Docker local private warehouse and harbor private warehouse
1, Build local private warehouse
1, Build local private warehouse
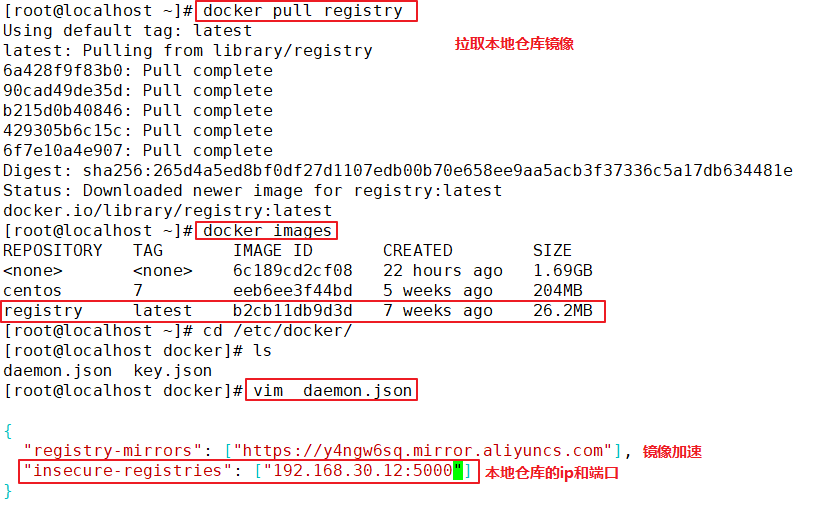
#First download the registry image
docker pull registry
#Add the private image repository address to the daemon.json file
vim /etc/ docker/daemon.json
{
"insecure-registries": ["192.168.80.10:5000"],
#Add, pay attention to ending with commas
"registry-mirrors": ["https://6ijb8ubo.mirror.aliyuncs.com"]
}
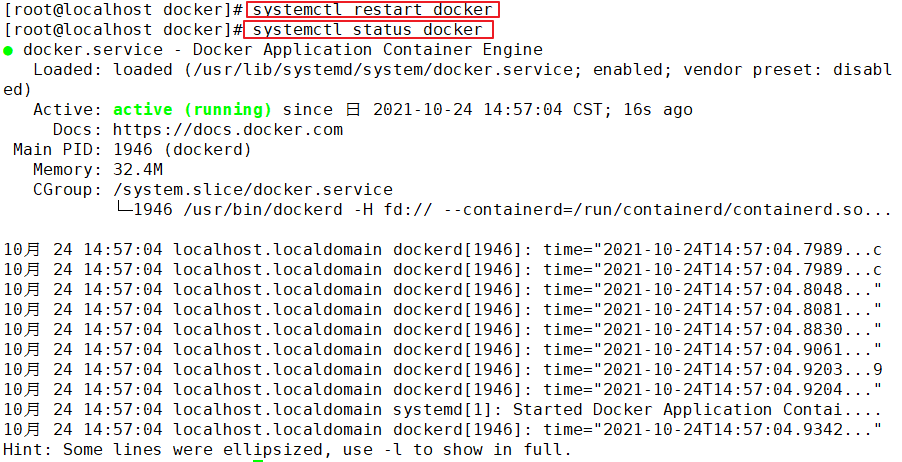
systemctl restart docker.service
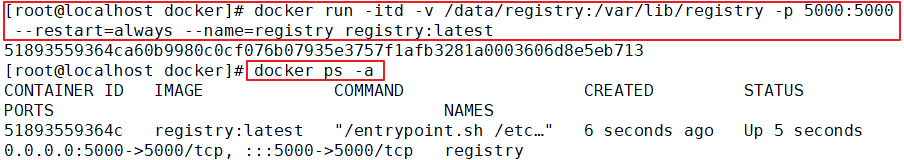
#Run registry container
docker run -itd -v /data/registry:/var/lib/registry -p 5000:5000 --restart=always --name registry registry:latest
===================================================
-itd: Open a pseudo terminal in the container for interactive operation and run in the background
-v: Put the host/data/registry Bind directory to container/var/lib/registry catalogue(This directory is registry The directory in which the image file is stored in the container),To achieve data
Persistence;
-p:Mapping port;Access the 5000 port of the host registry Container services
--restart=always: This is the restart strategy, which always restarts the container when it exits
--name registry: Create a container named registry
registry:latest:This is just now pull Down the mirror
====================================================
Docker The restart strategy of the container is as follows:
no:The default policy is not to restart the container when it exits
on-failure: When the container exits abnormally(Exit status is not 0),To restart the container
on-failure:3 :Restart the container when the container exits abnormally, up to 3 times
always: Always restart the container when it exits
unless-stopped: Always restart the container when it exits, but do not consider Docker Container that has been stopped when the daemon starts
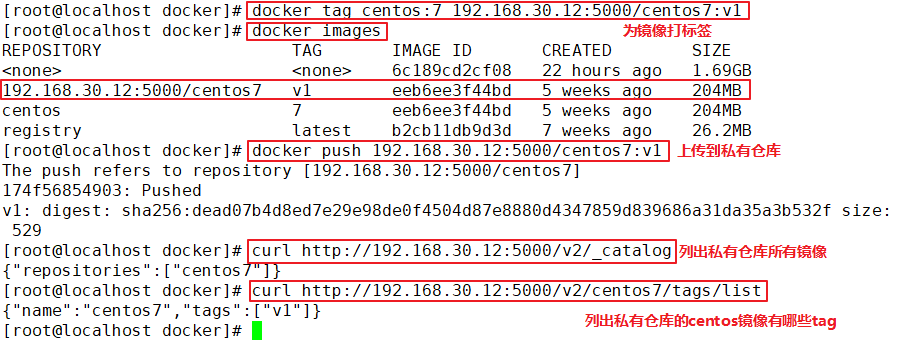
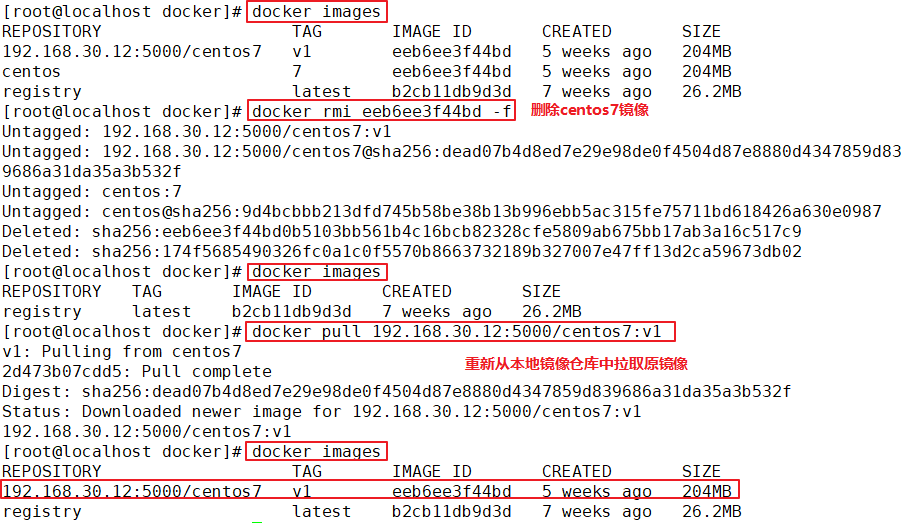
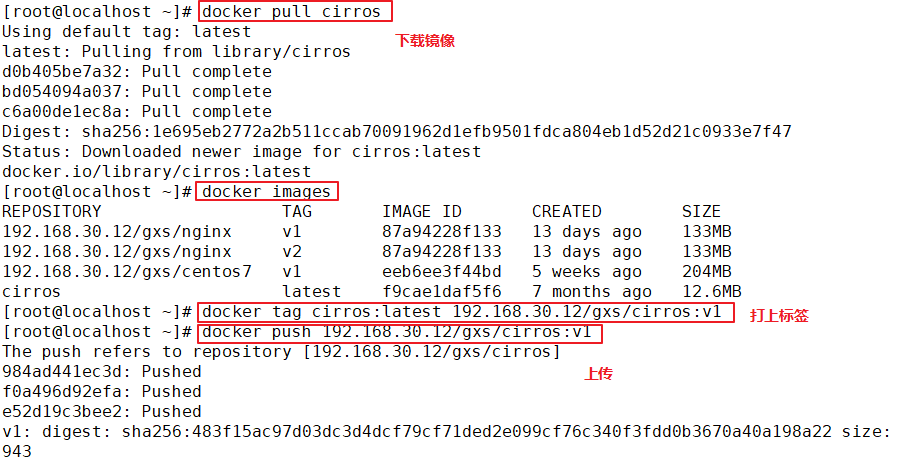
#Label images
docker tag centos:7 192.168.30.12:5000/centos:v1
#Upload to private warehouse
docker push 192.168.30.12:5000/centos:v1
#List all images of the private warehouse
curl http://192.168.30.12:5000/v2/_catalog
#What are the tag s of centos images out of private warehouses
curl http://192.168.30.12:5000/v2/centos/tags/list
#First delete the original centos image, and then test the private warehouse download
docker rmi -f 8652b9f0cb4c
docker pull 192.168.30.12:5000/centos:v1
Example:
2, Harbor overview
1. What is Harbor
• Harbor is an open source enterprise Docker Registry project of VMware. Its goal is to help users quickly build an enterprise Docker Registry service
• based on Docker's open source Registry, Harbor provides functions required by enterprise users such as graphical management UI, role-based access control, AD/LDAP integration, and audit logging. At the same time, it supports Chinese
• each component of Harbor is built in the form of Docker container, and Docker compose is used to deploy it. The docker-compose template for deploying Harbor is located at Harbor / docker-compose.yml
2. Characteristics of harbor
(1) Role based control: users and warehouses are organized based on projects, and users can have different permissions in projects
