ACL Access Control List
Functions:
1. Access Restrictions - Match traffic on router traffic-in or-out interfaces and then restrict them
2. Define traffic of interest
Introduction to ACL:
1. From top to bottom, match one by one, the previous match is executed as above, not the next
2. Calls to the ACL list are divided into in (matching the ACL before viewing the route) and out (checking the route before matching the ACL)
3. Pyramid structure must be satisfied
4. ACLs are divided into standard ACLs and extended ACLs
5. (implied denial of all in cisco at the end; default processing in Huawei devices if no ACL matches)
Classification of ACL s
Standard ACL: Focus on the source IP address and use it as close to the target as possible
Extended ACL: Focus on the source IP, target IP, protocol, and use as close to the source as possible (ACL can no longer filter its own generated traffic over the source)
ACL deployment: Matching suffix parameter in ACL is wildcard 0 for fixed bit 1 for any bit
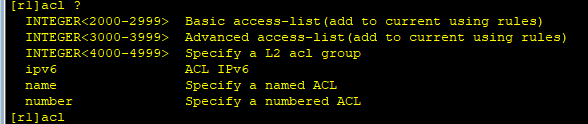
INTEGER<2000-2999>Used by Standard ACL s----A number is a table
INTEGER<3000-3999>Extended ACL Used
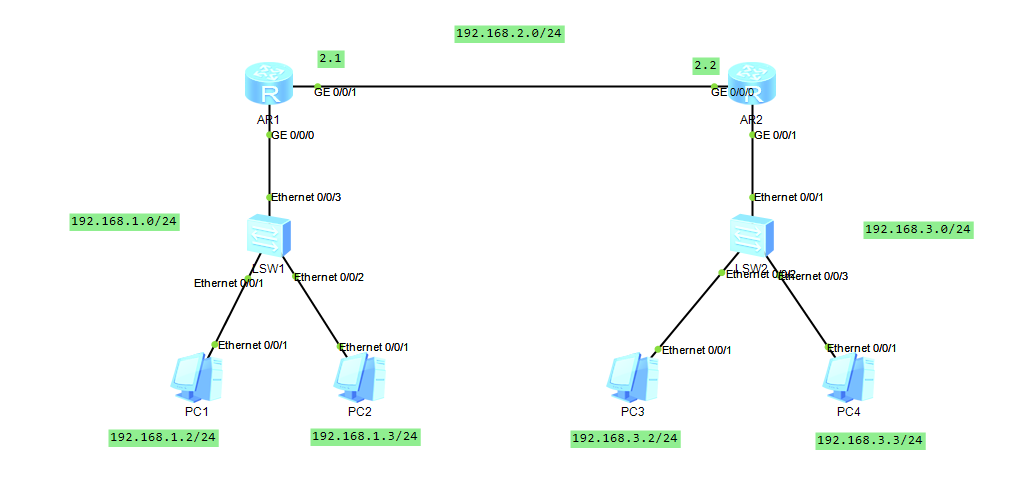
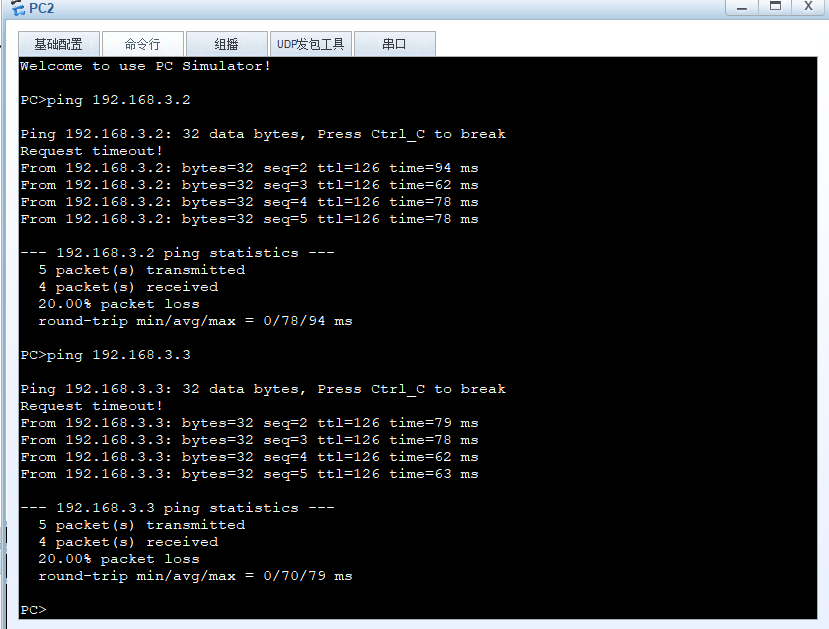
Implementation: pc1 cannot access pc3 and pc4, pc2 can access pc3 and PC4
R1 Configure Static Routing
[r1]int g 0/0/0 [r1-GigabitEthernet0/0/0]ip add 192.168.1.1 [r1]int g 0/0/1 [r1-GigabitEthernet0/0/1]ip add 192.168.2.1 24 [r1]ip route-stat 192.168.3.0 24 192.168.2.2
R2 Configure Static Routing
[r2]int g 0/0/1 [r2-GigabitEthernet0/0/1]ip add 192.168.3.1 24 [r2]int g 0/0/0 [r2-GigabitEthernet0/0/0]ip add 192.168.2.2 24 [r2]ip route-static 192.168.1.0 24 192.168.2.1
Attach ip and gateway to pc, use pc1 to test interoperability
ping 192.168.2.2 ping 192.168.3.1 ping 192.168.3.3
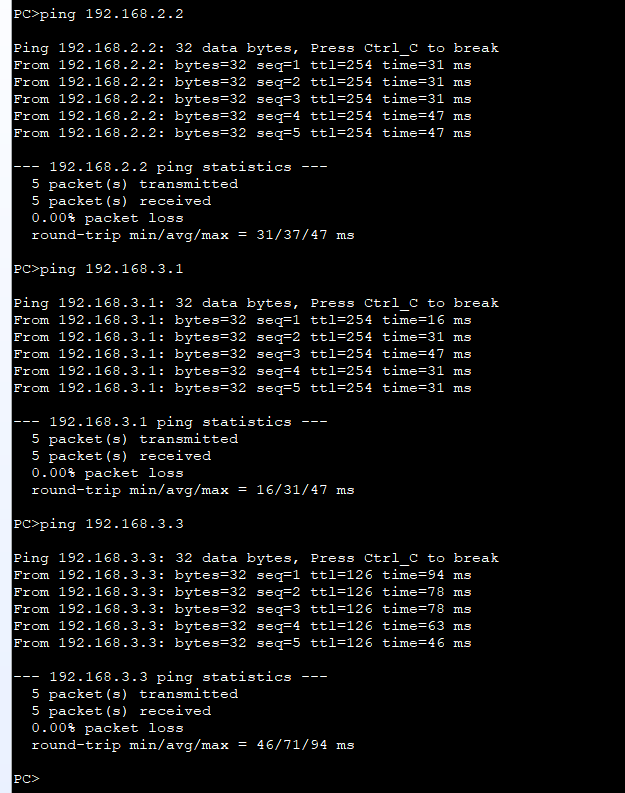
Testing interoperability using pc2
ping 192.168.3.2 ping 192.168.3.3
Set ACL, because it is standard ACL, need to be as close to target as possible, so need to configure on R2 router
[r2]acl 2000 `Create Number 2000 ACL` [r2-acl-basic-2000]rule deny source 192.168.1.2 0.0.0.0 `Rejection 1.2 this ip`
