Five common data types of centos7 redis
Redis key
| command | effect |
|---|---|
| key * | View all key s in the current library |
| exists key | Determine whether a key exists |
| type key | View the type of key |
| del key | Delete the specified key data (delete directly) |
| unlink key | Select non blocking deletion (asynchronous deletion) according to value. Only keys are deleted from the metadata of the keyspace. The real deletion will be performed in subsequent asynchronous operations |
| expire key expiration value (seconds) | Set the expiration time for the given key, in seconds |
| ttl key | The key will expire in a few seconds, - 1: never expire, - 2: expired |
| select | Switch database |
| dbsize | View the number of key s in the current database |
| flushdb | Clear current library |
| flushall | Clear all libraries |
1. keys * view the number of key s in the current library
1,Enter using client commands Redis redis-cli 2,Write value set k1 v1 set k2 v2 set k3 v3 3,use keys * View how many libraries there are currently key keys *
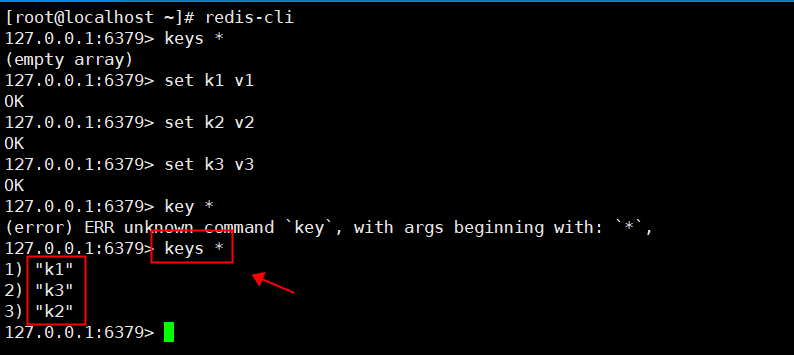
2. exists key determines whether the key exists
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k1" 2) "k3" 3) "k2" 2,Judge an existing key 127.0.0.1:6379> exists k3 (integer) 1 3,Judge a nonexistent key 127.0.0.1:6379> exists k4 (integer) 0
3. type key view the type of key
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k1" 2) "k3" 3) "k2" 2,see k2 What type is it 127.0.0.1:6379> type k2 string
4. del key and unlink key delete key and value values
- del key
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k1" 2) "k3" 3) "k2" 2,Delete the specified key Data: k2 127.0.0.1:6379> del k2 (integer) 1 3,View current library deletion k2 Posterior key quantity 127.0.0.1:6379> keys * 1) "k1" 2) "k3"
- unlink key
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k1" 2) "k3" 2,Delete the specified key Data: k1 127.0.0.1:6379> unlink k1 (integer) 1 3,View current library deletion k1 Posterior key quantity 127.0.0.1:6379> keys * 1) "k3"
5. expire key expiration value (seconds) and ttl key set key expiration time and view expiration time
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k3" 2,set up k3 Expires in ten seconds 127.0.0.1:6379> expire k3 10 (integer) 1 3,View expiration time 127.0.0.1:6379> ttl k3 (integer) 6 127.0.0.1:6379> ttl k3 (integer) 4 127.0.0.1:6379> ttl k3 (integer) 2 127.0.0.1:6379> ttl k3 (integer) -2 (-2 Indicates: expired;-1 (never expires) 4,Newly added key,The default is-1 Never expire 127.0.0.1:6379> set k1 v1 OK 127.0.0.1:6379> ttl k1 (integer) -1
6. select switch database
1,Redis There are 16 libraries (0) in by default-15) 127.0.0.1:6379> select 1 OK 127.0.0.1:6379[1]> select 15 OK 127.0.0.1:6379[15]> select 11 OK 127.0.0.1:6379[11]> select 16 (error) ERR DB index is out of range 127.0.0.1:6379[11]> select 0 OK 127.0.0.1:6379>
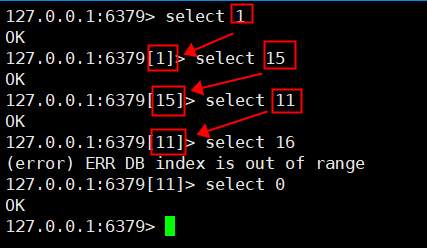
7. dbsize view the number of key s in the current database
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k1" 2,View the current database key quantity 127.0.0.1:6379> dbsize (integer) 1
8. Flush DB empties the current library
1,Existing in the current library key situation 127.0.0.1:6379> keys * 1) "k1" 2,Clear the data of the current library 127.0.0.1:6379> flushdb OK 3,View the in the current library again key situation 127.0.0.1:6379> keys * (empty array)
1. Redis String (String)
1. Introduction
- It is the simplest data type in Redis
- A key corresponds to a value
- It is binary safe and can contain any data, such as JPG pictures, serialized objects, etc
- A Redis string value can be 512M at most
2. Common commands
| command | effect |
|---|---|
| set <key><value> | Sets the value of the specified key |
| setnx <key><value> | When the key does not exist, the value of the key is set |
| mset <key1><value1><key2><value2>... | Write multiple key s and value s at a time |
| msetnx<key1><value1><key2><value2> | Write multiple keys and value s at a time (only when all the keys set do not exist in the current library can they be written successfully.) |
| get <key> | Gets the value of the specified key |
