Article catalog
1, Demand analysis
Simulator: Cisco packet tracker version 5.3.3.0019
As shown in the figure below, four departments of a company's Beijing headquarters are connected to the core switch through the switch. The headquarters has four departments: finance, R & D, senior management and Information Center, each of which belongs to a VLAN. We need to configure port security and flow control on the layer 2 switch. In order to ensure the security of the sensitive data of the finance department, we need to configure the security policy on the three-layer switch, which only allows the senior management department to access the finance department. In order to prevent DoS denial of service attack on the exit router connected to the external network, we need to configure the extended ACL on the exit router, and do not allow the users of the external network to ping the exit router
2, Network topology
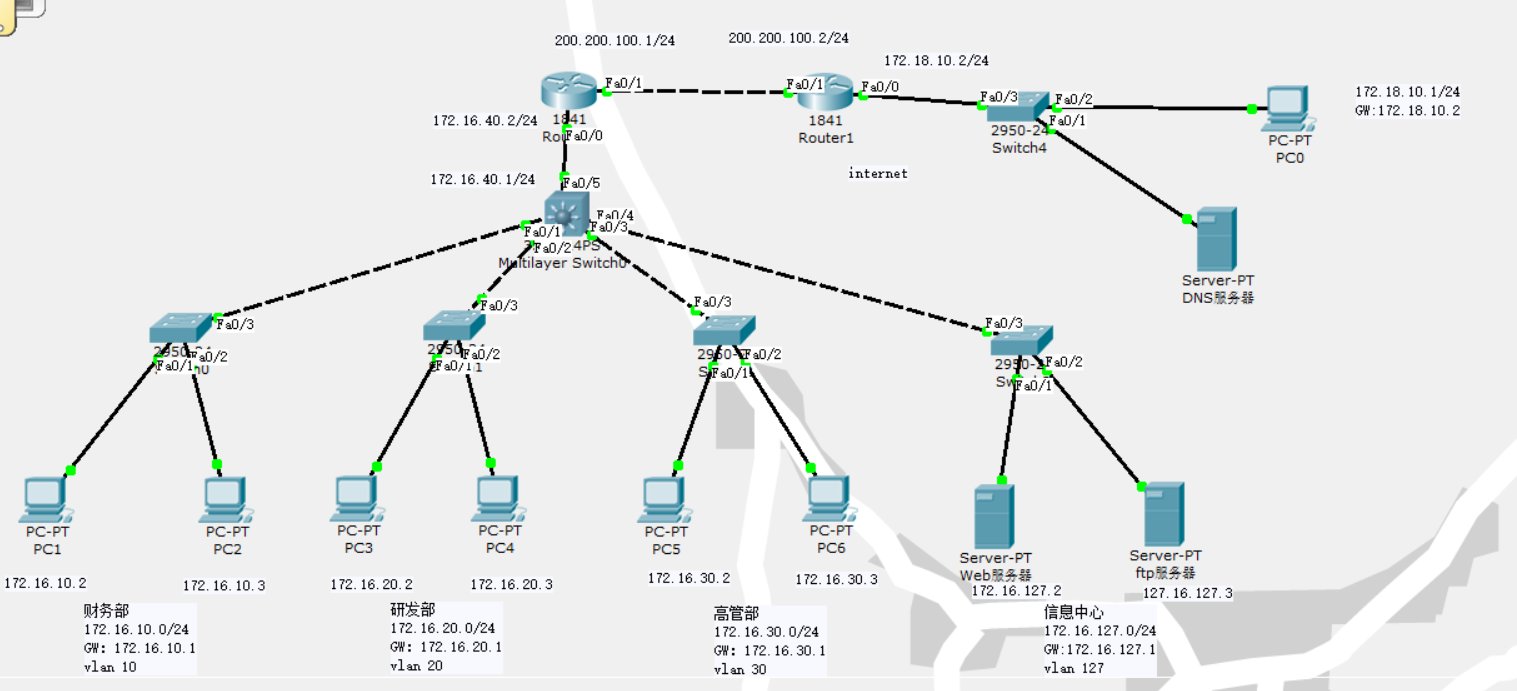
3, ip address planning and design
| department | ip address | gateway | VLAN |
|---|---|---|---|
| Finance Department | 172.16.10.0/24 network segment | 172.16.10.1 | 10 |
| R & D department | 172.16.20.0. / 24 network segment | 172.16.20.1 | 20 |
| Senior management department | 172.16.30.0/24 network segment | 172.16.30.1 | 30 |
| Information Center | 172.16.127.0/24 network segment | 172.16.172.1 | 127 |
4, Main equipment configuration scheme
1. Three layer switch
① Turn on the routing function and create the corresponding SVI interface
Single arm routing or SVI virtual switching interface can be used for VLAN communication. Because single arm routing has bandwidth limitation and single point failure, it uses more SVI virtual switching interface to let different VLANs communicate. SVI uses a three-layer switch. Each VLAN has and only has one SVI port. IP is configured on the SVI port. The gateway of the terminal points to the IP address of this VLAN on the layer-3 switch.