Note: ACL uses wildcards and OSPF uses backmasks; the difference is that wildcards can be 0 and 1 interpolated, similar to the following
[r2-acl-basic-2000]rule deny source 192.168.1.2 0.255.0.255
Reject an address range
[r2-acl-basic-2000]rule deny source 192.168.1.2 0.0.0.255
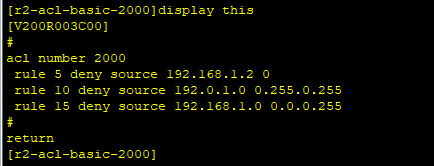
Increase need at 5 step by default to facilitate insertion of rules
192.168.1.3 is allowed because it is top-down, so we need to write before rule 10 or access will be denied
[r2-acl-basic-2000]rule 9 permit source 192.168.1.3 0
Note: ACL must be invoked on the interface after customization is complete to work effectively
[r2]int GigabitEthernet 0/0/1 [r2-GigabitEthernet0/0/1]traffic-filter ? inbound Apply ACL to the inbound direction of the interface `Inbound` outbound Apply ACL to the outbound direction of the interface `Outgoing` [r2-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
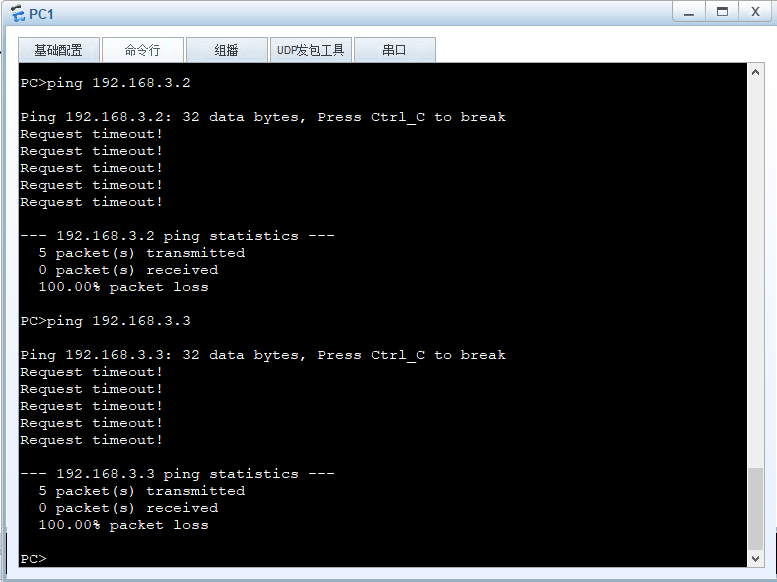
Rules are written for testing, use PC1 to test first
Testing with PC2
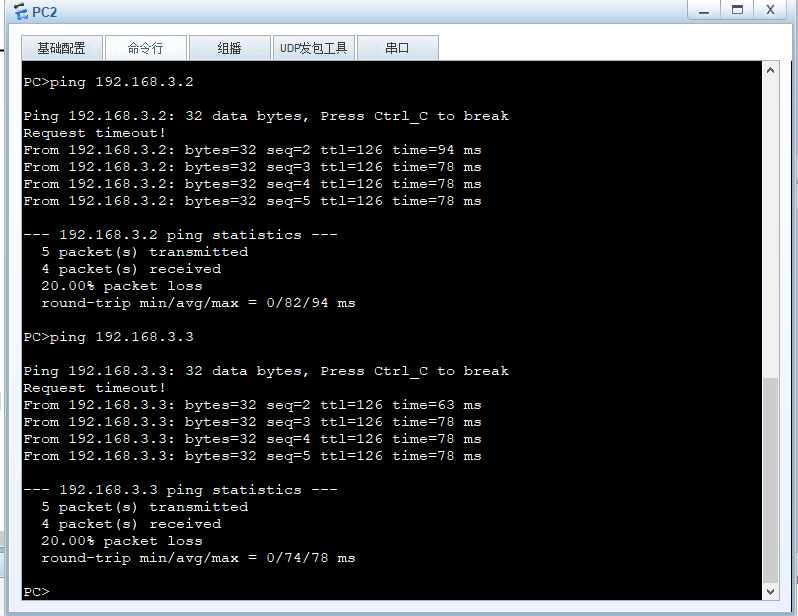
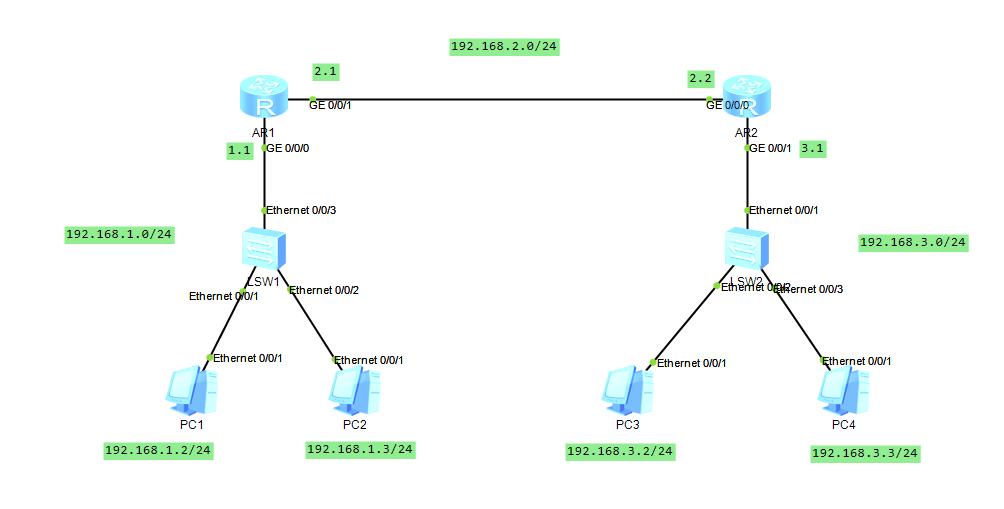