(2) Image based replication strategy: images can be replicated (synchronized) between multiple Harbor instances
(3) LDAP / ad support: harbor can integrate AD/LDAP (a table similar to the database) within the enterprise to authenticate and manage existing users
(4) Image deletion and garbage collection: the image can be deleted or the space occupied by the image can be recycled
(5) Graphical user interface: users can browse, search the image warehouse and manage the project through the browser
(6) Audit management: all operations on the image warehouse can be recorded and traced for audit management
(7) Support for RESTful API: RESTful API provides administrators with more control over Harbor, making it easier to integrate with other management software
(8) Relationship between harbor and docker registry: Harbor essentially encapsulates docker registry and extends its own business template
3. Composition of harbor
In terms of architecture, Harbor mainly includes six components: Proxy, Registry, Core services, database (Harbor dB), log collector (Harbor log) and Job services
● Proxy: Harbor's Registry, UI, Token service and other components are behind nginx reverse proxy. The agent forwards requests from browsers and docker clients to different back-end services
● Registry: responsible for storing Docker images and handling Docker push/pull commands. Due to the access control of users, that is, different users have different read and write permissions on the Docker image, Registry will point to a Token service, forcing users to carry a legal Token in each Docker pull/push request, and Registry will decrypt and verify the Token through the public key
● core services: the core function of harbor, which mainly provides the following three services:
UI (harbor UI): provides a graphical interface to help users manage images on Registry. And authorize users
Webhook: in order to obtain the status changes of the image on Registry. In time, configure Webhook on Registry. And pass the status changes to the UI module
Token service: responsible for issuing tokens to each Docker push/pull command according to user permissions. The request initiated by the Docker client to the Registry service,
If the Token is not included, it will be redirected to the Token service. After obtaining the Token, it will make a request to the Registry again
● database (harbor dB): it provides database services for core services, and is responsible for storing data such as user permissions, audit logs, Docker image grouping information, etc
● Job services: mainly used for image replication. Local images can be synchronized to remote Harbor instances
● log collector (harbor log): responsible for collecting logs of other components to one place
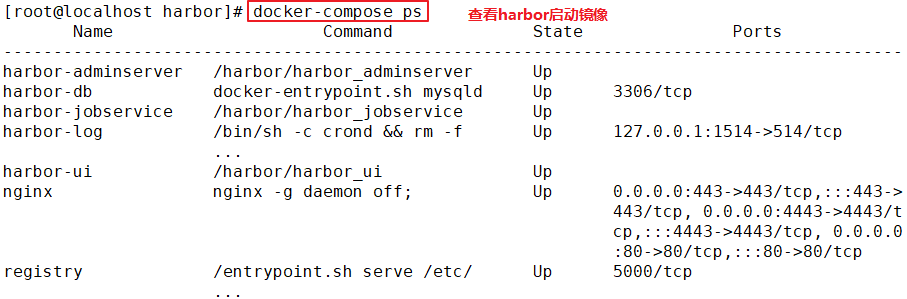
• Harbor Each component of is Docker Containers are built in the form of, therefore, using Docker Compose To deploy it. • A total of 7 containers were run through docker-compose.yml Execute in the same directory docker-compose ps Command to view, The names are: nginx, harbor-jobservice, harbor-ui, harbor-db,harbor-adminserver,registry, harbor-log. among harbor-adminserver Mainly as a back-end configuration data management, there are not many other functions. harbor-ui All data to be operated is passed harbor-adminserver
Such a data configuration management center to complete.
