1. docker Resource Limitation
Docker runs depending on two features in the kernel, namespaces and CGroups. By default, the container has no resource constraints, so it can exhaust all the resources allocated to the container by the kernel on the host. Therefore, in order to prevent a container from running out of all the resources of the host, resource constraints need to be used. Some features of resource constraints require Linux kernel support for Linux Capabilities. Before docker version 1.13, only CFS schedule (Completely Fair Scheduler) was supported, and later versions also support realtime schedule.
CFS schedule: Each process has priority, the priority of non-real-time processes is from 100 to 139. CSF schedule is used to schedule these non-real-time processes. The priority process is executed by the cpu first.
realtime schedule: Real-time process scheduler with priority from 0-99. realtime schedule is a special scheduler for scheduling real-time processes.
2. Doker's memory and cpu resource constraints
1. cpu limitation
- cpus=<value>: Specify how many available CPU resources a container can use. If it is a 4-core cpu, it can be set to 1.5, then the container can only use 1.5-core CPU resources at most. If it is not set-cpuset-cpus, the 1.5-core that can be used can be any one of the core resources. This option can only be used in versions above docker 1.3
-- cpu-shares: Allocate CPU resources to containers proportionally. If the CPU resources of other containers are idle, container 1 will use all CPU resources if needed and assign tasks to any core processing.
- cpuset-cpus: Specify which cpu cores can be used for containers. If the CPUs are 4 and 3, then distinguish each core according to the number 0-3. This parameter is set to 0,1, which means the first and second cores can be used.
2. memory and swap restrictions
Memor=<value>: Specify the maximum amount of memory that can be used for containers, and if a process uses more memory than the limit, it may be kill ed out.
Memor-swap: Specify the maximum swap space available for the container. This option must be used with the -- memory parameter. If the -- memory parameter is not set, it will not take effect.
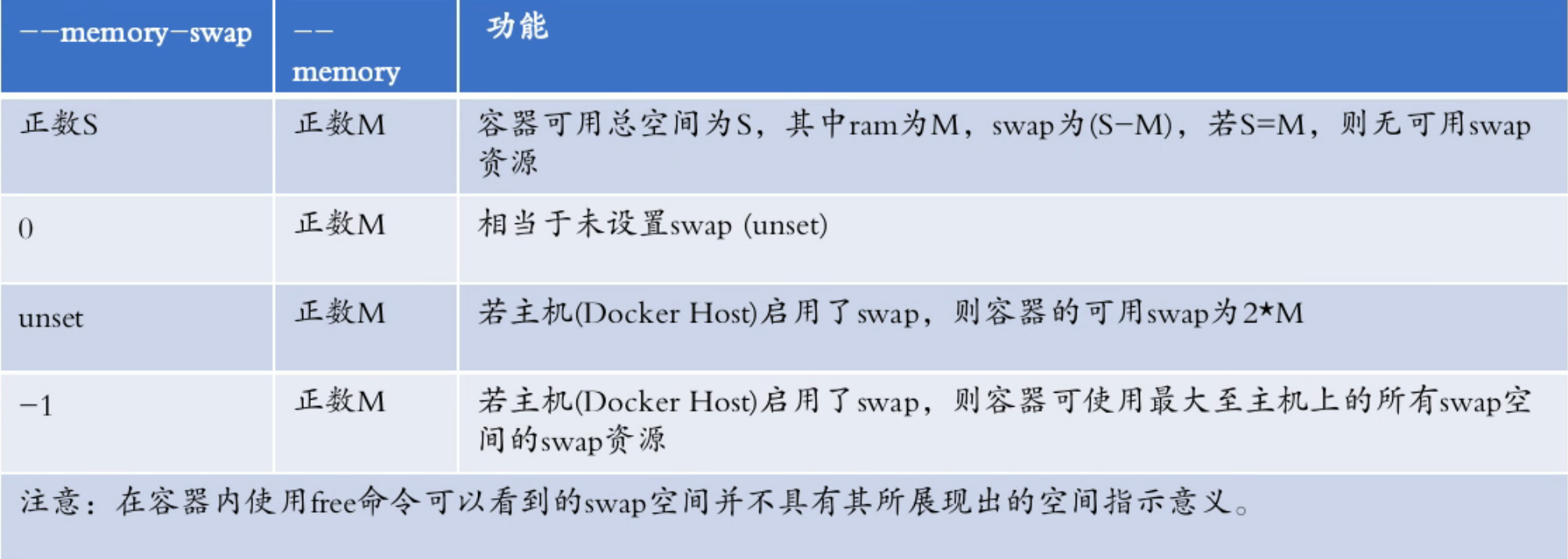
Memory-swapping: How inclined is it to use swap in setting containers, 0-100?
memory-reservation: The soft limitation of memory used by a container, which means that it must be set smaller than memory. When the system memory is tight, the memory of the container's memory value-reservation value will be reclaimed and the container's memory usage will be reduced to the reservations standard.
