Information collection_ CDN bypass
What is CDN? Why bypass?
The full name of CDN is content delivery network. Its purpose is to enable users to get the requested data more quickly.
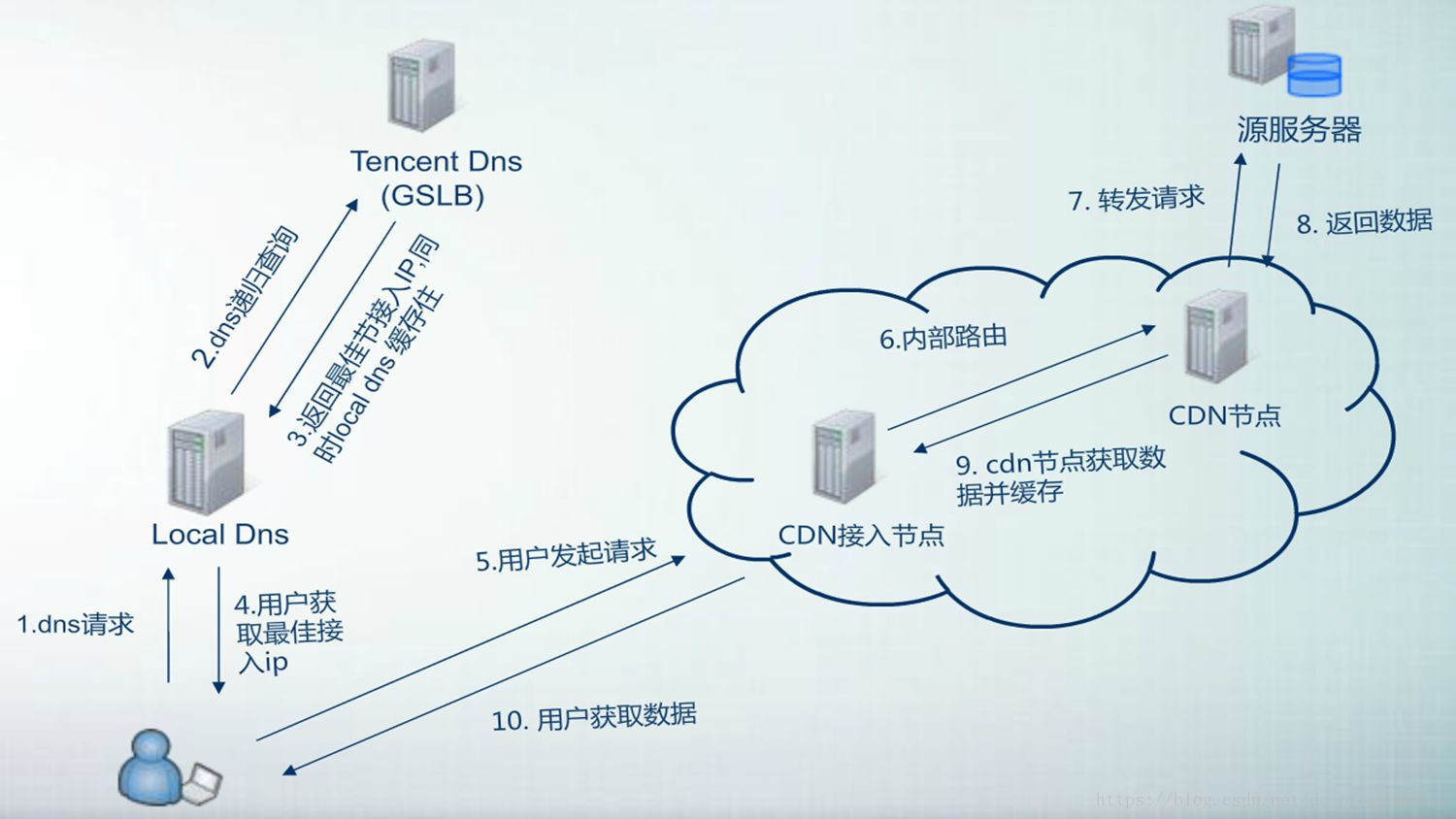
I found a picture on the Internet. Take Tencent as an example. Users want to visit Tencent's official website to rush QB. First, computers want to know which ip to request (the communication between computers depends on ip rather than url), so they need DNS to request to convert the domain name into ip. First, the LDNS local DNS server is requested (the local cache is ignored here). LDNS checks whether there is a response record in the local cache. If there is, it directly returns the ip. If not, it sends the domain name resolution request to Tencent DNS scheduling system and returns the best node ip address assigned by the scheduling system to the user, At the same time, the best node ip domain name records are also cached to the local DNS server. At this time, the user initiates a request not to Tencent's own server, but to a CDN.
