1, Target
Recently, when capturing an e-commerce App, I found an encrypted data. When it made a communication address request, the requested data was encrypted. The address information in the returned data is also ciphertext.

Today, our goal is to encrypt and decrypt this data.
App version: v10 three
2, Steps
Analyze it
1. The end of the data is "= =", indicating that it is Base64 encoded. Then we can try to go to the Hook Base64 related functions, and then print the stack.
2. If the returned data format is json, we can try the Hook json related parsing function.
3. Another way is to try to search the key strings of CityName, CountryName and Where.
Search the string first
Search the longest "Where"
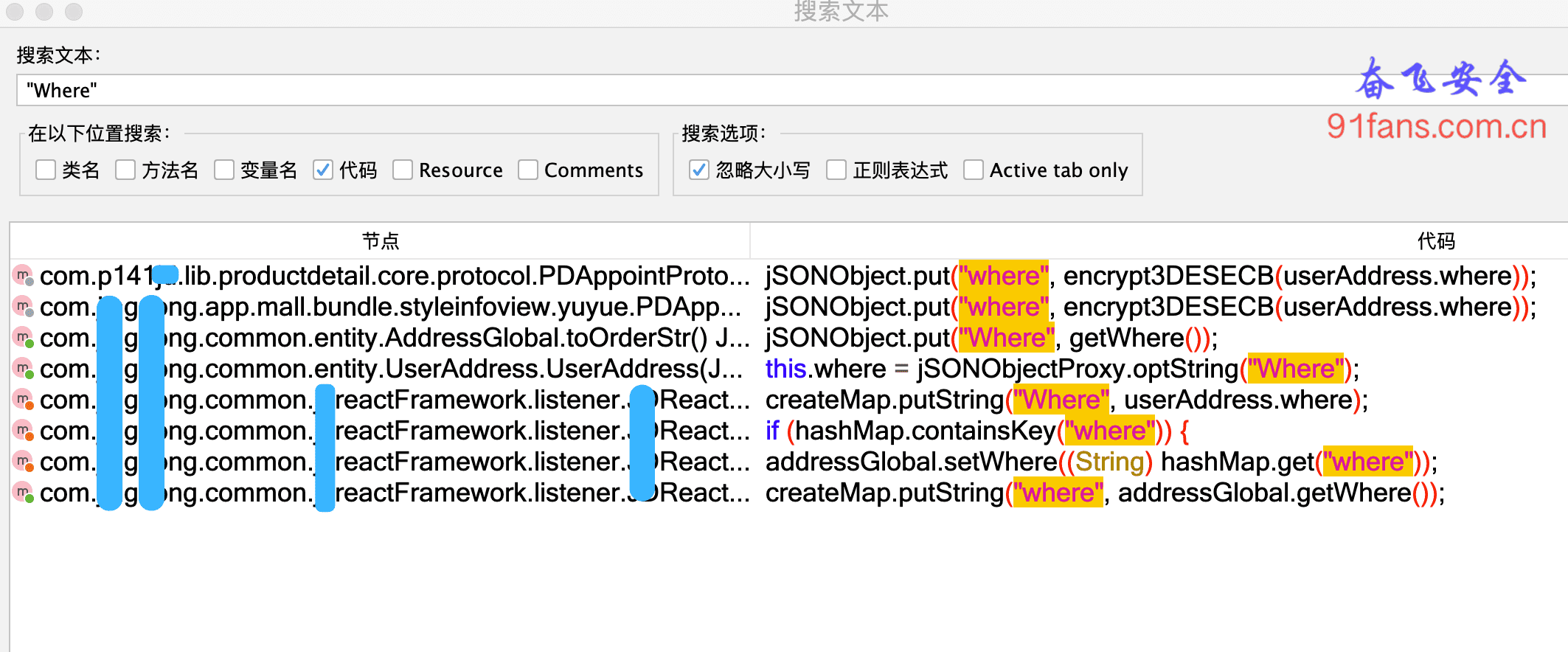
The encrypted function encrypt3DESECB was found, but the decrypted function was not found. However, the encryption and decryption rates are probably in the same class file.

