View and read permissions
I Permission view
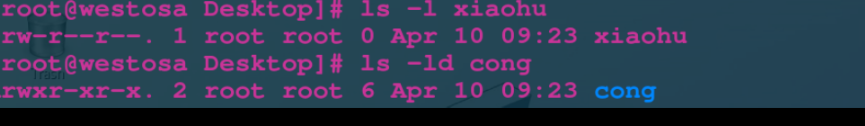
ls -l file view file permissions
ls -ld dir view directory permissions
II Understanding permissions
File permission information

Directory permission information

$: explanation for each digit
[1] File type
-Ordinary file d catalogue l Soft connection b Fast equipment c Character device s socket socket p The Conduit "|"
[2] User rights
[3] selinux on the system
[4] For files: the number of times the file content is recorded by the system (number of hard links)
For directory: the number of subdirectories in the directory
[5] File owner
[6] File owning group
[7] For files: file content size
For directory: the metadata size of the sub file in the directory
[8] Time when the file content was modified
[9] File name
Types and functions of common permissions
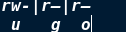
1. User's identity to the file
u: user The owner of the document, ls -l See the fifth column of information g: group File owning group, ls -l See the sixth column of information o: other A generic name for other users who are neither owners nor group members
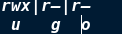
2. Permission bit
3. User identity matching
user>group>other
4. Permission type
- Permission not opened r readable For files: you can read the contents of the file For directories: Yes ls Lists the files in the directory w Writable For files: you can change the contents of the file For directory: you can create or delete files in the directory x Executable For files: the program recorded in the file can be called with the file name For directory: you can enter the directory
III How to set normal permissions
chmod - + - set file permissions
chmod copy permissions
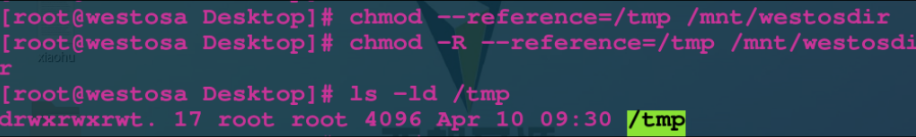
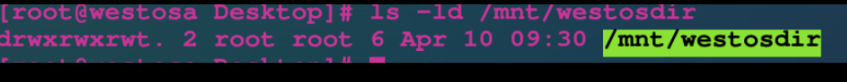
chmod --reference = /tmp/mnt/westosdir $:copy/tmp Directory permissions to/mnt/westosdir upper chmod -R --reference=/tmp /mnt/westosdir $:copy/tmp Directory permissions to/mnt/westosdir And sub files in the directory -R Represents the second return operation
chmod character setting permission
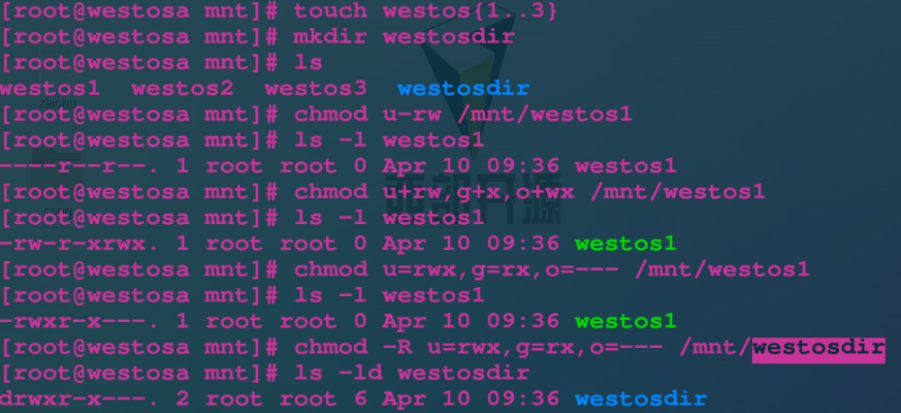
chmod <a|u|g|o><+|-|=><r|w|x> file $:Set file permissions in the form of word copy chmod -R <a|u|g|o><+|-|=><r|w|x> catalogue
EG
chmod digital setting permission
Permission Bohr refers to the representation
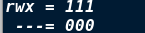
The maximum range that can be represented by three bit binary is 8-digit
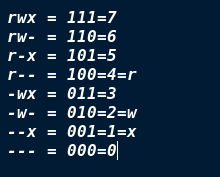
System default permission settings
From the point of view of security, the smaller the power sharing system, the higher the security of the system. We should not only ensure the security of the system, but also create value for the system, so we should open the power that should be opened by default and retain the unsafe power by default.