Implementation: pc1 cannot access pc3 but can access pc4 and pc2 can be accessed normally (at this point extended ACL must be used)
Let's delete the acl we just set up
[r2-acl-basic-2000]undo rule 5 [r2-acl-basic-2000]undo rule 9 [r2-acl-basic-2000]undo rule 10 [r2-acl-basic-2000]undo rule 15
Because the ACL is extended, we need to set it close to the source, so we need to set it on R1. According to the default feature of Huawei, we just need to set the deny permission.
[r1]acl 3000 [r1-acl-adv-3000]rule deny ip source 192.168.1.2 0 destination 192.168.3.2 0 deny: refuse permit: allow ip: Agreement source: source destination: target
Call on interface
[r1]int g 0/0/0 [r1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
Use pc1 test
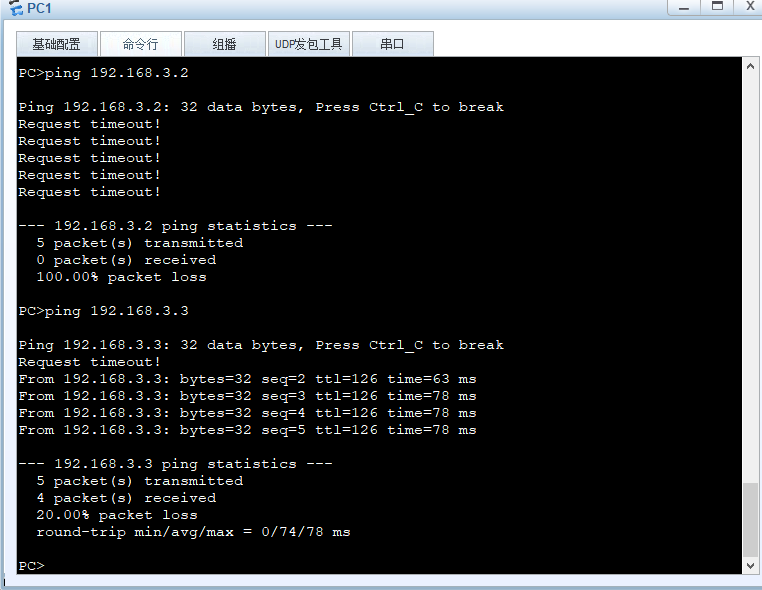
Use pc2 testing
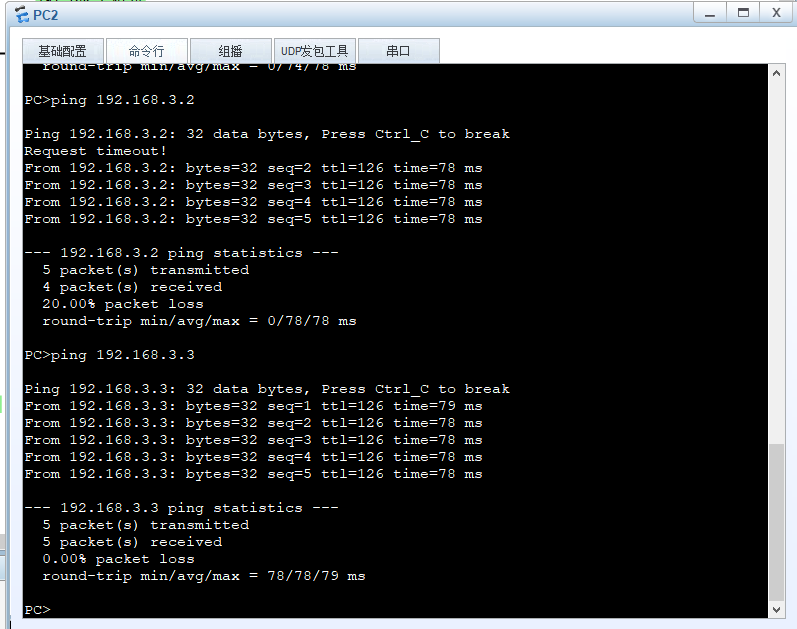
Implementation: setting 192.168.2.1 cannot ping 192.168.2.2, but 192.168.2.2 can ping 192.168.2.1
[r2]acl 3000 [r2-acl-adv-3000]rule deny icmp source 192.168.2.1 0 destination 192.168.2.2 0 i cmp-type echo [r2]int GigabitEthernet 0/0/0 [r2-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
