preface
Harbor is an open source enterprise Docker Registry project of VMware
1.Harbor's advantages
1. Role based control: there are administrators and ordinary users. Ordinary users can be empowered. For example, they can only upload and download, and can be operated and managed according to the project
2. Image based replication policy: it is also related to permissions. For example, only some users and groups can perform corresponding operations on this item
3. Support LDAP/AD: domain control, such as Nanjing to download Beijing harbor
The image of the private warehouse is marked at both ends, and the LAN address is connected one by one. The data information is transmitted through a tunnel and encrypted through two layers. The first layer is the tunnel
Encryption, the second layer is data encryption, safe and reliable
4. Image deletion and garbage collection: i.e. recycle bin mechanism
5. Graphical UI: it has statistical functions, such as traffic and image ^ download popularity
6. Audit: log is of little significance here, mainly with the help of ELK
7.RESTful API: defines the format of Web language specification, which is convenient for calling Harbor interface and secondary development
1.2 composition of harbor
| assembly | effect |
|---|---|
| Proxy | Receive the requests from the browser and Docker clients through a front-end reverse proxy, and forward the requests to different back-end services |
| Registry | (core component) is responsible for storing Docker images and handling docker push/pull commands |
| Core services | The core functions of Harbor include UI, webhook and token services |
| Database | Providing database services for core services |
| Log collector | Collect log s of other components for future analysis |
These components are packaged in containers and managed using docker compose orchestration
registry is a code repository
2.3 there are two types of parameters in Harbor.cfg configuration file
2.3.1 required parameters
If the user updates them and runs the install.sh script to reinstall Harbor, the parameters will take effect. Specific parameters are as follows:
**hostname: * * used to access the user interface and register service. It should be the IP address or fully qualified domain name (FQDN) of the target machine
For example, 192.168.35.40 or hub.klj.cn. Do not use localhost or 127.0.0.1 as the host name.
ui_url_protocol: (http or https, the default is http) the protocol used to access the UI and token / notification services. If notarization is enabled, this parameter must be https. (during authentication, the Mysql database will be compared and the token will be granted)
**max_job_workers: * * mirror copy job thread.
db_password: used for DB_ The password of the root user of auth's MySQL database.
**customize_crt: * * this attribute can be set to on or off. It is on by default. When this property is turned on, the preparation script creates a private key and root certificate for generating / validating registry tokens. Set this property to off when the key and root certificate are provided by an external source.
**ssl_cert: * * the path of the SSL certificate, which is only applied when the protocol is set to https.
ssl_cert_key: the path of the SSL key, which is only applied when the protocol is set to https.
secretkey_path: the key path used to encrypt or decrypt the remote register password in the replication policy.
2.3.2 optional parameters
These parameters are optional for updating, that is, users can keep them as default values and update them on the Web UI after starting Harbor.
If you enter Harbor.cfg, it will only take effect when you start Harbor for the first time. Subsequent updates to these parameters will be ignored.
Note: if you choose to set these parameters through the UI, make sure to do so immediately after starting Harbour. Specifically, the required auth must be set before registering or creating any new users in Harbor_ mode. When there are users in the system (except the default admin user), auth_mode cannot be modified. Specific parameters are as follows:
Email: Harbor needs this parameter to send "password reset" email to users, and only when this function is required.
Note that SSL connection is not enabled by default. If the SMTP server requires SSL but does not support STARTTLS, SSL email should be enabled by setting_ ssl = TRUE.
harbour_admin_password: the initial password of the administrator. It only takes effect when Harbour is started for the first time. After that, this setting will be ignored and the administrator's password should be set in the UI.
Note that the default username / password is admin/Harbor12345.
auth_mode: the authentication type used. By default, it is db_auth, that is, the credentials are stored in the database. For LDAP authentication (file authentication), set it to ldap_auth.
self_registration: enables / disables the user registration function. When disabled, new users can only be created by Admin users, and only administrator users can create new users in Harbour.
Note: when auth_mode is set to LDAP_ When auth, the self registration function will always be disabled and this flag is ignored.