<1> How does umask retain power
umask $: View reserved rights umask Permission value $: Temporarily set the reserved power of the system
File default permission = 777-umask-111
Directory default permission = 777 umask
The greater the umask value, the higher the system security
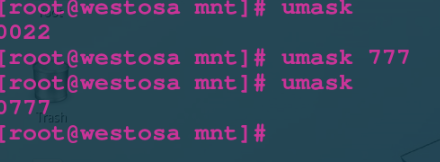
a.umask temporary changes
umask 077
b. Permanent change
First, we open the vim /etc/bashrc shell system configuration file
 Then transfer to the corresponding code.
Then transfer to the corresponding code.
 Change 022 to 077
Change 022 to 077
 Then open the vim/etc/profile system environment configuration file
Then open the vim/etc/profile system environment configuration file
 The operation is the same as above
The operation is the same as above

 Reuse
Reuse
**source /etc/bashrc** $:source When working, the content we change is immediately recognized by the system **source /etc/profile**
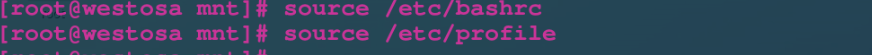
Complete, this is the permanent change.
IV Management of file users and user groups
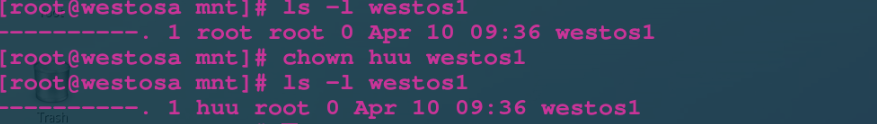
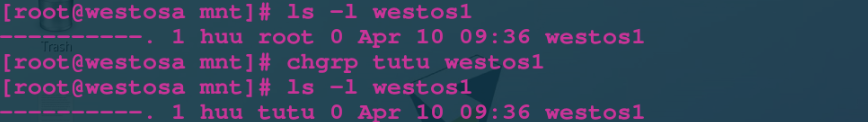
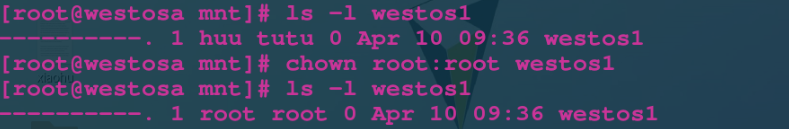
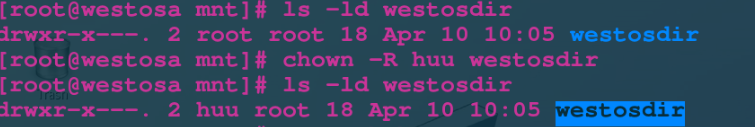
chown username file Change file owner chgrp groupname file Change file ownership group chown username:groupname file Change the owner and ownership group of the file at the same time chown|chgrp -R user | group dir Change the owner or group of the directory itself and the contents in the directory
The specific operations are as follows:

V Management of special permissions
1.stickyid sticking position
For directory: # if a directory stickyid is enabled, the files in this directory can only be deleted by the file owner
chmod 1 Original permissions dir chmod o+t dir
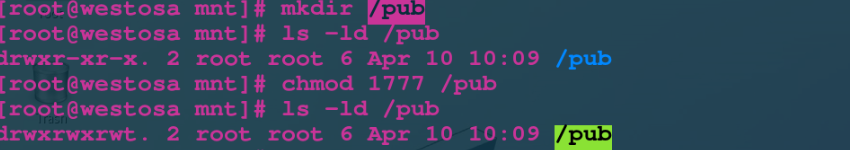
experiment:
su - westos ----> touch /pub/westosfile
exit
su - lee --------> touch /pub/leefile
rm -fr /pub/leefile # can be deleted
rm -fr /pub/westosfile # files that do not belong to you can also be deleted
But when we give it stickyid, we can solve this problem:
chmod 1777 /pub
chmod o+t /pub
The above two commands can open the t permission of the pub directory
su - westos ----> touch /pub/westosfile
exit
su - lee --------> touch /pub/leefile
rm -fr /pub/leefile # can be deleted
rm -fr /pub/westosfile # does not belong to its own file and cannot be deleted
Sgid.2 mandatory bit
You can make the newly created files in the directory automatically belong to the group to which the directory belongs
chmod 2 source file permission dir
chmod g+s dir
experiment:
First, we create files under ordinary users. We can see that the file group created by the user is the file of the user
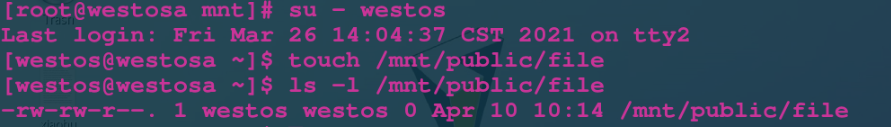 Then we give sgid rights to super users. When we switch to ordinary users to create files, we can see that the file owning group has nothing to do with the operator, but automatically belongs to the name of the group to which the directory belongs:
Then we give sgid rights to super users. When we switch to ordinary users to create files, we can see that the file owning group has nothing to do with the operator, but automatically belongs to the name of the group to which the directory belongs:
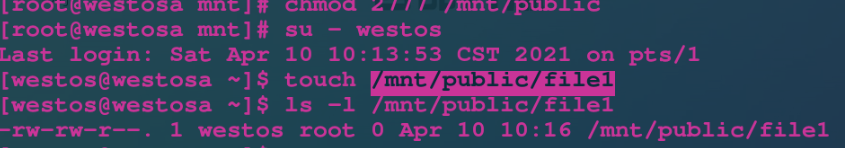
$: only for binary executable files (c programs). When running binary executable files, they are run as a file owning group, which has nothing to do with the execution user.
