In the penetration test, information collection is particularly important. In the information collection stage, the penetration test team can use various methods to obtain information about the topology and system configuration of the target network. Whether the information is perfect or not will seriously affect the speed and depth of subsequent penetration test.
- Two ways of information collection
- Active collection: directly interact with the tested target system by actively sending detection data packets
- Passive collection: when the target is not easy to detect, the information of the target is collected through search engines, social media and other means, and there is no direct interaction with the target system
- Main contents of information collection:
- IP Resources
- Domain name discovery
- Server information collection
- Human resource intelligence collection
- Website key information identification
- Historical loopholes
- Passive information collection
Active information collection
Host discovery based on ICMP Protocol
- Introduction to ICMP Protocol
ICMP Protocol works in the network layer and is used to transfer control information between IP hosts and routers.
ICMP message- Error report message
- Unreachable end point (3)
- Source suppression (4)
- Redirect (5)
- Timeout (11)
- Parameter failure (12)
- IGMP Query
- Response request / reply (8 / 0)
- Timestamp request / reply (13 / 14)
- Address mask request / reply (17 / 18)
- Router inquiry or announcement (10 / 9)
It can be seen that ICMP query message has both request and response, so it can be used for host discovery.
- Error report message
- Response request and response to realize host discovery
The principle is that host A sends an echo request of ICMP message type=8 to host B. after receiving the message, host B will type=0 and then return it to A; If the result is given, the target is in the active state. The most typical one is the ping command. However, due to the abuse of the early ping command, many host firewalls and other security devices directly isolate ICMP messages.
nmap
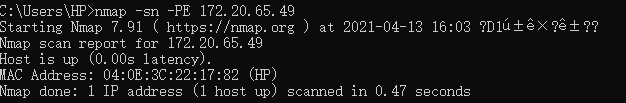
-sn only detects the state of the target host
-PE uses ICMP to respond to requests and responses to discover hosts
Python code implementation
#Guide Package
from scapy.all import *
from scapy.layers.inet import ICMP, IP
target = '192.168.1.1'
#Construct ICMP request packet
ans, unans = sr(IP(dst=target)/ICMP())
for request, answer in ans:
print(answer.sprintf("%IP.src% is alive"))
- ICMP timestamp request and reply
ICMP practice stamp request allows you to query the current time from another host and return coordinated universal time. Therefore, if we want to know whether the target host B is active, we can send a query time request to B through host A. if we get a response (we don't emphasize the content of the response here, just see whether we receive the response from host B), it indicates that host B is active.namp
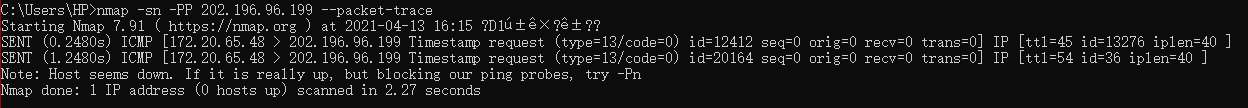
The target machine here is actually active, but why the detection state is inactive officially confirms the above-mentioned filtering of ICMP messages.- ICMP address mask request and reply
The ICMP address mask request is sent by the source host to obtain its own subnet mask when booting the diskless system. The RFC stipulates that it must be the authorized agent of the address mask to send the address mask response. However, most hosts will still give a response when receiving the request to obtain the subnet mask. We can use this feature to realize host discovery.
- ICMP address mask request and reply
Host discovery based on ARP Protocol
ARP protocol works in the network layer and is used to realize the conversion from IP address (logical address) to MAC address (physical address). The working process is to join host A and want to send messages to host B (assuming that the IP is 172.20.65.49). Host A sends ARP request packets in the form of broadcast (that is, ask who is 172.20.65.49 in the LAN and tell me your Mac address), However, only hosts with IP 172.20.65.49 will send A response. Therefore, we can use this process to realize host discovery.