test
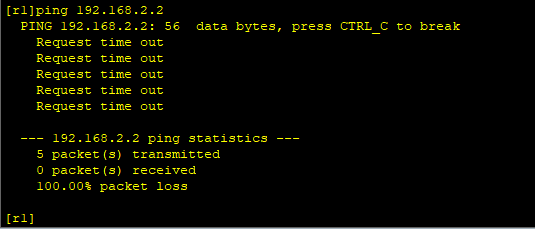
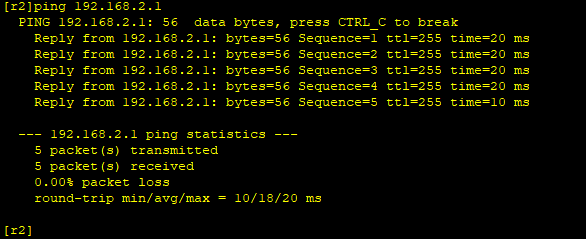
Implementation: R1 remote login R2 (as Huawei's pc cannot use remote login, so test with router)
telnet remote login: based on port 23 under tcp;
Conditions:
1. Normal communication between login and login devices
2. Open remote login service by logged-in device
Configure login account and password
[r2]aaa [r2-aaa]local-user ppx password cipher 123456 `Account, password` [r2-aaa]local-user ppx service-type telnet `Functions of this account` [r2-aaa]local-user ppx privilege level ? INTEGER<0-15> Level value [r2-aaa]local-user ppx privilege level 15 `Set the permissions the user has, 15 being the maximum permission` [r2]user-interface vty 0 4 `Virtual Login Interface` [r2-ui-vty0-4]authentication-mode aaa `Call Authentication`
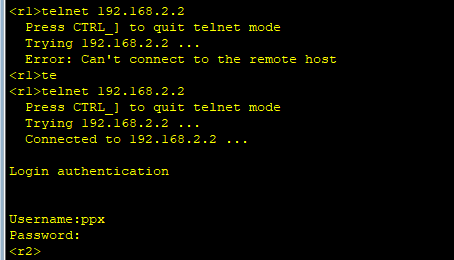
Deny R1 remote login R2
[r2]acl 3000 [r2-acl-adv-3000]rule deny tcp source 192.168.2.1 0.0.0.0 destination 192.168.2.2 0 destination-port eq 23 [r2]int g 0/0/0 [r2-GigabitEthernet0/0/0]traffic-filter inbound acl 3000