Harbor Foundation
Harbor is an enterprise Registry server for storing and distributing Docker images that extends the open source Docker Distribution by adding some of the features necessary for the enterprise, such as security, identity, and management. As an enterprise private Registry server, Harbor provides better performance and security. Enhance the efficiency with which users use Registry to build and run environment transport mirrors. Harbor supports replication of mirrored resources installed on multiple Registry nodes, keeping all mirrors in a private Registry to ensure that data and intellectual property are controlled within the company's internal network. In addition, Harbor provides advanced security features such as user management, access control, and activity auditing.
Official address: https://goharbor.io/
Characteristic
- security
- Security and Vulnerability Analysis
- Content Signature and Verification
- Administration
- multi-tenancy
- Extensible API and Web UI
- Copy across multiple registries, including Harbor
- Identity integration and role-based access control
Harbor Deployment
- Install DockerCompose
github address: https://github.com/docker/compose/
wget https://github.com/docker/compose/releases/download/v2.2.2/docker-compose-linux-x86_64 mv docker-compose-linux-x86_64 /usr/bin/docker-compose chmod +x /usr/bin/docker-compose docker-compose version
- Install Harbor
github address: https://github.com/goharbor/harbor/
2.1 Download and Unzip
wget https://github.com/goharbor/harbor/releases/download/v2.4.1/harbor-offline-installer-v2.4.1.tgz tar xf harbor-offline-installer-v2.4.1.tgz -C /usr/local/ cd /usr/local/harbor/
2.2 Preparing configuration files
