1, Deploy PPTP VPN server
1. Check whether the server system environment supports the installation of pptp
1,Check whether the system kernel supports MPPE patch [root@PPTP ~]# modprobe ppp-compress-18 && echo success display success Description system support MPPE If the patch is not supported, you need to install it first kernel-devel [root@PPTP ~]# yum -y install kernel-devel 2,Check whether the system is on TUN/TAP support [root@PPTP ~]# cat /dev/net/tun If this command displays the following text, it indicates that it is passed: cat: /dev/net/tun: File descriptor in bad state 3,Check whether the system is on ppp support [root@PPTP ~]# cat /dev/ppp If this command displays the following text, it indicates that it is passed: cat: /dev/ppp: No such device or address
The above three items must be met at the same time, otherwise pptp cannot be installed
2. Install pptpd package
[root@PPTP ~]# yum clean all #Empty local yum source [root@PPTP ~]# yum repolist #Reload local yum source [root@PPTP ~]# yum -y install pptpd iptables bash-completion ppp #I use the iptables firewall function here. Huawei cloud does not need to be installed. In the later stage, I can directly change the security group [root@PPTP ~]# bash #After executing this statement, you can complete the command with the tab key [root@PPTP ~]# rpm -qc pptpd #View pptpd software configuration file directory #Display: /etc/ppp/options.pptpd /etc/pptpd.conf /etc/sysconfig/pptpd
3. Modify profile
3.1. Modify / etc / pptpd conf
[root@PPTP ~]# vim /etc/pptpd.conf #Press Caps on the keyboard to adjust to the uppercase state, and press the uppercase G to go directly to the last line #Then press the keyboard Caps to switch to the lowercase state Press i key #vim insertion function Remove the following notes and modify the following, localip 192.168.3.100 #External ip address of the server remoteip 172.16.0.1-50 #IP address pool assigned to clients After modification, press esc Key, :wq #vim save exit
Note: localip is the external ip of the server
3.2. Modify / etc / PPP / options pptpd
[root@PPTP ~]# vim /etc/ppp/options.pptpd name pptpd ms-dns 8.8.8.8 #The dns address of the server can be customized or viewed ms-dns 8.8.8.2 #dns address of the server, which can be customized :wq #vim save exit [root@PPTP ~]# cat /etc/resolv.conf #View dns of this machine #nameserver dns address nameserver 8.8.8.8
3.3. Modify / etc / PPP / chap secrets and add user and password
[root@PPTP ~]# vim /etc/ppp/chap-secrets User name connection name password ip address zhangsan * 123 * lisi * 123 * #One line for one user, * indicates any. If you need to display the connection name and ip, you can customize it
Note: the connection name and IP address can be customized, which means that the client is automatically assigned an IP address
3.4. Enable routing forwarding function
Temporary opening:
[root@PPTP ~]# echo "1" > /proc/sys/net/ipv4/ip_forward [root@PPTP ~]# cat/proc/sys/net/ipv4/ip_forward #Just display 1
Note: this value cannot be modified with vim, but can only be modified with echo redirection. It is a temporary modification. Restore the initial value after restart
Permanently open
[root@PPTP ~]# vim /etc/sysctl.conf Add a row net.ipv4.ip_forward = 1 :wq Save exit [root@PPTP ~]# /sbin/sysctl -p ##Effective immediately
3.5. CentOS7 firewall settings (either can be configured, both can be configured, or neither can be configured)
firewall settings
[root@PPTP ~]# firewall-cmd --permanent --add-service=ipsec [root@PPTP ~]# firewall-cmd --permanent --add-port=1701/udp [root@PPTP ~]# firewall-cmd --permanent --add-port=4500/udp [root@PPTP ~]# firewall-cmd --permanent --add-masquerade [root@PPTP ~]# firewall-cmd --reload
I use the security group on the server instead of the system firewall. In order to pass the test, I stop the firewall
[root@PPTP ~]# systemctl stop firewalld
iptables settings
Add rule
[root@PPTP ~]# iptables -t nat -A POSTROUTING -s 172.16.0.0/255.255.255.0 -j SNAT --to-source 192.168.3.100 [root@PPTP ~]# iptables -A FORWARD -p tcp --syn -s 172.16.0.0/255.255.255.0 -j TCPMSS --set-mss 1356 [root@PPTP ~]# /etc/init.d/iptables save #Save rule
Open pptp service port tcp 1723 and set * * * dial in client ip address pool 172.16.1.0 / 255.255.255.0 to pass through the firewall
[root@PPTP ~]# vim /etc/sysconfig/iptables #Edit and add the following code -A RH-Firewall-1-INPUT -p tcp -m state --state NEW -m tcp --dport 1723 -j ACCEPT -A RH-Firewall-1-INPUT -s 192.168.1.0/255.255.255.0 -j ACCEPT :wq! #Save, exit [root@PPTP ~]# systemctl restart iptables #Restart iptables [root@PPTP ~]# systemctl enable iptables #Startup and self start [root@PPTP ~]# cat /etc/sysconfig/iptables #View firewall profile
I use the security group on the server instead of the system firewall. In order to pass the test, I stop the firewall
[root@PPTP ~]# systemctl stop iptables
4. Start service
[root@PPTP ~]# systemctl restart pptpd [root@PPTP ~]# systemctl enable pptpd [root@PPTP ~]# ss -ntlup | grep pptpd ##View the service port number. The default is 1723
Note: after executing systemctl stop iptables and systemctl stop firewalld, the security group of the server needs to add its own rules. Adding rules requires a port number, so please remember the port number
5. Huawei cloud security group configuration
1) Console - find the EIP
2) Find access control - Security Group - find instance of server binding - configure rule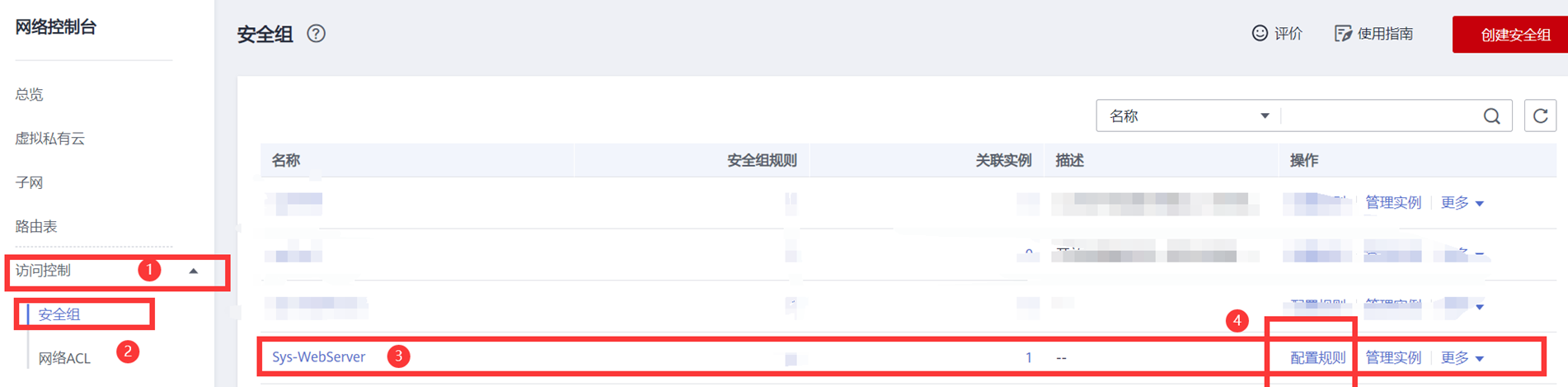
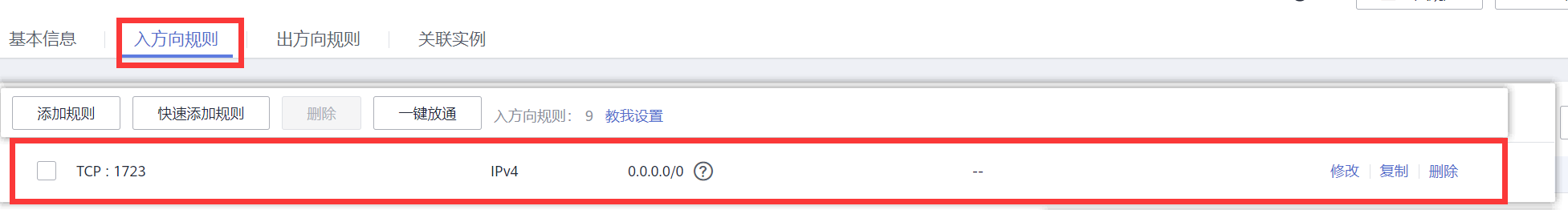
3) Incoming direction rule - add rule - select TCP protocol - enter the service port 1723 of pptpd - OK

