1, NoSQL
1.1 overview
Relational database: a database created based on a relational model. The so-called relationship model is "one to one, one to many, many to many".
NoSQL = Not Only SQL, meaning: not just SQL; Generally refers to non relational database.
Non relational database:
- A column of data is stored in the model. The relational database takes a row as a record, and the column model database takes a column as a record. (in this model, data is index, and IO is fast, mainly distributed databases)
- Key value pair model: the stored data is "key value pairs", such as name:liming, so the value stored in the name key is Liming
- Document type model: store data in documents one by one, which is somewhat similar to "key value pairs"
Many data types include users' personal information, social networks and geographical locations. The storage of these data types can be expanded horizontally without a fixed format and redundant operations.
The generation of NoSQL database is to solve the challenges brought by large-scale data collection and various data types, especially the problems of big data application, including the storage of large-scale data.
1.2 NoSQL features
- Easy to expand: there is no relationship between data and it is easy to expand
- Large amount of data and high performance: Redis can write 80000 times and read 110000 times a second. Thanks to its non relational nature, the structure of the database is simple. NoSQL's cache is record level, which is a fine-grained cache with high performance.
- Diverse and flexible data models: you can store customized data formats at any time without designing the database in advance. In relational database, it is very troublesome to add and delete fields in tables with large amount of data
- Traditional RDBMS and NoSQL
Traditional relational database RDBMS - Highly organized structured data - Structured query language( SQL) - Data and relationships are stored in separate tables - Data manipulation language - Strict consistency - Basic transaction NoSQL - Represents more than just SQL - No declarative query language - There are no predefined patterns - Key value pair storage, column storage, document storage, graphic database - Final consistency, not ACID attribute - Unstructured and unpredictable data - CAP theorem - High performance, high availability and scalability
1.3. 3V+3 high
3V in the era of big data: it mainly describes the problem
- Massive Volume
- Diversity
- Real time Velocity
Three high demands of the Internet: mainly the requirements for procedures
- High concurrency
- High availability
- High performance
1.4 four categories of NoSQL
KV key value:
- Sina: BerkeleyDB+redis
- Meituan: redis + tail
- Alibaba, baidu: memcache+redis
Document database (there are many bson formats, the same as json):
- CouchDB
- MongoDB
- Is a database based on distributed file storage, written in C + +
- It is mainly used to process a large number of documents
- MongoDB is a product between relational database and non relational database
- It is the most functional non relational database and most like relational database
Column storage database:
- Cassandra, HBase
- distributed file system
Figure relational database:
- It doesn't put graphics, but relationships, such as circle of friends, social networks and advertising recommendation system
- Social networks, recommendation systems, etc. Focus on building relationship maps
- Neo4J, InfoGrid
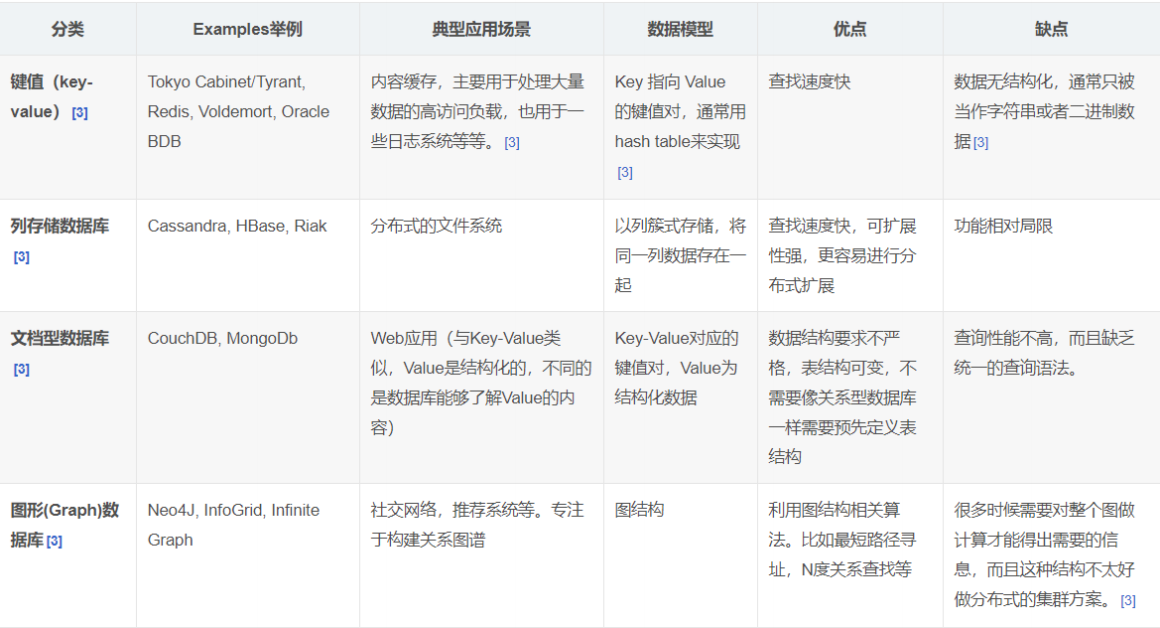
Comparison of the four:
2, Getting started with Redis
2.1 overview
Redis: REmote DIctionary Server
It is an open source, written in C language, supports network, can be based on memory or persistent daily execution, key value database, and provides multi language API.
Redis and other key value caching products have the following three characteristics:
- Redis supports data persistence. It can keep the data in memory on disk and can be loaded again for use when restarting.
- Redis not only supports simple key value data, but also provides storage of list, set, zset, hash and other data structures.
- Redis supports data backup, that is, data backup in master slave mode.
Redis function:
- Memory storage and persistence: redis supports writing data in memory to the hard disk asynchronously without affecting the continuous service (rdb, aof)
- High efficiency and can be used for caching
- Publish and subscribe message system
- Map information analysis
- Timer, counter
Redis features:
- Data type, basic operation and configuration
- Persistence and replication, RDB, AOF
- Transaction control
2.2 installation
2.2.1 Windows installation
Download address: https://github.com/dmajkic/redis/downloads
Just unzip the compressed package
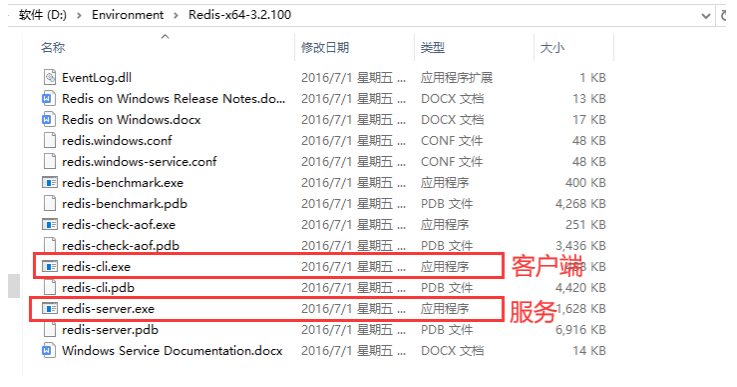
Double click redis server Exe to start
Access through the client
2.2.2 Linux Installation
Download address http://download.redis.io/releases
-
Download redis-5.0.7 tar. GZ and put it in the Linux directory / opt
-
/Under the opt directory, unzip the command: tar -zxvf redis-5.0.7 tar. gz
-
After decompression, the following folder appears: redis-5.0.7
-
Enter the directory: cd redis-5.0.7
-
Execute the make command in the redis-5.0.7 directory
function make Error parsing command: 1. install gcc (gcc yes linux The next compiler is c Compiler tool for program) Internet access: yum install gcc-c++ Version test: gcc-v 2. secondary make 3. Jemalloc/jemalloc.h: There is no such file or directory function make distclean Later make 4. Redis Test((no need to execute) -
After making, continue to execute make install
-
View the default installation directory: usr/local/bin
/usr This is a very important directory, similar to windows Lower Program Files,Store user's program
-
Copy profile
cd /usr/local/bin ll # Back up redis.com in the decompression directory of redis conf mkdir config cp redis.conf config# Copy a backup and form a good habit, so we can modify this file # Modify the configuration to ensure that it can be applied in the background vim redis.conf
Daemon set yes or no difference
daemonize:yes
Redis adopts the mode of single process and multithreading. When redis When the option Daemon in conf is set to yes, it means that the daemon mode is turned on. In this mode, redis will run in the background and write the process pid number to redis The conf option is in the file set by pidfile. At this time, redis will always run unless you manually kill the process.