Static data resources frequently accessed by users (such as html, css, js, pictures and other files) are directly cached on a CDN node. When users need some data or perform some logical operations, they will be forwarded to the real server. Visiting a website does not need to be loaded for a long time, which greatly improves the speed of entering the QB website.
Therefore, if the real server and CDN are not distinguished, subsequent penetration tests will be all tested on the CDN server!!! At the same time, pay attention not to conduct DDOS attacks after finding the real ip of the target, and do not try to attack the high-risk ports they open
How to determine whether there is a CDN?
Mode 1 http://ping.chinaz.com Conduct multiple ping detection at the webmaster's house
Here are two examples: www.cuit.com edu. cn,www.jd.com
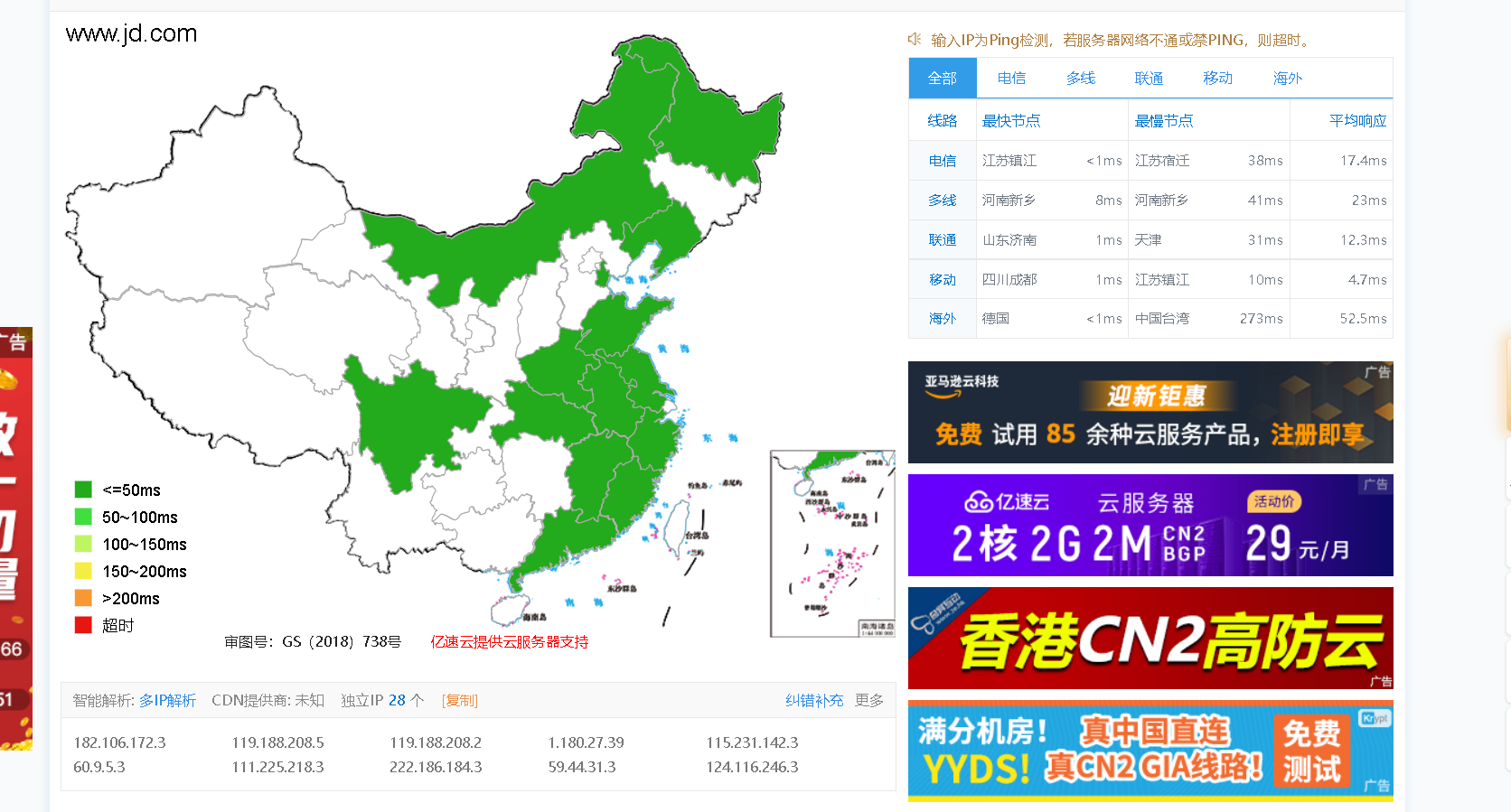
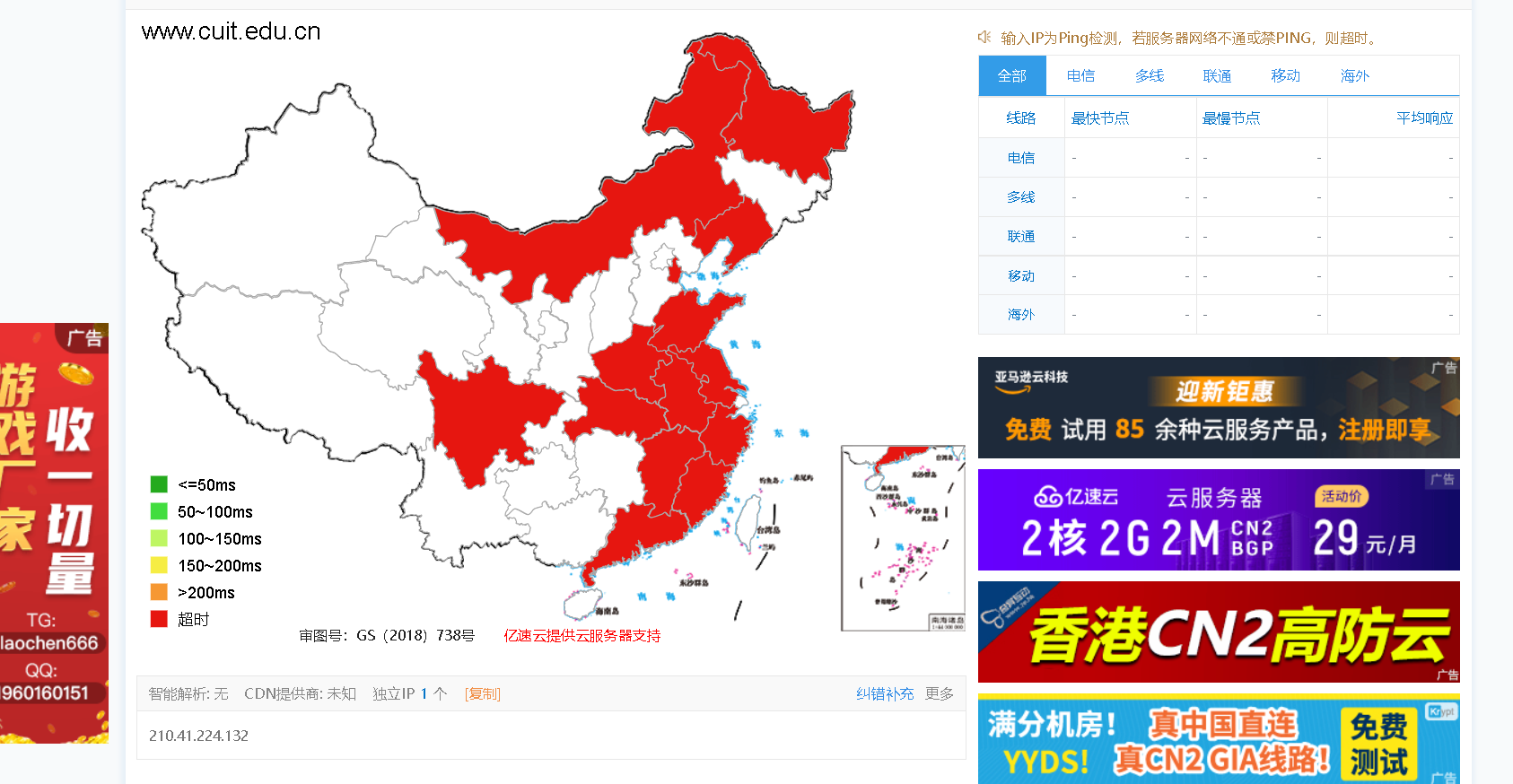
The above two results are obvious edu. Cn has no CDN, and Jingdong has a large green area with CDN
Principle: the main purpose of CDN is to distribute content to the network, so if the target website uses CDN, the ip obtained by ping ing the website domain name in different geographical locations must be different!!!
