Role-based access control (RBAC)
One way to restrict system access to authorized users is to define policy-independent access control mechanisms around roles and privileges, and the components of RBAC make it easy to perform user assignments.
Within the organization, various jobs will be created role .Permissions to perform certain actions have been assigned to specific roles.Members or staff (or other system users) are assigned specific roles through which they obtain the privileges required to perform specific system functions.Since users are not directly assigned permissions but are only granted permissions through their roles (one or more roles), the management of individual user permissions becomes a simple matter of assigning appropriate roles to user accounts.This simplifies common operations, such as adding users or changing user departments.
RBAC defines three main rules
1. Role Assignment: An object can exercise its privileges only if it has selected or assigned roles.
2. Role Authorization: An active role that must be the principal authorizing body.Using Rule 1 above, this rule ensures that users can only assume roles that are authorized by them.
3. Privilege Authorization: An object can exercise privileges only if its active role is authorized.Rules 1 and 2 are used to ensure that users can only exercise their authorized rights.
Create RBAC Model
Menu
public class SysMenu { /// <summary> /// Parent /// </summary> public int ParentId { get; set; } = 0; /// <summary> /// Menu Name /// </summary> [StringLength(20)] public string Name { get; set; } /// <summary> /// Menu Address /// </summary> [StringLength(20)] [Required] public string Url { get; set; } /// <summary> /// Hierarchy /// </summary> [Column(TypeName = "tinyint(4)")] public int Level { get; set; } = 1; /// <summary> /// Menu Permissions(list<int /> json) /// </summary> [StringLength(100)] public string Operates { get; set; } /// <summary> /// sort /// </summary> public int Sort { get; set; } /// <summary> /// Menu Icon /// </summary> public string Icon { get; set; } }
Functions
