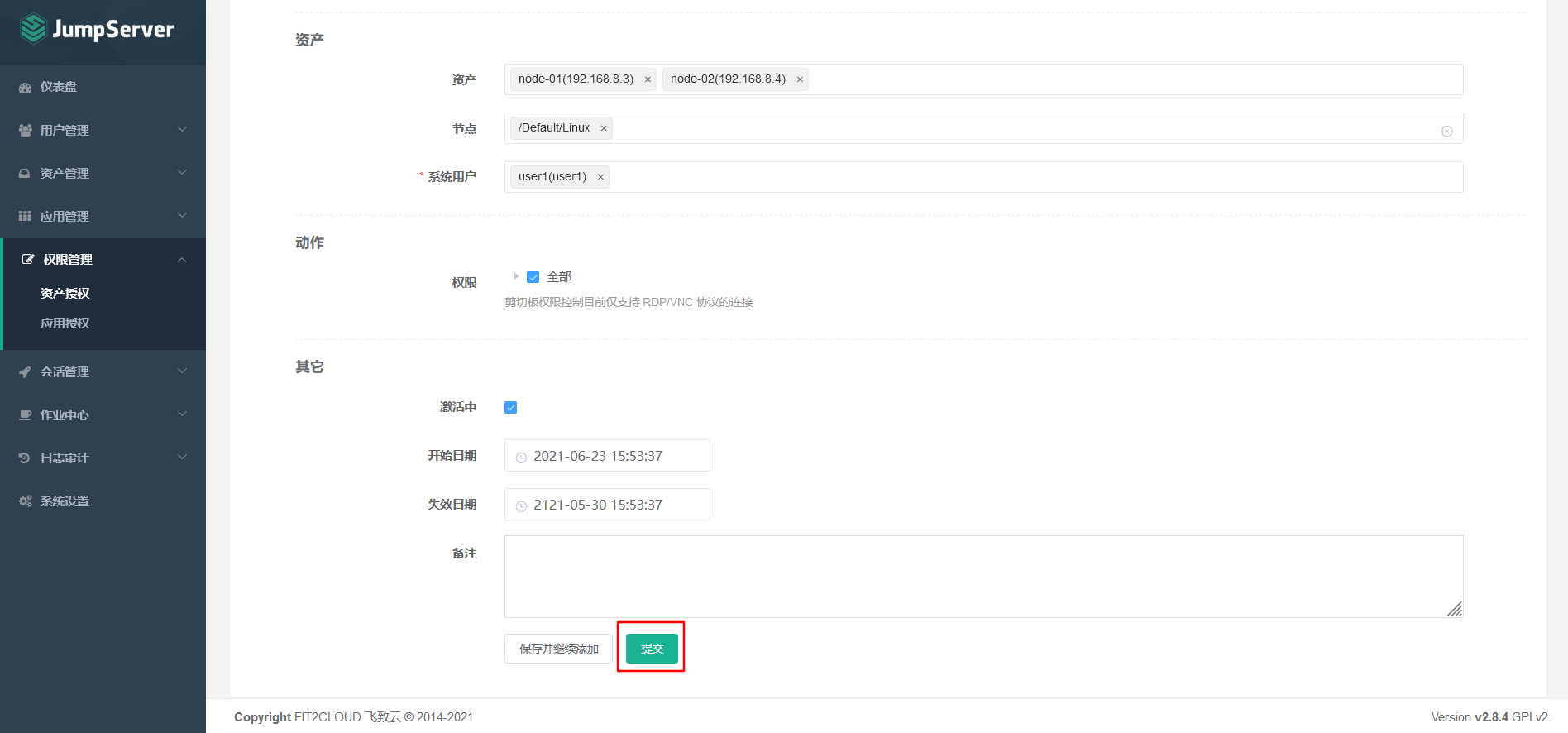
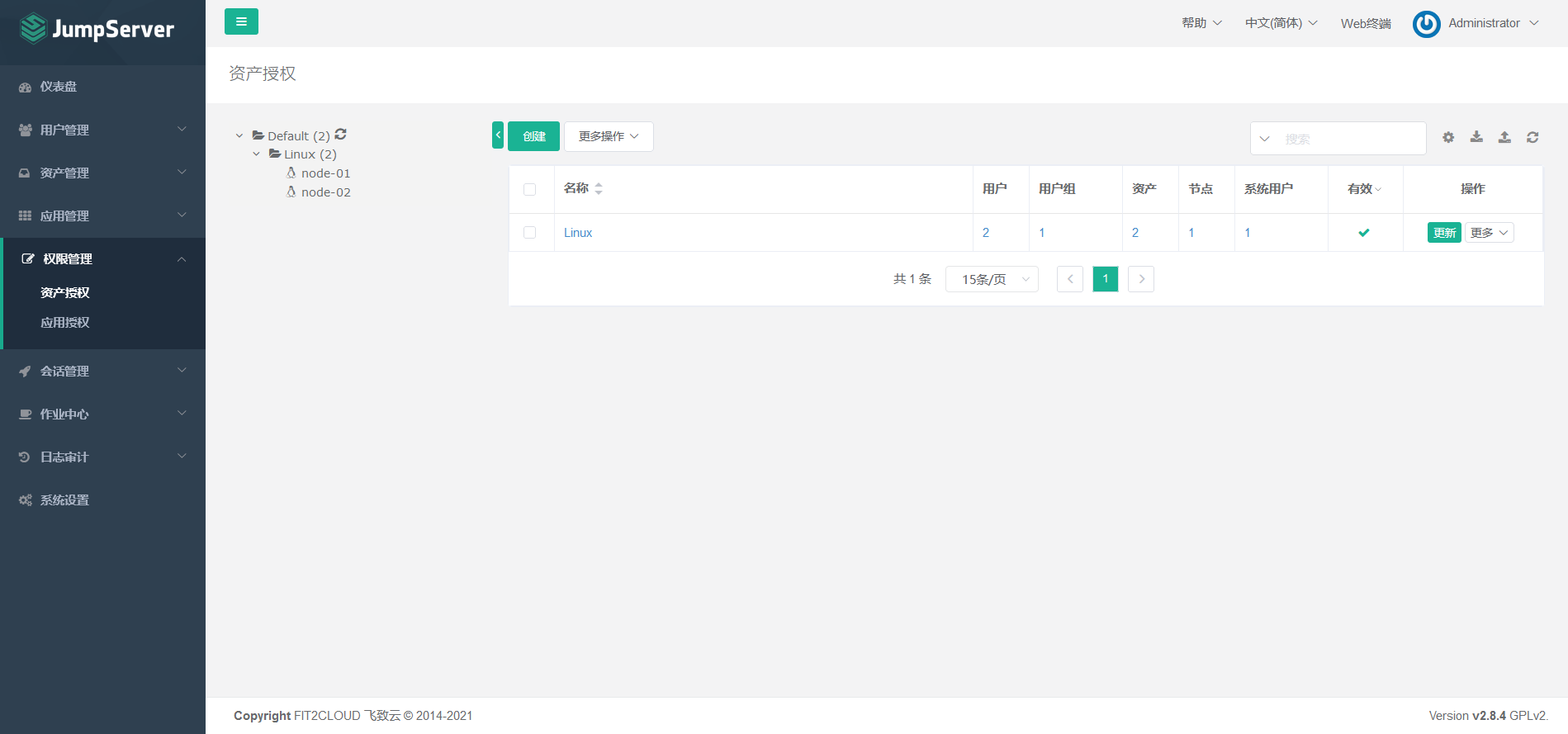
7.6 connecting the background