1. Preface
When it comes to remote desktop, you may think of third-party software such as TeamViewer and sunflower
However, most of them are commercial software, which is expensive; Even if the free version is provided, there are various restrictions, and the stability and security cannot be guaranteed
This article will introduce how to use Intranet penetration 」 Remote desktop management
2. Intranet penetration Frp
Common solutions for intranet penetration include Frp, Ngrok and natapp
Among them, Frp is an open source, simple and easy-to-use, high-performance reverse agent software
It supports TCP, UDP, HTTP and HTTPS Other protocol types
Official address: https://github.com/fatedier/frp
3. Operation steps
Take Frp intranet penetration as an example to realize remote desktop access
3-1 Deploy Frp server to ECS
According to the system platform, download the Frp source code from the following link and upload it to the ECS
https://github.com/fatedier/frp/releases
Of course, it can also be downloaded directly through the wget command
# Download version 0.37.1 using the wget command wget https://github.com/fatedier/frp/releases/download/v0.37.1/frp_0.37.1_linux_amd64.tar.gz
Next, unzip the file package
# Unzip file tar -zxvf frp_0.37.1_linux_amd64.tar.gz
Then, use vi/vim to edit the Frp server configuration file frps.ini 」
among
-
bind_port is used to specify the port number of the Frp server
-
dashboard_user, dashboard_pwd and dashboard_port are used to configure the account information and access port number of Frp background management respectively
# frps.ini [common] bind_addr = 0.0.0.0 bind_port = 7777 token = 12345678 # Authorization code # Configure frp background management account dashboard_user = admin dashboard_pwd = admin dashboard_port = 8888 enable_prometheus = true # Configure log configuration folder log_file = /var/log/frps.log log_level = info log_max_days = 3
Finally, open the ECS firewall port, configure security group rules, and run the Frp service
# Open firewall port number, configure security group rules # 7777 and 8888 port numbers are configured here # Configure services mkdir -p /etc/frp cp frps.ini /etc/frp cp frps /usr/bin cp systemd/frps.service /usr/lib/a # Start frps service systemctl enable frps systemctl start frps
3-2 Access Frp background management
Open the browser, access the ip address of ECS + the port number "8888" specified above, and enter the user name and password above to enter the Frp background management interface
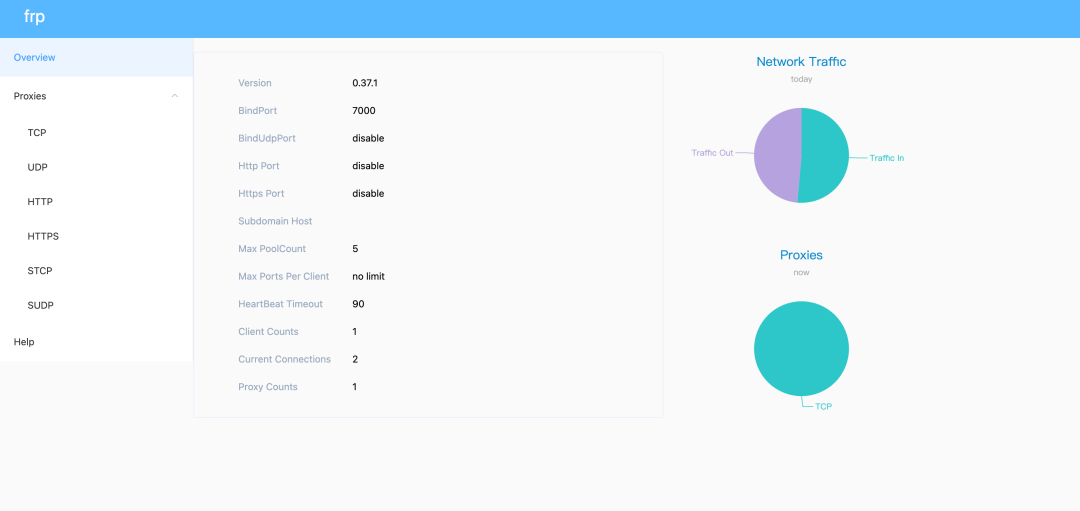
The management interface can view the running status and agent statistics of Frp in real time
3-3 Deploy Frp client to target computer
PS: since the target computer is windows, you need to download the Windows version of Frp first Source code