4) After configuration, just see the rules
2, Windows client connection and mac connection are directly added in the network preference settings.
Here we mainly introduce window connection
1) Lower right corner of desktop - Network symbol (wifi or small computer icon) - network and Inter settings - VPN

2) VPN - add VPN connection - windows (built-in) - hhh (custom connection name) - 192.168.3.100 (external ip address of the server) - point-to-point PPTP - zhangsan (configured user name) - 123 (configured password) - save


3) hhh - connected - connected will be displayed after successful connection

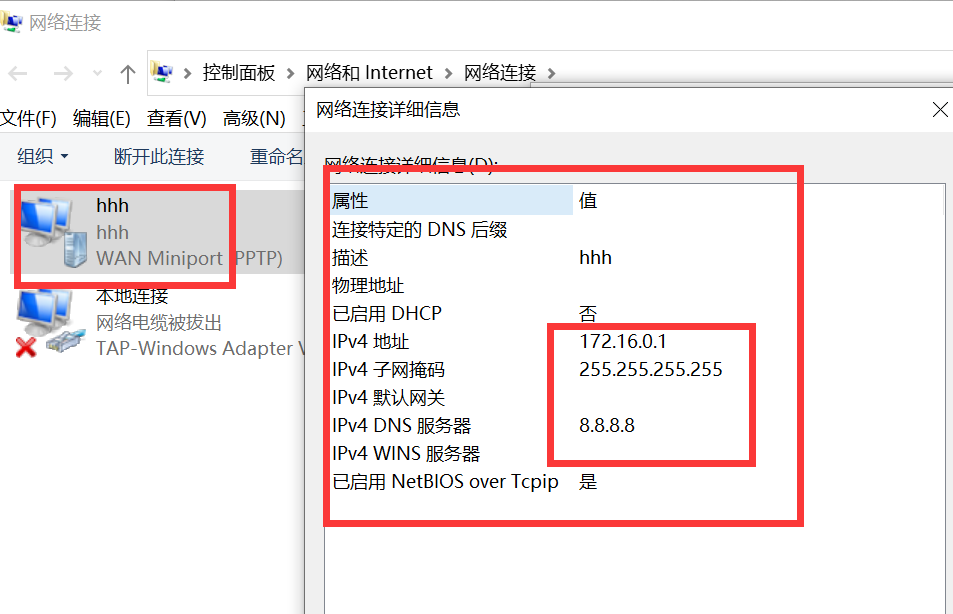
4) Check the network properties to see if the ip is in the configured property pool