Iptables is located in / sbin/iptables. It is a tool used to manage firewall rules. It is called the user state of Linux firewall.
The firewall for packet filtering mainly works in the network layer, and for IP packets, it reflects the processing of the IP address port in the packet.
From the application layer of the external network to the network layer of the firewall, and then to the application layer of the protected network. The actual result shows the restriction processing of the rule.
Priority of packets to firewall: raw table () – > mangle table () – > NAT table () – > filter table (), rules can be specified manually in the table
Iptables is called user space, which belongs to a user state firewall function system.
iptables is a kernel based firewall.
Rule table
| Table name | effect |
|---|---|
| raw table | To determine whether to track the status of the packet, there are two rule chains: OUTPUT and preouting |
| mangle table | Modify the content of the data packet, which is used for traffic shaping, and set a flag for the data packet. There are actually five rule chains: INPUT, OUTPUT, FORWARD, preouting and POSTROUTING |
| nat table | Responsible for network address translation, which is used to modify the source, destination IP address or port in the packet. It includes three rule chains: INPUT, FORWARD and OUTPUT |
| filter table | Be responsible for filtering the data packet and determining whether to release the data packet: INPUT, FORWARD, OUTPUT |
-
Filter table - three chains: INPUT, FORWARD and OUTPUT
Function: filter packet kernel module: iptables_filter. -
Nat table - three chains: preouting, POSTROUTING and OUTPUT
Function: used for network address translation (IP, port) kernel module: iptable_nat -
Mangle table - five chains: preouting, POSTROUTING, INPUT, OUTPUT and FORWARD, that is, they act on all chains
Function: modify the service type and TTL of the packet, and configure the routing to realize the QOS kernel module: IPtable_ Mangle (although this table is so troublesome, we hardly use it when setting policies) -
Raw table - two chains: OUTPUT and preouting
Function: determine whether the data packet is processed by the state tracking mechanism. Kernel module: iptable_raw
(this is not available in REHL4, but don't be afraid. It's not used much)
Important / commonly used are Filter, Nat
Five chains
| Chain name | effect |
|---|---|
| INPUT | Process inbound packets and match the packets whose target IP is local |
| OUTPUT | Processing outbound packets is generally not configured on this chain |
| FORWARD | Process and forward data packets and match the data packets flowing through the machine |
| PREROUTING | The packet is processed before routing, which is used to modify the destination address |
| POSTROUTING | The packet is processed after routing, which is used to modify the source address |
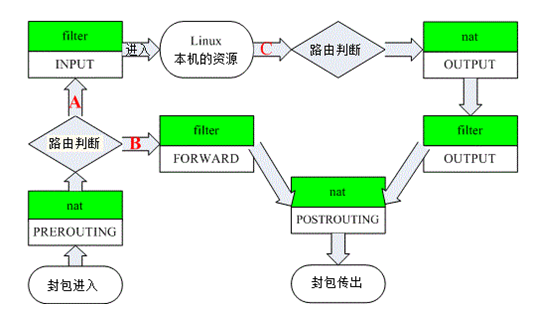
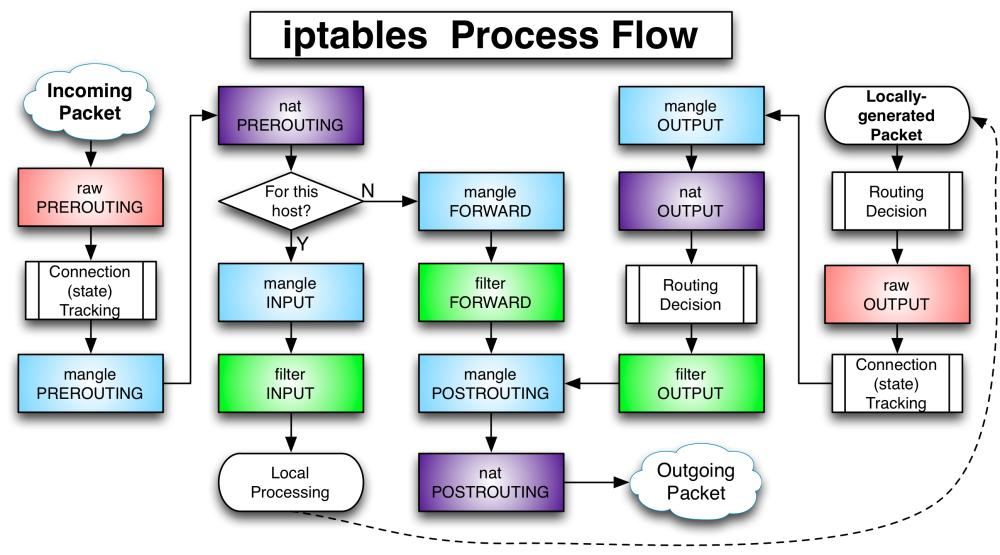
Priority between rule chains (in three cases):
The first case: inbound data flow
Packets arriving at the firewall from the outside will be processed by the forwarding rule chain first (whether to modify the packet address, etc.), and then routing will be carried out (judge where the packet should be sent). If the target host of the packet is the firewall itself (for example, the packets of Internet users accessing the web server in the firewall host), Then the kernel passes it to the INPUT chain for processing (to decide whether to allow it to pass, etc.), and then sends it to the application on the upper layer of the system (such as Apache server) for response.