Token_expiration: the expiration time (minutes) of the token created by the token service. The default is 30 minutes.
project_creation_restriction: flag used to control which users are authorized to create projects. By default, everyone can create a project. If its value is set to "adminonly", only admin can create projects.
verify_remote_cert: on or off. It is on by default. This flag determines whether the SSL/TLS certificate is verified when Harbor communicates with the remote register instance. Setting this property to off bypasses SSL/TLS authentication, which is often used when the remote instance has a self signed or untrusted certificate.
2. Deploy Harbor services
2.1 download Harbor installer
wget http:// harbor.orientsoft.cn/harbor-1.2.2/harbor-offline-installer-v1.2.2.tgz Or upload a compressed package harbor-offline-installer-v1.2.2.tgz tar zxvf harbor-offline-installer-v1.2.2.tgz -C /usr/local/
2.2 configuring Harbor parameter files
vim /usr/local/harbor/harbor.cfg 5 hostname = 192.168.226.128 ##Modify cost machine address
2.3 start Harbor
Before starting, confirm whether the docker compose version is installed successfully
[root@harbor ~]# docker-compose -v docker-compose version 1.21.1, build 5a3f1a3 [root@harbor ~]# sh /usr/local/harbor/install.sh ##Start Harbor; Relevant scripts have been defined in docker compose Creating network "harbor_harbor" with the default driver Creating harbor-log ... done Creating harbor-db ... done Creating registry ... done Creating harbor-adminserver ... done Creating harbor-ui ... done Creating harbor-jobservice ... done Creating nginx ... done ✔ ----Harbor has been installed and started successfully.----
2.4 viewing Harbor boot image
[root@harbor harbor]# cd /usr/local/harbor/
[root@harbor harbor]# docker-compose ps ##View currently running containers
Name Command State Ports