Following the clue, we found here.
Don't say anything, Hook.
On Frida
var utilsCls = Java.use('com.xx.lib.productdetail.core.utils.PDUtils');
utilsCls.encrypt.overload('java.lang.String', 'boolean', 'java.lang.String').implementation = function(a,b,c){
var result = this.encrypt(a,b,c);
console.log(">>> encrypt a=" + a + ",b=" + b + ",c=" + c);
console.log("rc=" + result);
return result;
}
utilsCls.decrypt.overload('java.lang.String', 'boolean', 'java.lang.String').implementation = function(a,b,c){
var result = this.decrypt(a,b,c);
console.log(">>> decrypt a=" + a + ",b=" + b + ",c=" + c);
console.log("rc=" + result);
return result;
}Run. This time, I use the Attach mode, which may prompt that the package name cannot be found. I tried to use the Chinese name of the App, but it can be attached. It's amazing.
TIP: remember to refer to the previous article http://91fans.com.cn/post/ldqsignone/ Change frida port number
Let's click "address management". Unfortunately, there is no output. It seems that I found something wrong.
Once more
Now expand the point range and search where

The results are not many, more than 200 items. In detail, this big brother is the most suspicious.
1. The class name AddressSelectView looks like an assignment to the address page.
2. The function setWhere looks like assigning a value to an address variable.
Let's go in and have a look
optString = optBoolean ? DesCbcCrypto.decrypt(optString, generateKey, (byte[]) null) : DesCommonUtils.decryptThreeDESECB(optString, generateKey);
Found two decryption functions. Hook them both first.
var StrCls = Java.use('java.lang.String');
var desCbcCls = Java.use('com.xx.xxsdk.security.DesCbcCrypto');
desCbcCls.encrypt.overload('java.lang.String','java.lang.String','[B','java.lang.String').implementation = function(a,b,c,d){
var result = this.encrypt(a,b,c);
console.log("### encrypt original text = "+ a +", key = "+ B +", d = "+ D");
console.log("rc=" + bytesToBase64(result));
return result;
}
desCbcCls.decrypt.overload('java.lang.String','java.lang.String','[B').implementation = function(a,b,c){
var result = this.decrypt(a,b,c);
console.log("### decrypt ciphertext = "+ a +", key = "+ b);
console.log("rc=" + StrCls.$new(result));
return result;
}
var desCommonCls = Java.use('com.xxngxxng.common.entity.DesCommonUtils');
desCommonCls.encryptThreeDESECB.implementation = function(a,b){
var result = this.encryptThreeDESECB(a,b);
console.log("### encryptThreeDESECB a=" + a + ",b=" + b ) ;
console.log("rc=" + result);
return result;
}
desCommonCls.decryptThreeDESECB.implementation = function(a,b){
var result = this.decryptThreeDESECB(a,b);
console.log("### decryptThreeDESECB a=" + a + ",b=" + b ) ;
console.log("rc=" + result);
return result;
}All right, put your hands together this time and run again.

No problem. It's over.
3, Summary
String search can appropriately expand the scope.
The base64 algorithm is too easy to implement, so the Hook standard Base64 algorithm may not work well. At this time, you can try to search the base64 string in the code. If you are lucky, you can find the base64 algorithm implemented in the App.
Usually, after several rounds of version iteration of App, the encryption and decryption algorithm may have been upgraded for several rounds, so don't drill a bull's horn. The algorithm you see at first glance may be an old algorithm. Don't be discouraged. You can continue to look for it.
Night never treats people who sleep late. It will give you dark circles under your eyes and a body that is about to die suddenly.
TIP: the only purpose of this article is to learn more reverse skills and ideas. If someone uses this technology to engage in illegal business and obtain benefits, the legal responsibility is borne by the operator, which has nothing to do with this article and the author. The code projects involved in this article can be taken by the friends who are struggling, Welcome to join the knowledge planet to learn and explore technology.