3, Harbor deployment
Environment deployment
| The server | ip | assembly |
|---|---|---|
| Harbor server | 192.168.30.12 | docker-ce,docker-compose,harbor-offline-v1.2.2 |
| client server | 192.168.30.16 | docker-ce |
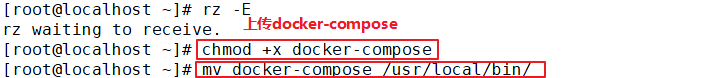
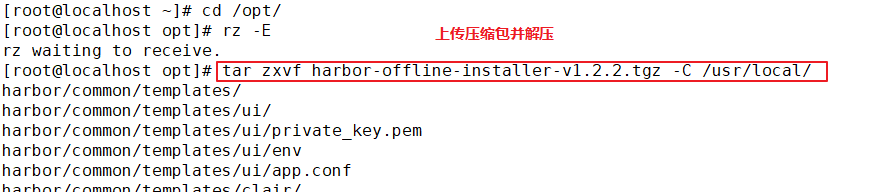
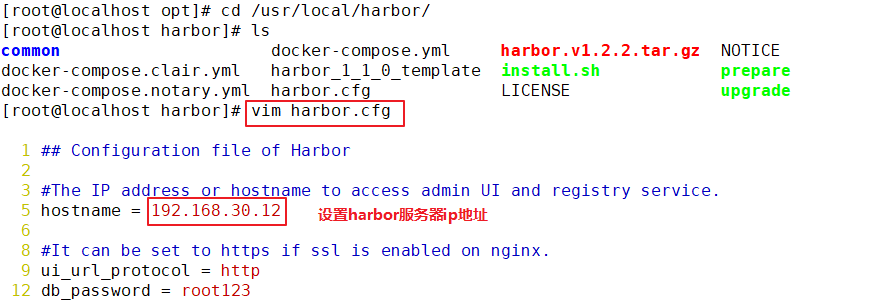
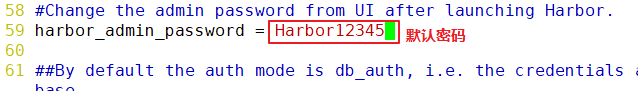
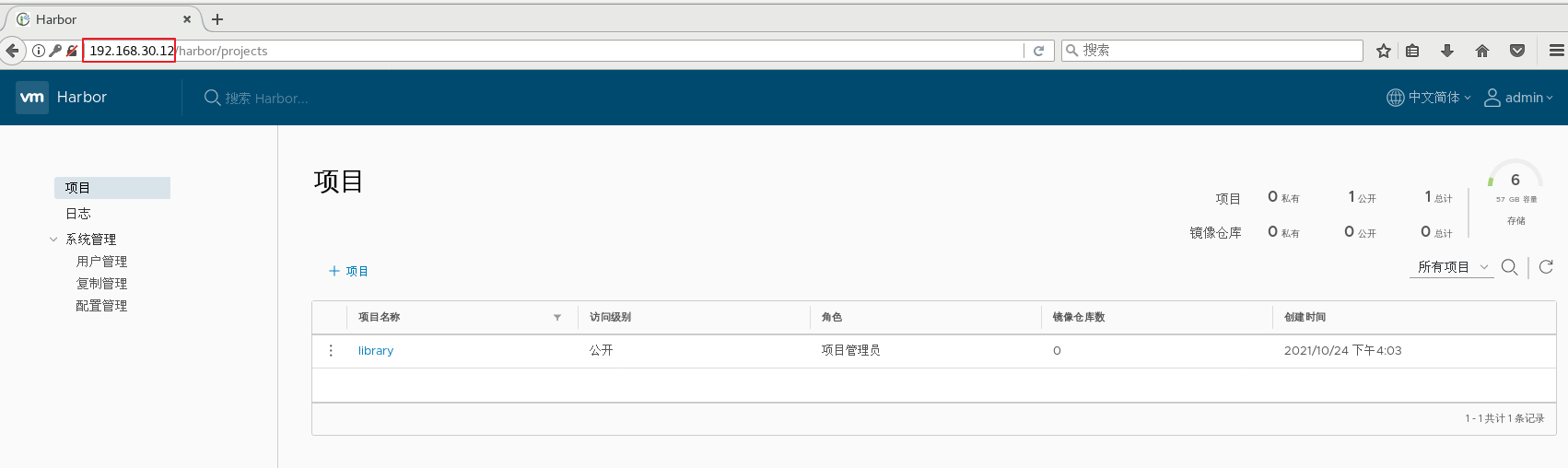
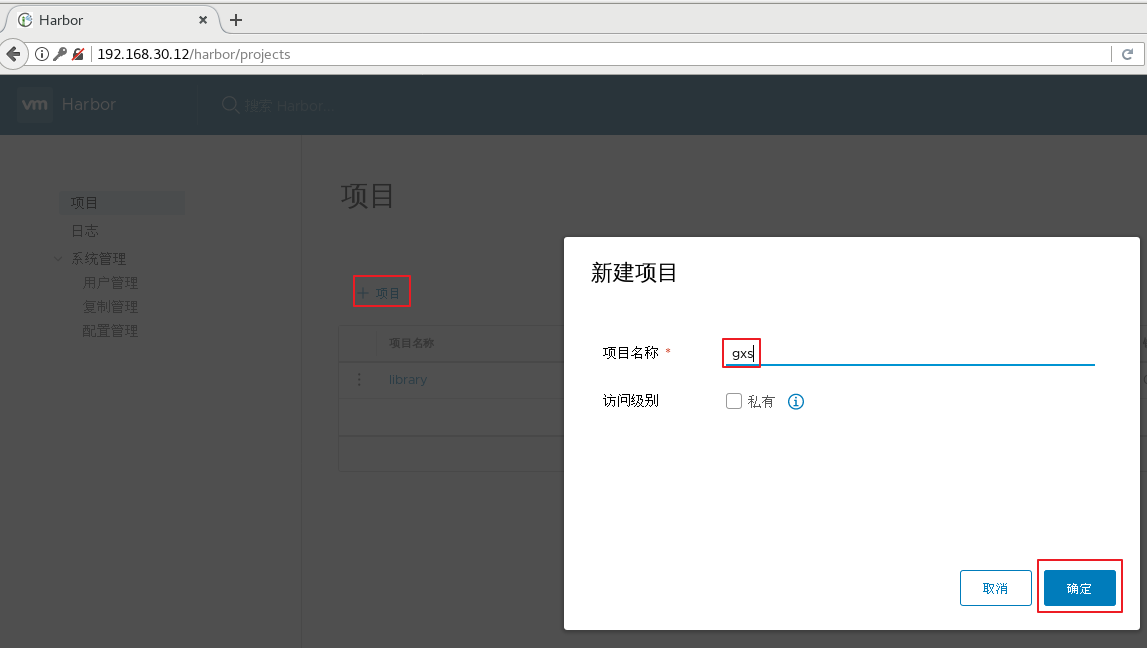
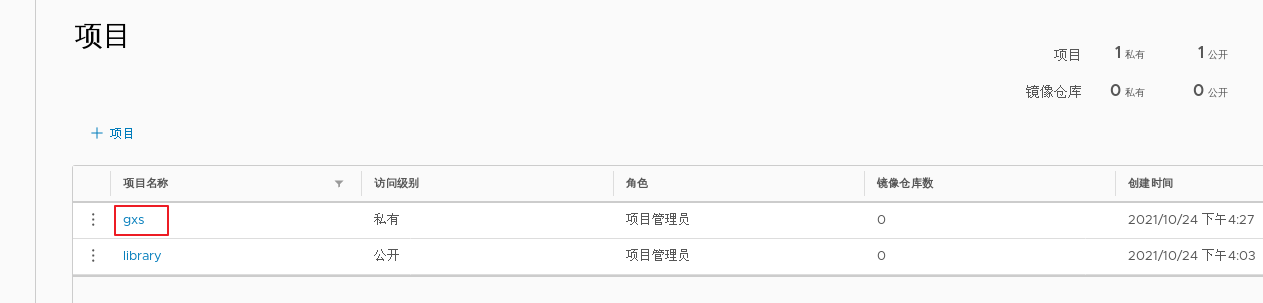
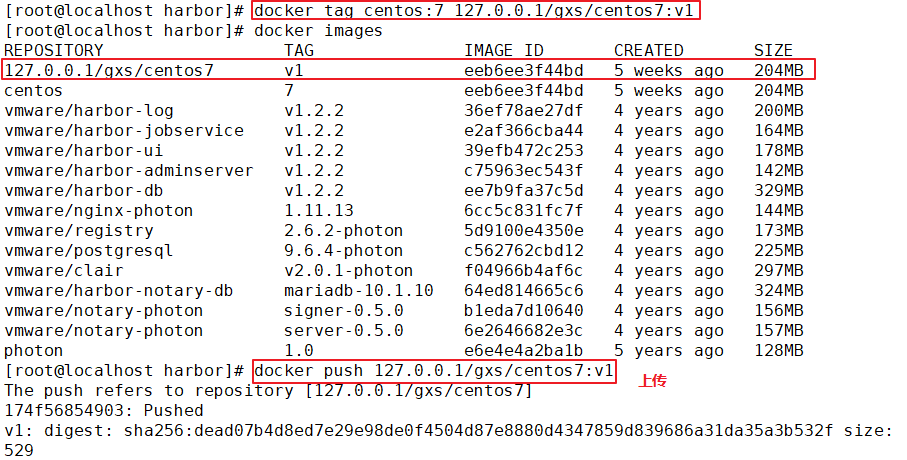
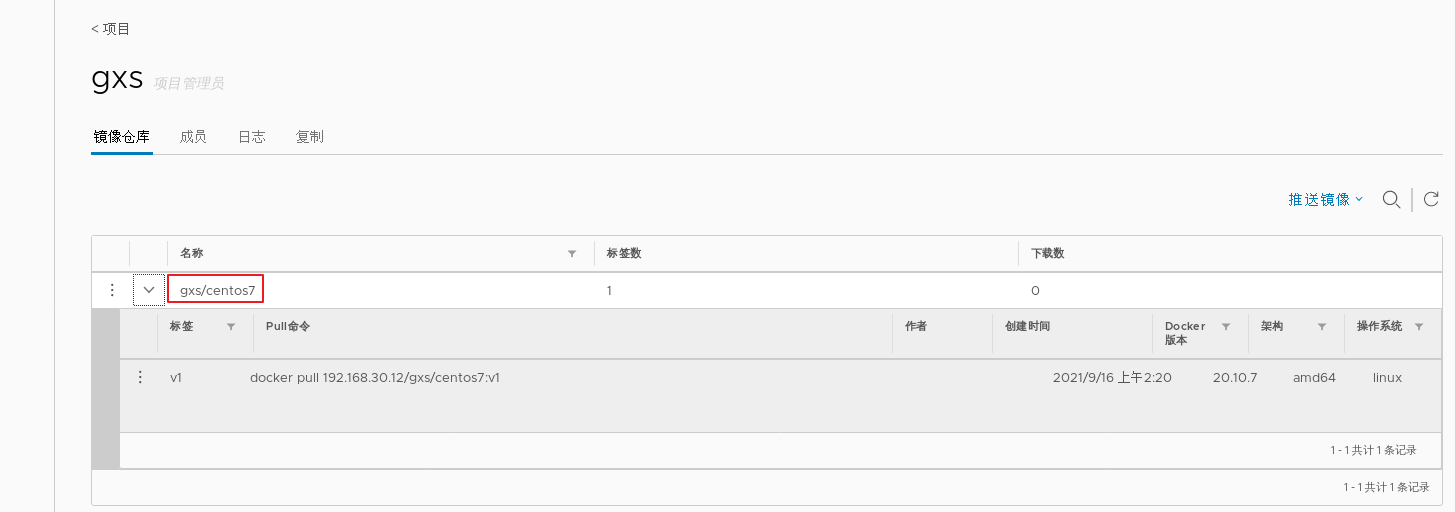
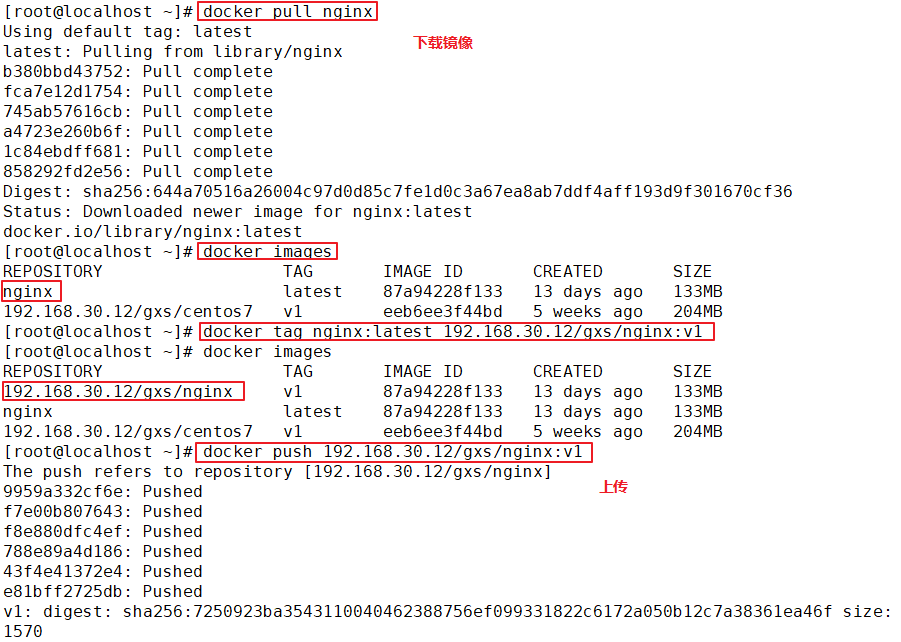
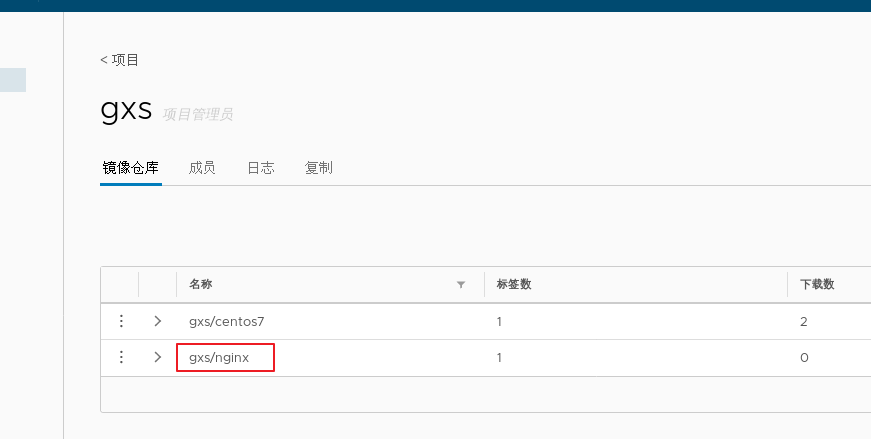
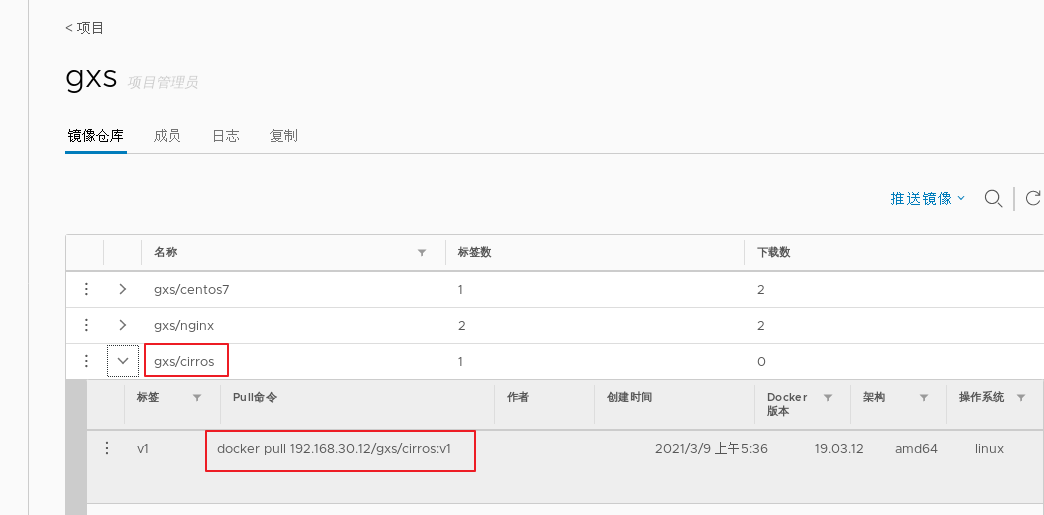
1.deploy Docker-Compose service| #Download or upload docker compose curl -L https://github.com/docker/compose/releases/download/1.21.1/docker-compose-`uname -s`-`uname -m`-o /usr/local/bin/docker-compose chmod +x /usr/local/bin/docker-compose docker-compose -v 2.deploy Harbor service (1)Download or upload Harbor erection sequence wget http://harbor.orientsoft.cn/harbor-1.2.2/harbor-offline installer-v1.2.2.tgz tar zxvf harbor-offline-installer-v1.2.2.tgz -C /usr/local/ (2)modify harbor Installed profile vim /usr/1ocal/harbor/harbor.cfg --5 that 's ok--Modify, set to Harbor Server IP Address or domain name hostname = 192.168.30.12 -- 59 that 's ok--Specify the initial password of the administrator and the default user name/The password is admin/ Harbor12345 harbor_admin_ password = Harbor12345 ====================================================== about Harbor.cfg There are two types of parameters in the configuration file:Required and optional parameters 1,Required parameters:These parameters need to be in the configuration file Harbor.cfg Set in. If the user updates them and runs install.sh Script reinstallation Harbour,The parameter will take effect. Specific parameters are as follows: ●hostname:Used to access the user interface and register Service. It should be the target machine IP Address or fully qualified domain name(FQDN) ,For example 192.168.80.10 or hub. gxs.cn. Do not use