Method 2: nslookup
beginner@beginner-virtual-machine:~$ nslookup www.cuit.edu.cn Server: 127.0.0.53 Address: 127.0.0.53#53 Non-authoritative answer: Name: www.cuit.edu.cn Address: 210.41.224.132 Name: www.cuit.edu.cn Address: 2001:250:2004:224::132 ======================================================================================= beginner@beginner-virtual-machine:~$ nslookup www.jd.com Server: 127.0.0.53 Address: 127.0.0.53#53 Non-authoritative answer: www.jd.com canonical name = www.jd.com.gslb.qianxun.com. www.jd.com.gslb.qianxun.com canonical name = www.jdcdn.com. www.jdcdn.com canonical name = img20.360buyimg.com.s.galileo.jcloud-cdn.com. img20.360buyimg.com.s.galileo.jcloud-cdn.com canonical name = img2x-sched.jcloud-cdn.com. Name: img2x-sched.jcloud-cdn.com Address: 60.9.5.3
The school website nslookup is very direct without CDN; The following results of JD -- > jcloud CDN
Methods of bypassing CDN
Method 1: through email
If the target website has a mailbox service and the website actively sends us an email, we are likely to know the real server ip (in most cases, the mail service system is deployed in the company without CDN). We can obtain the server ip by viewing the original version of the email. (when you register or change your password, many websites will send e-mail! Of course, in addition to this situation, there are other cases that take the initiative to send e-mail to us)
When we reset our password, Netease will send us an email and export the email to view the original version
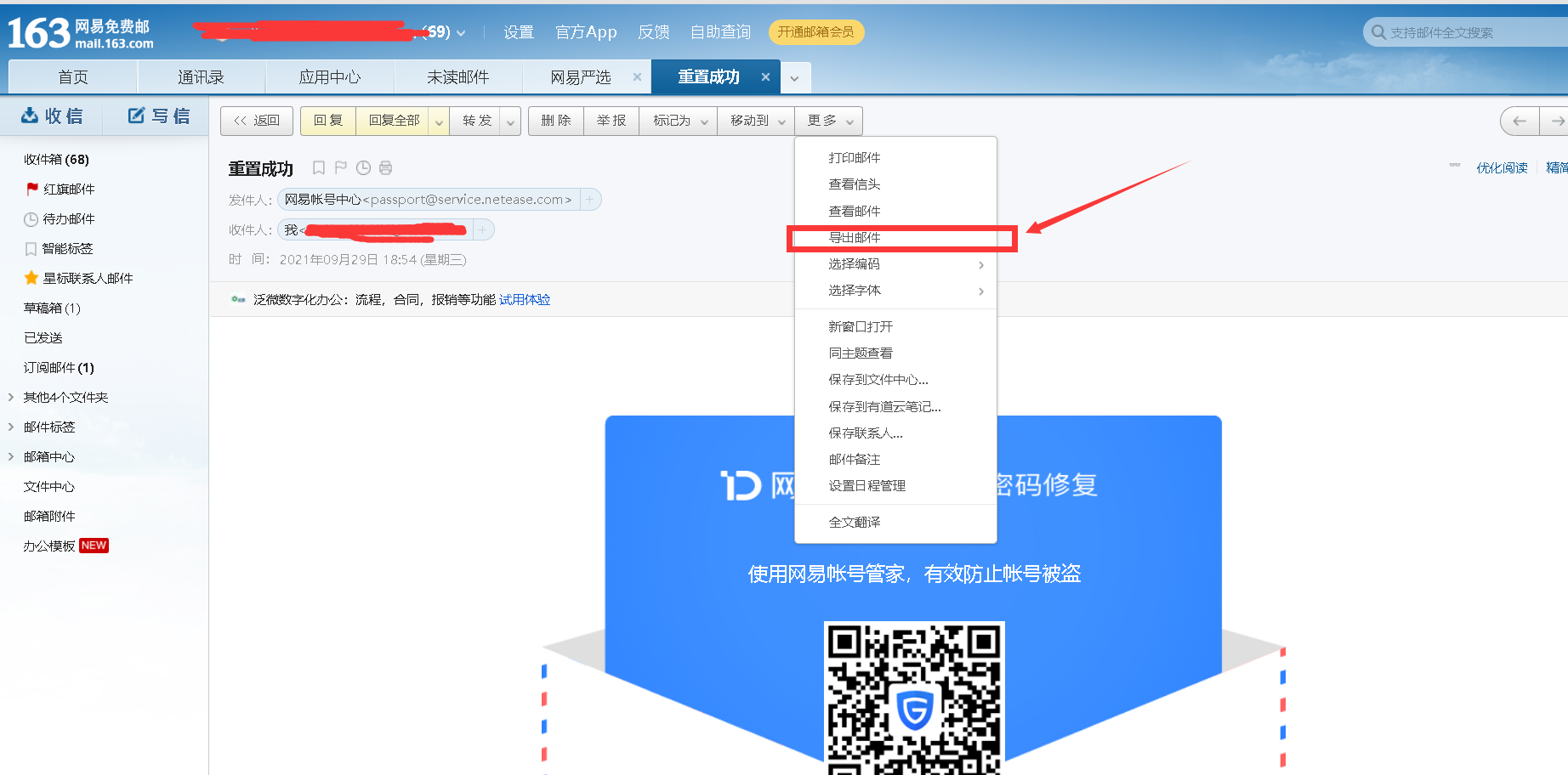
The following is the content of the exported file. The first line contains the ip information of the server
Received: from urs-virt7-mail-server1.dg.163.org (unknown [59.111.178.141]) by trans1 (Coremail) with SMTP id gMCowADn83niRVRhC9uCEA--.26066S2; Wed, 29 Sep 2021 18:54:26 +0800 (CST) From: =?gb2312?B?zfjS19XKusXW0NDEIA==?= <passport@service.netease.com> To: $$$$$$$$$$ Message-ID: <1696392617.20477267.1632912866976.JavaMail.appuser@urs-virt7-mail-server1.dg.163.org> Subject: =?gb2312?B?1tjWw7PJuaY=?= MIME-Version: 1.0 Content-Type: text/html;charset=UTF-8 Content-Transfer-Encoding: quoted-printable X-Netease-Folder: INBOX X-CM-TRANSID:gMCowADn83niRVRhC9uCEA--.26066S2 X-Coremail-Antispam: 1Uf129KBjDUn29KB7ZKAUJUUUb5529EdanIXcx71UUUUU7v73 VFW2AGmfu7bjvjm3AaLaJ3UbIYCTnIWIevJa73UjIFyTuYvjxUk4SrUUUUU X-Originating-IP: [59.111.178.141] Date: Wed, 29 Sep 2021 18:54:26 +0800 (CST) slightly......