namp 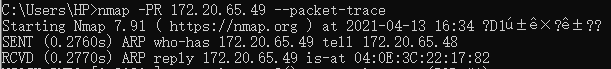
code implementation
from scapy.all import *
from scapy.layers.l2 import ARP, Ether
target = '192.168.1.1'
pkt = Ether(dst='ff:ff:ff:ff:ff:ff') / ARP(pdst=target)
ans,unans = srp(pkt, timeout=1)
for s,r in ans: #The sent package is stored in s and the received package is stored in r
print("Target is alive")
print(s.sprintf("%Ether.src% - %ARP.psrc%"))
print(r.sprintf("%Ether.src% - %ARP.psrc%"))
Host discovery based on TCP protocol
TCP is a connection oriented, reliable and byte stream based protocol working in the transport layer. When it comes to TCP, what you have to say is three handshakes. It probably describes a story that the active section sends a SYN signal saying that I want to establish a connection with you. The passive end gives an ACK confirmation after receiving the request and sends a SYN packet. When the active end receives the reply from the passive end, it sends an ACK again to tell the passive end that it is connected.
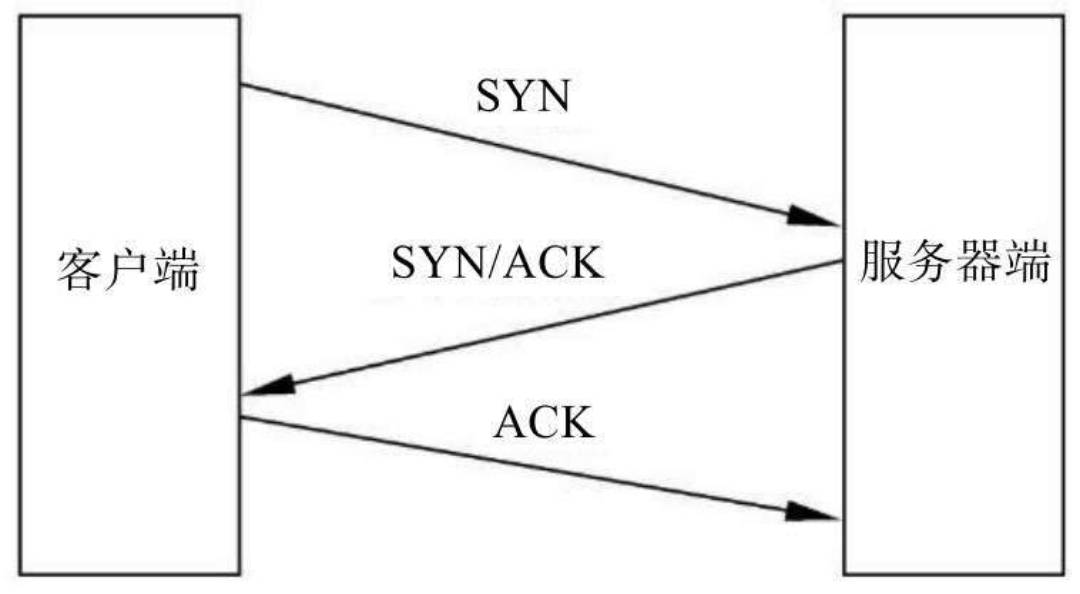
We will find that according to the previous principle that we realize host discovery through request and response, there are two situations we can use in the three times of TCP protocol, as follows:
- SYN scan of TCP
Principle: when detecting the target host, we send a SYN connection establishment request to the target host. If the port of the target host allows access, it will return the SYN/ACK packet to the sender according to the rule of three-time handshake. If the port of the target host is not open, it will also return an RST packet to the sender. Because we don't care about the port here, Therefore, as long as the data packet is received, it indicates that the target is active, and if the data packet is not received, it indicates that the target is not online.