localhost Or 127.0.0.1 Is the host name ●ui_url_protocol:(http or https,Default to http)For access UI And token/Agreement for notification services. If justice is enabled, this parameter must be https ●max_job_workers: Mirror copy job thread ●db_password: be used for db_auth of MySQL database root User's password ●customize_crt:This property can be set to on or off. It is on by default. When this property is turned on, prepare the script to create the private key and root certificate for generation/Validate registry token. Set this property to when the key and root certificate are provided by an external source off ●ssl_cert: SSL Path to the certificate, only if the protocol is set to https Apply only when ●secretkey_path:Used to encrypt or decrypt remote in replication policy register Key path for password ●project_creation_restriction: Flag that controls which users have permission to create items. By default, everyone can create-A project. If its value is set to“ adminonly" So only admin You can create projects ●verify_remote_cert: On or off, on by default. This flag determines when Harbor With remote register Verify when communicating with instances SSL/TLS Certificate. Set this property to off Will bypass SSL/TLS Authentication, which is often used when the remote instance has a self signed or untrusted certificate In addition, by default, Harbour Store the image on the local file system.In a production environment, you can consider using other storage back ends instead of local file systems, such as S3,Openstack Swif,Ceph And so on. But it needs to be updated common/templates/registry/config.yml file ======================================================== 3.start-up Harbor cd /usr/local/harbor/ ./install.sh 4.see Harbor Start mirroring cd /usr/local/harbor/ docker-compose ps 5.Create a new project (1)Browser access: http://192.168.30.12 log in to the Harbor WEB UI interface. The default administrator user name and password are admin / harbor 12345 (2)After entering the user name and password, you can create a new item. Click“+Project button (3)Fill in the item name