| mget<key1><key2>... | Get the values of multiple key s at one time |
| append<key><value> | Appends the value to the end of the original value of the specified key |
| strlen <key> | Get the length of value in key |
| incr <key> | Add 1 to the value of key (incr can only operate on numeric values) |
| decr <key> | Subtract 1 from the value of key (decr can only operate on numeric values) |
| Incrby < key > < step > | Add the specified step size to the value value of the key (incrby can only operate on numeric values) |
| Decrby < key > < step size > | Subtract the specified step size from the value value of the key (decrby can only operate on numeric values) |
| Getrange < key > < start position > < end position > | Gets the range of values |
| Setrange < key > < start position > < value > | Insert data at the specified location (the original data will be overwritten) |
| Setex < key > < expiration time > < value > | Set the expiration time (in seconds) while setting the key value |
| getset<key><value> | Set the new value and get the old value at the same time |
1. Set < key > < value > and get < key > commands
1,In the current library key Situation 127.0.0.1:6379> keys * (empty array) 2,add to key 127.0.0.1:6379> set k1 v100 OK 127.0.0.1:6379> set k2 v200 OK 3,View current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k2" 4,Get specified key Value of 127.0.0.1:6379> get k1 "v100"
- Set the value of the existing key
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k2" 2,current k1 Value of 127.0.0.1:6379> get k1 "v100" 3,set up k1 Value of 127.0.0.1:6379> set k1 v1100 OK 4,After viewing the settings, k1 Value of (original value) v100 Set later v1100 (covered) 127.0.0.1:6379> get k1 "v1100"
2, append<key><value>
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k2" 2,current k1 Value of 127.0.0.1:6379> get k1 "v1100" 3,take hell Additional k1 Original value v1100 At the end of, print the new after success value Length of 10 127.0.0.1:6379> append k1 hello (integer) 10 4,View the appended results 127.0.0.1:6379> get k1 "v1100hello"
3. Strlen < key > get the length of value in key
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k2" 2,current k1 Value of 127.0.0.1:6379> get k1 "v1100hello" 3,obtain k1 in value Length of value 127.0.0.1:6379> strlen k1 (integer) 10
4. Setnx < key > < value > set the value of the key only when the key does not exist
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k2" 2,current k1 Value of 127.0.0.1:6379> get k1 "v1100hello" 3,Setting an already exists key Value of (setting failed) 127.0.0.1:6379> setnx k1 123 (integer) 0 4,Setting a does not exist key Value of (set successfully) 127.0.0.1:6379> setnx k3 v300 (integer) 1 127.0.0.1:6379> keys * 1) "k1" 2) "k3" 3) "k2" 127.0.0.1:6379> get k3 "v300"
5. Incr < key > and decr < key > commands
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k3" 3) "k2" 2,Create a new k4,Set a value of numeric type 127.0.0.1:6379> set k4 100 OK 127.0.0.1:6379> get k4 "100" 3,adopt incr k4 set up k4 Add one to the value of( incr (can only operate on numeric values) 127.0.0.1:6379> incr k4 (integer) 101 127.0.0.1:6379> get k4 "101" 4,adopt decr k4 set up k4 Minus one( decr (can only operate on numeric values) 127.0.0.1:6379> decr k4 (integer) 100 127.0.0.1:6379> get k4 "100"
6. Incrby < key > < step > and decrby < key > < step >
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k1" 2) "k4" 3) "k3" 4) "k2" 2,current k4 value 127.0.0.1:6379> get k4 "100" 3,adopt incrby k4 100 to k4 Add 100 to the value of 127.0.0.1:6379> incrby k4 100 (integer) 200 127.0.0.1:6379> get k4 "200" 4,adopt decrby k4 100 to k4 The value of minus 150 127.0.0.1:6379> decrby k4 150 (integer) 50 127.0.0.1:6379> get k4 "50"
Atomicity
- The operation in Redis is atomic. Once started, it will not be interrupted by other thread scheduling mechanisms (atomic)
- In a single thread, the operations that can be completed in a single instruction can be regarded as "atomic operations", and interrupts can only occur between instructions
- In multithreading, operations that cannot be interrupted by other processes (threads) can also be considered "atomic operations"