server through the Web terminal
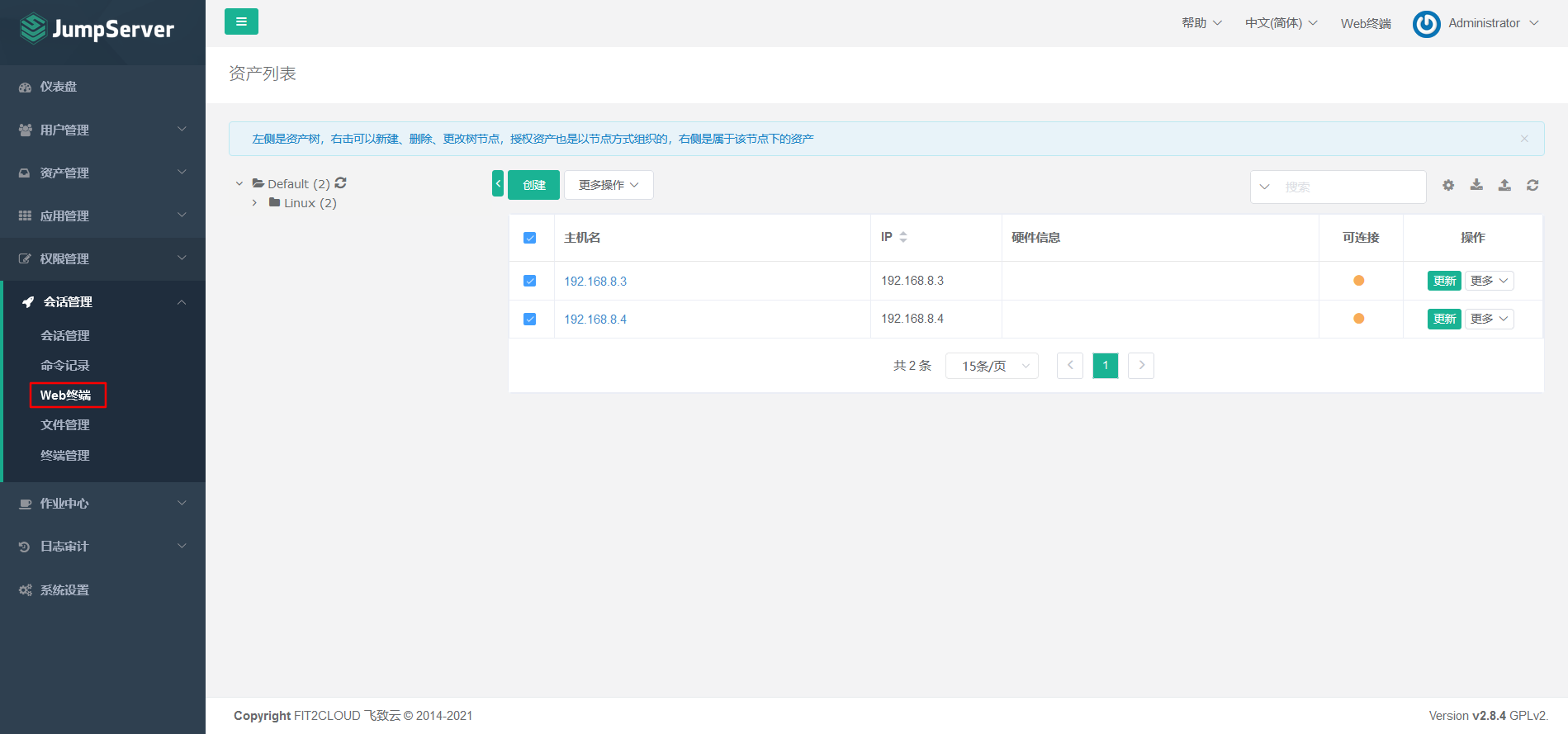
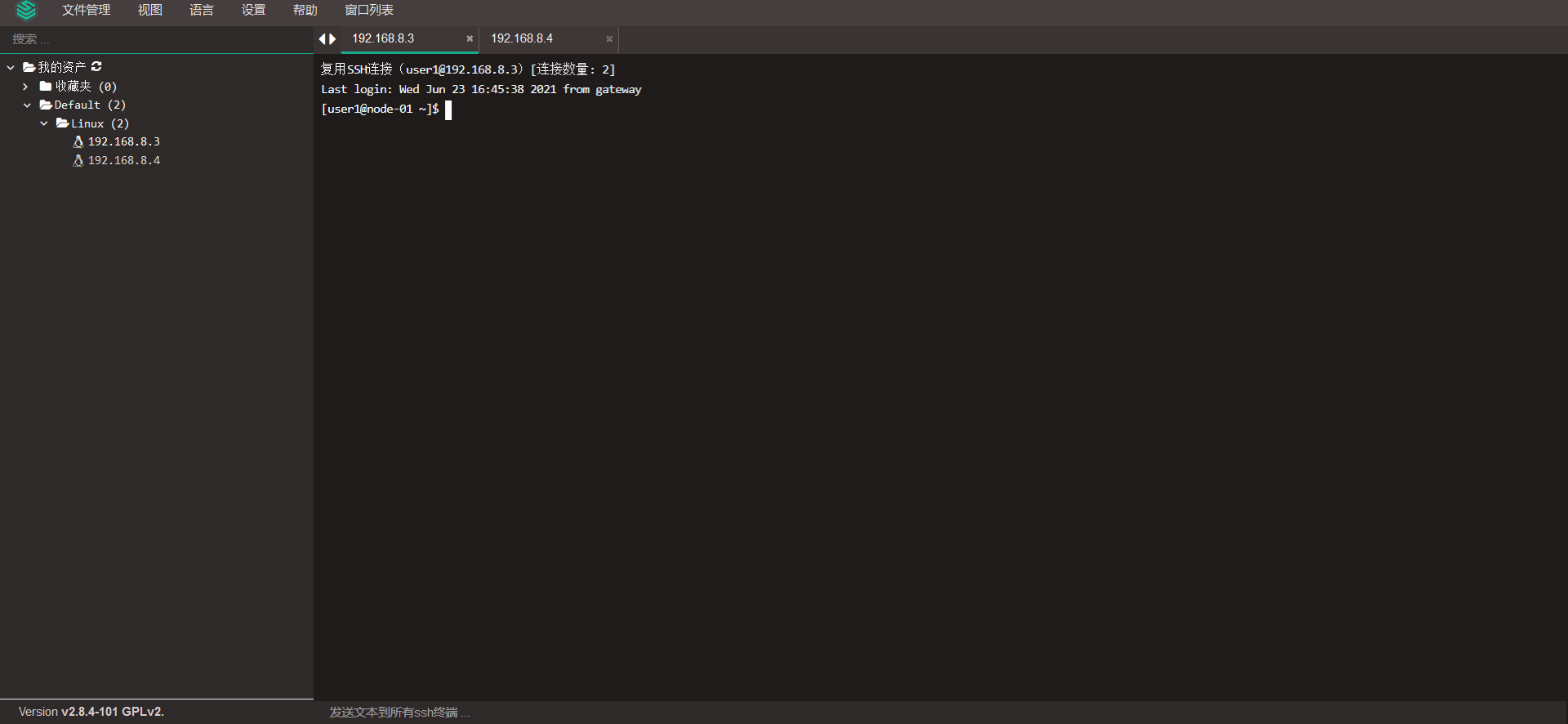