Second impulse: forwarding data flow
After arriving at the firewall, the packets from the outside world are first processed by the routing rule chain, and then routing will be carried out. If the destination address of the packets is other external addresses (such as the packets of local area network users accessing the QQ site through the gateway), the kernel will pass them to the FORWARD chain for processing (whether to FORWARD or intercept), Then it is handed over to the POSTROUTING rule chain (whether to modify the address of the packet, etc.) for processing.
The third case: outbound data flow
The data packets sent by the firewall to the external address (for example, when testing the public network DNS server in the firewall host) are first processed by the OUTPUT rule chain, then routed, and then passed to the POSTROUTING rule chain (whether to modify the address of the data packet, etc.) for processing.
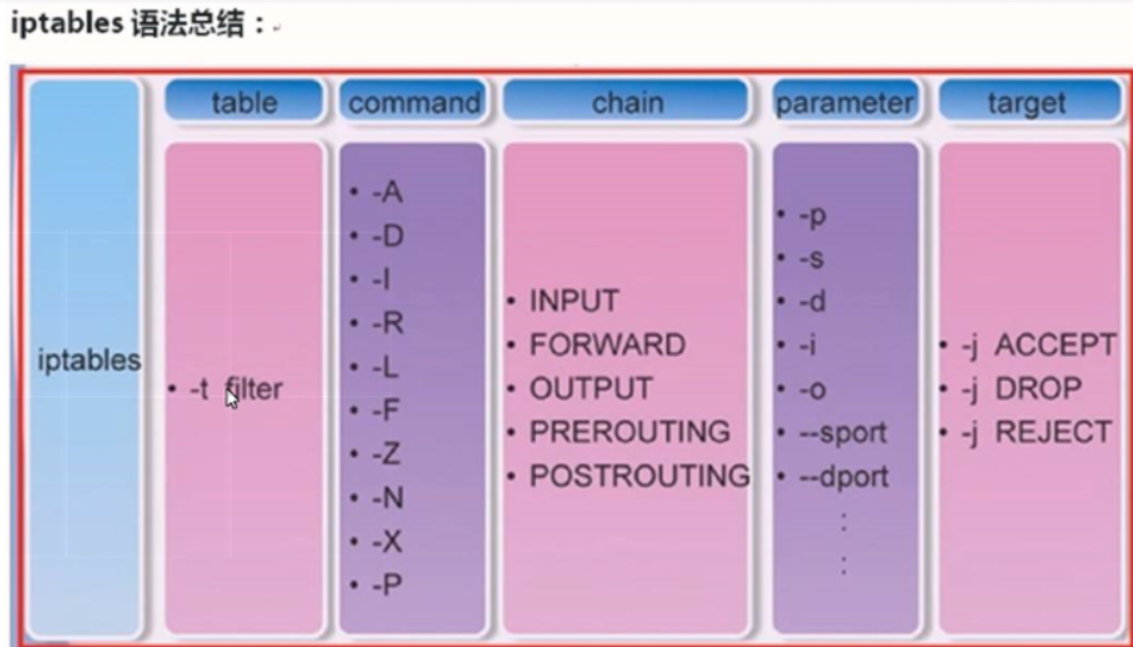
Management control options for iptables command
-A Add at the end of the specified chain( append)A new rule -D Delete( delete)Specify a rule in the chain, which can be deleted by rule sequence number and content -I Insert in the specified chain( insert)A new rule is added in the first line by default -R Modification and replacement( replace)Specify a rule in the chain, which can be replaced by rule sequence number and content -L List( list)Specify all rules in the chain to view -E Renaming a user-defined chain does not change the chain itself -F Empty( flush) -N New construction( new-chain)A user-defined rule chain -X Delete the user-defined rule chain in the specified table( delete-chain) -P Sets the default policy for the specified chain( policy) -Z Clear the byte and packet counters of all chains of all tables -n Use digital form( numeric)Display output results -v View rule table details( verbose)Information -V View version(version) -h Get help( help)
Four ways of firewall processing data packets
Four ways of firewall processing data packets ACCEPT Allow packets to pass DROP Directly discard the data packet without giving any response information REJECT If the packet is rejected, a response message will be sent to the data sender if necessary. LOG stay/var/log/messages Log information is recorded in the file, and then the packet is passed to the next rule
Saving and restoring iptables firewall rules
iptables Saving and restoring firewall rules iptables-save Save the rules to a file and then use the directory rc.d Script under(/etc/rc.d/init.d/iptables)Automatic loading Use command iptables-save To save the rule. General use iptables-save > /etc/sysconfig/iptables Generate a file to save the rule /etc/sysconfig/iptables, It can also be used service iptables save It can automatically save rules in/etc/sysconfig/iptables Yes. When the computer starts, rc.d The script under will use the command iptables-restore Call this file and the rules are automatically restored.