as"myproject-kgc",Click OK to create a new project (4)Available at this time Docker The command is passed locally.0.0.1 To log in and push images. By default, Registry The server is on port 80. Listen on. //Log in to Harbor docker login -u admin -p Harbor12345 http://127.0.0.1 //Download the image for testing docker pull nginx //Label the image format: docker tag image:Label warehouse IP/entry name/Image name:label docker tag nginx:latest 127.0.0.1/gxs/nginx:v1 //Upload image to Harbor docker push 127.0.0.1/gxs/cirros:v1 (5)stay Harbor Jieer gxs The image and related information can be seen in the directory 6.Upload images on other clients The above operations are in Harbor The server operates locally. If other clients log in to Harbor, The following error will be reported. The reason for this problem is Docker Registry Interactive default is HTTPS,However, the default setting for building private images is HTTP Service, so the following error occurred when interacting with the private image. docker login -u admin -p Harbor12345 http://192.168.30.12 WARNING! Using --password via the CLI is insecure. Use --password-stdin. Error response from daemon: Get https:L/192.168.30.12/v2/: dial tcp 192.168.30.12:443: connect: connection refused (1)stay Docker Client configuration operation //The solution is: when the Docker server is started, add the startup parameters and use HTTP access by default. vim /usr/lib/systemd/system/docker.service --13 that 's ok--modify ExecStart=/usr/bin/dockerd -H fd:// --insecure-registry 192.168.30.12 --containerd=/run/containerd/containerd. sock or ExecStart=/usr/bin/dockerd --insecure-registry 192.168.30.12 //Restart Docker and log in again systemctl daemon- reload systemctl restart docker //Log in to Harbor again docker login -u admin -p harbor12345 http://192.168.30.12 WARNING! Using --password via the CLI is insecure. Use --password-stdin. WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Login Succeeded //The credentials will be automatically saved to / root/.docker/config.json. You can directly log in to Harbor with your credentials when logging in