- The atomicity of Redis single command benefits from the single thread of Redis
7. Mset < key1 > < value1 > < key2 > < Value2 >..., msetnx < key1 > < value1 > < key2 > < Value2 >, and mget < key1 > < key2 >
1,In the current library key Situation 127.0.0.1:6379> keys * (empty array) 2,use mset Write more than one at a time key and value 127.0.0.1:6379> mset k1 v1 k2 v2 k3 v3 OK 127.0.0.1:6379> keys * 1) "k3" 2) "k2" 3) "k1" 3,use msetnx Write more than one at a time key(among k3 Already exists) and value(Write failed) -- Only when all settings key If it does not exist in the current library, it can be written successfully; -- Just set up all key , which already exists in the current library, and the rest are not duplicate key Also write failed; 127.0.0.1:6379> msetnx k11 v11 k22 v22 k3 v3 (integer) 0 4,Set all key , does not exist in the current library 127.0.0.1:6379> msetnx k11 v11 k22 v22 k33 v33 (integer) 1 127.0.0.1:6379> keys * 1) "k3" 2) "k2" 3) "k1" 4) "k11" 5) "k22" 6) "k33" 5,use mget Multiple at a time key Value of 127.0.0.1:6379> mget k1 k2 k3 1) "v1" 2) "v2" 3) "v3"
8. Getrange < key > < start position > < end position > range of values obtained
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "k3" 2) "k2" 3) "k1" 4) "k11" 5) "k22" 6) "k33" 2,Write the value of a test 127.0.0.1:6379> set name helloworld OK 3,use getrange obtain key yes name Subscript from 0-4 Five subscript value value 127.0.0.1:6379> getrange name 0 4 "hello"
9. Setrange < key > < start position > < value > insert data at the specified position (the original data will be overwritten)
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "name" 127.0.0.1:6379> get name "helloworld" 2,stay hello Insert 123 after, using setrange((the inserted data overwrites the original data) 127.0.0.1:6379> setrange name 5 123 (integer) 10 127.0.0.1:6379> get name "hello123ld"
10. Setex < key > < expiration time > < value > set the expiration time (unit: seconds) while setting the key value
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "name" 2,Set a color of key,Expiration time: 10 seconds, value The values are: skyblue 127.0.0.1:6379> setex color 10 skyblue OK 127.0.0.1:6379> ttl color (integer) 8 127.0.0.1:6379> ttl color (integer) 6 127.0.0.1:6379> ttl color (integer) 5 127.0.0.1:6379> ttl color (integer) 5 127.0.0.1:6379> ttl color (integer) 3 127.0.0.1:6379> ttl color (integer) 3 127.0.0.1:6379> ttl color (integer) 1 127.0.0.1:6379> ttl color (integer) 0 127.0.0.1:6379> ttl color (integer) -2 3,In the current library key Situation 127.0.0.1:6379> keys * 1) "name"
11. GetSet < key > < value > set the new value and get the old value at the same time
1,In the current library key Situation 127.0.0.1:6379> keys * 1) "name" 127.0.0.1:6379> get name "zhangsan" 2,set up name The value of is: lisi,Print name Old value of: zhangsan 127.0.0.1:6379> getset name lisi "zhangsan" 3,obtain name Value of 127.0.0.1:6379> get name "lisi"
3. Data structure
- Simple dynamic string (abbreviated as SDS)
- Is a string that can be modified
- The internal structure is similar to ArrayList in Java
- The method of pre allocating redundant space is adopted to reduce the frequent allocation of memory
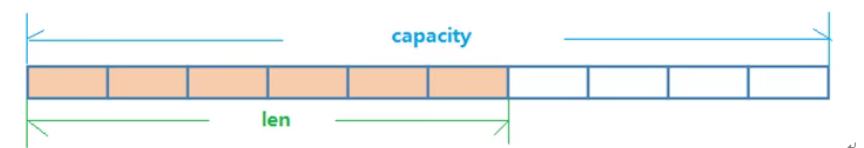
- Internal space capacity actually allocated for the current string
- It is generally higher than the actual string length len
- When the string length is less than 1m, the expansion is to double the existing space
- When the string length is > 1M, only 1M more space will be expanded at a time
- The maximum string length is 512M
2. Redis List
1. Introduction
- Equivalent to the LinkedList structure in the Java language, it is a linked list rather than an array
- The underlying storage structure of Redis list is a structure called quicklist
- When there are few elements stored in the list, Redis will use a continuous memory to store these elements. This continuous structure is called ziplost compressed list
- Compressed list is developed by Redis to save memory. It is a sequential data structure composed of a series of specially coded continuous memory blocks. A compressed list can contain any number of nodes, and each node can save a character array or integer value.