-------------------------------------------------------------------------------------------------------------------------------------------------------------
harbor-adminserver /harbor/harbor_adminserver Up
harbor-db docker-entrypoint.sh mysqld Up 3306/tcp
harbor-jobservice /harbor/harbor_jobservice Up
harbor-log /bin/sh -c crond && rm -f ... Up 127.0.0.1:1514->514/tcp
harbor-ui /harbor/harbor_ui Up
nginx nginx -g daemon off; Up 0.0.0.0:443->443/tcp,:::443->443/tcp, 0.0.0.0:4443->4443/tcp,:::4443->4443/tcp,
0.0.0.0:80->80/tcp,:::80->80/tcp
registry /entrypoint.sh serve /etc/ ... Up 5000/tcp
[root@harbor harbor]# cat /usr/local/harbor/docker-compose.yml ##View file content; Details of 7 components
version: '2'
services:
log:
image: vmware/harbor-log:v1.2.2
container_name: harbor-log
restart: always
volumes:
- /var/log/harbor/:/var/log/docker/:z
ports:
- 127.0.0.1:1514:514
networks:
- harbor
registry:
image: vmware/registry:2.6.2-photon
container_name: registry
restart: always
volumes:
- /data/registry:/storage:z
- ./common/config/registry/:/etc/registry/:z
networks:
- harbor
environment:
- GODEBUG=netdns=cgo
command:
["serve", "/etc/registry/config.yml"]
depends_on:
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://127.0.0.1:1514"
tag: "registry"
mysql:
image: vmware/harbor-db:v1.2.2
container_name: harbor-db
restart: always
volumes:
- /data/database:/var/lib/mysql:z
networks:
- harbor
env_file:
- ./common/config/db/env
depends_on:
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://127.0.0.1:1514"
tag: "mysql"
adminserver:
image: vmware/harbor-adminserver:v1.2.2
container_name: harbor-adminserver
env_file:
- ./common/config/adminserver/env
restart: always
volumes:
- /data/config/:/etc/adminserver/config/:z
- /data/secretkey:/etc/adminserver/key:z
- /data/:/data/:z
networks:
- harbor
depends_on:
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://127.0.0.1:1514"
tag: "adminserver"
ui:
image: vmware/harbor-ui:v1.2.2
container_name: harbor-ui
env_file:
- ./common/config/ui/env
restart: always
volumes:
- ./common/config/ui/app.conf:/etc/ui/app.conf:z
- ./common/config/ui/private_key.pem:/etc/ui/private_key.pem:z
- /data/secretkey:/etc/ui/key:z
- /data/ca_download/:/etc/ui/ca/:z
- /data/psc/:/etc/ui/token/:z
networks:
- harbor
depends_on:
- log
- adminserver
- registry
logging:
driver: "syslog"
options:
syslog-address: "tcp://127.0.0.1:1514"
tag: "ui"
jobservice:
image: vmware/harbor-jobservice:v1.2.2
container_name: harbor-jobservice
env_file:
- ./common/config/jobservice/env
restart: always
volumes:
- /data/job_logs:/var/log/jobs:z
- ./common/config/jobservice/app.conf:/etc/jobservice/app.conf:z
- /data/secretkey:/etc/jobservice/key:z
networks:
- harbor
depends_on:
- ui
- adminserver
logging:
driver: "syslog"
options:
syslog-address: "tcp://127.0.0.1:1514"
tag: "jobservice"
proxy:
image: vmware/nginx-photon:1.11.13
container_name: nginx
restart: always
volumes:
- ./common/config/nginx:/etc/nginx:z
networks:
- harbor
ports:
- 80:80
- 443:443
- 4443:4443
depends_on:
- mysql
- registry
- ui
- log
logging:
driver: "syslog"
options:
syslog-address: "tcp://127.0.0.1:1514"
tag: "proxy"
networks:
harbor:
external: false
2.5 accessing the UI interface of harbor
Open browser access http://192.168.226.128 The default administrator user name and password is admin/Harbor12345.
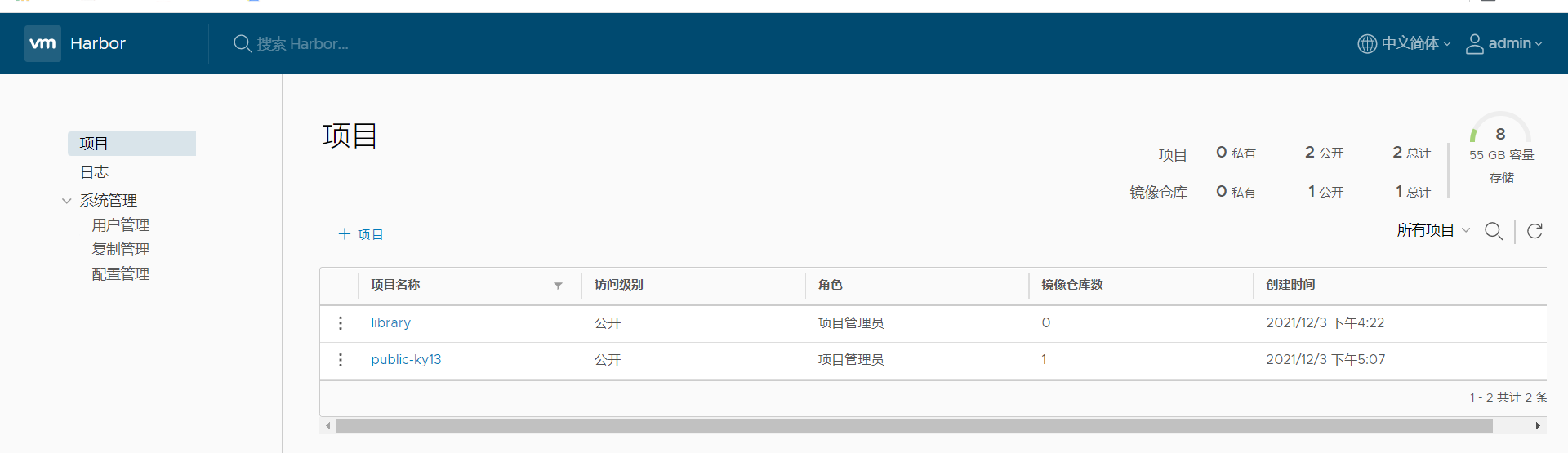
Add the project and fill in the project name mytest
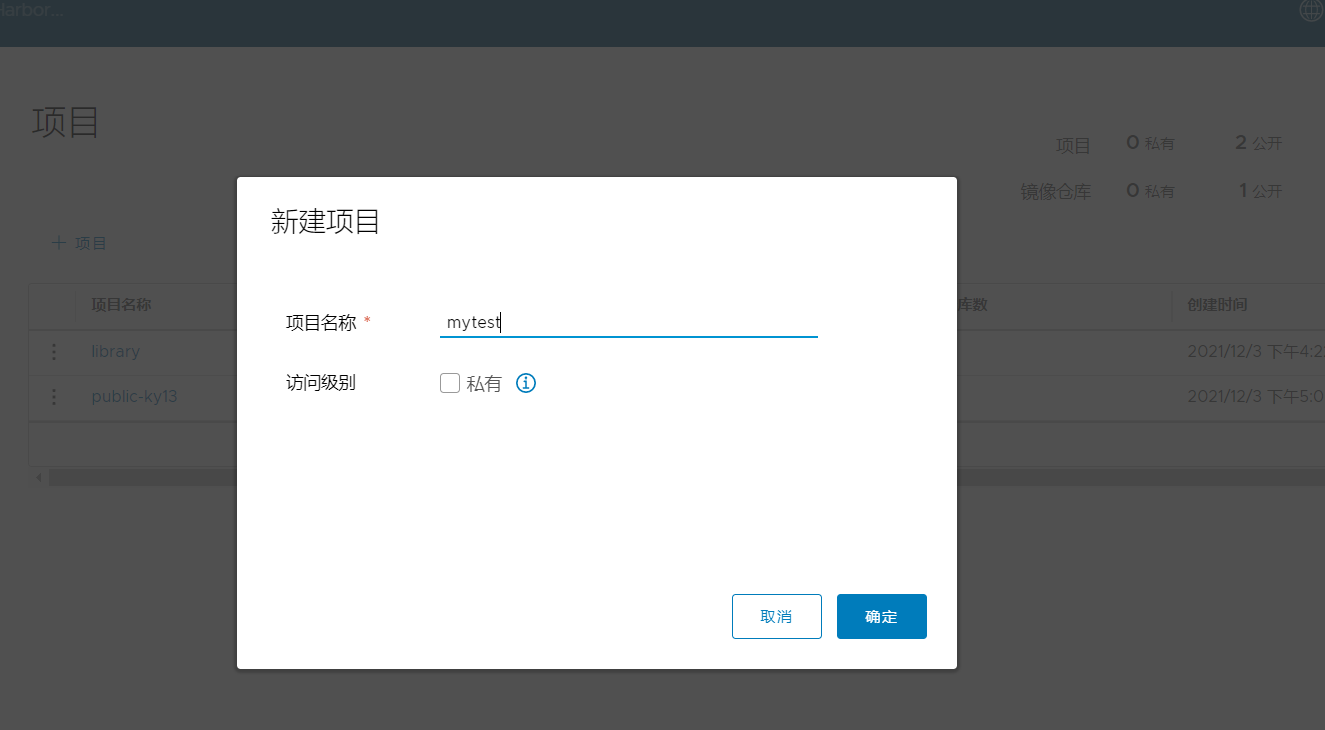
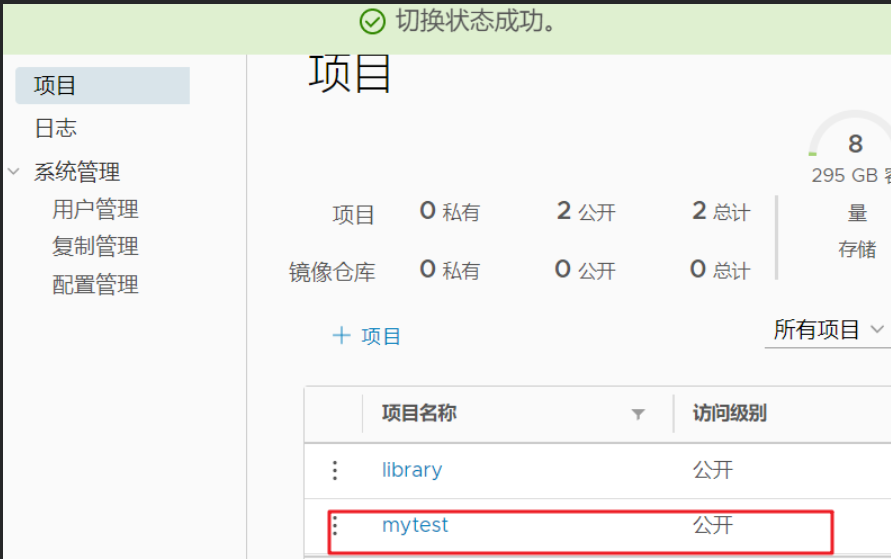
2.6 command line login to harbor
1.Harbor server is based on local operation
Use the Docker command to log in and push images locally through 127.0.0.1. By default, the Register server listens on port 80.