Common strategies of iptables firewall
delete INPUT The first rule of the chain iptables -D INPUT 1 iptables Common strategies of firewall 1.Deny all access to the firewall ICMP Protocol packet iptables -I INPUT -p icmp -j REJECT 2.Allow firewall forwarding except ICMP All packets outside the protocol iptables -A FORWARD -p ! icmp -j ACCEPT Description: use "!" You can reverse the condition. 3.Reject forwarding from 192.168.1.10 The data from the host is allowed to be forwarded.168.0.0/24 Data of network segment iptables -A FORWARD -s 192.168.1.11 -j REJECT iptables -A FORWARD -s 192.168.0.0/24 -j ACCEPT Note: pay attention to put the rejected in front, otherwise it won't work. 4.Discard the slave Internet interface( eth1)Packets with private network address as the source address of the machine entering the firewall iptables -A INPUT -i eth1 -s 192.168.0.0/16 -j DROP iptables -A INPUT -i eth1 -s 172.16.0.0/12 -j DROP iptables -A INPUT -i eth1 -s 10.0.0.0/8 -j DROP 5.Blocking network segment (192).168.1.0/24),Two hours later. # iptables -I INPUT -s 10.20.30.0/24 -j DROP # iptables -I FORWARD -s 10.20.30.0/24 -j DROP # at now 2 hours at> iptables -D INPUT 1 at> iptables -D FORWARD 1 Explanation: we can use this strategy crond It's better to plan a task to complete. [1] Stopped at now 2 hours 6.Only administrators are allowed from 202.13.0.0/16 Network segment usage SSH Log in to the firewall host remotely. iptables -A INPUT -p tcp --dport 22 -s 202.13.0.0/16 -j ACCEPT iptables -A INPUT -p tcp --dport 22 -j DROP Note: this usage is more suitable for remote management of devices, such as those located in branches SQL When the server needs to be managed by the administrator of the head office. 7.Allow native open slave TCP Port 20-1024 Application services provided. iptables -A INPUT -p tcp --dport 20:1024 -j ACCEPT iptables -A OUTPUT -p tcp --sport 20:1024 -j ACCEPT 8.Allow forwarding from 192.168.0.0/24 LAN segment DNS Parse the request packet. iptables -A FORWARD -s 192.168.0.0/24 -p udp --dport 53 -j ACCEPT iptables -A FORWARD -d 192.168.0.0/24 -p udp --sport 53 -j ACCEPT 9.Prohibit other hosts ping Firewall host, but allow from firewall ping Other hosts iptables -I INPUT -p icmp --icmp-type Echo-Request -j DROP iptables -I INPUT -p icmp --icmp-type Echo-Reply -j ACCEPT iptables -I INPUT -p icmp --icmp-type destination-Unreachable -j ACCEPT 10.Prohibit forwarding from MAC The address is 00:0 C: 29: 27: 55: 3F And host packets iptables -A FORWARD -m mac --mac-source 00:0c:29:27:55:3F -j DROP explain: iptables Used in“-m The matching is displayed by calling in the form of "module keyword". Let's use it here“-m mac –mac-source"To represent the source of the packet MAC Address. 11.Allow the firewall to be opened locally TCP Ports 20, 21, 25, 110 and passive mode FTP Port 1250-1280 iptables -A INPUT -p tcp -m multiport --dport 20,21,25,110,1250:1280 -j ACCEPT Note: used here“-m multiport –dport"To specify the destination port and range 12.No transfer source IP The address is 192.168.1.20-192.168.1.99 of TCP Data packet. iptables -A FORWARD -p tcp -m iprange --src-range 192.168.1.20-192.168.1.99 -j DROP Note: used here“-m –iprange –src-range"appoint IP Range. 13.Forwarding forbidden and normal TCP Connection independent non - syn Request packet. iptables -A FORWARD -m state --state NEW -p tcp ! --syn -j DROP Description:“-m state"Indicates the connection status of the packet“ NEW"It means that it has nothing to do with any connection. It's new! 14.Deny access to new packets of the firewall, but allow response connections or packets related to existing connections iptables -A INPUT -p tcp -m state --state NEW -j DROP iptables -A INPUT -p tcp -m state --state ESTABLISHED,RELATED -j ACCEPT Description:“ ESTABLISHED"A packet indicating that a request has been responded to or a connection has been established“ RELATED"Indicates that it is related to the established connection, such as FTP Data connection, etc. 15.Open only local web Service (80) FTP(20,21,20450-20480),Release the response packets sent by the external host to other ports of the server, and discard other inbound packets. iptables -I INPUT -p tcp -m multiport --dport 20,21,80 -j ACCEPT iptables -I INPUT -p tcp --dport 20450:20480 -j ACCEPT iptables -I INPUT -p tcp -m state --state ESTABLISHED -j ACCEPT iptables -P INPUT DROP