cp harbor.yml.tmpl harbor.yml Modify as follows: vim harbor.yml # Host address or domain name hostname: 10.10.1.107 # Enable http http: port: 80 # Disable https protocol #https: #https port for harbor, default is 443 #port: 443 # The path of cert and key files for nginx #certificate: /your/certificate/path #private_key: /your/private/key/path # Modify admin password harbor_admin_password: 123456 # harbor storage directory data_volume: /data/harbor
2.3 Install harbor
Command Options
- --with-notary #Verify ssl
- --with-trivy i #Open Vulnerability Scanner
- --with-chartmuseum #Supports mirror scanning
# install ./install.sh --with-trivy --with-chartmuseum # Complete as follows [+] Running 13/13 ⠿ Network harbor_harbor Created 0.1s ⠿ Network harbor_harbor-chartmuseum Created 0.1s ⠿ Container harbor-log Started 1.2s ⠿ Container redis Started 5.1s ⠿ Container registryctl Started 4.9s ⠿ Container harbor-db Started 4.5s ⠿ Container harbor-portal Started 4.3s ⠿ Container registry Started 4.0s ⠿ Container chartmuseum Started 4.2s ⠿ Container harbor-core Started 10.8s ⠿ Container trivy-adapter Started 10.8s ⠿ Container nginx Started 13.3s ⠿ Container harbor-jobservice Started 13.2s ✔ ----Harbor has been installed and started successfully.----
2.4 Landing Test
http://ip_or_hostname
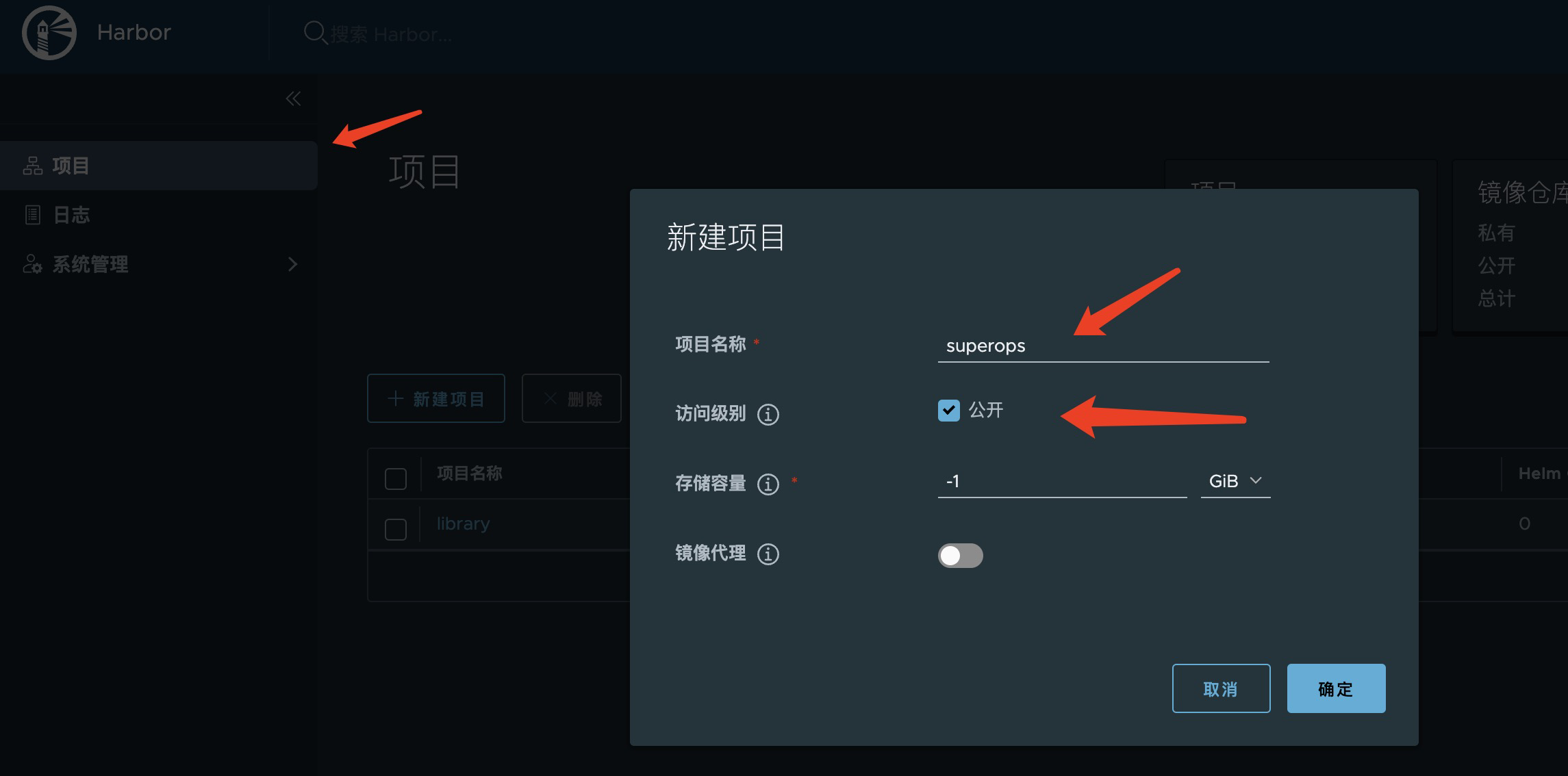
harbor new project
Option Description
- Public: A password is also required if public downloads are not checked
- Storage capacity: Maximum mirror capacity for this project, -1 is unlimited
- Mirror Agent: Mirror Agent function
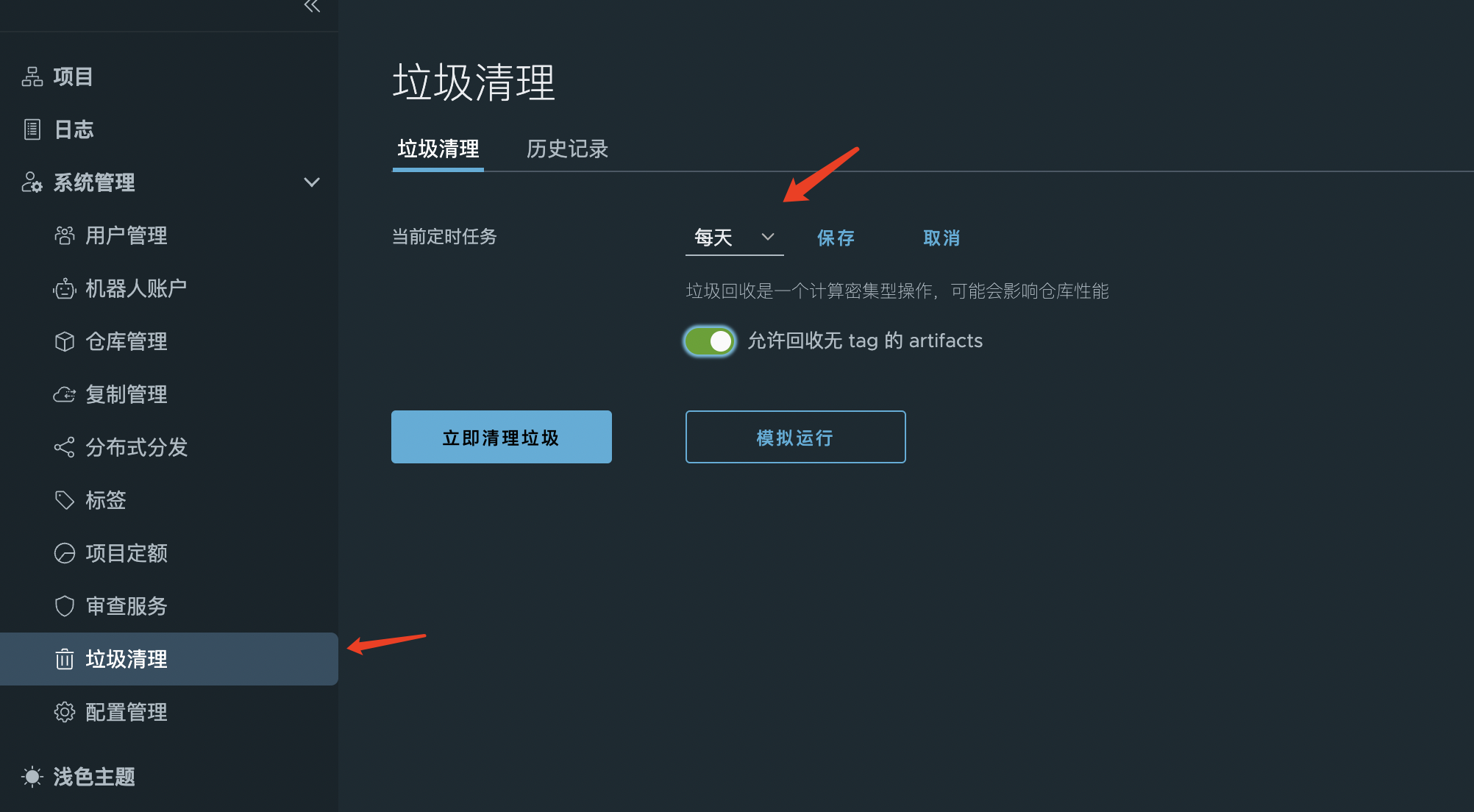
harbor opens garbage disposal
When turned on, harbor automatically cleans up tag less images.
Harbor High Availability
Harbor High Availability Implementation
This highly available scenario is implemented in scenario 1
Option 1:
Use haproxy to proxy harbor data stored locally (or remotely, harbor is enabling synchronization policy).