- When the amount of data is large, Redis list will use quicklist to store elements
- It adopts the combination of linked list and compressed list, that is, QuickList + ziplost
- Multiple ziplosts are connected in series with bidirectional pointers, which can not only meet the characteristics of fast insertion and deletion, but also save some storage space
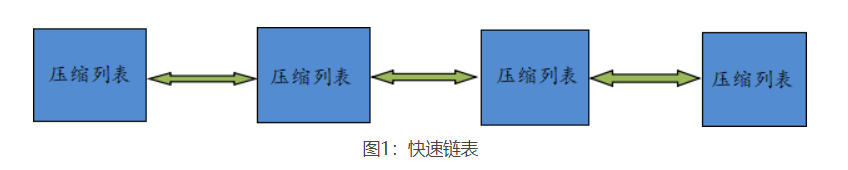
2. Basic command
| command | effect |
|---|---|
| lppush <key><value1><value2>... | Write value from left |
| rpush<key><value1><value2>... | Write value from right |
| Lrange < key > < start position > < end position > | View the elements in the key. key 0 -1 means to view all elements in the current key |
| lpop | Left value |
| rpop | Right value |
| rpoplpush<key><key> | Take a value from the right of the first key and insert it to the left of the second key |
| lindex<key><index> | Get elements by index subscript |
| llen<key> | Get list length |
| linsert <key> before<value><newvalue> | Insert a new value newvalue before the value in the key |
| linsert <key> after<value><newvalue> | Insert a new value newvalue after the value in the key |
| lrem<key><n><value> | Delete n value s from the left of the key (from left to right) |
| lset<key><index><value> | Replace the value with index in the key with value |
1. Lppush < key > < value1 > < Value2 >..., rpush < key > < value1 > < Value2 >... And lrange < key > < start position > < end position >
1,In the current database key situation 127.0.0.1:6379> keys * (empty array) 2,use lpush Write value from left 127.0.0.1:6379> lpush k1 v1 v2 v3 (integer) 3 3,Value 0 -1 Values representing all ranges 127.0.0.1:6379> lrange k1 0 -1 1) "v3" 2) "v2" 3) "v1"
- Left write value
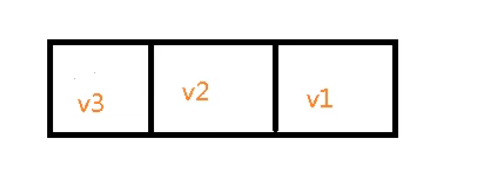
1,use rpush Write value from right 127.0.0.1:6379> rpush k2 v1 v2 v3 (integer) 3 2,Value 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v2" 3) "v3"
- Right write value
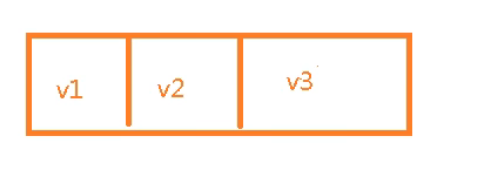
2. Lpop < key > left value and rpop < key > right value
1,In the current database key situation 127.0.0.1:6379> keys * 1) "k2" 2) "k1" 127.0.0.1:6379> lrange k1 0 -1 1) "v3" 2) "v2" 3) "v1" 2,use lpop Value from left 127.0.0.1:6379> lpop k1 "v3" 127.0.0.1:6379> lpop k1 "v2" 127.0.0.1:6379> keys * 1) "k2" 2) "k1" 3,When k1 When the last value in is taken out, k2 It doesn't exist (the value is in the key, the value is not in the key) 127.0.0.1:6379> lpop k1 "v1" 127.0.0.1:6379> keys * 1) "k2"
1,In the current database key situation 127.0.0.1:6379> keys * 1) "k2" 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v2" 3) "v3" 2,Right value 127.0.0.1:6379> rpop k2 "v3" 3,Left value 127.0.0.1:6379> lpop k2 "v1" 4,View results 127.0.0.1:6379> lrange k2 0 -1 1) "v2"
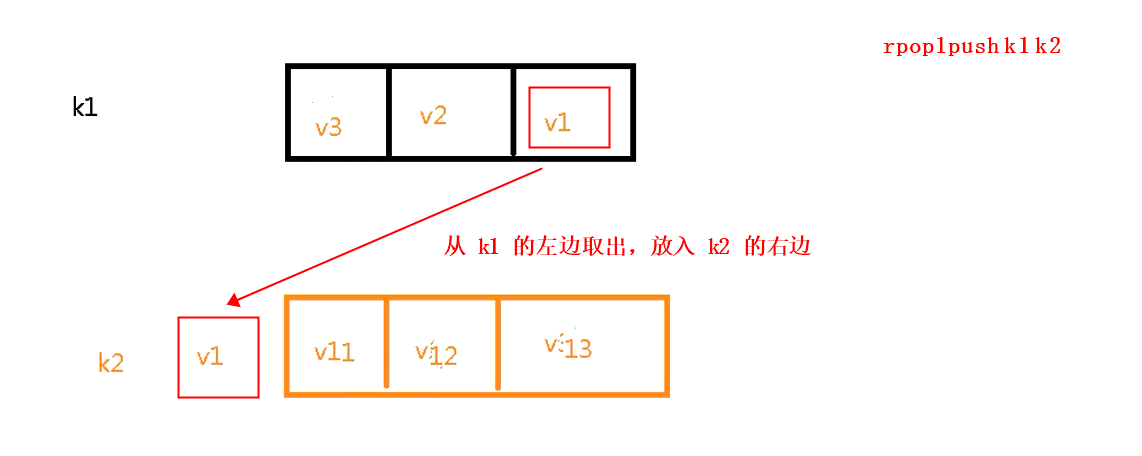
3. Rpoplpush < < key with right value > < put to the left of key >
1,Left write value k1 127.0.0.1:6379> lpush k1 v1 v2 v3 (integer) 3 127.0.0.1:6379> lrange k1 0 -1 1) "v3" 2) "v2" 3) "v1" 2,Right write value k2 127.0.0.1:6379> rpush k2 v11 v22 v33 (integer) 3 127.0.0.1:6379> lrange k2 0 -1 1) "v11" 2) "v22" 3) "v33" 3,use rpoplpush from k1 Take a value to the right of and put it in k2 Left of 127.0.0.1:6379> rpoplpush k1 k2 "v1" 4,View results 127.0.0.1:6379> lrange k1 0 -1 1) "v3" 2) "v2" 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v11" 3) "v22" 4) "v33"
- rpoplpush right value
4. Lindex < key > < index > get elements by index subscript
1,current k2 Values in 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v11" 3) "v22" 4) "v33" 2,Get by index subscript k2 Element of 127.0.0.1:6379> lindex k2 0 "v1" 127.0.0.1:6379> lindex k2 2 "v22" 127.0.0.1:6379> lindex k2 4 (Out of index) (nil)
5. Len < key > get the length of the list
1,current k2 Values in 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v11" 3) "v22" 4) "v33" 2,obtain k2 Length of list 127.0.0.1:6379> llen k2 (integer) 4
6. Linsert < key > before < value > < newvalue > insert a new value before
- before