public class SysOperate { /// <summary> /// Button name /// </summary> [StringLength(20)] [Required] public string Name { get; set; } /// <summary> /// Remarks /// </summary> [StringLength(int.MaxValue)] public string Remark { get; set; } /// <summary> /// Unique Identification /// </summary> [Required] public int Unique { get; set; } }
role
public class SysRole { /// <summary> /// Role Name /// </summary> [StringLength(20)] [Required] public string Name { get; set; } /// <summary> /// Remarks /// </summary> [StringLength(int.MaxValue)] public string Remark { get; set; } }
user
public class SysUser { /// <summary> /// role id /// </summary> public int RoleId { get; set; } /// <summary> /// User name /// </summary> [StringLength(32)] [Required] public string UserName { get; set; } /// <summary> /// Password /// </summary> [StringLength(500)] [Required] public string Password { get; set; } }
Make it an Authorized Rights Service in Micro Services
In daily work, there will always be many systems to do, each system should have a complete set of permission functions, have ready-made direct take paste copy, not ready-made and waste a lot of time to design and implement it.If we have such a service, we can save a lot of unnecessary paste and copy operations and a lot of time.
SoKetchup.zeroSuch a service was born.It is a privilege authorization service based on ketchu micro-service framework, which can basically meet the privilege requirements of our daily work.
The front end of the service is based on vue's template d2admin.
Ketchup.zeroFunctions
Land

panel
User Configuration Roles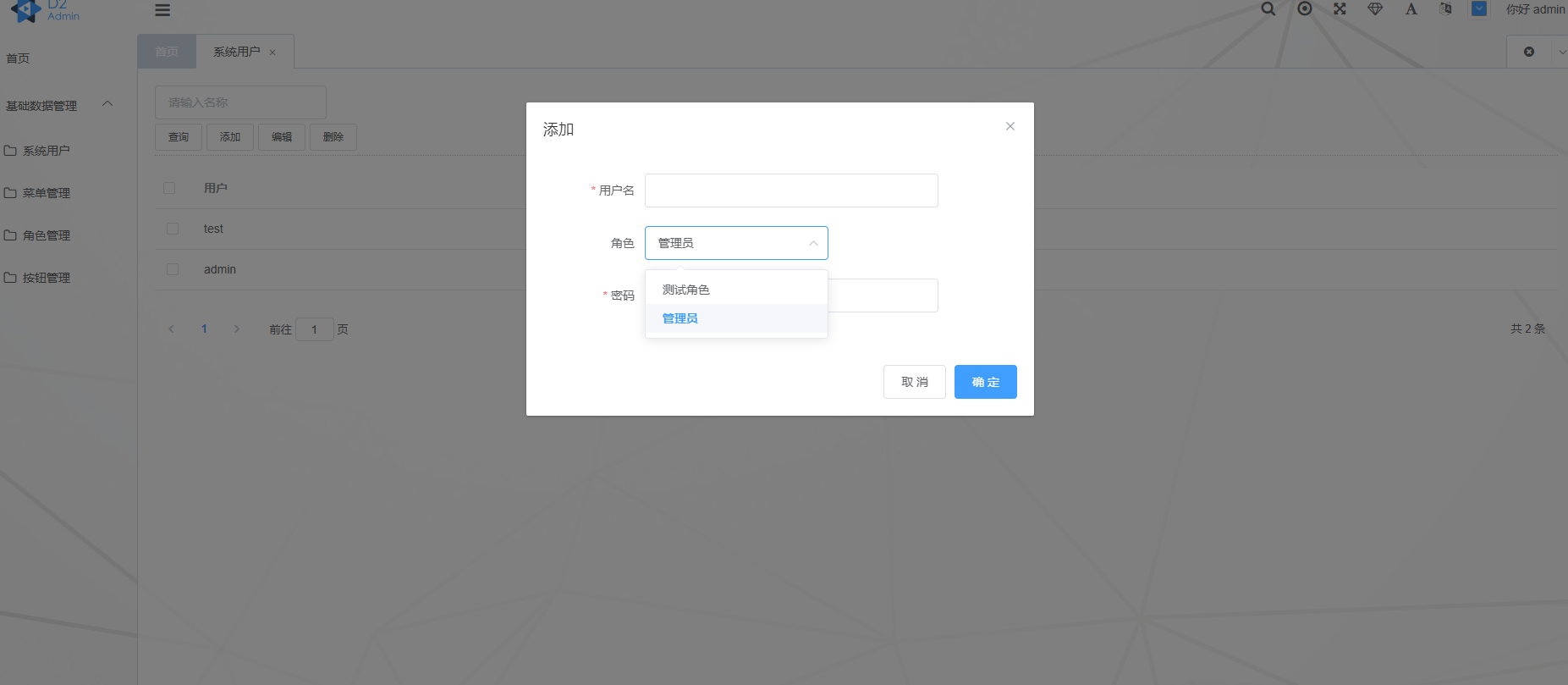
What permissions do menu settings have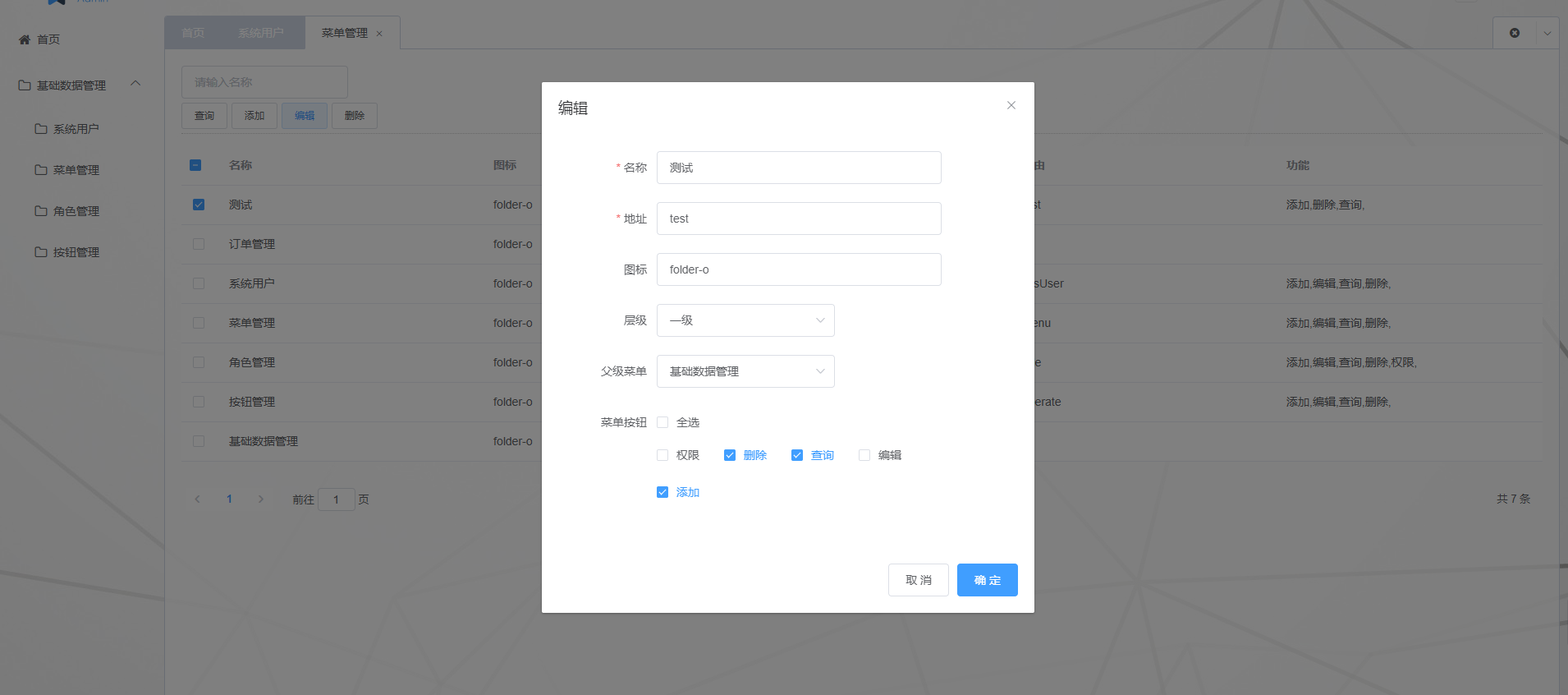
Privilege/Function/Button Management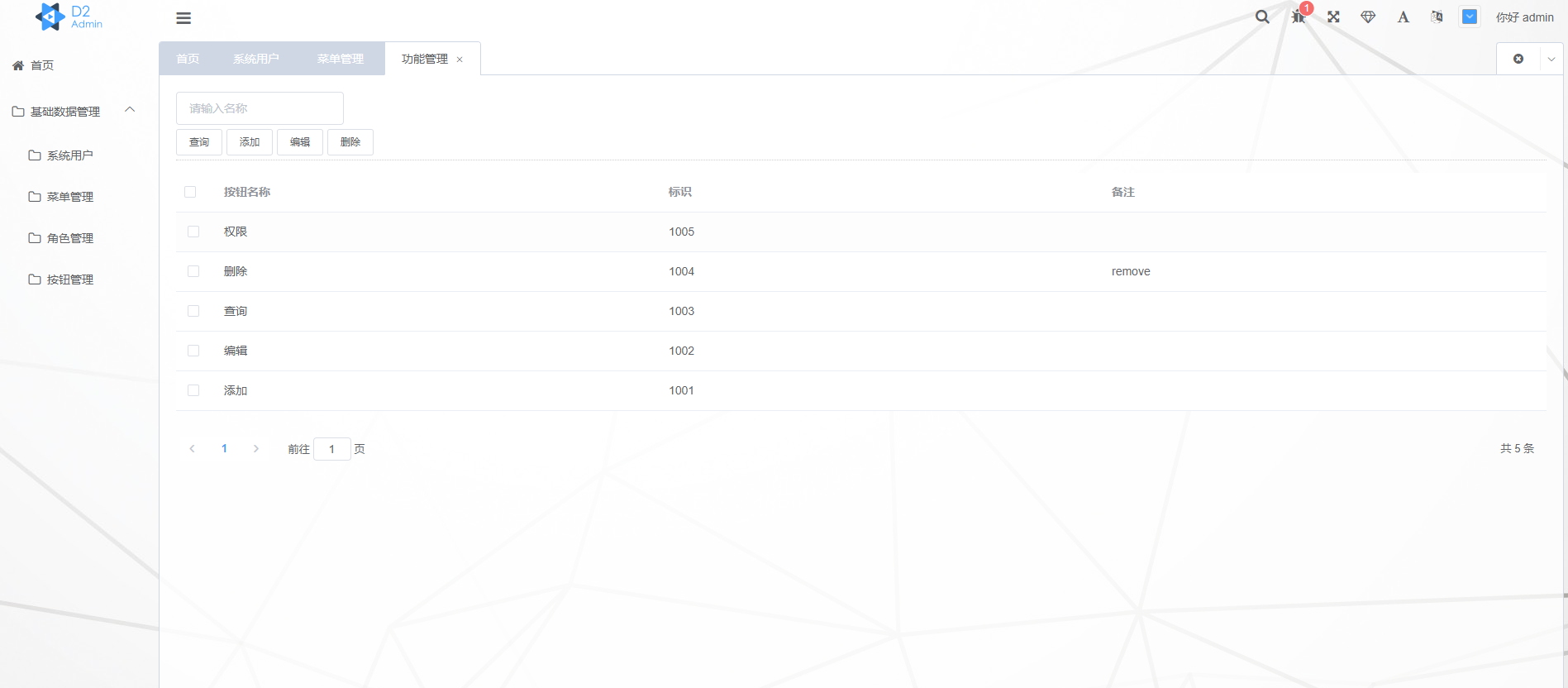
Role Setting Permissions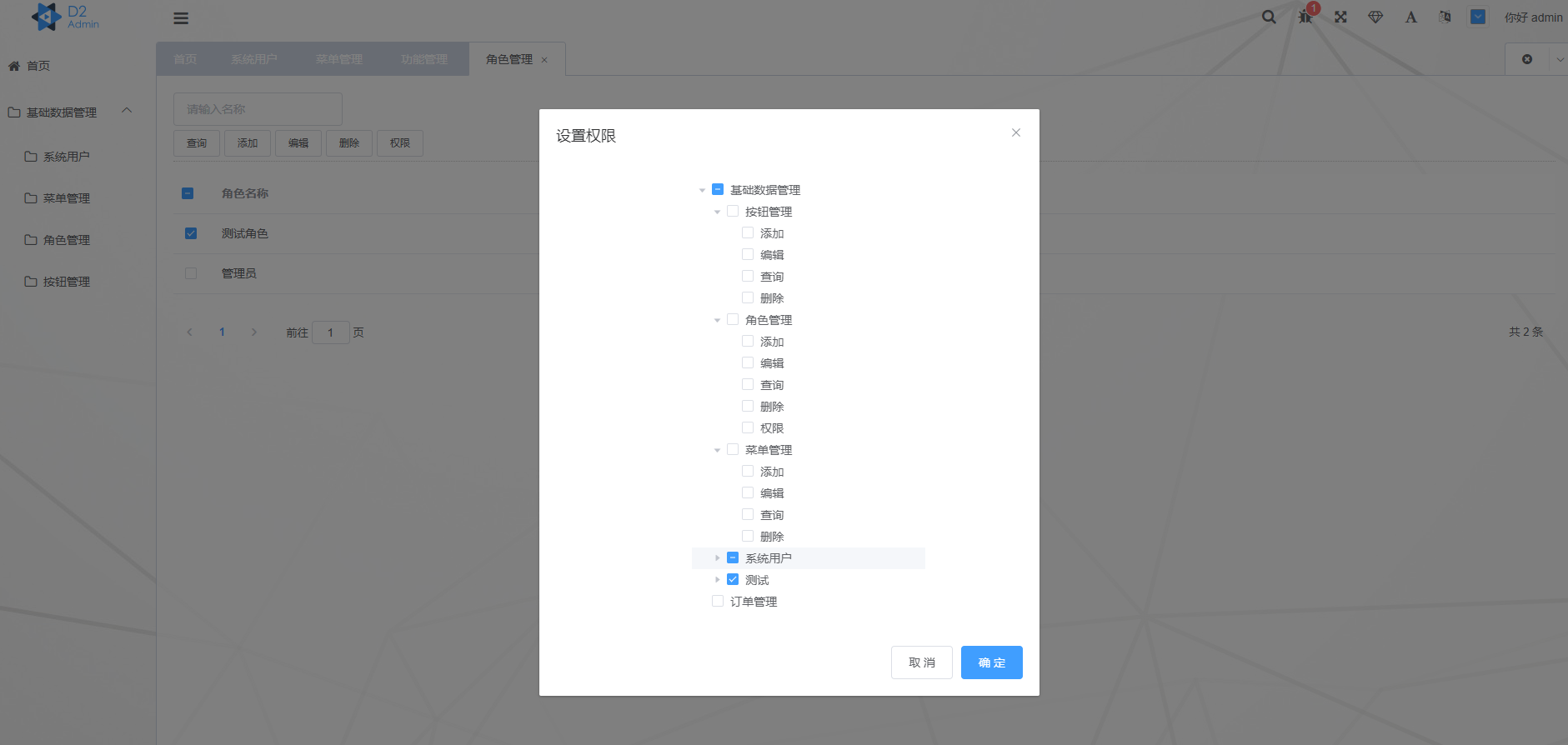
Final Amway
If it helps you, give a wave start
serviceKetchup.zeroSource address: https://github.com/simple-gr/ketchup.zero
Microservice framework ketchup source address: https://github.com/simple-gr/ketchup
ketchup exchange group: 592407137