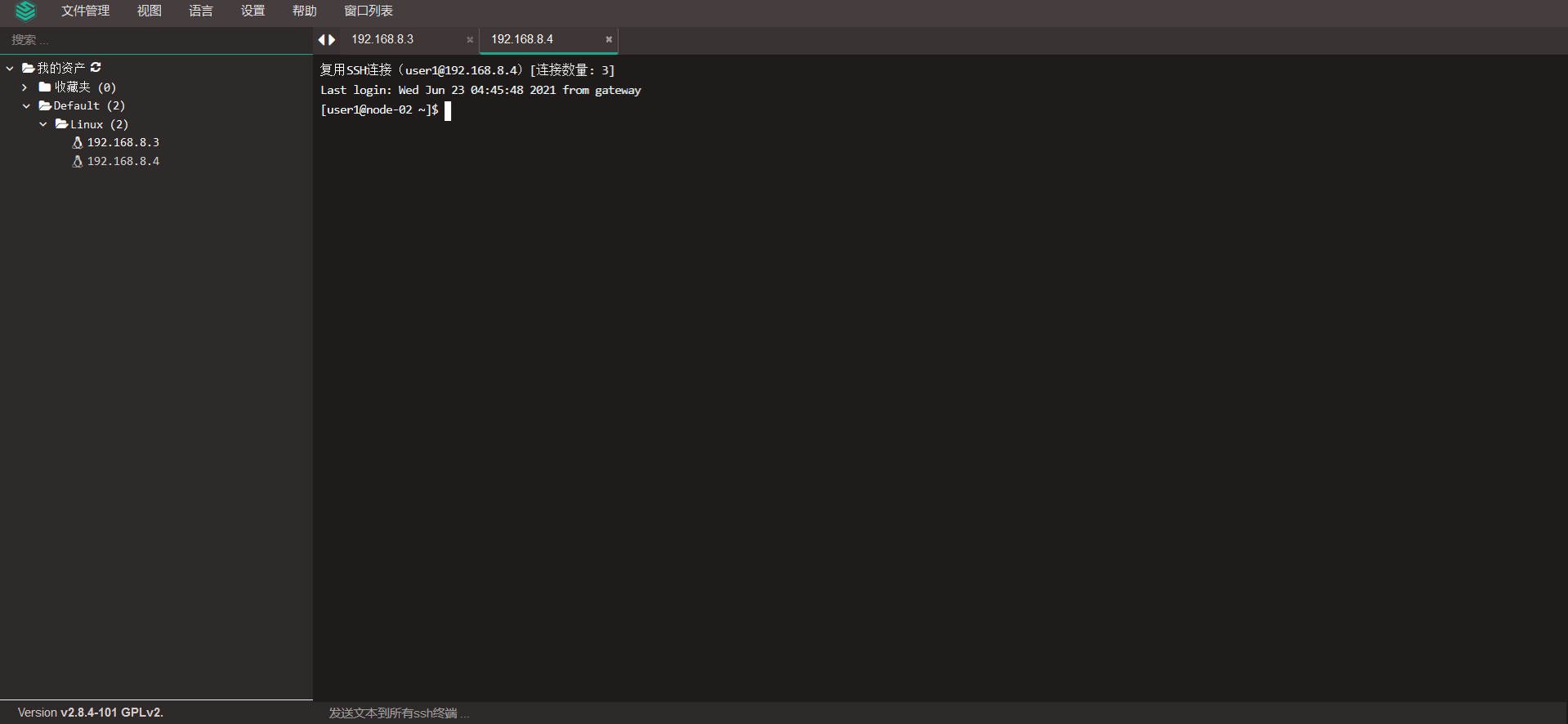
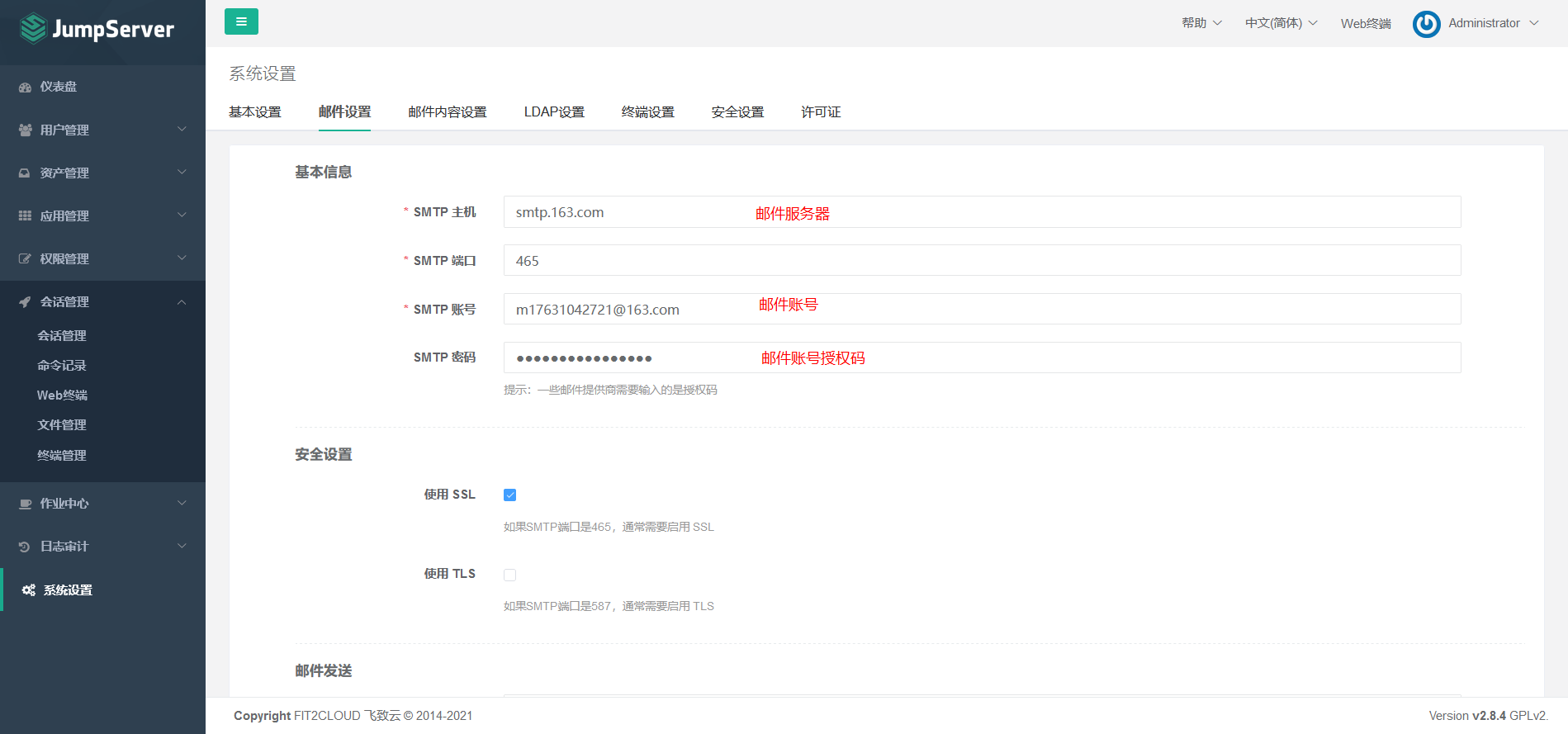
7.7 configuring jumpserver email notification