[root@harbor harbor]# docker login -u admin -p Harbor12345 http://127.0.0.1 ##// Sign in .... Login Succeeded [root@harbor harbor]# docker pull cirros ##Download the image for testing Using default tag: latest latest: Pulling from library/cirros d0b405be7a32: Pull complete bd054094a037: Pull complete c6a00de1ec8a: Pull complete Digest: sha256:1e695eb2772a2b511ccab70091962d1efb9501fdca804eb1d52d21c0933e7f47 Status: Downloaded newer image for cirros:latest docker.io/library/cirros:latest [root@harbor harbor]# docker tag cirros:latest 127.0.0.1/mytest/cirros:v1 ##Image labeling [root@harbor harbor]# docker push 127.0.0.1/mytest/cirros:v1 The push refers to repository [127.0.0.1/mytest-test/cirros] 984ad441ec3d: Preparing f0a496d92efa: Preparing e52d19c3bee2: Preparing denied: requested access to the resource is denied [root@harbor harbor]# docker tag cirros:latest 127.0.0.1/mytest/cirros ##Image labeling [root@harbor harbor]# docker push 127.0.0.1/mytest/cirros ##Upload image to Harbor Using default tag: latest The push refers to repository [127.0.0.1/mytest/cirros] 984ad441ec3d: Pushed f0a496d92efa: Pushed e52d19c3bee2: Pushed latest: digest: sha256:483f15ac97d03dc3d4dcf79cf71ded2e099cf76c340f3fdd0b3670a40a198a22 size: 943
2. Non local operation of harbor server
The above operations are performed locally on the Harbor server. If other clients upload images to Harbor, a message will be sent
The following error. The reason for this problem is that HTTPS is used by default for Docker Registry interaction, but private mirrors are built
For example, the HTTP service is used by default, so the following error occurs when interacting with the private image.