-- oom-kill-disable: Whether to kill the container when oom occurs in the process inside the container
3. Testing with Pressure Measuring Tools
[root@bogon ~]# docker pull lorel/docker-stress-ng Using default tag: latest latest: Pulling from lorel/docker-stress-ng c52e3ed763ff: Pull complete a3ed95caeb02: Pull complete 7f831269c70e: Pull complete Digest: sha256:c8776b750869e274b340f8e8eb9a7d8fb2472edd5b25ff5b7d55728bca681322 Status: Downloaded newer image for lorel/docker-stress-ng:latest
1. Test memory
1.1. No restrictions on cpu usage
[root@bogon ~]# docker container run --name stress -it --rm lorel/docker-stress-ng:latest --cpu 8 stress-ng: info: [1] defaulting to a 86400 second run per stressor stress-ng: info: [1] dispatching hogs: 8 cpu [root@bogon ~]# docker stats CONTAINER ID NAME CPU % MEM USAGE / LIMIT MEM % NET I/O BLOCK I/O PIDS 92b0b8d916c1 stress 101.54% 15.81MiB / 983.3MiB 1.61% 648B / 0B 0B / 0B 9 [root@bogon ~]# top top - 19:15:49 up 2 days, 2:38, 2 users, load average: 7.02, 3.00, 1.15 Tasks: 131 total, 10 running, 121 sleeping, 0 stopped, 0 zombie %Cpu(s): 99.7 us, 0.3 sy, 0.0 ni, 0.0 id, 0.0 wa, 0.0 hi, 0.0 si, 0.0 st KiB Mem : 1006892 total, 100680 free, 320704 used, 585508 buff/cache KiB Swap: 2097148 total, 2096628 free, 520 used. 422732 avail Mem PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND 40035 root 20 0 6908 4180 252 R 12.6 0.4 0:12.79 stress-ng-cpu 40037 root 20 0 6908 4180 252 R 12.6 0.4 0:12.78 stress-ng-cpu 40038 root 20 0 6908 2136 252 R 12.6 0.2 0:12.78 stress-ng-cpu 40040 root 20 0 6908 2136 252 R 12.6 0.2 0:12.78 stress-ng-cpu 40036 root 20 0 6908 2136 252 R 12.3 0.2 0:12.77 stress-ng-cpu 40039 root 20 0 6908 2136 252 R 12.3 0.2 0:12.78 stress-ng-cpu 40041 root 20 0 6908 4180 252 R 12.3 0.4 0:12.77 stress-ng-cpu 40042 root 20 0 6908 2136 252 R 12.3 0.2 0:12.77 stress-ng-cpu 1 root 20 0 128484 7208 4196 S 0.0 0.7 0:10.12 systemd
As you can see, cpu usage is full
1.2. Restart the container to add memory restriction parameters
[root@bogon ~]# docker container run --name stress --cpus=0.5 -it --rm lorel/docker-stress-ng:latest --cpu 8 stress-ng: info: [1] defaulting to a 86400 second run per stressor stress-ng: info: [1] dispatching hogs: 8 cpu [root@bogon ~]# docker stats CONTAINER ID NAME CPU % MEM USAGE / LIMIT MEM % NET I/O BLOCK I/O PIDS 845220ef9982 stress 51.57% 20.05MiB / 983.3MiB 2.04% 648B / 0B 0B / 0B 9
Setted parameters take effect
2. Test memory
2.1. There is no restriction on memory usage. Pressure measurements specify two memory, 128m each.
[root@bogon ~]# docker container run --name stress -it --rm lorel/docker-stress-ng:latest --vm 2 --vm-bytes 128m stress-ng: info: [1] defaulting to a 86400 second run per stressor stress-ng: info: [1] dispatching hogs: 2 vm [root@bogon ~]# docker stats CONTAINER ID NAME CPU % MEM USAGE / LIMIT MEM % NET I/O BLOCK I/O PIDS beb3cfa10748 stress 99.29% 256.2MiB / 983.3MiB 26.05% 648B / 0B 0B / 0B 5
In fact, 256M memory was used.
2.2. Restart the container and add memory restrictions
--Memory limits containers to 128m of memory
[root@bogon ~]# docker container run --name stress -it --memory=128m --rm lorel/docker-stress-ng:latest --vm 2 --vm-bytes 128m stress-ng: info: [1] defaulting to a 86400 second run per stressor stress-ng: info: [1] dispatching hogs: 2 vm [root@bogon ~]# docker stats CONTAINER ID NAME CPU % MEM USAGE / LIMIT MEM % NET I/O BLOCK I/O PIDS decee18cb471 stress 99.47% 126.4MiB / 128MiB 98.77% 648B / 0B 3.19MB / 461MB 5