7.7.1 mail settings
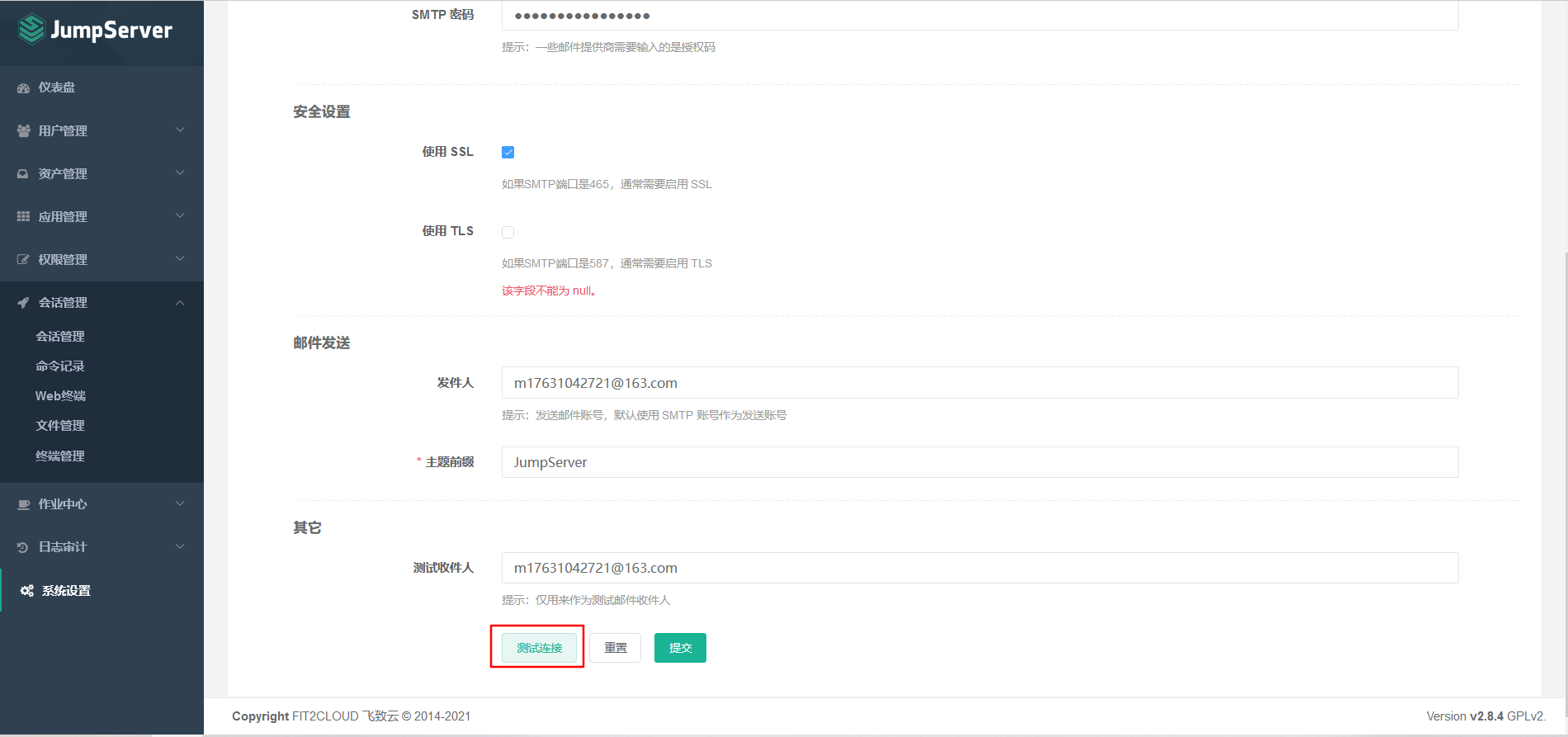
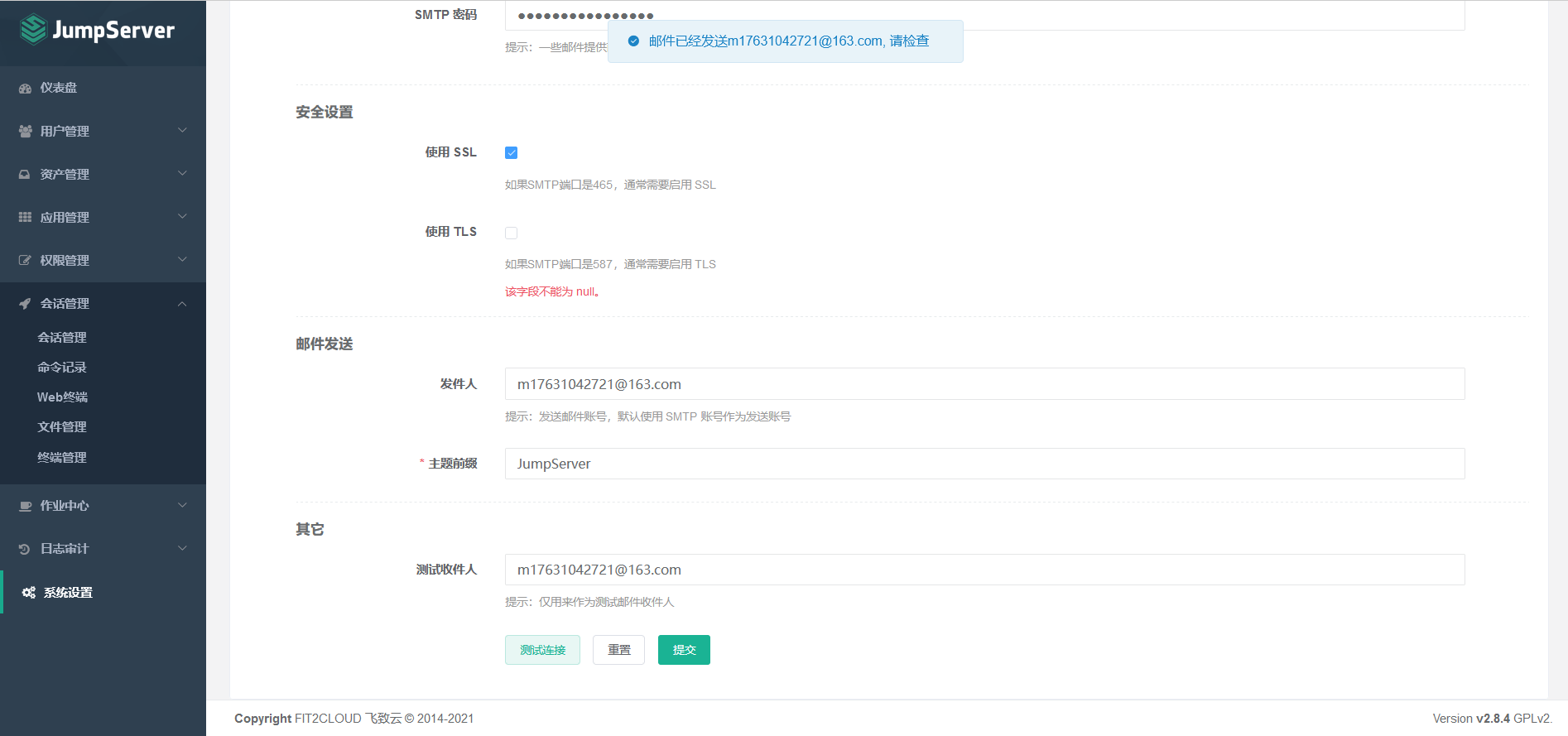