next time //Download the image for testing docker pull 192.168.30.12/gxs/nginx:v1 //Upload images for testing docker pull cirros docker tag cirros:latest 192.168.30.12/gxs/cirros:v2 docker push 192.168.30.12/gxs/cirros:v2 (2)Refresh Harbor of Web View the management interface and you will find gxs There are two images in the project
Example:
Deploy docker compose service
Deploy Harbor service
Start harbor
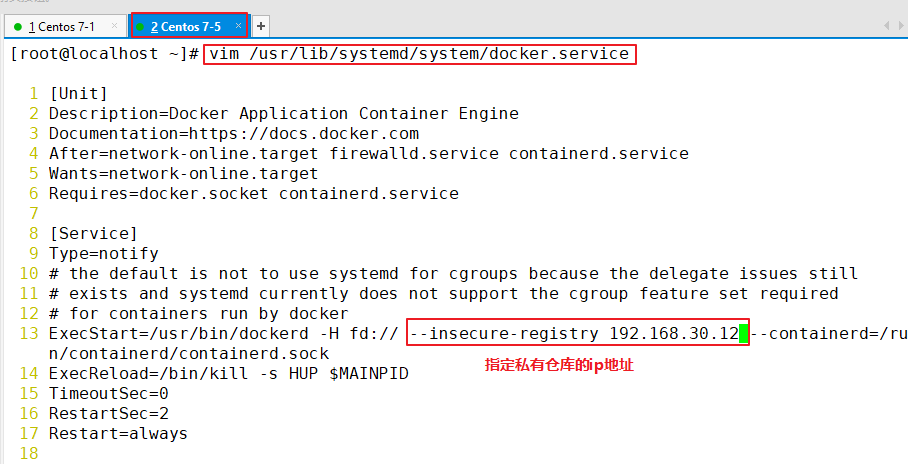
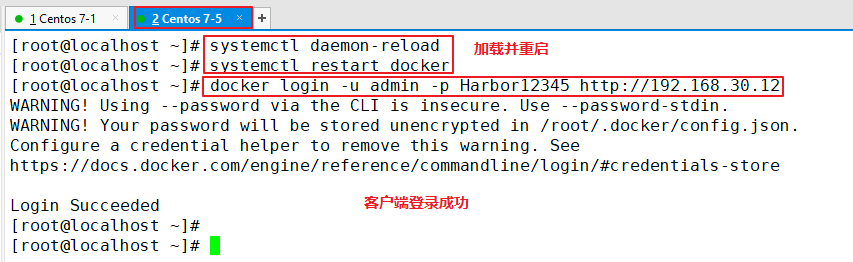
The above operations are performed locally on the Harbor server. If other clients log in to Harbor, the following error will be reported. The reason for this problem is that the Docker Registry interaction uses HTTPS by default, but the private image is built using HTTP service by default. Therefore, the following error occurs when interacting with the private image
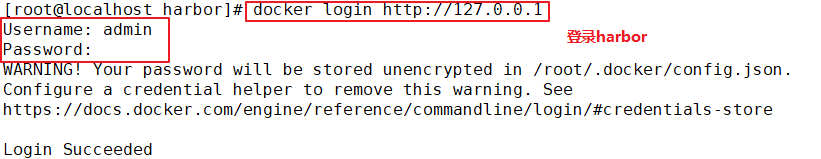
docker login -u admin -p Harbor12345 http://192.168.30.12 WARNING! Using --password via the CLI is insecure. Use --password-stdin. Error response from daemon: Get https://192.168.30.12/v2/: dial tcp 192.168.30.12:443: connect: connection refused (1)stay Docker Client configuration operation //The solution is: when the Docker server is started, add the startup parameters and use HTTP access by default. vim /usr/lib/systemd/system/docker.service --13 that 's ok--modify ExecStart=/usr/bin/dockerd -H fd:// --insecure-registry 192.168.30.12 --containerd=/run/containerd/containerd.sock or ExecStart=/usr/bin/dockerd --insecure-registry 192.168.30.12 //Restart Docker and log in again systemctl daemon-reload systemctl restart docker //Log in to Harbor again docker login -u admin -p harbor12345 http://192.168.30.12 WARNING! Using --password via the CLI is insecure. Use --password-stdin. WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Login Succeeded //The credentials will be automatically saved to / root/.docker/config.json. You can directly log in to Harbor with your credentials when logging in next time //Download the image for testing docker pull 192.168.30.12/gxs/nginx:v1 //Upload images for testing docker pull cirros docker tag cirros:latest 192.168.30.12/gxs/cirros:v2 docker push 192.168.30.12/gxs/cirros:v2 (2)Refresh Harbor of Web View the management interface and you will find gxs There are two images in the project