[root@client ~]# docker login -u admin -p Harbor12345 http://192.168.226.128 ## Non local login will report an error WARNING! Using --password via the CLI is insecure. Use --password-stdin. Error response from daemon: Get https://192.168.226.128/v2/: EOF [root@client ~]# vim /usr/lib/systemd/system/docker.service ##Point to private warehouse address 13 ExecStart=/usr/bin/dockerd -H fd:// --insecure-registry 192.168.35.40 --containerd=/run/containerd/containerd.sock [root@client ~]# systemctl daemon-reload [root@client ~]# systemctl restart docker [root@harbor harbor]# docker login -u admin -p Harbor12345 http://192.168.226.128 WARNING! Using --password via the CLI is insecure. Use --password-stdin. WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded [root@client ~]# docker pull cirros Using default tag: latest latest: Pulling from library/cirros Digest: sha256:1e695eb2772a2b511ccab70091962d1efb9501fdca804eb1d52d21c0933e7f47 Status: Image is up to date for cirros:latest docker.io/library/cirros:latest [root@client ~]# docker tag cirros 192.168.226.128/myproject-kgc/cirros:v2 [root@harbor harbor]# docker tag cirros:latest 192.168.226.128/mytest/cirros:1 [root@harbor harbor]# [root@harbor harbor]# docker push 192.168.226.128/mytest/cirros:1 The push refers to repository [192.168.226.128/mytest/cirros] 984ad441ec3d: Layer already exists f0a496d92efa: Layer already exists e52d19c3bee2: Layer already exists 1: digest: sha256:483f15ac97d03dc3d4dcf79cf71ded2e099cf76c340f3fdd0b3670a40a198a22 size: 943
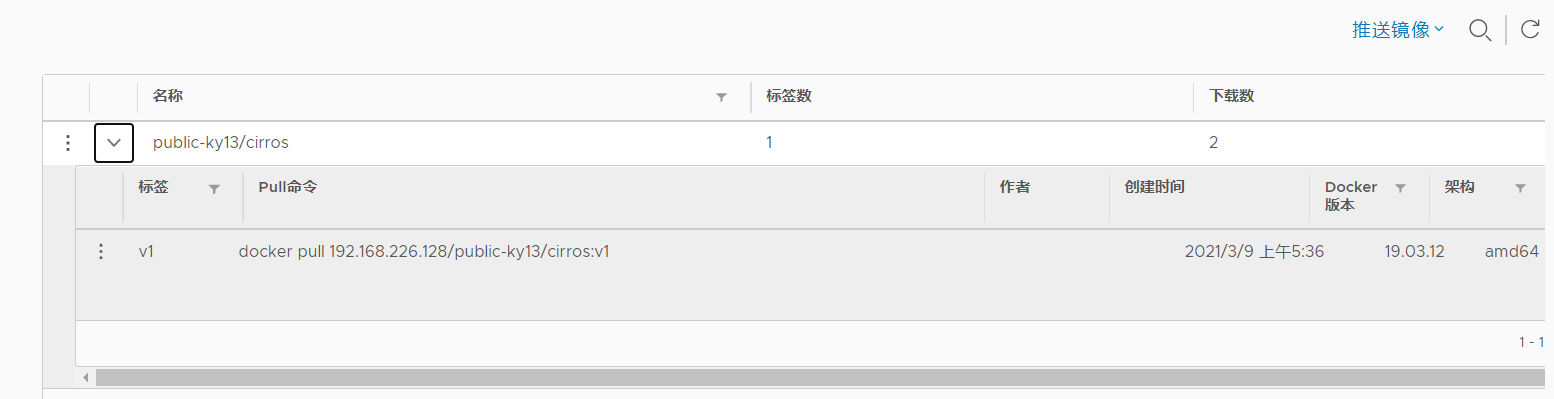
2.7 harbor user management
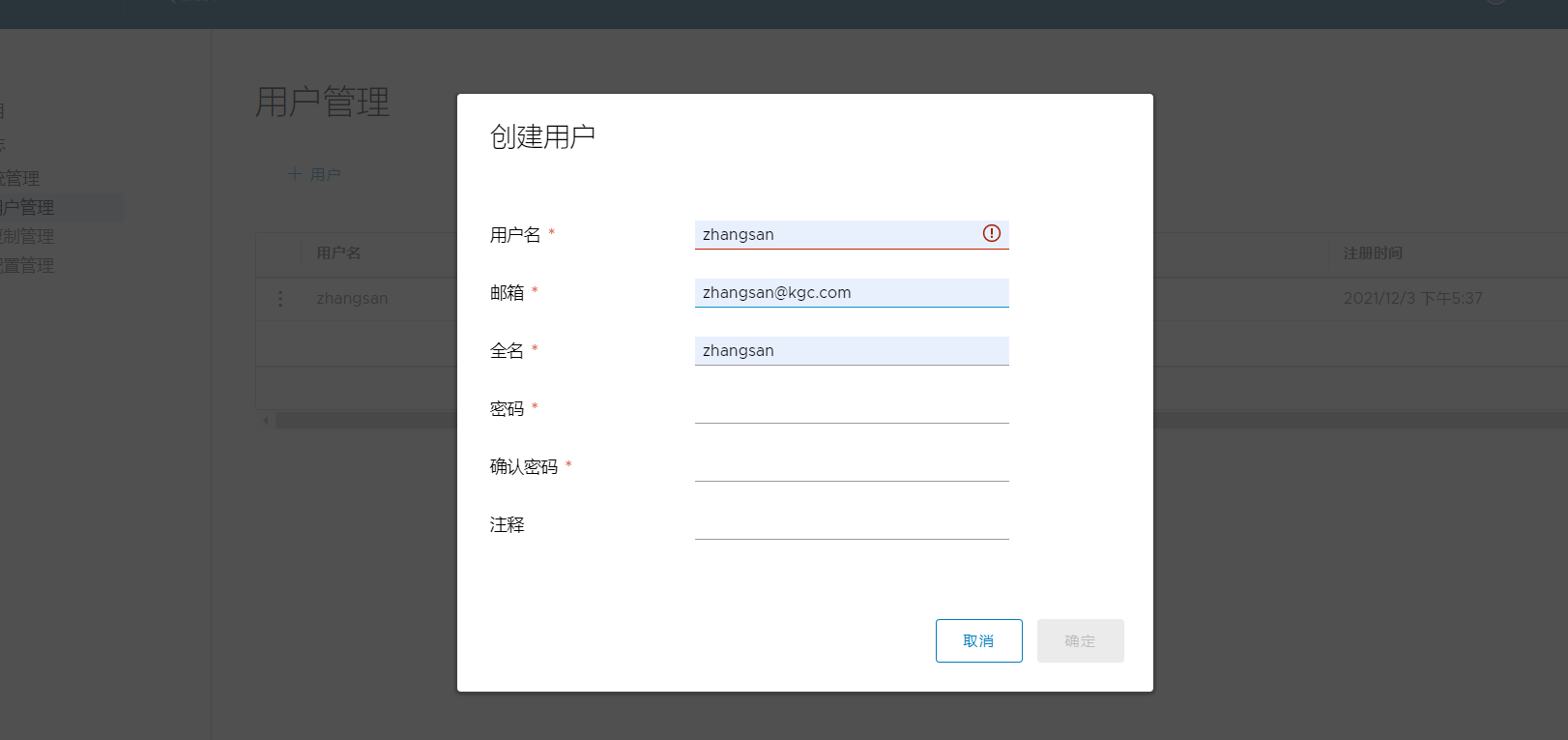
1. Create Harbor user
System management - user management - + user - enter user name, email address, full name and password
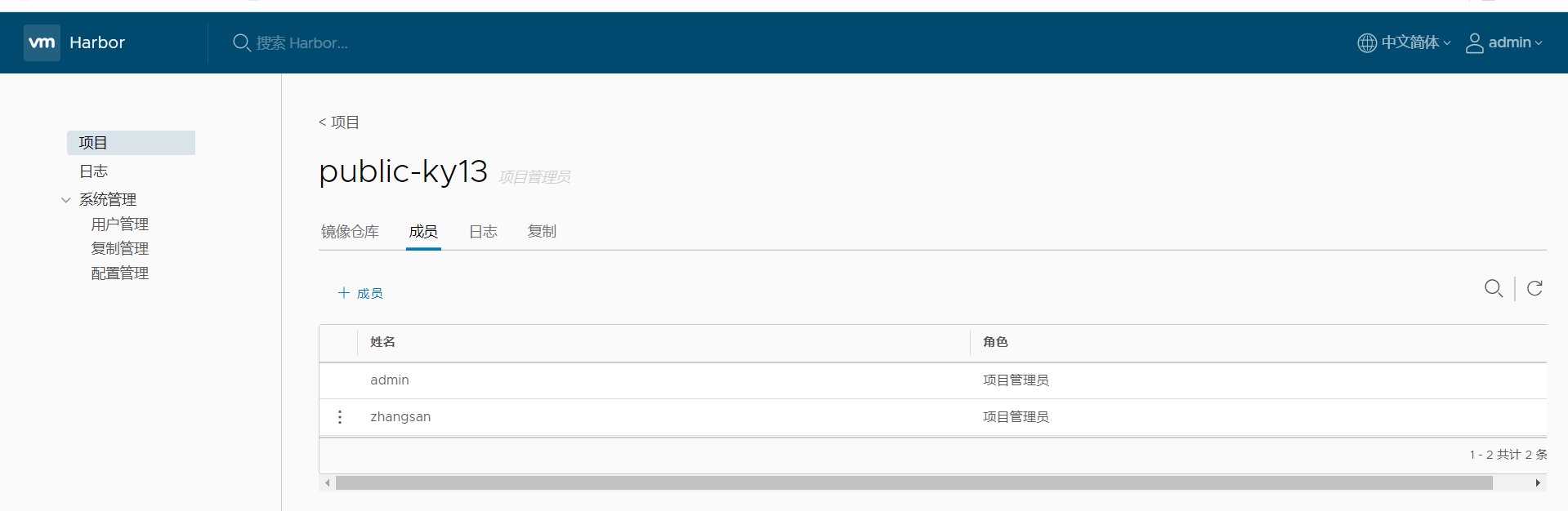
2. Add members to the project