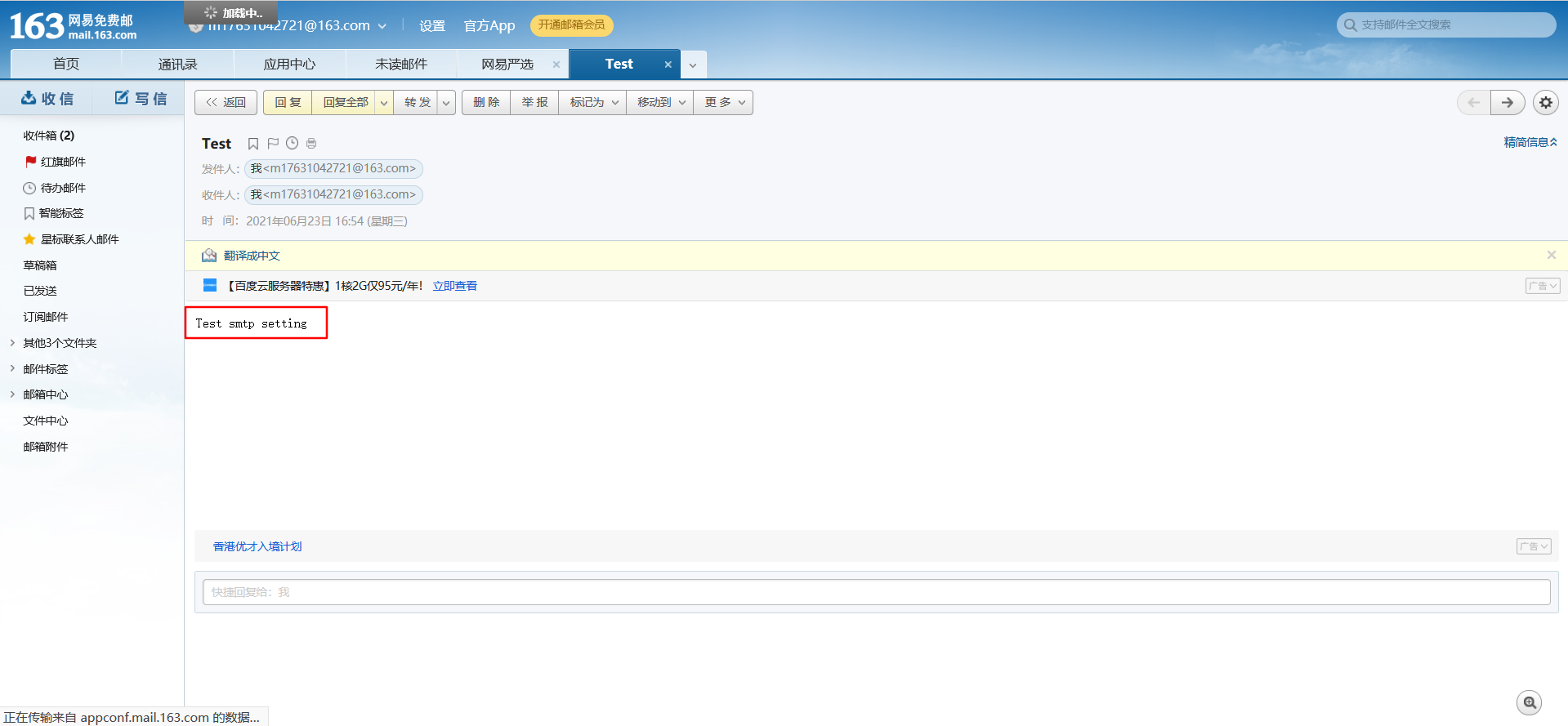
7.7.2 email content setting
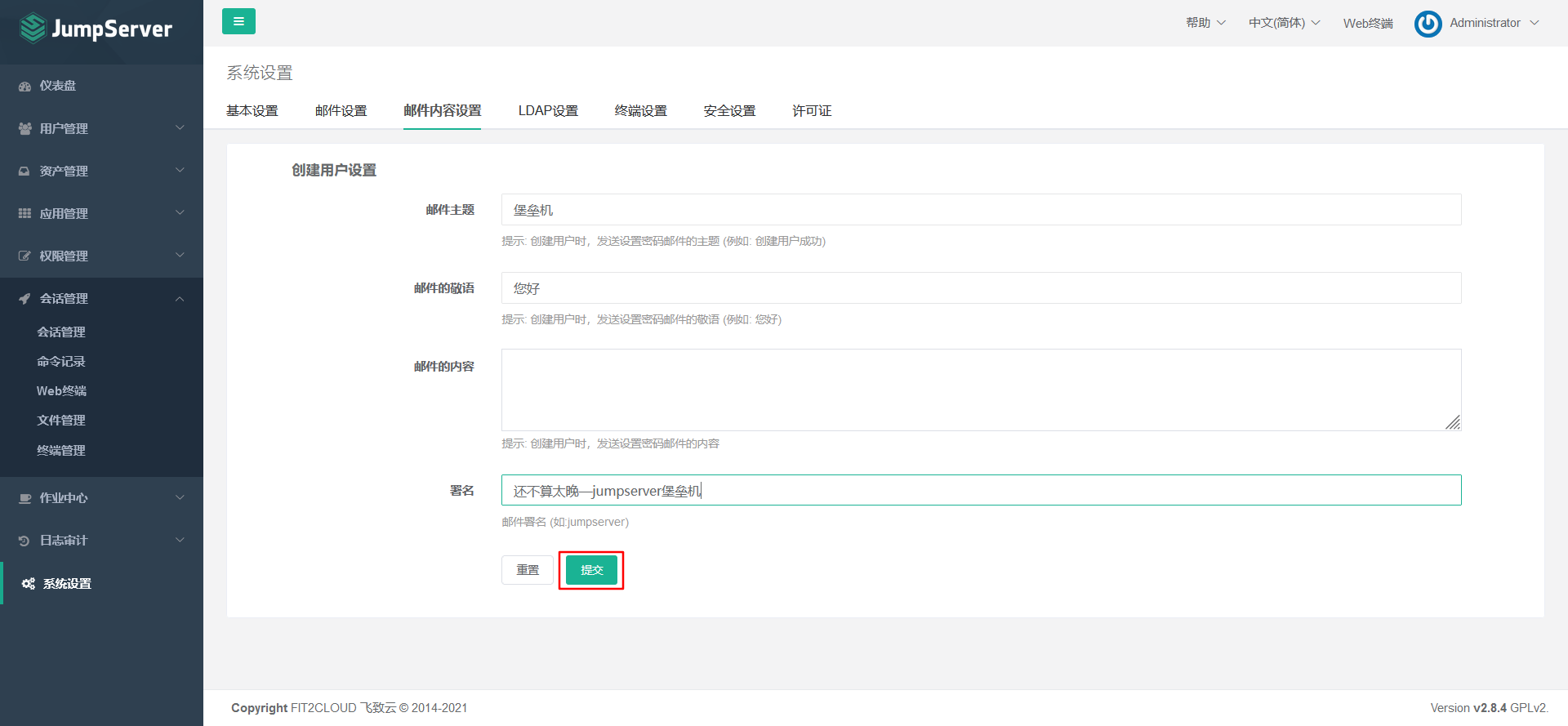