If you often use qq mailbox to view the mail source file, it will be easier. Then take steam as an example
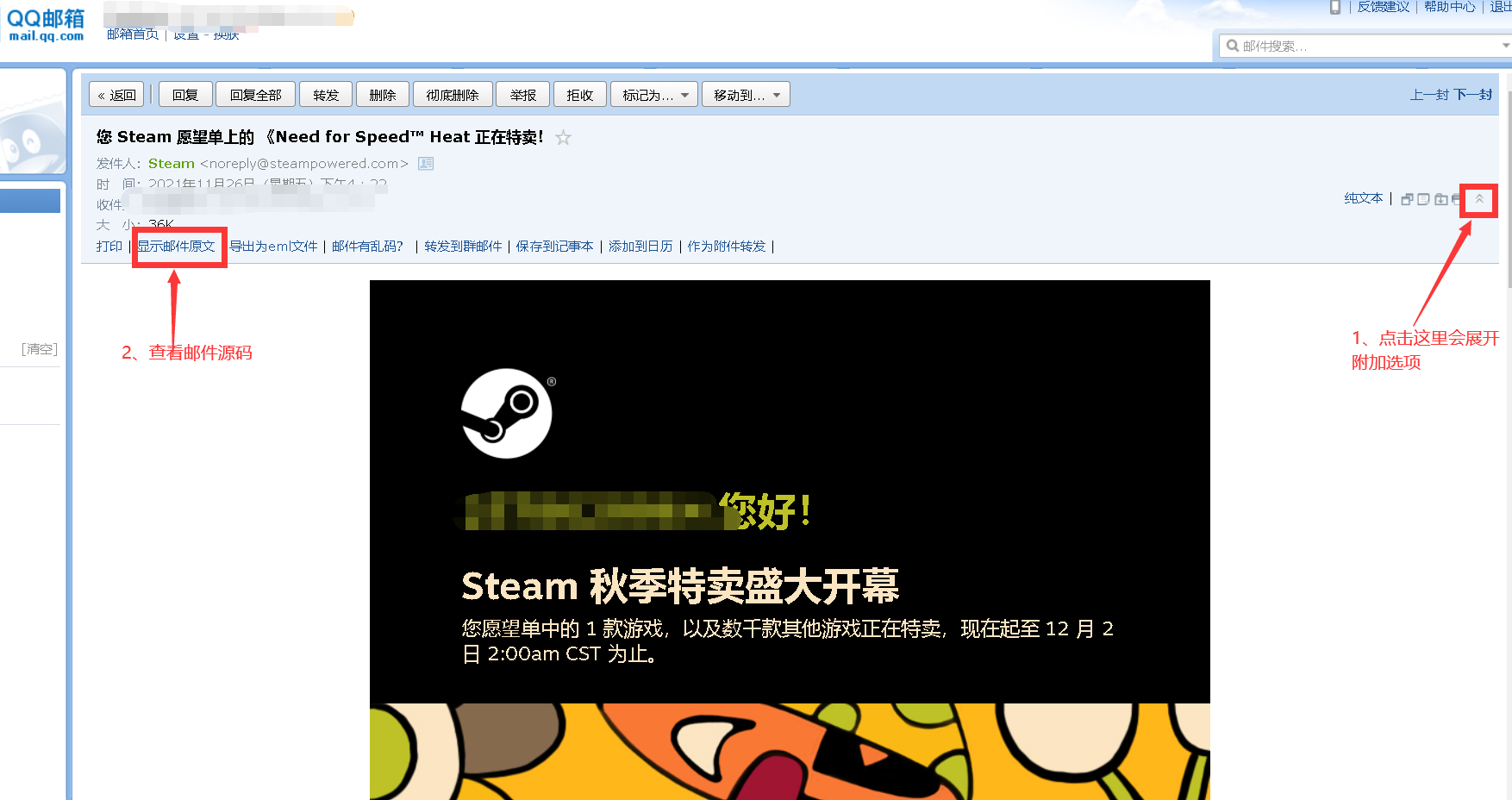
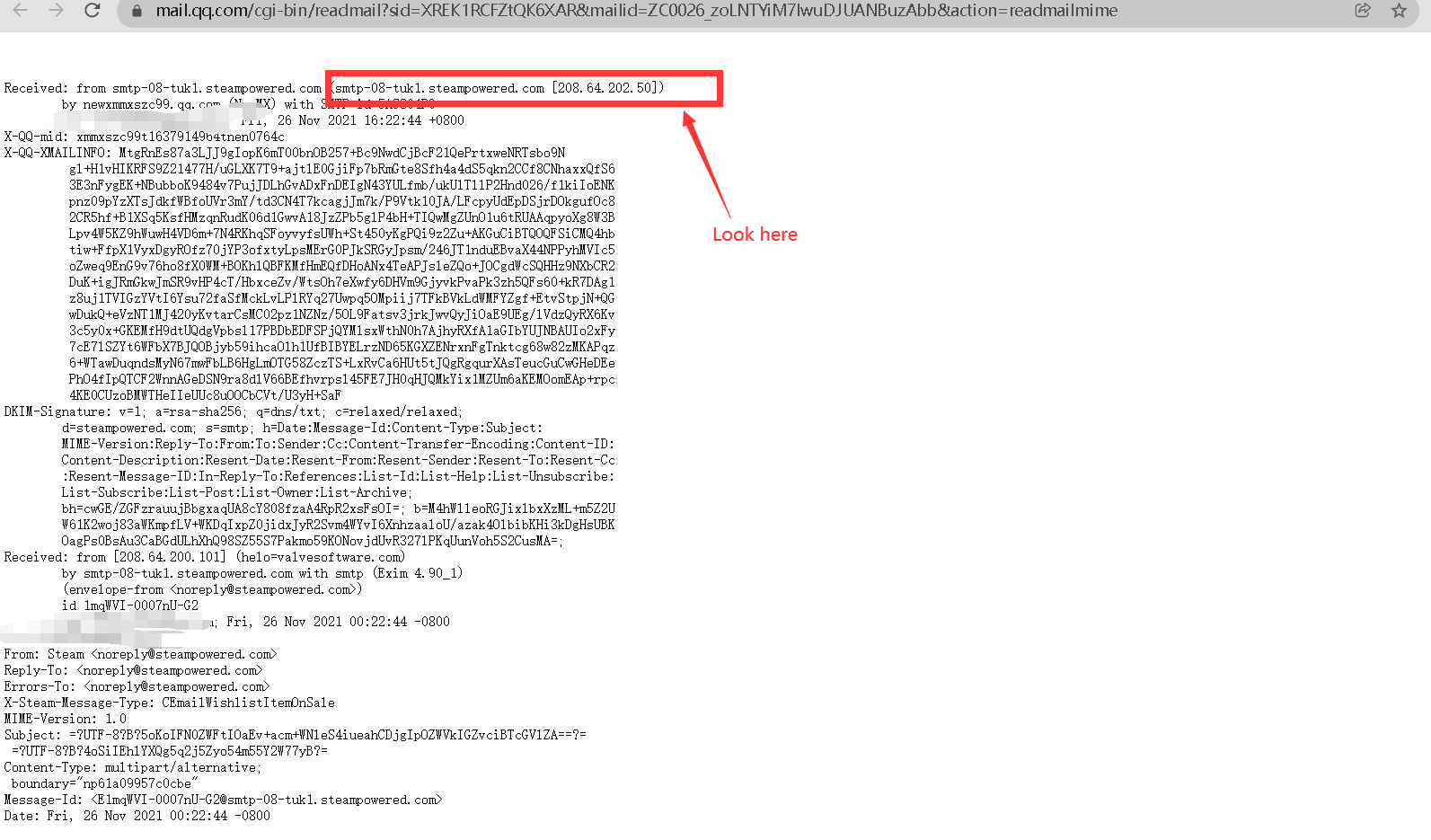
Method 2: check sub domain name
CDN is not cheap. Only the main station (www.xxx.com) and the sub station with large traffic (hub.xxx.com) of the target website may buy CDN. Many small stations (mail.xxx.com) and the former may be distributed in the same machine or segment C. in this way, we may guess the real ip of the website
-
Google, Baidu and Bing can all be found
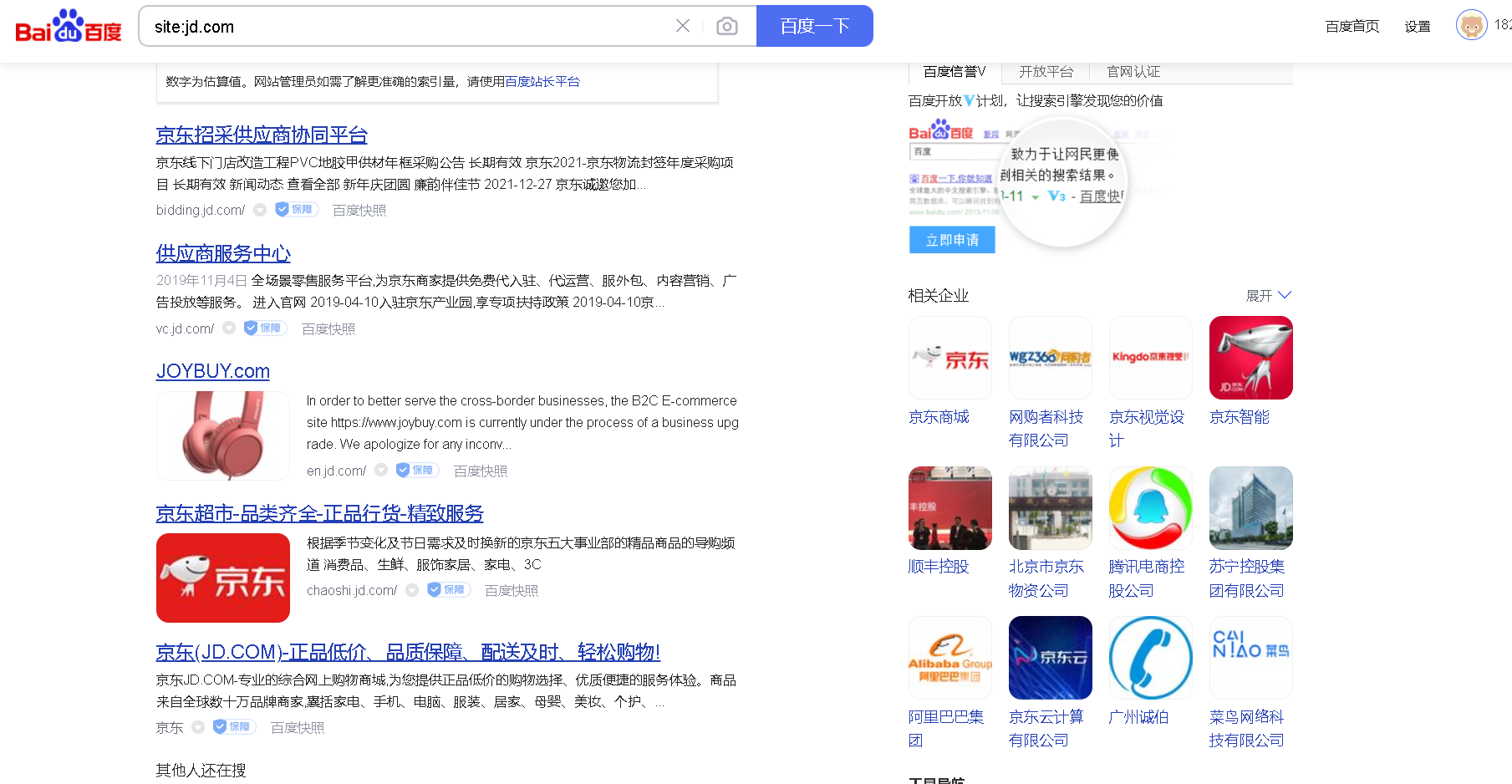
- For example, sub domain name excavator, sub domain name searcher and other tools search