daemonize:no
When the daemon option is set to no, the current interface will enter the redis command line interface. Forced exit or closing the connection tools (putty,xshell, etc.) will cause the redis process to exit. -
test
# [shell] start redis service [root@192 bin]# cd /usr/local/bin [root@192 bin]# redis-server /opt/redis-5.0.7/redis.conf # Redis client connection = = = > observe the change of address. If the connection is ok, it is connected directly. The default port number of redis is 6379 [root@192 bin]# redis-cli -p 6379 127.0.0.1:6379> ping PONG 127.0.0.1:6379> shutdown # Close connection
2.3 performance test
**Redis benchmark: * * is an official built-in stress testing tool
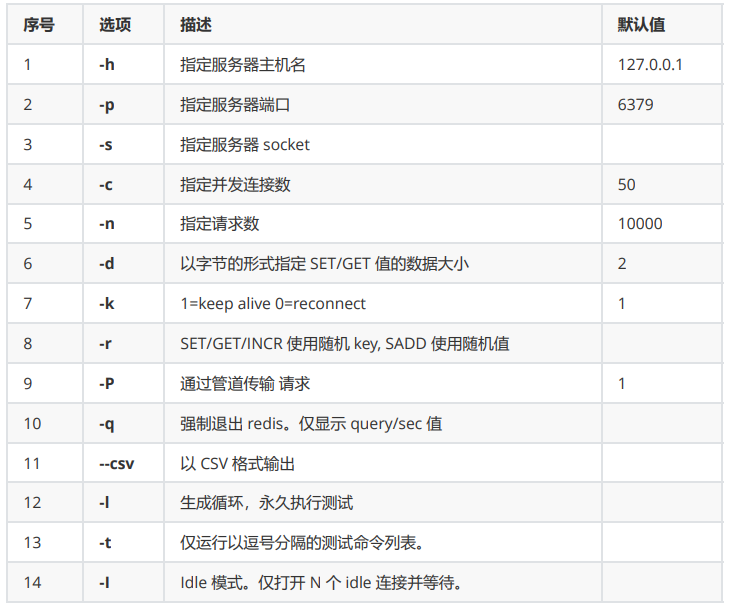
Optional parameters for performance test:
# Test 1: 100 concurrent connections and 100000 requests. Test the performance of redis server with local host and 6379 port
redis-benchmark -h localhost -p 6379 -c 100 -n 100000
====== SET ======
100000 requests completed in 1.88 seconds # Write test to collection
100 parallel clients # There are 100 concurrent clients per request
3 bytes payload # Write 3 bytes of data at a time, payload
keep alive: 1 # Maintain a connection and a server to process these requests
17.05% <= 1 milliseconds
97.35% <= 2 milliseconds
99.97% <= 3 milliseconds
100.00% <= 3 milliseconds # All requests completed in 3 milliseconds
53248.14 requests per second # 53248.14 requests processed per second
2.4 basic knowledge description
redis has 16 databases by default, and the 0 database is used by default
You can use select to switch databases
127.0.0.1:6379> select 7 OK 127.0.0.1:6379[7]> # Different libraries can store different data # Dbsize view the number of key s in the current database 127.0.0.1:6379[7]> DBSIZE (integer) 0 # View specific key s 127.0.0.1:6379> keys * 127.0.0.1:6379> flushdb # Empty current library 127.0.0.1:6379> flushall # Empty all libraries
redis is single threaded:
Redis is fast. Officials say that redis is based on memory operation, and CPU is not the performance bottleneck of redis. The performance bottleneck of redis is based on the memory and network bandwidth of the machine. Since it can be implemented with single thread, single thread is used.