First, modify the client configuration file frpc.ini 」
# Configure Frp client information # frpc.ini [common] server_addr = frp Public network ip address #frp service public network ip address server_port = 7777 # The port number specified in frps.ini token = 12345678 # Consistent with the token in frps.ini [ssh] type = tcp # communication mode local_ip = 127.0.0.1 local_port = 3389 # The default port for remote access service is 3389 remote_port = 6000 # Define the remote port to point to the local 3389 port through 6000
Then, run the Frp client using the following command in CMD
# Running the frp client frpc -c frpc.ini
Finally, refresh the Frp Dashboard management page to observe the connection information of the Frp client
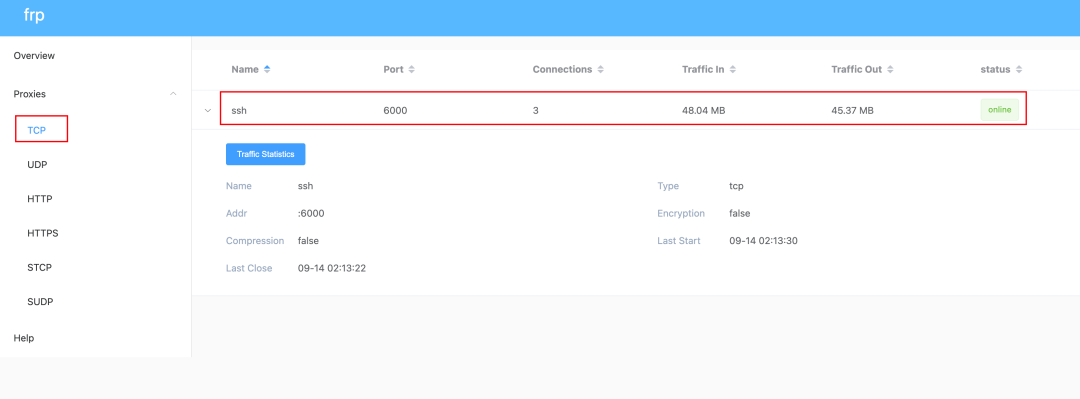
3-4 Target computer startup - winsw
To ensure that the target computer is permanently online, you can use winsw 」 Configure the client connection as a service and configure it to start automatically
Project download address: https://github.com/winsw/winsw/releases
The configuration steps are as follows:
-
Download the corresponding source code according to the system version, unzip it and place it in the same level directory of Frp
-
Modify the executable name to winsw.exe
-
Create a new profile winsw.xml, add and run Frp Client commands
The configuration information is as follows:
# winsw.xml<service> <id>frp</id> <name>frp</name> <description>frp Remote control client service</description> <executable>frpc</executable> <arguments>-c frpc.ini</arguments> <logmode>reset</logmode> </service>
Finally, open the CMD terminal as an administrator and run the following command, so that the Frp client can become a system service and run in the background
# Run as Administrator winsw install winsw start
3-5 Remote desktop access
Through ECS ip+ The remote access port number specified by the client allows remote desktop control of the target computer
Assume that the ECS ip is "*. *. *."* 」, The remote port number specified in the Frp client configuration file is 6000
Just use the command mstsc 」 Enter the remote desktop window, enter "*. *. *: 6000" and enter the user name and password of the target computer to remotely control the target computer
Of course, you can also use mobile App, such as " RD Client 」 To control remote desktop
4. Finally
The remote desktop control is realized through Frp intranet penetration. The actual use experience is really not too good
In fact, the purpose of Intranet penetration is far more than that. You can consult the data to expand it by yourself
If you think the article is good, please Like, share and leave messages Next, because this will be the strongest driving force for me to continue to output more high-quality articles!