Example:
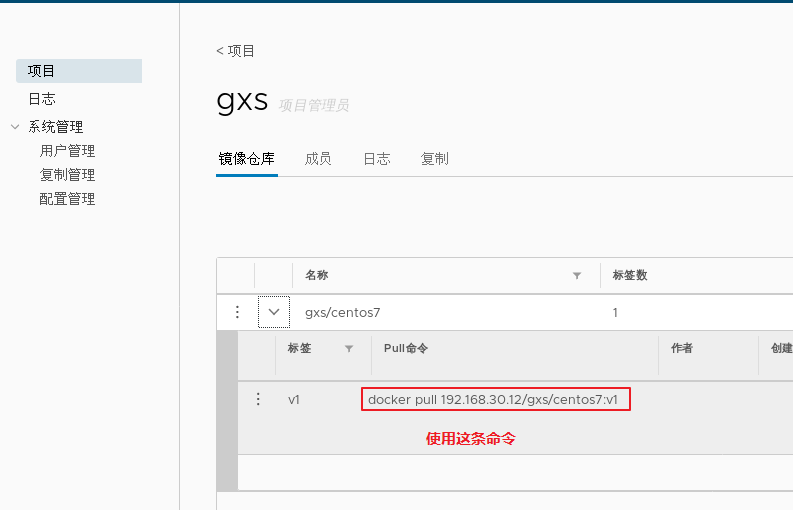
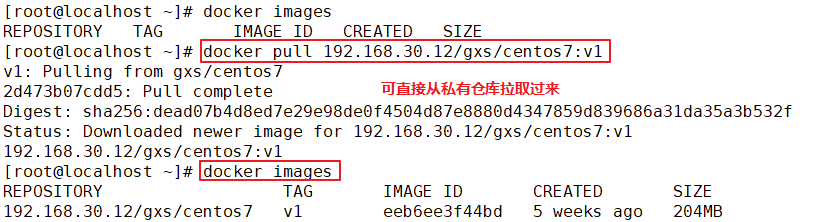
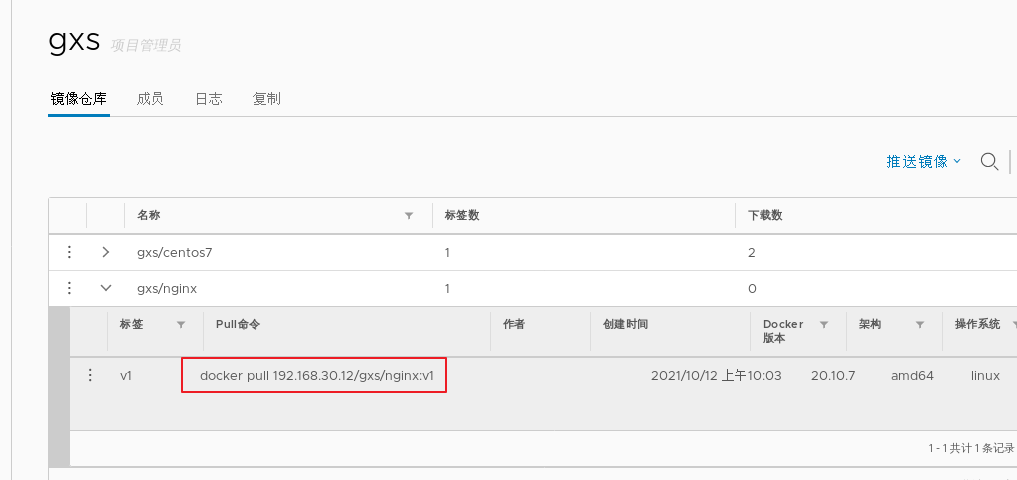
Maintenance management harbor
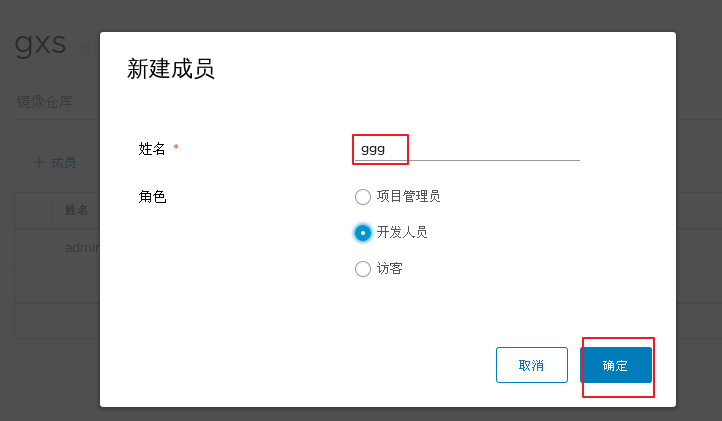
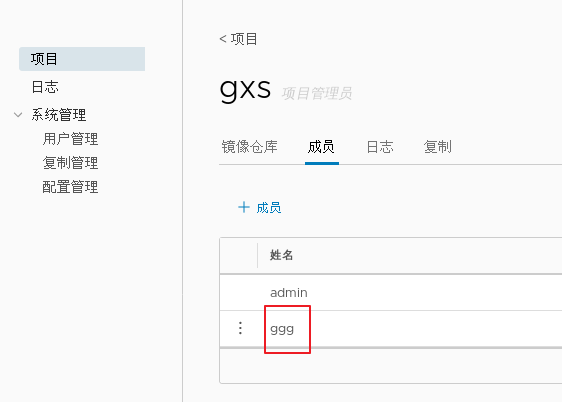
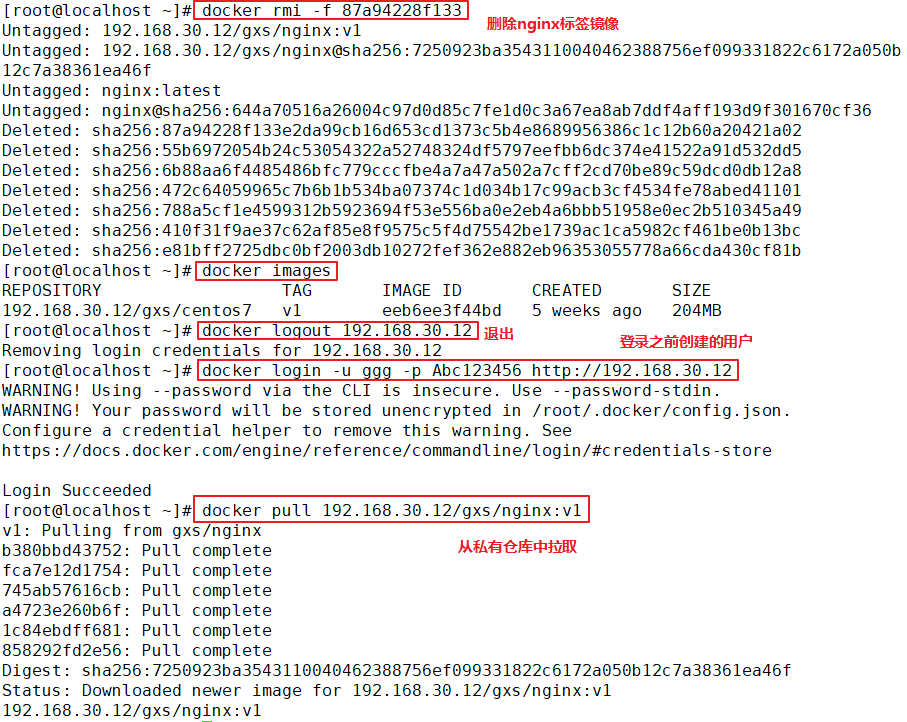
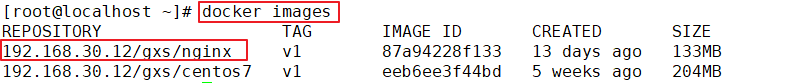
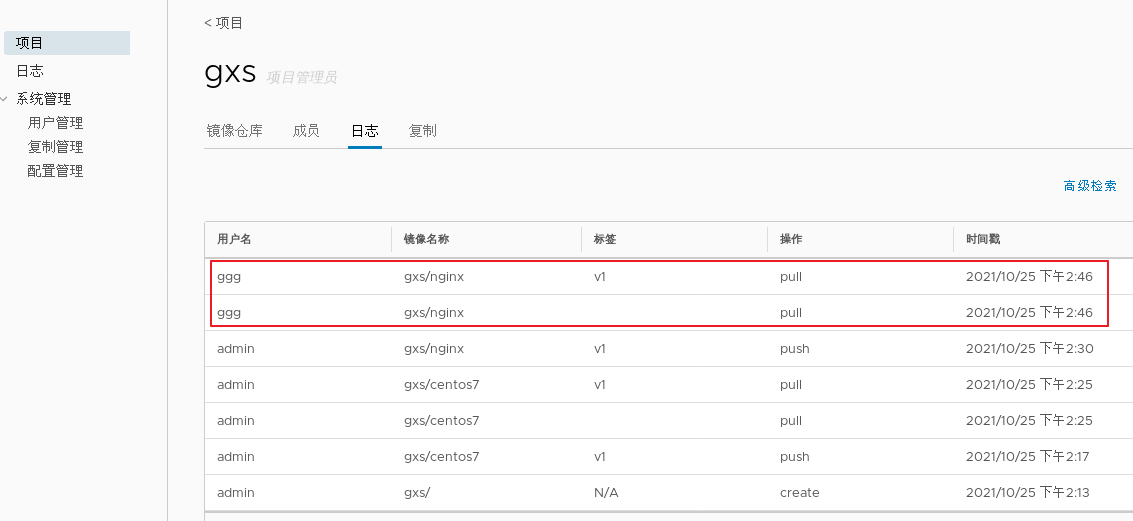
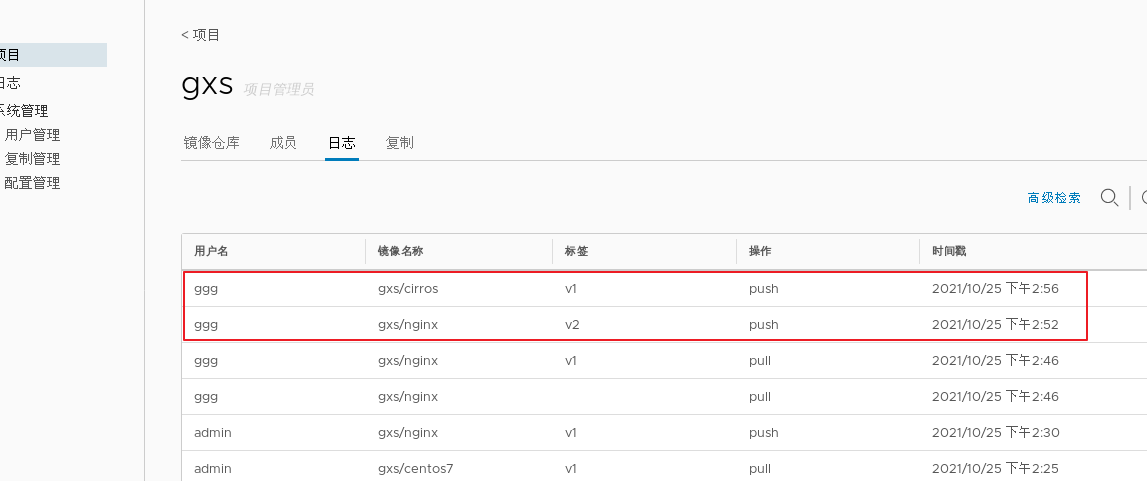
1.adopt Harbor Web Create project stay Harbor In the warehouse, any image is push reach regsitry Before, you must have a project to which you belong. Click“+Project ", fill in the project name, if the project level is set to"private",If it is set as a public warehouse, the owner has read permission for the image under this item, and it does not need to be executed on the command line"Docker login"You can download the image, and the image operation is the same as Docker Hub-To 2.establish Harbor user (1)Create users and assign permissions stay Web Click system management in the management interface->user management -> +Users, Fill in the user name as“ ggg",Mailbox is“ ggg@qq.com",The full name is“ aabbcc",Password is“ Abc123456",The comment is "Administrator"(Can be omitted). attach:After the user is created successfully, click on the left"...""Button to set the user created above as an administrator role or delete it. This example does not make any settings. (2)Add project members Click item-> gxs-> member-> +Member, fill in the user created above aabbcc And assign the role "developer". attach:Click the left side“..."Button can still change or delete member roles (3)Operate the image with a normal account on the client //Delete the above labeled local image docker rmi 192.168.30.12/gxs/cirros:v2 //Exit the current user first, and then log in using the account aabbcc created above docker logout 192.168.30.12 docker login 192.168.30.12 or docker login -u aabbcc -P Abc123456 http://192.168.30.12 //Download and upload images for testing docker pull 192.168.30.12/gxs/cirros:v2 docker tag cirros:latest 192.168.30.12/gxs/cirros:v3 docker push 192.168.30.12/gxs/cirros:v3 3.view log Web The operation log records user related operations in chronological order
