Basic concepts of docker roofing
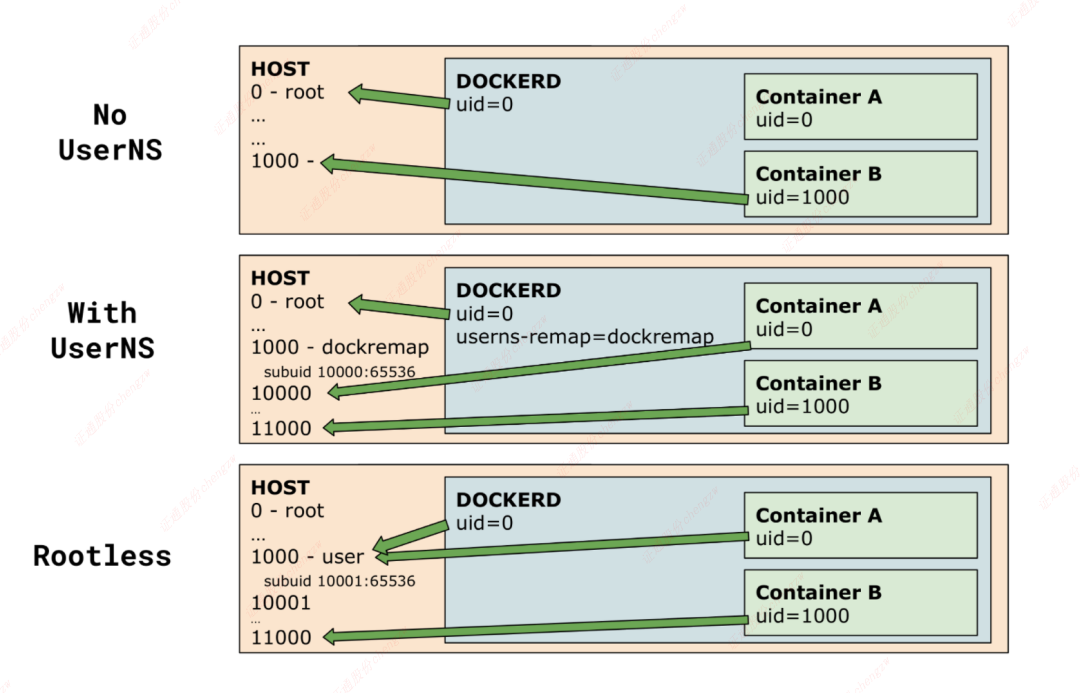
Rootless mode allows the Docker daemon and container to run as a non root user to mitigate potential vulnerabilities in the runtime of Docker daemon and container. Rootless mode was introduced as an experimental function in Docker v19.03 and GA in Docker v20.10.
At present, Rootless mode has certain restrictions on Cgroups resource control, appendor security configuration, Overlay network, storage driver, etc., and can not completely replace "Rootful" Docker for the time being. For details about Docker roofing, please refer to the official Docker document [run the Docker daemon as a non root user (roofing mode)]( https://docs.Docker.com/engine/security/Rootless/#limiting -resources)
Rootless mode uses user namespaces to connect the root user in the container with the docker daemon (docked) users are mapped to the range of non privileged users of the host. Docker has previously provided the -- users remap flag, which supports relevant capabilities and improves the security isolation of the container. Based on this, the rootless mode allows the docker daemon to run in the remapped user namespace.
Practical verification
Environmental preparation
This paper uses the virtual machine of Centos 7.5 operating system to experiment.
[root@demo ~]# cat /etc/redhat-release CentOS Linux release 7.5.1804 (Core)
Create user
useradd rootless echo 123456 | passwd rootless --stdin
Installation dependency
Rootless mode can run the Docker daemon and container without root permission, but newuidmap and newgidmap tools need to be installed to create subordinating user and group remapping in the user namespace. Install the newuidmap and newgidmap tools with the following command.
cat <<EOF | sudo sh -x curl -o /etc/yum.repos.d/vbatts-shadow-utils-newxidmap-epel-7.repo https://copr.fedorainfracloud.org/coprs/vbatts/shadow-utils-newxidmap/repo/epel-7/vbatts-shadow-utils-newxidmap-epel-7.repo yum install -y shadow-utils46-newxidmap cat <<EOT >/etc/sysctl.conf user.max_user_namespaces = 28633 EOT sysctl --system EOF
UID/GID mapping configuration
The mapping of dependent users and groups is controlled by two configuration files, / etc/subuid and / etc/subgid. Use the following command to set the mapping of 65536 dependent users and groups for rootless users.