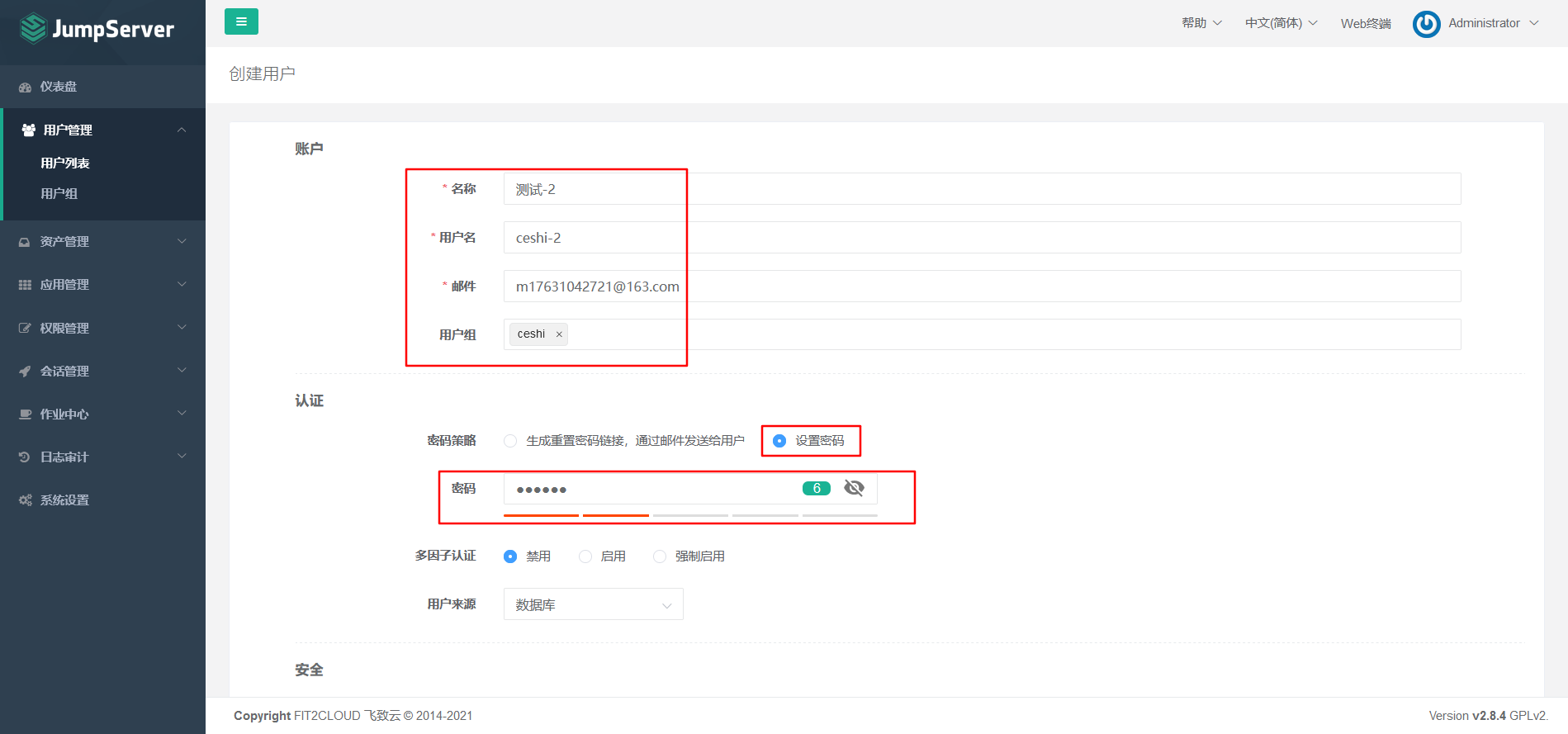
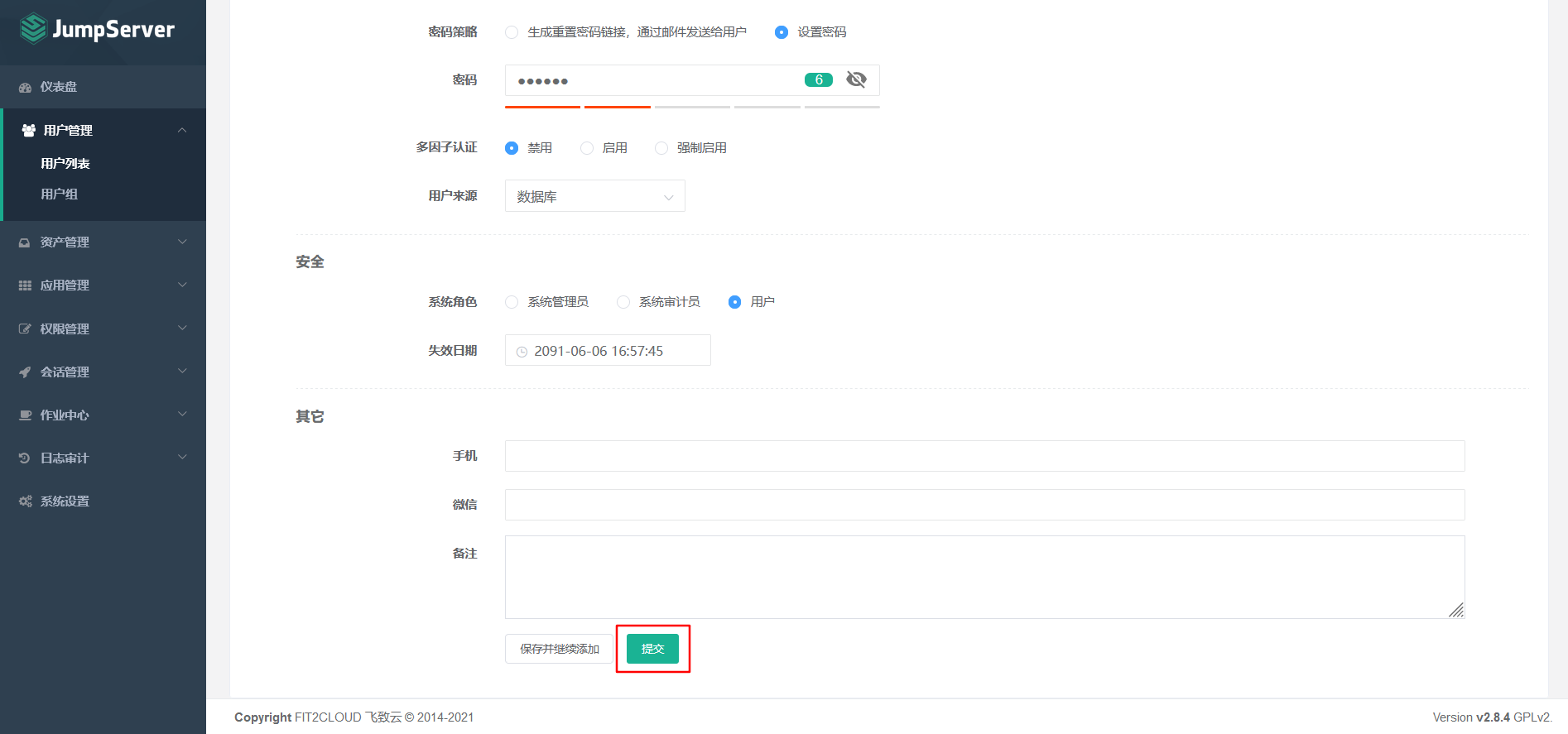
7.7.3 create a user for mail test