Option 2:
Using harbor using keepalived vip, the data is stored at the same remote end.
Role Division
| Host Address | role |
|---|---|
| 10.10.1.105 | docker client |
| 10.10.1.106 | Client+haproxy+keepalive |
| 10.10.1.107 | Harbor1 |
| 10.10.1.108 | Harbor2 |
keepalived configuration
Installation skipped
Find it on my blog: https://www.cnblogs.com/yanshicheng/
Configuration is as follows
! Configuration File for keepalived
global_defs {
notification_email {
root@localhost
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1
smtp_connect_timeout 30
router_id Keepalived_107
vrrp_skip_check_adv_addr
vrrp_garp_interval 0
vrrp_gna_interval 0
vrrp_mcast_group4 224.0.0.18
vrrp_strict
vrrp_iptables
vrrp_instance Harbor {
state BACKUP
interface eth1
virtual_router_id 100
nopreempt
priority 80
advert_int 1
authentication {
auth_type PASS
auth_pass 123456
}
virtual_ipaddress {
10.10.1.180
}
track_interface {
eth0
eth1
}
}
haproxy configuration
Installation skipped
Find it on my blog: https://www.cnblogs.com/yanshicheng/
Add agents as follows
listen harbor bind 10.10.1.180:80 mode tcp balance source server harbor107 10.10.1.107:80 weight 10 check inter 3s fall 3 rise 5 server harbor108 10.10.1.108:80 weight 10 check inter 3s fall 3 rise 5
Configure Harbor repository synchronization
Note: Both opposite Harbor and native configurations need to be configured
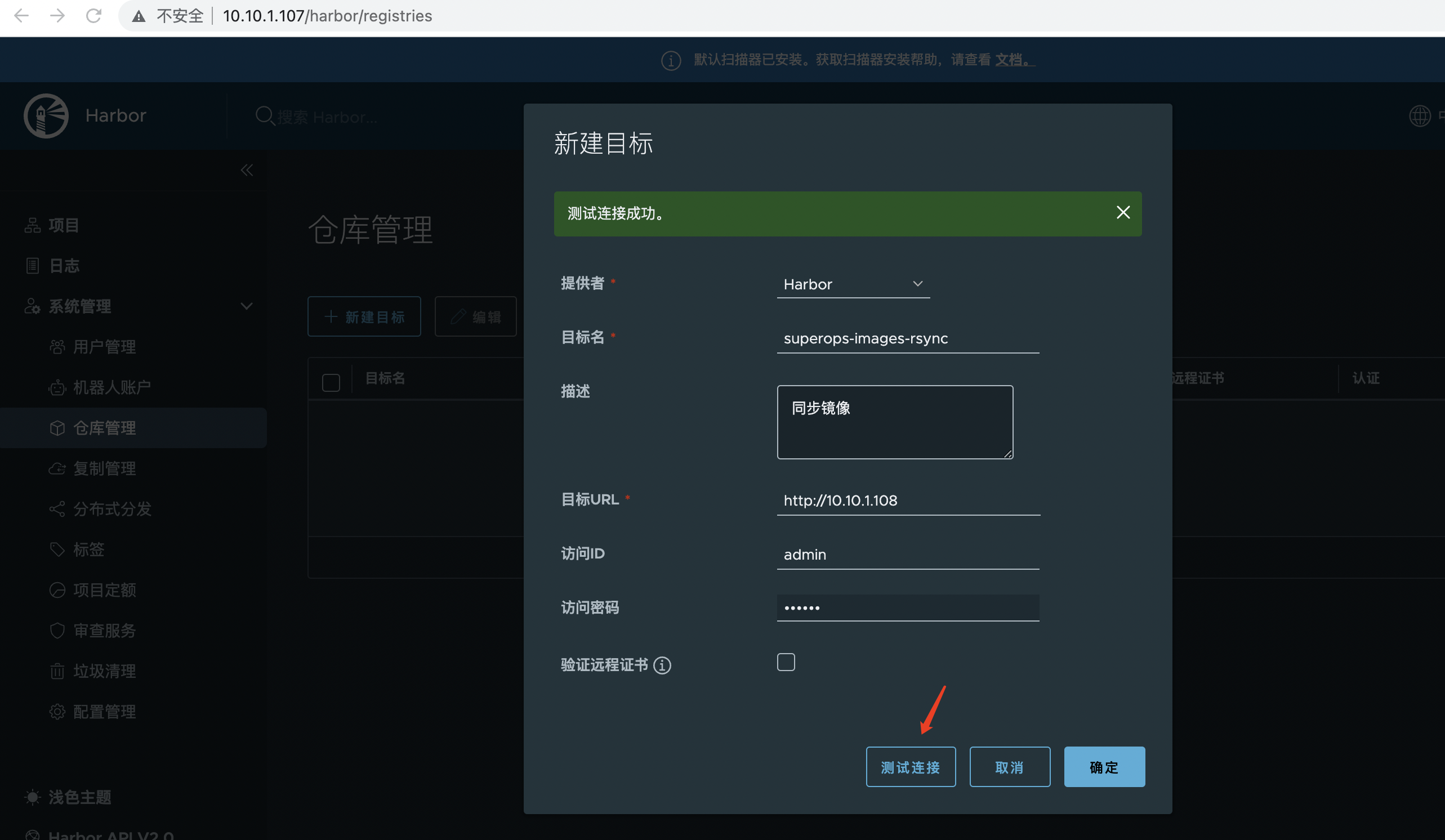
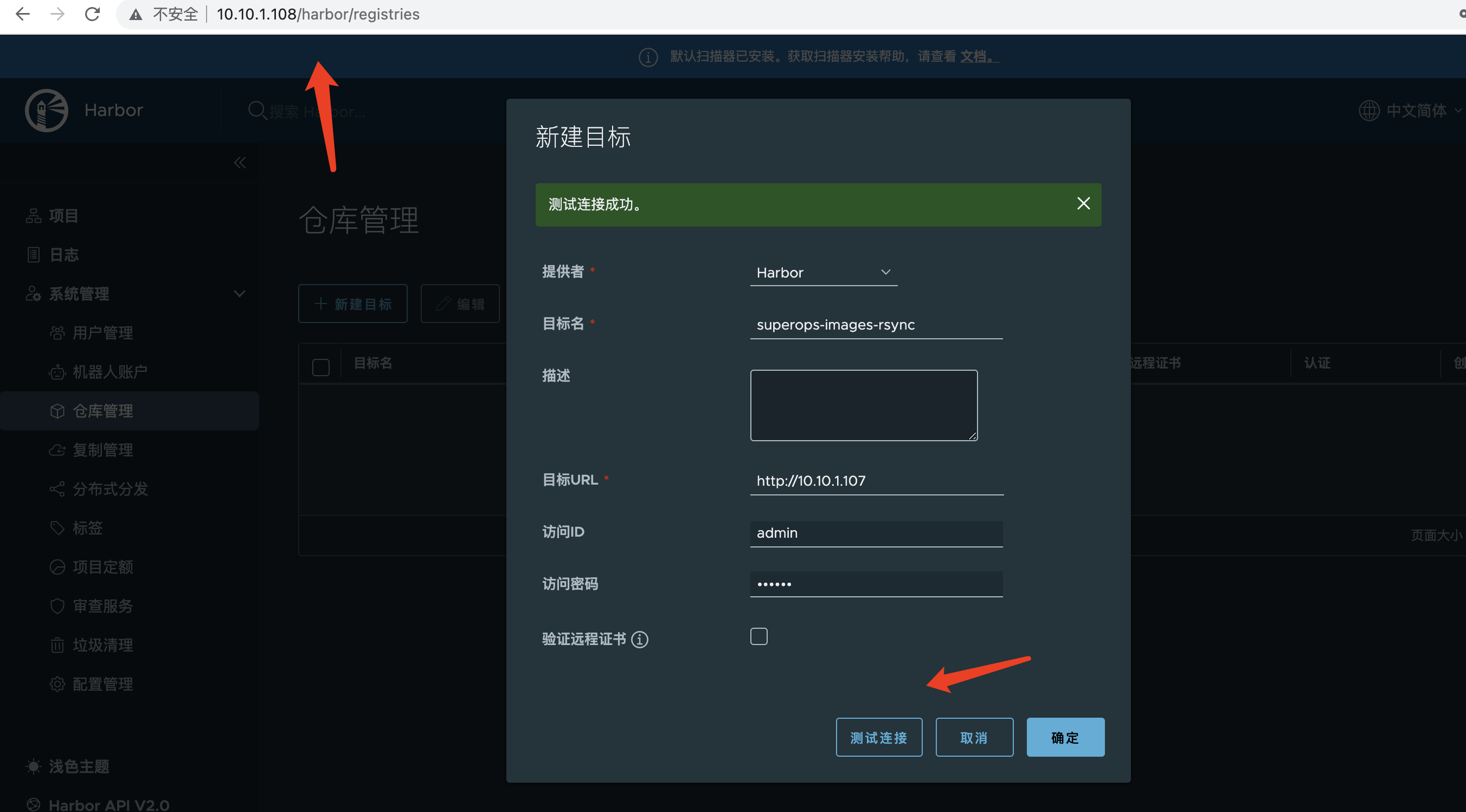
Setup configures warehouse management as follows
107 as follows
108 as follows
Configure Harbor Synchronization Rules
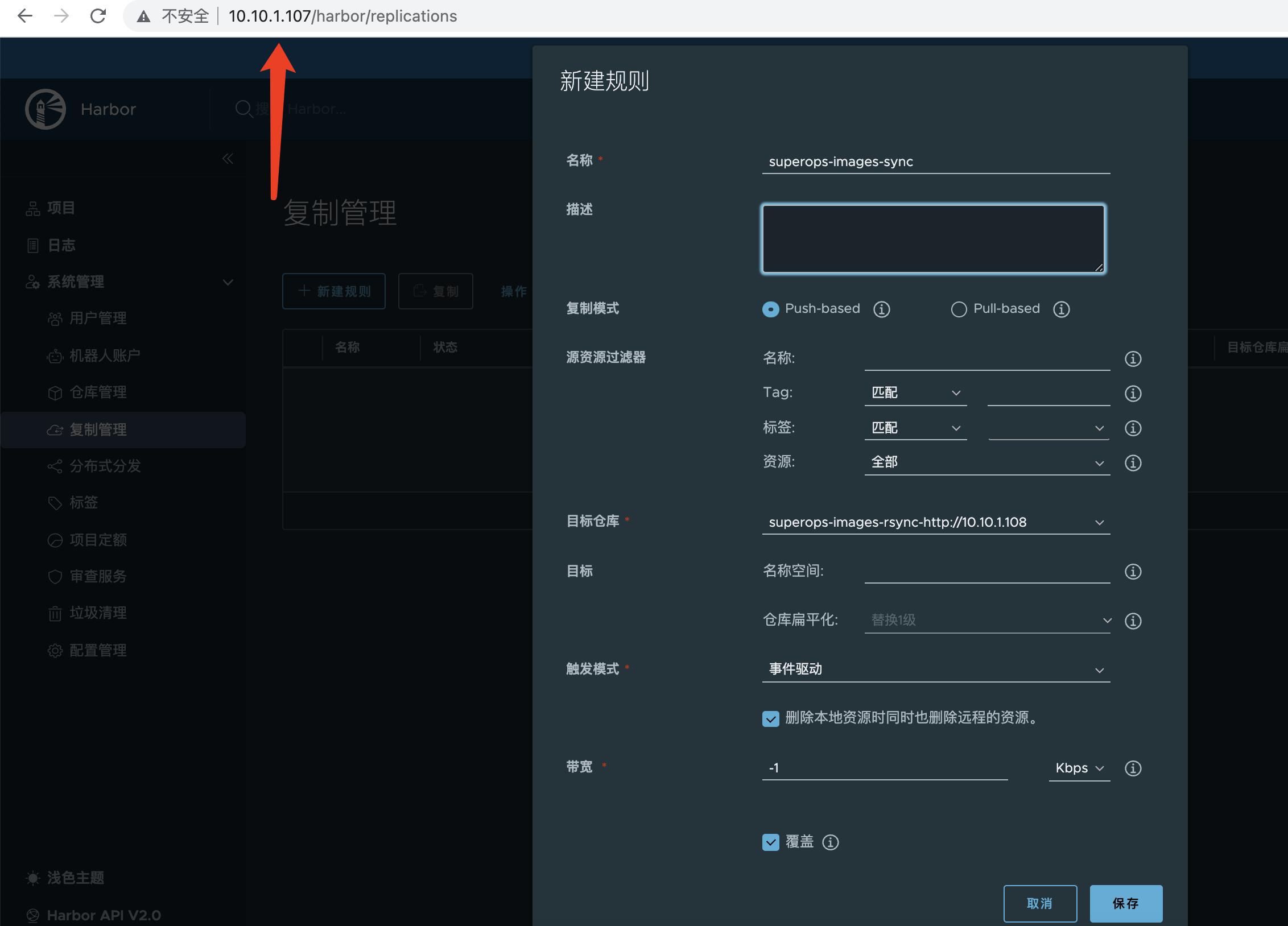
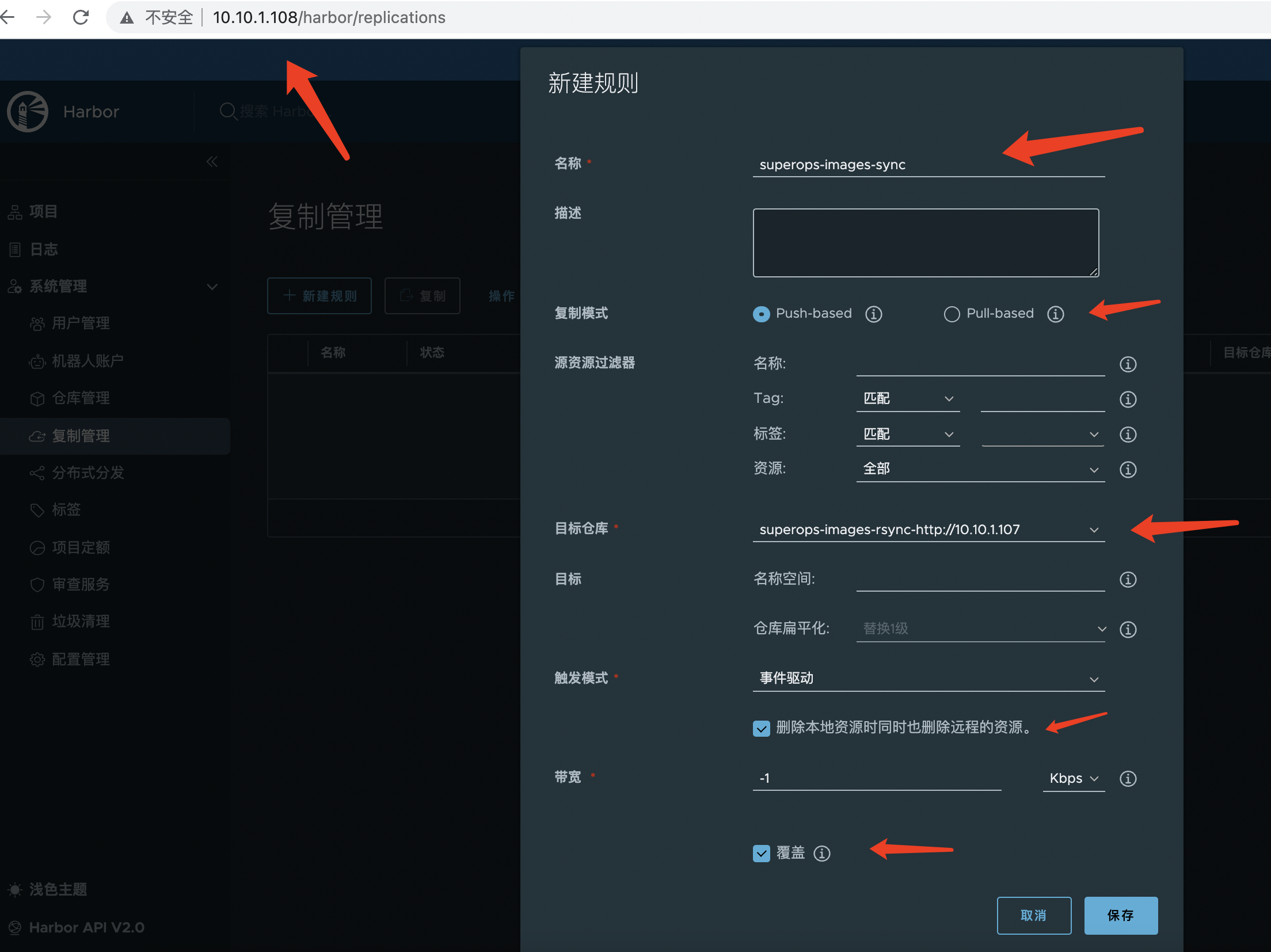
Note: Both opposite Harbor and native configurations need to be configured
Configure replication management in settings as follows:
- Copy mode: Recommend using push to receive mirrors on the local side, push to the opposite side
- Resource filter: It depends
- Target warehouse: Select the opposite end
- Target: The end-to-end project
- Trigger mode: Recommend time-driven and Delete remote resources when local resources are also checked
- Bandwidth: Current Limit
107 as follows
108 as follows
Client Test Upload Mirror
# Log on to warehouse first [root@k8s-105 ~]# docker login harbor.superops.cc Username: admin Password: WARNING! Your password will be stored unencrypted in /root/.docker/config.json. Configure a credential helper to remove this warning. See https://docs.docker.com/engine/reference/commandline/login/#credentials-store Login Succeeded # Relabel Mirror [root@k8s-105 ~]# docker tag alpine:latest harbor.superops.cc/superops/alpine:v1 # Upload Mirror [root@k8s-105 ~]# docker push harbor.superops.cc/superops/alpine:v1 The push refers to repository [harbor.superops.cc/superops/alpine] 8d3ac3489996: Pushed v1: digest: sha256:e7d88de73db3d3fd9b2d63aa7f447a10fd0220b7cbf39803c803f2af9ba256b3 size: 528 # Other Client Download Tests [root@k8s-106 ~]# docker pull harbor.superops.cc/superops/alpine:v1 v1: Pulling from superops/alpine Digest: sha256:e7d88de73db3d3fd9b2d63aa7f447a10fd0220b7cbf39803c803f2af9ba256b3 Status: Downloaded newer image for harbor.superops.cc/superops/alpine:v1 harbor.superops.cc/superops/alpine:v1 [root@k8s-106 ~]# docker image ls REPOSITORY TAG IMAGE ID CREATED SIZE alpine latest c059bfaa849c 5 weeks ago 5.59MB harbor.superops.cc/superops/alpine v1 c059bfaa849c 5 weeks ago 5.59MB
Harbor Warehouse Check Mirror Synchronization
107 Check
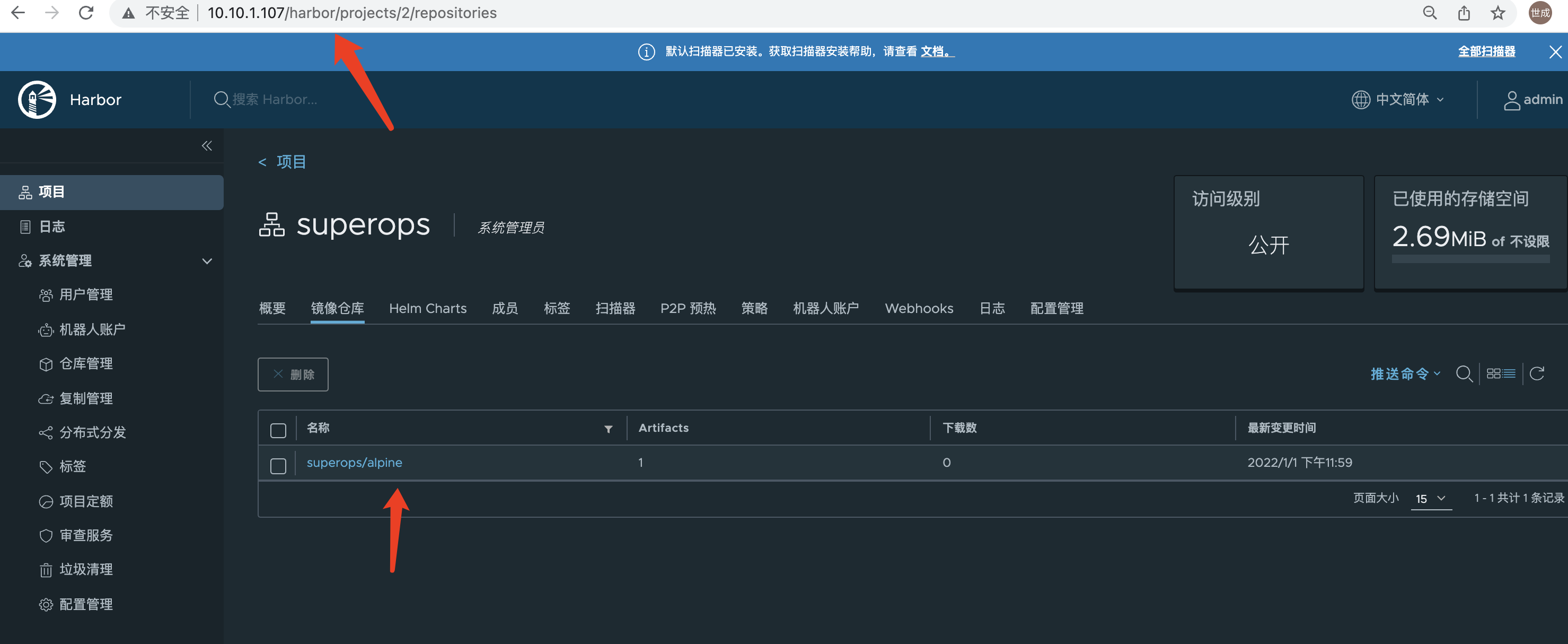
108 Check
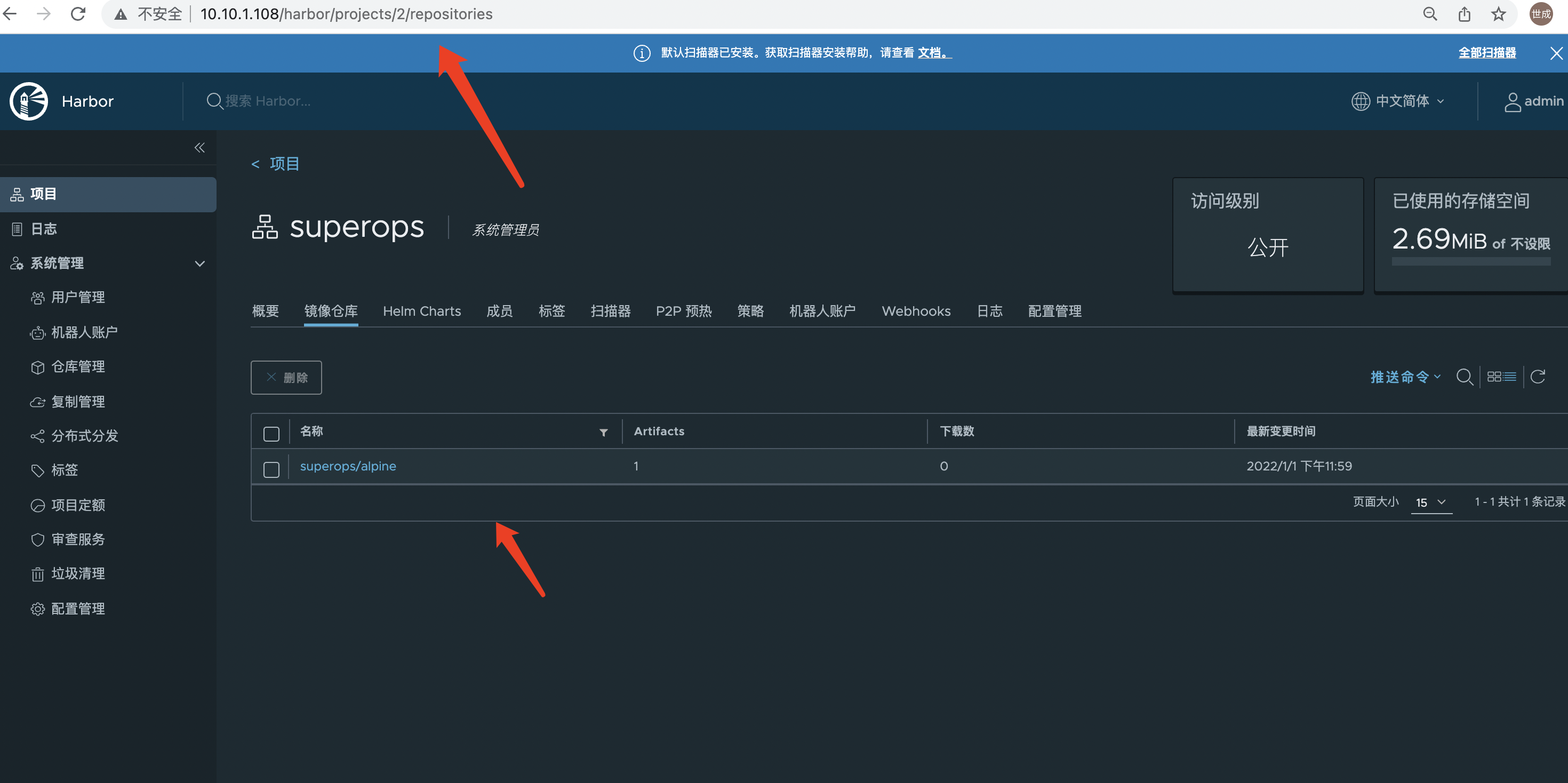
Harbor implementation based on https
Not Ended to Continue