1,current k2 Elements in 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v11" 3) "v22" 4) "v33" 2,stay k2 Medium v11 Add one before hello Value of 127.0.0.1:6379> linsert k2 before "v11" "hello" (integer) 5 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "hello" 3) "v11" 4) "v22" 5) "v33" 3,stay k2 Medium v22 Add one before hello Value of 127.0.0.1:6379> linsert k2 before "v22" "hello" (integer) 6 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "hello" 3) "v11" 4) "hello" 5) "v22" 6) "v33" 4,stay k2 Medium v33 Add one before hello Value of 127.0.0.1:6379> linsert k2 before "v33" "hello" (integer) 7 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "hello" 3) "v11" 4) "hello" 5) "v22" 6) "hello" 7) "v33"
- after
1,current k1 Elements in 127.0.0.1:6379> lrange k1 0 -1 1) "v3" 2) "v2" 2,stay k2 Medium v3 Add one later hello Value of 127.0.0.1:6379> linsert k1 after "v3" "hello" (integer) 3 127.0.0.1:6379> lrange k1 0 -1 1) "v3" 2) "hello" 3) "v2"
7. Lrem < key > < n > < value > delete n values from the left (from left to right)
1,current k2 Elements in 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "hello" 3) "v11" 4) "hello" 5) "v22" 6) "hello" 7) "v33" 2,stay k2 Delete 2 from left to right hello Value of 127.0.0.1:6379> lrem k2 2 "hello" (integer) 2 3,View results 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v11" 3) "v22" 4) "hello" 5) "v33"
8. Lset < key > < index > < value > replace the value with index in the key with value
1,current k2 Elements in 127.0.0.1:6379> lrange k2 0 -1 1) "v1" 2) "v11" 3) "v22" 4) "hello" 5) "v33" 2,stay k2 The middle subscript is 0“ v1" Replace with“ helloworld" 127.0.0.1:6379> lset k2 0 helloworld OK 127.0.0.1:6379> lrange k2 0 -1 1) "helloworld" 2) "v11" 3) "v22" 4) "hello" 5) "v33"
3. Data structure
- The underlying storage structure of Redis list is a structure called quicklist
- When there are few elements stored in the list, Redis will use a continuous memory to store these elements. This continuous structure is called ziplost compressed list
- Compressed list is developed by Redis to save memory. It is a sequential data structure composed of a series of specially coded continuous memory blocks. A compressed list can contain any number of nodes, and each node can save a character array or integer value.
- When the amount of data is large, Redis list will use quicklist to store elements
- It adopts the combination of linked list and compressed list, that is, QuickList + ziplost
- Multiple ziplosts are connected in series with bidirectional pointers, which can not only meet the characteristics of fast insertion and deletion, but also save some storage space
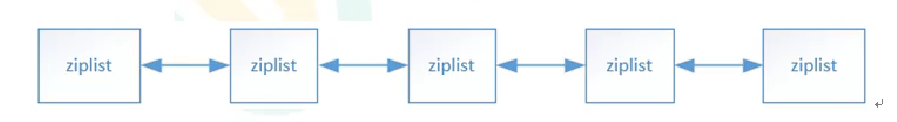
3. Redis Set
1. Introduction
- Functions similar to list
- Automatic de duplication (no duplicate data)
- It is an unordered collection of String type, and the bottom layer is a hash table with null value
2. Common commands
| command | effect |
|---|---|
| sadd<key><value1><value2>... | Add one or more values |
| smembers<key> | Value |
| sismember<key><value> | Judge whether the value exists in the key. 1 is returned, but 0 is not returned |
| scardy<key> | Returns the number of elements in the collection |
| spop<key> | Spit out a value randomly from the set |
| srandmember<key><n> | Randomly take n values from the set, but they will not be deleted from the set |
| smove<source><destination>value | Moves a value in a set from one set to another |
| sinter<key1><key2> | Returns the intersection element of two collections |
| sunion<key1><key2> | Returns the union element of two collections |
| sdiff<key1><key2> | Returns the difference elements of two sets (elements that exist in key1 and not in key2) |
1. Sadd < key > < value1 > < Value2 >... Add one or more values and smembers < key > values
1,Add multiple values at a time, where v2 Added twice 127.0.0.1:6379> sadd k1 v1 v2 v2 v3 (integer) 3 2,Value (use) sadd When adding a new value, only one value is selected for the same value) 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 3) "v3"
2. Sismember < key > < value > judge whether the value exists in the key. 1 is returned, but 0 is not returned