3.suid adventure bit
(the landlord will not insert screenshots here. Friends can try to see them by themselves. Screenshots are really eye-catching, alas)
$: only for binary executables (c programs). When running binary executable files, they are run as the file owner, which has nothing to do with the execution user.
chmod 4 Original attribute file chmod u+s file
experiment:
1.su - westos
/bin/cat
Open another shell
ps ax -o user,group,comm | grep cat
westos westos cat
2. Use the root user identity
chmod u+s /bin/watch
su - westos
/bin/cat
Open another shell
ps ax -o user,group,comm | grep cat
root westos cat
Vi acl permission list
Full name: access control lists $: access control lists
function:In the list, special users can be set to have special permissions for special files
1.acl list opening ID
-rw-rw---- 1 root caiwu 0 Apr 18 09:03 westosfile
No,"+"representative acl List not open
-rw-rw----+ 1 root caiwu 0 Apr 18 09:03 westosfile
acl List function on
2.acl list permission reading
$: when the file permission list is opened, do not use ls -l to read the file permission
To use getfacl westosfile
Display content analysis
file: westosfile File name owner: root File owner group: root File owning group user::rw- File owner permissions user:lee:rw- Special specified user permissions group::r-- The file has group permissions group:westos:--- Permissions for specially specified user groups mask::rw- Maximum permission threshold that can be given to special users and special user groups other::r-- Permission of others