Reasons for Redis single thread speed:
- Myth: high performance servers must be multithreaded, and multithreading must be more efficient than single thread
- redis core: put all data in memory, so using single thread to operate is the most efficient. Multithreading (CPU context switching, which takes time). For memory systems, if there is no context switching, the efficiency is the highest. Multiple reads and writes are on the same CPU, but in the case of memory, this is the best solution
3, Five data types
3.1,Redis-key
127.0.0.1:6379> set age 1 # Store key value pairs OK 127.0.0.1:6379> get age # Get value "1" 127.0.0.1:6379> EXISTS age # Determine whether the key exists (integer) 1 127.0.0.1:6379> move age 1 # Remove key value pairs from the current database (integer) 1 127.0.0.1:6379> EXPIRE age 10 # Set the default expiration time in seconds (integer) 1 127.0.0.1:6379> ttl age # View the remaining time of the current key, - 1 means it will never expire, - 2 means it has expired (integer) 7 127.0.0.1:6379> type name # View the type of current key string
3.2. String
Single value
# =================================================== # set,get,del,append,strlen # =================================================== 127.0.0.1:6379> set key1 value1 # Set value OK 127.0.0.1:6379> get key1 # Get key "value1" 127.0.0.1:6379> del key1 # Delete key (integer) 1 127.0.0.1:6379> keys * # View all key s (empty list or set) 127.0.0.1:6379> exists key1 # Make sure key1 does not exist (integer) 0 127.0.0.1:6379> append key1 "hello" # Does not exist for pend, which is equivalent to SET key1 "hello" (integer) 5 # Character length 127.0.0.1:6379> APPEND key1 "-2333" # APPEND an existing string (integer) 10 # Length increased from 5 to 10 characters 127.0.0.1:6379> get key1 "hello-2333" 127.0.0.1:6379> STRLEN key1 # # Gets the length of the string (integer) 10 # =================================================== # incr and decr must be numbers to add or subtract, + 1 and - 1. # The incrby and decrby commands add the specified increment value to the number stored in the key. # =================================================== 127.0.0.1:6379> set views 0 # Set the number of views to 0 OK 127.0.0.1:6379> incr views # Browse + 1 (integer) 1 127.0.0.1:6379> incr views # Browse + 1 (integer) 2 127.0.0.1:6379> decr views # Browse - 1 (integer) 1 127.0.0.1:6379> incrby views 10 # +10 (integer) 11 127.0.0.1:6379> decrby views 10 # -10 (integer) 1 # =================================================== # getrange gets the value within the specified range, similar to substring. From zero to negative one represents all # =================================================== 127.0.0.1:6379> set key2 abcd123456 # Set the value of key2 OK 127.0.0.1:6379> getrange key2 0 -1 # Get all values "abcd123456" 127.0.0.1:6379> getrange key2 0 2 # Intercept part of string "abc" # =================================================== # Setrange sets the string starting at the specified position. The format is setrange key value and the specific value # =================================================== 127.0.0.1:6379> get key2 "abcd123456" 127.0.0.1:6379> SETRANGE key2 1 xx # Replace value (integer) 10 127.0.0.1:6379> get key2 "axxd123456" # =================================================== # setex (set with expire) key second value # setnx(set if not exist) # =================================================== 127.0.0.1:6379> setex key3 60 expire # Set expiration time OK 127.0.0.1:6379> ttl key3 # View remaining time (integer) 55 127.0.0.1:6379> setnx mykey "redis" # If it does not exist, it will be set, and 1 will be returned successfully (integer) 1 127.0.0.1:6379> setnx mykey "mongodb" # If it does not exist, set it. Otherwise, 0 will be returned if it fails (integer) 0 127.0.0.1:6379> get mykey "redis" # =================================================== # mset is used to set one or more key value pairs at the same time. # mget returns the values of all (one or more) given key s. # If a given key does not exist, the key returns the special value nil. # msetnx returns 1 when all key s are set successfully. # If all given keys fail to be set (at least one key already exists), 0 is returned. Atomic operation # =================================================== 127.0.0.1:6379> mset k10 v10 k11 v11 k12 v12 OK 127.0.0.1:6379> keys * 1) "k12" 2) "k11" 3) "k10" 127.0.0.1:6379> mget k10 k11 k12 k13 1) "v10" 2) "v11" 3) "v12" 4) (nil) 127.0.0.1:6379> msetnx k10 v10 k15 v15 # Atomic operation! (integer) 0 127.0.0.1:6379> get key15 (nil) # Traditional object cache set user:1 value(json data) # Can be used to cache objects mset user:1:name zhangsan user:1:age 2 mget user:1:name user:1:age # =================================================== # getset (get before set) # =================================================== 127.0.0.1:6379> getset db mongodb # No old value, return nil (nil) 127.0.0.1:6379> get db "mongodb" 127.0.0.1:6379> getset db redis # Return old value mongodb "mongodb" 127.0.0.1:6379> get db "redis"
String data structure is a simple key value type. In fact, value can be not only string, but also number.