echo "rootless:100000:65536" | tee /etc/subuid echo "rootless:100000:65536" | tee /etc/subgid
For subuid, the meaning of this line of record is: user rootless. In the current user namespace, there are 65536 dependent users with user IDs of 100000-165535. In a child user namespace, these dependent users are mapped to users with IDs of 0-65535. subgid has the same meaning as subuid.
For example, the user rootless is only a user with normal permissions on the host. We can assign a subordinate ID (such as 100000) to the user namespace to which the container belongs, and map the ID 100000 to the uid 0 in the user namespace. At this time, even if the process in the container has root permission, it is only in the user namespace where the container is located. Once it reaches the host, it will have rootless user permission at most.
Installing Rootless Docker
Switch to the rootless user.
su - rootless
Execute the following command to install roof docker.
curl -fsSL https://get.docker.com/rootless | sh
After successful installation, the following contents are displayed.
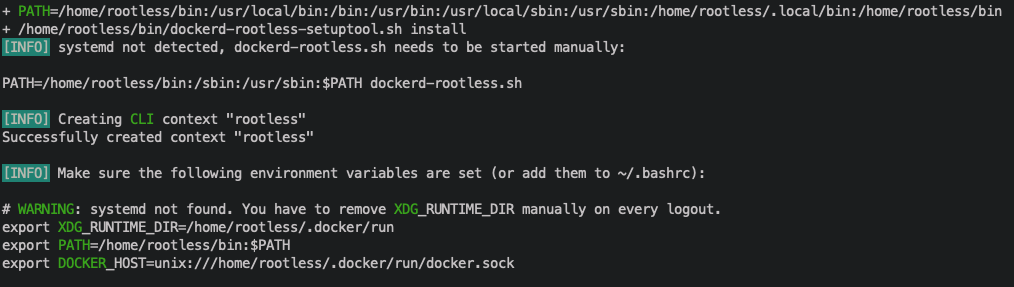
Add the following to ~ / In the bashrc file, use source ~ /. After adding The bashrc command takes the environment variable into effect.
export XDG_RUNTIME_DIR=/home/rootless/.docker/run export PATH=/home/rootless/bin:$PATH export DOCKER_HOST=unix:///home/rootless/.docker/run/docker.sock
Start Docker daemon
Start the Docker daemon with the following command.
dockerd-rootless.sh
Run container
Use the following command to start an nginx container and map port 80 to port 8080 of the host.
docker run -d -p 8080:80 nginx
View the container.
[rootless@demo ~]$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES f3b204c97a84 nginx "/docker-entrypoint...." 9 minutes ago Up 9 minutes 0.0.0.0:8080->80/tcp, :::8080->80/tcp bold_stonebraker
Access the container.
[rootless@demo ~]$ curl http://localhost:8080
# Return result Nginx welcome interface
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
reference material
- [container safety collection - a preliminary study of roof container]( https://developer.aliyun.com/article/700923)
- [Run the Docker daemon as a non-root user (Rootless mode)] (https://docs.docker.com/engine/security/rootless/)
- [Experimenting with Rootless Docker] (https://medium.com/@tonistiigi/experimenting-with-rootless-docker-416c9ad8c0d6)
- [on Docker's security support (Part 2)]( http://blog.itpub.net/31559359/viewspace-2645966/ )
- [introduction and practice of Docker v20.10 core functions]( https://mp.weixin.qq.com/s/iMF211vWL722Wqxw9mRf7A)
- [shadow-utils-newxidmap] (https://copr.fedorainfracloud.org/coprs/vbatts/shadow-utils-newxidmap/)
- [Hardening Docker Daemon with Rootless Mode] (https://www.youtube.com/watch?v=uWURUtqLiqQ)
- [Linux Namespace : User] (https://www.cnblogs.com/sparkdev/p/9462838.html)
- [understand uid and GID in docker container]( https://www.cnblogs.com/sparkdev/p/9614164.html )
- [isolate users in docker container]( https://www.cnblogs.com/sparkdev/p/9614326.html)