Switch(config)#ip routing //Enable routing Switch(config)#vlan 10 %LINK-5-CHANGED: Interface Vlan10, changed state to up Switch(config-vlan)#exit Switch(config)#int vlan 10 Switch(config-if)#ip add 172.16.10.1 255.255.255.0 Switch(config-if)#no shut Switch(config-if)#exit Switch(config)#vlan 20 Switch(config-vlan)#exit Switch(config)#int vlan 20 %LINK-5-CHANGED: Interface Vlan20, changed state to up Switch(config-if)#ip add 172.16.20.1 255.255.255.0 Switch(config-if)#no shut Switch(config-if)#exit Switch(config)#vlan 30 Switch(config-vlan)#exit Switch(config)#int vlan 30 Switch(config-if)# %LINK-5-CHANGED: Interface Vlan30, changed state to up Switch(config-if)#ip add 172.16.30.1 255.255.255.0 Switch(config-if)#no shut Switch(config-if)#exit Switch(config)#vlan 127 Switch(config-vlan)#exit Switch(config)#int vlan 127 Switch(config-if)# %LINK-5-CHANGED: Interface Vlan127, changed state to up Switch(config-if)#ip add 172.16.127.1 255.255.255.0 Switch(config-if)#no shut Switch(config-if)#exit Switch(config)#
② Set Fa0/5 interface to router as three-layer interface
Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface FastEthernet0/5 Switch(config-if)#no switchport Switch(config-if)#ip add 172.16.40.1 255.255.255.0 Switch(config-if)#no shut Switch(config-if)#exit Switch(config)# Switch#
③ The interface directly connected to the layer-2 switch encapsulates the dot1q protocol, which is set as trunk link, allowing multiple VLANs to pass through
Switch(config)#int range fa 0/1-4 Switch(config-if-range)#switchport mode trunk Switch(config-if-range)#switchport trunk encapsulation dot1q Switch(config-if-range)#exit Switch(config)#
④ Set Access Control List ACL and apply it to vlan 10
The extended access list is set here. In fact, the standard access control list can also be used to restrict the communication between the finance department and the departments other than the senior management department.