Example:
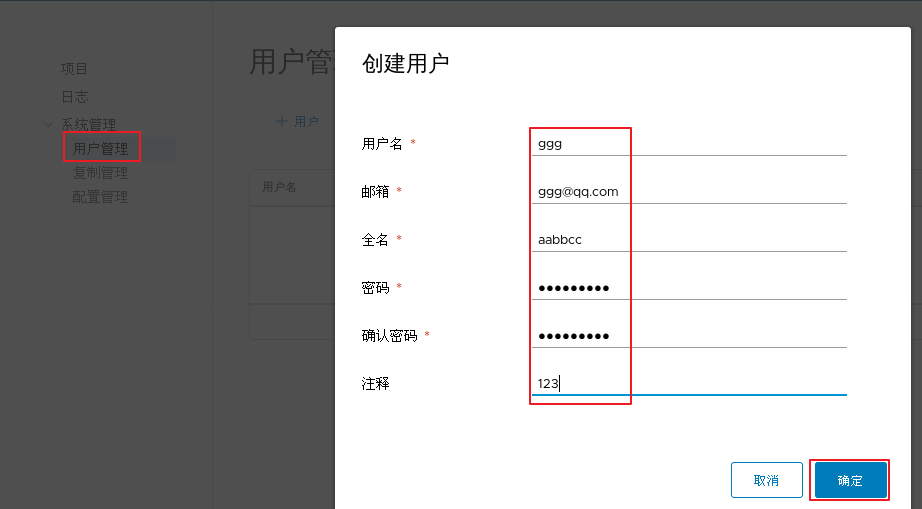
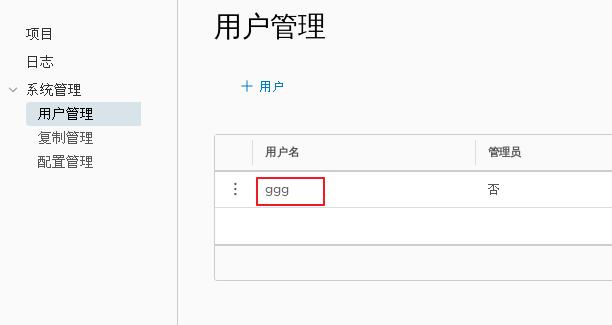
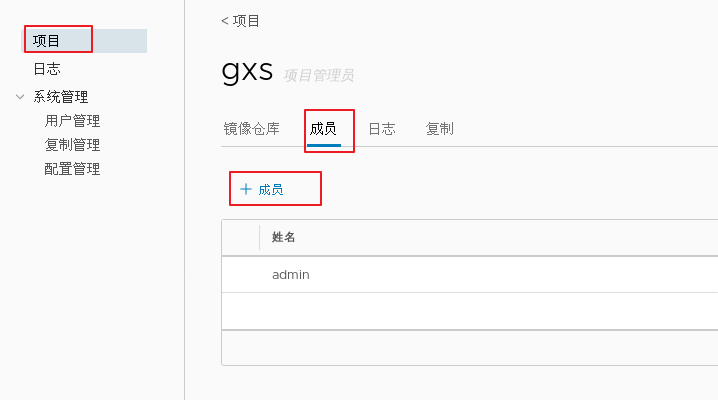
modify Harbor.cfg configuration file To change Harbour When selecting optional parameters in the configuration file of, please stop the existing configuration file first Harbour Instance and update Harbor.cfg; Then run prepare Script to populate the configuration: Finally, recreate and start Harbour Examples of. use docker-compose Administration Harbor When working with docker-compose.yml Run in the same directory. cd /usr/1oca1/harbor docker-compose down -v vim harbor.cfg #Only optional parameters can be modified ./prepare docker-compose up -d //If the following errors are reported, you need to turn on the firewall firewalld service Creating network "harbor_ harbor" with the default driver ERROR: Failed to Setup IP tables: Unable to enable SKIP DNAT rule: (iptables failed: iptables --wait -t nat -I DOCKER -i br-b53c314f45e8 -j RETURN: iptables: No chain/target/match by that name. (exit status 1) ) systemctl restart firewalld.service docker-compose up -d 5.remove Harbor The service container retains mirrored data at the same time/Database and migrate //Operate on Harbor server (1)remove Harbor Service container cd /usr/local/harbor docker-compose down -V (2)Package the image data in the project //Persistent data, such as images and databases, are in the / data / directory of the host, and logs are in the / var/log/Harbor / directory of the host ls /data/registry/docker/registry/v2/repositories/gxs cd /data/registry/docker/registry/v2/repositories/gxs tar zcvf gxs-registry.tar.gz ./* 6.If redeployment is required, it needs to be removed Harbor All data of service container cd /usr/local/harbor docker-compose down -v rm -r /data/database rm -r /data/registry