General key value cache application:
Regular count: number of microblogs, fans, etc.
3.3. List
Single Value multi Value
In redis, the list can be made into stack, queue and blocking queue
All list commands start with l
# =================================================== # Lpush: inserts one or more values into the list header. (left) # rpush: inserts one or more values at the end of the list. (right) # lrange: returns the elements within the specified interval in the list. The interval is specified by offset START and END. # Where 0 represents the first element of the list, 1 represents the second element of the list, and so on. # You can also use negative subscripts, with - 1 for the last element of the list, - 2 for the penultimate element of the list, and so on. # =================================================== 127.0.0.1:6379> LPUSH list "one" (integer) 1 127.0.0.1:6379> LPUSH list "two" (integer) 2 127.0.0.1:6379> RPUSH list "right" (integer) 3 127.0.0.1:6379> Lrange list 0 -1 1) "two" 2) "one" 3) "right" 127.0.0.1:6379> Lrange list 0 1 1) "two" 2) "one" # =================================================== # The lpop command removes and returns the first element of the list. When the list key does not exist, nil is returned. # rpop removes the last element of the list, and the return value is the removed element. # =================================================== 127.0.0.1:6379> Lpop list "two" 127.0.0.1:6379> Rpop list "right" 127.0.0.1:6379> Lrange list 0 -1 1) "one" # =================================================== # Lindex, get the element according to the index subscript (- 1 for the last, 0 for the first) # =================================================== 127.0.0.1:6379> Lindex list 1 (nil) 127.0.0.1:6379> Lindex list 0 "one" 127.0.0.1:6379> Lindex list -1 "one" # =================================================== # llen is used to return the length of the list. # =================================================== 127.0.0.1:6379> flushdb OK 127.0.0.1:6379> Lpush list "one" (integer) 1 127.0.0.1:6379> Lpush list "two" (integer) 2 127.0.0.1:6379> Lpush list "three" (integer) 3 127.0.0.1:6379> Llen list # Returns the length of the list (integer) 3 # =================================================== # lrem key removes the elements in the list equal to the parameter VALUE according to the parameter. # =================================================== 127.0.0.1:6379> lrem list 1 "two" (integer) 1 127.0.0.1:6379> Lrange list 0 -1 1) "three" 2) "one" # =================================================== # Ltrim key trims a list so that only the elements within the specified interval are retained in the list, and the elements not within the specified interval will be deleted. # =================================================== 127.0.0.1:6379> RPUSH mylist "hello" (integer) 1 127.0.0.1:6379> RPUSH mylist "hello" (integer) 2 127.0.0.1:6379> RPUSH mylist "hello2" (integer) 3 127.0.0.1:6379> RPUSH mylist "hello3" (integer) 4 127.0.0.1:6379> ltrim mylist 1 2 OK 127.0.0.1:6379> lrange mylist 0 -1 1) "hello" 2) "hello2" # =================================================== # rpoplpush removes the last element of the list, adds it to another list, and returns. # =================================================== 127.0.0.1:6379> rpush mylist "hello" (integer) 1 127.0.0.1:6379> rpush mylist "foo" (integer) 2 127.0.0.1:6379> rpush mylist "bar" (integer) 3 127.0.0.1:6379> rpoplpush mylist myotherlist "bar" 127.0.0.1:6379> lrange mylist 0 -1 1) "hello" 2) "foo" 127.0.0.1:6379> lrange myotherlist 0 -1 1) "bar" # =================================================== # lset key index value sets the value of the element whose index is the index of the list key to value. # =================================================== 127.0.0.1:6379> exists list # LSET the empty list (key does not exist) (integer) 0 127.0.0.1:6379> lset list 0 item # report errors (error) ERR no such key 127.0.0.1:6379> lpush list "value1" # LSET non empty list (integer) 1 127.0.0.1:6379> lrange list 0 0 1) "value1" 127.0.0.1:6379> lset list 0 "new" # Update value OK 127.0.0.1:6379> lrange list 0 0 1) "new" 127.0.0.1:6379> lset list 1 "new" # Error when index exceeds the range (error) ERR index out of range # =================================================== # linsert key before/after pivot value is used to insert elements before or after the elements in the list. # Insert the value value into the list key, before or after the value pivot. # =================================================== redis> RPUSH mylist "Hello" (integer) 1 redis> RPUSH mylist "World" (integer) 2 redis> LINSERT mylist BEFORE "World" "There" (integer) 3 redis> LRANGE mylist 0 -1 1) "Hello" 2) "There" 3) "World"
Summary:
- It is a string linked list, left and right can be inserted and added
- If the key does not exist, create a new linked list
- If the key already exists, add content
- If all values are removed, the corresponding key disappears
- The operation of the linked list, both head and tail, is highly efficient, but if it is to operate the intermediate elements, the efficiency is very poor.
Using the List structure, we can easily realize the latest news ranking and other functions.
Another application is the message queue. You can use the PUSH operation of the List to store the task in the List, and then the working thread takes out the task for execution with POP operation.
3.4. Set
Single value multi value
# =================================================== # sadd adds one or more member elements to the collection and cannot be repeated # smembers returns all members in the collection. # The sismember command determines whether a member element is a member of a collection. # =================================================== 127.0.0.1:6379> sadd myset "hello" (integer) 1 127.0.0.1:6379> sadd myset "world" (integer) 1 127.0.0.1:6379> sadd myset "world" (integer) 0 127.0.0.1:6379> SMEMBERS myset 1) "world" 2) "hello" 127.0.0.1:6379> SISMEMBER myset "hello" (integer) 1 127.0.0.1:6379> SISMEMBER myset "zhangsan" (integer) 0 # =================================================== # scard, get the number of elements in the collection # =================================================== 127.0.0.1:6379> scard myset (integer) 2 # =================================================== # srem key value is used to remove one or more member elements from the collection # =================================================== 127.0.0.1:6379> srem myset "world" (integer) 1 127.0.0.1:6379> SMEMBERS myset 1) "hello" # =================================================== # The srandmember key command returns a random element in a collection. # =================================================== 127.0.0.1:6379> SMEMBERS myset 1) "zhangsan" 2) "world" 3) "hello" 127.0.0.1:6379> SRANDMEMBER myset "hello" 127.0.0.1:6379> SRANDMEMBER myset 2 1) "world" 2) "zhangsan" 127.0.0.1:6379> SRANDMEMBER myset 2 1) "zhangsan" 2) "hello" # =================================================== # smove SOURCE DESTINATION MEMBER # Moves the specified member element from the source collection to the destination collection. # =================================================== 127.0.0.1:6379> sadd myset "hello" (integer) 1 127.0.0.1:6379> sadd myset "world" (integer) 1 127.0.0.1:6379> sadd myset "zhangsan" (integer) 1 127.0.0.1:6379> sadd myset2 "set2" (integer) 1 127.0.0.1:6379> smove myset myset2 "zhangsan" (integer) 1 127.0.0.1:6379> SMEMBERS myset 1) "world" 2) "hello" 127.0.0.1:6379> SMEMBERS myset2 1) "zhangsan" 2) "set2" # =================================================== # Digital collection class # Difference sets: sdiff # Intersection: sinter # Union: sunion # =================================================== 127.0.0.1:6379> sadd key1 "a" (integer) 1 127.0.0.1:6379> sadd key1 "b" (integer) 1 127.0.0.1:6379> sadd key1 "c" (integer) 1 127.0.0.1:6379> sadd key2 "c" (integer) 1 127.0.0.1:6379> sadd key2 "d" (integer) 1 127.0.0.1:6379> sadd key2 "e" (integer) 1 127.0.0.1:6379> SDIFF key1 key2 # Check the difference set that exists in key1 but does not exist in key2 1) "a" 2) "b" 127.0.0.1:6379> SINTER key1 key2 # Check the intersection of key1 and key2 1) "c" 127.0.0.1:6379> SUNION key1 key2 # key1, key2 merge, union 1) "a" 2) "b" 3) "c" 4) "e" 5) "d"
In the microblog application, all the followers of a user can be stored in a collection, and all their fans can be stored in a collection. Redis also provides intersection, union, difference and other operations for collections, which can easily realize functions such as common concern, common preference, second degree friend and so on.