switch(config)#access-list 100 permit ip 172.16.10.0 0.0.0.255 172.16.30.0 0.0.0.255 switch(config)#access-list 100 deny ip any any switch(config)#int vlan 10 switch(config-if)#ip acc switch(config-if)#ip access-group 100 in switch(config-if)#exit switch(config)# switch#
⑤ Use OSPF protocol for route update summary
Switch(config)#router ospf 1 Switch(config-router)#network 172.16.10.0 0.0.0.255 area 0 Switch(config-router)#network 172.16.20.0 0.0.0.255 area 0 Switch(config-router)#network 172.16.30.0 0.0.0.255 area 0 Switch(config-router)#network 172.16.127.0 0.0.0.255 area 0 Switch(config-router)#network 172.16.40.0 0.0.0.255 area 0 Switch(config-router)#exit Switch(config)#
⑥ Limit port traffic based on MAC address
//The port traffic is limited by MAC address. This configuration allows a TRUNK port to pass 100 MAC addresses at most. If the MAC address exceeds 100, the data frame from the new host will be lost. switch(config)#int fa 0/1 switch(config-if)#switchport port-security maximum 50 //The maximum number of MAC addresses allowed for this port is 50. switch(config-if)#switchport port-security violation protect //When the number of host MAC addresses exceeds 50, the switch continues to work, but data frames from the new host will be lost. switch(config)#int fa 0/2 switch(config-if)#switchport port-security maximum 50 switch(config-if)#switchport port-security violation protect switch(config)#int fa 0/3 switch(config-if)#switchport port-security maximum 50 switch(config-if)#switchport port-security violation protect
2. Router 0
① Do napt address translation
Router(config)#ip nat pool to-internet 200.200.100.1 200.200.100.1 netmask 255.255.255.0 //Define address pool Router0(config)#access-list 1 permit 172.16.10.0 0.0.0.255 //Define allowed translation address Router0(config)#access-list 2 permit 172.16.20.0 0.0.0.255 Router0(config)#access-list 3 permit 172.16.30.0 0.0.0.255 Router0(config)#access-list 4 permit 172.16.127.0 0.0.0.255 Router0(config)#ip nat inside source list 1 pool to-internet overload //Translate address pool for internal local calls Router0(config)#ip nat inside source list 2 pool to-internet overload Router0(config)#ip nat inside source list 3 pool to-internet overload Router0(config)#ip nat inside source list 4 pool to-internet overload //Port mapping, which maps the 80 port and 21 port of the public ip we own to two servers respectively Router0(config)#ip nat inside source static tcp 172.16.127.2 80 200.200.100.1 80 Router0(config)#ip nat inside source static tcp 172.16.127.3 21 200.200.100.1 21 Router0(config)#int fa 0/0 //Define internal interface Router0(config-if)#ip nat inside Router0(config-if)#exit Router0(config)#int fa 0/1 //Define external interface Router0(config-if)#ip nat outside Router0(config-if)#exit Router0(config)#
② Using OSPF dynamic routing protocol to update and summarize routes
Router0(config)#router ospf 1 Router0(config-router)#network 172.16.40.0 0.0.0.255 area 0 Router0(config-router)#network 200.200.100.0 0.0.0.255 area 0
③ Set the access control list, do not allow the external network device to ping the router's external network exit
Router0(config)#access-list 100 deny icmp any any echo Router0(config)#access-list 100 permit ip any any Router0(config)#int fa 0/1 Router0(config-if)#ip access-group 100 in Router0(config-if)#exit Router0(config)#
3. Router 1
① Using OSPF dynamic routing protocol to update and summarize routes
Router1(config)#router ospf 1 Router1(config-router)#network 200.200.100.0 0.0.0.255 area 0 Router1(config-router)#network 172.18.10.0 0.0.0.255 area 0 Router1(config-router)#exit Router1(config)#
② NAPT conversion
Router(config)#access-list 1 permit 172.18.10.0 0.0.0.255 Router(config)#ip nat pool to-internet 200.200.100.2 200.200.100.2 netmask 255.255.255.0 Router(config)#ip nat inside source list 1 pool to-internet overload Router(config)#int fa 0/0 Router(config-if)#ip nat inside Router(config-if)#exit Router(config)#int fa 0/1 Router(config-if)#ip nat outside Router(config-if)#exit
4. Layer 2 switch
Create a vlan on each layer 2 switch and add the port to the vlan
①switch0 vlan 10
Switch0(config)#vlan 10 Switch0(config-vlan)#exit Switch0(config)#int range fa 0/1-2 Switch0(config-if-range)#switchport mode access Switch0(config-if-range)#switchport access vlan 10 Switch0(config-if-range)#exit Switch0(config)#