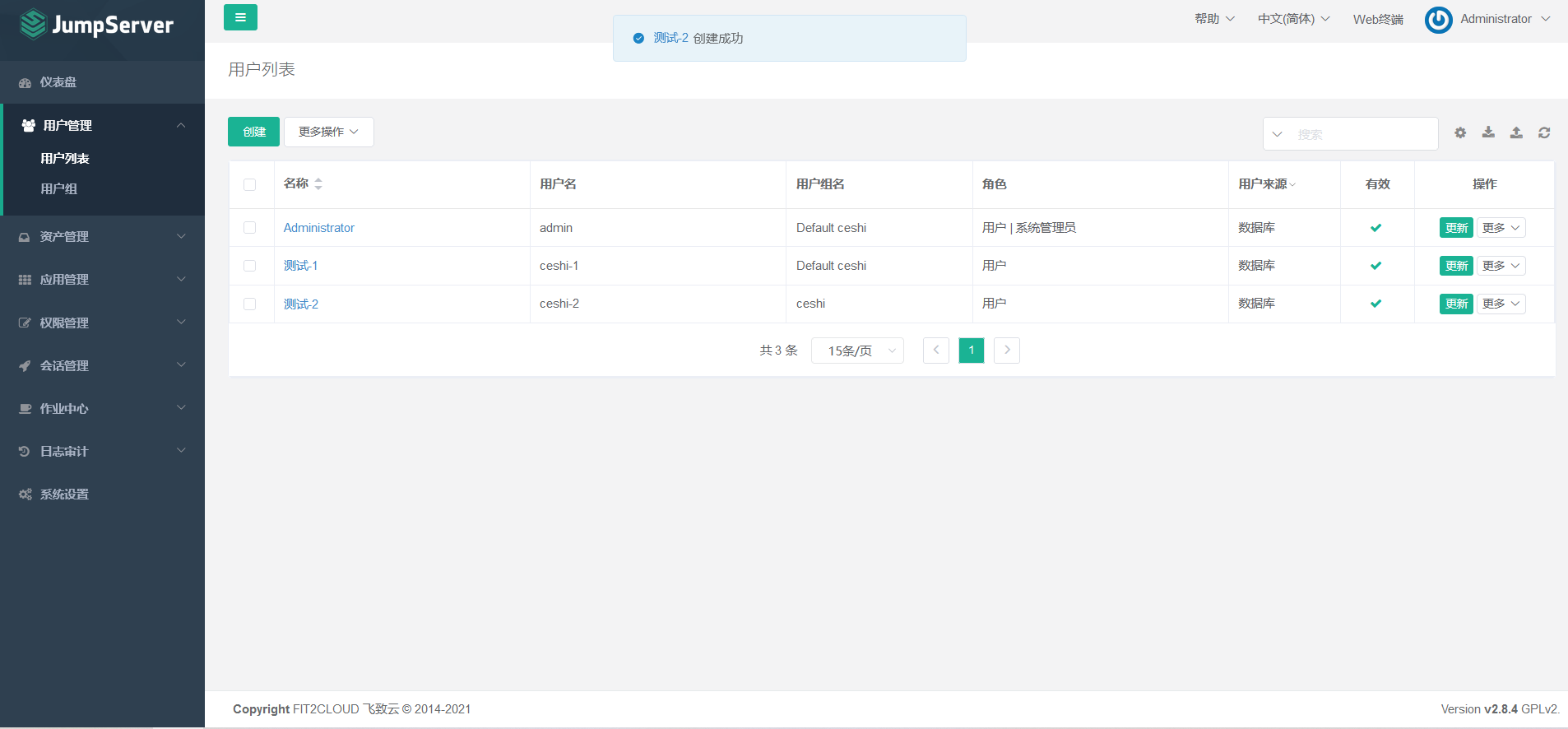
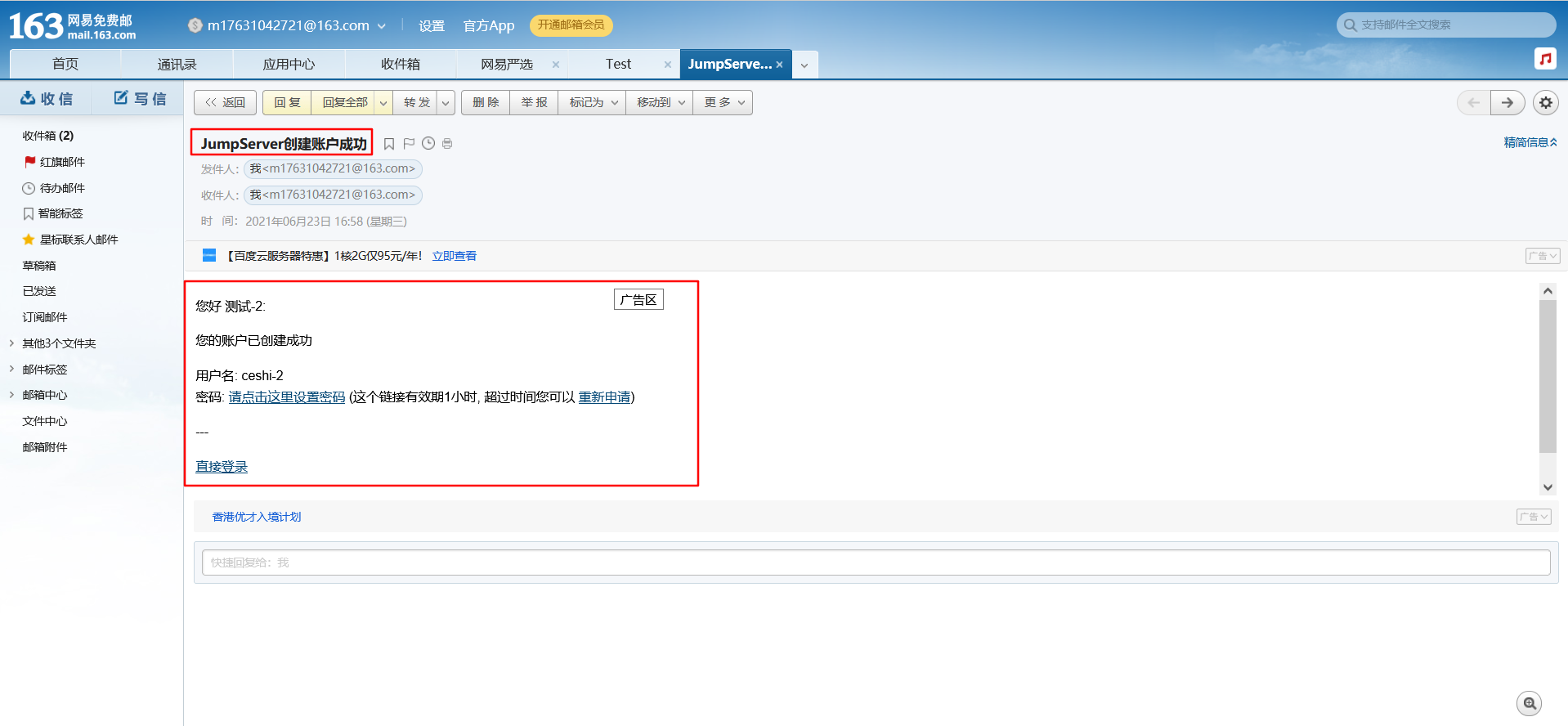
The contents of the above articles are my own understanding. If there are mistakes to mislead you, please comment and point them out. Thank you.