1,current k1 Elements in 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 3) "v3" 2,judge k1 Exists in v2(Presence (return 1) 127.0.0.1:6379> sismember k1 v2 (integer) 1 3,judge k1 Exists in v4(Exist (return 0) 127.0.0.1:6379> sismember k1 v4 (integer) 0
3. Scardy < key > returns the number of elements in the collection
1,current k1 Elements in 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 3) "v3" 2,return k1 Number of elements in 127.0.0.1:6379> scard k1 (integer) 3
4. Spop < key > spits out a value randomly from the set
1,current k1 Elements in 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 3) "v3" 2,Spit out a value randomly from the set 127.0.0.1:6379> spop k1 "v1" 127.0.0.1:6379> spop k1 "v3" 3,View again k1 Elements in 127.0.0.1:6379> smembers k1 1) "v2"
5. Srandmember < key > < n > randomly take n values from the set, but they will not be deleted from the set
1,current k1 Element of 127.0.0.1:6379> smembers k1 1) "v4" 2) "v2" 3) "v1" 4) "v3" 5) "v5" 2,Random from k1 Take out 2 elements from 127.0.0.1:6379> srandmember k1 2 1) "v3" 2) "v1" 127.0.0.1:6379> srandmember k1 2 1) "v4" 2) "v1" 3,View again k1 Elements in 127.0.0.1:6379> smembers k1 1) "v4" 2) "v2" 3) "v1" 4) "v3" 5) "v5"
6. Smove < source > < destination > value moves a value in a set from one set to another
1,current k1 k2 Elements in 127.0.0.1:6379> smembers k1 1) "v4" 2) "v2" 3) "v1" 4) "v3" 127.0.0.1:6379> smembers k2 1) "v5" 2) "v4" 3) "v6" 2,take k1 Medium "v3"Move to k2 in 127.0.0.1:6379> smove k1 k2 v3 (integer) 1 127.0.0.1:6379> smembers k2 1) "v5" 2) "v4" 3) "v6" 4) "v3" 127.0.0.1:6379> smembers k1 1) "v4" 2) "v2" 3) "v1" 3,take k1 Medium "v4"Move to k2 Medium( k2 Already exists in“ v4") 127.0.0.1:6379> smove k1 k2 v4 (integer) 1 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 127.0.0.1:6379> smembers k2 1) "v5" 2) "v4" 3) "v6" 4) "v3"
7. Sinter < key1 > < key2 > returns the intersection elements of two sets
1,current k1 k2 Elements in 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 3) "v3" 127.0.0.1:6379> smembers k2 1) "v5" 2) "v4" 3) "v3" 2,Returns the intersection element of two collections 127.0.0.1:6379> sinter k1 k2 1) "v3"
8. Sunion < key1 > < key2 > returns the union elements of two sets
1,current k1 k2 Elements in 127.0.0.1:6379> smembers k1 1) "v2" 2) "v1" 3) "v3" 127.0.0.1:6379> smembers k2 1) "v5" 2) "v4" 3) "v3" 2,Returns the union element of two collections 127.0.0.1:6379> sunion k1 k2 1) "v2" 2) "v1" 3) "v3" 4) "v5" 5) "v4"
9. Sdiff < key1 > < key2 > returns the difference elements of two sets (elements that exist in key1 and do not exist in key2)
1,current k1 k2 Elements in 127.0.0.1:6379> smembers k1 1) "v4" 2) "v2" 3) "v1" 4) "v3" 127.0.0.1:6379> smembers k2 1) "v5" 2) "v4" 3) "v6" 2,with k1 Prevail, return k2 Element that does not exist in 127.0.0.1:6379> sdiff k1 k2 1) "v2" 2) "v1"
3. Data structure
- The Set data structure is a dict dictionary, which is implemented through a hash table
- hash structure, all values point to the same internal value
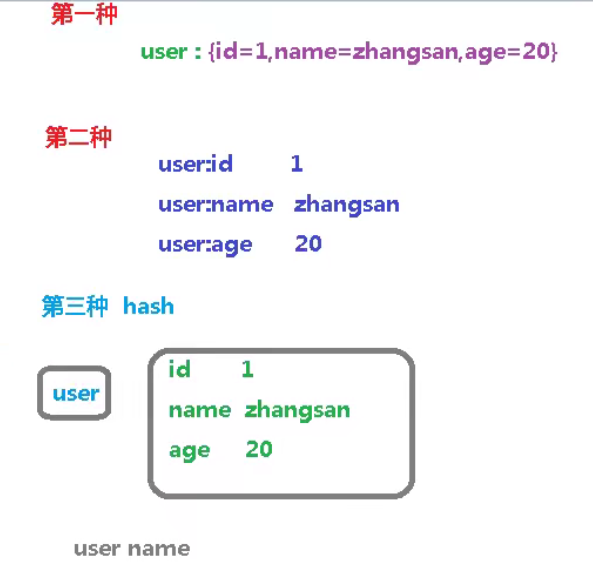
4. Redis Hash (Hash)
1. Introduction
- Is a collection of key value pairs
- Is a mapping table of field and value of String type, which is suitable for storing objects
- Similar to map < string, Object > in Java
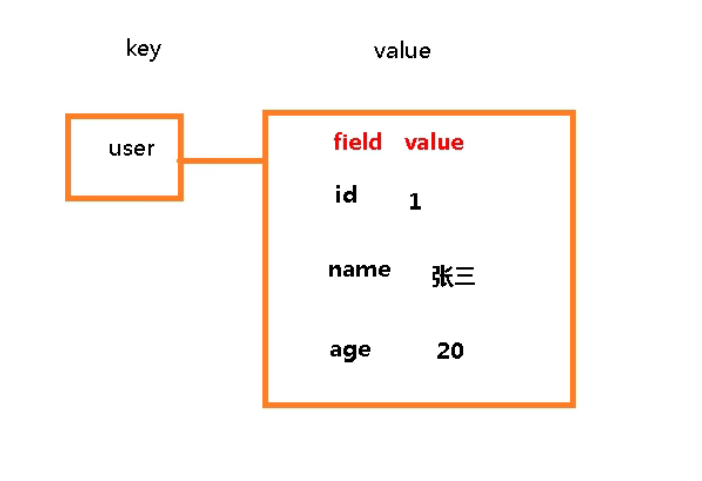
- Hash takes the third approach
2. Basic command
| command | effect |
|---|---|
| hset <key><field><value> | Assign value to the field key in the key set |
| hget<key><field> | Value |
| hmset<key1><field1><value1><field1><value1>... | Add multiple values at once |
| hkeys<key> | List all field s in the key |
| hvals<key> | List all value s in key |
| hexists<key><field> | Check whether the field exists in the hash table key |
| hincrby<key><field><increment> | Increment the value corresponding to the field in the key |
| hsetnx<key><field><value> | When the field in the key does not exist, set the value corresponding to the field to value |
1. Hset < key > < field > < value > assigns value and hget < key > < field > values to the field keys in the key set