Take Netease as an example, first through Baidu site: 163 Then find the one that looks unpopular and give it to. Www. 68mn http://ping.chinaz.com To determine whether there is a CDN, after screening, it may be inferred that 53.111.0.0/16 may be part of Netease's intranet
jubao.aq.163.com 59.111.160.194 8.163.com 59.111.18.135 wowui.w.163.com 42.186.69.197 campus.163.com 59.111.160.244
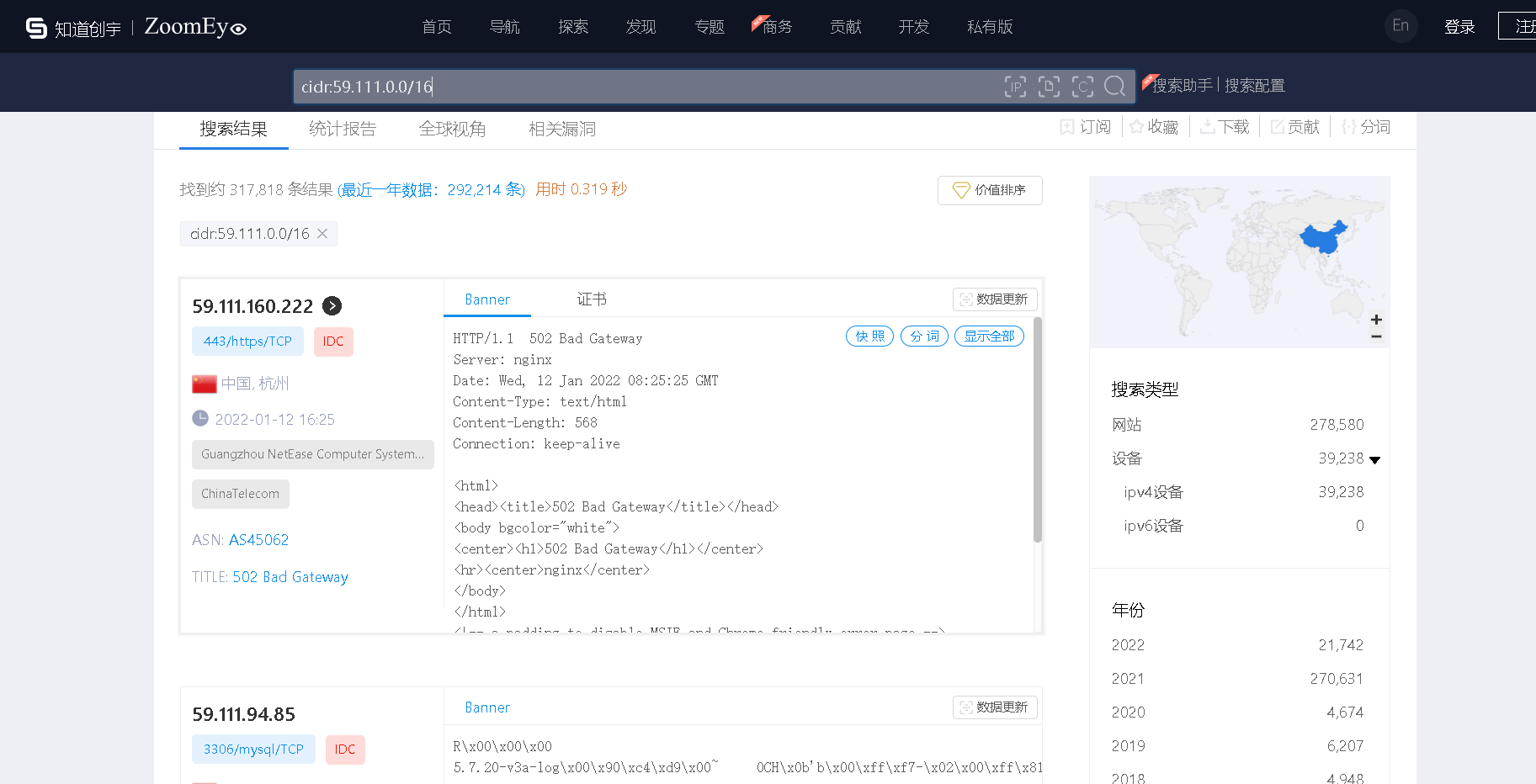
Then Zhong Kui's eyes judged and found that a large number of ip have words such as Netease and 163 ok~~~
Method 3: view the history of domain name resolution
When the domain name of the target website is used for a long time, and the CDN binding service may not be used when the target website first appears, there may be a real ip address in the historical resolution record of the DNS server
http://viewdns.info/iphistory/
Method 4 resolves the domain name through the historical NS server
NS (Name Server) record is a domain Name Server record, which is used to specify which DNS server resolves the domain name
https://whoisrequest.com/history/
Method 5 use shodan
You need to log in here to filter and search. We won't log in here
shodan common syntax
hostname: Search for the specified host or domain name. For example, hostname:"google" port: Search for the specified port or service. For example, port:"21" country: Search for the specified country. For example, country:"CN" city: Search the specified city. For example, city:"Hefei" org: Search for the specified organization or company. For example, org:"google" isp: Search for the specified ISP supplier. For example, isp:"China Telecom" product: Search for the specified operating system/Software/Platform. For example, product:"Apache httpd" version: Search for the specified software version. For example, version:"1.6.2" geo: Search for the specified geographic location with latitude and longitude as the parameter. For example, geo:"31.8639,117.2808" before/after: Search the data before and after the specified collection time in the format of dd-mm-yy. For example, before:"11-09-19" net: Search for the specified IP Address or subnet. For example, net:"210.45.240.0/24"