Note: TCP is end-to-end, and both ends are sockets (ip+port)
nmapSYN scan
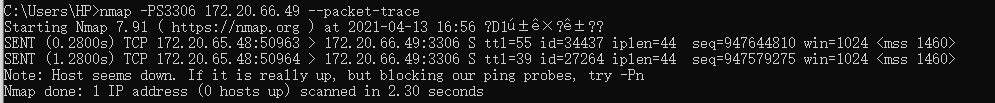
Code implementation Python
from scapy.all import *
from scapy.layers.inet import TCP, IP
targetIP = '192.168.1.1'
targetPort=80
#Construct packet
ans, unans = sr(IP(dst=targetIP) / TCP(dport=80, flags='S'),timeout = 1)
for s,r in ans:
print(r.sprintf("%IP.src% is alive"))
for s in unans:
print(s.sprintf("%IP.dst% is not alive"))
ACK scan
Principle: send ACK packets directly to the target. Since this does not comply with the principle of three handshakes and send SYN first, the connection cannot be established. Therefore, if the target is active, a packet with RST flag bit will be returned, indicating that the connection cannot be established.
namp: nmap -PA[port,port,...] ip
UDP based active device discovery
UDP (User Datagram Protocol) is a connectionless transport layer protocol. Under normal circumstances, when we send messages to the target host with UDP, the target host will not return any packets to us, but the target host is active, but the port is unreachable. At this time, ICMP packets will be sent to us, and if the target host is not active, we will not receive any packets.
code implementation
from scapy.all import *
from scapy.layers.inet import UDP, IP
targetIP = '192.168.1.1'
targetPort = 54763
#Construct packet
ans, unans = sr(IP(dst=targetIP) / UDP(dport=targetPort), timeout=1)
for s,r in ans:
print(r.sprinf("%IP.src% is alive"))
for s in unans:
print(s.sprintf("%IP.dst% is not alive"))
Port scanning technology
Port scanning technology based on TCP full open
(normal three handshakes) if the target port of the target host is open, when we send a SYN request, the target will return a SYN+ACK packet, and we will send another ACK packet to successfully establish the connection.
If the target port is closed, we will receive RST packet after sending SYN packet, indicating that you do not accept the connection request.
In addition, there is another case when the target port is closed, that is, we cannot receive any response after sending SYN packets. There are many reasons for this situation, such as the target host is inactive, or some security devices shield SYN packets on some ports.
code implementation
from scapy.all import *
from scapy.layers.inet import TCP, IP
dst_ip = '192.168.1.1'
src_port = RandShort()
dst_port = 80
resp =sr1(IP(dst=dst_ip) / TCP(sport=src_port,dport=dst_port,flags='S'),timeout=1) #flags='S' indicates a SYN request
if str(type(resp)) == "<class 'NoneType'>":
print("The port %s is Closed" %(dst_port))
elif (resp.haslayer(TCP)):
if resp.getlayer(TCP).flags == 'SA':
seq1 = resp.ack
ack1 = resp.seq+1
pkt = IP(dst=dst_ip) / TCP(sport=src_port,dport=dst_port,flags='A')
send(pkt) #Only send but not receive
print("The port %s is Open" %(dst_port))
elif resp.getlayer(TCP).flags == '0X14':
print("The port %s is Closed" %(dst_port))
Port scanning based on TCP half open
Normal TCP requires three connections, but our purpose is port scanning. As long as we receive SYN+ACK packets, the ack of the third handshake is unnecessary.
Specific process: we send SYN connection request. After receiving SYN+ACK packet, we don't really need to establish a connection with it, so we send RST packet (we don't need to send it ourselves or not). In this way, we don't really establish a connection, so it's called half open.
code implementation
from scapy.all import *
from scapy.layers.inet import IP, TCP
dst_ip = "192.168.1.1"
src_port = RandShort()
dst_port= 1900
pkt= IP(dst=dst_ip)/TCP(sport=src_port,dport=dst_port,flags="S")
resp=sr1(pkt,timeout=1)
if(str(type(resp))=="<class 'NoneType'>"):
print("The port %s is Closed" %( dst_port))
elif (resp.haslayer(TCP)):
if(resp.getlayer(TCP).flags == 0x12):
print("The port %s is Open" %( dst_port))
elif (resp.getlayer(TCP).flags == 0x14):
print("The port %s is Closed" %( dst_port))