1,Write value 127.0.0.1:6379> hset user:001 name zhangsan (integer) 1 127.0.0.1:6379> hset user:001 age 10 (integer) 1 2,adopt key and field Key value 127.0.0.1:6379> hget user:001 name "zhangsan" 127.0.0.1:6379> hget user:001 age "10"
2. Hmset < key1 > < field1 > < value1 > < field1 > < value1 >... Add multiple values at a time
1,Add multiple values at once 127.0.0.1:6379> hmset user:002 name lisi age 30 shenggao 173 OK 2,Value 127.0.0.1:6379> hget user:002 name "lisi" 127.0.0.1:6379> hget user:002 age "30" 127.0.0.1:6379> hget user:002 shenggao "173"
3. Hkeys < key > lists all field s in the key and hvals < key > lists all value s in the key
1,list key yes user:002 All in field 127.0.0.1:6379> hkeys user:002 1) "name" 2) "age" 3) "shenggao" 2,list key yes user:002 All in value 127.0.0.1:6379> hvals user:002 1) "lisi" 2) "30" 3) "173"
4. Hexists < key > < field > check whether the field exists in the hash table key
1,current key= user:002 All in field 127.0.0.1:6379> hkeys user:002 1) "name" 2) "age" 3) "shenggao" 2,see key= user:002 Medium field="name"Exists or not (returns 1) 127.0.0.1:6379> hexists user:002 name (integer) 1 3,see key= user:002 Medium field="tel"Whether it exists (if it does not exist, return 0) 127.0.0.1:6379> hexists user:002 tel (integer) 0
5. Hincrby < key > < field > < increment > adds an increment to the value corresponding to the field in the key
1,key=user:002 Medium field and value situation 127.0.0.1:6379> hkeys user:002 1) "name" 2) "age" 3) "shenggao" 127.0.0.1:6379> hvals user:002 1) "lisi" 2) "30" 3) "173" 2,to key=user:002 in field="age"Corresponding 30 plus 20 127.0.0.1:6379> hincrby user:002 age 20 (integer) 50 127.0.0.1:6379> hvals user:002 1) "lisi" 2) "50" 3) "173" 3,to key=user:002 in field="age"Corresponding 50 minus 20 127.0.0.1:6379> hincrby user:002 age -20 (integer) 30 127.0.0.1:6379> hvals user:002 1) "lisi" 2) "30" 3) "173"
6. Hsetnx < key > < field > < value > when the field in the key does not exist, set the value corresponding to the field to value
1,key=user:002 Medium field and value situation 127.0.0.1:6379> hkeys user:002 1) "name" 2) "age" 3) "shenggao" 127.0.0.1:6379> hvals user:002 1) "lisi" 2) "30" 3) "173" 2,set up key=user:002 in field="name"The corresponding value is“ zhangsan"(field="name"(already exists, setting failed) 127.0.0.1:6379> hsetnx user:002 name zhangsan (integer) 0 3,set up key=user:002 in field="tel"The corresponding value is "123456789"( field="tel"(does not exist, set successfully) 127.0.0.1:6379> hsetnx user:002 tel 123456789 (integer) 1 4,View results 127.0.0.1:6379> hkeys user:002 1) "name" 2) "age" 3) "shenggao" 4) "tel" 127.0.0.1:6379> hvals user:002 1) "lisi" 2) "30" 3) "173" 4) "123456789"
3. Data structure
- The corresponding data structures are: zip list and hash table
- When the field value length is short and the number is small, the compressed list is used
- When the field value length is long and the number is large, the hash table is used
5. Redis ordered set (Zset)
1. Introduction
- An ordered collection is a collection of strings without duplicate elements
- Each member in the ordered set is associated with a score, which is used to sort the members in the set from the lowest score to the highest score
- Members in the collection are unique, but scores can be repeated
2. Basic command
| command | effect |
|---|---|
| zadd<key><score1><value1><score2><value2>... | Write multiple values at once |
| zrange <key> | View values |
| zrangebyscore key minmax[withscores][limit offset count ] | Return all members in the key whose score is between min and max (including equal to), arranged from small to large |
| zrevrangebyscore key maxmin [withscores][limit offset count] | Return all members in the key whose score is between max and min (including equal to), arranged from large to small |
| zincrby<key><increment><value> | Increment the score of the element |
| zrem<key><value> | Delete the element with the specified value under the collection |