3. Verify whether it can be downloaded using the identity of zhangsan user developer
//Operate on client [root@harbor harbor]# docker rmi 192.168.226.128mytest/cirros ##Delete previously downloaded images Untagged: 192.168.226.128/mytest/cirros:latest [root@client ~]# docker logout 192.168.226.128 ##Logout login Removing login credentials for 192.168.226.128 [root@harbor harbor]# docker login -u zhangsan -p Harbor12345 http://192.168.226.128 ## Sign in WARNING! Using --password via the CLI is insecure. Use --password-stdin. WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded [root@harbor harbor]# docker pull 192.168.226.128/mytest/cirros:latest latest: Pulling from mytest/cirros Digest: sha256:483f15ac97d03dc3d4dcf79cf71ded2e099cf76c340f3fdd0b3670a40a198a22 Status: Downloaded newer image for 192.168.226.128/mytest/cirros:latest 192.168.226.128/mytest/cirros:latest
2.8 maintenance management Harbor
have access to docker-compose To manage Harbor. Some useful commands are shown below and must be used with docker-compose.yml Run in the same directory. modify Harbor.cfg configuration file To change Harbour Please stop the existing configuration file first Harbour Instance and update Harbor.cfg;Then run prepare Script to fill in the configuration; Finally, recreate and start Harbour Examples of. docker-compose down -v Stopping nginx ... done Stopping harbor-jobservice ... done Stopping harbor-ui ... done Stopping harbor-adminserver ... done Stopping harbor-db ... done Stopping registry ... done Stopping harbor-log ... done Removing nginx ... done Removing harbor-jobservice ... done Removing harbor-ui ... done Removing harbor-adminserver ... done Removing harbor-db ... done Removing registry ... done Removing harbor-log ... done Removing network