3.acl list control
setfacl -m u:lee:rw westosfile setfacl -m g:westos:rw westosfile setfacl -m u::rwx westosfile setfacl -m g::0 westosfile setfacl -x u:lee westosfile Delete from list lee setfacl -b westosfile close
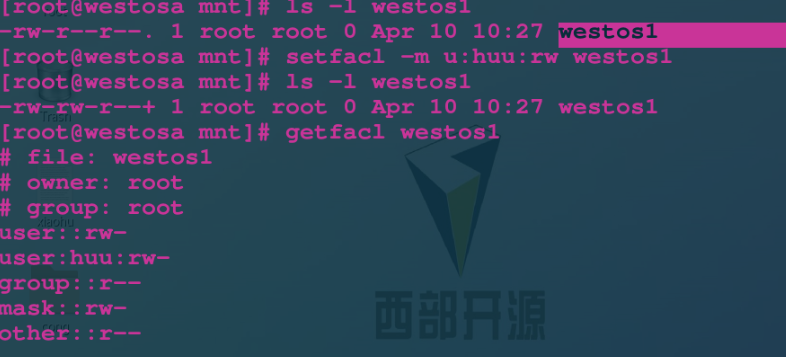
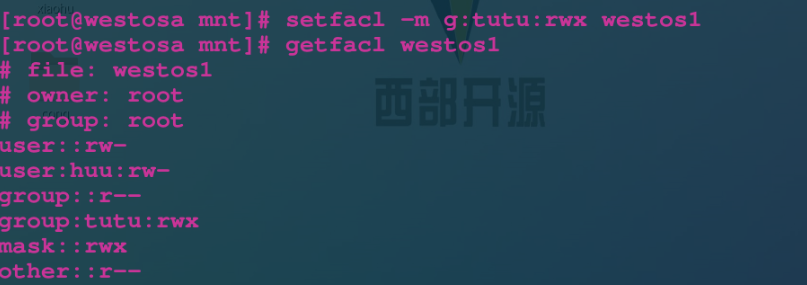
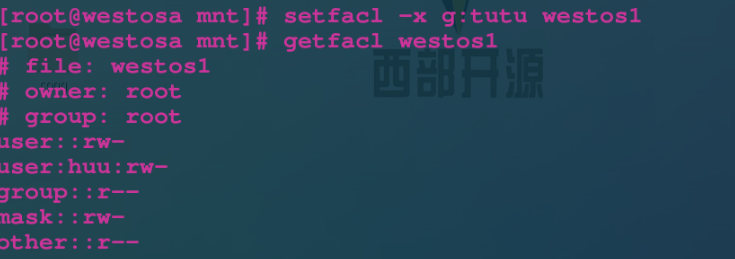
4.acl permission priority
Owners > specially designated users > groups with more permissions > groups with less permissions > others
5.acl mask control
mask is the maximum threshold that can be given to a specified user
After setting the acl list of files, use chmod to narrow down the file ownership group
The mask will change
Recovery:
Setfacl - M: permission file
6. Default permissions of ACL list
setfacl -m u:lee:rwx /mnt/westosdir Only for/mnt/westosdir The catalog itself takes effect setfacl -Rm u:lee:rwx /mnt/westosdir about/mnt/westosdir The directory and contents already existing in the directory take effect **The above commands are valid for existing files, and new files will not be set** setfacl -m d:u:lee:rwx /mnt/westosdir/ For and/mnt/westosdir The new file in the directory takes effect
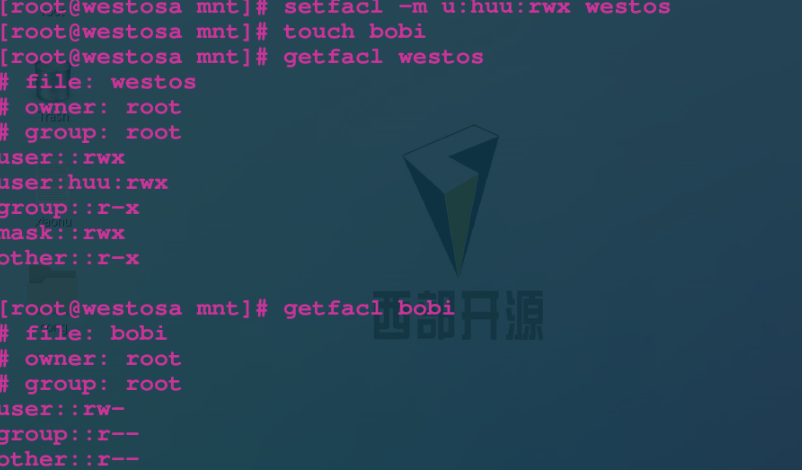
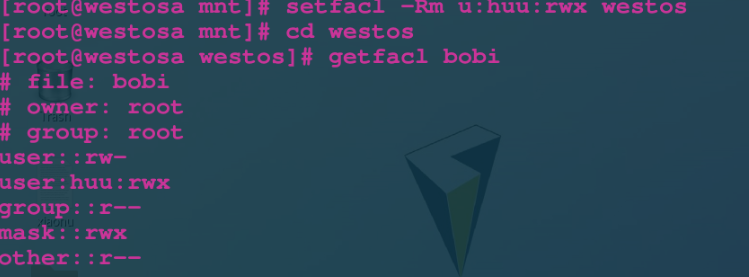
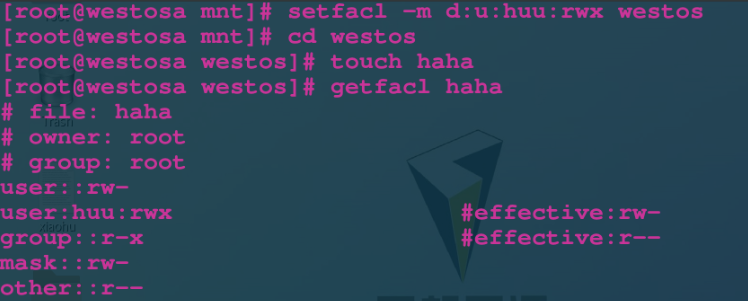
VII attr permissions
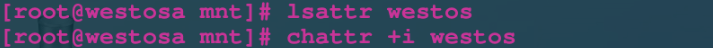
attr permission limits all users
i No changes can be made a Can you add or delete
lsattr dir|file view attr permissions
Chatr + i| + a| - i| - a dir| file set attr permission