| zcount<key><min><max> | Count the number of elements in the set and score interval |
| zrank<key><value> | Returns the ranking of the value in the collection, starting from 0 |
1. Zadd < key > < Score1 > < value1 > < score2 > < Value2 >... Write multiple values at a time and zrange < key > View values
1,Write multiple values at once 127.0.0.1:6379> zadd k1 100 java 200 c++ 300 phthon 400 c (integer) 4 2,View values only value 127.0.0.1:6379> zrange k1 0 -1 1) "java" 2) "c++" 3) "phthon" 4) "c" 3,View values and ratings withscores(Default (sort from small to large) 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "java" 2) "100" 3) "c++" 4) "200" 5) "phthon" 6) "300" 7) "c" 8) "400"
2. Zrangebyscore key minmax [WithCores] [limit offset count] returns all members in the key whose score is between min and max (including equal to), arranged from small to large
1,k1 Situation in 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "java" 2) "100" 3) "c++" 4) "200" 5) "phthon" 6) "300" 7) "c" 8) "400" 2,View ratings score At 200-300 Members between 127.0.0.1:6379> zrangebyscore k1 200 300 1) "c++" 2) "phthon" 3,Query result display score 127.0.0.1:6379> zrangebyscore k1 200 300 withscores 1) "c++" 2) "200" 3) "phthon" 4) "300"
3. Zrevrangebyscore key maxmin [WithCores] [limit offset count] returns all members in the key whose score is between max and min (including equal to), arranged from large to small
1,k1 Situation in 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "java" 2) "100" 3) "c++" 4) "200" 5) "phthon" 6) "300" 7) "c" 8) "400" 2,View ratings score At 400-200 Members between 127.0.0.1:6379> zrevrangebyscore k1 400 200 1) "c" 2) "phthon" 3) "c++" 3,Query result display score 127.0.0.1:6379> zrevrangebyscore k1 400 200 withscores 1) "c" 2) "400" 3) "phthon" 4) "300" 5) "c++" 6) "200"
4. Zincrby < key > < increment > < value > adds an increment to the score of the element
1,k1 Situation in 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "java" 2) "100" 3) "c++" 4) "200" 5) "phthon" 6) "300" 7) "c" 8) "400" 2,to k1 Medium Java of score Plus 50 increments 127.0.0.1:6379> zincrby k1 50 java "150" 3,View results 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "java" 2) "150" 3) "c++" 4) "200" 5) "phthon" 6) "300" 7) "c" 8) "400"
5. Zrem < key > < value > delete the element with the specified value under the set
1,k1 Situation in 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "java" 2) "100" 3) "c++" 4) "200" 5) "phthon" 6) "300" 7) "c" 8) "400" 2,delete 127.0.0.1:6379> zrem k1 java (integer) 1 3,View results 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "c++" 2) "200" 3) "phthon" 4) "300" 5) "c" 6) "400"
6. Zcount < key > < min > < Max > counts the number of elements in the score interval of the set
1,current k1 Situation in 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "c++" 2) "200" 3) "phthon" 4) "300" 5) "c" 6) "400" 2,see k1 The average score is 200-300 Number of elements between 127.0.0.1:6379> zcount k1 200 300 (integer) 2
7. Zrank < key > < value > returns the ranking of the value in the collection, starting from 0
1,current k1 Situation in 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "c++" 2) "200" 3) "phthon" 4) "300" 5) "c" 6) "400" 2,see value="phthon"stay k1 Ranking in (No. 1) 127.0.0.1:6379> zrank k1 phthon (integer) 1
3. Data structure
- Similar to map < string, double > in Java
- On the one hand, each element can be given a weight score
- On the other hand, it is similar to TreeSet. The internal elements are sorted according to the weight score to get the ranking of each element. You can also get the list of elements through the range of score
- The underlying layer of Zset uses two data structures:
- hash is used to associate the element value with the weight score to ensure the uniqueness of the element value. The corresponding score value can be found through the element value.
- Jump table. The purpose is to sort the element value and obtain the element list according to the scope of score.
[Shang Silicon Valley] Redis 6 Introduction to mastery super detailed tutorial