harbor_harbor [root@harbor harbor]# cd /usr/local/harbor/ [root@harbor harbor]# ./prepare Clearing the configuration file: ./common/config/adminserver/env Clearing the configuration file: ./common/config/ui/env Cleari: ng the configuration file: ./common/config/ui/app.conf Clearing the configuration file: ./common/config/ui/private_key.pem Clearing the configuration file: ./common/config/db/env Clearing the configuration file: ./common/config/jobservice/env Clearing the configuration file: ./common/config/jobservice/app.conf Clearing the configuration file: ./common/config/registry/config.yml Clearing the configuration file: ./common/config/registry/root.crt Clearing the configuration file: ./common/config/nginx/nginx.conf loaded secret from file: /data/secretkey Generated configuration file: ./common/config/nginx/nginx.conf Generated configuration file: ./common/config/adminserver/env Generated configuration file: ./common/config/ui/env Generated configuration file: ./common/config/registry/config.yml Generated configuration file: ./common/config/db/env Generated configuration file: ./common/config/jobservice/env Generated configuration file: ./common/config/jobservice/app.conf Generated configuration file: ./common/config/ui/app.conf Generated certificate, key file: ./common/config/ui/private_key.pem, cert file: ./common/config/registry/root.crt The configuration files are ready, please use docker-compose to start the service. [root@harbor harbor]# docker-compose up -d Creating network "harbor_harbor" with the default driver Creating harbor-log ... done Creating registry ... done Creating harbor-adminserver ... done Creating harbor-db ... done Creating harbor-ui ... done Creating nginx ... done Creating harbor-jobservice ... done