②switch 1 vlan 20
Switch1(config)#vlan 20 Switch1(config-vlan)#exit Switch1(config)#int range fa 0/1-2 Switch1(config-if-range)#switchport mode access Switch1(config-if-range)#switchport access vlan 20 Switch1(config-if-range)#exit Switch1(config)#
③switch 2 vlan 30
Switch2(config)#vlan 30 Switch2(config-vlan)#exit Switch2(config)#int range fa 0/1-2 Switch2(config-if-range)#switchport mode access Switch2(config-if-range)#switchport access vlan 30 Switch2(config-if-range)#exit Switch2(config)#
④switch 3 vlan 127
Switch3(config)#vlan 127 Switch3(config-vlan)#exit Switch3(config)#int range fa 0/1-2 Switch3(config-if-range)#switchport mode access Switch3(config-if-range)#switchport access vlan 127 Switch3(config-if-range)#exit Switch3(config)#
Bind port to MAC address
//Switch switch0 Switch0(config)#int range fa 0/1-2 Switch0(config-if-range)#switchport port-security //Turn on port security mode Switch0(config-if-range)#switchport port-security violation restrict //Set the measures to be taken when a security violation is detected, discard all packets from the insecure host at the port security process level, and increase the security violation count. Switch0(config-if-range)#switchport port-security mac-address sticky //Binding the MAC address with reliable viscosity will automatically learn the MAC address of the first connected device and bind it to the port Switch0(config-if-range)#exit Switch0(config)#exit //Note: you can ping another host connected to this switch, so that you can learn the MAC address of the connected port device, and then bind it automatically //Otherwise, the following table will not display binding information switch0# show port-security address //View port binding information Secure Mac Address Table --------------------------------------------------------------------------------- Vlan Mac Address Type Ports Remaining Age (mins) ---- ----------- ----------- --------------- ------------- 10 0001.9753.07E6 SecureSticky FastEthernet 0/1 - 10 0005.5E80.674B SecureSticky FastEthernet0/2 - --------------------------------------------------------------------------------- Total Addresses in System (excluding one mac per port) :0 Max Addresses limit in System (excluding one mac per port) : 1024 switch0# //Switch switch1 switch1(config)#int range fa 0/1-2 switch1(config-if-range)#switchport-s switch1(config-if-range)#switchport port switch1(config-if-range)#switchport port-security switch1(config-if-range)#switchport port-security violation restrict switch1(config-if-range)#switchport port-security mac-address sticky switch1(config-if-range)#exit switch1(config)#exit //Note: you can ping another host connected to this switch, so that you can learn the MAC address of the connected port device, and then bind it automatically //Otherwise, the following table will not display binding information switch1# show port-security address //View port binding information Secure Mac Address Table --------------------------------------------------------------------------------- Vlan Mac Address Type Ports Remaining Age (mins) ---- ----------- ----------- --------------- ------------- 20 00E0.A369.CCA9 SecureSticky FastEthernet0/1 - 20 0007.ECC1.0B62 SecureSticky FastEthernet0/2 - --------------------------------------------------------------------------------- Total Addresses in System (excluding one mac per port) :0 Max Addresses limit in System (excluding one mac per port) : 1024 switch1# //Switch 2 switch2(config)#int range fa 0/1-2 switch2(config-if-range)#switchport port-security switch2(config-if-range)#switchport port-security violation restrict switch2(config-if-range)#switchport port-security mac-address sticky switch2(config-if-range)#exit switch2(config)#exit //Note: you can ping another host connected to this switch, so that you can learn the MAC address of the connected port device, and then bind it automatically //Otherwise, the following table will not display binding information switch2# show port-security address //View port binding information Secure Mac Address Table --------------------------------------------------------------------------------- Vlan Mac Address Type Ports Remaining Age (mins) ---- ----------- ----------- --------------- ------------- 30 00E0.F7EE.1A8D SecureSticky FastEthernet0/1 - 30 0010.11C0.E382 SecureSticky FastEthernet0/2 - --------------------------------------------------------------------------------- Total Addresses in System (excluding one mac per port) :0 Max Addresses limit in System (excluding one mac per port) : 1024 switch2# //Switch 3 switch3(config)#int range fa 0/1-2 switch3(config-if-range)#switchport po switch3(config-if-range)#switchport port-security switch3(config-if-range)#switchport port-security violation restrict switch3(config-if-range)#switchport port-security mac-address sticky switch3(config-if-range)#exit switch3(config)#exit //Note: you can ping another host connected to this switch, so that you can learn the MAC address of the connected port device, and then bind it automatically //Otherwise, the following table will not display binding information switch3# show port-security address //View port binding information Secure Mac Address Table --------------------------------------------------------------------------------- Vlan Mac Address Type Ports Remaining Age (mins) ---- ----------- ----------- --------------- ------------- 127 0030.F228.3956 SecureSticky FastEthernet0/1 - 127 0003.E492.B354 SecureSticky FastEthernet0/2 - --------------------------------------------------------------------------------- Total Addresses in System (excluding one mac per port) :0 Max Addresses limit in System (excluding one mac per port) : 1024 switch3#
5. Network test
① napt conversion test
//First Ping the 200.200.100.2 of the external network with the internal PC 172.16.20.2, and then check the address conversion table Router0#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 200.200.100.1:9 172.16.20.2:9 200.200.100.2:9 200.200.100.2:9 Router0#
② External network ping router external network exit test
ping fails, ACL takes effect
Router1#ping 200.200.100.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 200.200.100.1, timeout is 2 seconds: UUUUU Success rate is 0 percent (0/5) Router1#
③ Access test of Finance Department
//R & D department ping finance department, no communication allowed PC>ping 172.16.10.2 Pinging 172.16.10.2 with 32 bytes of data: Request timed out. Request timed out . Request timed out . Request timed out . Ping statistics for 172. 16.10.2: Packets: Sent = 4,Received = 0,Lost = 4 (100 % loss) , PC> //The senior management department ping the finance department, which can communicate PC>ping 172. 16.10.2 Pinging 172.16.10.2 with 32 bytes of data: Reply from 1 72.16.10.2: bytes=32 time=18ms TTL=127 Reply from 172.16.10.2: bytes=32 time=13ms TTL=127 Reply from 172.16.10.2: bytes=32 time=14ms TTL=127 Reply from 172.16. 10.2: bytes=32 time=18ms TTL=127 Ping statistics for 172.16.10.2: Packets: Sent = 4,Received = 4,Lost = 0 (0% loss) , Approximate round trip times in mill i- seconds : Minimum = 1 3ms, Maximum = 1 8ms,Average = 1 5ms PC>
④ Port security test
//After the MAC address of the PC is changed, it is found that it is unable to communicate with other devices, and the port security works, and the packet is discarded
⑤ Internal access to WEB and FTP server test
//WEB, DNS service test Web Browser < > URL http: //www.test.com/index.html Go Stop Cisco Packet Tracer Welcome to Cisco Packet Tracer. Opening doors to new opportunities. Mind Wide Open. Quick Links: A sma11 paze Copyri shts Image page Image //FTP service test PC>ftp 172.16.127.3 Trying to connect. . .172.16.127.3 Connected to 172.16.127 .3 220- Welcome to PT Ftp server Username: cisco 331- Username ok, need password Password: 230- Logged in (passive mode On) ftp>dir Listing /ftp directory from 172. 16.127.3: 0 : c1841 -advipservicesk9-mz.124-15.T1 .bin 33591768 1 : c1841 -ipbase-mz.123-14.T7.bin 13832032 2 : c1841- ipbasek9-mz.124-12.bin 16599160 ftp>
⑥ External access to WEB and FTP server test
//WEB, DNS service test Web Browser < > URL http: //www.test.com/index.html Go Stop Cisco Packet Tracer Welcome to our company Quick Links: A sma11 paze Copyri shts Image page Image //FTP service test PC>ftp ftp.test.com Trying to connect. . .ftp.test.com Connected to 172.16.127 .3 220- Welcome to PT Ftp server Username: cisco 331- Username ok, need password Password: 230- Logged in (passive mode On) ftp>