The old draft has not been sent, and it has been sent out and saved in the blog. I haven't been in touch with security for a long time. I've been learning data structures and algorithms.
Introduction to Burpsuite sequencer
BurpSuite series (VII) -- Sequencer module (Sequencer)
As a tool used to detect the randomness quality of data samples in Burp Suite, burp sequencer is usually used to detect whether the access token is predictable and whether the password reset token is predictable. Through the data sample analysis of Sequencer, the risk of forgery of these key data can be well reduced.
Effective entropy: effective entropy
significance level
The significance level is used to estimate the probability of possible errors when the overall parameters fall within a certain interval α express.
The significance level is to determine an allowable small probability standard as the judgment limit in advance when conducting hypothesis test. In the test, the probability is divided into two intervals according to the significance level. The probability interval less than the given standard is called the rejection interval, and the probability interval greater than this standard is the acceptance interval. The event belongs to the acceptance range, and the original hypothesis is true without significant difference; The event belongs to the rejection interval, which rejects the original hypothesis and considers that there is a significant difference.
Session ID introduction
Authentication means such as passwords and certificates are generally only used for the Login process. When the Login is completed, the user accesses the page of the website. It is impossible to use password authentication every time the browser requests a page. Therefore, when the certification is completed. You need to replace a credential that is transparent to users. This voucher is Session.
After the user logs in, a new Session will be created on the server side, in which the user's status and related information will be saved. The server maintains the sessions of all online users. For authentication at this time, you only need to know which user is browsing the current page. In order to tell the server which Session to use, the browser needs to inform the server of the Session ID held by the current user.
Once the Session ID is stolen in the life cycle, it is equivalent to account theft. At the same time, since session is the authentication certificate held by the user after logging in, there is no need to crack the password.
Low Weak Session IDs Source
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id'])) {
$_SESSION['last_session_id'] = 0;//Start from scratch
}
$_SESSION['last_session_id']++;//Increase by one each time
$cookie_value = $_SESSION['last_session_id'];
setcookie("dvwaSession", $cookie_value);
unsafe.
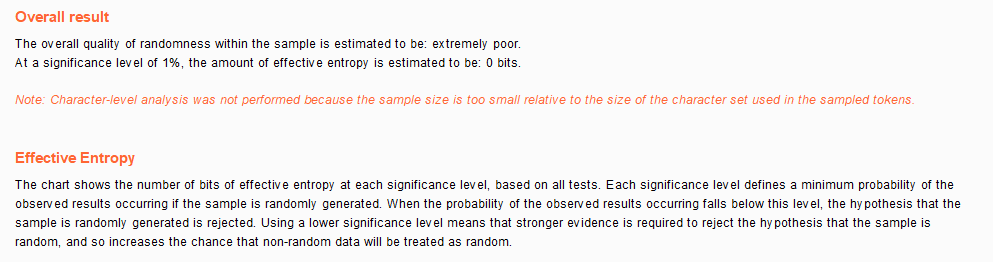
Medium Weak Session IDs Source
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = time();
setcookie("dvwaSession", $cookie_value);
}
?>
Take the time value as the cookie value, and you can find the rule by enumerating it many times
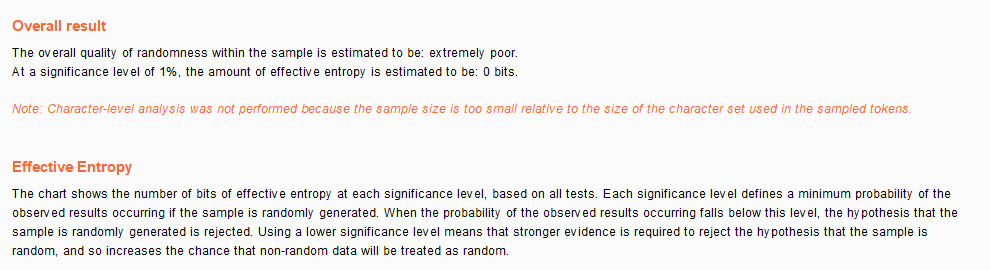
High Weak Session IDs Source
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
if (!isset ($_SESSION['last_session_id_high'])) {
$_SESSION['last_session_id_high'] = 0;
}
$_SESSION['last_session_id_high']++;
$cookie_value = md5($_SESSION['last_session_id_high']);
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulnerabilities/weak_id/", $_SERVER['HTTP_HOST'], false, false);
}
?>
//Although from the beginning, first increase by 1, then use md5 encryption, and set the cookie survival time to 3600 seconds, which is a better defense
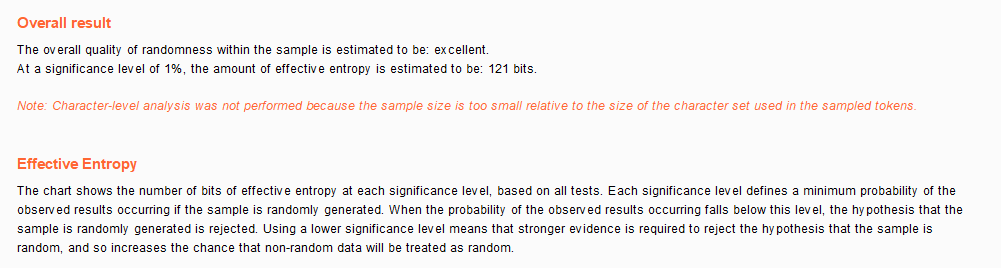
Impossible Weak Session IDs Source
<?php
$html = "";
if ($_SERVER['REQUEST_METHOD'] == "POST") {
$cookie_value = sha1(mt_rand() . time() . "Impossible");
setcookie("dvwaSession", $cookie_value, time()+3600, "/vulnerabilities/weak_id/", $_SERVER['HTTP_HOST'], true, true);
}
?>
sha-1 encryption is adopted here, and it is based on the set of random numbers linearly connected with time, which is almost impossible to crack. And set the cookie to live for 6 minutes.
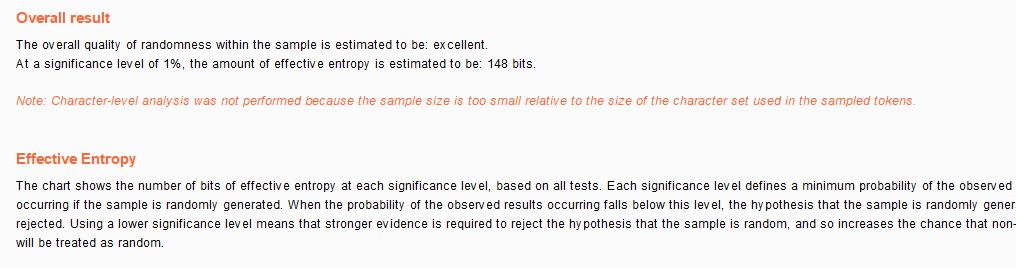
enlightenment
To set the cookie value as randomly as possible, it should be combined with sha-1 algorithm, mt_rand().time(), set the cookie lifetime.