3.5. Hash
kv mode remains unchanged, but V is a key value pair
# =================================================== # The hset and hget commands are used to assign values to fields in the hash table. # hmset and hmget set multiple field value pairs into the hash table at the same time. The existing fields in the hash table will be overwritten. # hgetall is used to return all fields and values in the hash table. # hdel is used to delete one or more specified fields in the hash table key # =================================================== 127.0.0.1:6379> hset myhash field1 "zhangsan" (integer) 1 127.0.0.1:6379> hget myhash field1 "zhangsan" 127.0.0.1:6379> HMSET myhash field1 "Hello" field2 "World" OK 127.0.0.1:6379> HGET myhash field1 "Hello" 127.0.0.1:6379> HGET myhash field2 "World" 127.0.0.1:6379> hgetall myhash 1) "field1" 2) "Hello" 3) "field2" 4) "World" 127.0.0.1:6379> HDEL myhash field1 (integer) 1 127.0.0.1:6379> hgetall myhash 1) "field2" 2) "World" # =================================================== # hlen gets the number of fields in the hash table. # =================================================== 127.0.0.1:6379> hlen myhash (integer) 1 127.0.0.1:6379> HMSET myhash field1 "Hello" field2 "World" OK 127.0.0.1:6379> hlen myhash (integer) 2 # =================================================== # hexists checks whether the specified field of the hash table exists. # =================================================== 127.0.0.1:6379> hexists myhash field1 (integer) 1 127.0.0.1:6379> hexists myhash field3 (integer) 0 # =================================================== # hkeys gets all field s in the hash table. # hvals returns the values of all fields in the hash table. # =================================================== 127.0.0.1:6379> HKEYS myhash 1) "field2" 2) "field1" 127.0.0.1:6379> HVALS myhash 1) "World" 2) "Hello" # =================================================== # hincrby adds the specified increment value to the field value in the hash table. # =================================================== 127.0.0.1:6379> hset myhash field 5 (integer) 1 127.0.0.1:6379> HINCRBY myhash field 1 (integer) 6 127.0.0.1:6379> HINCRBY myhash field -1 (integer) 5 127.0.0.1:6379> HINCRBY myhash field -10 (integer) -5 # =================================================== # hsetnx assigns values to fields that do not exist in the hash table. # =================================================== 127.0.0.1:6379> HSETNX myhash field1 "hello" (integer) 1 # Set successfully, return 1. 127.0.0.1:6379> HSETNX myhash field1 "world" (integer) 0 # Returns 0 if the given field already exists. 127.0.0.1:6379> HGET myhash field1 "hello"
Redis hash is a mapping table of field and value of string type. Hash is especially suitable for storing objects.
Store partially changed data, such as user information, etc.
3.6 ordered set Zset
Add a score value on the basis of set. Previously, set was k1 v1 v2 v3, and now zset is k1 score1 v1 score2 v2.
# =================================================== # zadd adds one or more member elements and their fractional values to an ordered set. # zrange returns an ordered set of members within a specified interval # =================================================== 127.0.0.1:6379> zadd myset 1 "one" (integer) 1 127.0.0.1:6379> zadd myset 2 "two" 3 "three" (integer) 2 127.0.0.1:6379> ZRANGE myset 0 -1 1) "one" 2) "two" 3) "three" # =================================================== # zrangebyscore returns a list of members of a specified score range in an ordered set. Increment by ordered member (from small to large) Order. # =================================================== 127.0.0.1:6379> zadd salary 2500 xiaoming (integer) 1 127.0.0.1:6379> zadd salary 5000 xiaohong (integer) 1 127.0.0.1:6379> zadd salary 500 zhangsan (integer) 1 # Inf infinity + ∞, similarly, -∞ can be expressed as - inf. 127.0.0.1:6379> ZRANGEBYSCORE salary -inf +inf # Displays the entire ordered set 1) "zhangsan" 2) "xiaoming" 3) "xiaohong" 127.0.0.1:6379> ZRANGEBYSCORE salary -inf +inf withscores # Incremental arrangement 1) "zhangsan" 2) "500" 3) "xiaoming" 4) "2500" 5) "xiaohong" 6) "5000" 127.0.0.1:6379> ZREVRANGE salary 0 -1 WITHSCORES # Decreasing arrangement 1) "xiaohong" 2) "5000" 3) "xiaoming" 4) "2500" 5) "zhangsan" 6) "500" 127.0.0.1:6379> ZRANGEBYSCORE salary -inf 2500 WITHSCORES # Display salary < = 2500 All members of 1) "zhangsan" 2) "500" 3) "xiaoming" 4) "2500" # =================================================== # zrem removes one or more members from an ordered set # =================================================== 127.0.0.1:6379> ZRANGE salary 0 -1 1) "zhangsan" 2) "xiaoming" 3) "xiaohong" 127.0.0.1:6379> zrem salary zhangsan (integer) 1 127.0.0.1:6379> ZRANGE salary 0 -1 1) "xiaoming" 2) "xiaohong" # =================================================== # The zcard command is used to count the number of elements in the collection. # =================================================== 127.0.0.1:6379> zcard salary (integer) 2 OK # =================================================== # zcount calculates the number of members in the specified score interval in the ordered set. # =================================================== 127.0.0.1:6379> zadd myset 1 "hello" (integer) 1 127.0.0.1:6379> zadd myset 2 "world" 3 "zhangsan" (integer) 2 127.0.0.1:6379> ZCOUNT myset 1 3 (integer) 3 127.0.0.1:6379> ZCOUNT myset 1 2 (integer) 2 # =================================================== # zrank returns the ranking of specified members in an ordered set. The members of the ordered set are arranged in the order of increasing the score value (from small to large). # =================================================== 127.0.0.1:6379> zadd salary 2500 xiaoming (integer) 1 127.0.0.1:6379> zadd salary 5000 xiaohong (integer) 1 127.0.0.1:6379> zadd salary 500 zhangsan (integer) 1 127.0.0.1:6379> ZRANGE salary 0 -1 WITHSCORES # Displays all members and their score values 1) "zhangsan" 2) "500" 3) "xiaoming" 4) "2500" 5) "xiaohong" 6) "5000" 127.0.0.1:6379> zrank salary zhangsan# Display the salary ranking of zhangsan, the lowest (integer) 0 127.0.0.1:6379> zrank salary xiaohong # Display xiaohong's salary ranking, third (integer) 2 # =================================================== # zrevrank returns the ranking of members in an ordered set. The members of the ordered set are sorted according to the decreasing value of the score (from large to small). # =================================================== 127.0.0.1:6379> ZREVRANK salary zhangsan# zhangsan third (integer) 2 127.0.0.1:6379> ZREVRANK salary xiaohong # xiaohong first (integer) 0
sorted set can be used as a weighted queue, such as PU
The score of the communication message is 1 and the score of the important message is 2. Then the worker thread can choose to obtain the work task in the reverse order of the score. Give Way
Priority should be given to the implementation of important tasks.
Leaderboard application, take TOP N operation